This Ain't a Scene, It's an Encryption Race
Instructions
Solution
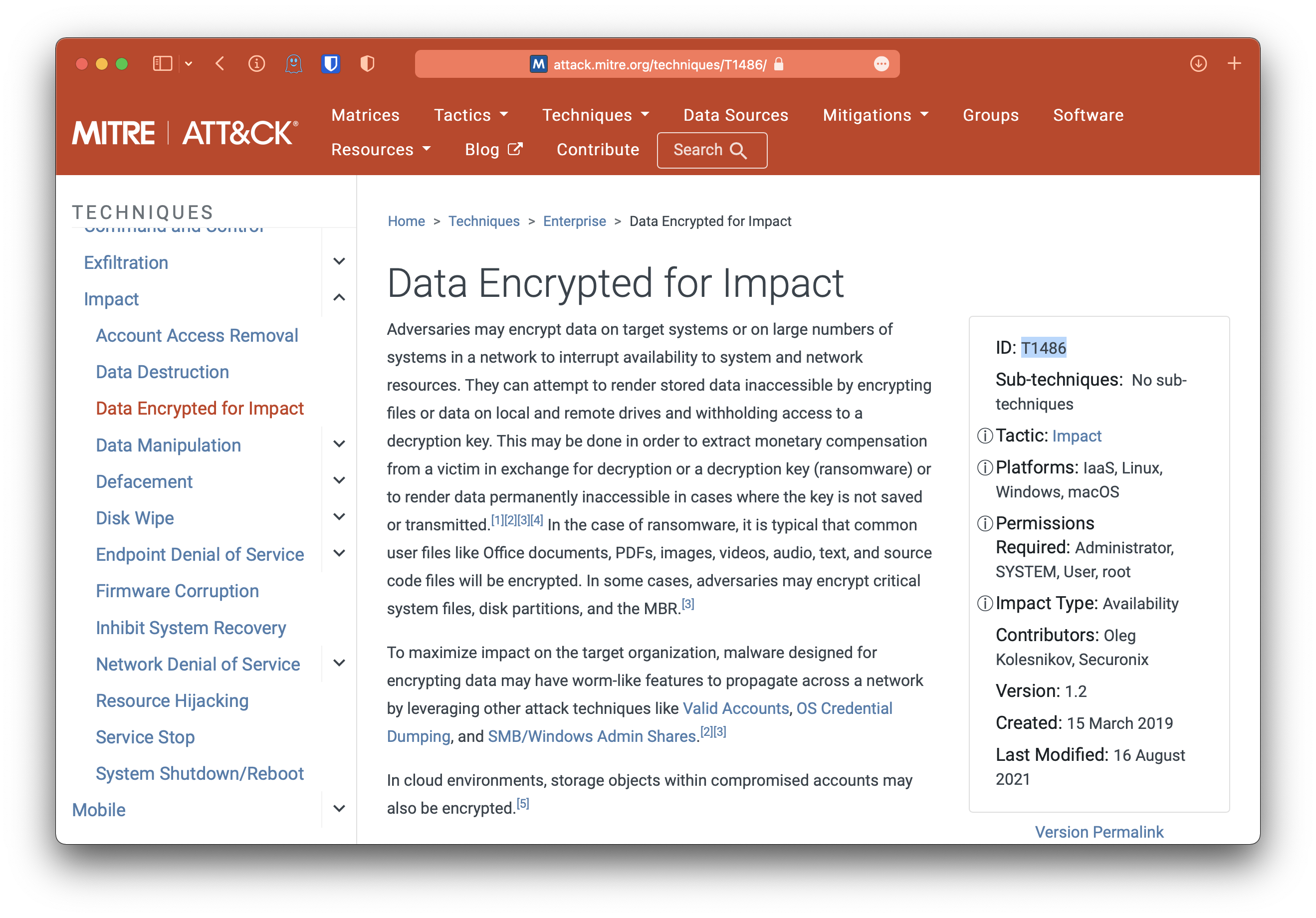
Found Data Encrypted for Impact technique at https://attack.mitre.org/techniques.
Next: A to Z

Found Data Encrypted for Impact technique at https://attack.mitre.org/techniques.

Next: A to Z