Key Mission
Solved by Me.
Challenge Info

Solution
Downloaded and unzipped file, saw it was a .pcap. Opened pcap in wireshark, saw that the protocol was logged as USB for all packets.
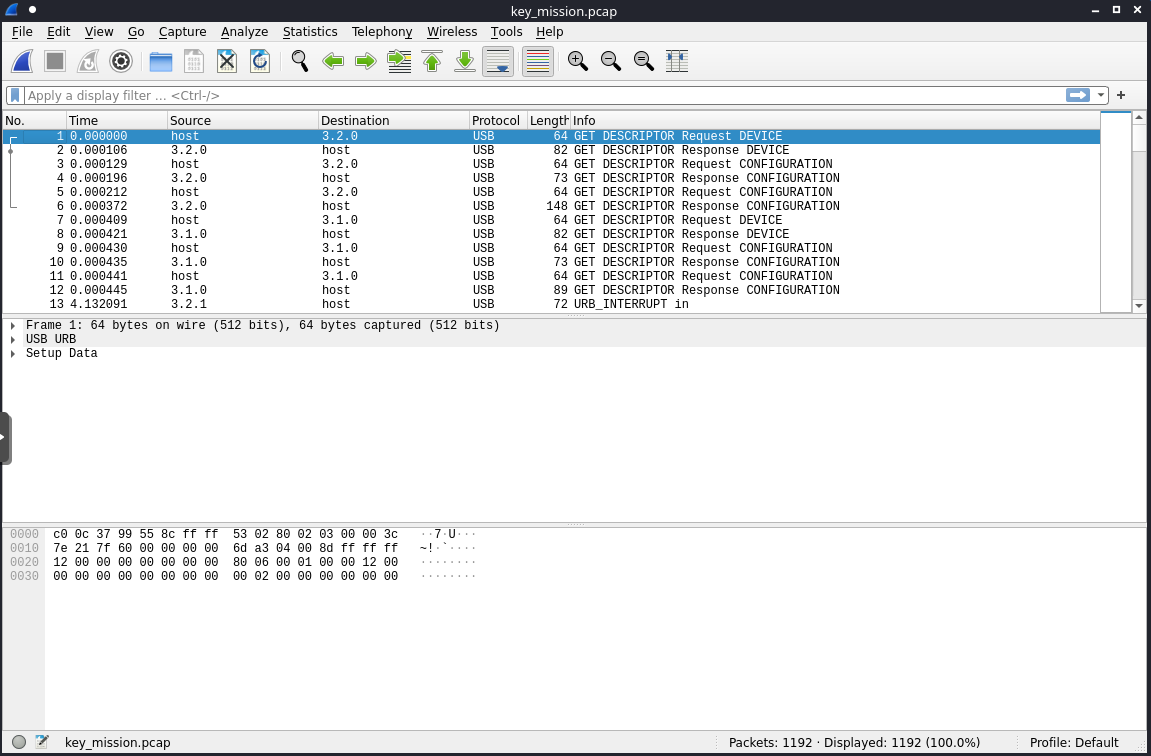
While investigating the handshake packets, I saw that the device appeared to be a Razer BlackWidow, aka a keyboard.
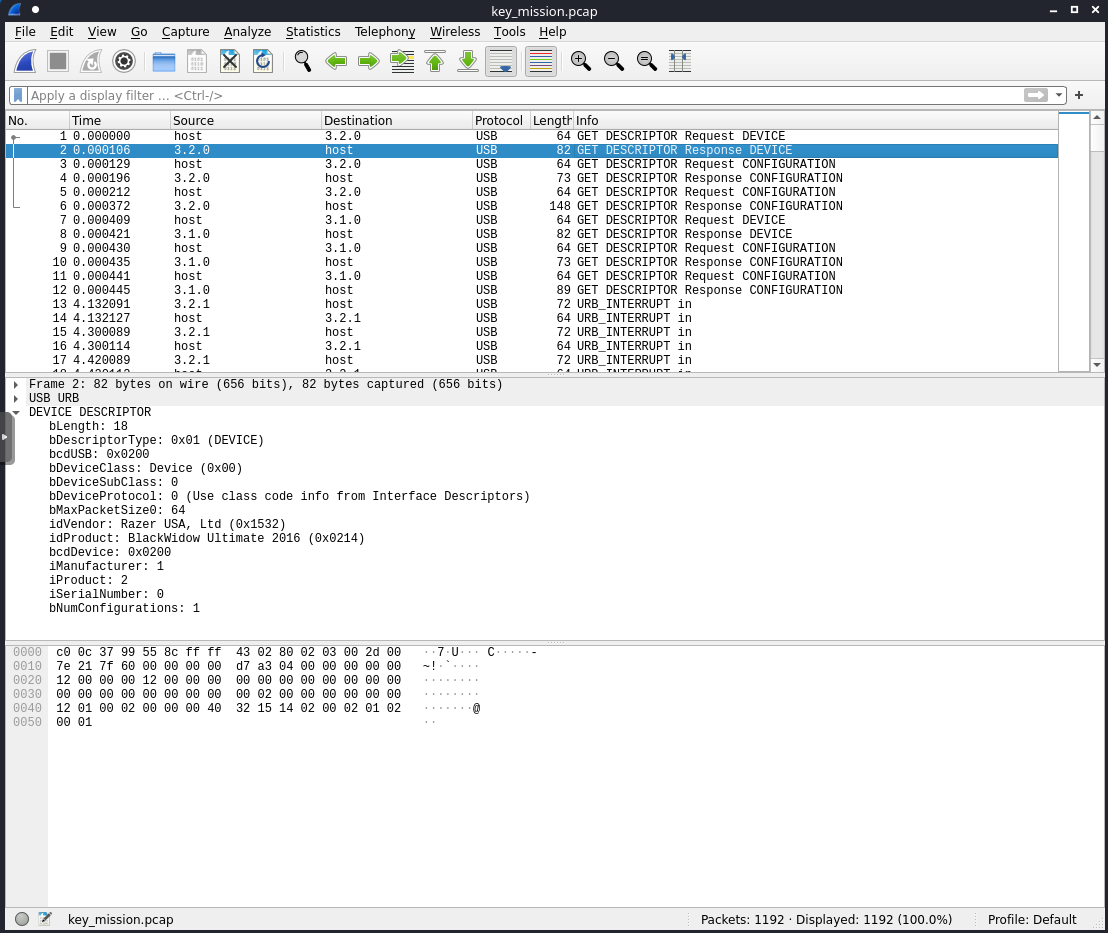
The HID input data appeared to be keystrokes on the wire being transmitted from keyboard to computer.
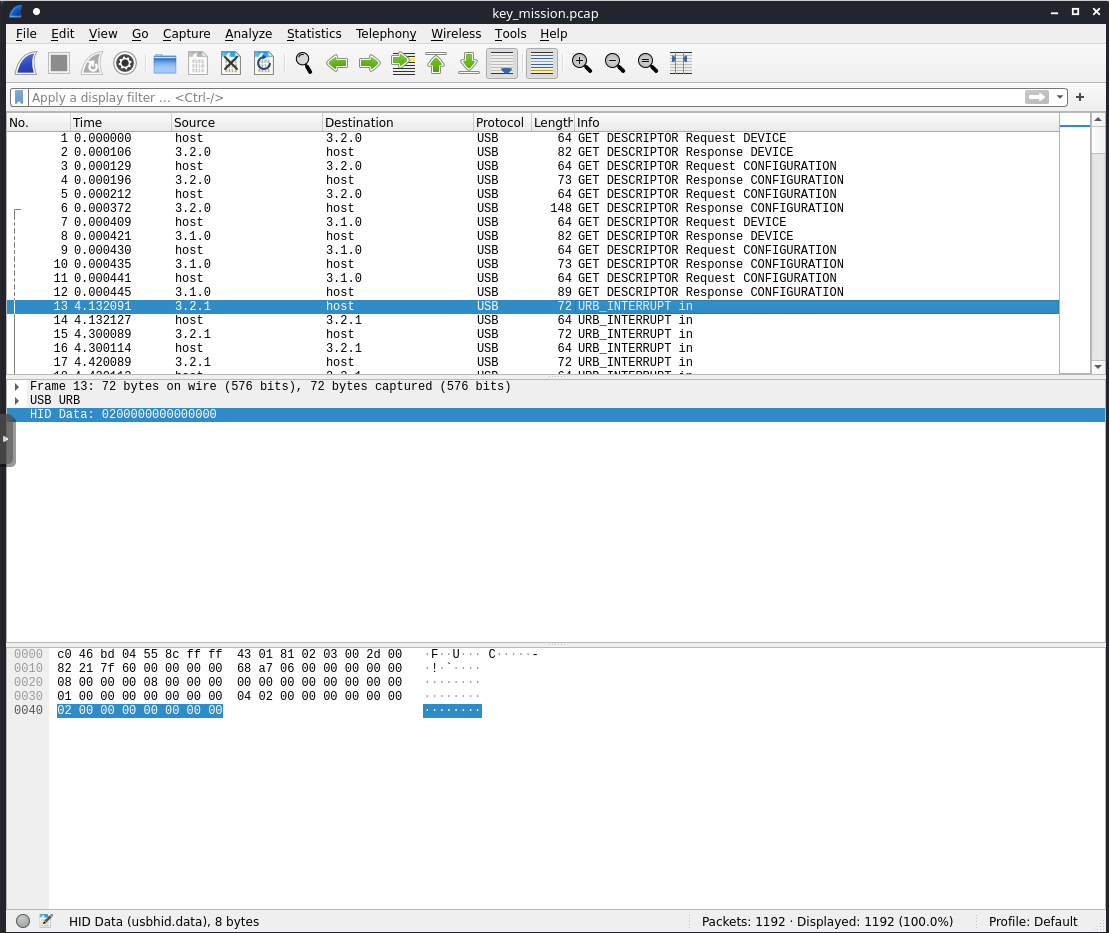
The URB transfer type was URB_INTERRUPT (0x01).
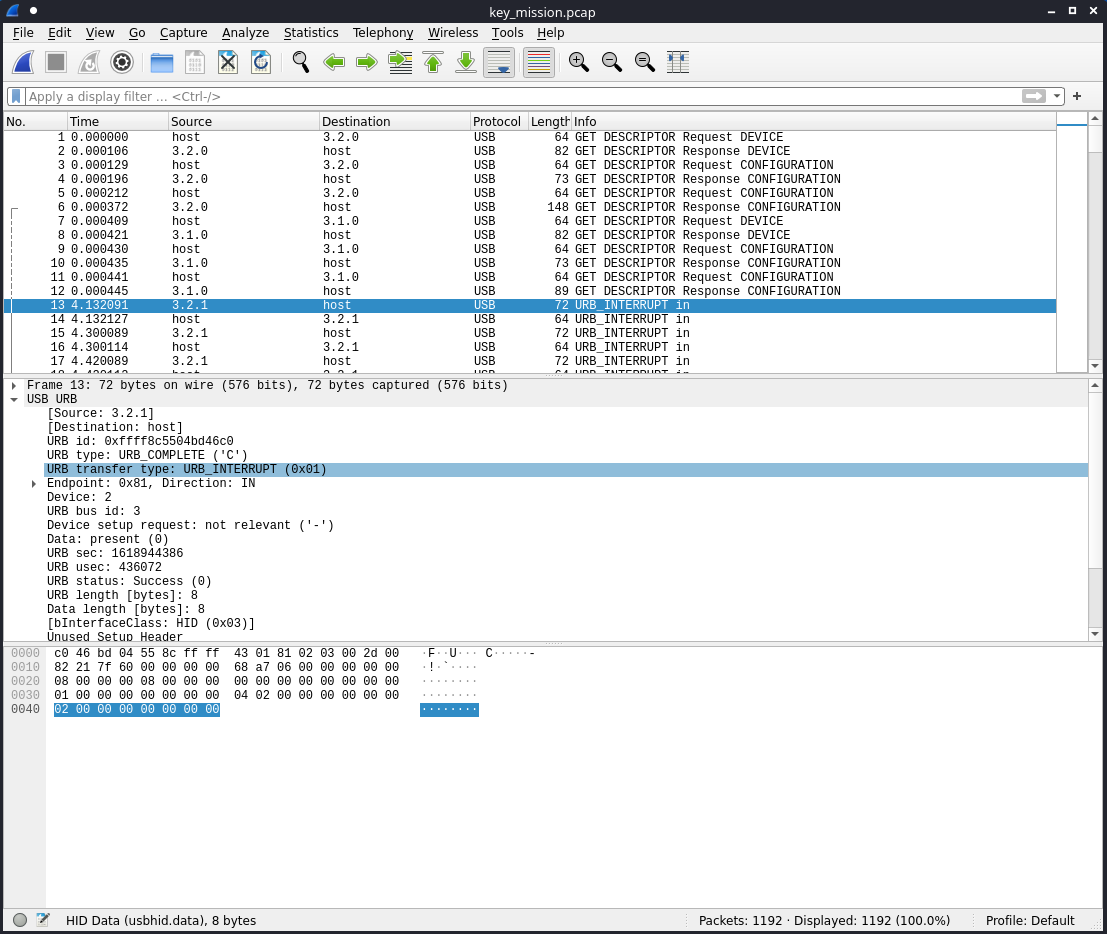
There were two packet types involved in the communication after the initial handshake, a URB_INTERRUPT in from the keyboard at 3.2.1 that was 72 bytes long, and a response from the host that was 64 bytes long. The 8 byte difference in each packet was the keyboard keypress.
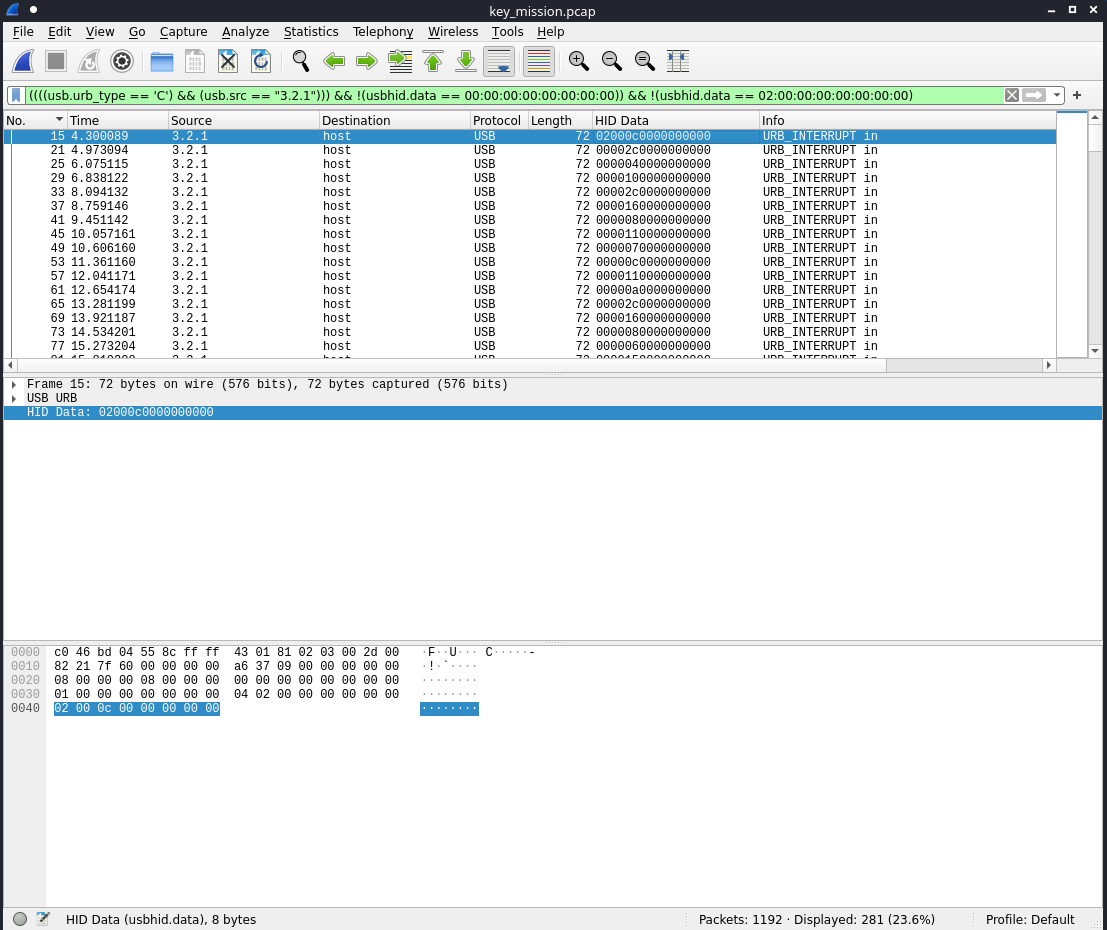
I saw that the URB type: URB_COMPLETE ('C') was the best filter to view only the char press packets.
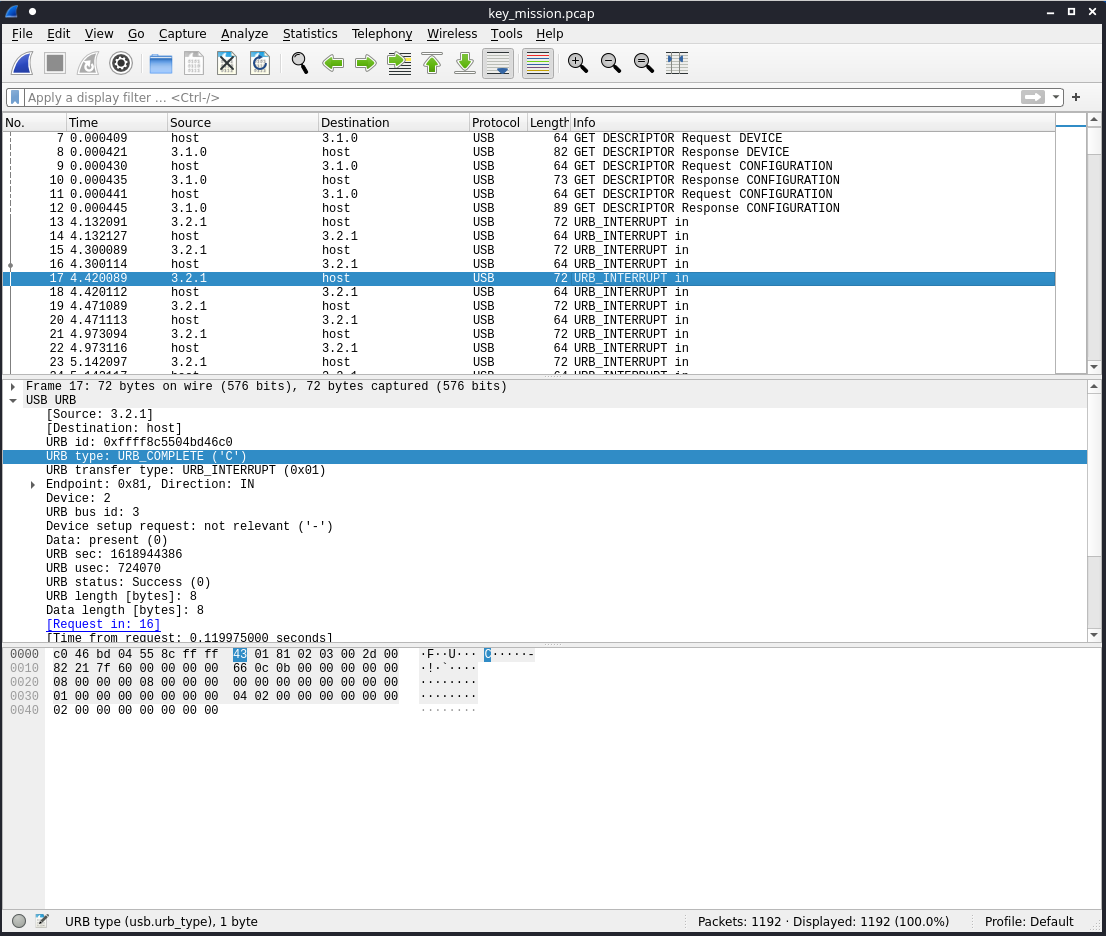
I narrowed the filter to JUST the char press packets by adding a usb source filter.
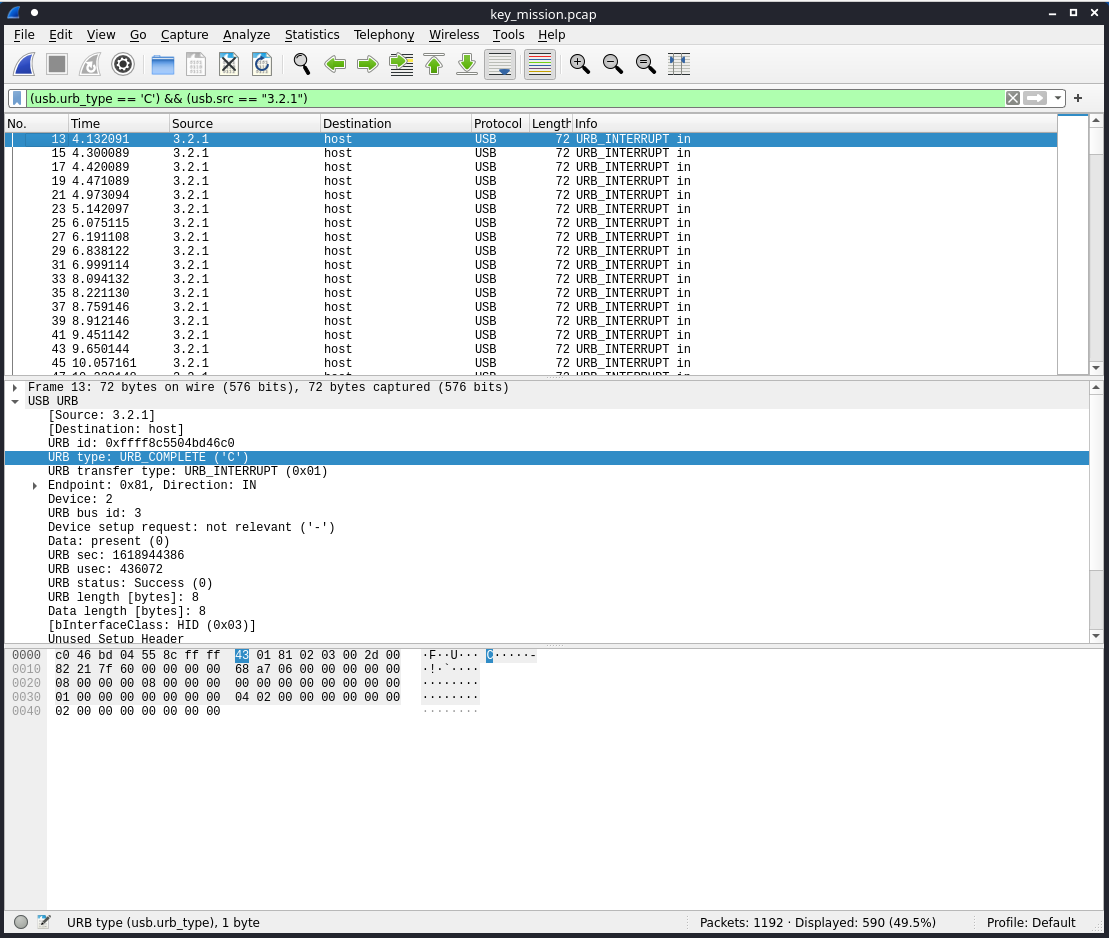
I selected the HID Data key value, then selected Apply as Column from the right-click menu:
This added the HID Data column to the packet window in wireshark:
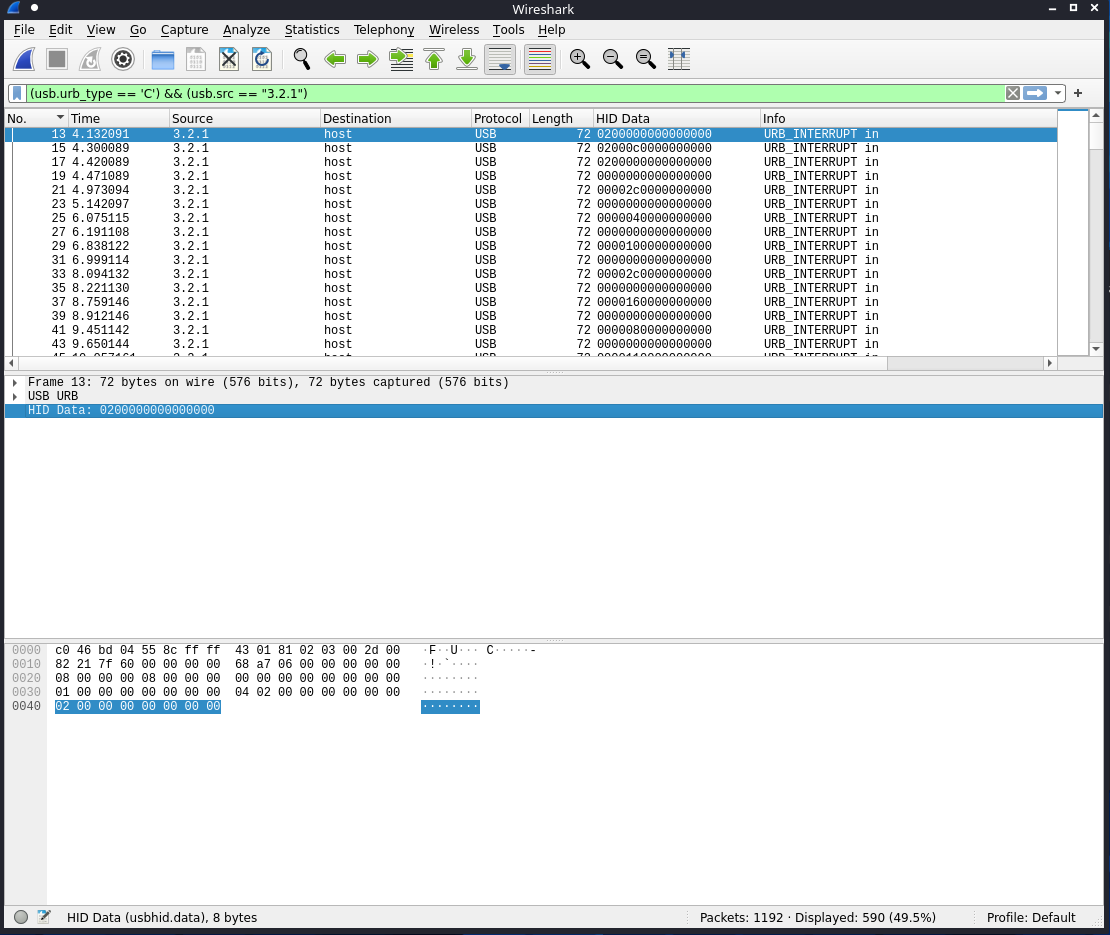
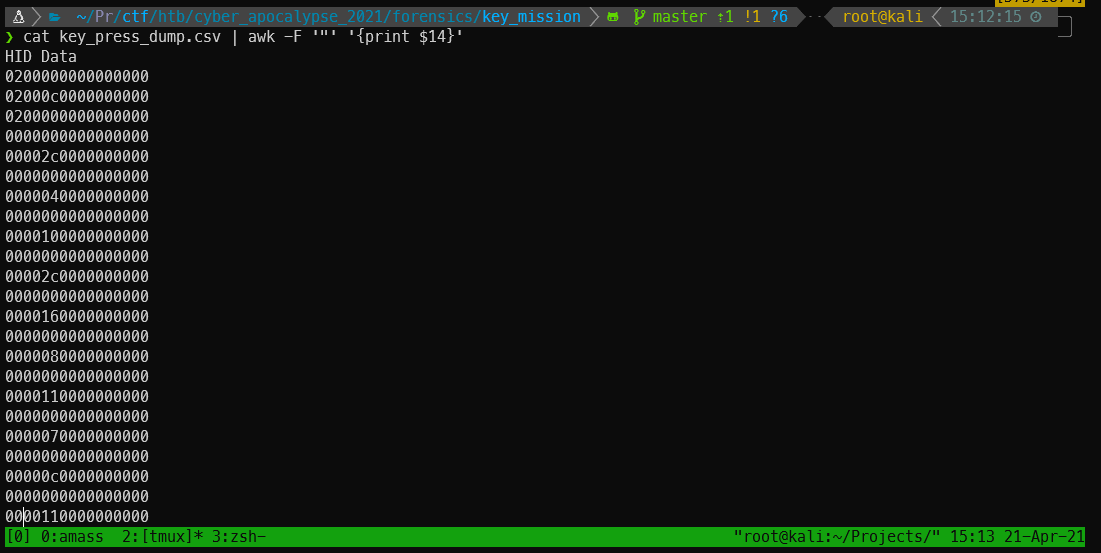
I saved the packets as a CSV, then I was able to print just the HID Data.
cat key_press_dump.csv | awk -F '"' '{print $14}'
Found list of HID Key scan codes, related as a dec and hex here: https://www.usb.org/sites/default/files/documents/hut1_12v2.pdf
I was initially having some trouble with getting the flag in the correct syntax, due to the characters printing multiple times, as well as the repeating \x02 byte from the shift key being pressed, plus the mask byte on the shifted key. I tuned the filter in WireShark to remove all the packets with an HID Data payload of 0000000000000000 and 0200000000000000.
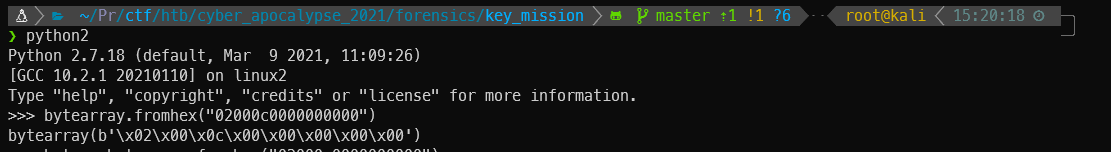
I also tested how the bytearray.fromhex() function worked in Python, and I saw that it split the 16 byte string into single bytes.
Based on that observation, I fixed a nested indent issue with my script that was causing some characters to print multiple times, and I re-ran the script on the hexOutput file sourced from the data exported with the updated WireShark filters. I also edited the array to display \x02 as 'ShiftMask'.
When I opened the output of this file, I saw a much easier to transcribe list.
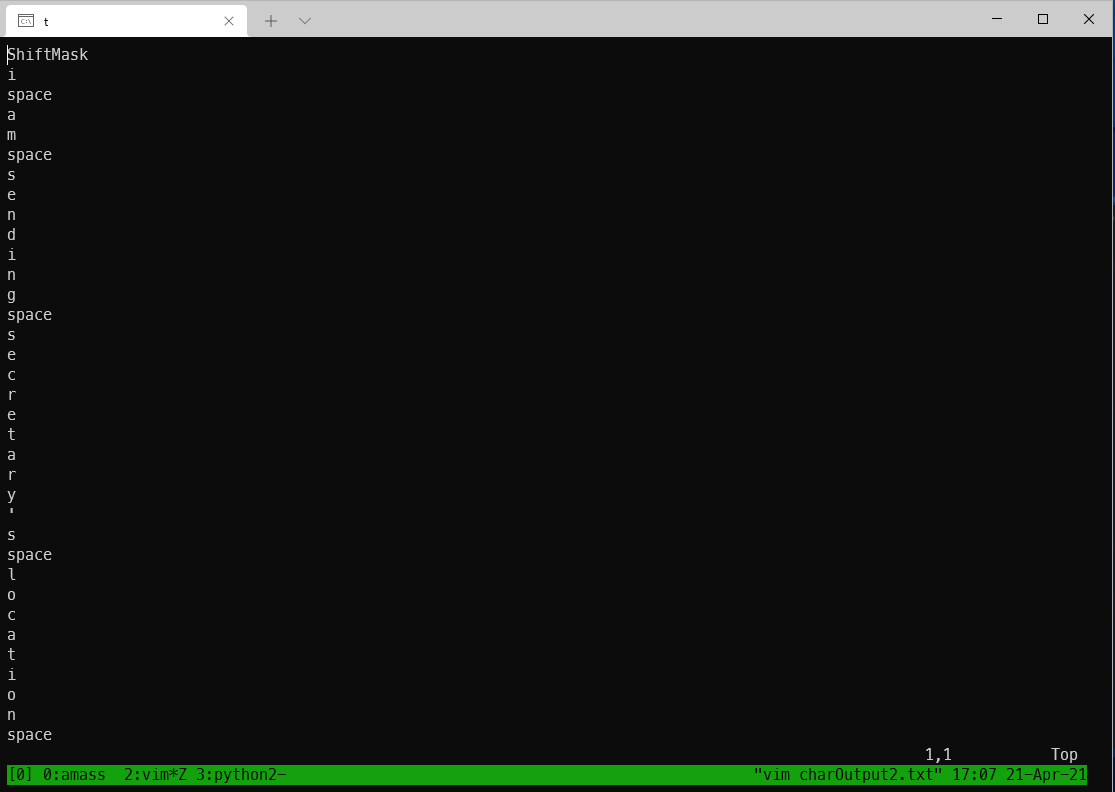
Transcribing the list led to the following:
I am sending secretary's location over this totally encrypted channel to make sure no one else will be able to read it except of us. This information is confidential and must not be shared with anyone else. The secretary' s hidden location is CHTB{a_plac3_fAr_fAr_away_fr0m_earth}
Flag
CHTB{a_plac3_fAr_fAr_away_fr0m_earth}