Objective 2: Investigate S3 Bucket
Launching the objective presents another interactive terminal.
Exploring home dir.
Alright, so whats in bucket_finder/?
Whats in the wordlist?
Ok, the tool just brute forces for amazon buckets. I'll add some more names to the wordlist. I added the names I found in the directory and the three turtle dove's names.
Added last names to wordlist. Still no.
Ok, on login there was reference to wrapper3000. Is that anywhere on the local filesystem? No.
Shit, ok, wait. What if I run that into bucket_finder?
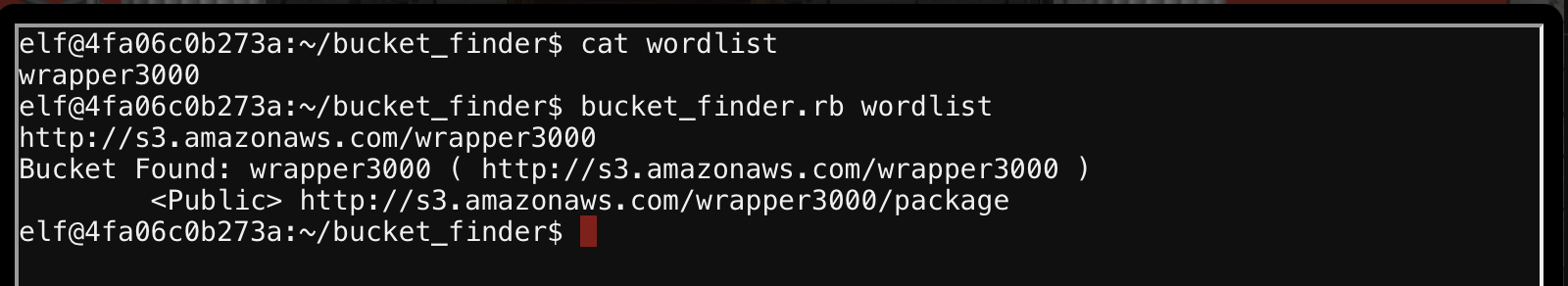
Alright, time to download the file.
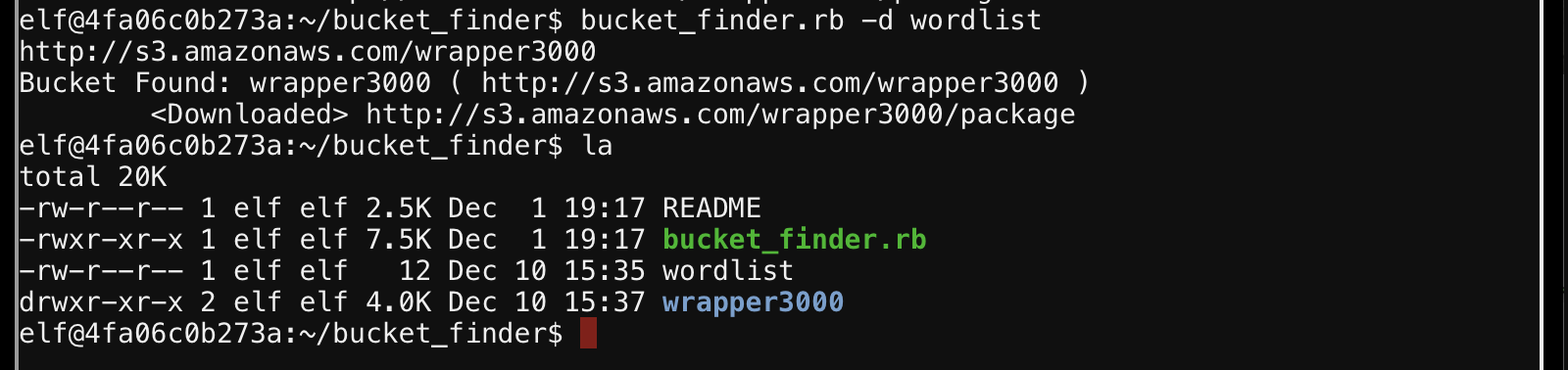
What’s in the folder?
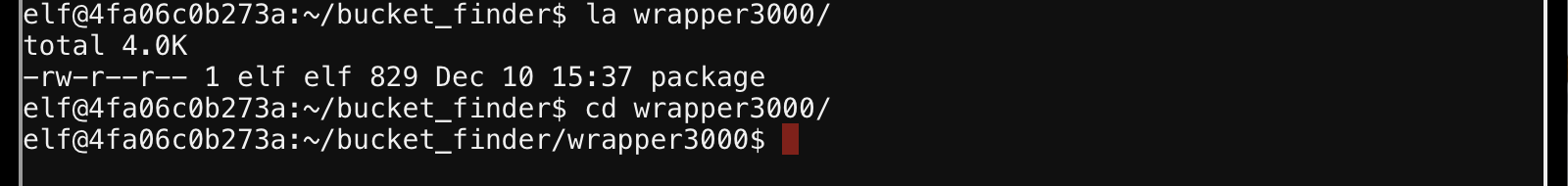
Whats this package?
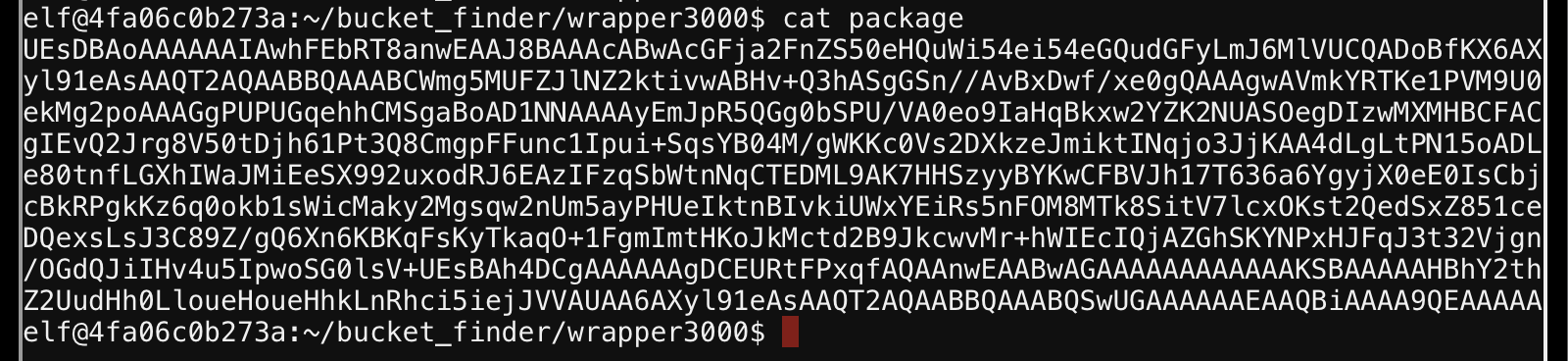
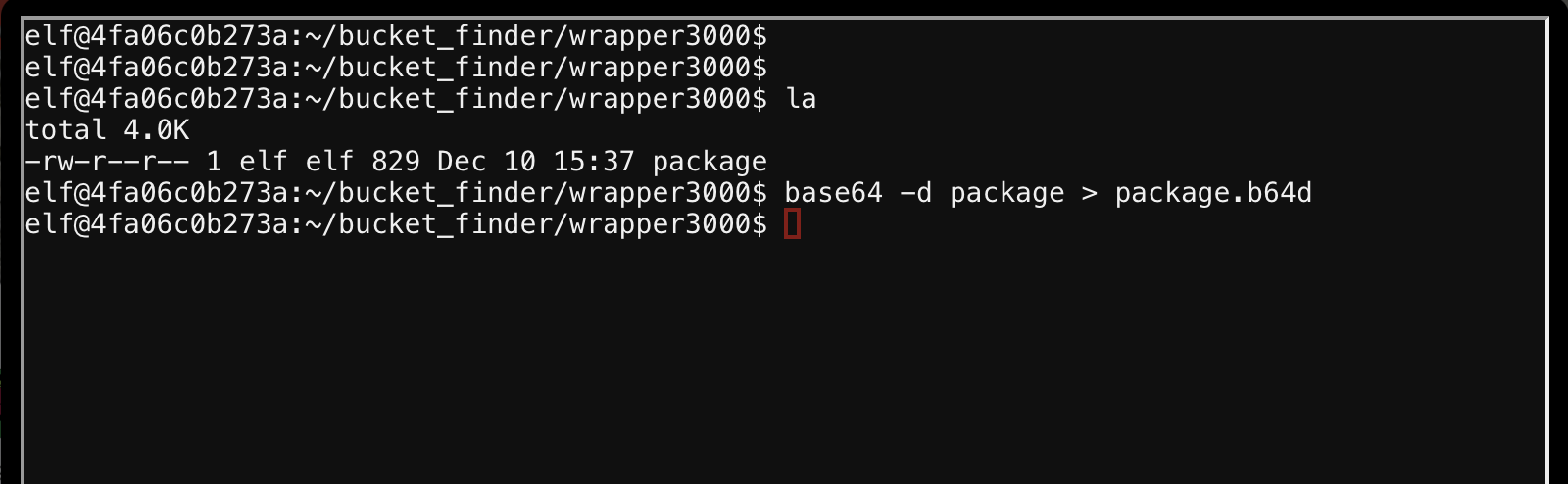
Can I base64 decode it? Yeah, looks like it has the PK magic header, and the string package.txt.Z.xz.xxd.tar.bz.
I redirected the output to package.b64d.
Extracting the archive with tar failed.
Can I unzip it? That's the PK header for real right? Yeah, and now I have a tar.bz2
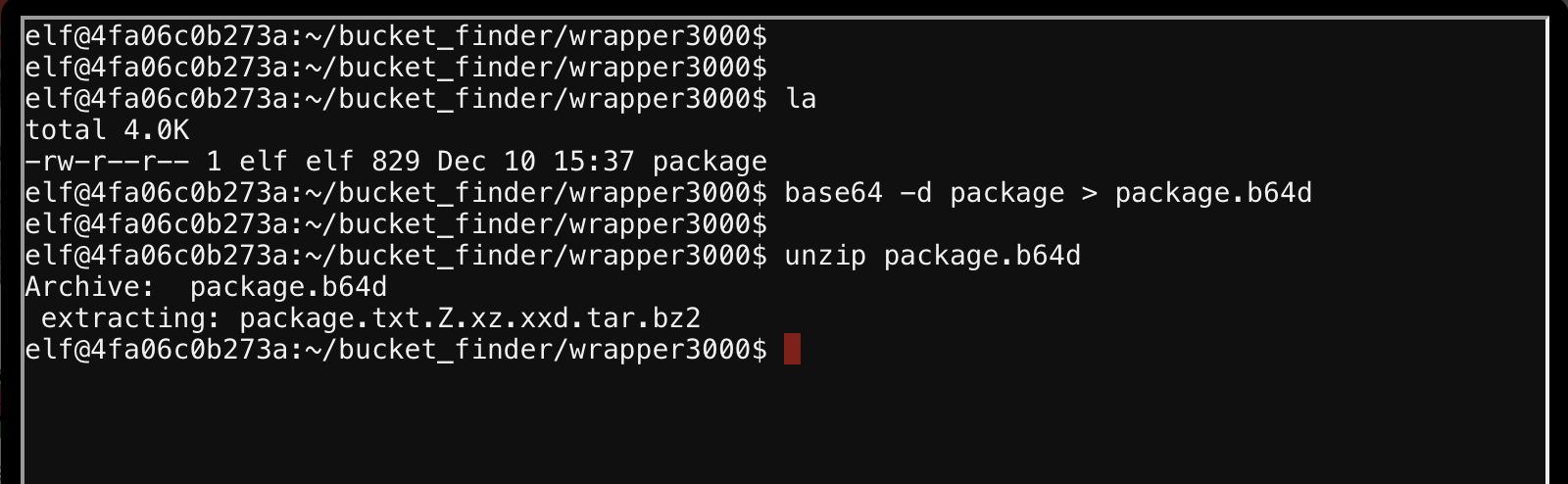
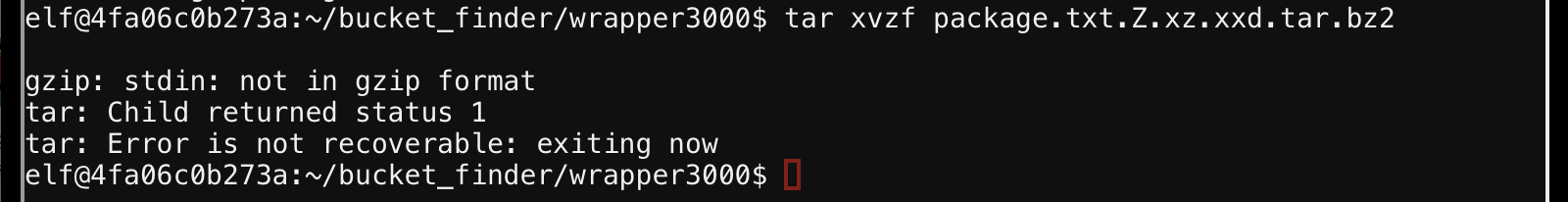
Now can I extrat the tarball? No?
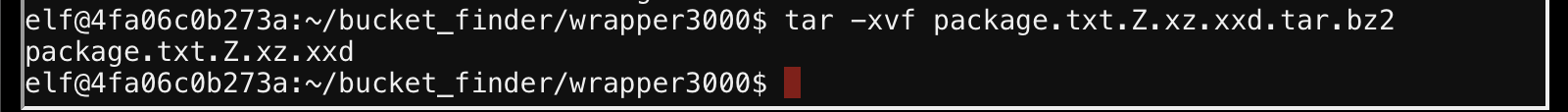
I don't know, I was adding a bad flag, and forgot to use the tac. Using -xvf worked fine.
Now the extracted file is an xxd hex dump of a 7z archive. I can reverse the hexdump with xxd -r.
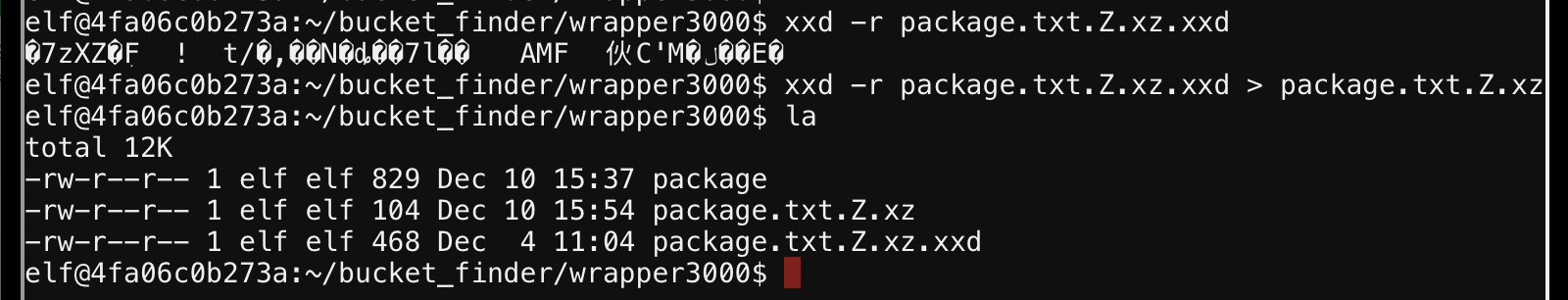
Tried uncompressing with 7z, not installed. Tried with tar, didn’t work. Found out about the xz tool. I looked at the help for syntax.
Then decompressed the file.
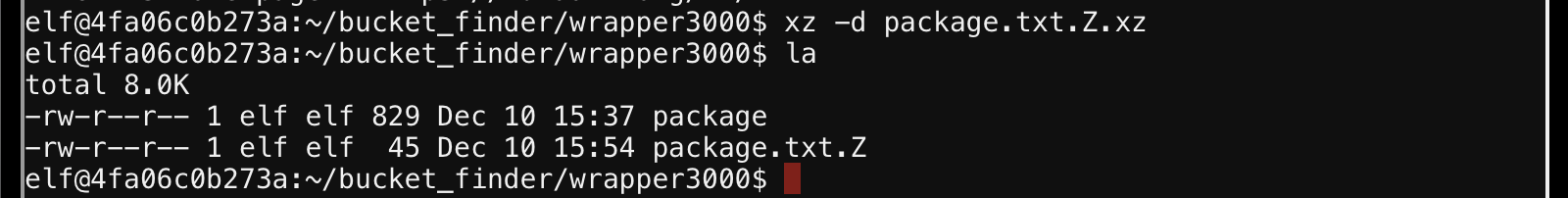
What the fuck is a .Z file? Oh, just another compresion tool…
Can I uncompress? Yup.
What's the txt file contents?
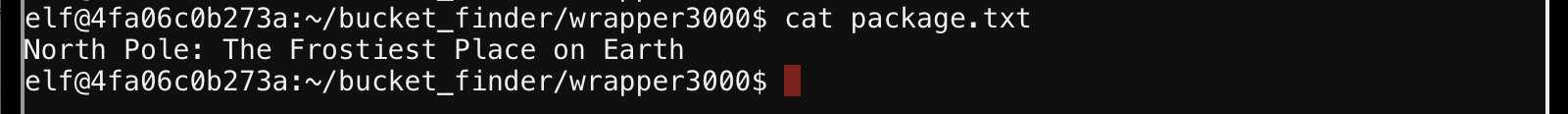
North Pole: The Frostiest Place on Earth
Next: 1F: Entry