Took the Byte
Notes
This is the third HTB challenge I have done. This challenge was created by CharlesTruluck. It has an easy rating and is worth 20 points.
Objective
Someone took my bytes! Can you recover my password for me?
Solution
Well, the clue prompt doesn't really give me much to go on here, so lets just jump in and see what files we have.
Unzipping the file dumps just a single file named password.
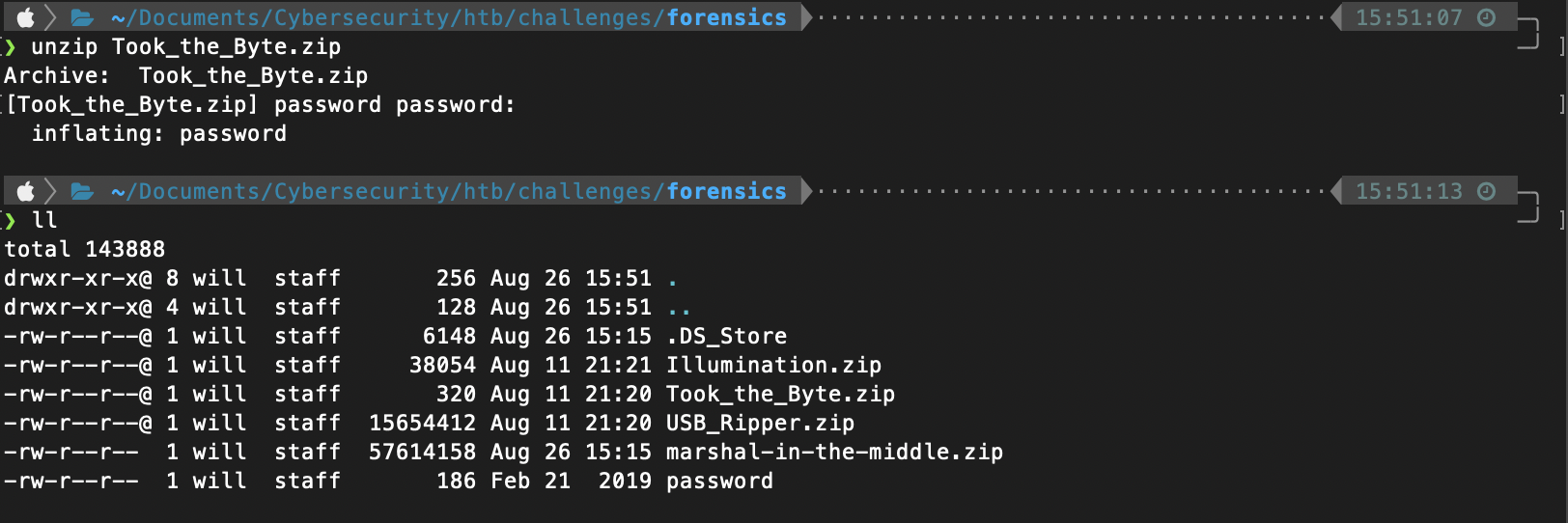
Using cat just dumps illegible data.
Strings doesn’t find anything useful.
I took a look at the HTB forums. On page 1 I saw a reference to using a hex editor.
Using xxd I can see the hex contents of the file.
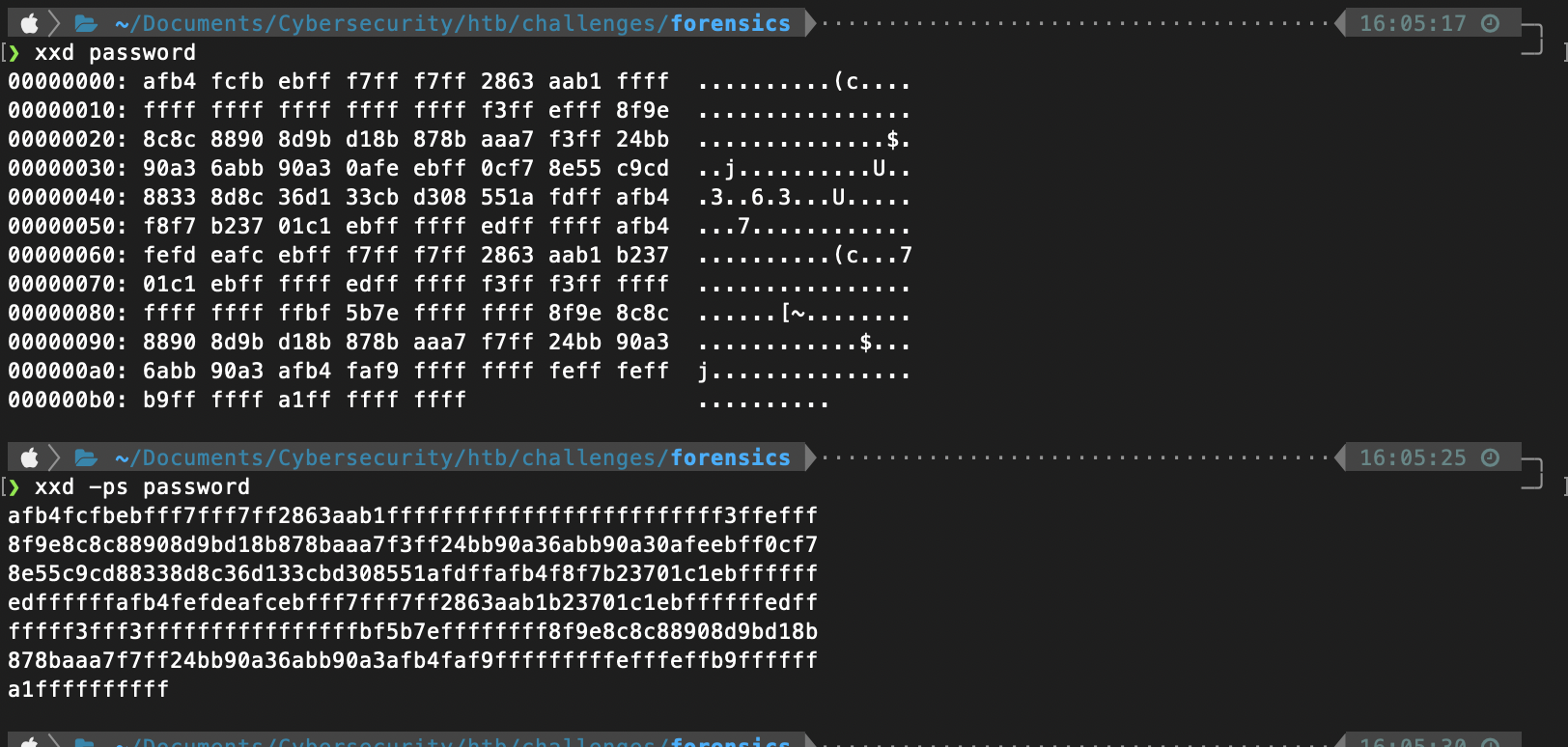
I still have no idea what this is, but the hex byte ff is repeated a ton here.
Ok, I'll upload this file to cyberchef and see what that makes of it.
I had to drag/drop the file in to cyberchef, for whatever reason it didn't like uploading through the dialog prompt.
Once uploaded, I ran the recipe named 'Magic' because it attempts to process the input data and recommend other operations that could help make sense of it…
Nothing was found during the initial run.
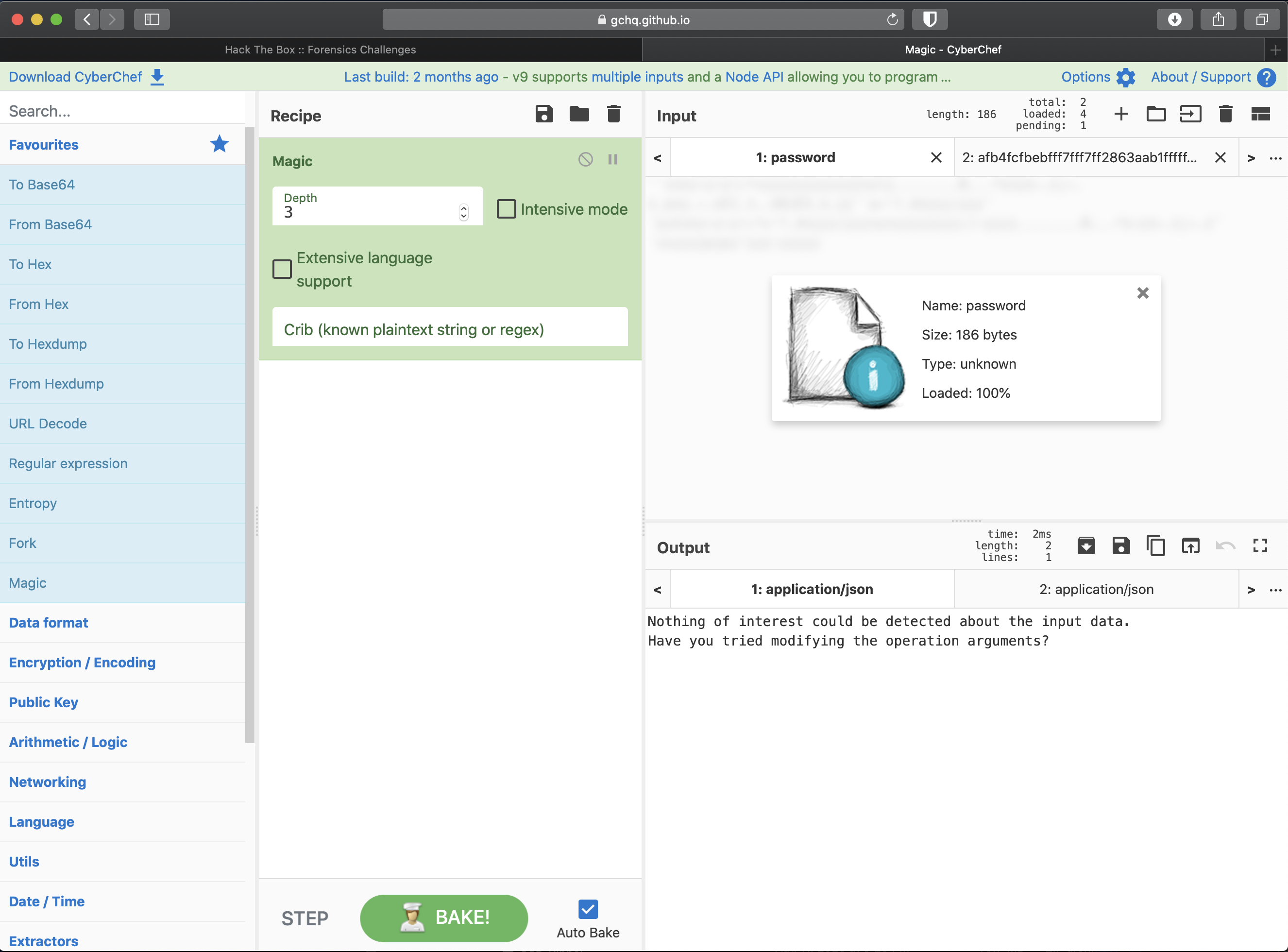
Ok, as it says in the output box, next I tried by modifying an operation argument, specifically enabling Intensive Mode.
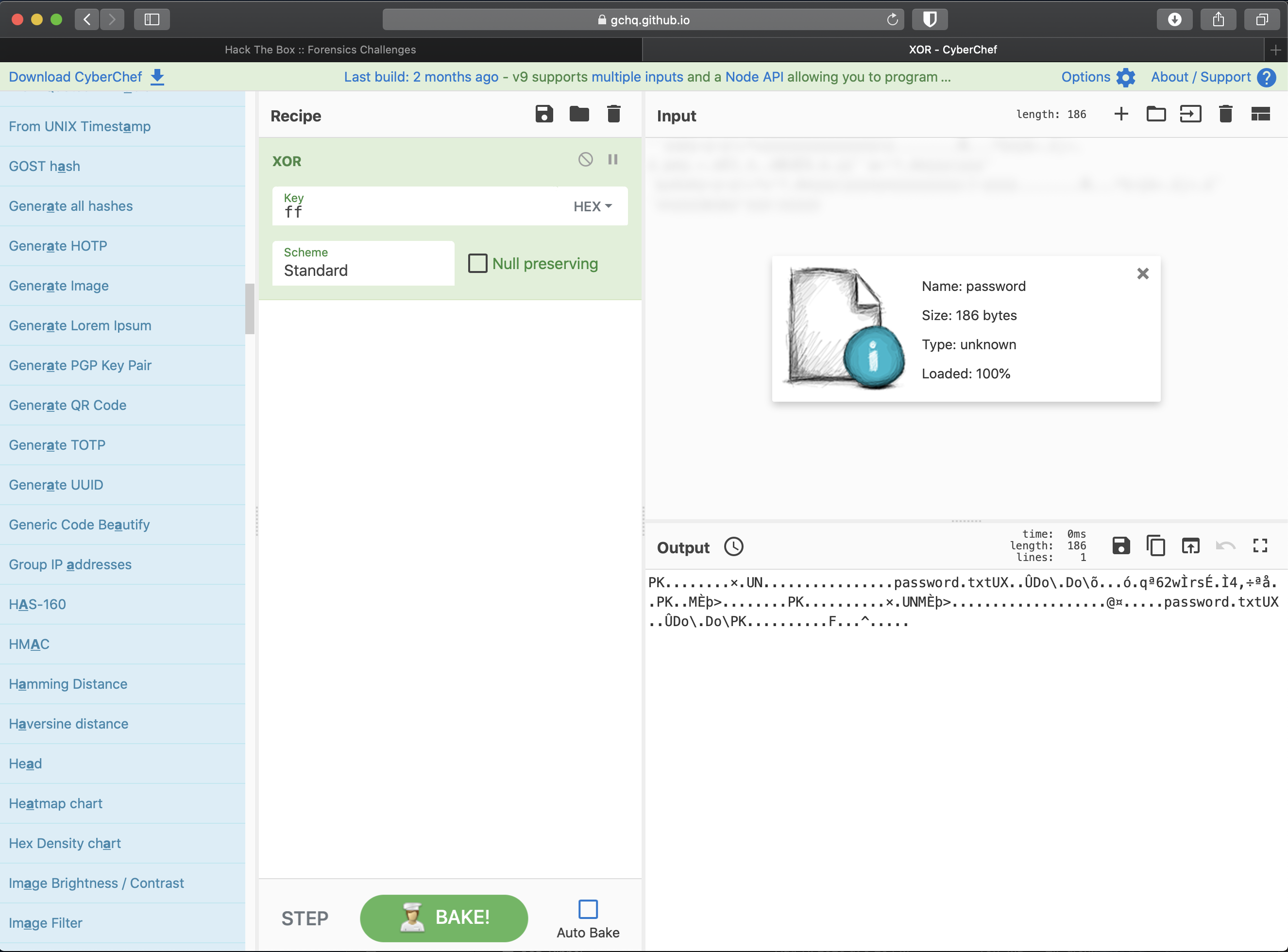
Alright, now the recipe result says that if I run the XOR recipe with the bit ff, I will wind up with a .zip.
So I add the XOR recipe with the correct settings, get a result with the PK magic byte.
I am able to unzip the file from within cyberchef and get the flag.
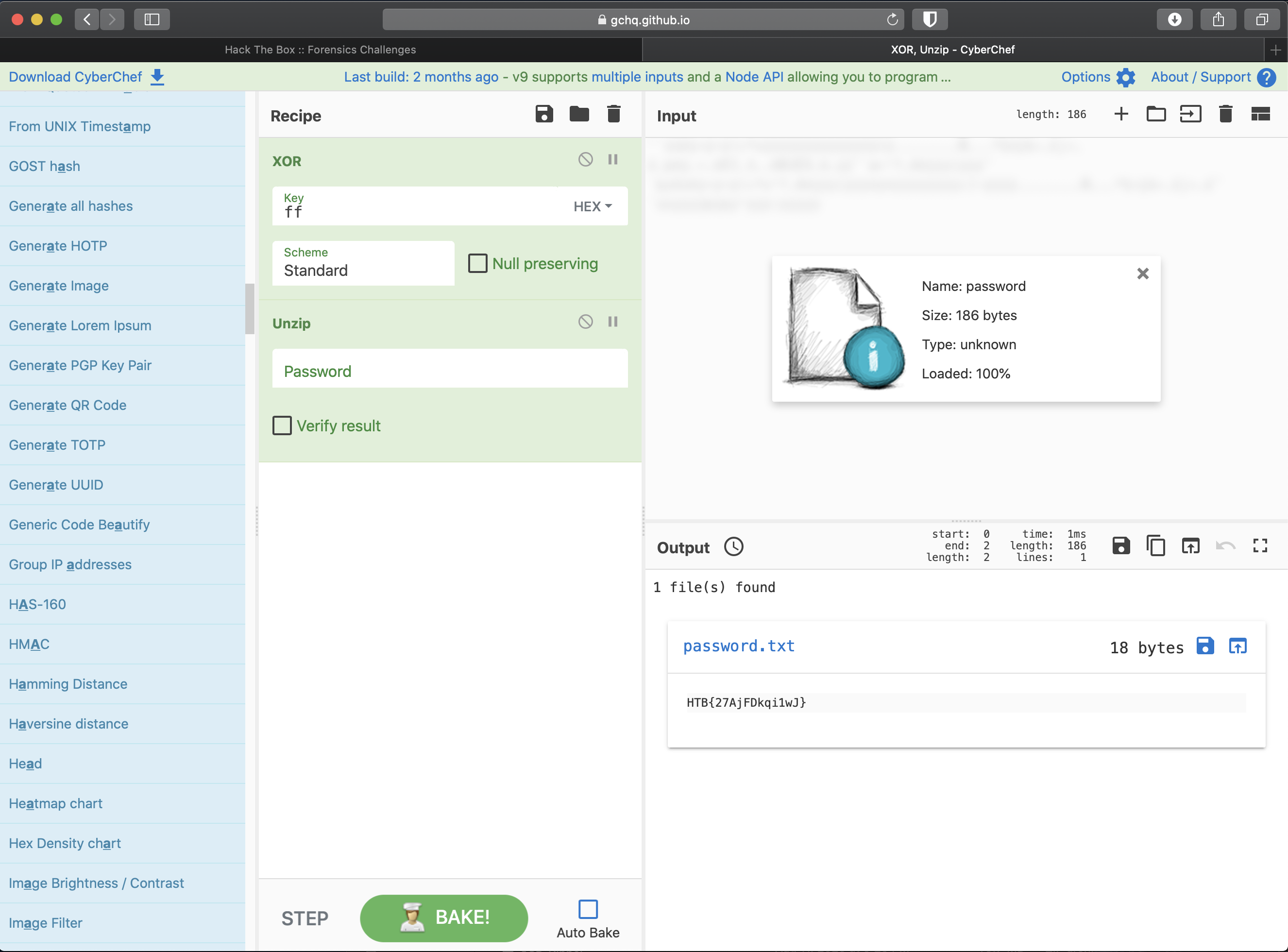
Flag
HTB{27AjFDkqi1wJ}