USB Ripper
Notes
This is the fourth HTB challenge I have done. This challenge was created by snovvcrash. It has an easy rating and is worth 20 points.
Objective
There is a sysadmin, who has been dumping all the USB events on his Linux host all the year... Recently, some bad guys managed to steal some data from his machine when they broke into the office. Can you help him to put a tail on the intruders? Note: once you find it, "crack" it.
Solution
The first file I looked at was auth.json. It was a file full of these strings.
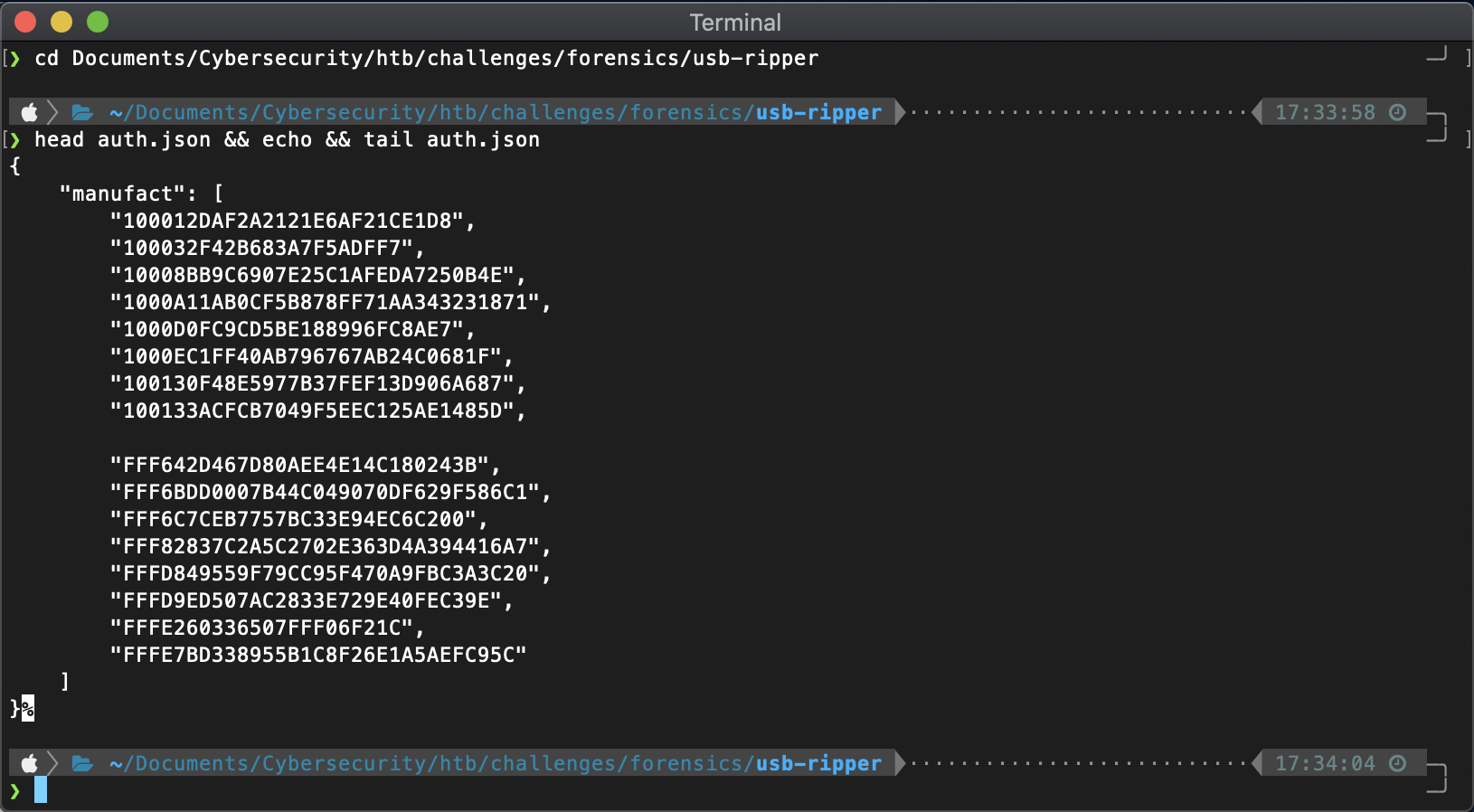
The second file has so many entries it's going to be a mess to discover anything.
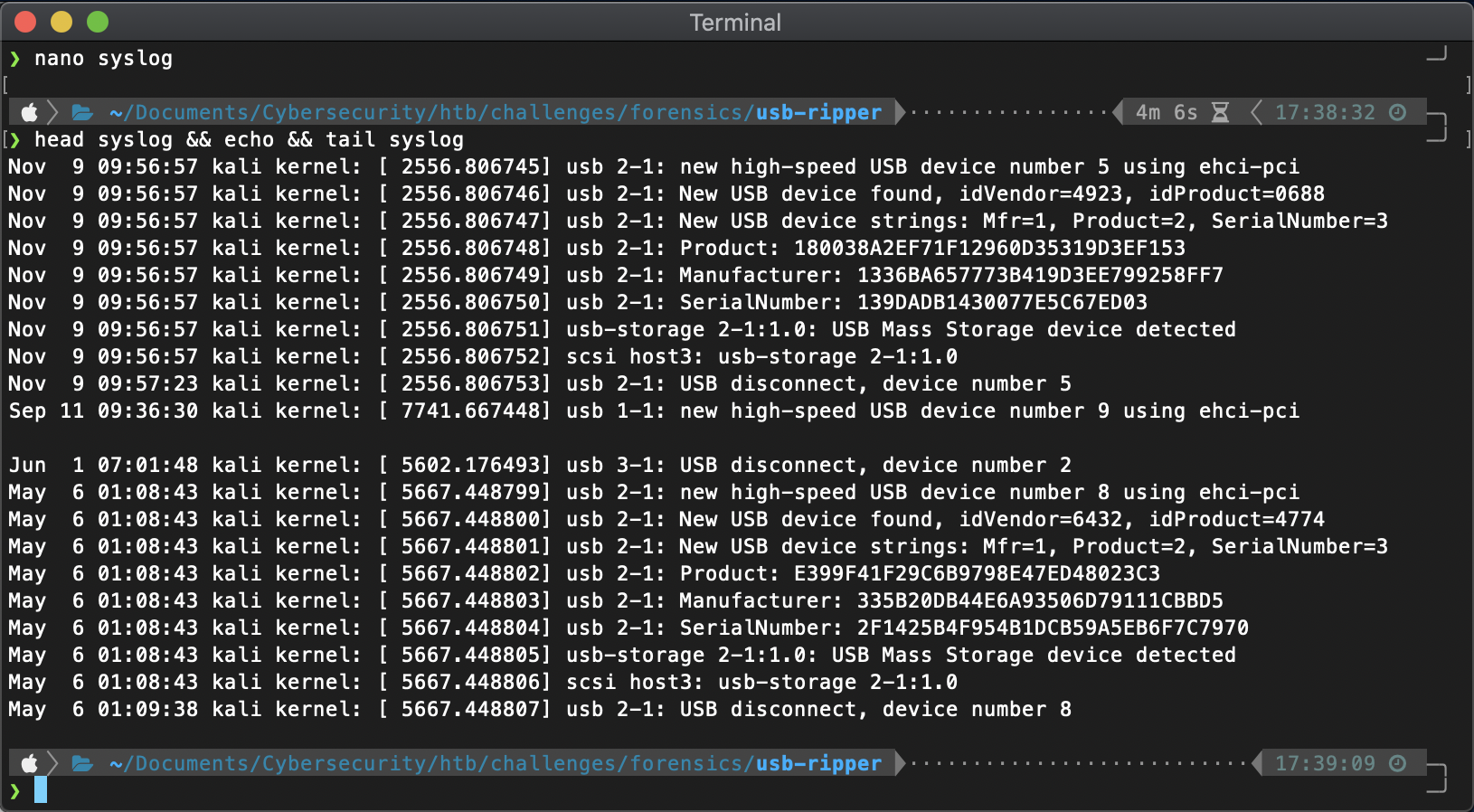
I performed a Google search for the challenge creator, snovvcrash. This resulted in a git repo owned by the same user for the usbrip tool. This tool is supposed to be able to analyze Linux log data and build a USB event history table with important columns. It can also search for "violation events", aka events with USB devices that do not appear in auth.json. I installed the tool.
python3 -m pip install usbrip
Ok, this tool is straight up fucking stupid, and it requires stupid syntax. I found a python script that will do the same shit manually-ish. https://gist.github.com/CER10TY/f68be04eaf0be3576c08d160db76d545
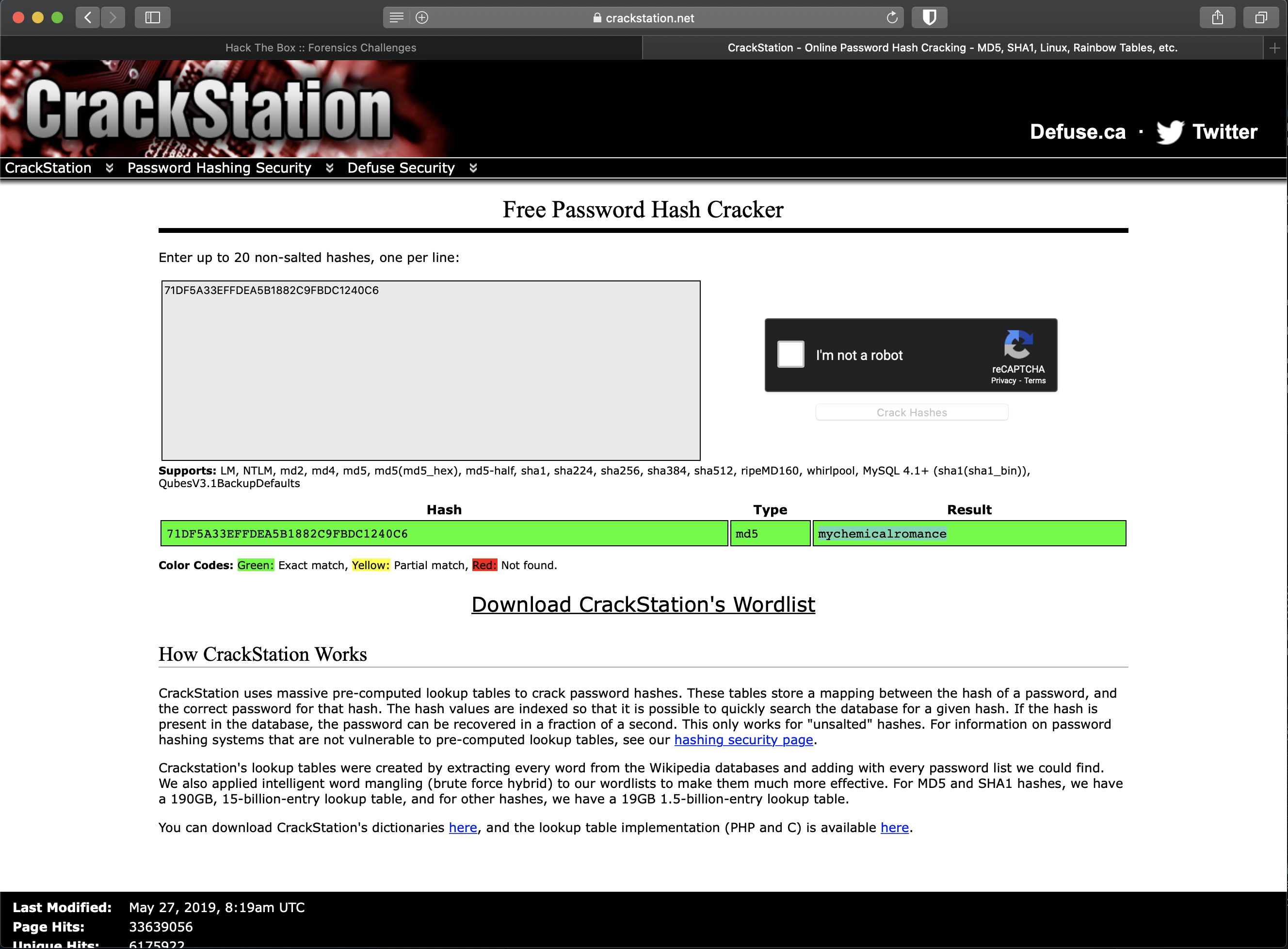
The new python script found 1 odd serial number: 71DF5A33EFFDEA5B1882C9FBDC1240C6
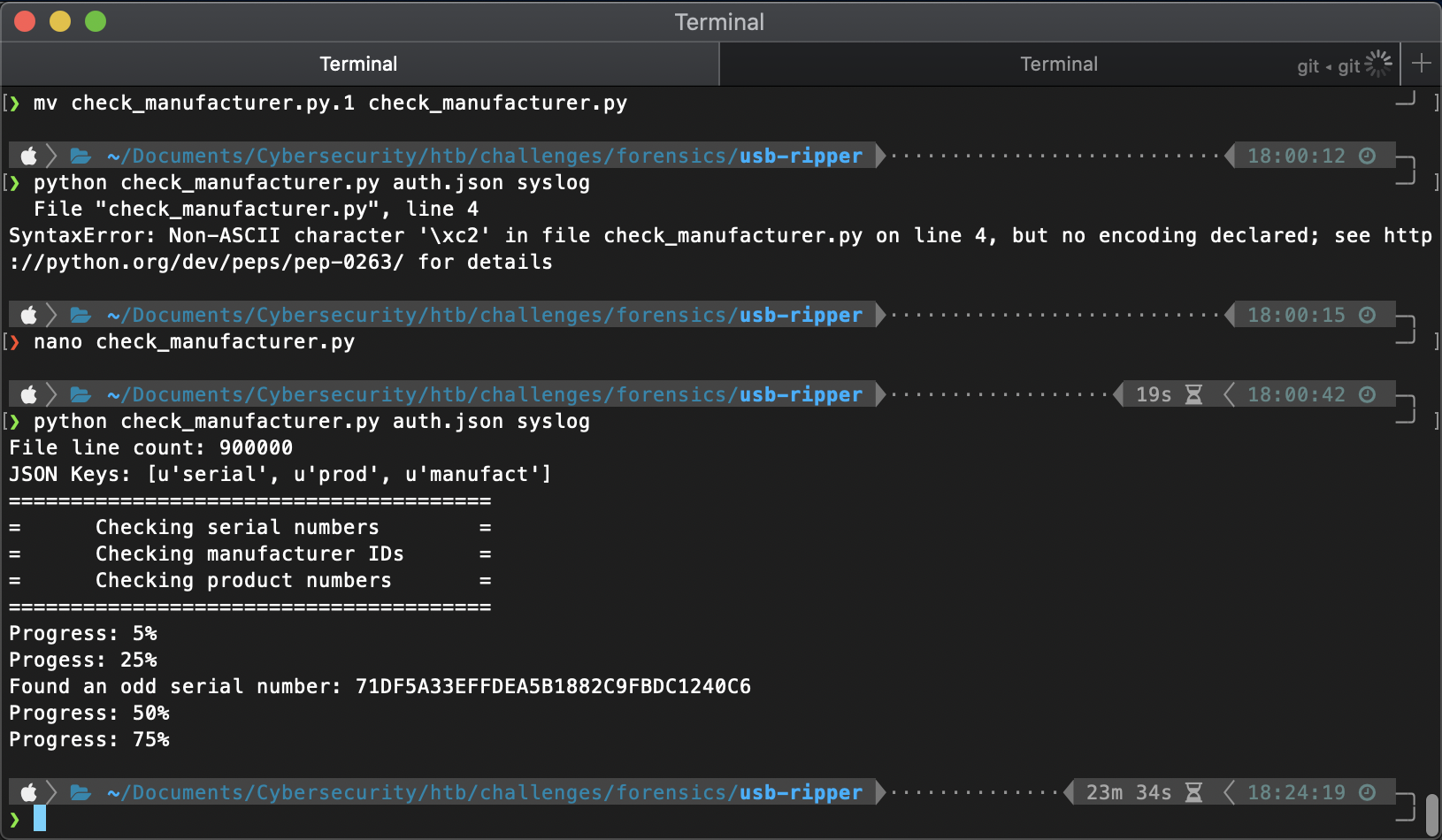
Checking this serial number with hashid shows that it is an md5 hash.
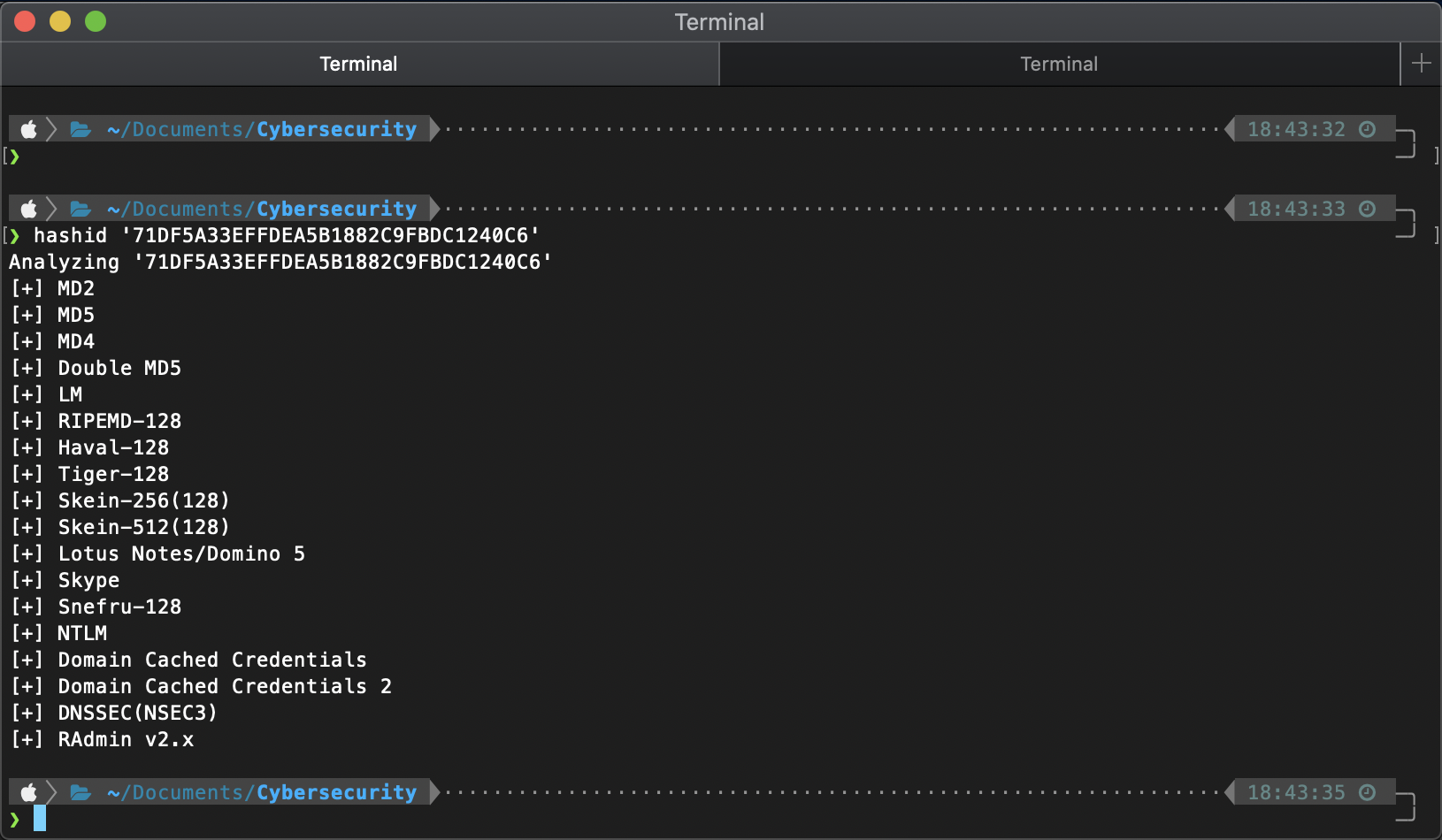
I was having issues getting seclists w/ rockyou downloaded on to my mac, so I cracked the hash on crackstation.
Flag
HTB{mychemicalromance}