IPv6 Sandbox
Information
KringleCon - Talks Lobby
 https://gist.github.com/chriselgee/c1c69756e527f649d0a95b6f20337c2f
https://gist.github.com/chriselgee/c1c69756e527f649d0a95b6f20337c2f
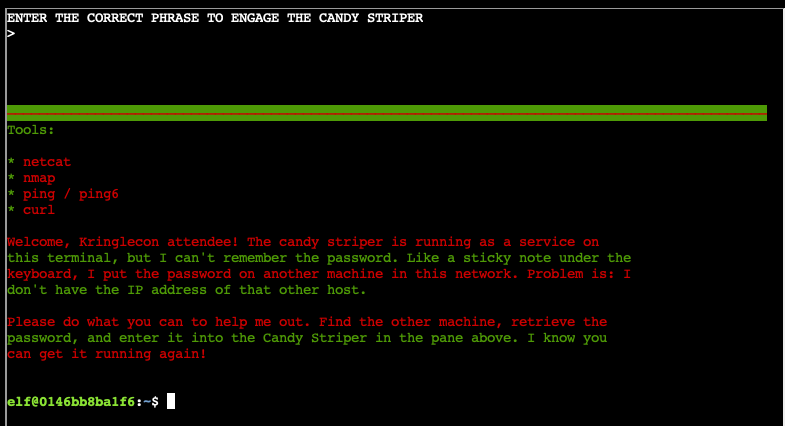
Solution
First I checked what my IP address was, hoping there was like an IPv6 CIDR range type thing.
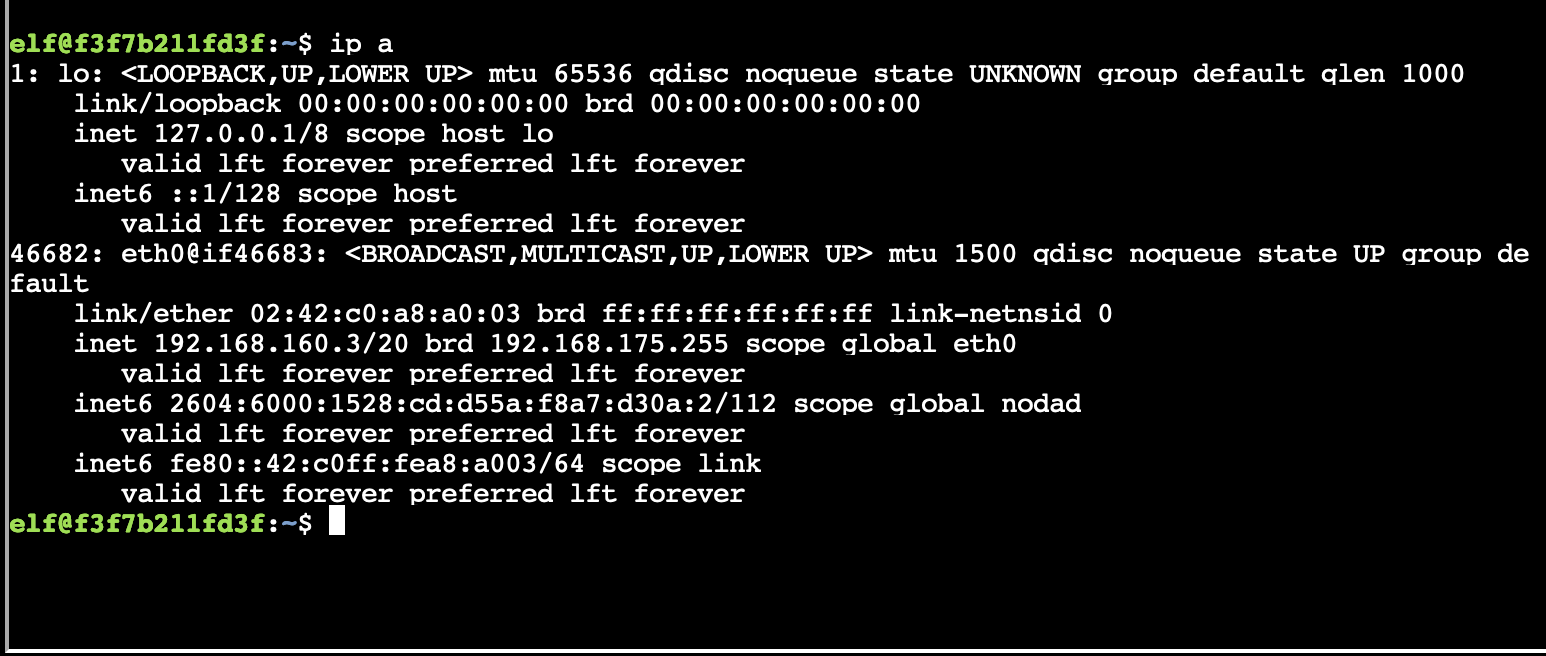
So there's two:
2604:6000:1528:cd:d55a:f8a7:d30a:2/112
fe80::42:c0ff:fea8:a003/64
Can nmap accept cidr notation for IPv6 target ranges? Yes, it can based on nmap.org entry found via web search. Also, non-global IPv6 address scope needs to have a zone id suffix, which is the % sign followed by the interface to use, ie '%eth0' appended to the address.
Tried to run the nmap scan with the cidr notation plus eth iface but that was erroring out. I realized I needed to add the '-6' flag for IPv6 mode in nmap, but that was still erroring out. Maybe I'll try converting the cidr to a range and trying that?
Ahhh ok. I needed to specify the %eth0 BEFORE the CIDR notation. So that seemed to work, but retransmission cap was hit for everything? Oh, do I normally do --max-retries 1 or 0? I'll try with 1 now I guess.
Still nothing.
I guess I'll try this other IPv6 subnet.
nmap -6 -T4 --max-retries 1 -p- -oN nmap.quick 2604:6000:1528:cd:d55a:f8a7:d30a:2/112
Nothing there either. Hm, maybe the other machine is on the IPv4 network?
Ok that was weird, it didn't look like any of the hosts were up, but after I let if finish it found two.
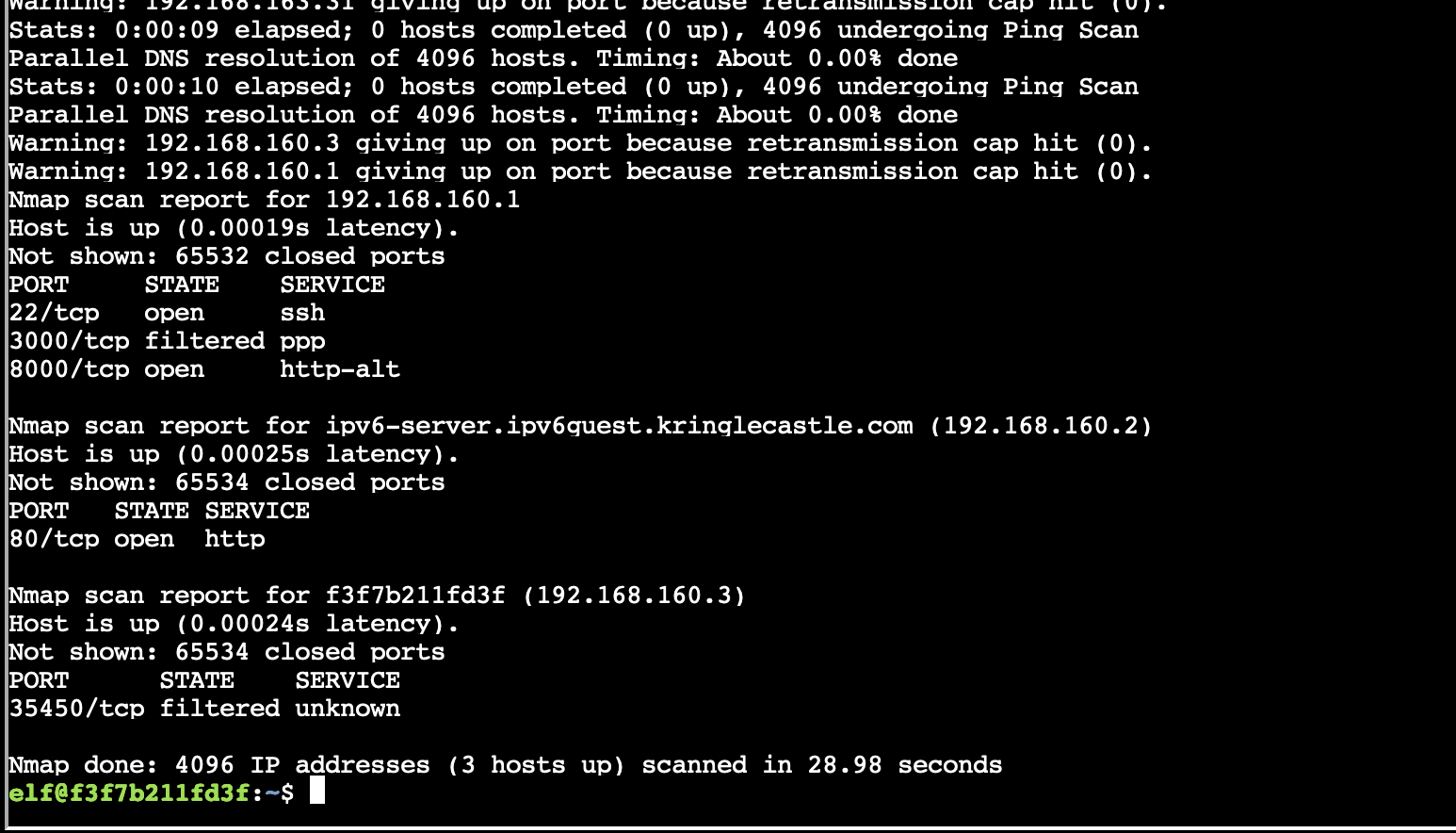
Since port 80 was open on 192.168.160.2 I decided to curl that, and got a response indicating I should try to access the site via IPv6.
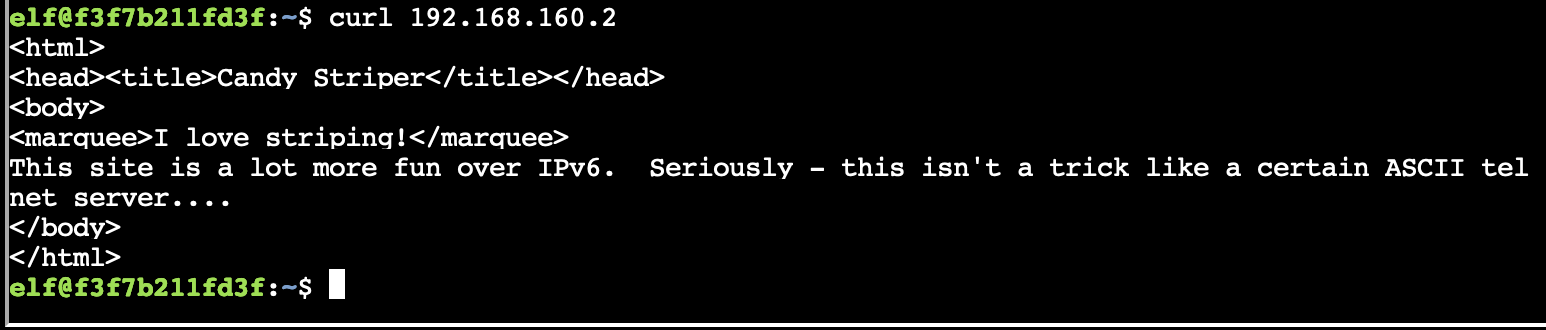
Ok, let's do that. Wait, how do I find the IPv6 address for that host?
I tried to curl rcp/8000 on 192.168.160.1, response indicated I needed an API key.

Oh! Am I on the 192.168.160.2 machine? Because they said the candy striper service was running on this machine….
Ah ok. Looking at that linked gist, there are a few commands that can be used to find link local addresses for systems on my network segment, so I ran the first one and got 4 replies.
ping6 ff02::1 -c2
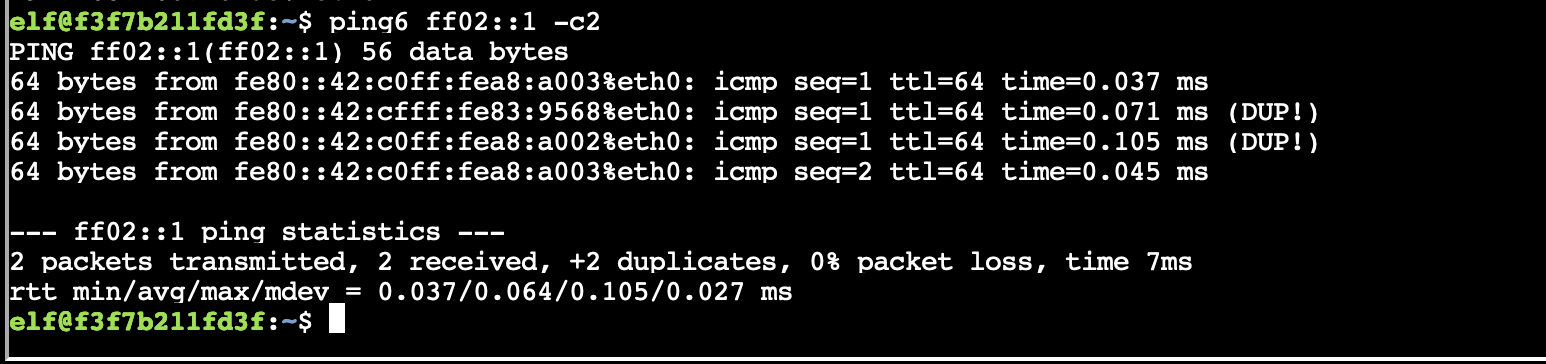
fe80::42:c0ff:fea8:a002%eth0
fe80::42:c0ff:fea8:a003%eth0
fe80::42:cfff:fe83:9568%eth0
When I tried to curl the first one, it said to try connecting on the other open port, so I guess I'll nmap that link local address.
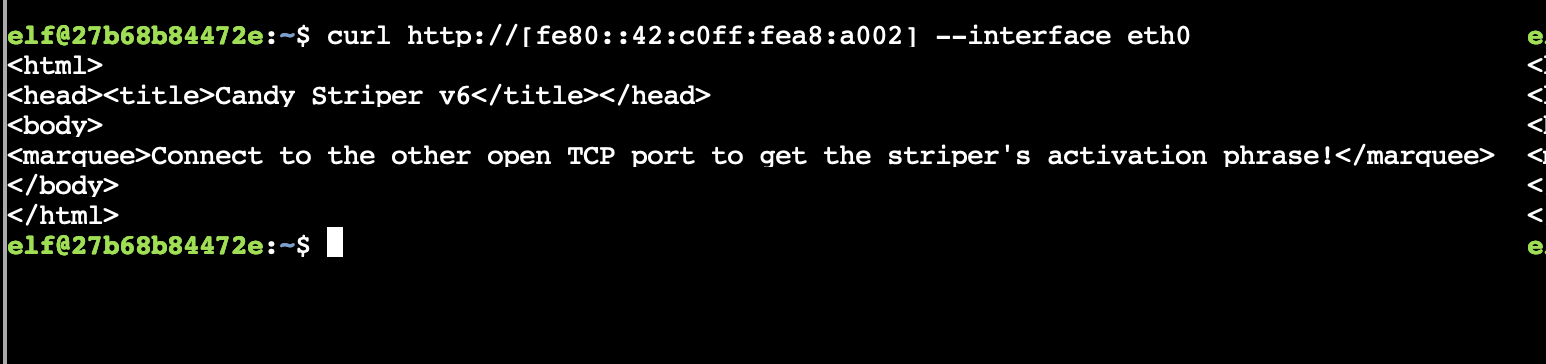
Ran nmap against it.
nmap -6 -T4 --max-retries 0 -p- fe80::42:c0ff:fea8:a002%eth0
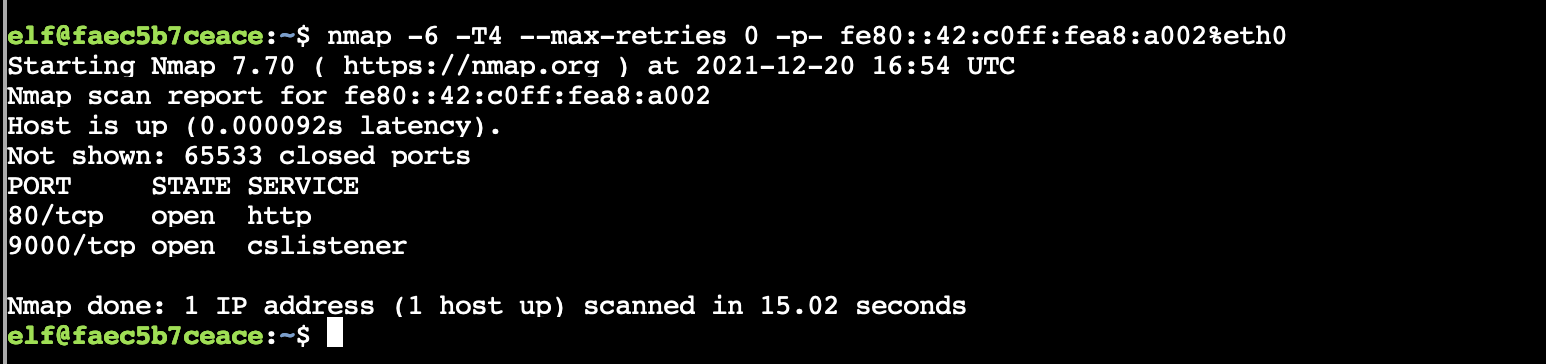
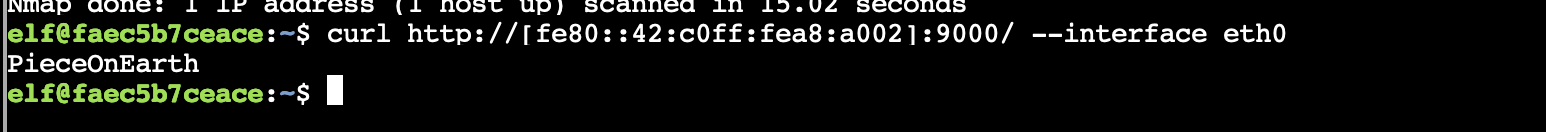
Ok, so I made a curl request for / on the other open port of 9000, and got the phrase PieceOnEarth.
Ran nmap against another one of the up hosts.
nmap -6 -T4 --max-retries 0 -p- fe80::42:cfff:fe83:9568%eth0
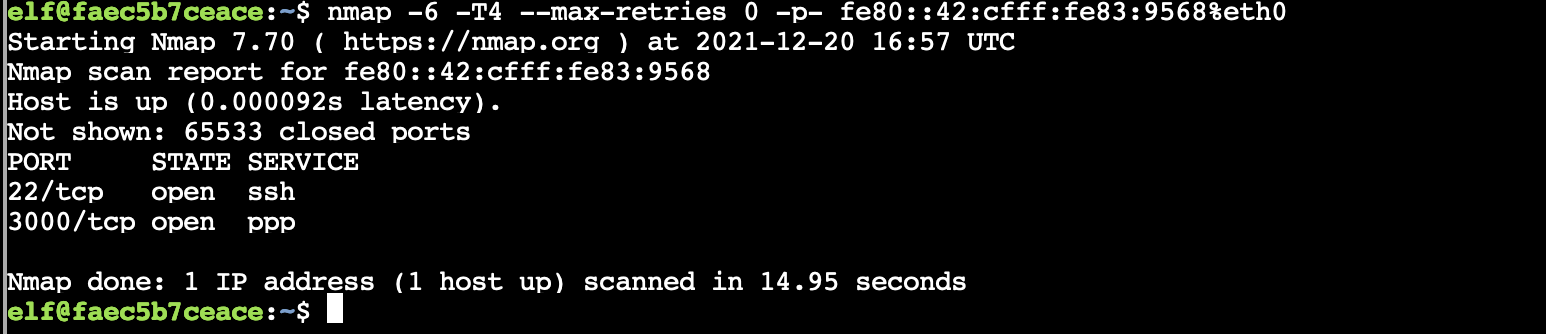
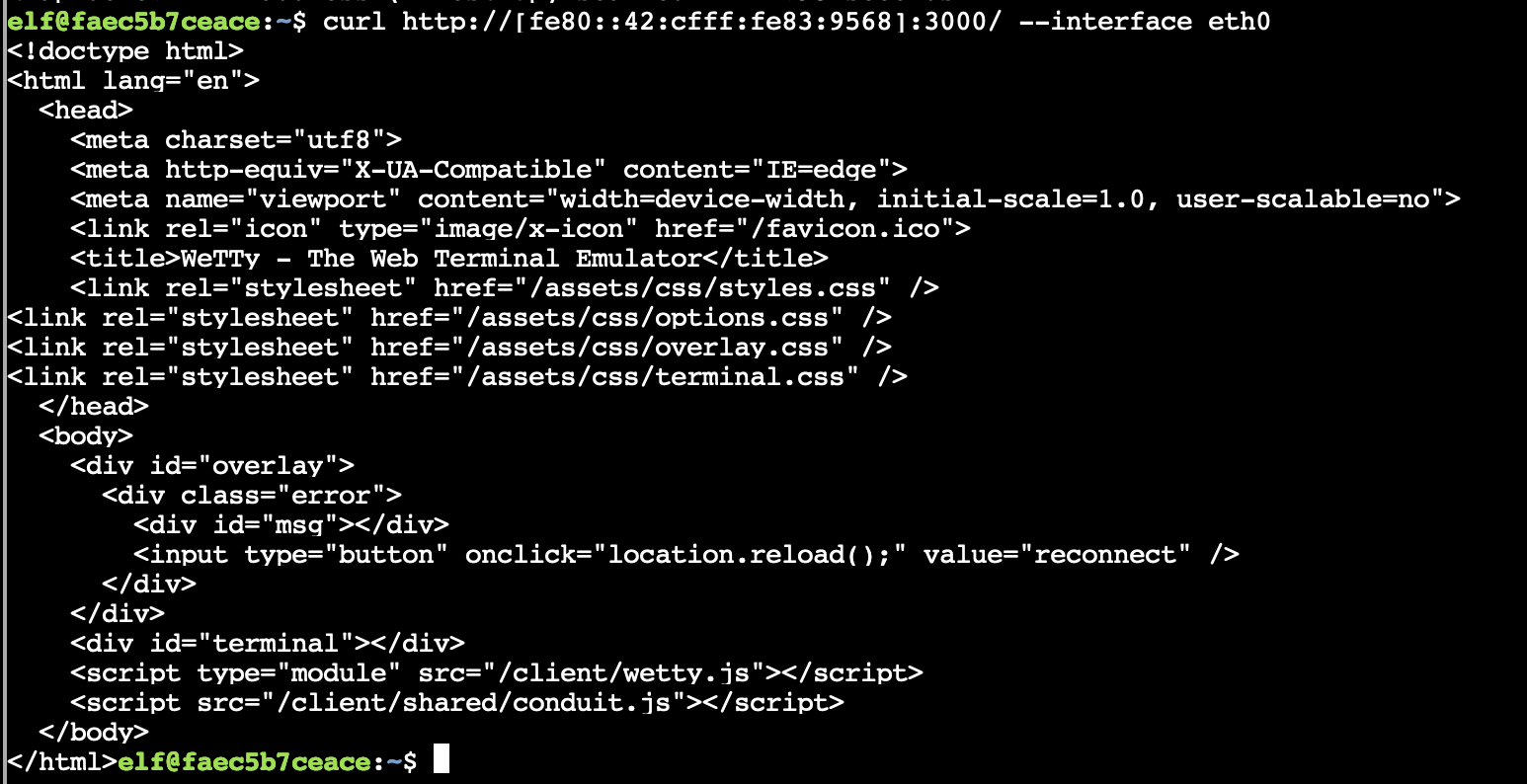
Tried connecting to the open port tcp/3000, looks like that trick site they mentioned earlier.
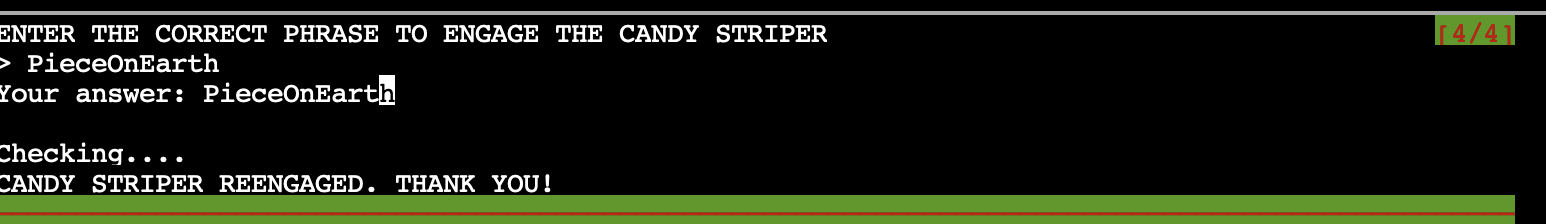
Oh jesus fucking christ. All I had to do was enter that phrase at the top of the terminal, I didn’t need to go hunting for another network service to key it in on lol.
Next: term-6