Templed
Instructions
Can you decrypt the message and get the flag?
Solution
Unzipping the file shows two files, an encoded flag and a public rsa key.
I can't for the life of me find it, but this is exactly like one of the HTB machine steps I had to do. The whole p, q, and e, and if one of them is small the whole thing is vulnerable. It was brainfuck!
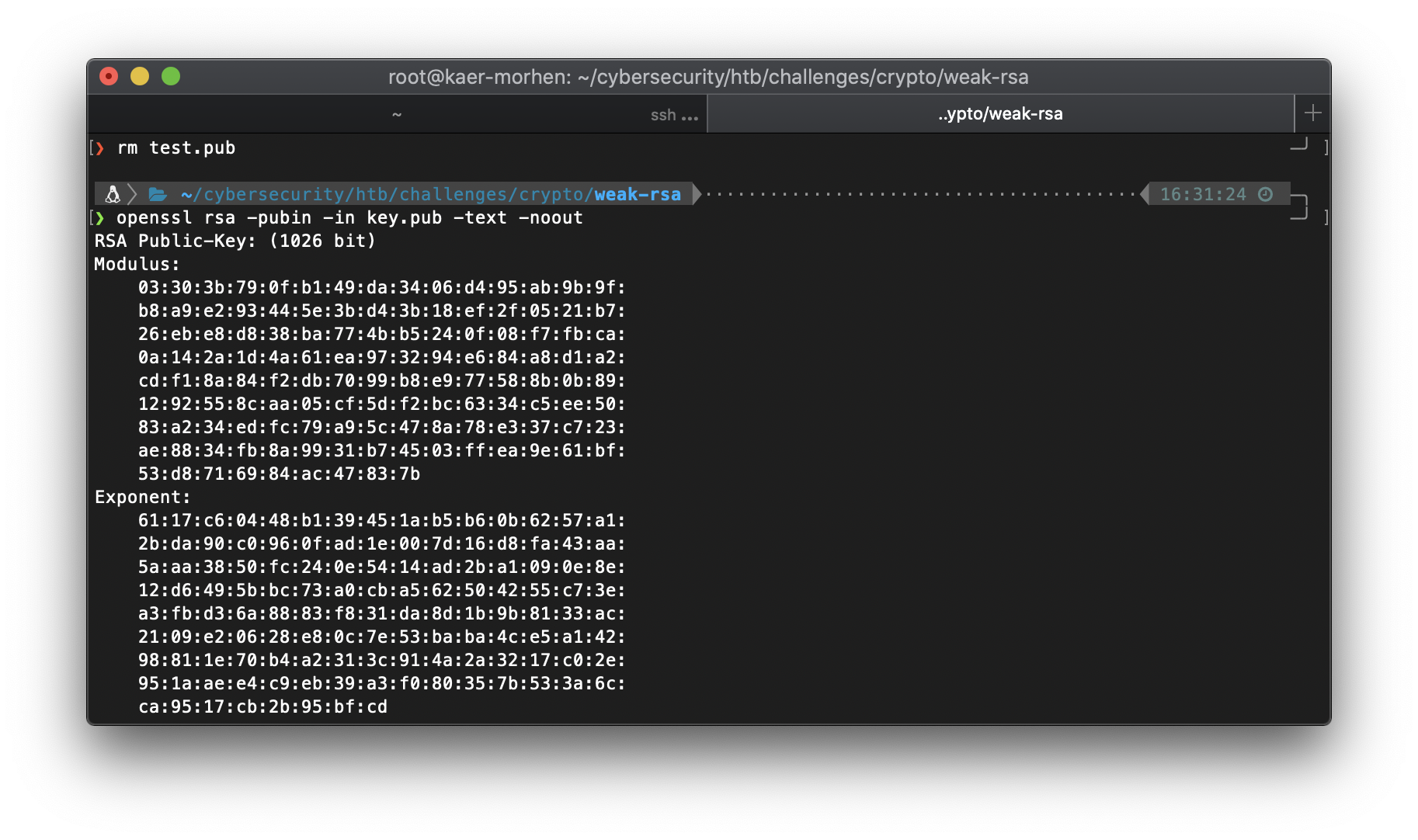
Ok, the script needs some other information in binary form. So I need to get the modulus and exponent etc. I can use openssl to get them.
openssl rsa -pubin -in key.pub -text -noout
I get the hex of the modulus with openssl and cut, and I store it to a local variable.
> HEX_MODULUS=$(openssl rsa -pubin -in key.pub -modulus -noout | cut -d'=' -f 2)
> echo $HEX_MODULUS
3303B790FB149DA3406D495AB9B9FB8A9E293445E3BD43B18EF2F0521B726EBE8D838BA774BB5240F08F7FBCA0A142A1D4A61EA973294E684A8D1A2CDF18A84F2DB7099B8E977588B0B891292558CAA05CF5DF2BC6334C5EE5083A234EDFC79A95C478A78E337C723AE8834FB8A9931B74503FFEA9E61BF53D8716984AC47837B
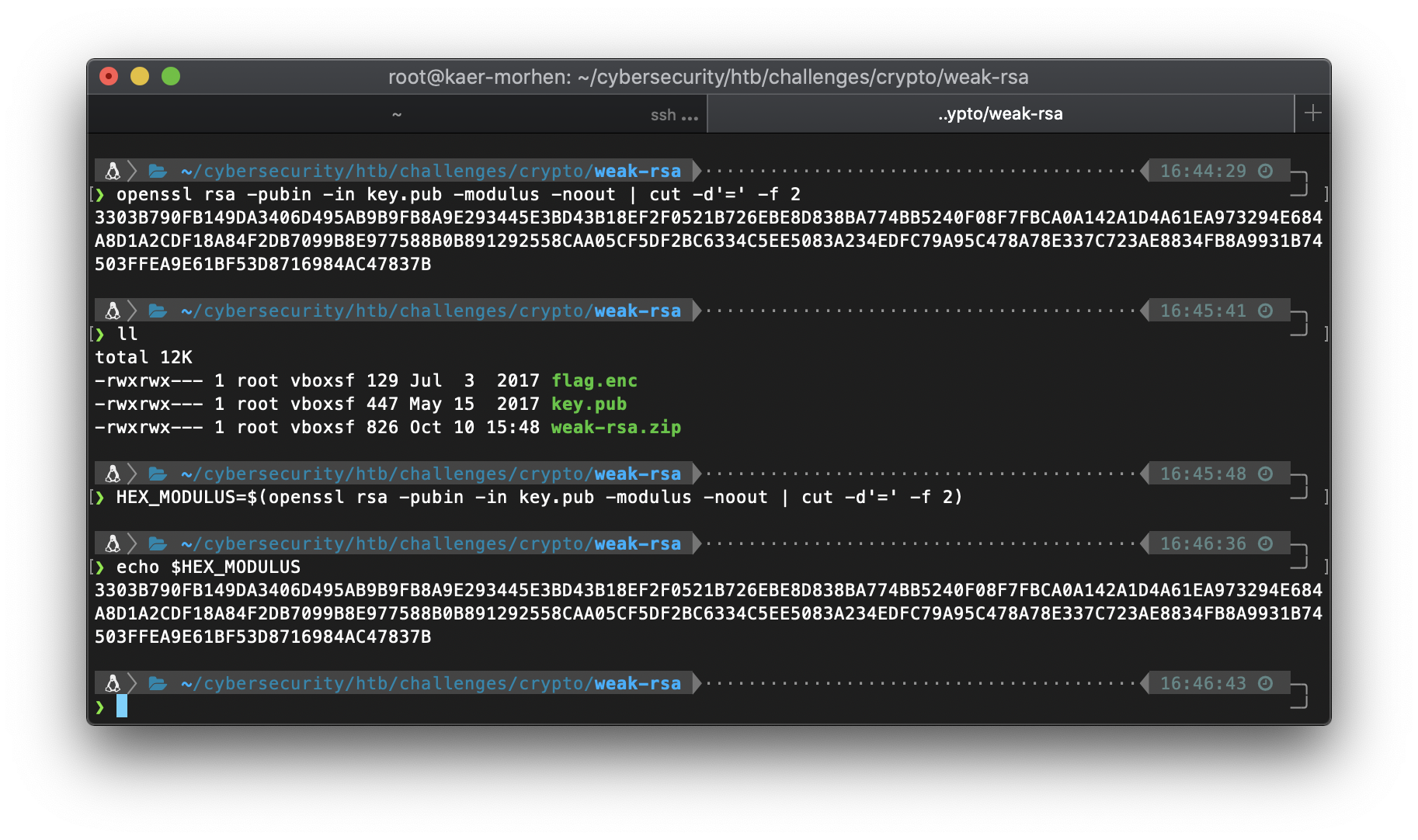 Then I can use the ruby interpreter to flip it to binary real quick.
Then I can use the ruby interpreter to flip it to binary real quick.
ruby<<EOF
heredoc> p "$HEX_MODULUS".to_i(16).to_s(10)
heredoc> EOF
"573177824579630911668469272712547865443556654086190104722795509756891670023259031275433509121481030331598569379383505928315495462888788593695945321417676298471525243254143375622365552296949413920679290535717172319562064308937342567483690486592868352763021360051776130919666984258847567032959931761686072492923"
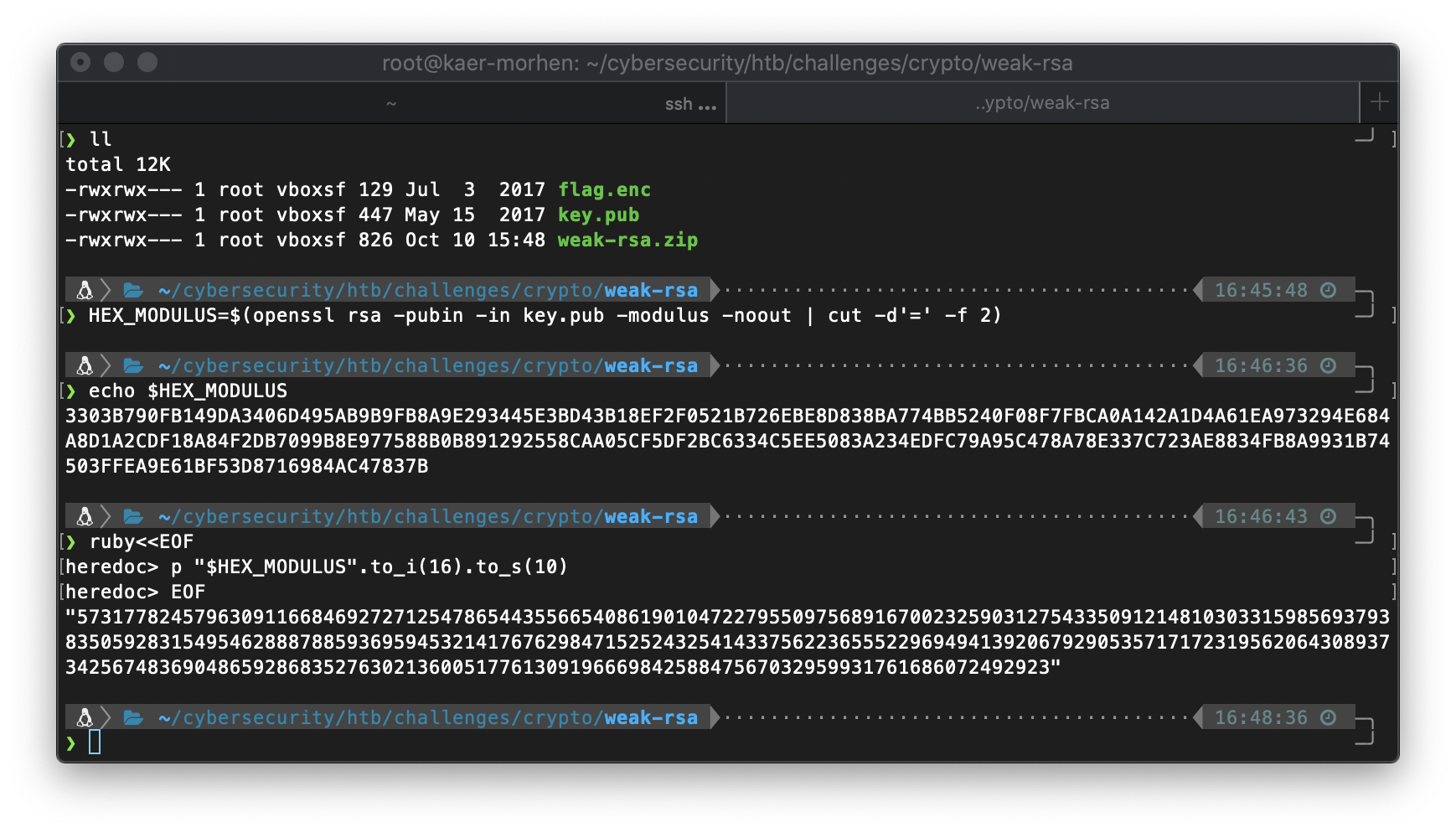 HOLD THE FUCK UP. Ok, I can use the Crypto library in python3 to do this so much easier… All I did was open the interpreter and import like 1 library lol.
HOLD THE FUCK UP. Ok, I can use the Crypto library in python3 to do this so much easier… All I did was open the interpreter and import like 1 library lol.
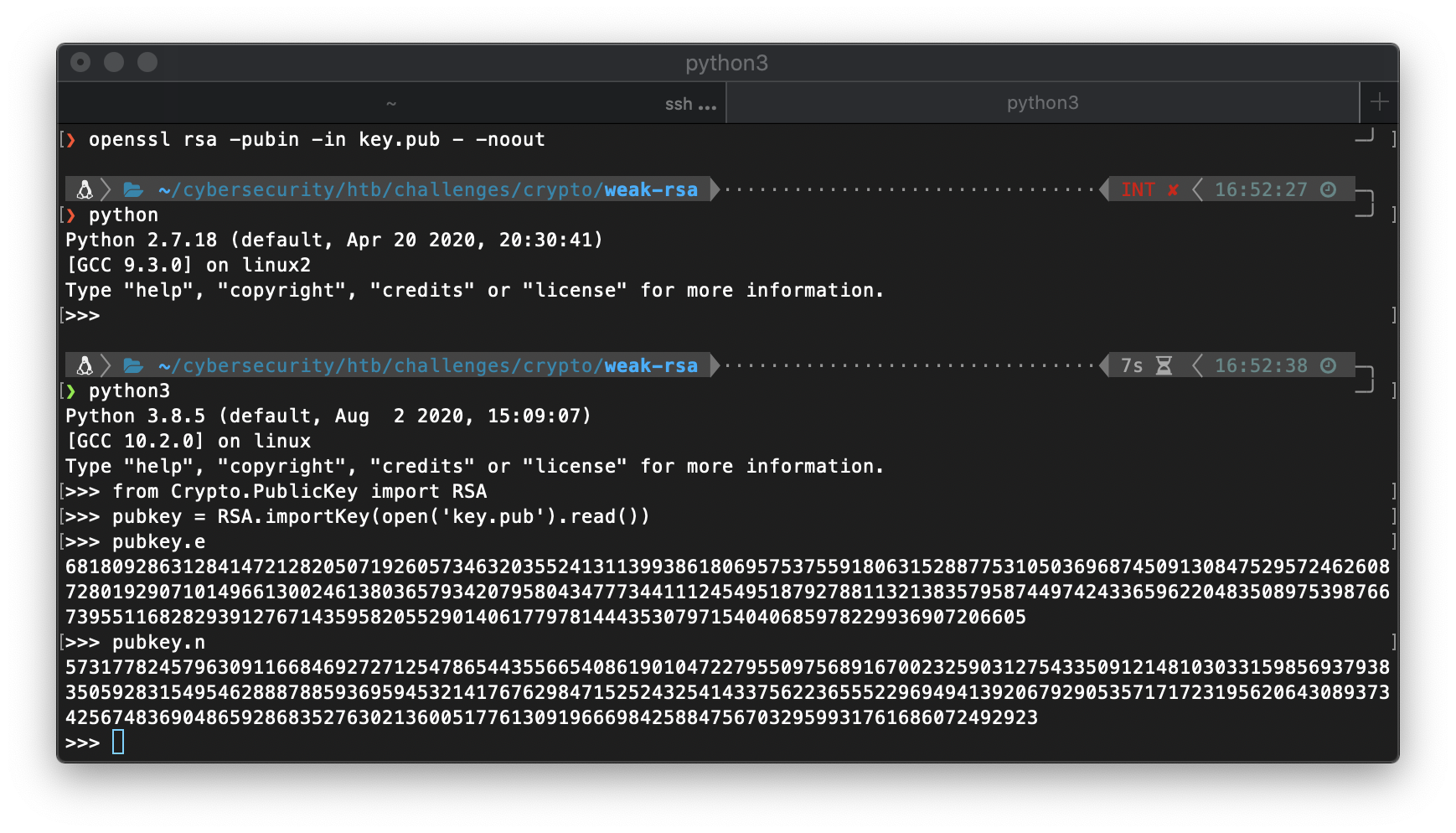
 wait…
wait…