Pattern of Life
Instructions
Solution
https://static.metaproblems.com/2a641db1c19526efb7e0c99004ccba0d/pattern_of_life.pcapng
Downloaded pcap and opened in wireshark.
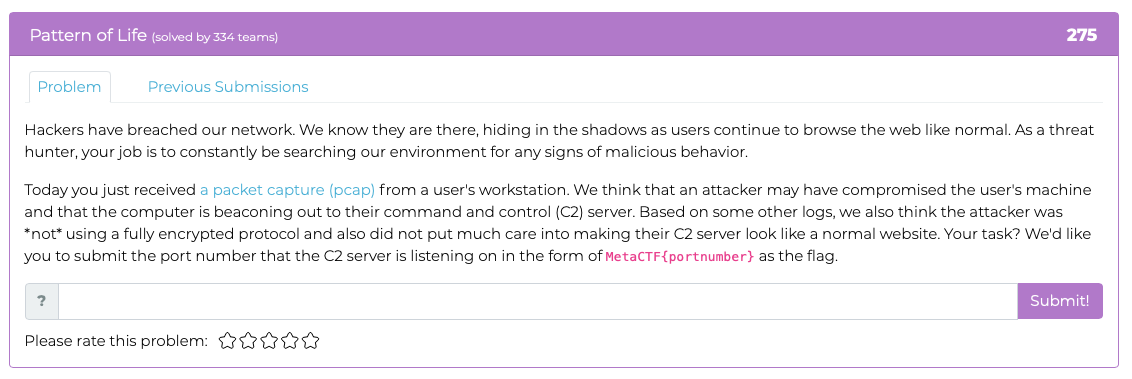
They said it's not in an encrypted protocol, so I can filter out TLSv1.2 with '!tls'.
There's a bunch of ACK packets going out 49606 to a public IP on port 443.
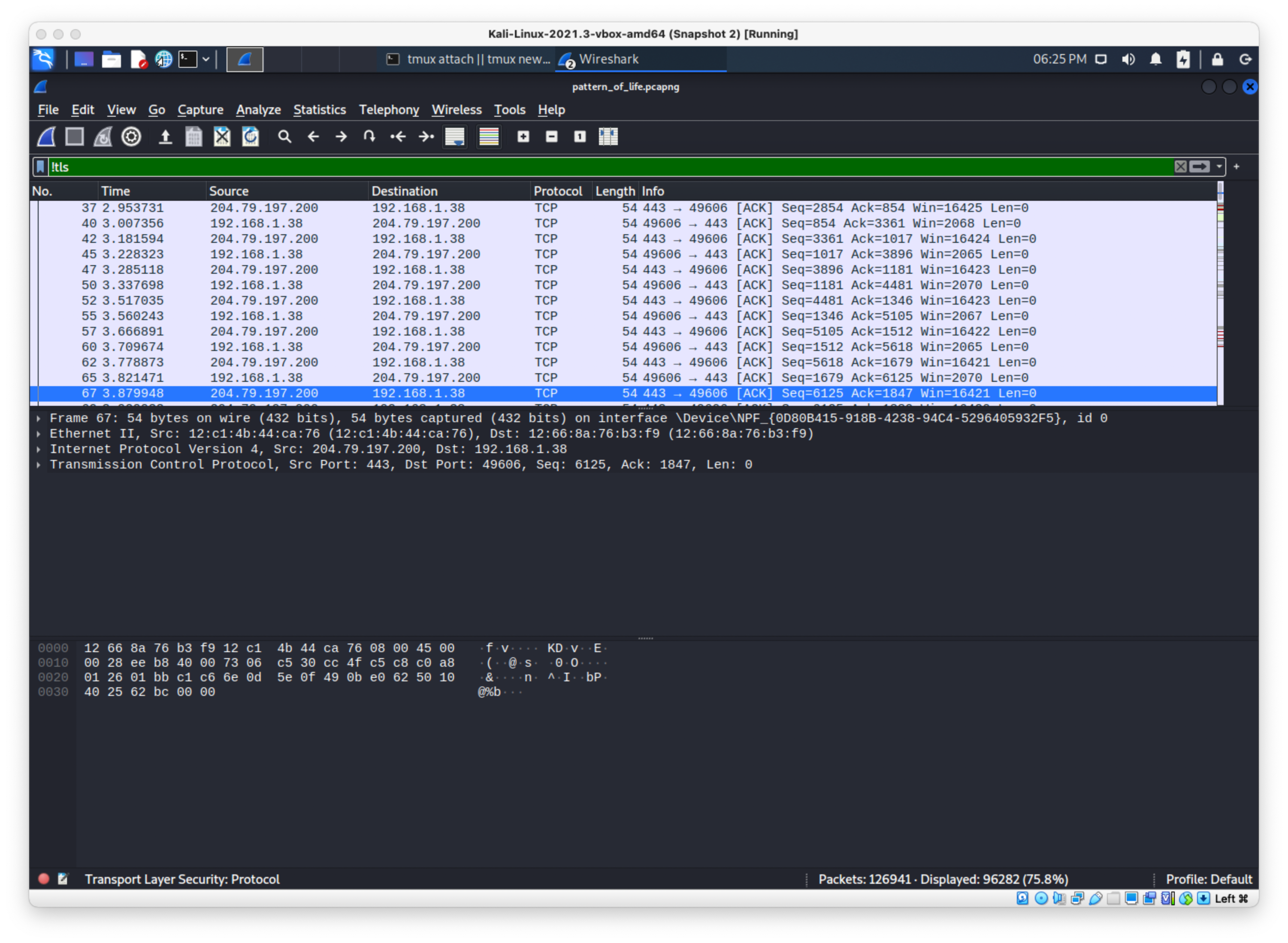 Again same thing:
Again same thing:
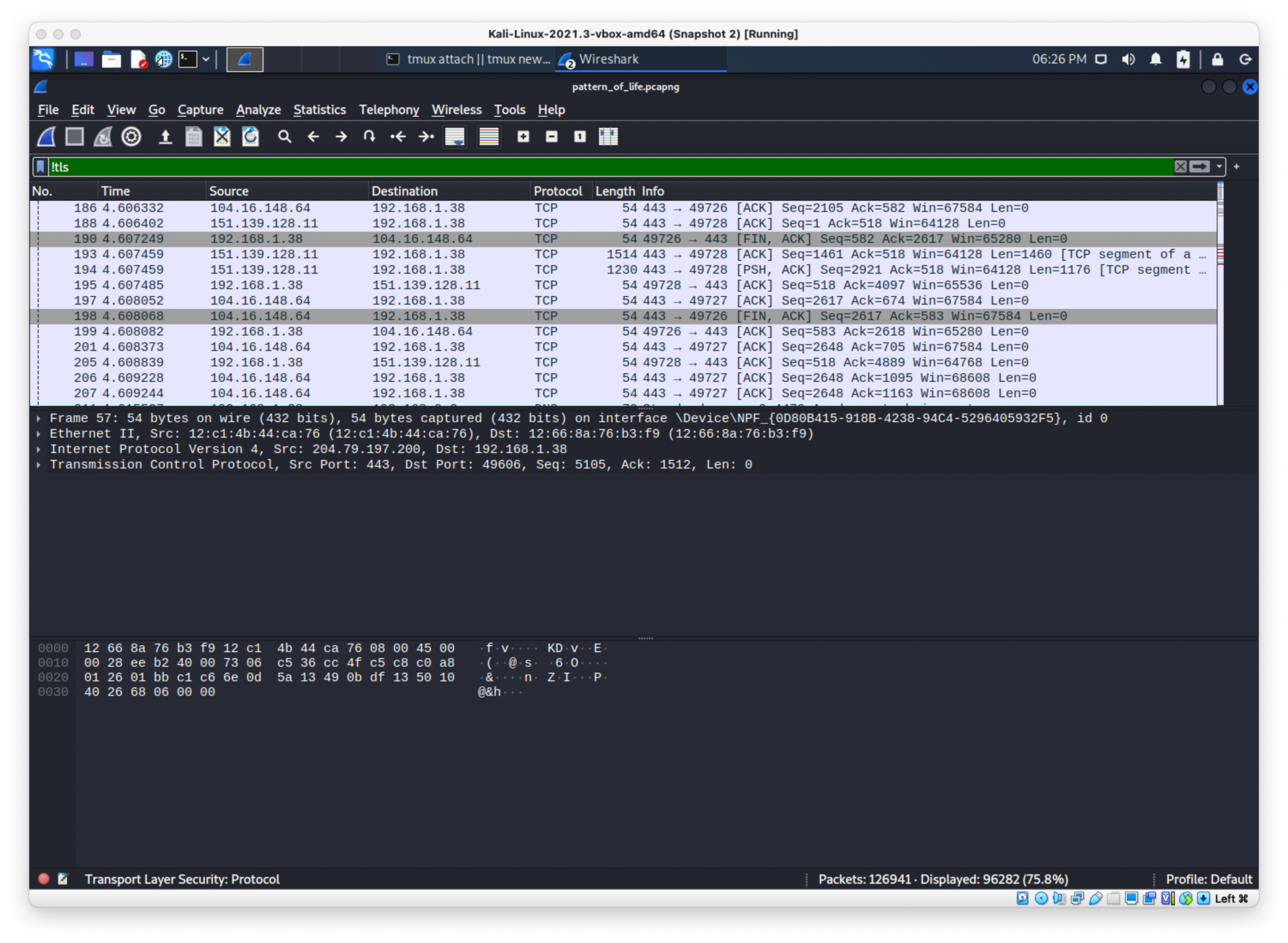
That wasn't it. There is some weird DNS requests
I'll filter only the packets with the infected host as the source, and I'll filter ouit tcp.port 443 since that's not the right answer seeing as I tried it…
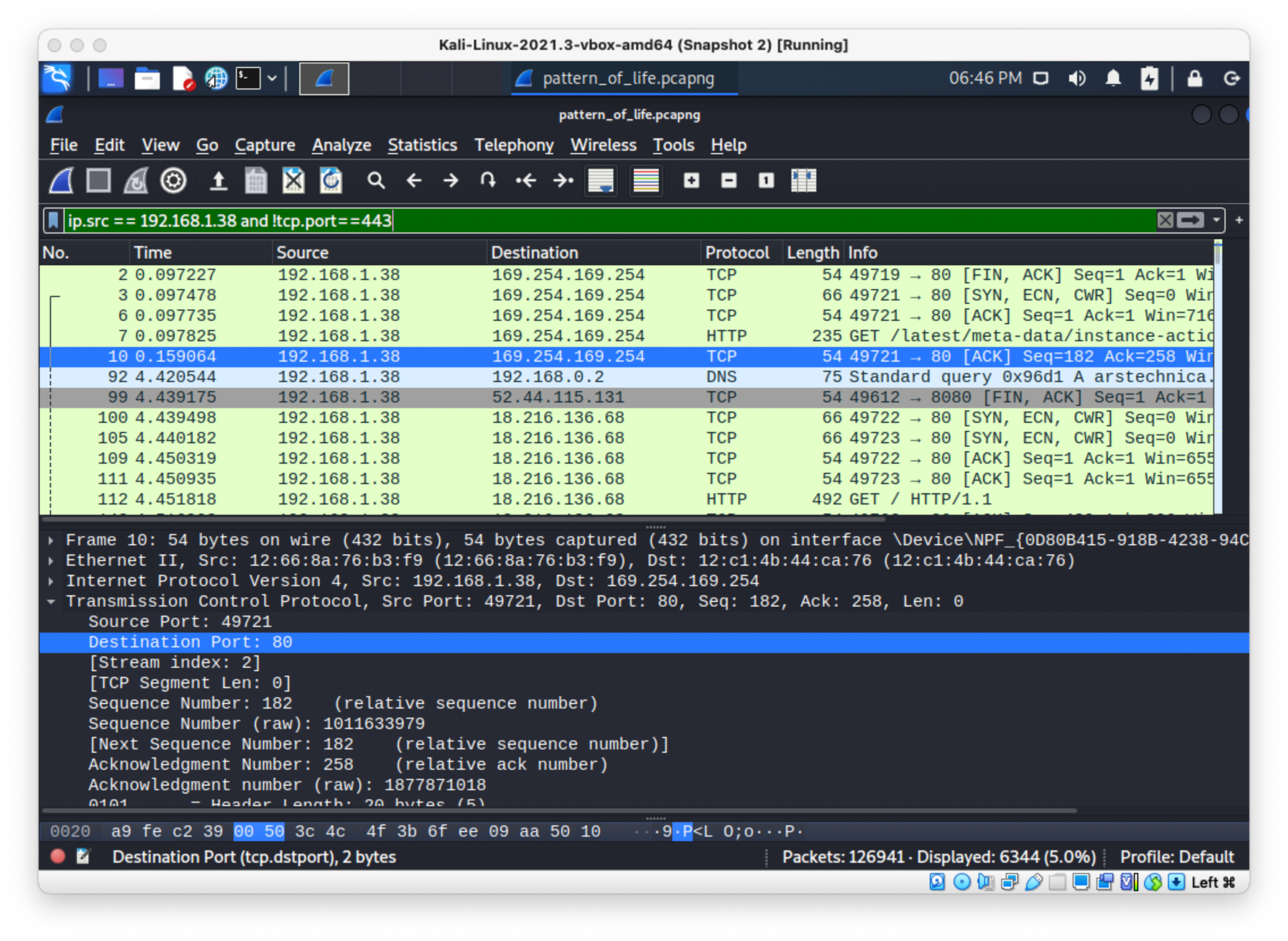 Something on 137:
Something on 137:
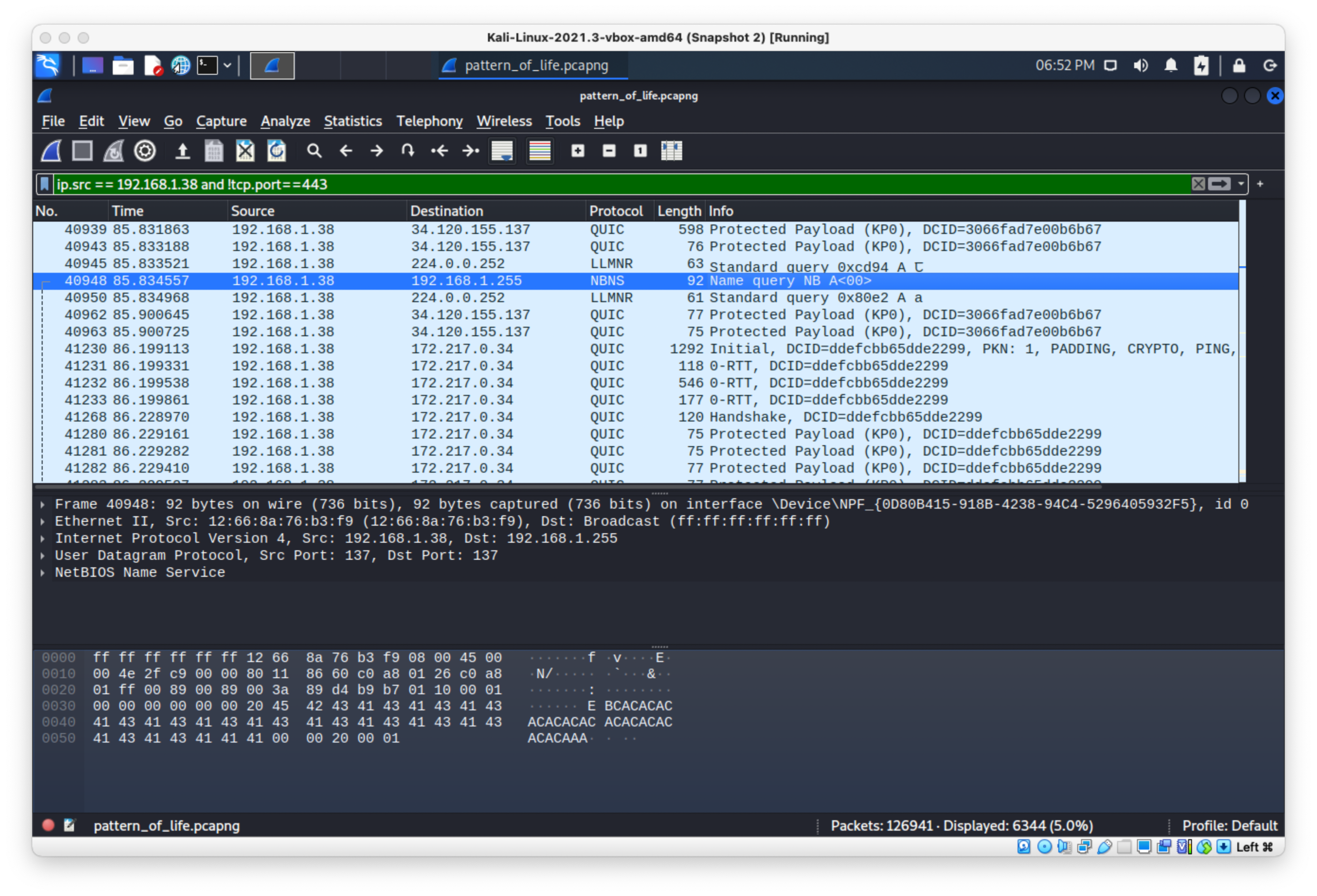 Ok, I filtered out the QUIC stuff, and there are just these weird single chars going over LLMNR to DST Port 5355:
Ok, I filtered out the QUIC stuff, and there are just these weird single chars going over LLMNR to DST Port 5355:
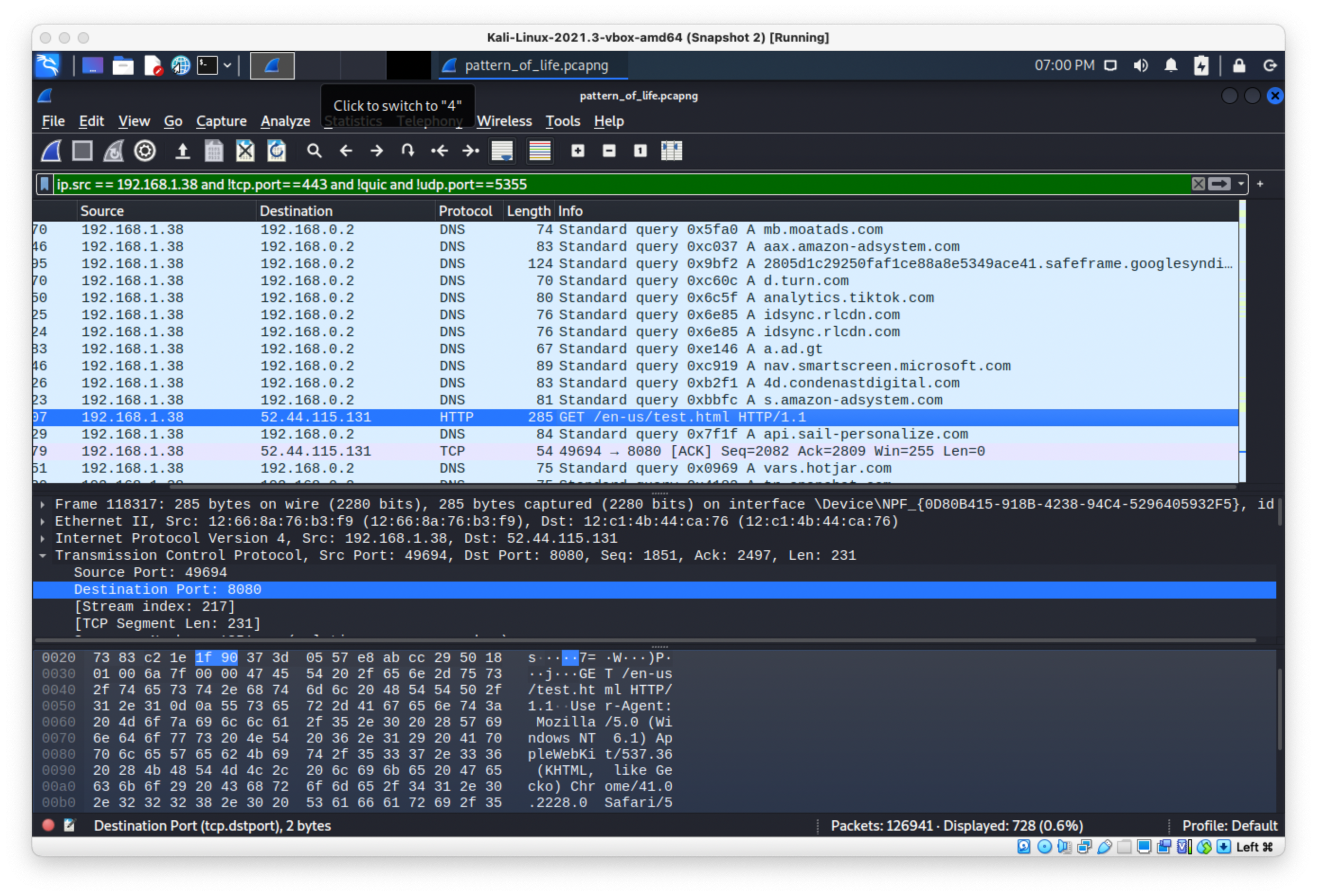
 I saw that there was this recurring request for /en-us/test.html, on port 8080, so I tried that, and it was the flag!
I saw that there was this recurring request for /en-us/test.html, on port 8080, so I tried that, and it was the flag!
 Flag:
Flag:
MetaCTF{8080}
Next: The Searcher