Router Pwn
Group Intro
Interested in more challenges like this? Dive deep into the offensive skills to solve them in the following course(s):
- SEC504: Hacker Tools, Techniques, and Incident Handling
- SEC560: Network Penetration Testing and Ethical Hacking
- SEC660: Advanced Penetration Testing, Exploit Writing, and Ethical Hacking
Flags
| Objective | Flag |
|---|---|
| 0x01 | catch22$ |
| 0x02 | thebruceleeband |
| 0x03 | 10.13.37.101 |
| 0x04 | reelbigfish |
| 0x05 | mustardplug |
| 0x06 | thespecials |
| 0x07 | bosstones7 |
| 0x08 | maytals |
| 0x09 | skatalites31 |
| 0x0A | Madness |
| 0x0B | GOTREKT |
| 0x0C | 9MFFZXHAKZ4 |
| 0x0D | ftppassword! |
| 0x0E | flag{its_a_long_way_here} |
| 0x0F | lessthanjake12 |
0x01
Objective
What is the HSRP password?
Files
Solution
First thing, opened pcap saw HSRP packets.
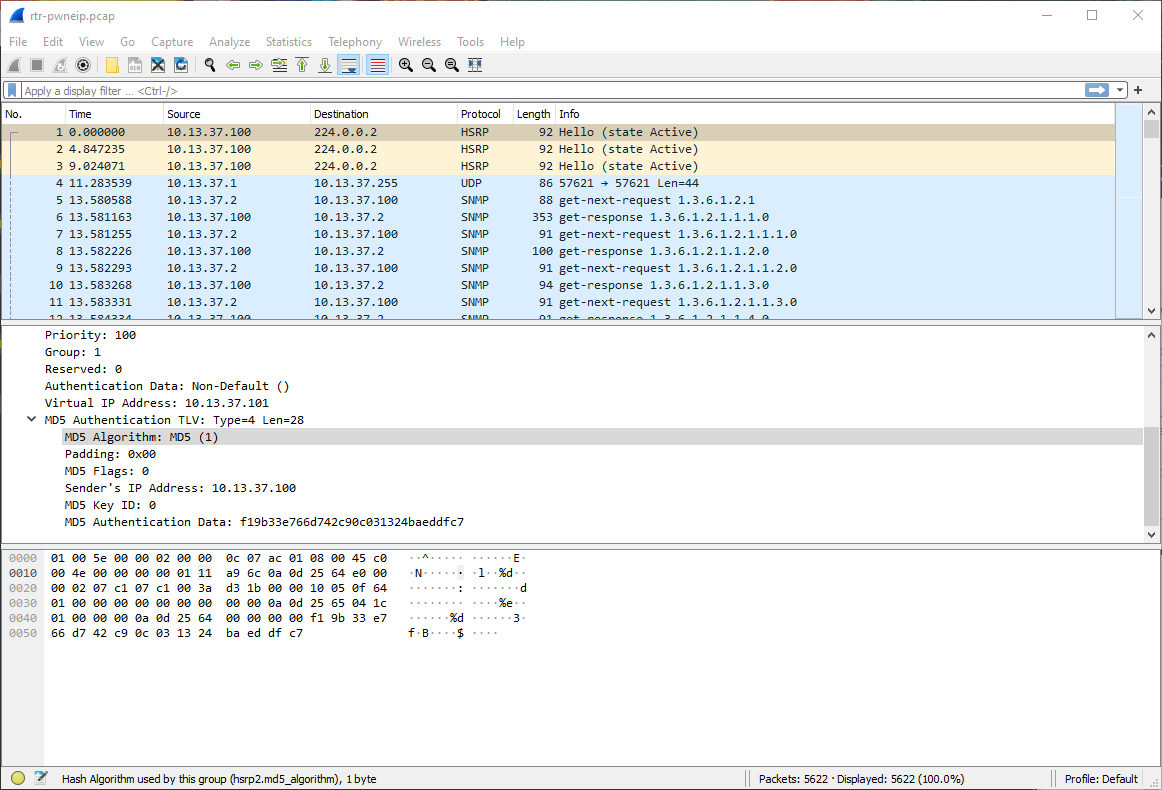
f19b33e766d742c90c031324baeddfc7
I guess I'll try to crack it with hashcat?
hashcat -m 0 -a 0 hash.md5 /usr/share/wordlists/rockyou.txt
Didn't work. Googled cracking HSRP MD5, found that JtR has built in support. https://john-users.openwall.narkive.com/cBMA0yv3/cracking-hsrp-md5-authentication-hashes
Ok, I needed to run pcap2john to get the hashes in the proper format. I couldn't run pcap2john.py.
Installing the required packages failed.
pip install --user dpkt
DEPRECATION: Python 2.7 reached the end of its life on January 1st, 2020. Please upgrade your Python as Python 2.7 is no longer maintained. pip 21.0 will drop support for Python 2.7 in January 2021. More details about Python 2 support in pip can be found at [https://pip.pypa.io/en/latest/development/release-process/#python-2-support](https://pip.pypa.io/en/latest/development/release-process/#python-2-support) pip 21.0 will remove support for this functionality.
Collecting dpkt
Downloading dpkt-1.9.7.2.tar.gz (165 kB)
|████████████████████████████████| 165 kB 3.4 MB/s
ERROR: Command errored out with exit status 1:
command: /usr/bin/python2 -c 'import sys, setuptools, tokenize; sys.argv[0] = '"'"'/tmp/pip-install-wcrnii/dpkt/setup.py'"'"'; __file__='"'"'/tmp/pip-install-wcrnii/dpkt/setup.py'"'"';f=getattr(tokenize, '"'"'open'"'"', open)(__file__);code=f.read().replace('"'"'\r\n'"'"', '"'"'\n'"'"');f.close();exec(compile(code, __file__, '"'"'exec'"'"'))' egg_info --egg-base /tmp/pip-pip-egg-info-czBOYS
cwd: /tmp/pip-install-wcrnii/dpkt/
Complete output (10 lines):
/usr/lib/python2.7/distutils/dist.py:267: UserWarning: Unknown distribution option: 'zip_safe'
warnings.warn(msg)
/usr/lib/python2.7/distutils/dist.py:267: UserWarning: Unknown distribution option: 'install_requires'
warnings.warn(msg)
usage: setup.py [global_opts] cmd1 [cmd1_opts] [cmd2 [cmd2_opts] ...]
or: setup.py --help [cmd1 cmd2 ...]
or: setup.py --help-commands
or: setup.py cmd --help
error: invalid command 'egg_info'
----------------------------------------
ERROR: Command errored out with exit status 1: python setup.py egg_info Check the logs for full command output.
To fix, I had to install the apt package python-setuptools.
apt install python-setuptools
Then I could pip install dpkt and scapy.
python -m pip install dpkt
pip install --user scapy
Now running is successful.
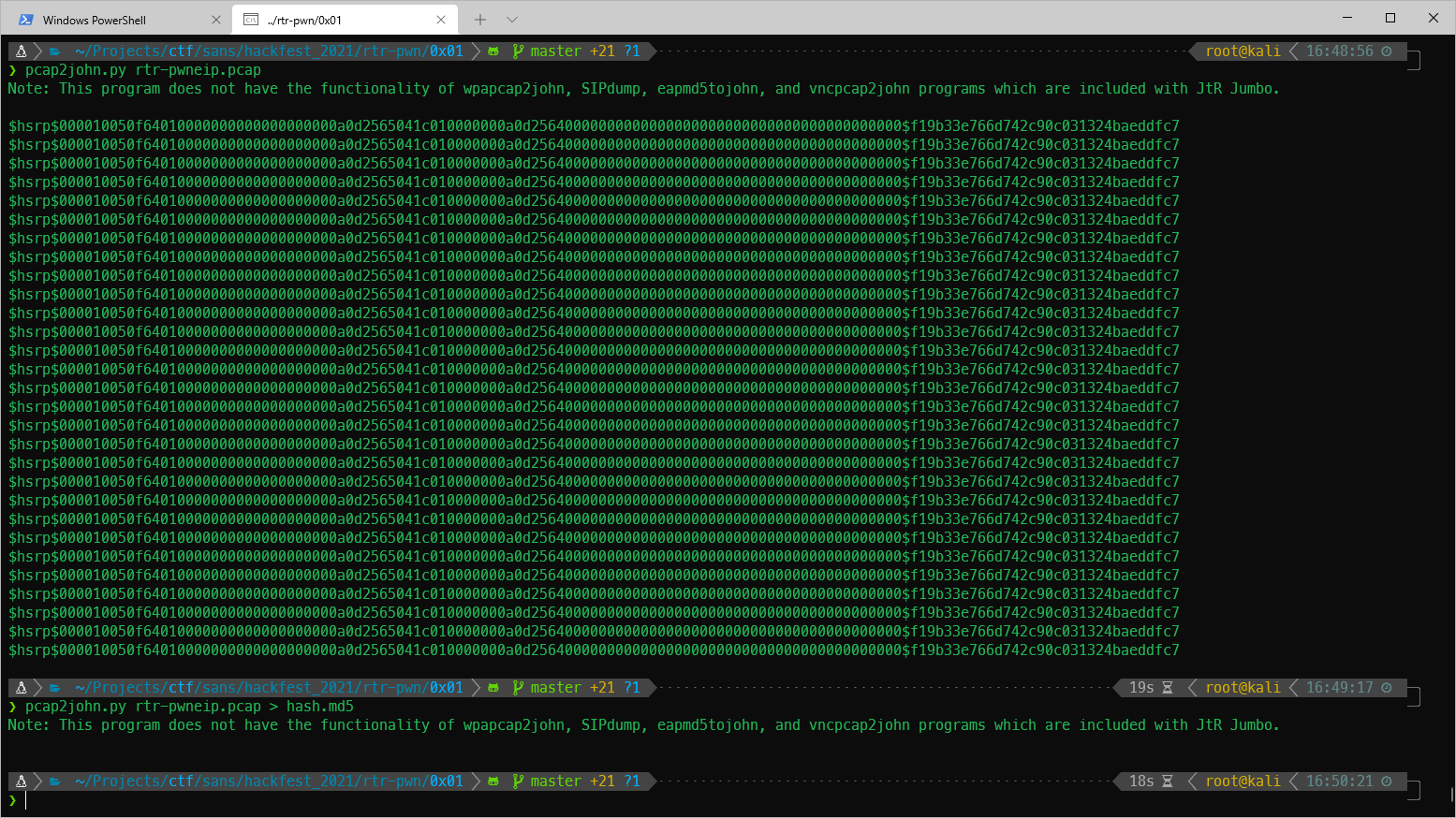
Saved output to hash.hsrp.
Ran john on file.
john --wordlist=/usr/share/wordlists/rockyou.txt --format=hsrp hash.hsrp
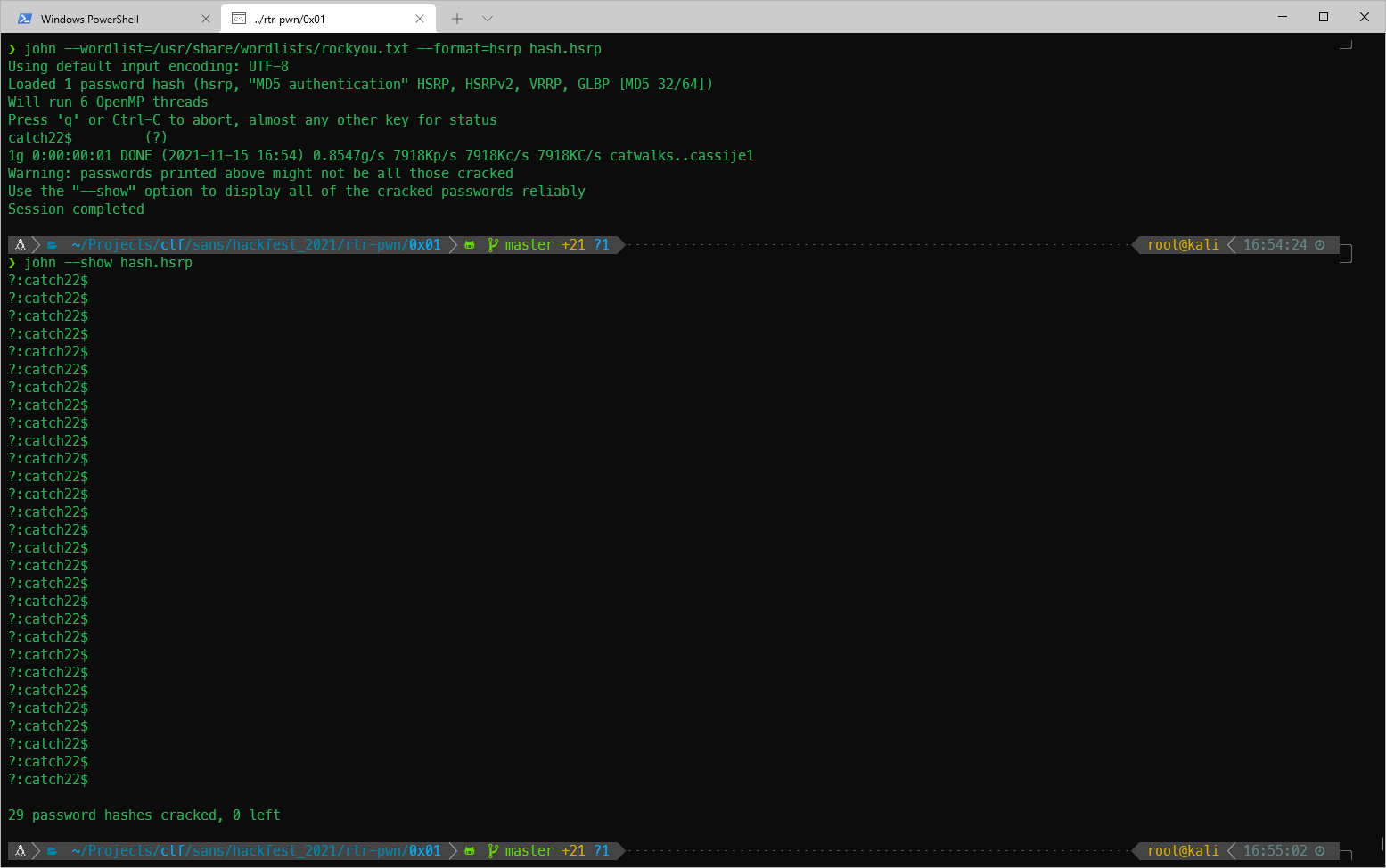
Output shows that password should be catch22$.
0x02
Objective
What is the HSRP group?
Files
Solution
What is the HSRP Group?
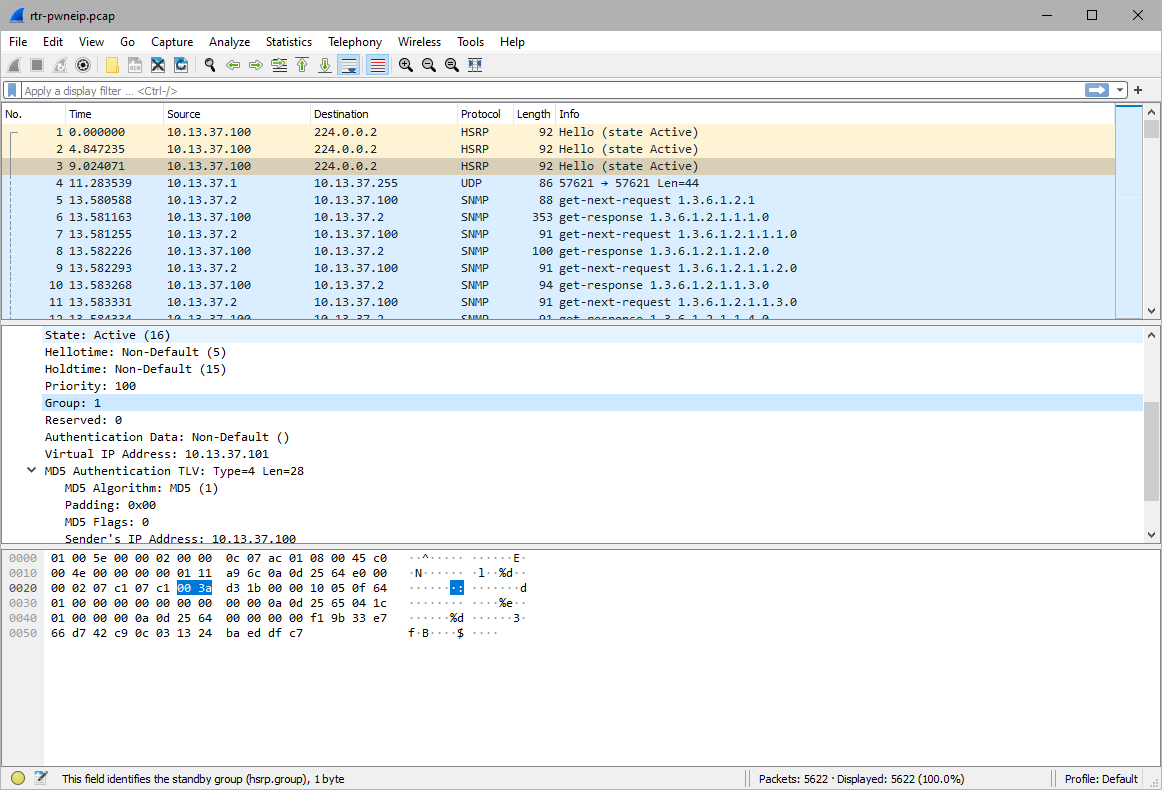
1
There's some other information for the standby name, oh, this is the hsrp shit, group name must be the cleartext 'thebruceleeband'. The key-string isn't raw md5.
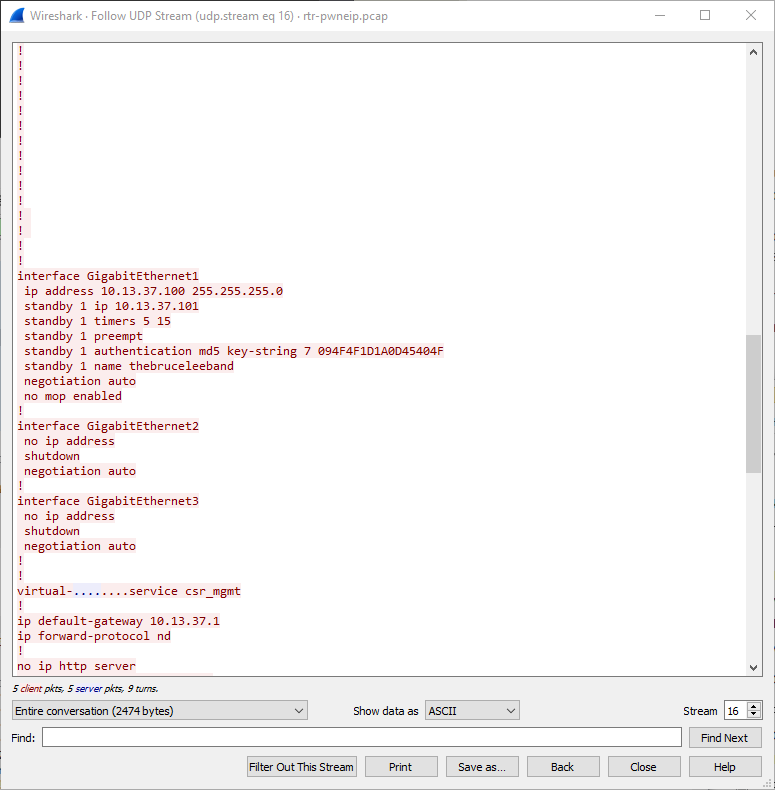
0x03
Objective
What is the HSRP virtual address?
Files
Solution
What's the Virtual IP?
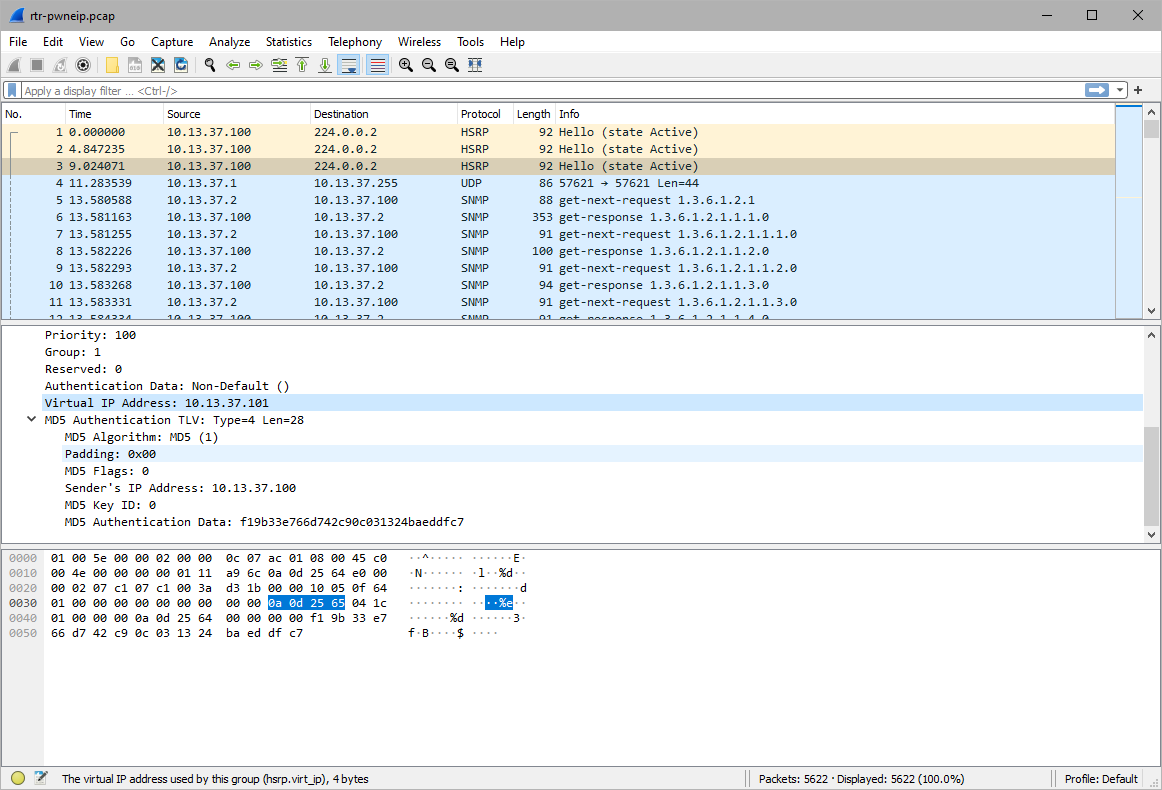
10.13.37.101
0x04
Objective
What is the enable password?
Files
Solution
Both enable secret and enable password are sent in cleartext UDP stream.
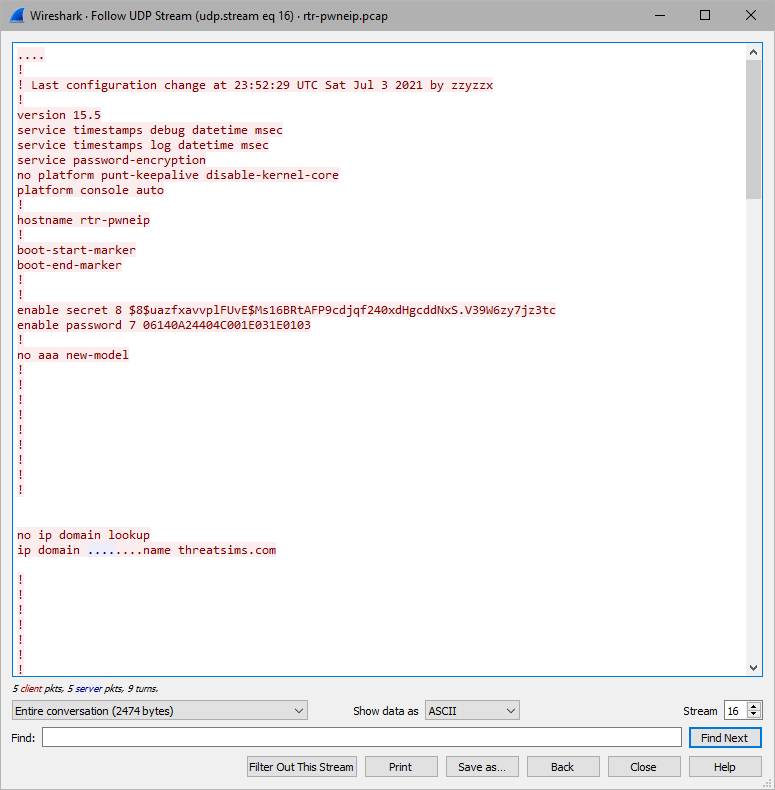
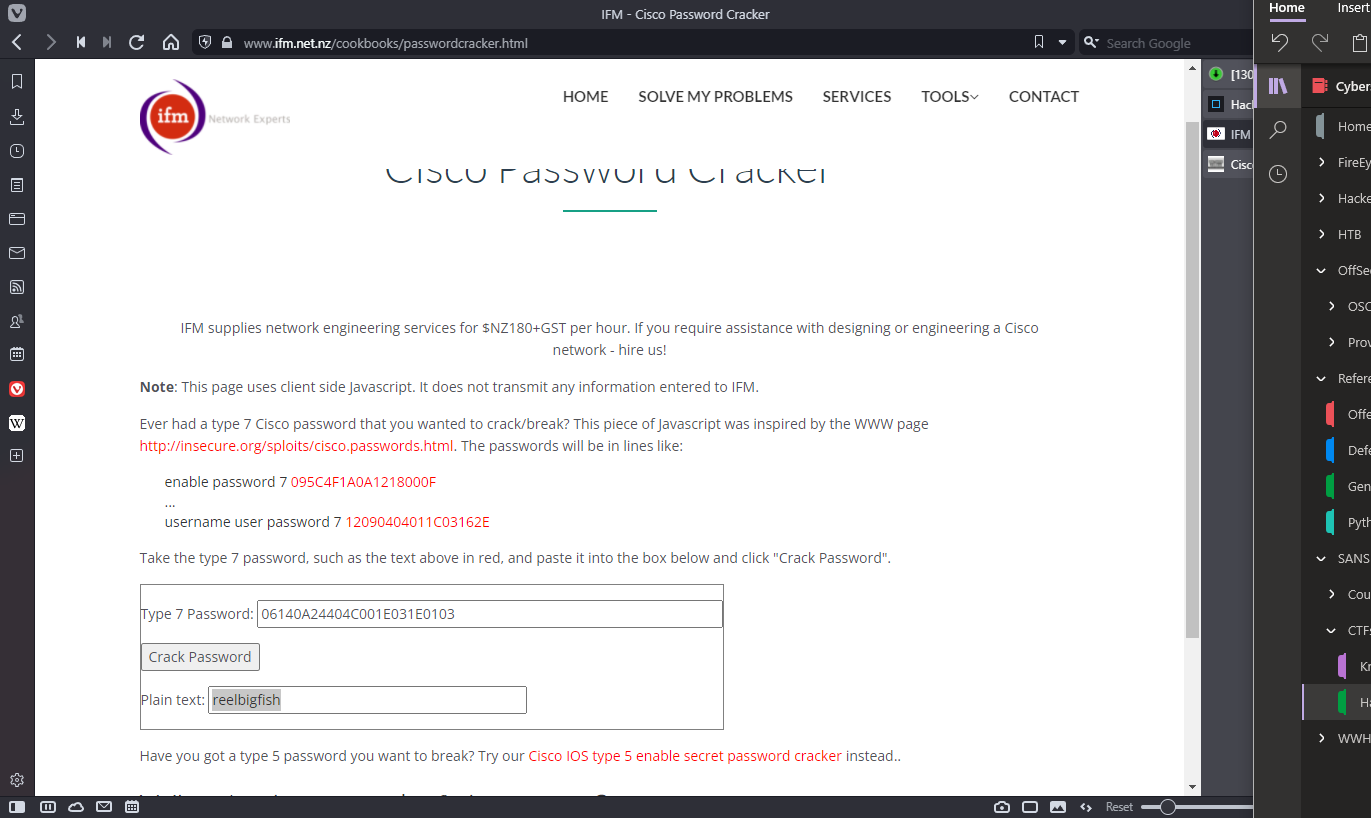
Ok, just need to do the same type 7 crack on:
06140A24404C001E031E0103
The plain text is reelbigfish :
0x05
Objective
What is the plaintext password for zzyzzx?
Files
Solution
While scrolling through the pcap, I saw that there was telnet data coming across as single bytes, and the letter z was repeated a few times.
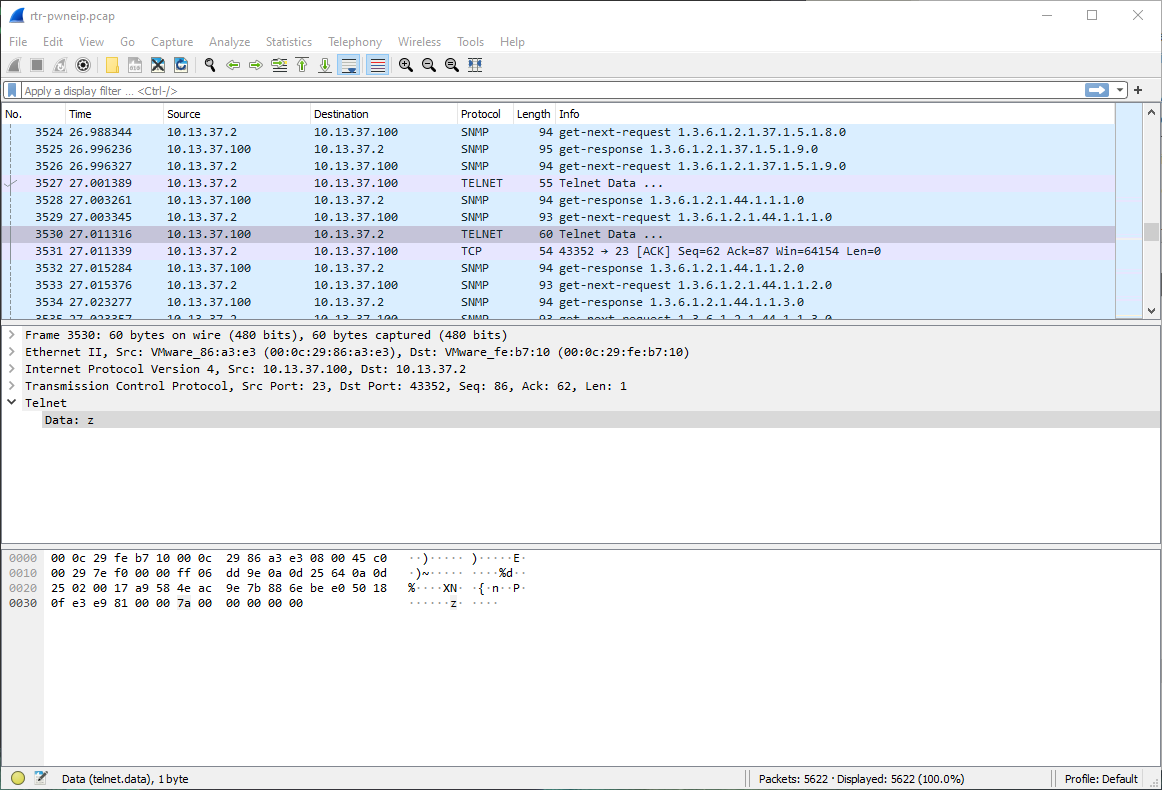
As I scanned through the questions, I saw that one was "Whats the password for zzyzzx?", and figured this would show me.
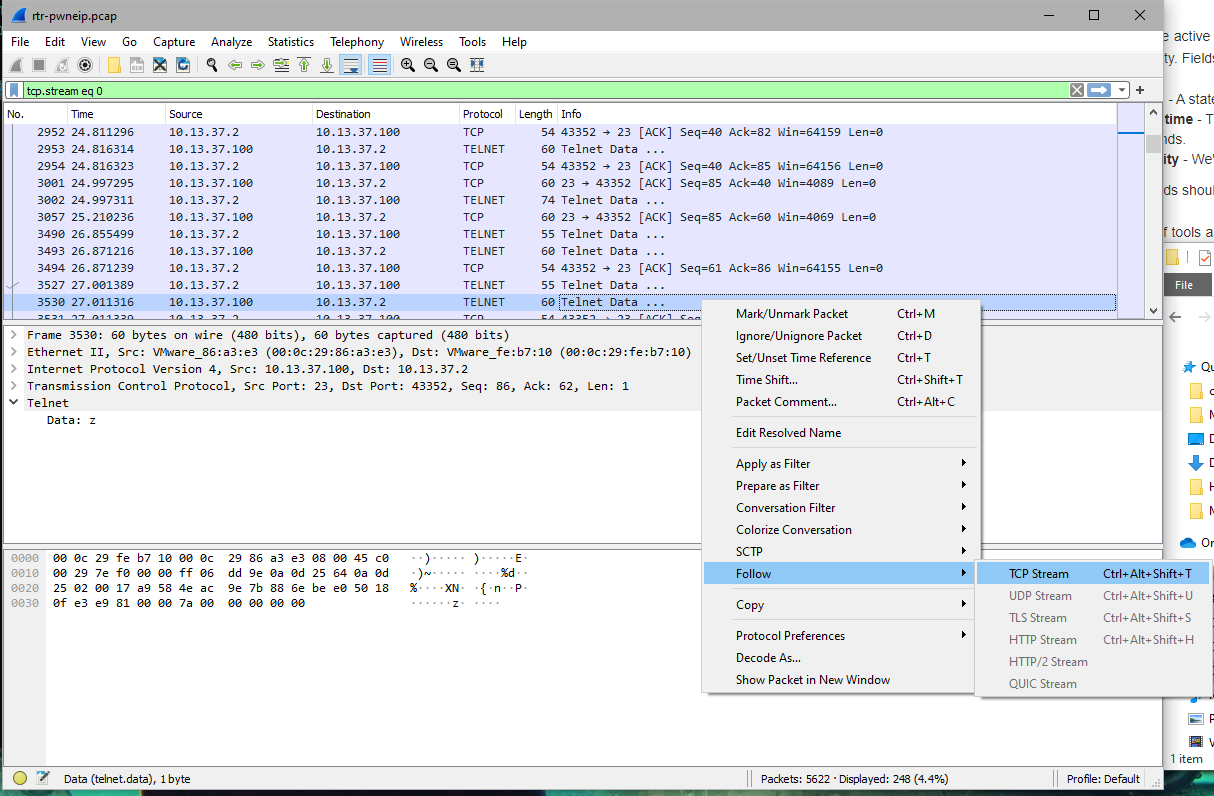
I right-clicked the packet and selected to follow the TCP stream.
The window popped up showing me the full telnet session.
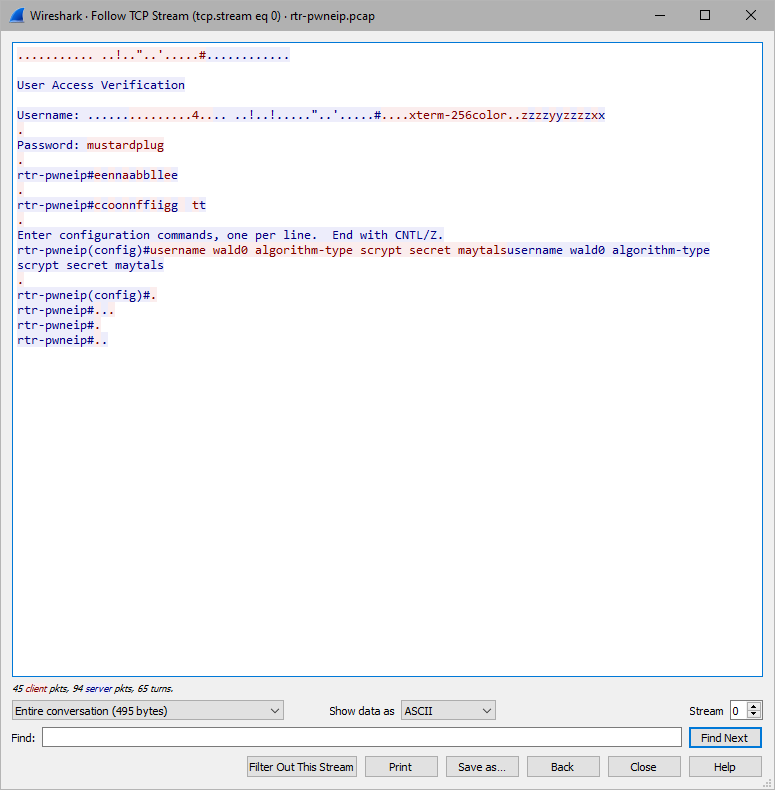
mustardplug
0x06
Objective
What is the plaintext password for rayhan?
Files
Solution
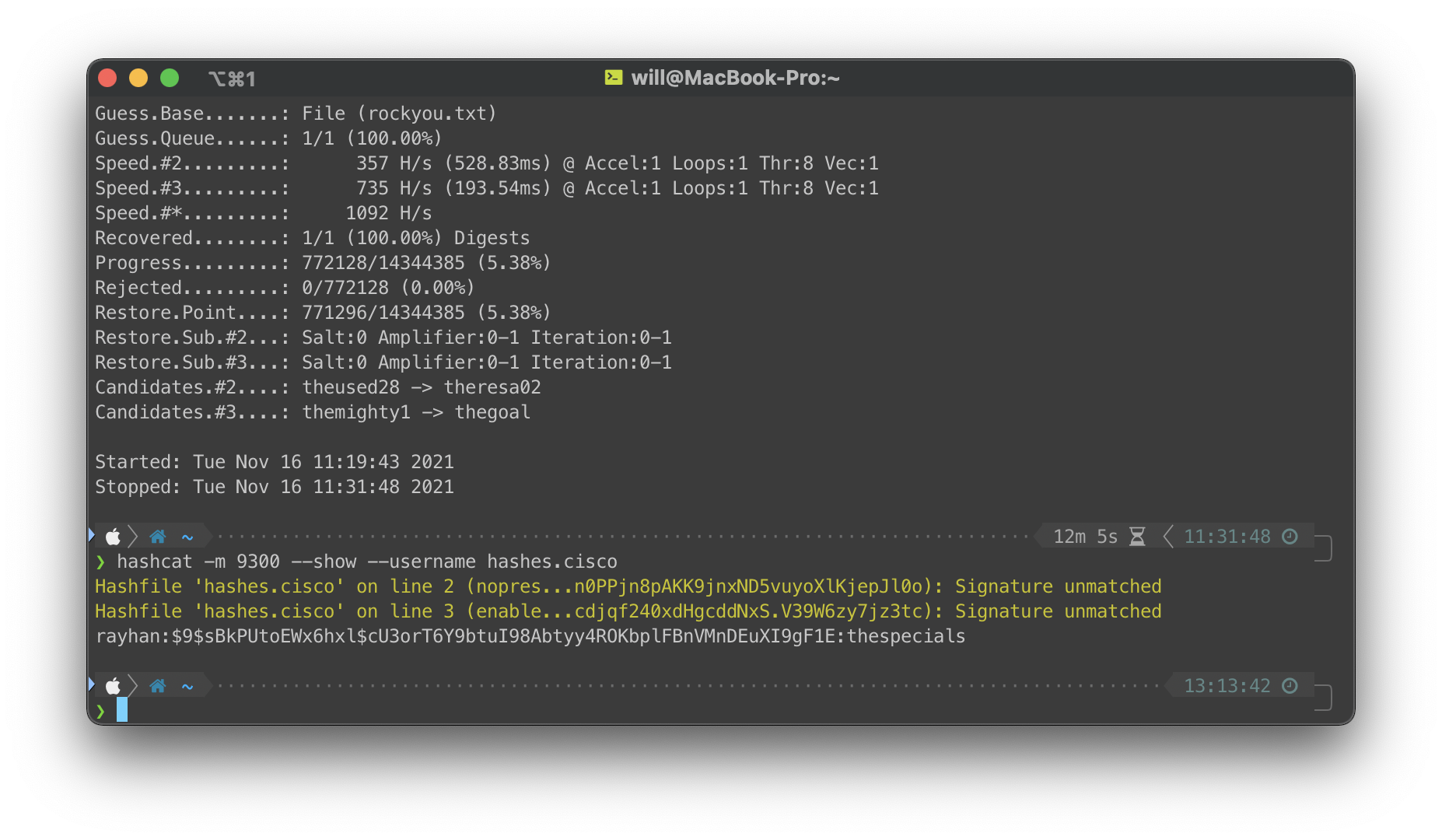
Grabbed the hashed password from the config and ran hashcat against it.
hashcat -m 9300 --username -a 0 hash.cisco /usr/share/wordlists/rockyou.txt
Cracked
0x07
Objective
What is the plaintext password for nopresearcher?
Files
Solution
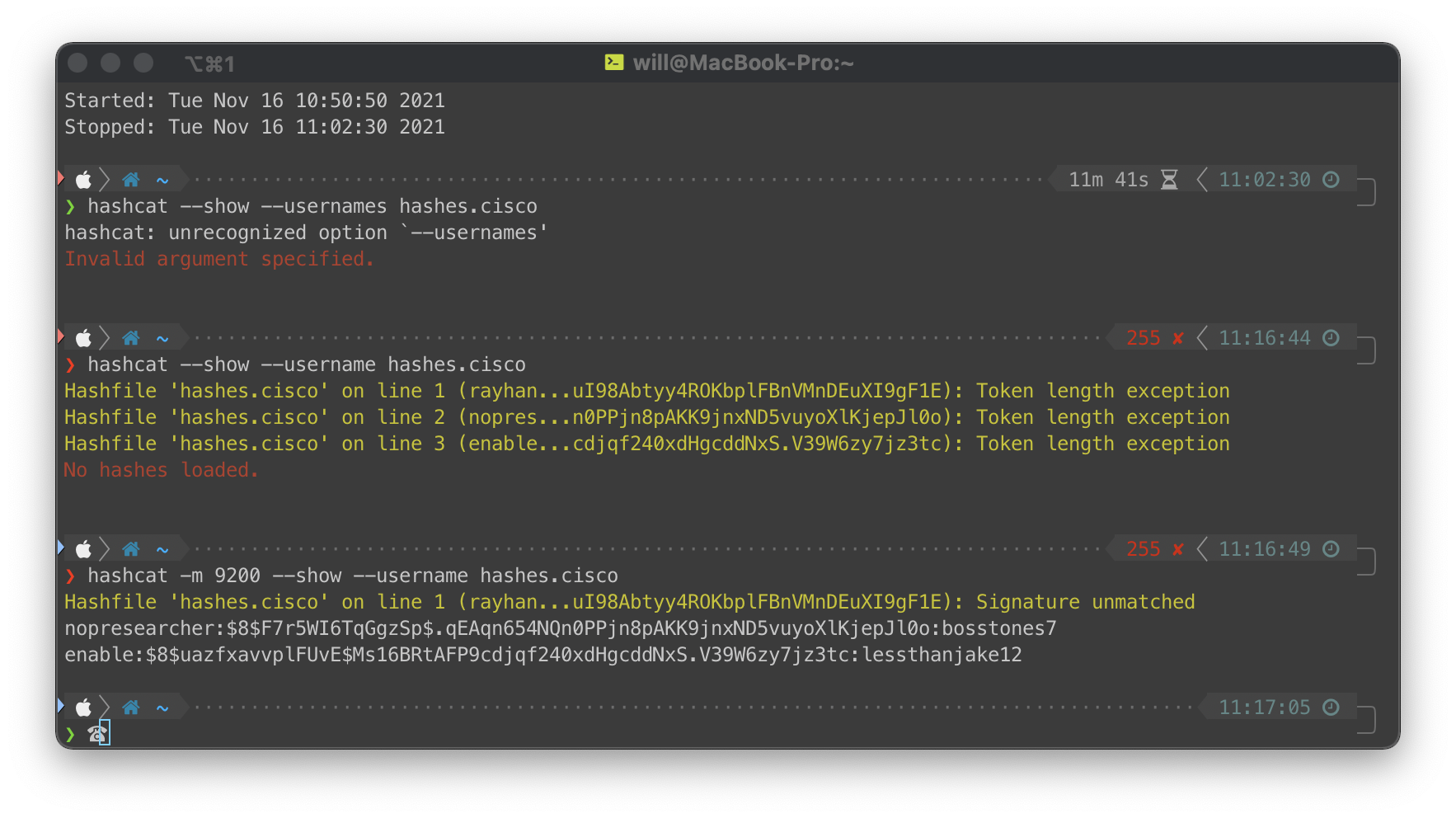
Loaded the password hash from the config file. Ran john against it since hashcat was being weird about it.
john --format=pbkdf2-hmac-sha256 --wordlist=/usr/share/wordlists/rockyou.txt hash.cisco
Had to run hashcat on my MBP, not on my server VM, this cracked pretty quickly.
0x08
Objective
What is the plaintext password for wald0?
Files
Solution
This user was created in the zzyzzx user telnet session, showing their password etc.
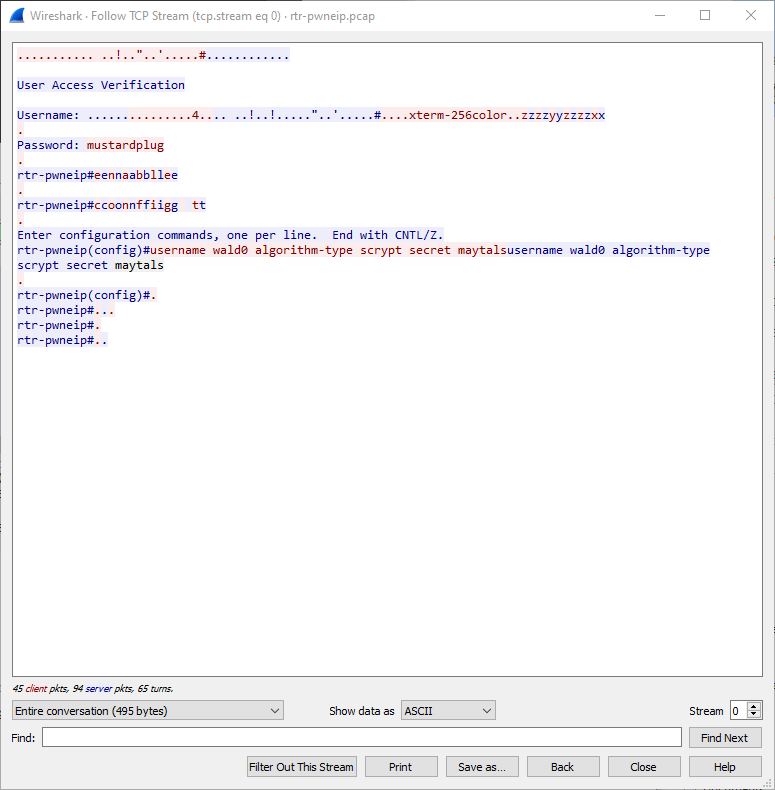
maytals
0x09
Objective
What is the snmp community string with RO capability?
Files
Solution
What is the snmp community string with RO capability?
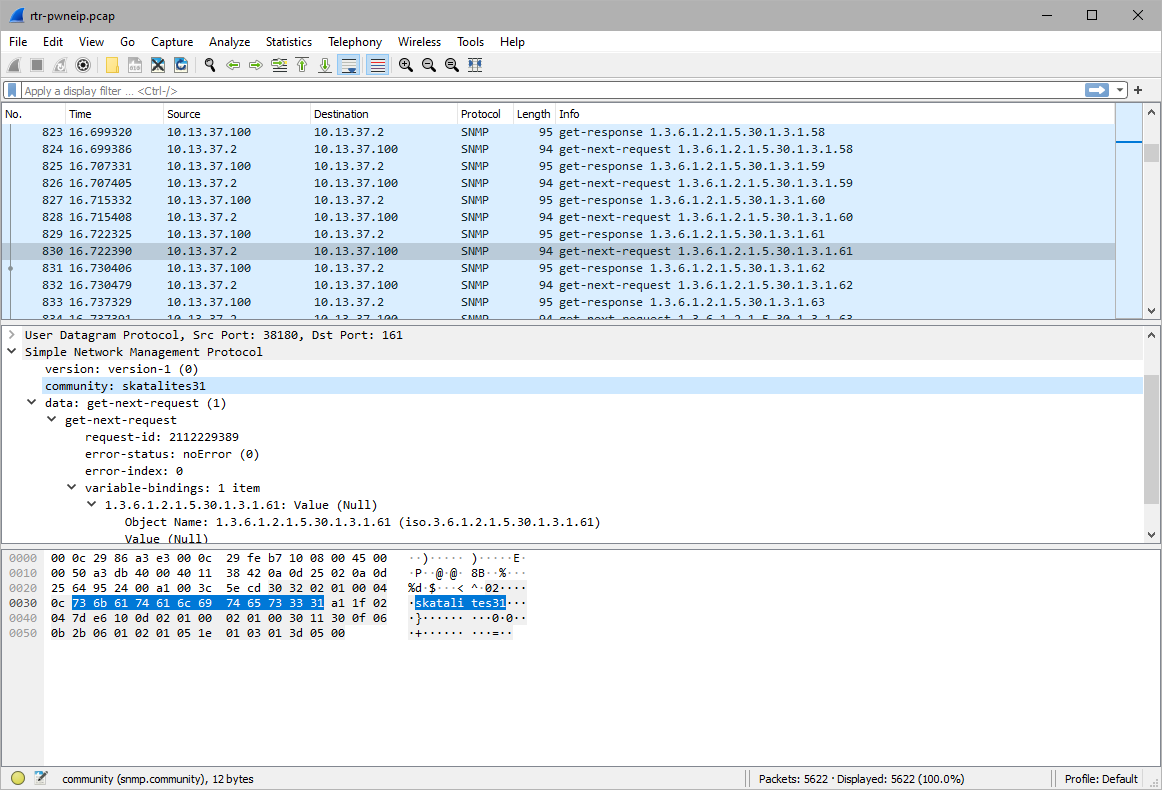
skatalites31
0x0A
Objective
An attacker brute forced the snmp community string to find the private string with RW capability, what is that snmp community string?
Files
Solution
Ok, I found the area where the attacker was brute-forcing the snmp community string with RW capability.
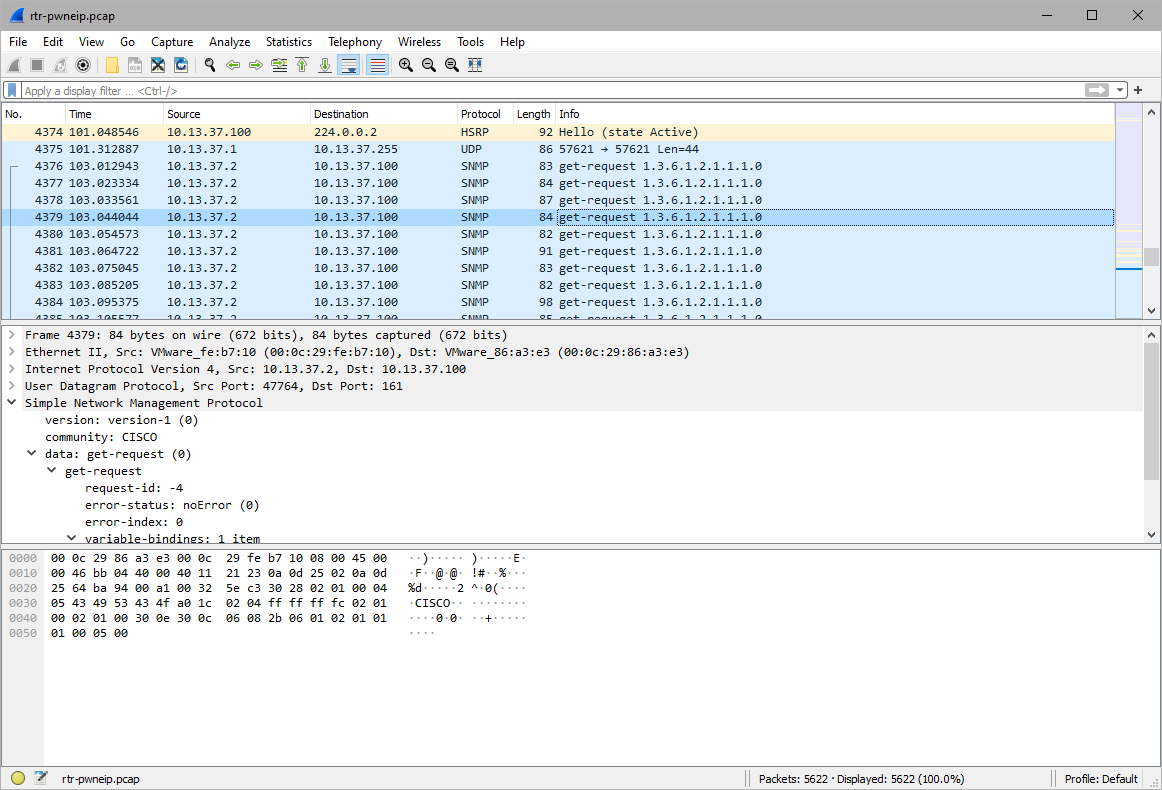
There was a response when using the community string Madness.
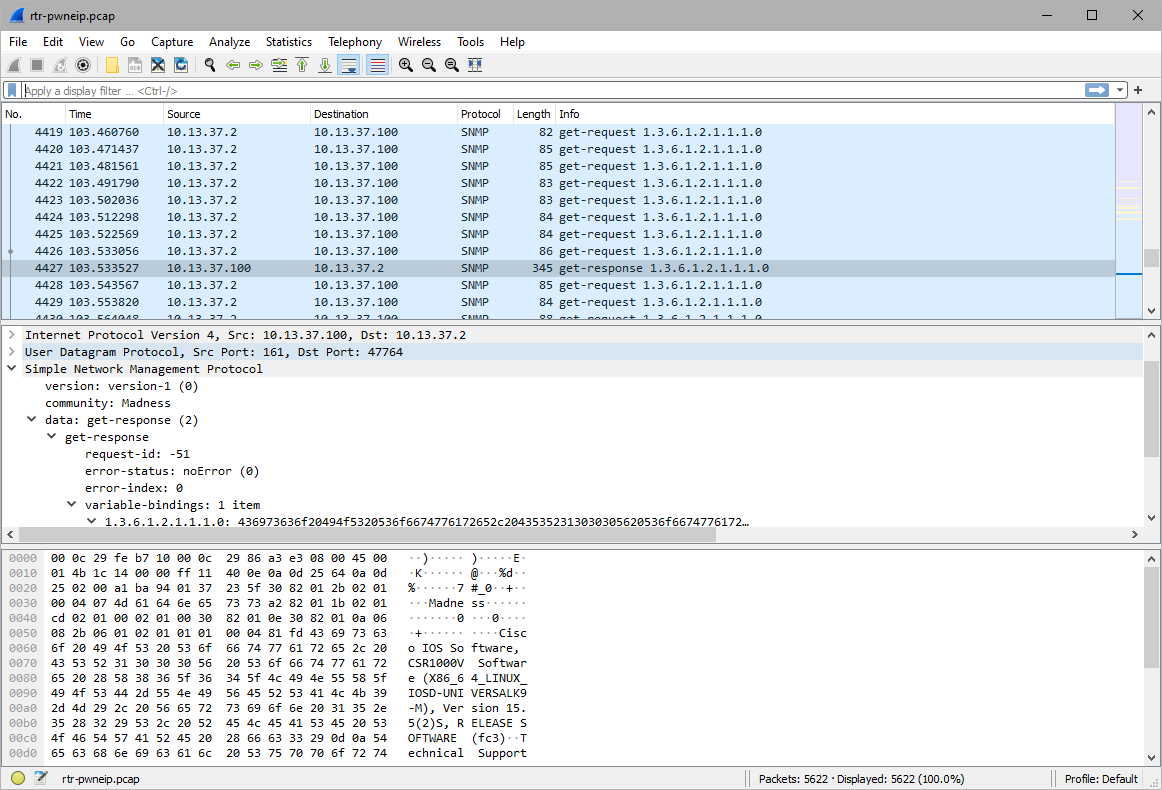
The attacker used the Madness community string to set something with object name 1.3.6.1.2.1.1.5.0 to GOTREKT.
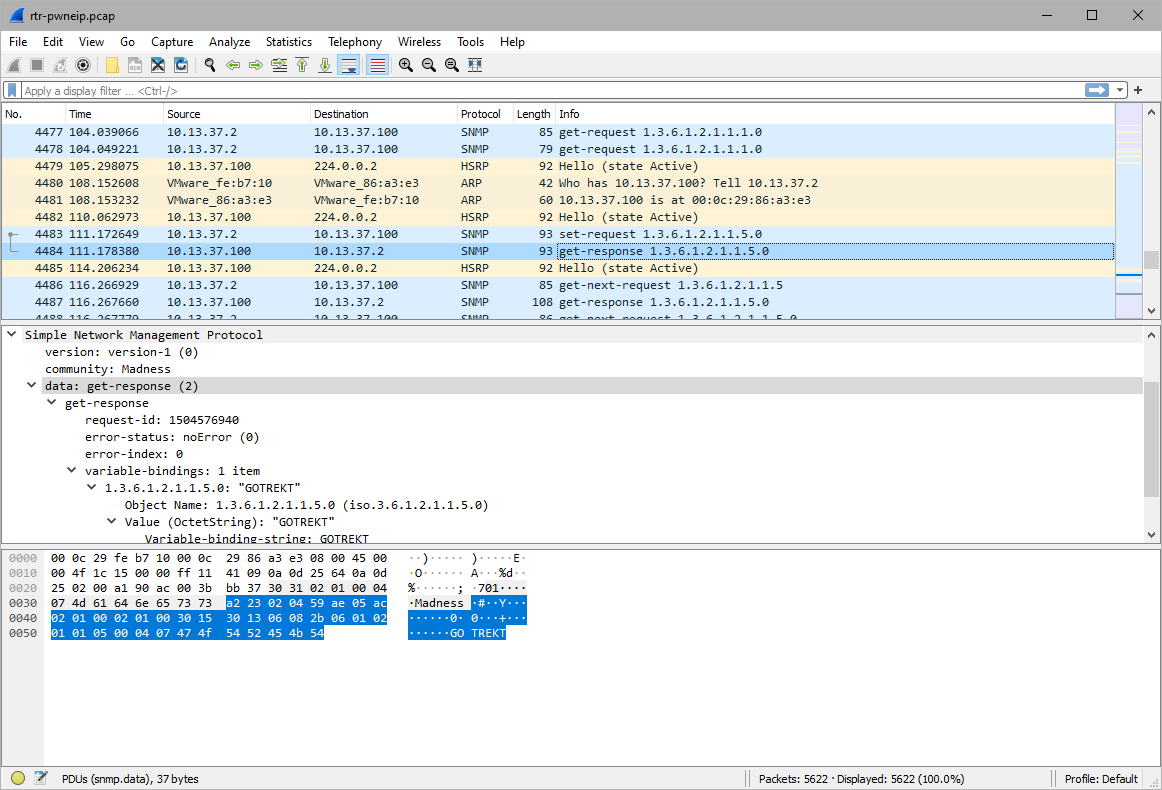
0x0B
Objective
After finding the community string to find the private string with RW capability, the attacker then changed the hostname of the router, what is the new hostname?
Files
Solution
Is this it?
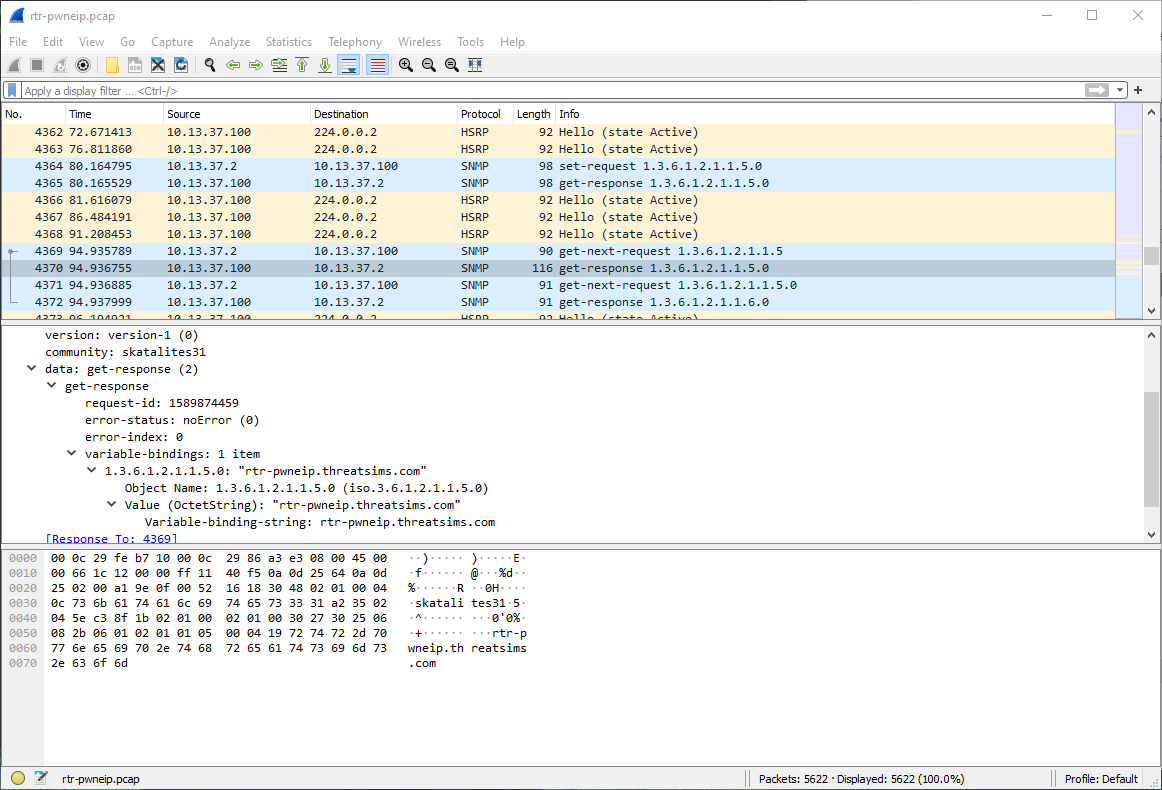
rtr-pwnip.threatsims.com. No I don't think so, but it does look to be like the router hostname default.
After getting the proper SNMP community string for RW, the attacker changed it to GOTREKT.
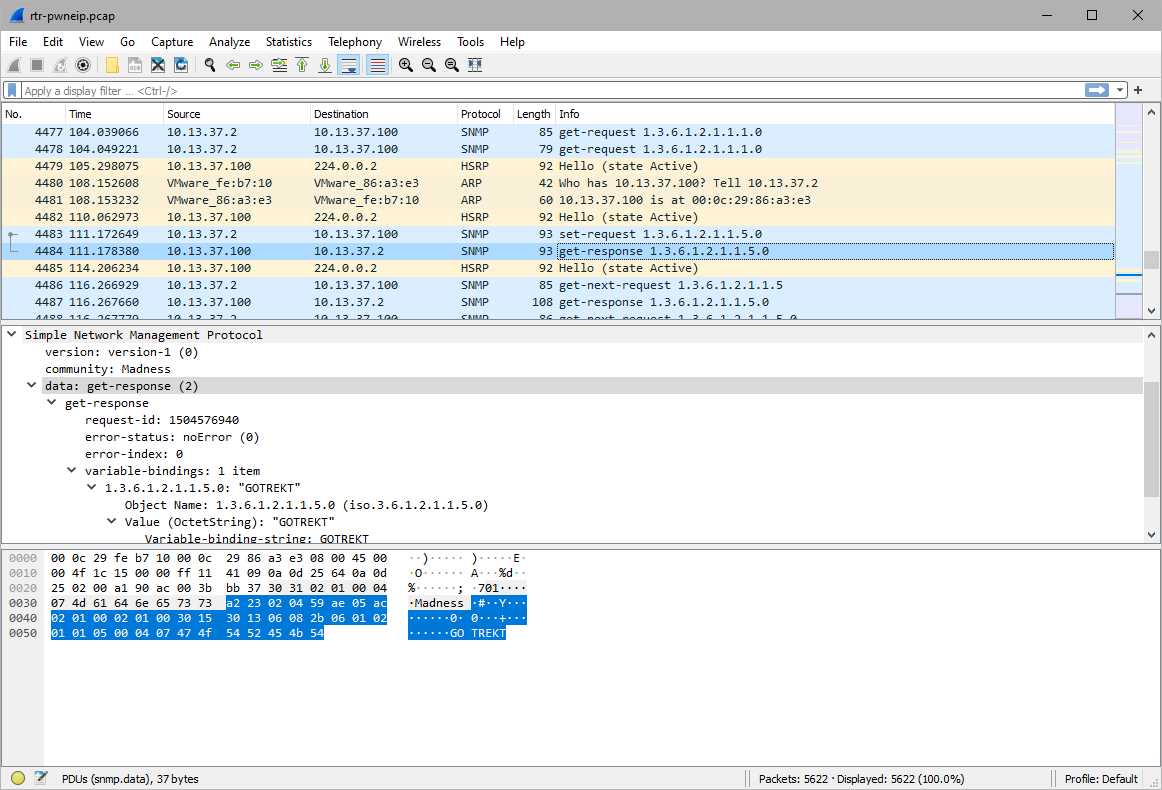
Confirmed when the attacker does a read snmp request and the full router name is in response.
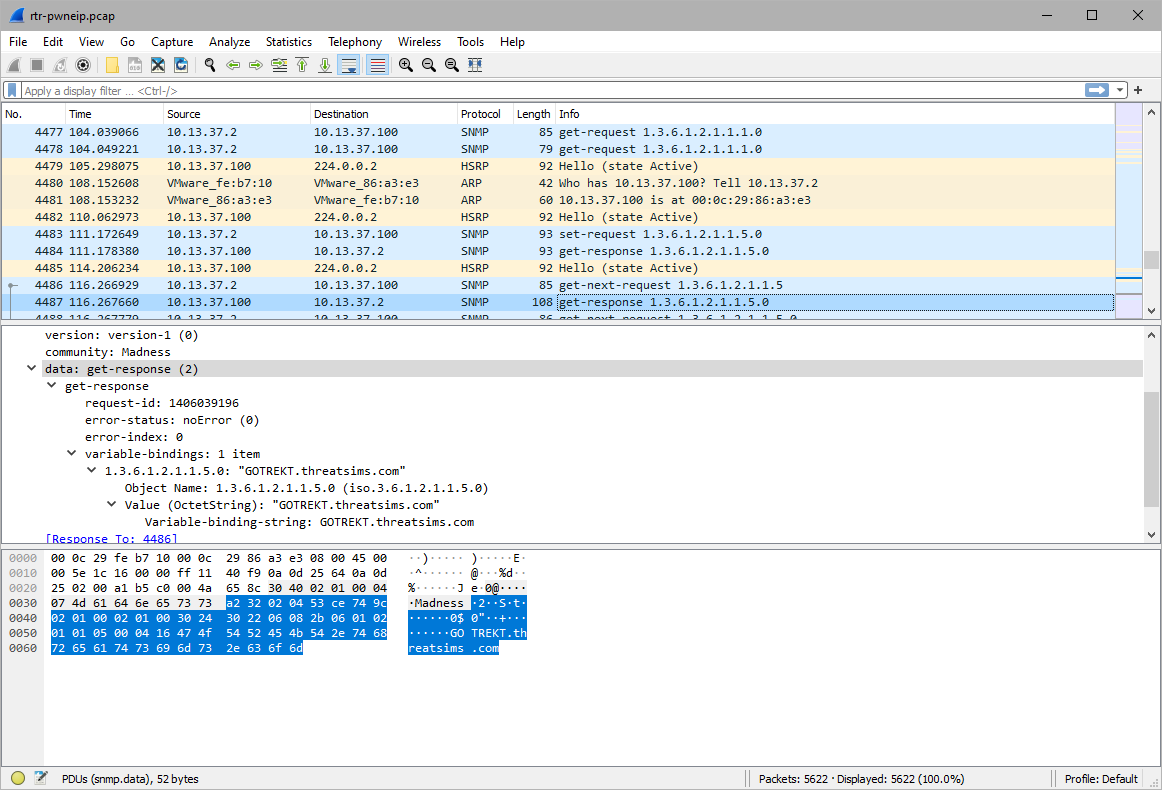
GOTREKT
0x0C
Objective
What is the chassisSerialNumberString of the router with the new hostname?
Files
Solution
I found the MIB for the Serial Number on Cisco's forums via a Google search.
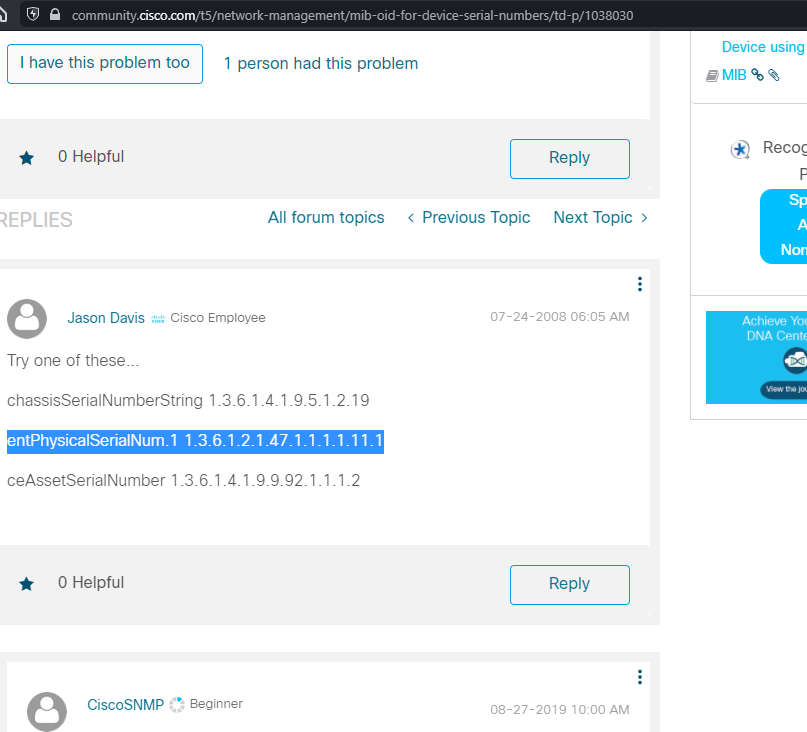
When filtering for this snmp.name in Wireshark I was able to retrieve the Serial Number:
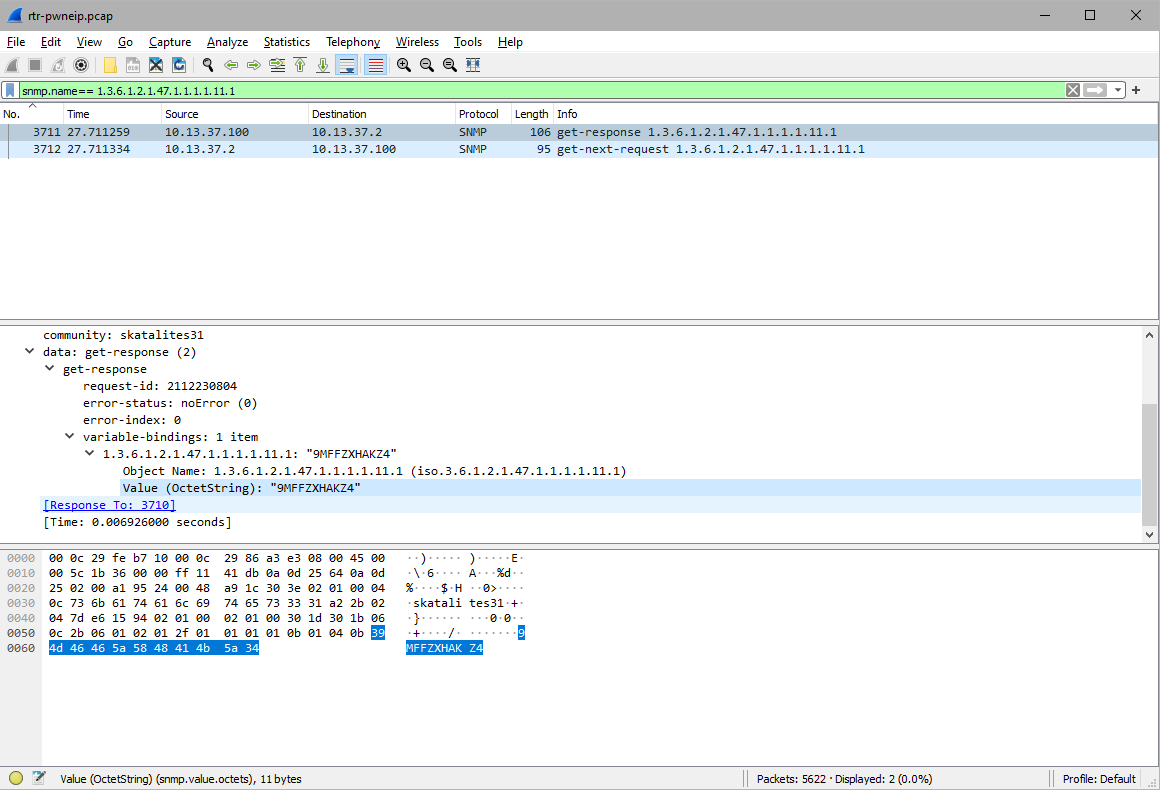
1.3.6.1.2.1.47.1.1.1.1.11.1: 9MFFZXHAKZ4
0x0D
Objective
What is the ftp password?
Files
Solution
Ah, ok. So here in the FTP TCP stream I can see the ftp user and password.
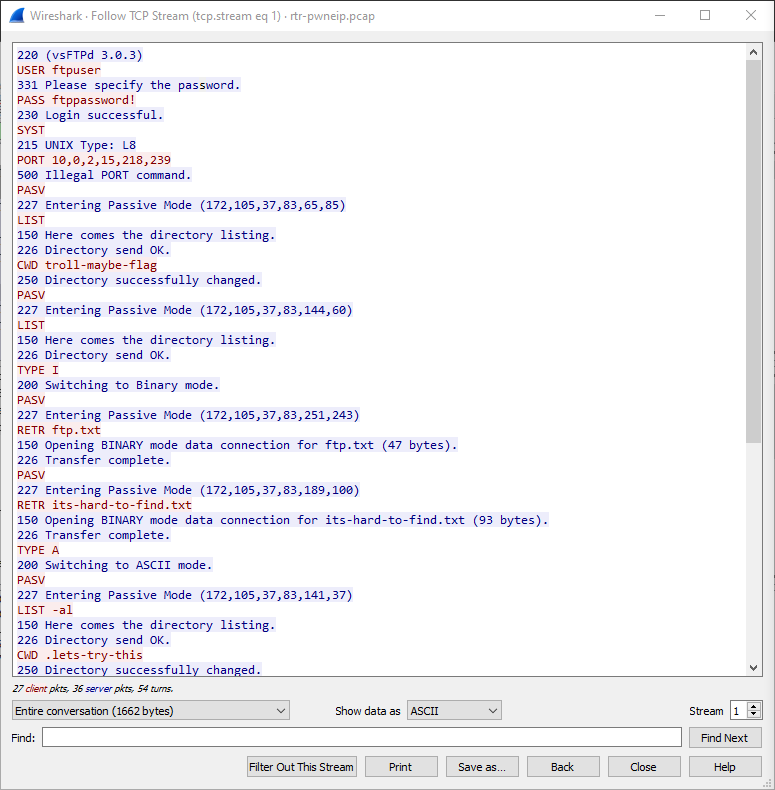
ftppassword!
0x0E
Objective
What is the ftp flag?
Files
Solution
There's a few here it may be.
troll-maybe-flag/its-hard-to-find.txt
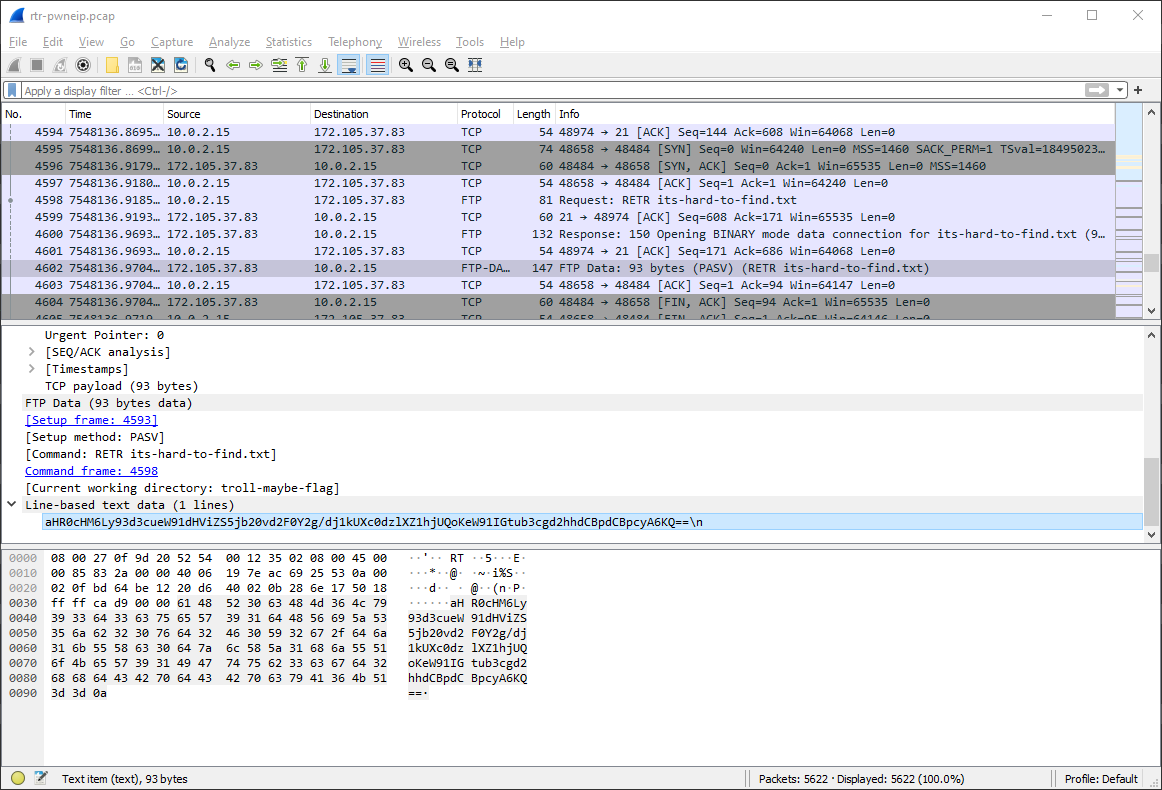
Base64:
aHR0cHM6Ly93d3cueW91dHViZS5jb20vd2F0Y2g/dj1kUXc0dzlXZ1hjUQoKeW91IGtub3cgd2hhdCBpdCBpcyA6KQ==\n
Decoded:
https://www.youtube.com/watch?v=dQw4w9WgXcQ
you know what it is :)
troll-maybe-flag/ftp.txt
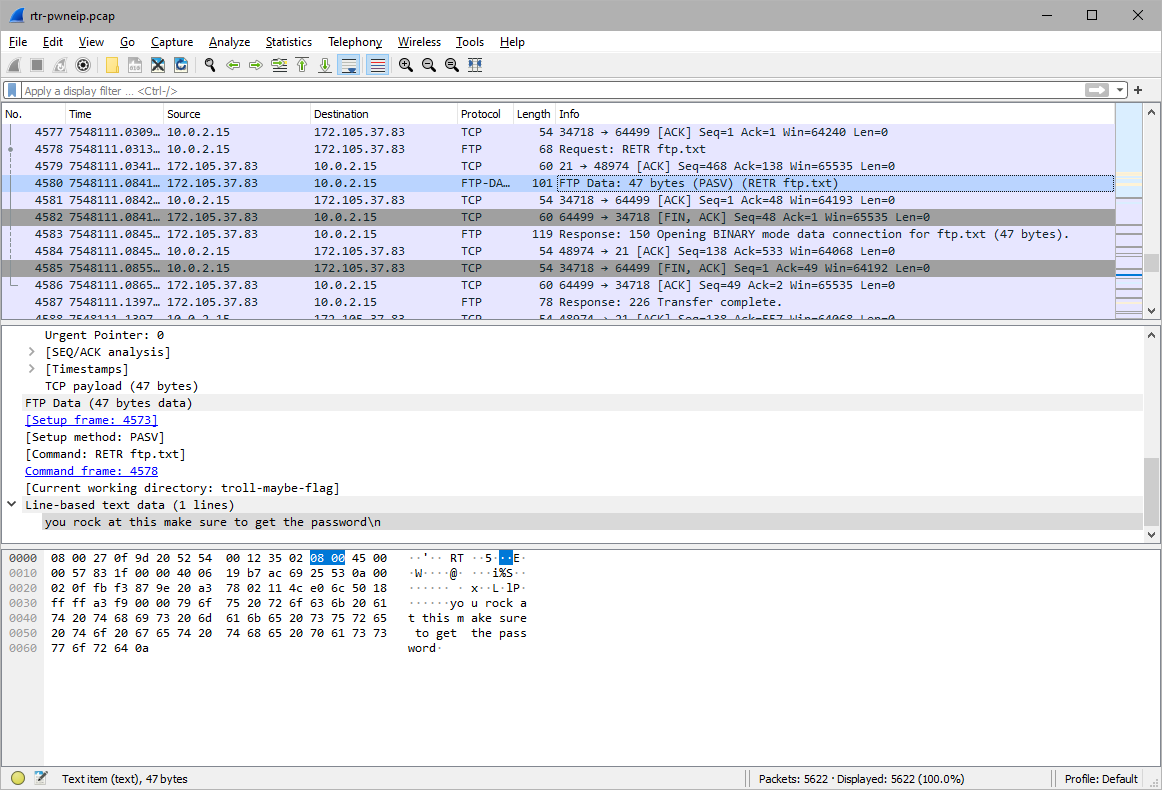
String:
you rock at this make sure to get the password\n
There is a directory ~flag~, with file nested called this-is-what-you-need.txt.
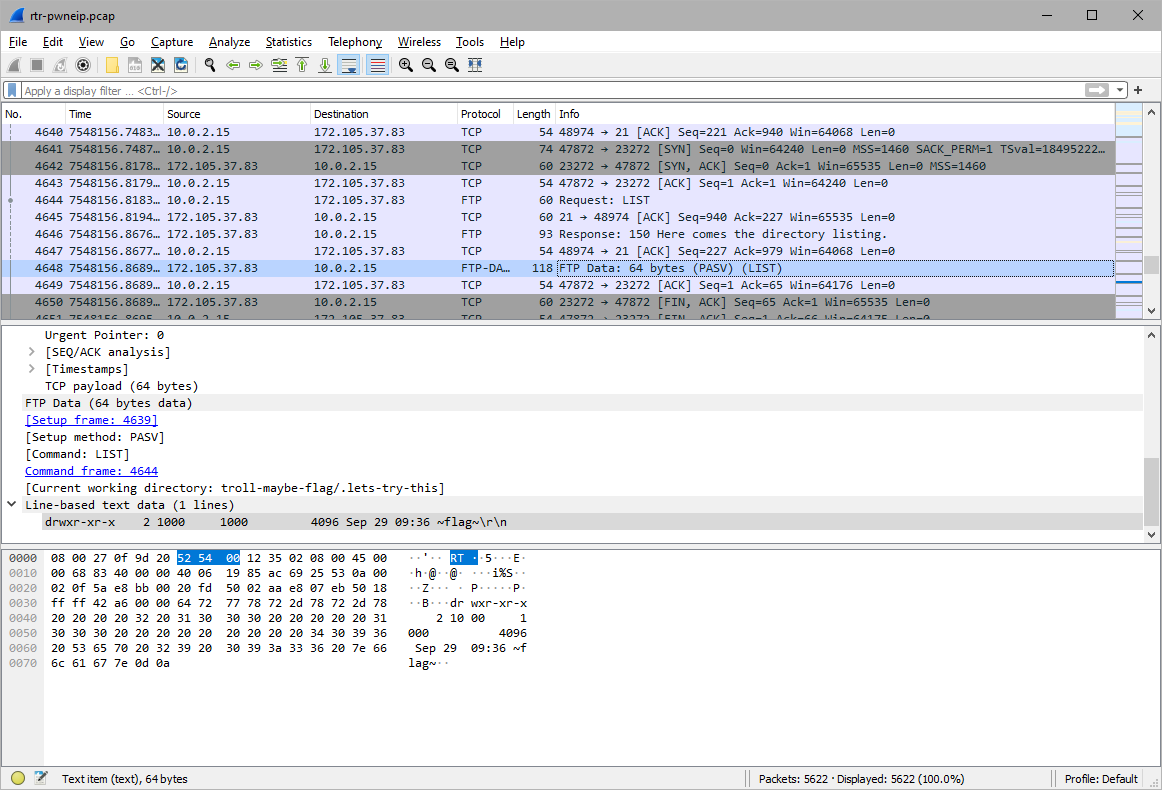
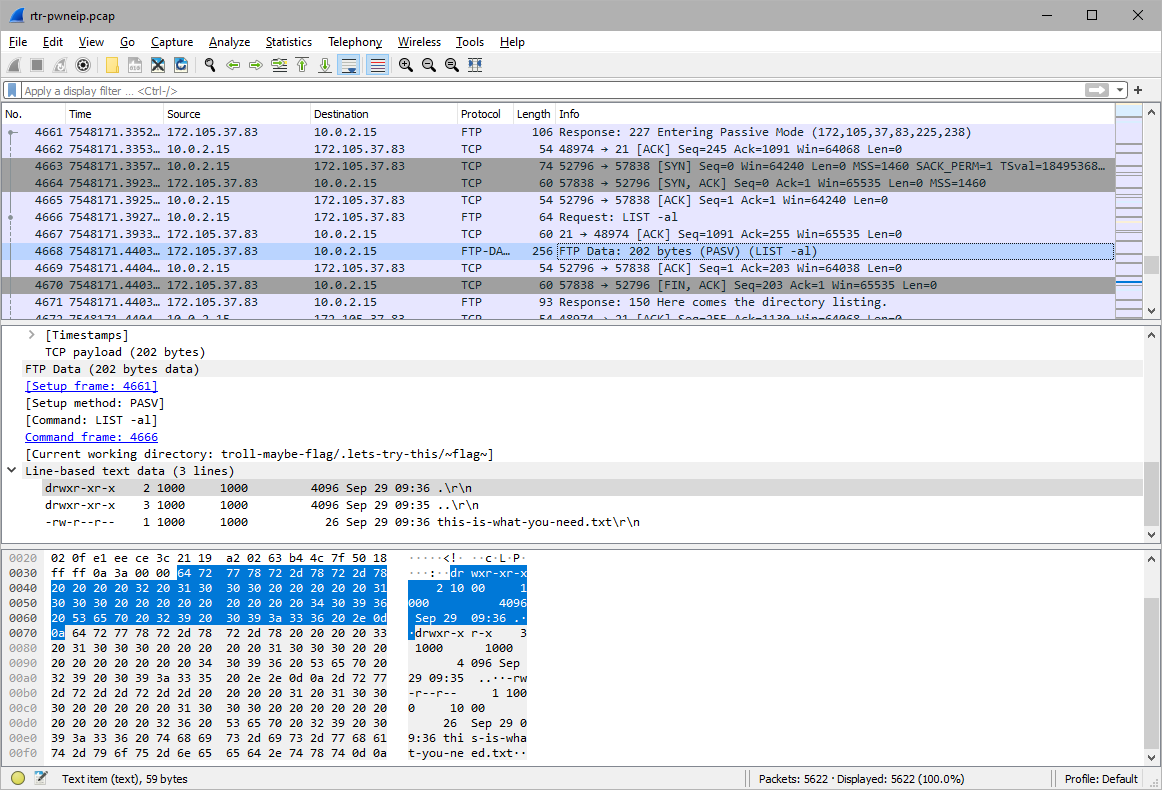
troll-maybe-flag/.lets-try-this/~flag~/this-is-what-you-need.txt
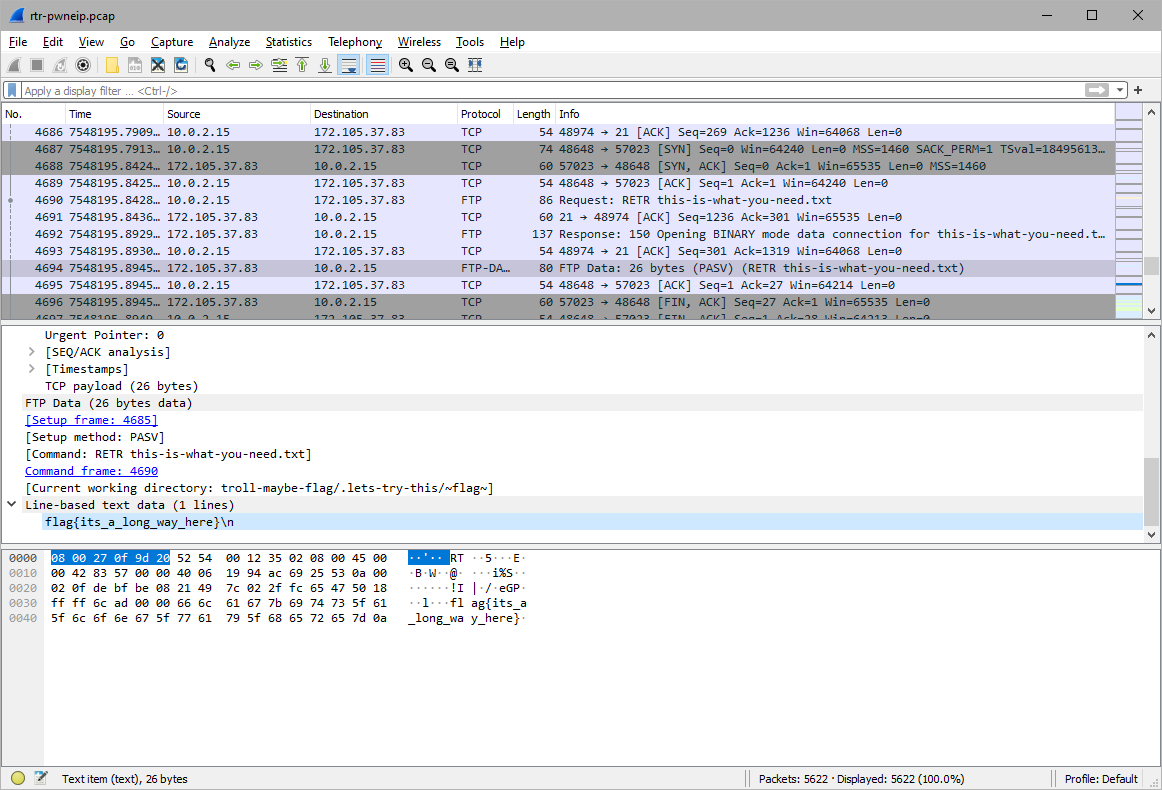
String:
flag{its_a_long_way_here}\n
0x0F
Objective
What is the enable secret?
Files
Solution
Had to run hashcat on my MBP, not on my server VM, this cracked pretty quickly.
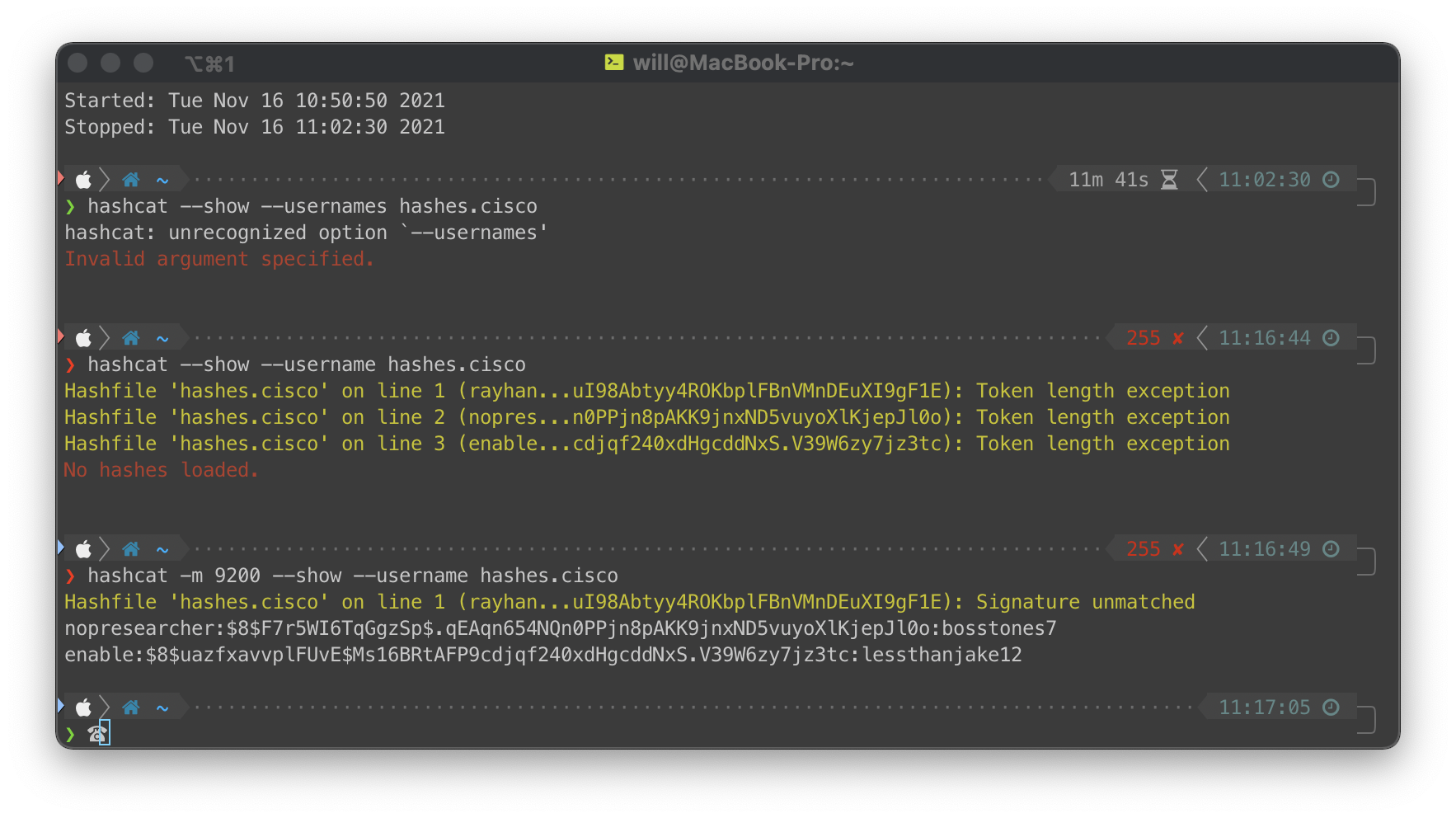
lessthanjake12