Find the Easy Pass
Instructions
Find the password (say PASS) and enter the flag in the form HTB{PASS}.
Solution
Ok, so after unzipping I see that the file is an exe. Running file on it shows me that it is a PE32 executable.
 Ok, looking at the hex dump I don’t see any indication this PE is packed.
Ok, looking at the hex dump I don’t see any indication this PE is packed.
 Nothing stood out to me after running objdump -x against the binary.
Nothing stood out to me after running objdump -x against the binary.
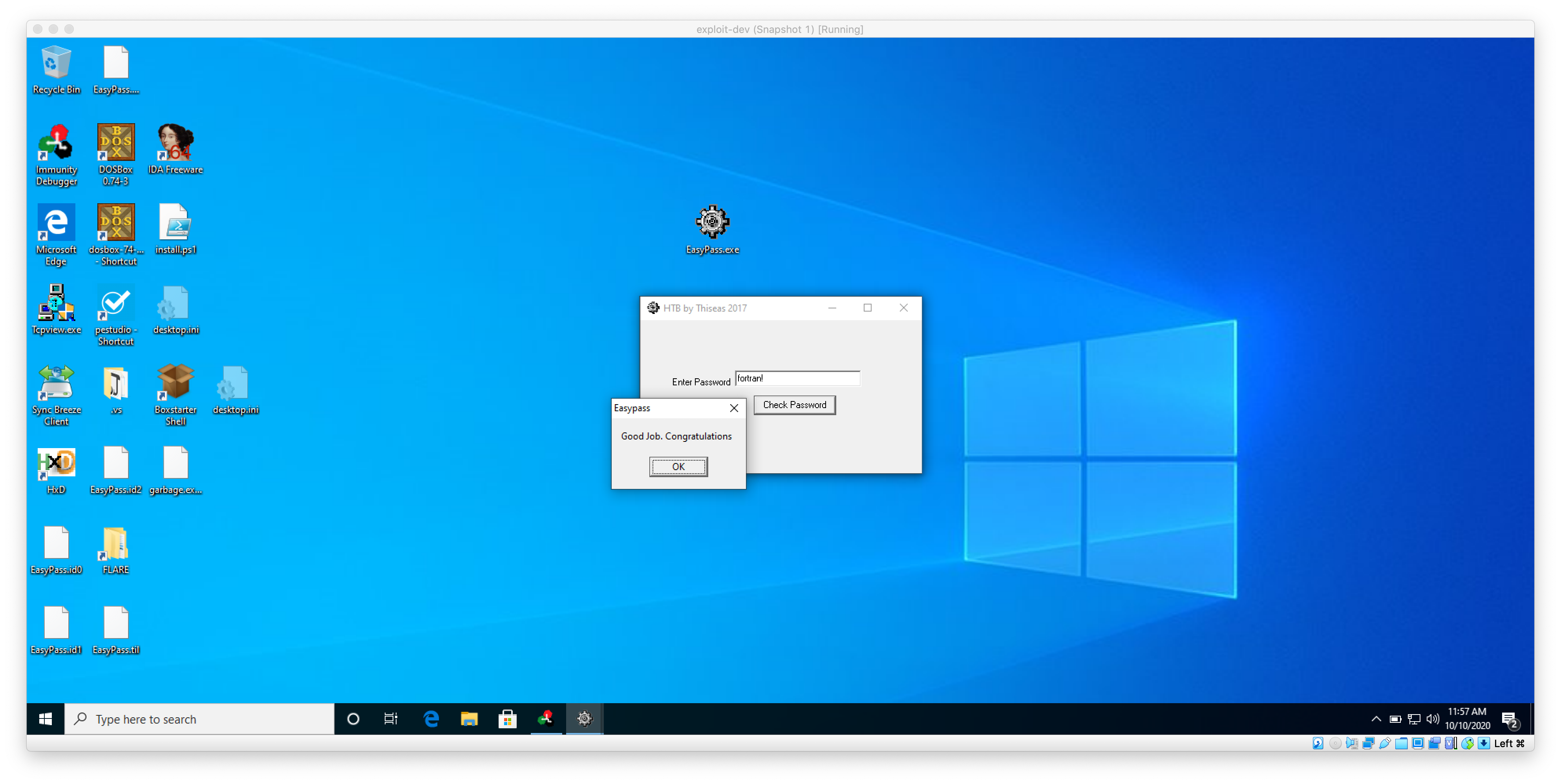
 Launching the program, I saw that it required a password to continue.
Launching the program, I saw that it required a password to continue.
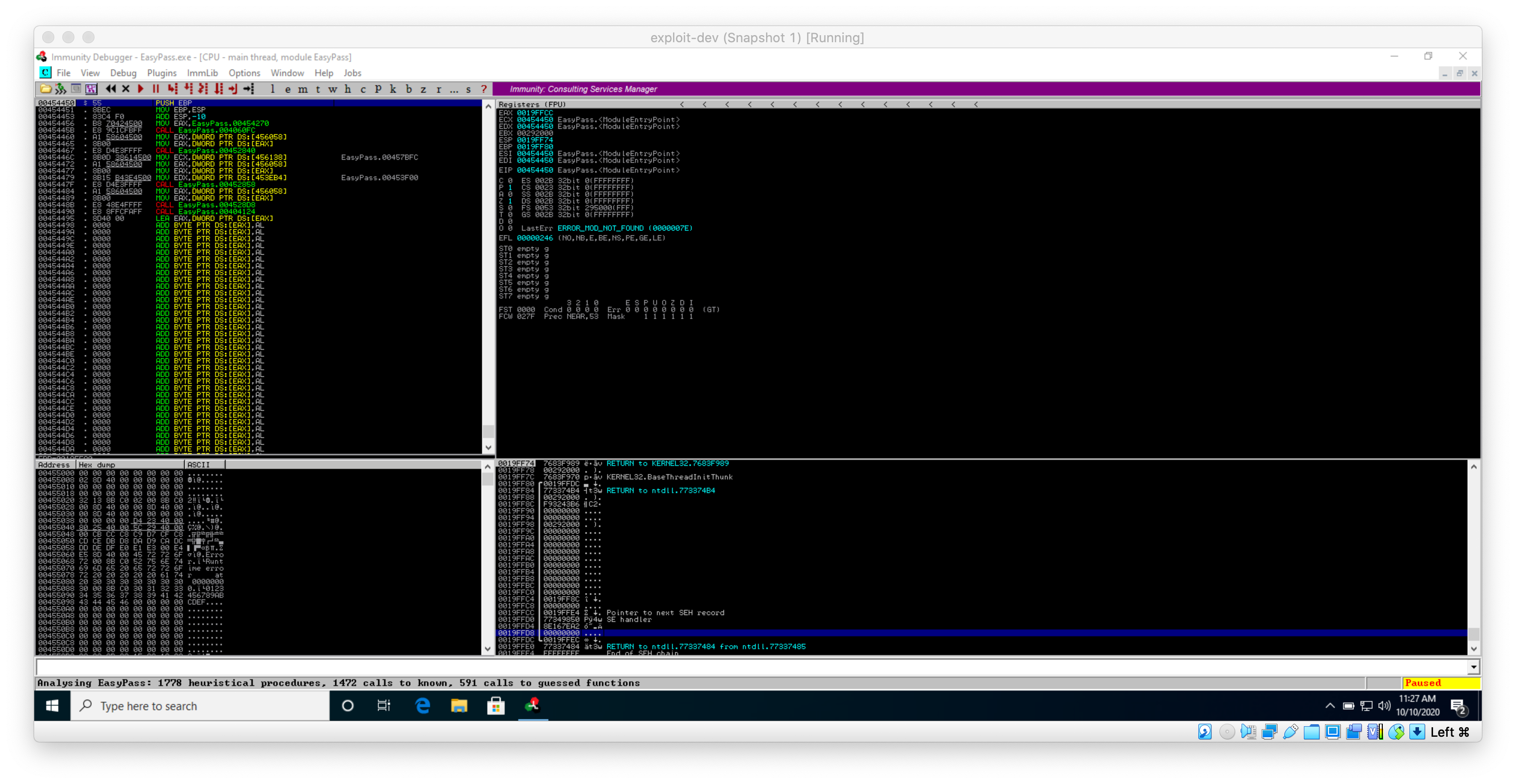
 I loaded the program into Immunity Debugger to see what was going on.
I loaded the program into Immunity Debugger to see what was going on.
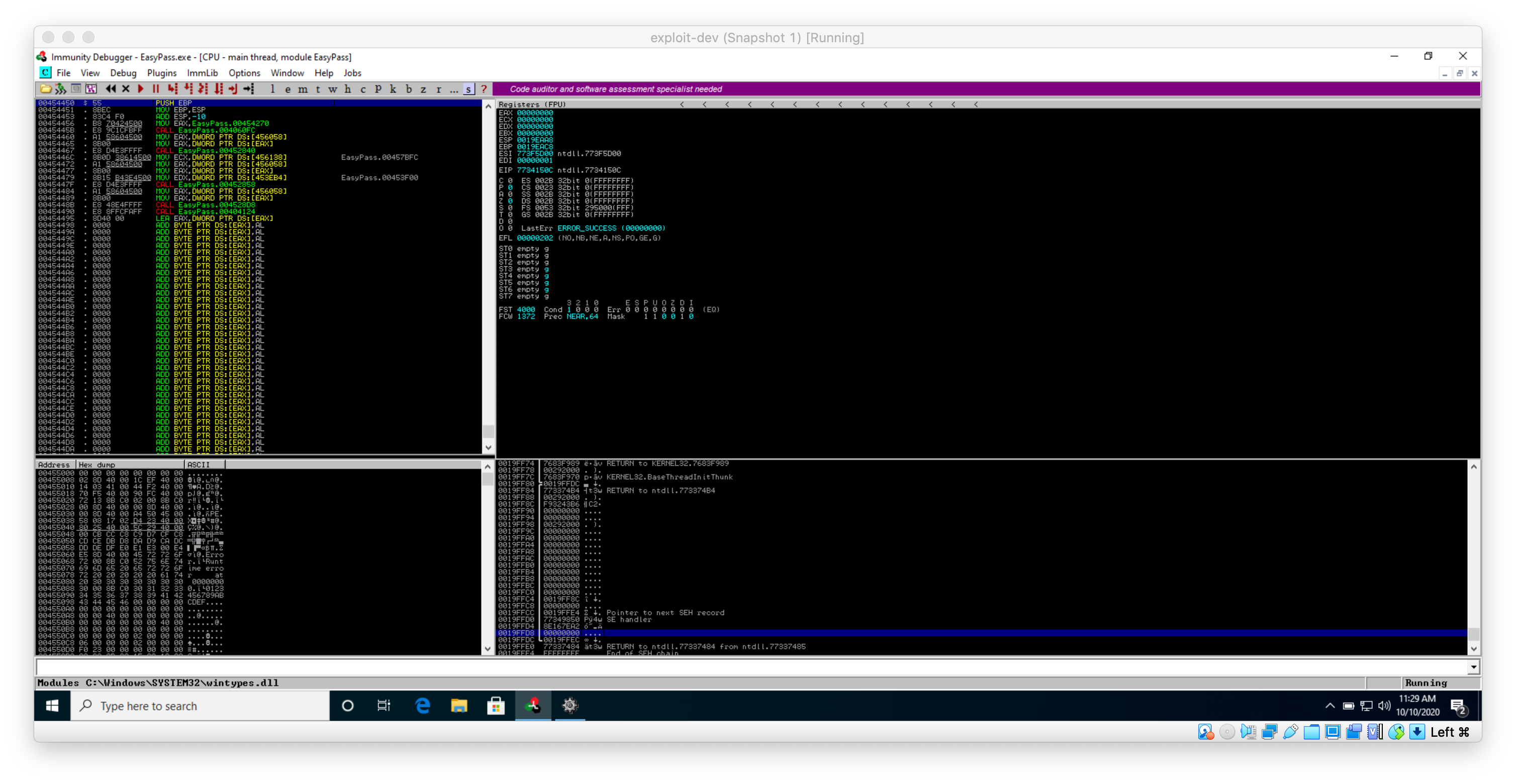
 I used the F9 key to run the debugger.
I used the F9 key to run the debugger.
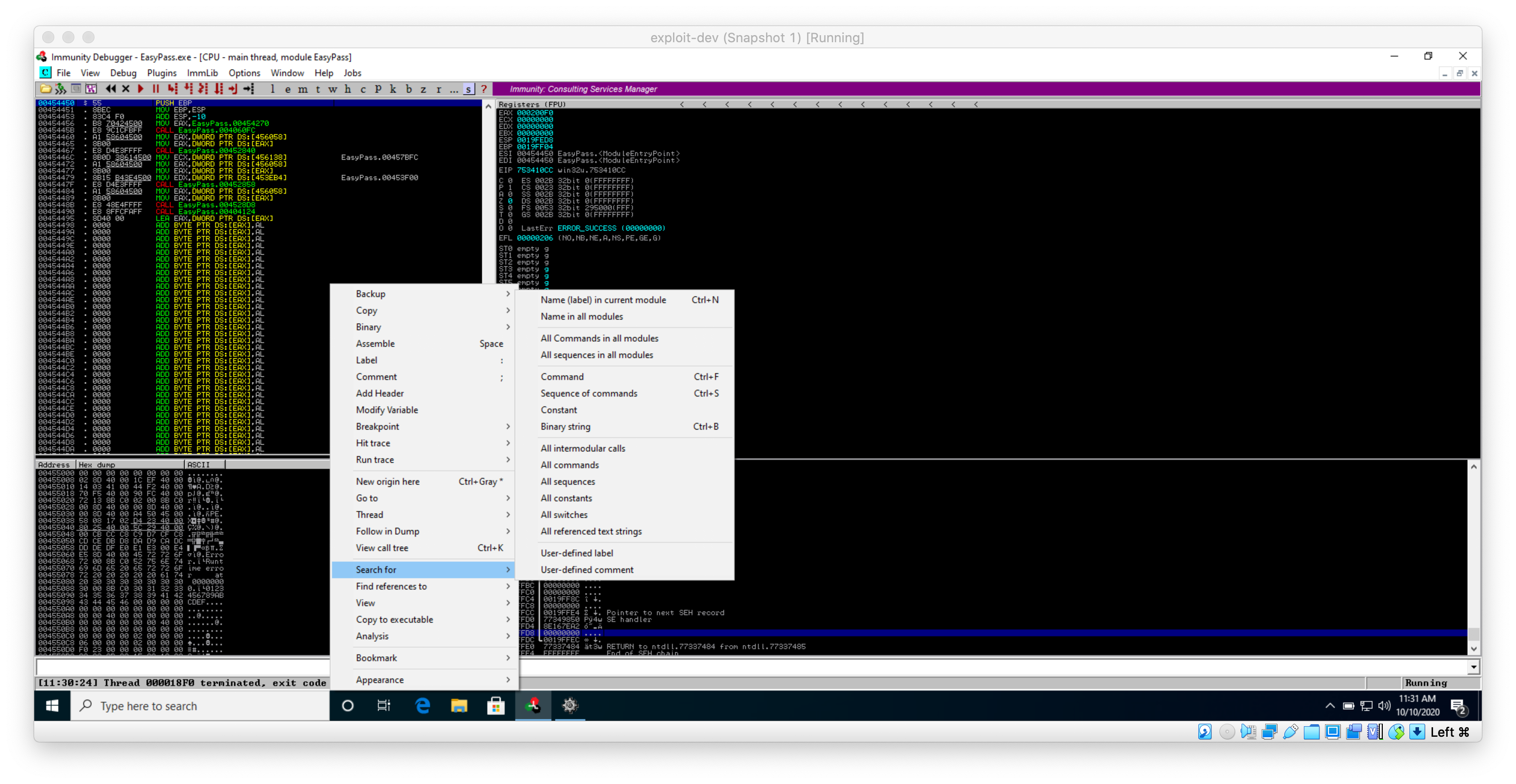
 All I know at this point is that the program is asking me to enter a string. I should use Immunity to search for all referenced strings. I can do this by right-clicking in the top left window and selecting 'search for > all referenced text strings'.
All I know at this point is that the program is asking me to enter a string. I should use Immunity to search for all referenced strings. I can do this by right-clicking in the top left window and selecting 'search for > all referenced text strings'.
 This pops open a new window that contains all the text strings. I can right click that new window and search for specific text.
This pops open a new window that contains all the text strings. I can right click that new window and search for specific text.
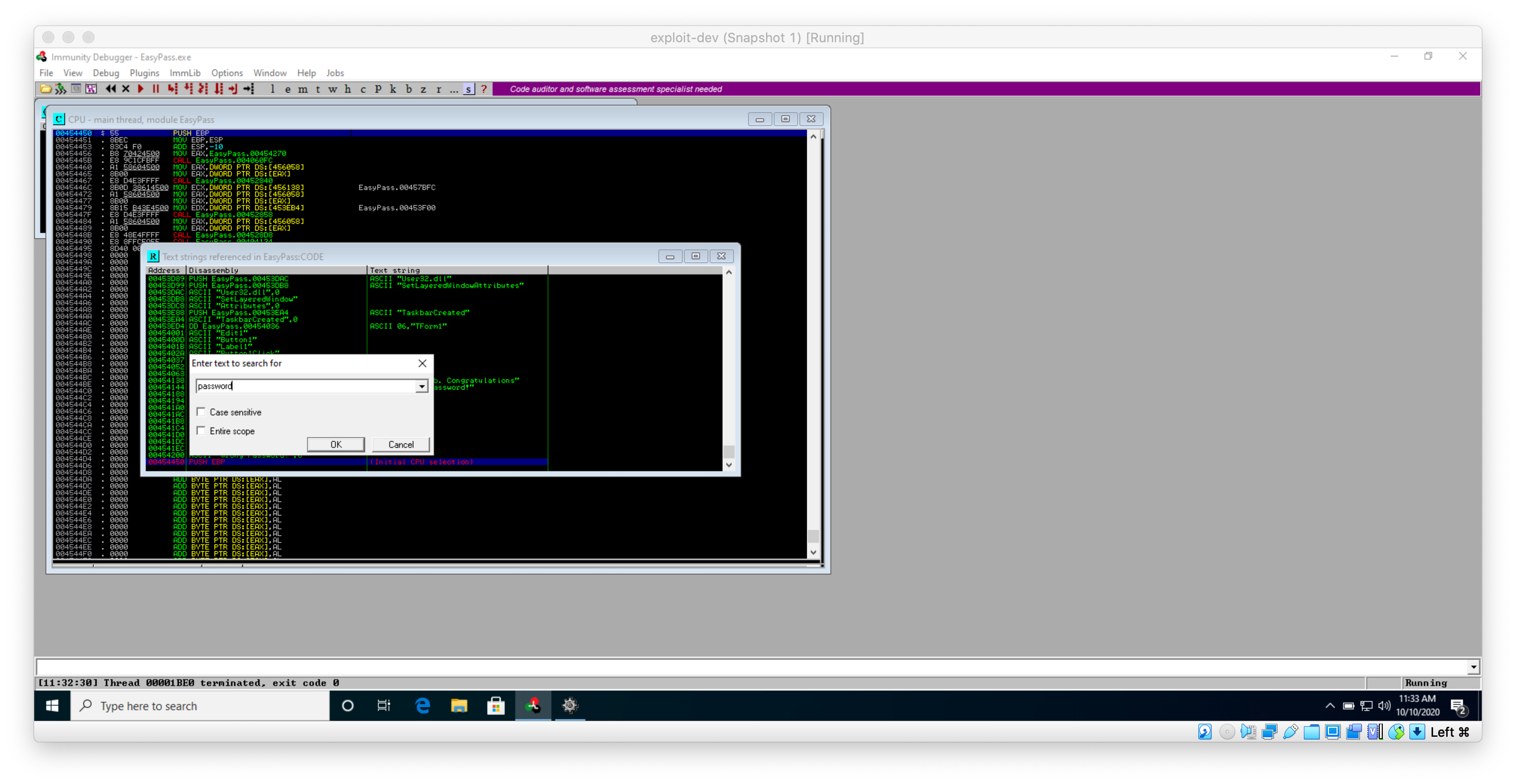 So I found a string that states "Good Job, Congra". I can assume that this is what is displayed when the password entered is correct. In order to see what happens in the program after that message is displayed, I right-click it and select follow in disassembler.
So I found a string that states "Good Job, Congra". I can assume that this is what is displayed when the password entered is correct. In order to see what happens in the program after that message is displayed, I right-click it and select follow in disassembler.
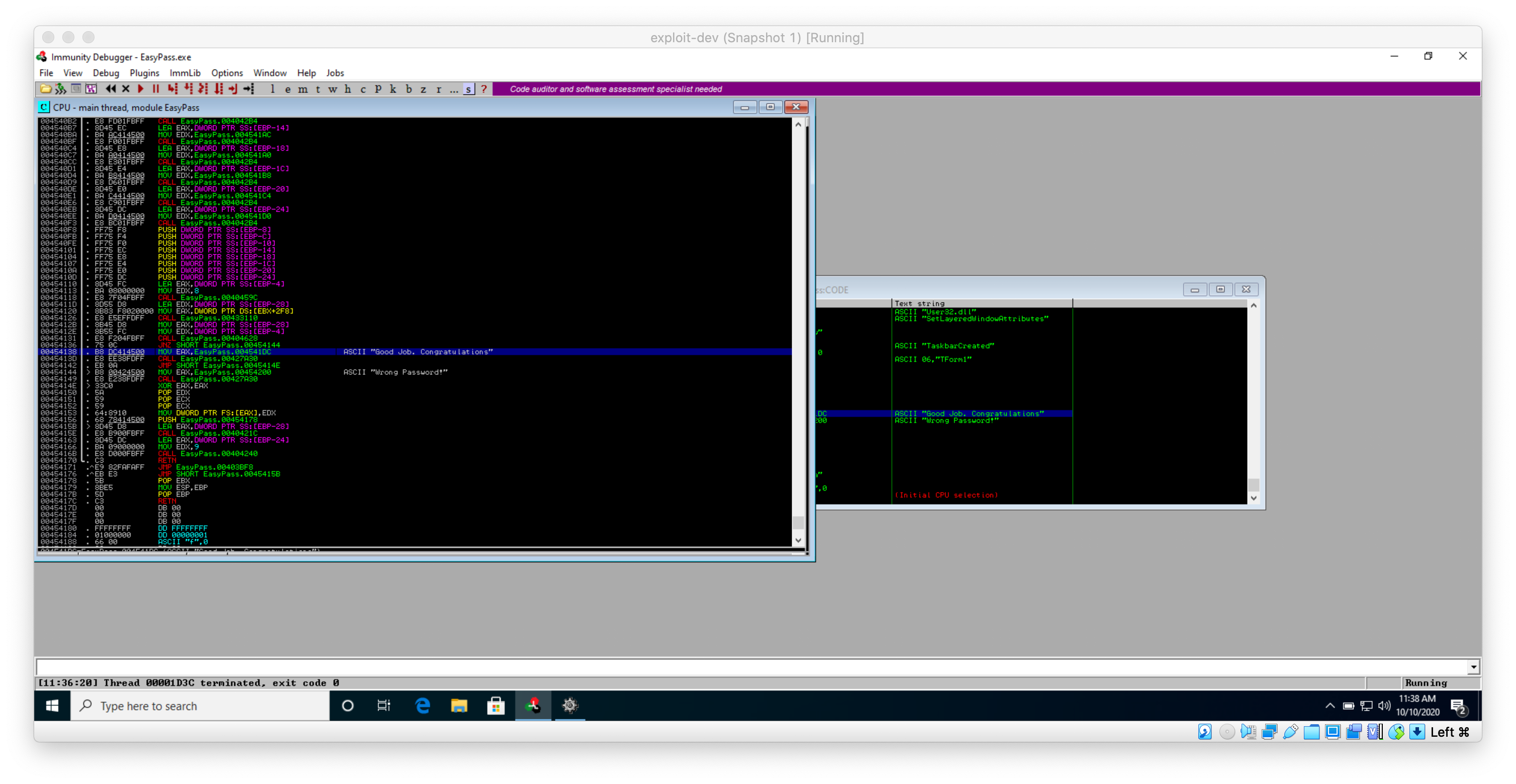 So that JNZ instruction sent me to the wrong password instruction. I can assume that the CALL instruction immediately preceding it is the one that checks the password then. I select it, then set a breakpoint on it with F2.
So that JNZ instruction sent me to the wrong password instruction. I can assume that the CALL instruction immediately preceding it is the one that checks the password then. I select it, then set a breakpoint on it with F2.
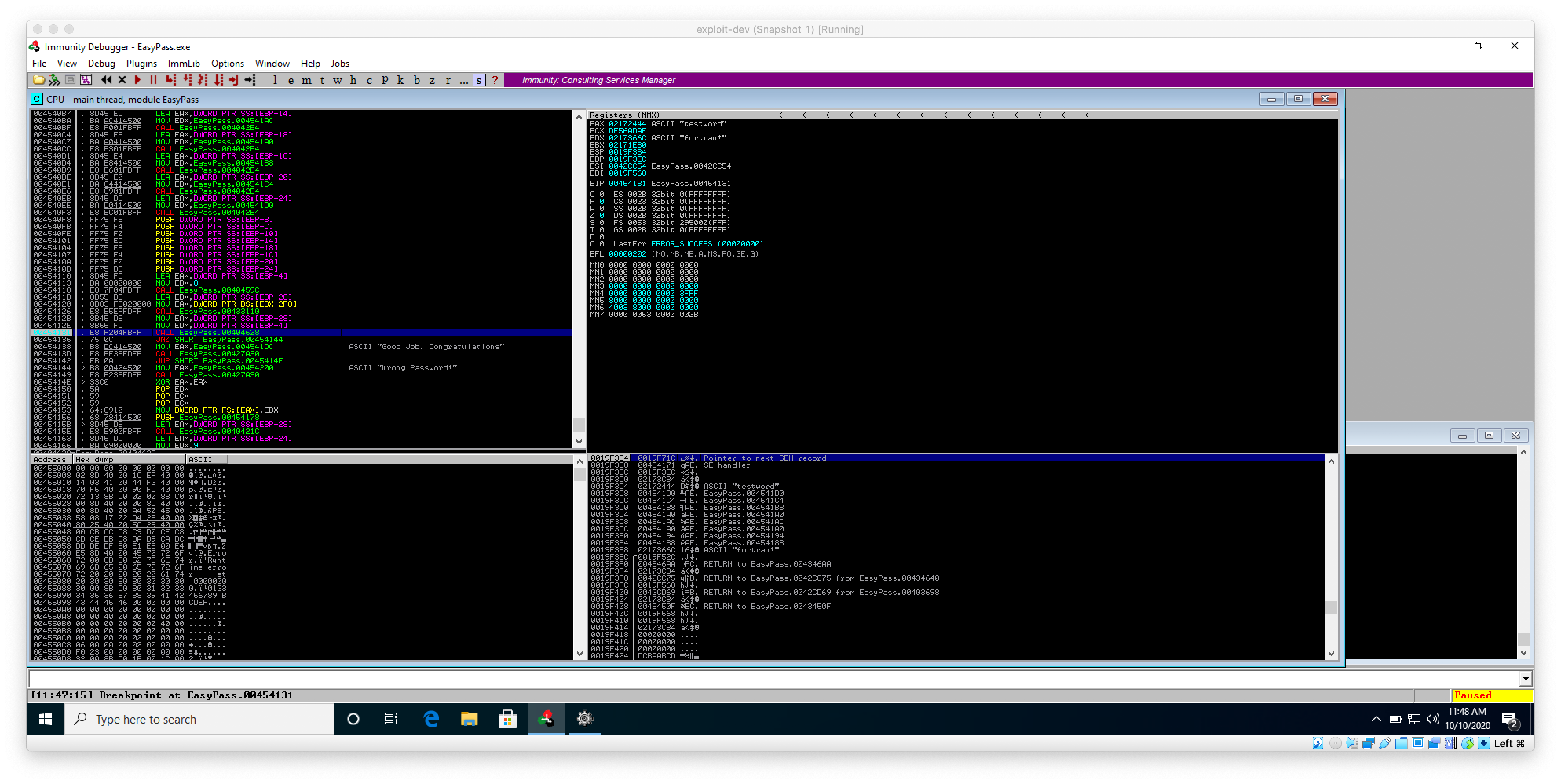
 Now, with my breakpoint set, I begin typing a password in to the program window. After I hit the check password button, the execution of the program is paused by Immunity, and I can see the test password I entered in the program in the EAX register, and fortran! in the EDX. The program is most likely comparing the value of the string stored in EAX against the value of the string stored in EDX.
Now, with my breakpoint set, I begin typing a password in to the program window. After I hit the check password button, the execution of the program is paused by Immunity, and I can see the test password I entered in the program in the EAX register, and fortran! in the EDX. The program is most likely comparing the value of the string stored in EAX against the value of the string stored in EDX.
 If I select follow on the CALL operation breakpoint in the main thread, I will follow the CALL into the function, where I can see what it is doing.
If I select follow on the CALL operation breakpoint in the main thread, I will follow the CALL into the function, where I can see what it is doing.
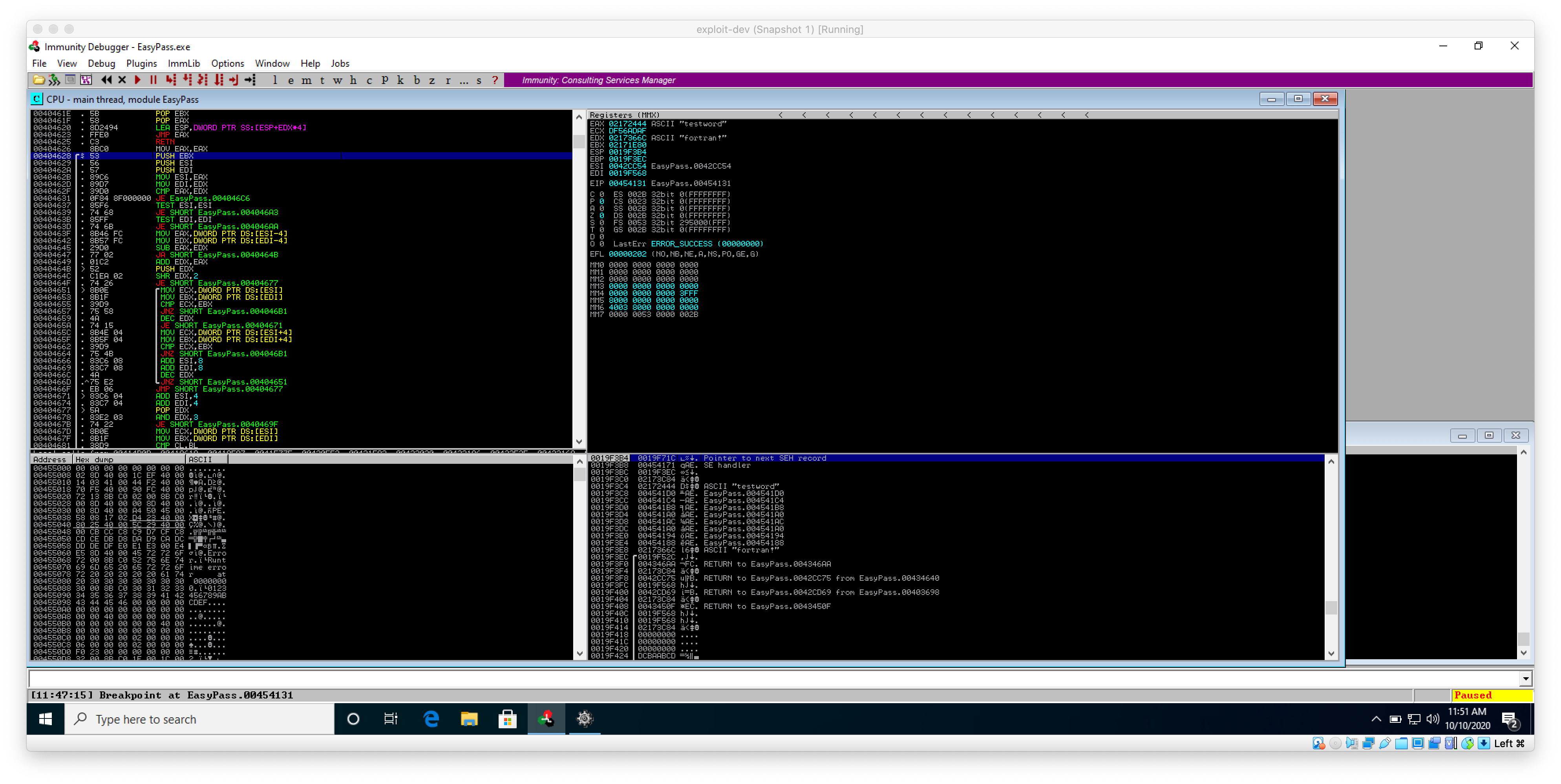 It takes me to address 00404628. A few operations down, I can see that my test password string is moved from ESI to EAX, and the real password is moved from EDI to EDX. With both strings stored in those memory registers, the program then uses the CMP operation to compare the two.
It takes me to address 00404628. A few operations down, I can see that my test password string is moved from ESI to EAX, and the real password is moved from EDI to EDX. With both strings stored in those memory registers, the program then uses the CMP operation to compare the two.
When I enter the password into the program, it displays the good job window as expected!