Shellcode Primer
Information
FrostFest - Jack's Office
- Shellcode Primer
Difficulty: 3/5
Complete the Shellcode Primer in Jack's office. According to the last challenge, what is the secret to KringleCon success? "All of our speakers and organizers, providing the gift of ____, free to the community." Talk to Chimney Scissorsticks in the NetWars area for hints.
Conversation
Solution
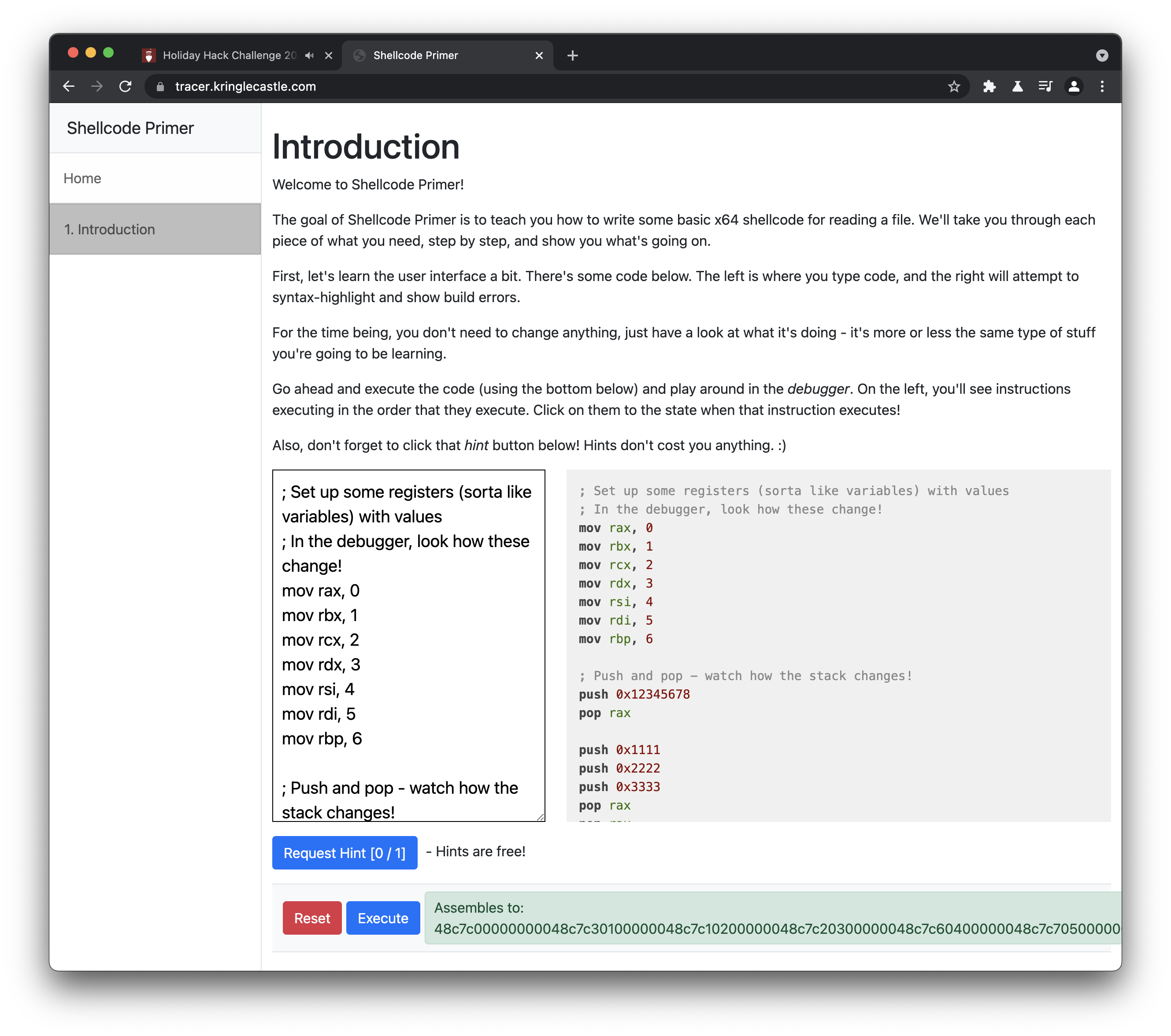
Introduction
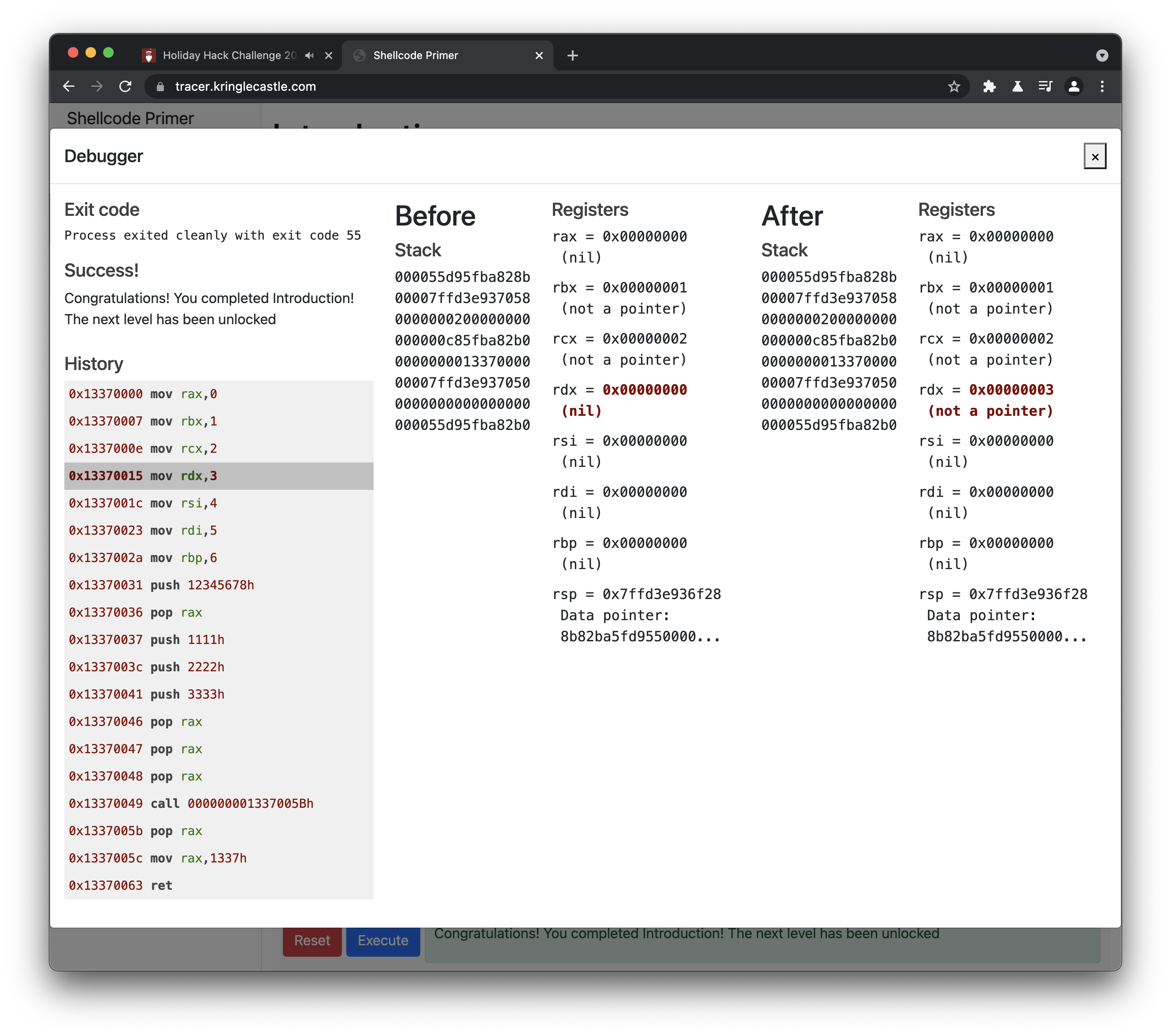
The Intro code was already done for me. Running it opened the debugger window where I can click around and stuff.
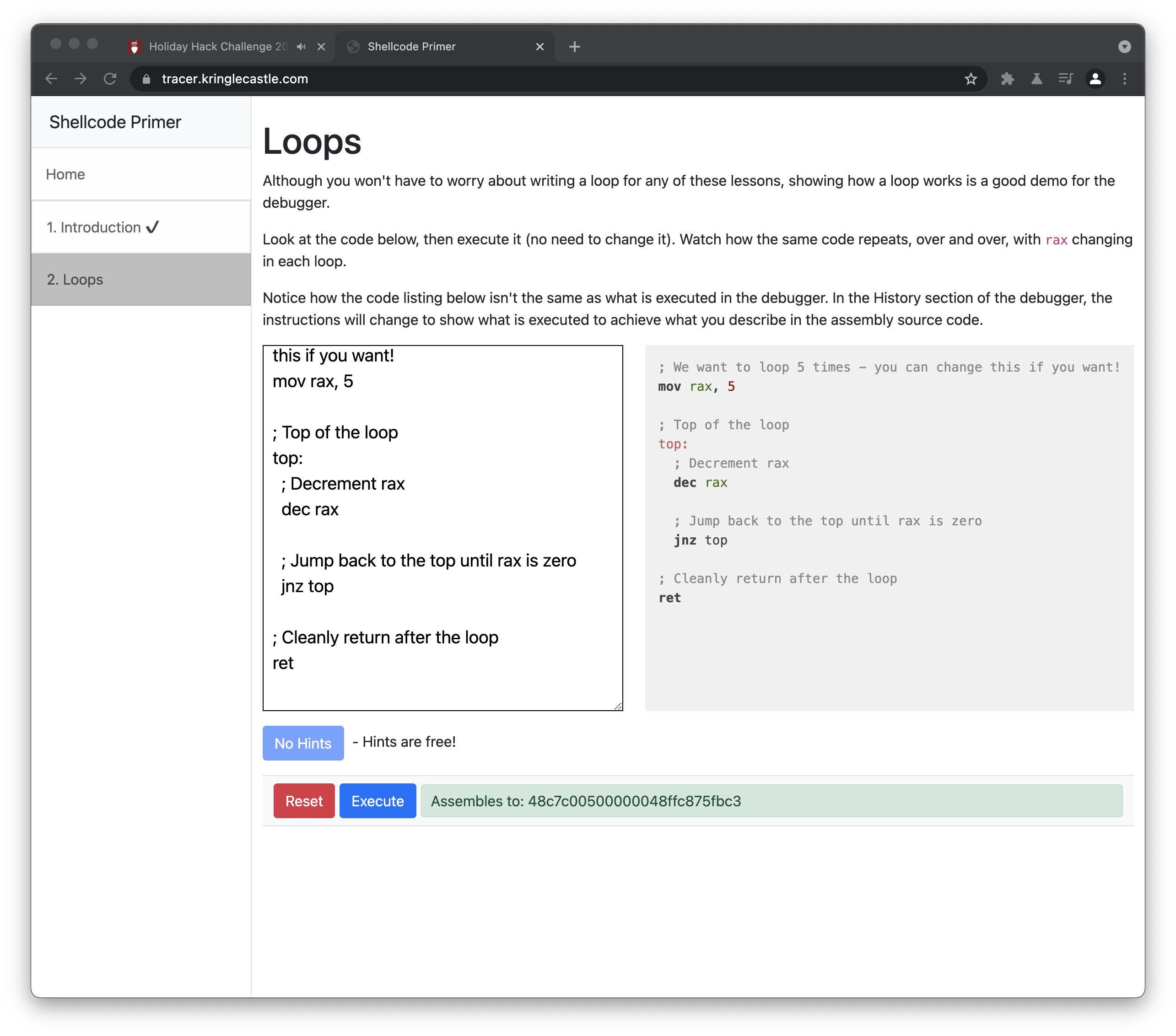
Loops
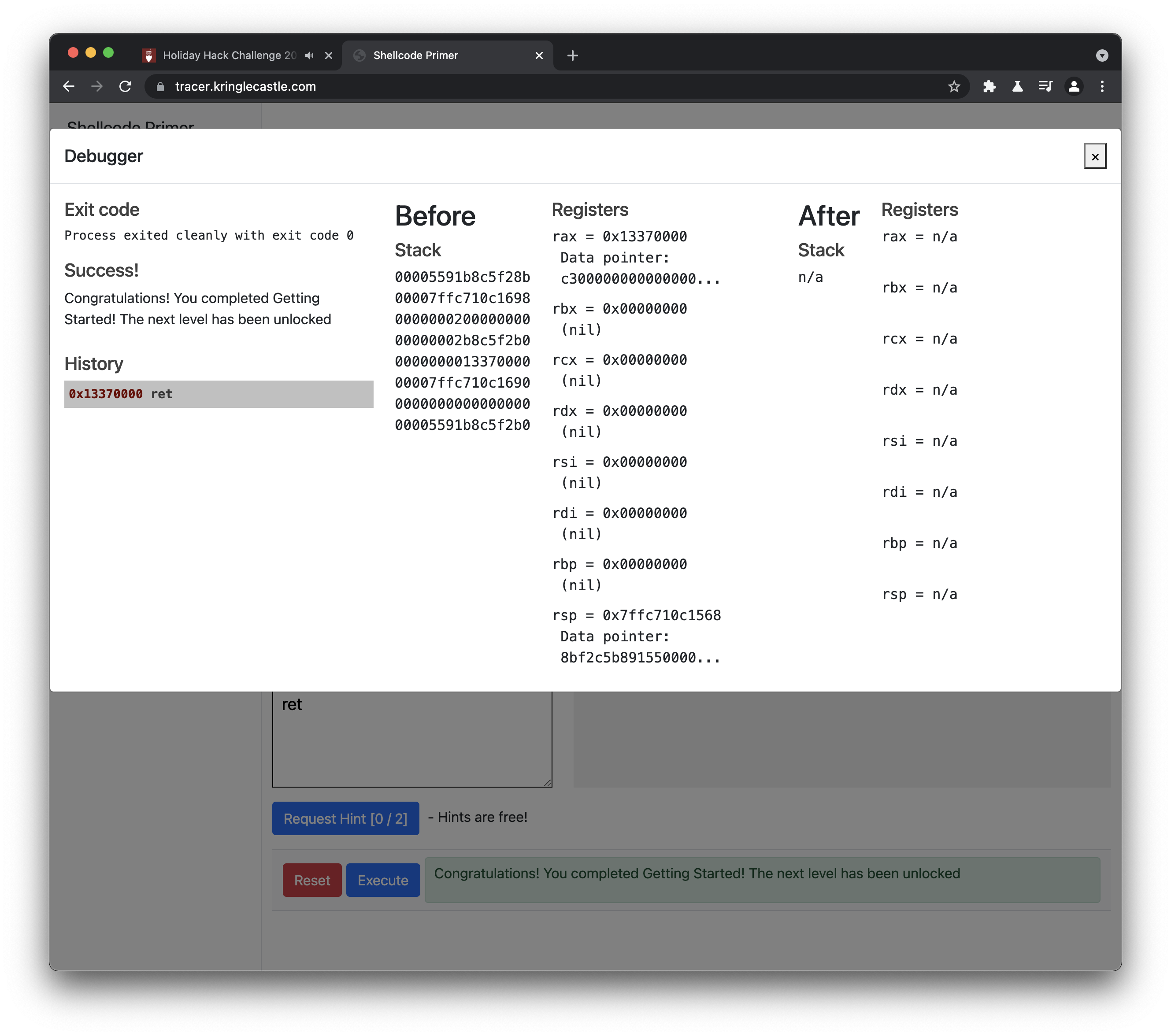
Getting Started
Code:
ret
Returning a Value
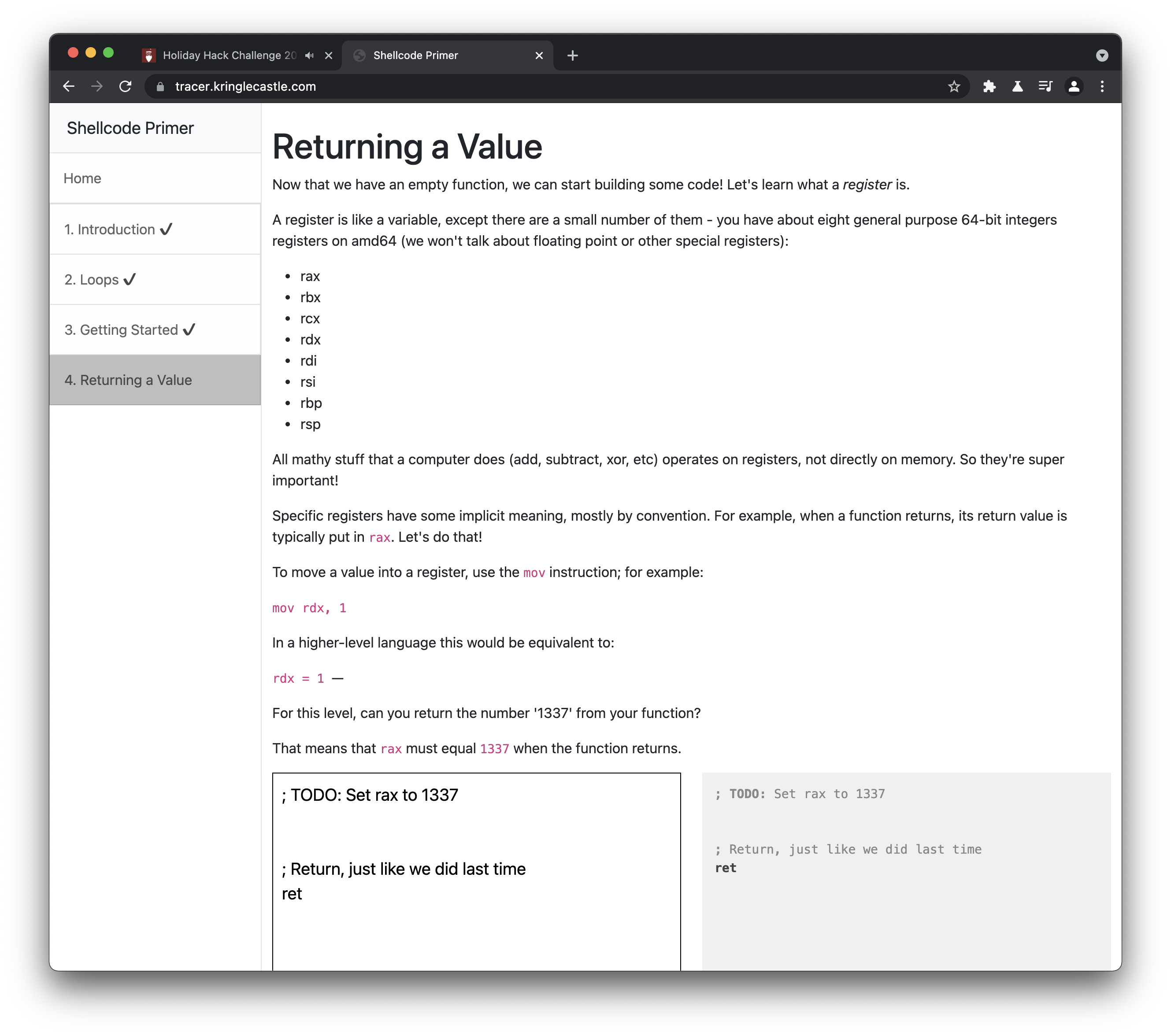
; TODO: Set rax to 1337
mov rax, 1337
; Return, just like we did last time
ret
System Calls
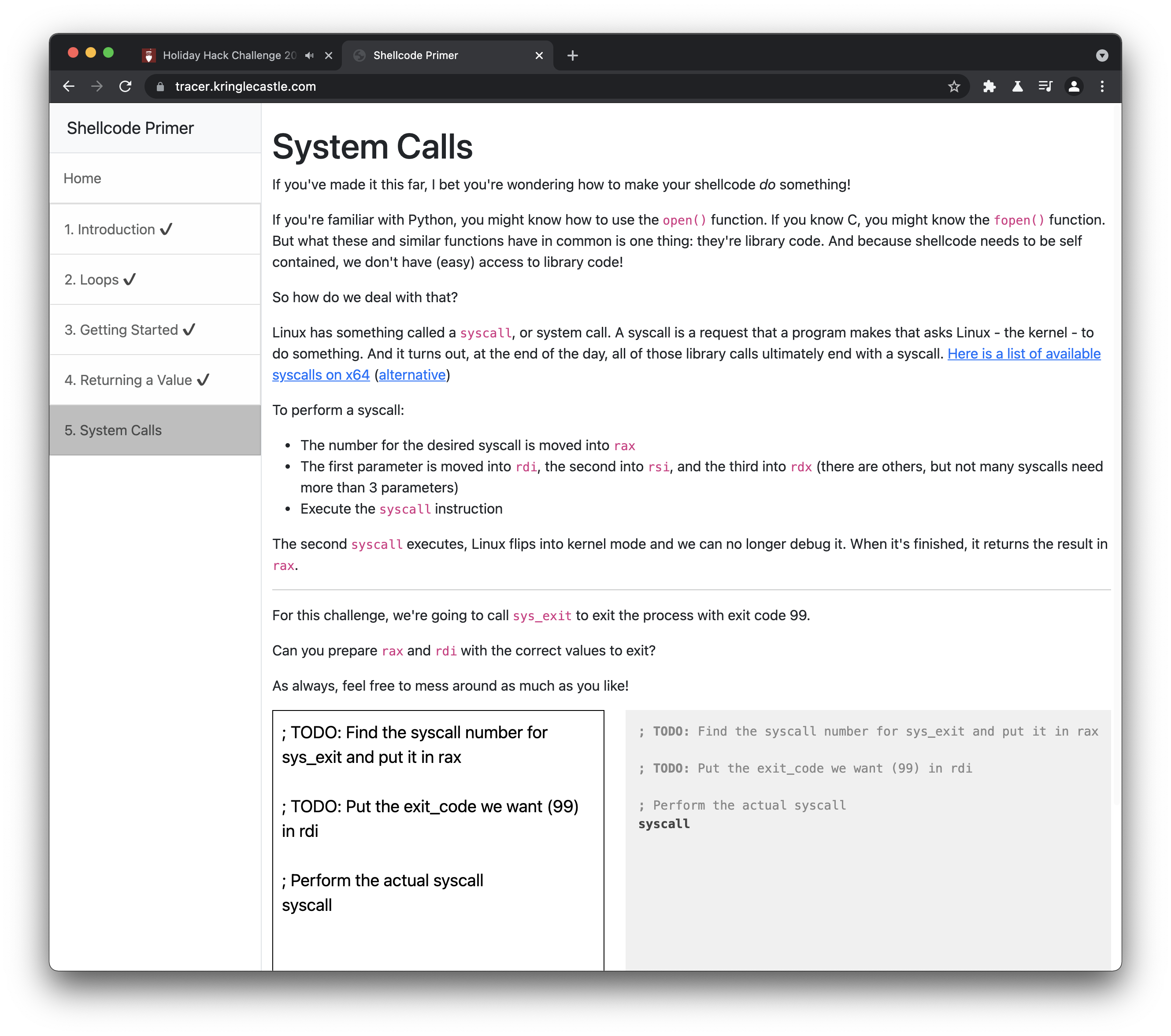 https://blog.rchapman.org/posts/Linux_System_Call_Table_for_x86_64/
https://blog.rchapman.org/posts/Linux_System_Call_Table_for_x86_64/
; TODO: Find the syscall number for sys_exit and put it in rax
mov rax, 60
; TODO: Put the exit_code we want (99) in rdi
mov rdi, 99
; Perform the actual syscall
syscall
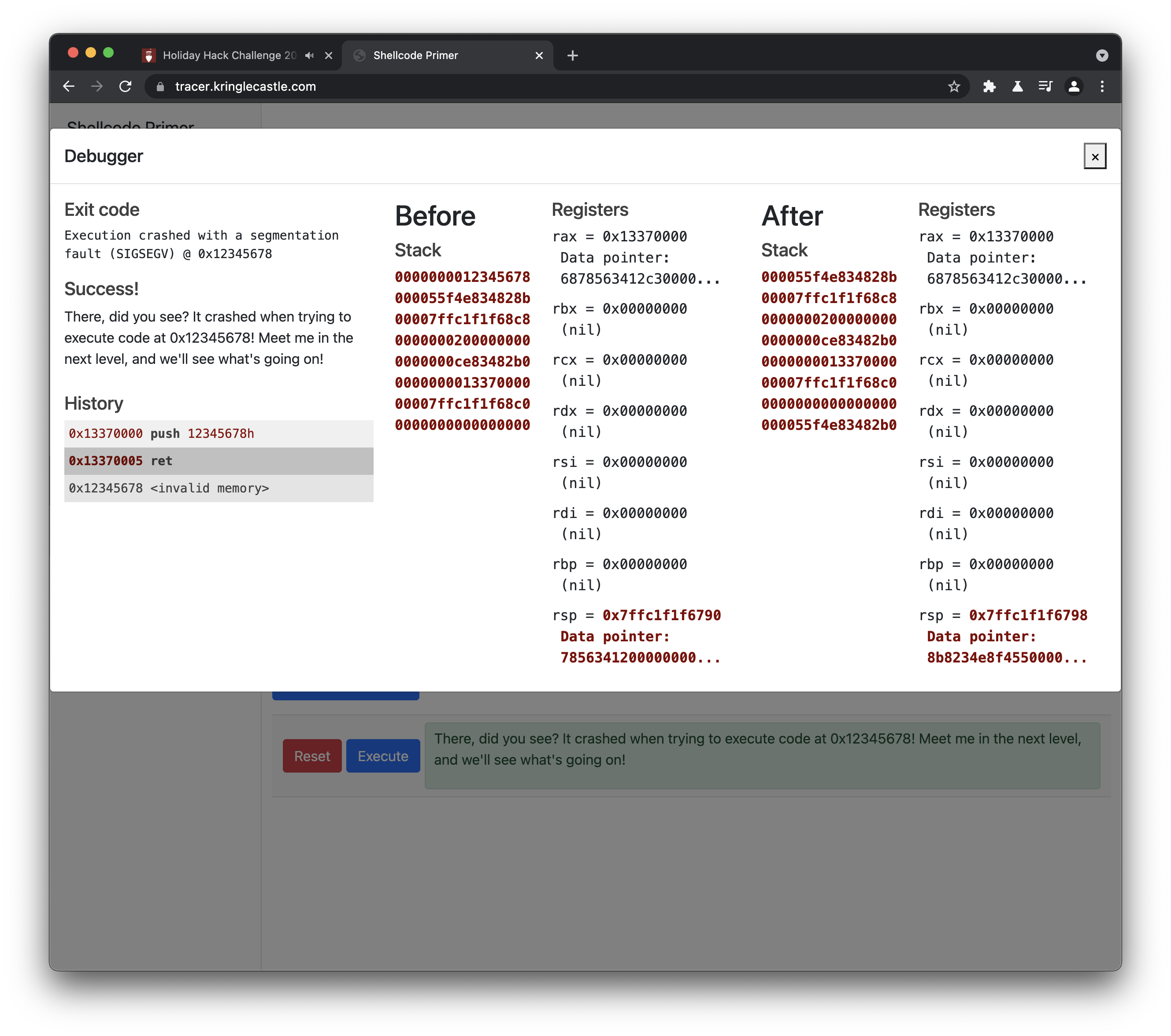
Calling Into the Void
; Push this value to the stack
push 0x12345678
; Try to return
ret
Debug
Getting RIP
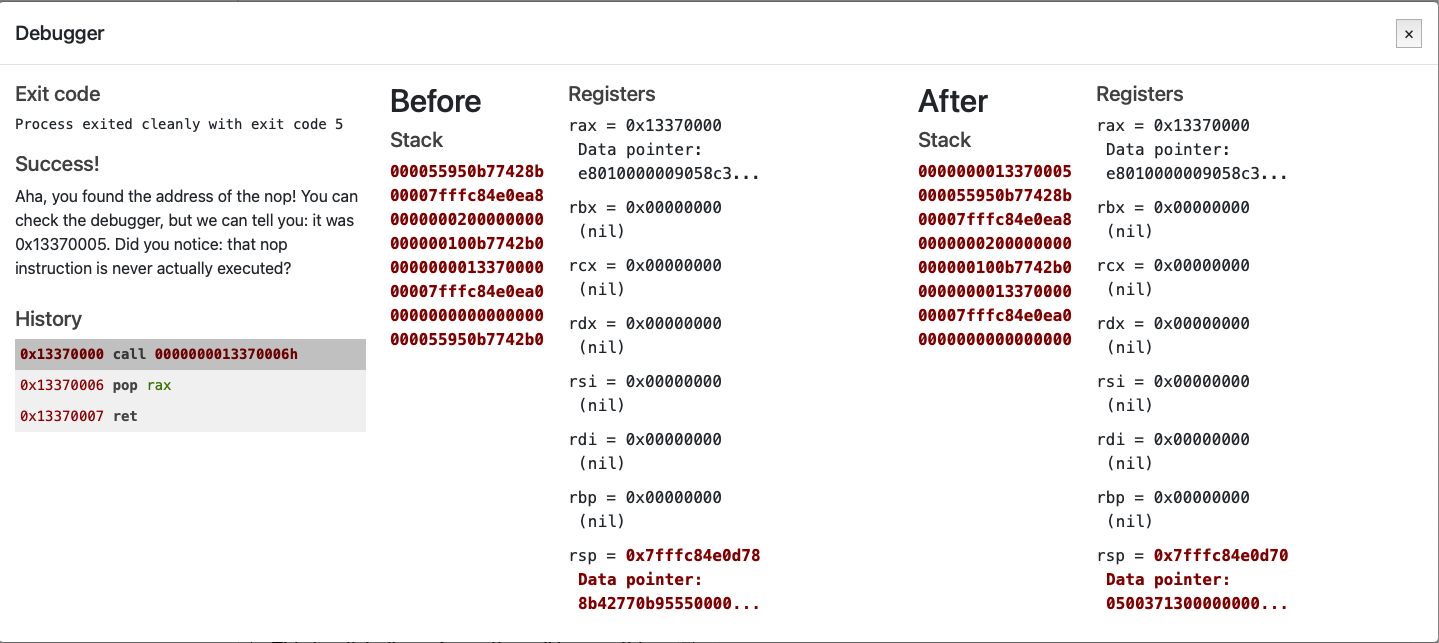
; Remember, this call pushes the return address to the stack
call place_below_the_nop
; This is where the function *thinks* it is supposed to return
nop
; This is a 'label' - as far as the call knows, this is the start of a function
place_below_the_nop:
; TODO: Pop the top of the stack into rax
pop rax
; Return from our code, as in previous levels
ret
Debug
Hints
Hello, World!
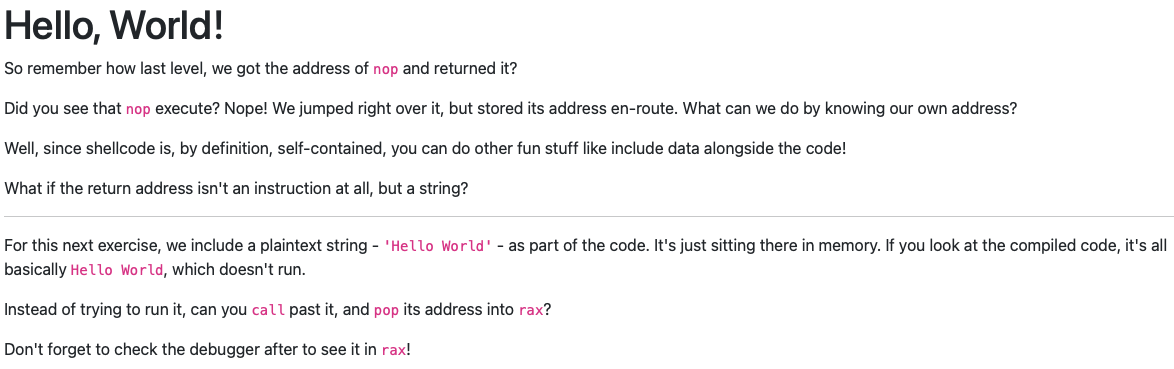
; This is the literal string 'Hello World', null terminated, as code. Except
; it'll crash if it actually tries to run, so we'd better jump over it!
db 'Hello World',0
; This would be a good place for a label and a pop
jump_func:
pop rax
; This would be a good place for a re... oh wait, it's already here. Hooray!
ret
Debug
Hints
Hello, World!!
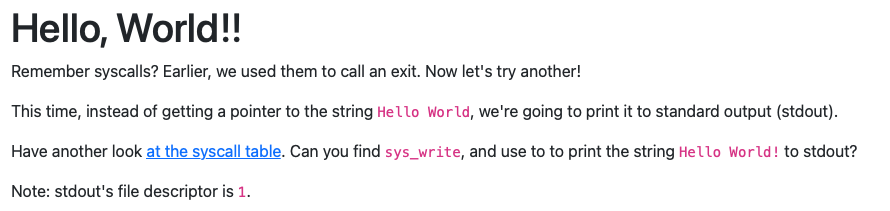
call jump_func
; TODO: Get a reference to this string into the correct register
db 'Hello World!',0
jump_func:
pop rbx
; Set up a call to sys_write
; TODO: Set rax to the correct syscall number for sys_write
mov rax, 1
; TODO: Set rdi to the first argument (the file descriptor, 1)
mov rdi, 1
; TODO: Set rsi to the second argument (buf - this is the "Hello World" string)
mov rsi, rbx
; TODO: Set rdx to the third argument (length of the string, in bytes)
mov rdx, 12
; Perform the syscall
syscall
; Return cleanly
ret
Debug
Hints

Opening a File
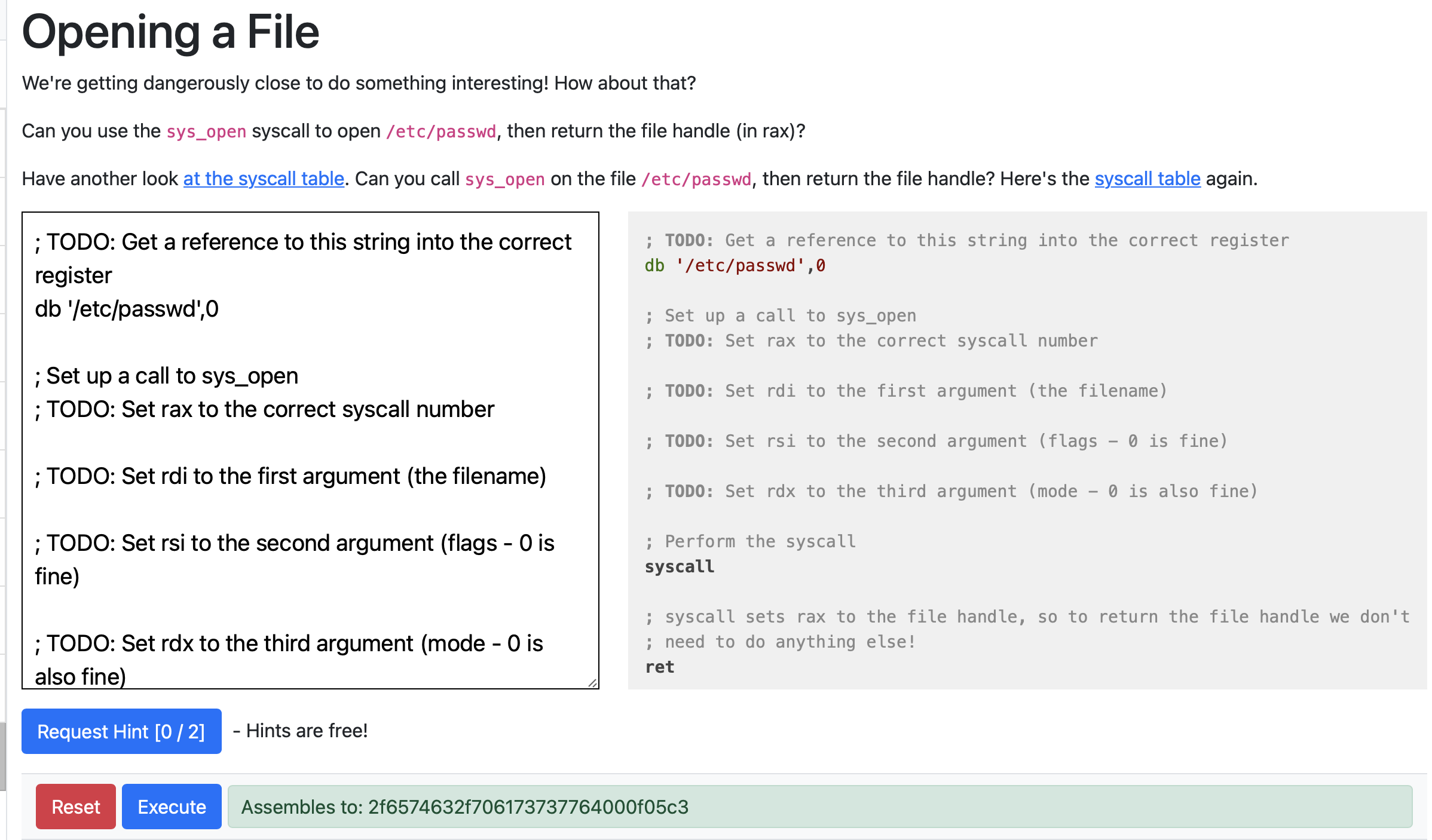
call jump_func
; TODO: Get a reference to this string into the correct register
db '/etc/passwd',0
jump_func:
pop rbx
; Set up a call to sys_open
; TODO: Set rax to the correct syscall number
mov rax, 2
; TODO: Set rdi to the first argument (the filename)
mov rdi, rbx
; TODO: Set rsi to the second argument (flags - 0 is fine)
mov rsi, 0
; TODO: Set rdx to the third argument (mode - 0 is also fine)
mov rdx, 0
; Perform the syscall
syscall
; syscall sets rax to the file handle, so to return the file handle we don't
; need to do anything else!
ret
Debug
Hints
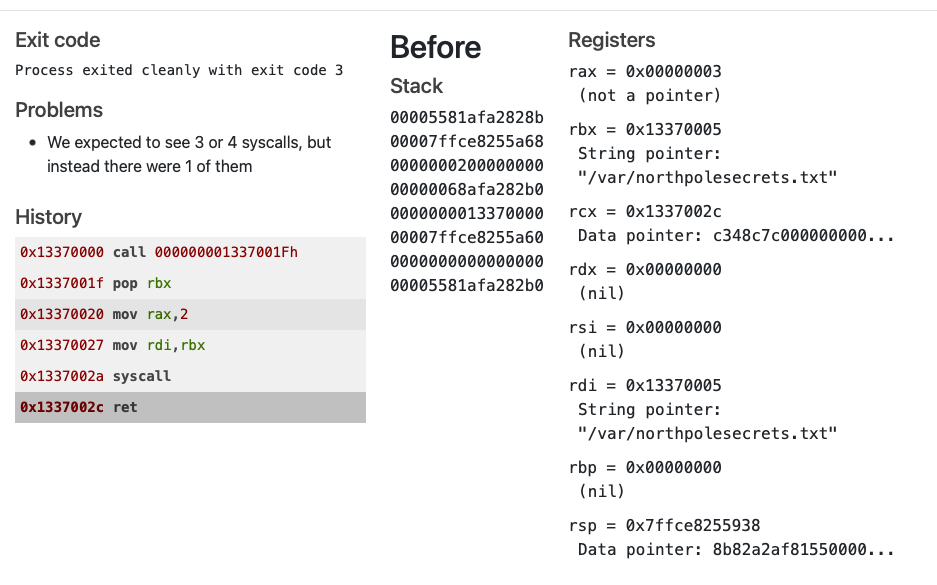
Reading a File
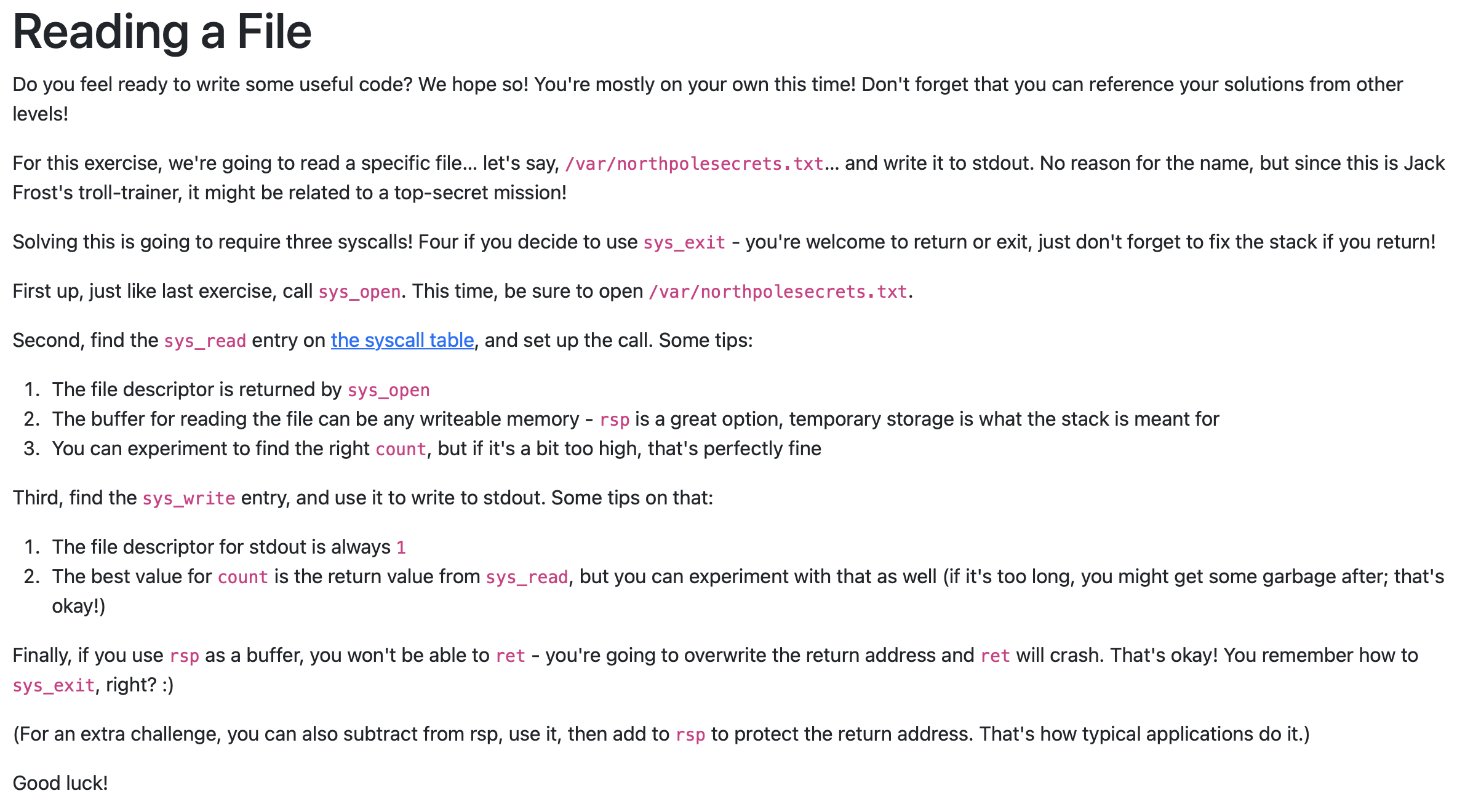
call jump_func
; TODO: Get a reference to this
db '/var/northpolesecrets.txt',0
jump_func:
pop rbx
; TODO: Call sys_open
mov rax, 2
mov rdi, rbx
syscall
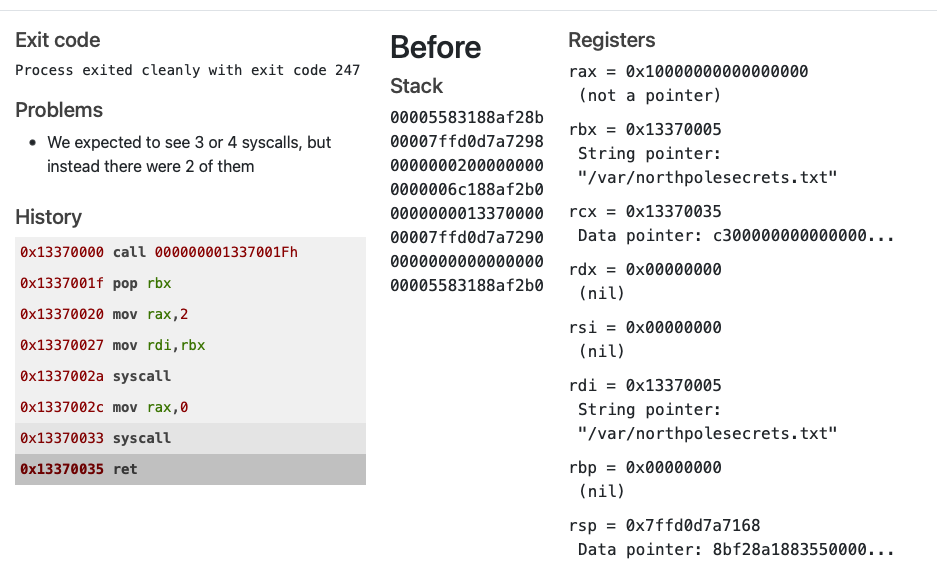
; TODO: Call sys_read on the file handle and read it into rsp
mov rdi, rax
mov rax, 0
mov rsi, rsp
mov rdx, 250
syscall
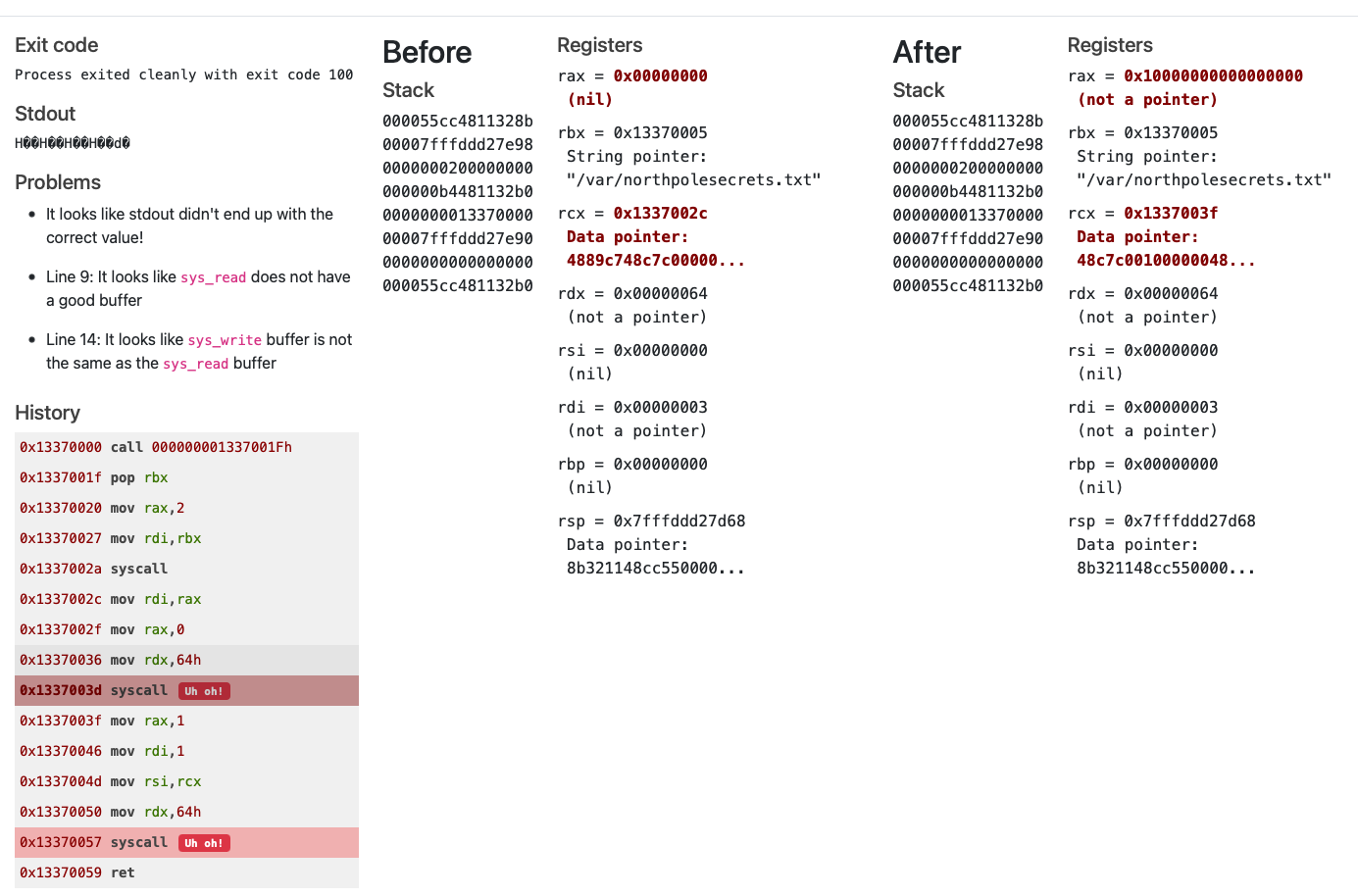
; TODO: Call sys_write to write the contents from rsp to stdout (1)
mov rax, 1
mov rdi, 1
mov rsi, rsp
mov rdx, 250
syscall
; TODO: Call sys_exit
mov rax, 60
syscall
Debug
Hints
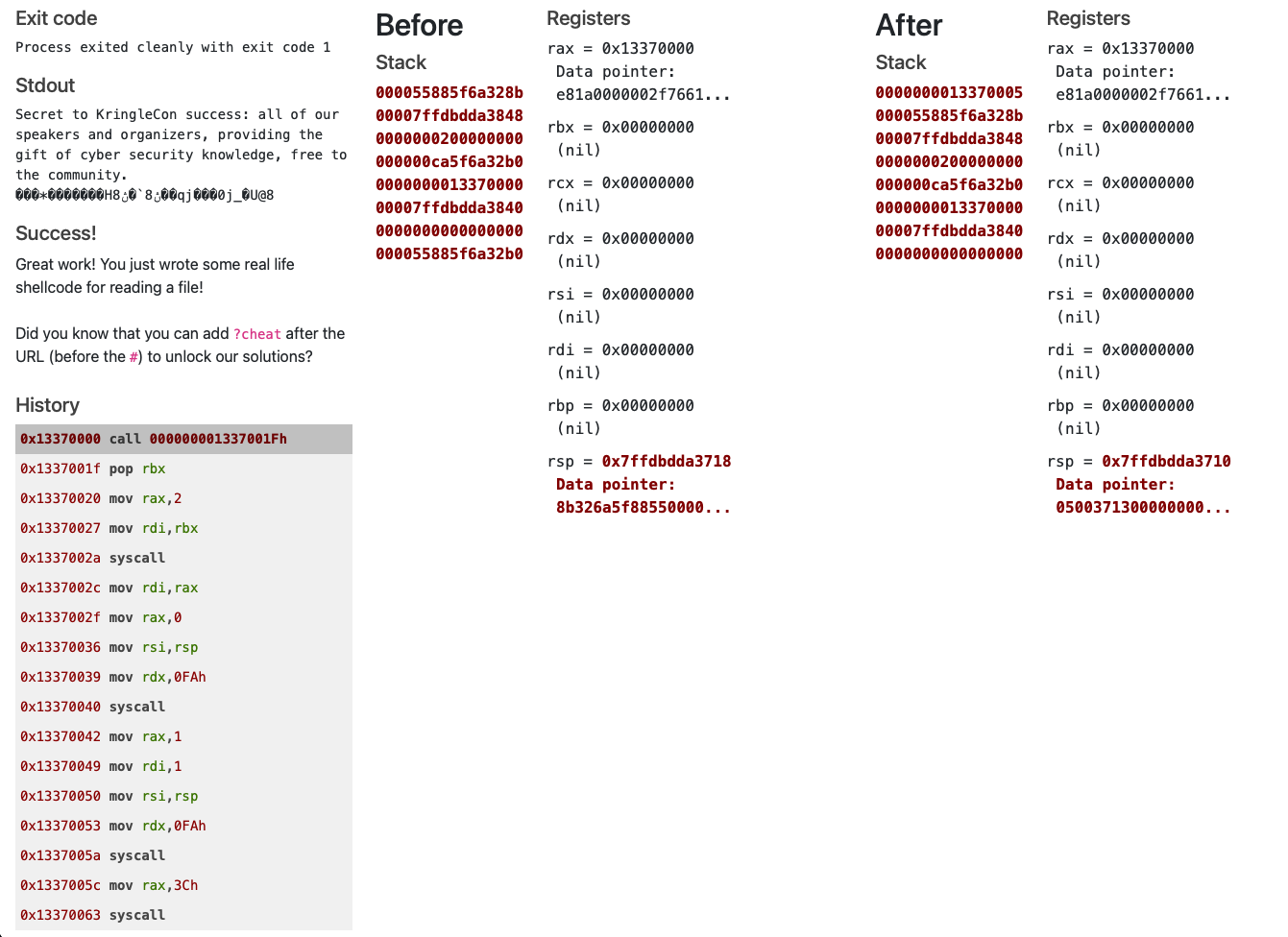
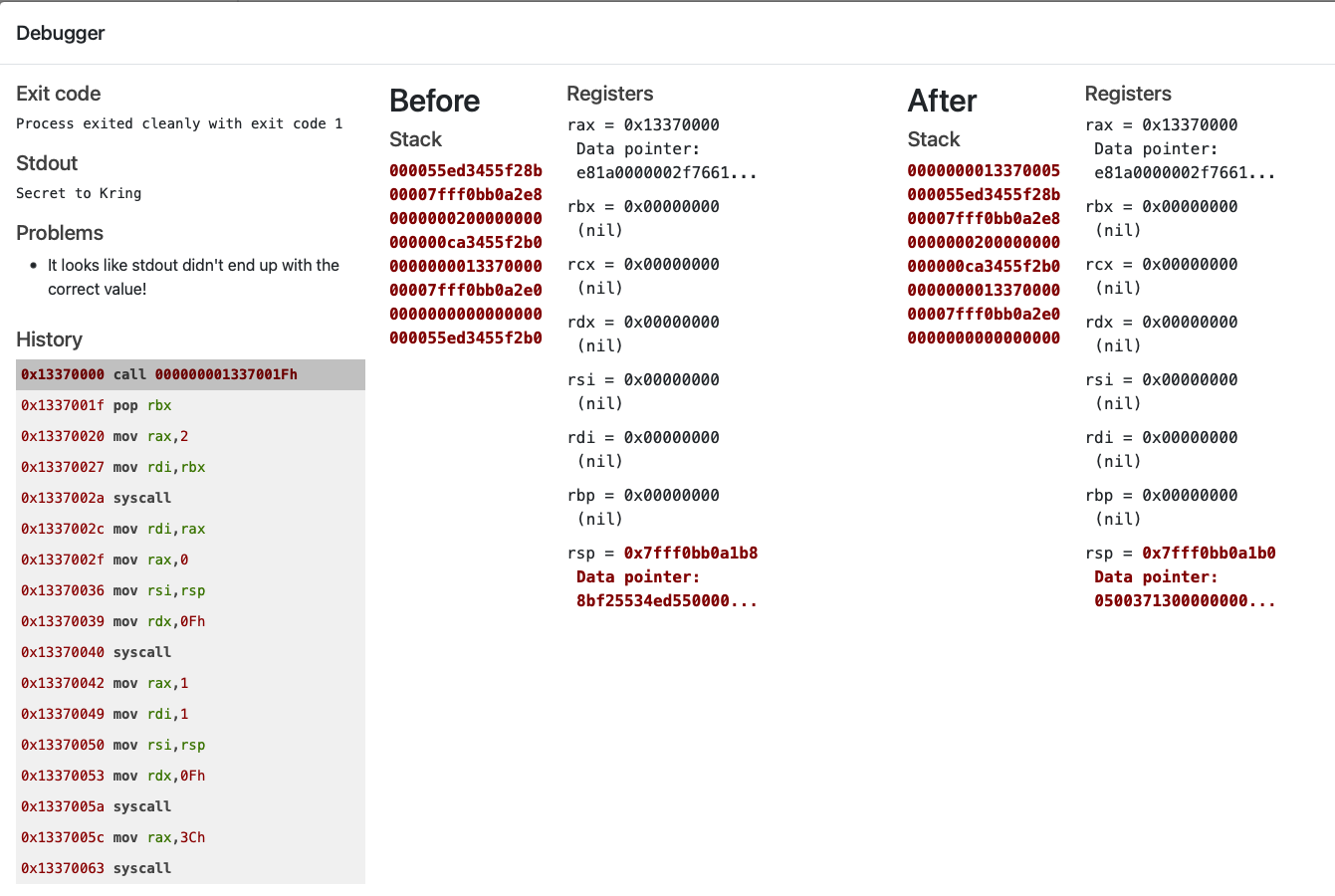
The string to prove successful completion of the challenge was:
cyber security knowledge
rcx
mov rax, 60 mov
Next: obj-7