Kerberoasting On An Open Fire
Introduction
Location - Unknown
- Kerberoasting on an Open Fire
Difficulty: 5/5
Obtain the secret sleigh research document from a host on the Elf University domain. What is the first secret ingredient Santa urges each elf and reindeer to consider for a wonderful holiday season? Start by registering as a student on the ElfU Portal. Find Eve Snowshoes in Santa's office for hints.
ElfU Portal: https://register.elfu.org/
Conversation
Hints from Eve Snowshoes after completing HoHo … No terminal challenge:
talk: Chris Davis, Demonstrating Active Directory Penetration Testing | KringleCon 2021
Kerberoasting: https://gist.github.com/TarlogicSecurity/2f221924fef8c14a1d8e29f3cb5c5c4a
OneRuleToRuleThemAll.rule: https://github.com/NotSoSecure/password_cracking_rules
CeWL: https://github.com/digininja/CeWL
Bloodhound: https://github.com/BloodHoundAD/BloodHound
methods: https://www.specterops.io/assets/resources/an_ace_up_the_sleeve.pdf
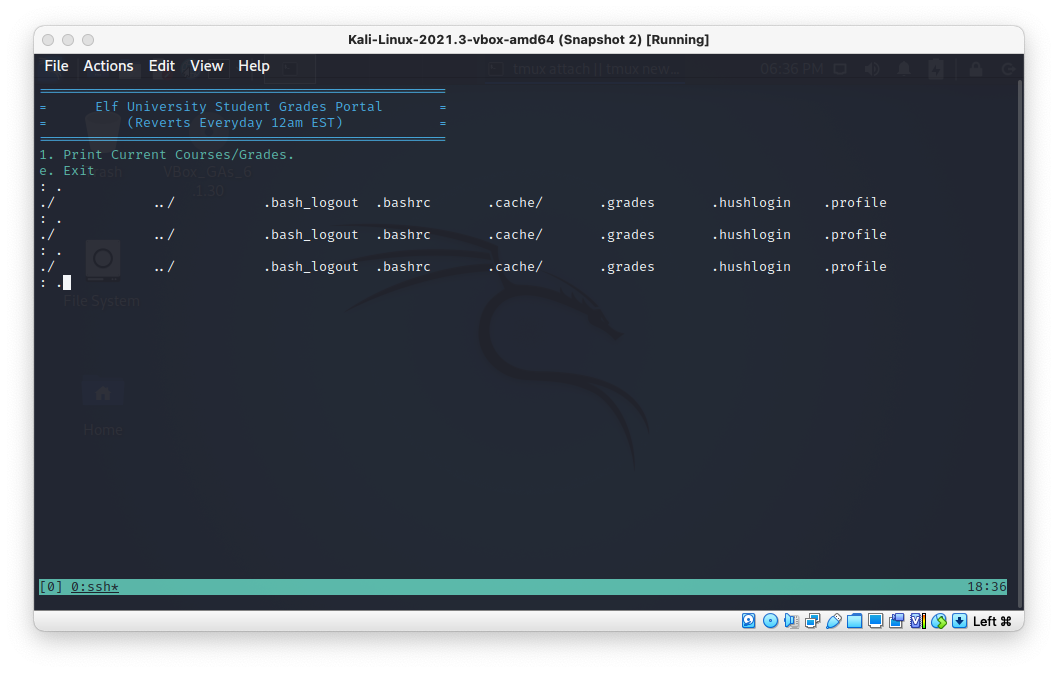
Solution
Ok, so I hit the site and registered.
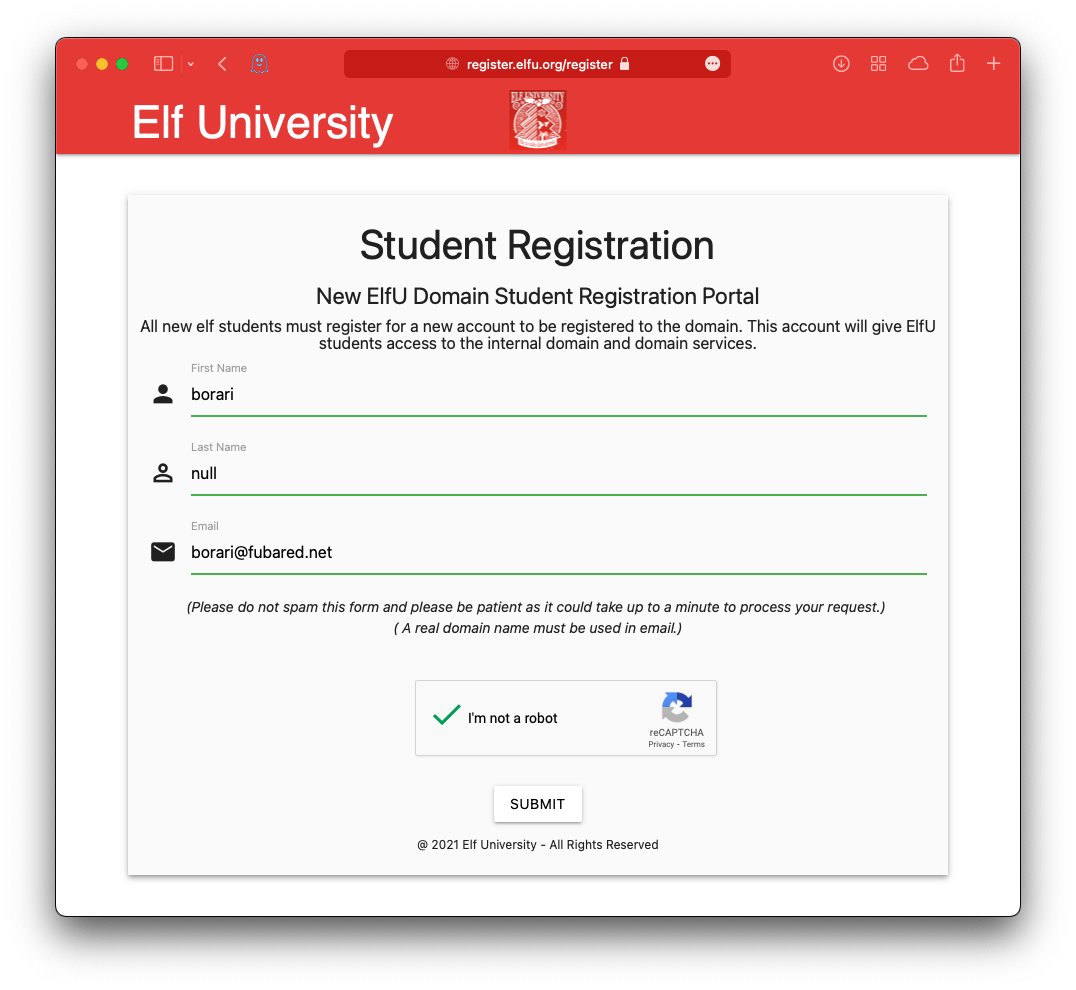 Got the instructions for getting into the domain.
Got the instructions for getting into the domain.
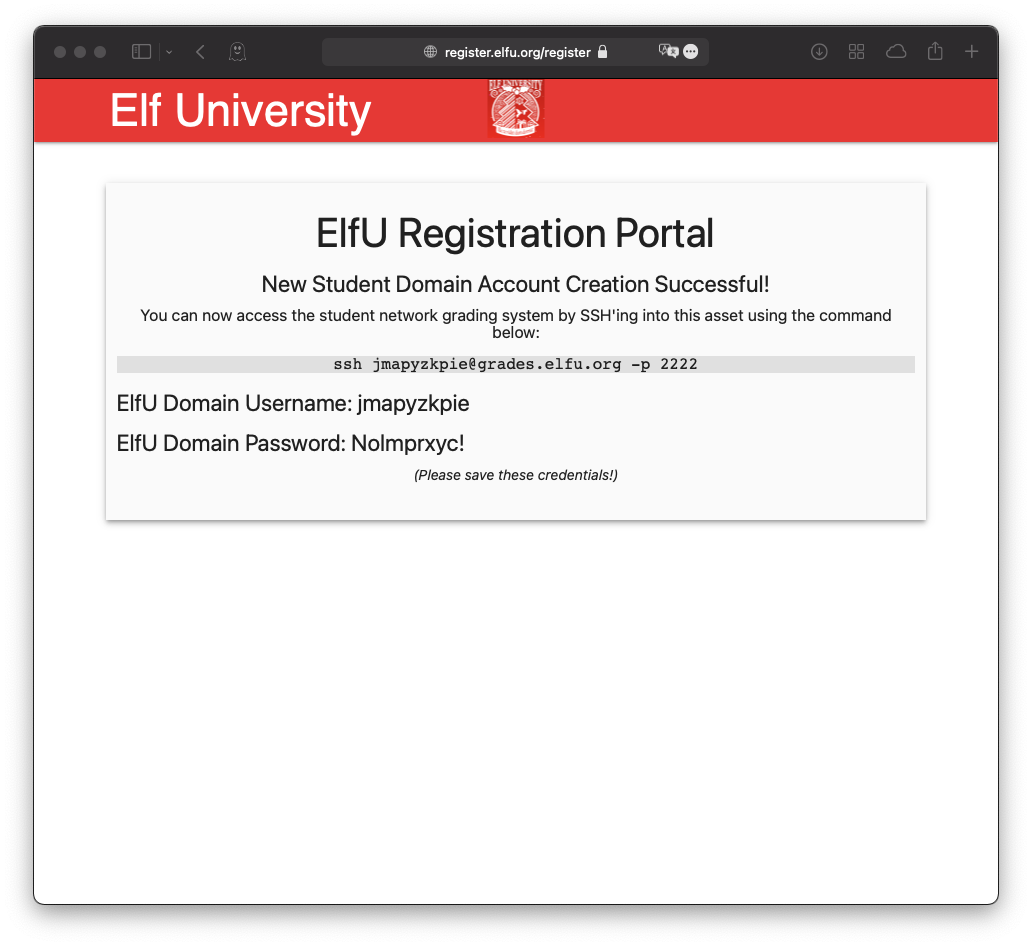
ssh jmapyzkpie@grades.elfu.org -p 2222
User: jhmrryypfy
Password: Ysvckvgyd@
Logged in via ssh
 What's this escape vim thing?
What's this escape vim thing?
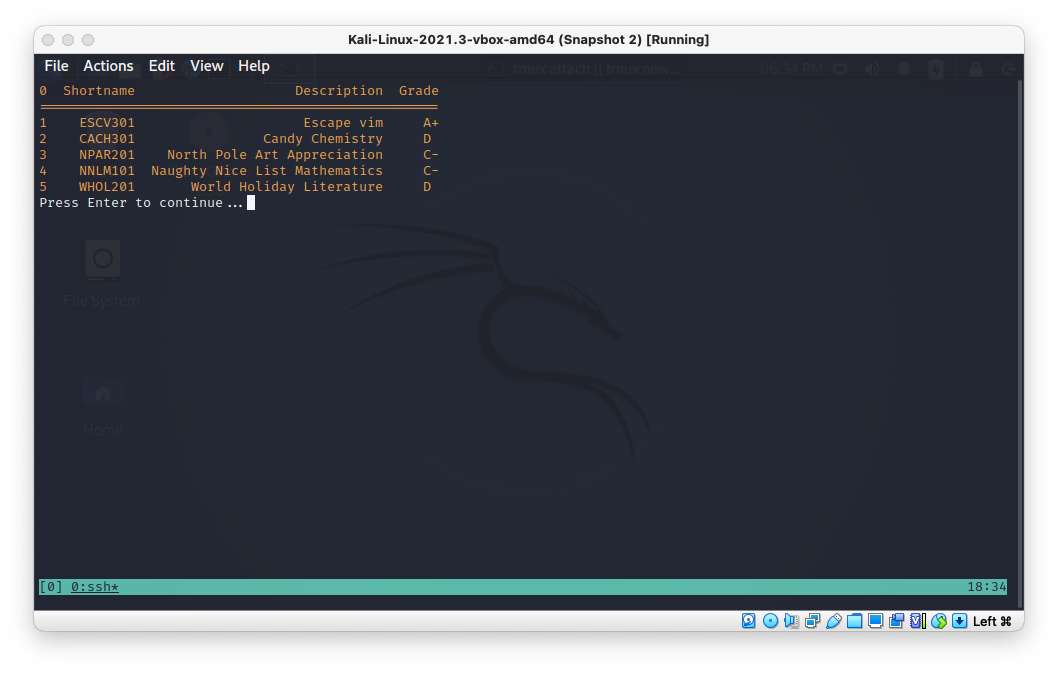 When I spam the Esc key I see that I'm in a shell?
When I spam the Esc key I see that I'm in a shell?
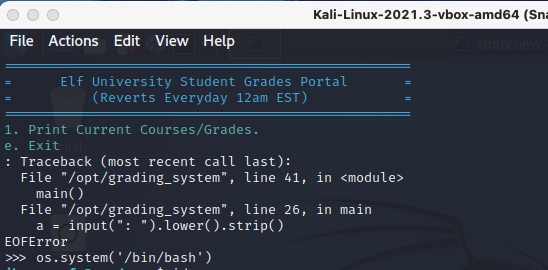
 Pressing ctrl+D brings up a python traceback and dumps me into a python shell, where I can then open bash with os.system('/bin/bash').
Pressing ctrl+D brings up a python traceback and dumps me into a python shell, where I can then open bash with os.system('/bin/bash').
I can then change my shell so reconnects go straight to bash.
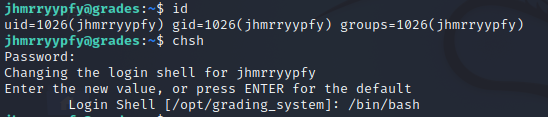
I can see what other machines this one knows about with arp -a.
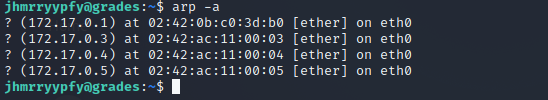
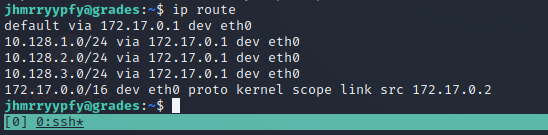
Well that hint said something about a domain controller on a 10.x.x.x network, so let's see what other networks I can route to from this machine.
Notes
I ran out of time and didn't finish this objective.
Next: obj-9